-
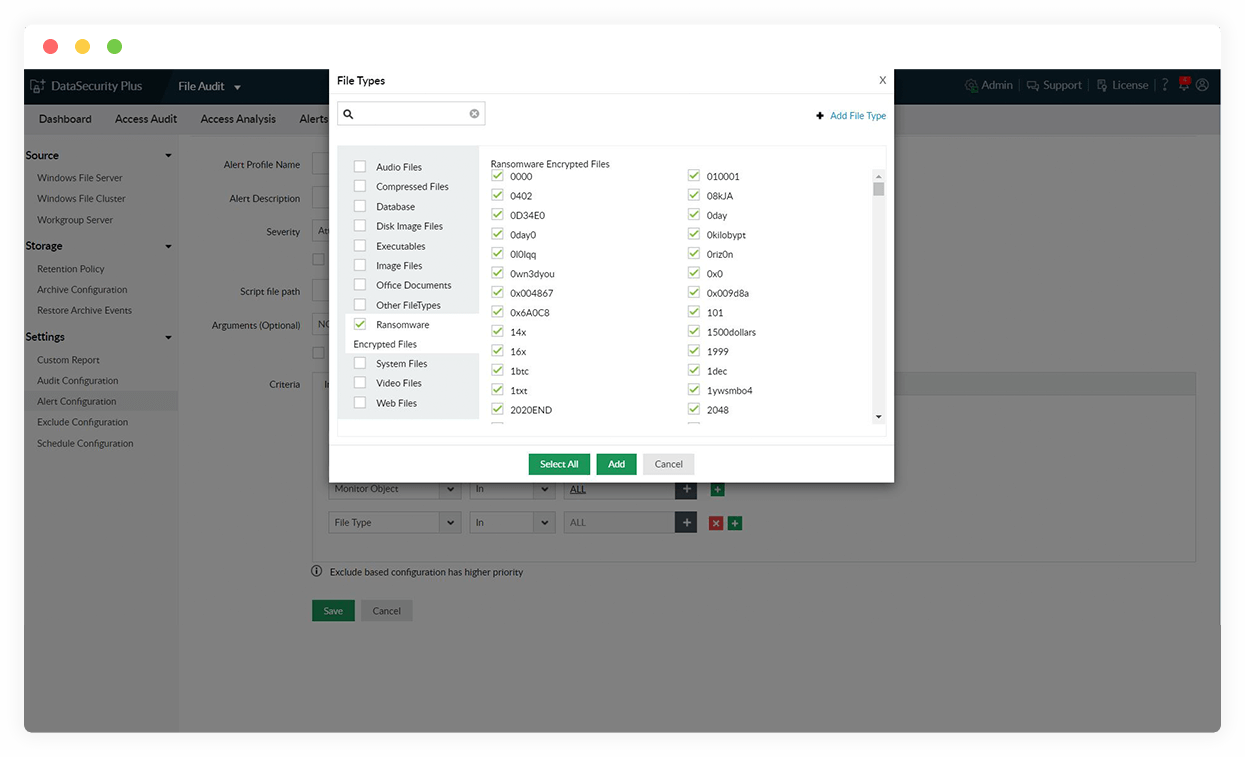
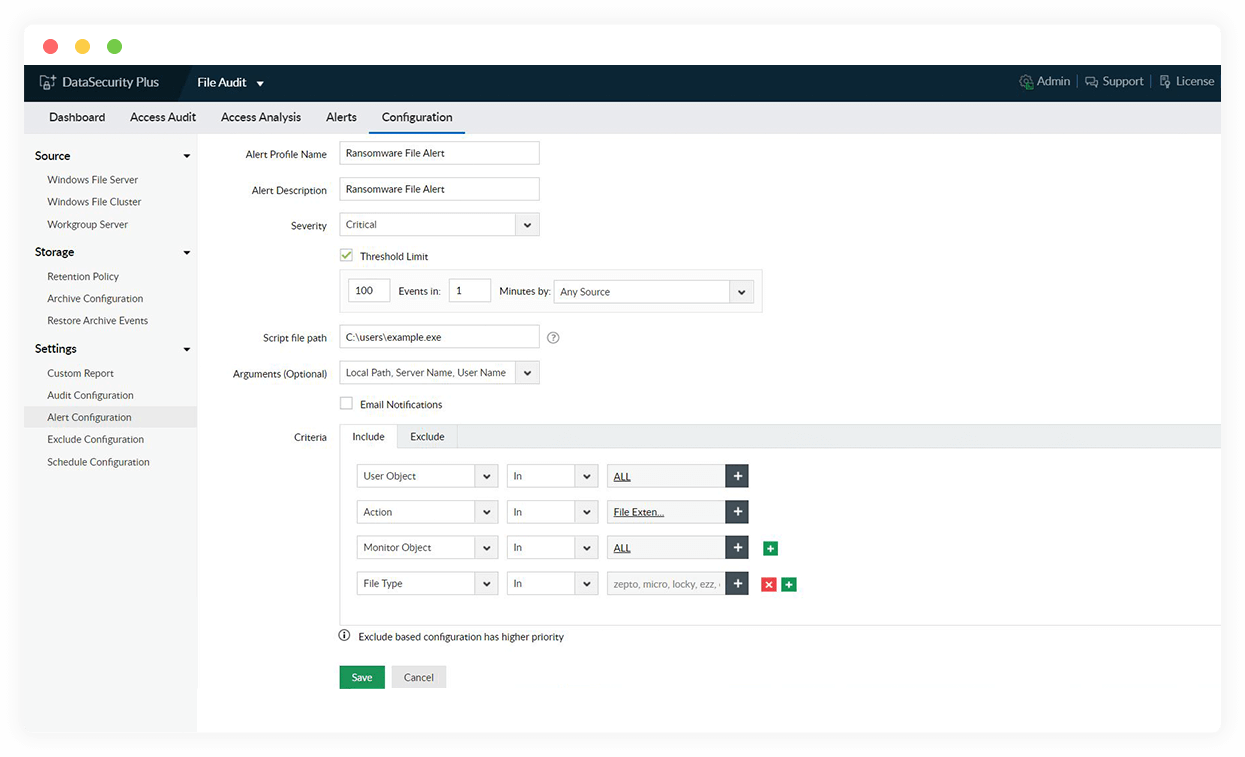
Detect ransomware attacks
Detect potential ransomware attacks by tracking sudden surges in file deletions, renaming, and permissions changes, which generate instant notifications.
-
Mitigate ransomware attacks
Initiate a threat response that will shut down ransomware-infected devices, isolate corrupted devices from the network, and more.
-
Reduce the attack surface
Closely monitor all file permissions changes and continuously scan for overexposed files to help reduce the points of distribution for ransomware.
-
Locate the source
Use the detailed audit trail of all file and folder activities as forensic evidence to locate the possible point of infiltration of a ransomware infection.
Detect and stop ransomware attacks instantly using our ransomware detection software.