-
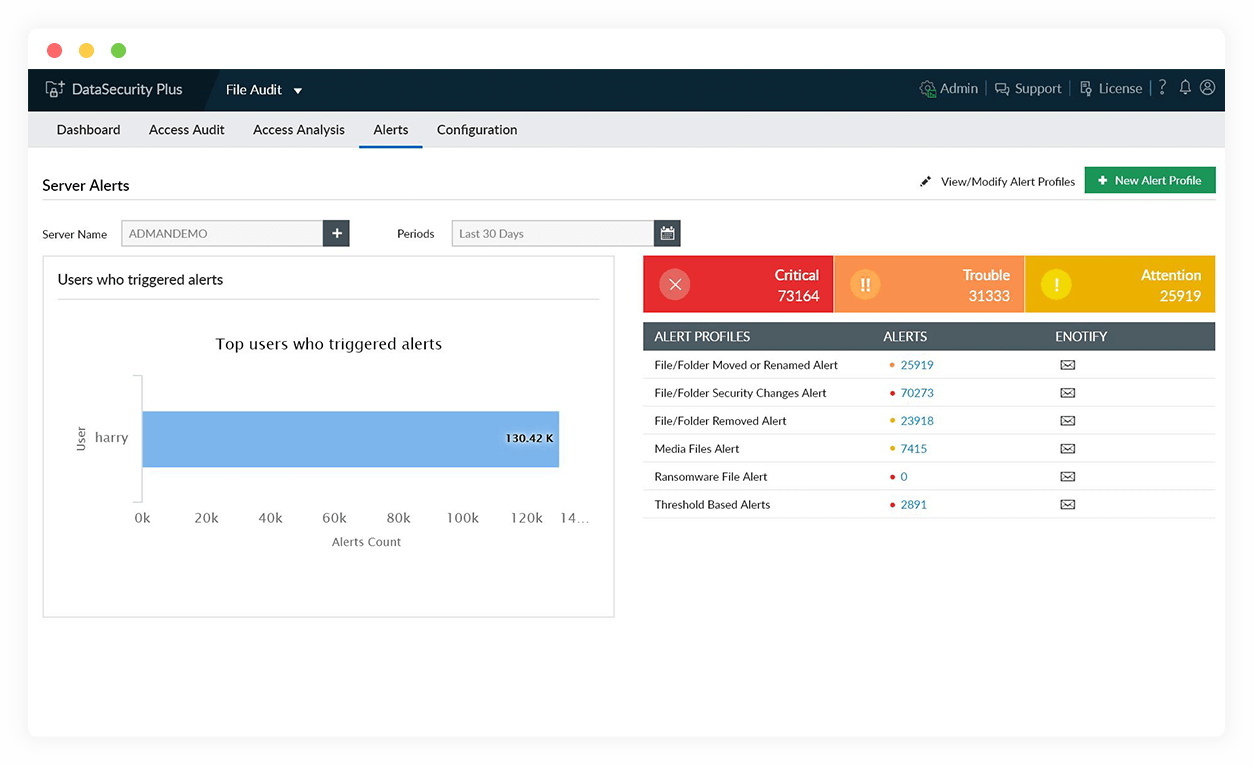
Detect ransomware attacks in seconds
Spot and get instant notifications about the telltale indicators of a ransomware attack such as a sudden spike in file modification, rename, and permission change events.
-
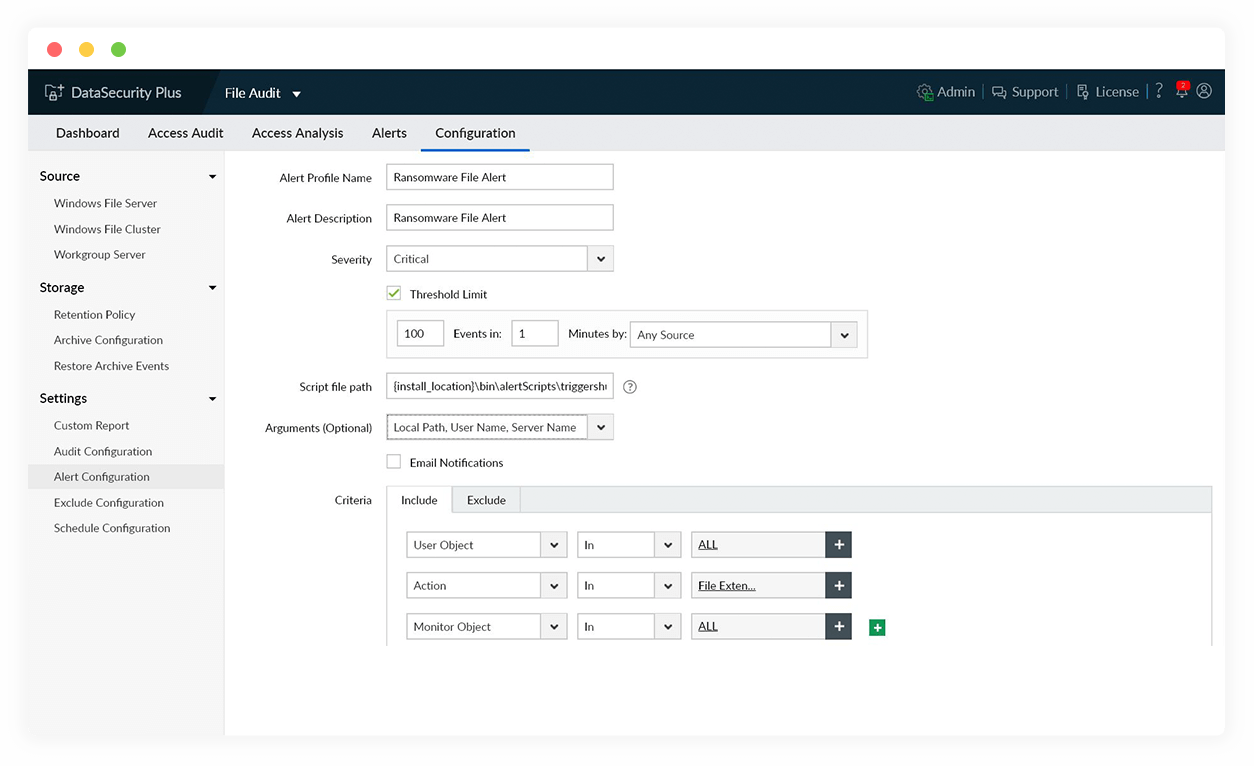
Automate ransomware response
Choose to shut down the infected device, isolate the corrupted system from the network, or disconnect user sessions as per your organization's guidelines.
-
Remove ransomware-corrupted files
Spot and purge files corrupted by notorious ransomware variants from your data stores with the help of our library of known ransomware file types.
-
Investigate ransomware attacks
Identify the "patient zero" of ransomware attacks with the help of a clear and concise audit trail, along with details on the client IP of the machine where it started.
Stop malicious data theft, leak, or exposure with our data leak prevention software