-
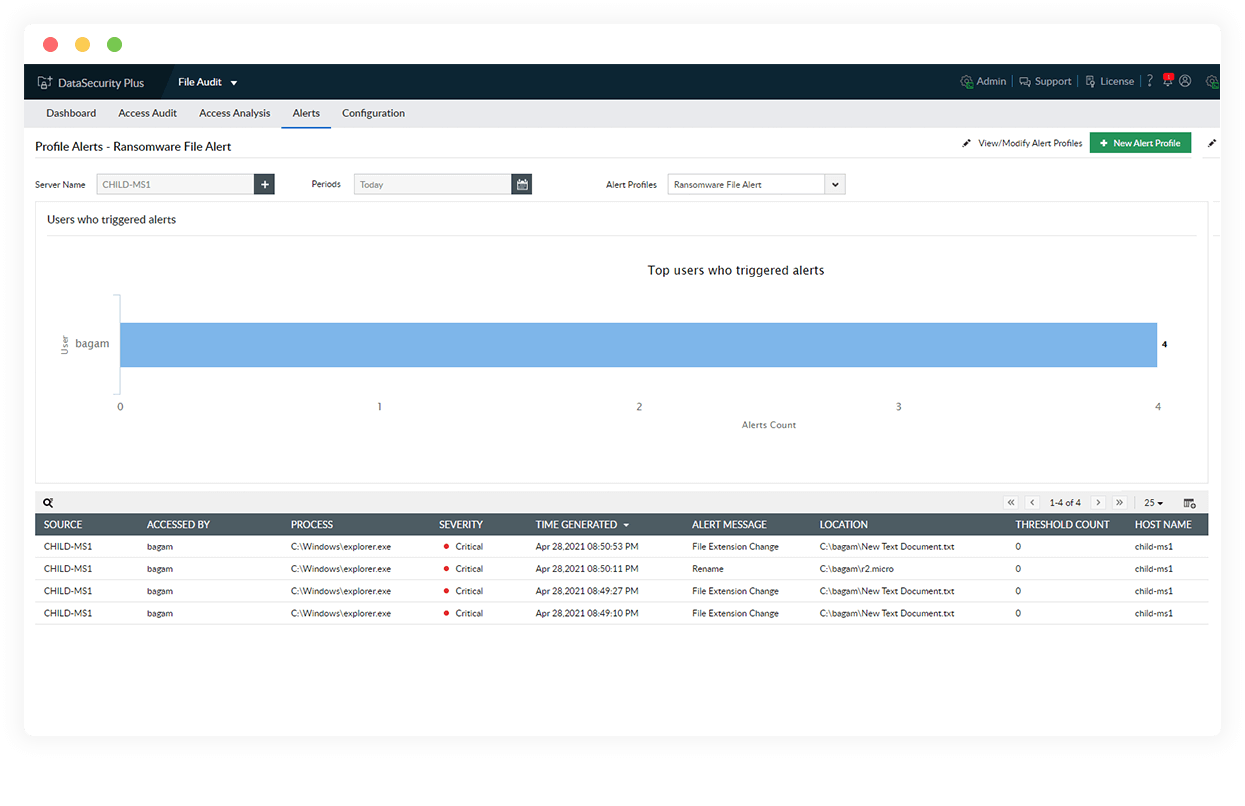
Spot ransomware attacks
Identify potential ransomware infections by tracking anomalous file activities that indicate the infiltration of harmful malware into the network.
-
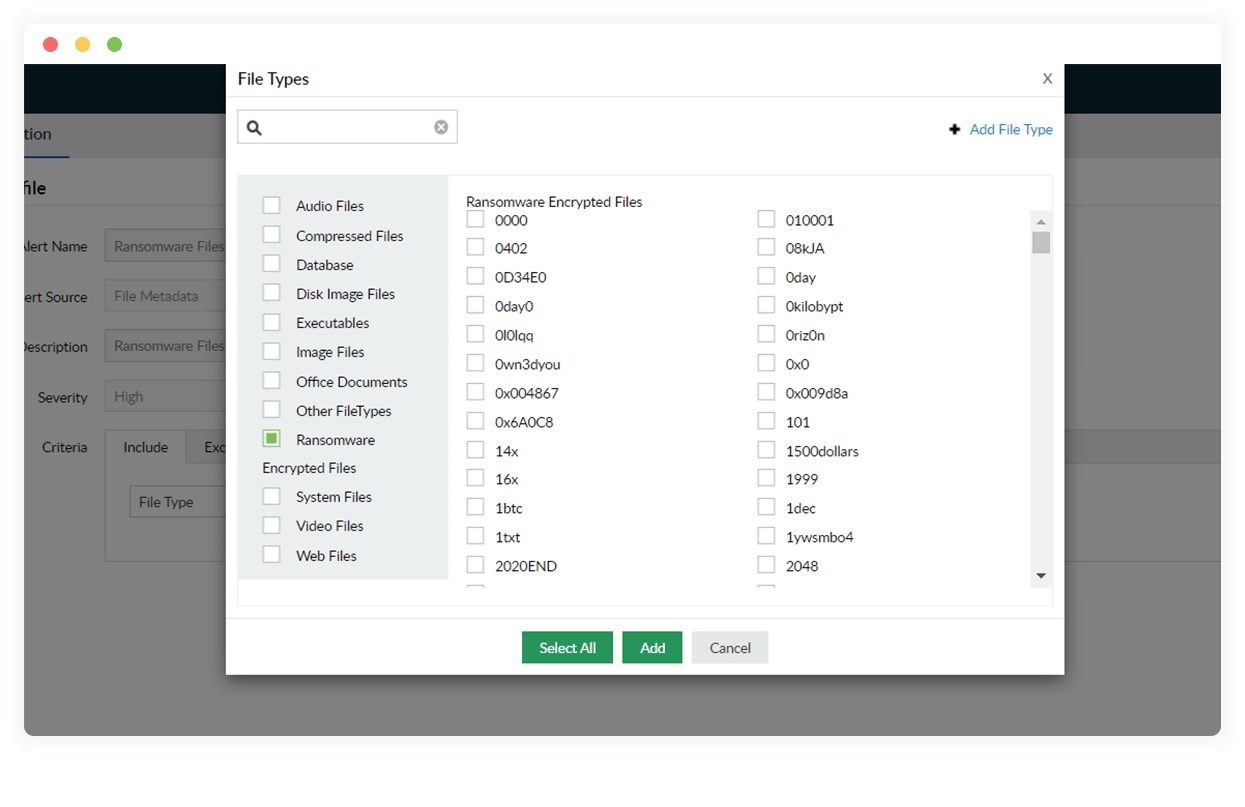
Locate infected files
Detect corrupted files using our library of known ransomware file types and purge them using the automated ransomware response mechanism.
-
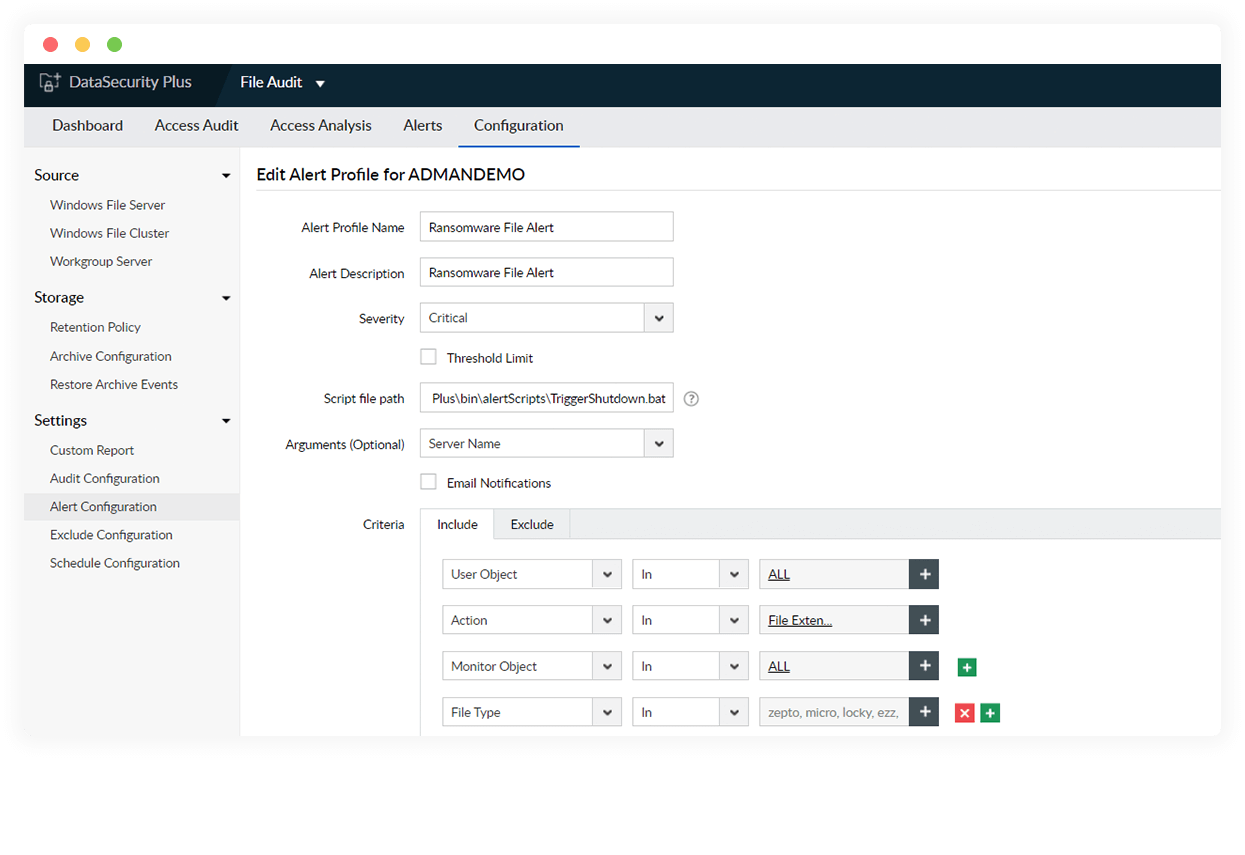
Launch automatic responses
Contain and curb further spread of malware by instantly quarantining and shutting down infected systems.
-
Create an incident response plan
Use reports to spot the source of a malware attack. Analyze audit trails to refine the ransomware response plan and minimize damage in the future.
Detect, stop, and prevent ransomware attacks using our ransomware protection software