-
Advanced file system reporting tool
Get detailed insights on who did what, from where, and when by auditing and reporting on file create, modify, move, delete, copy, paste, and more.
-
Ensure the integrity of your files
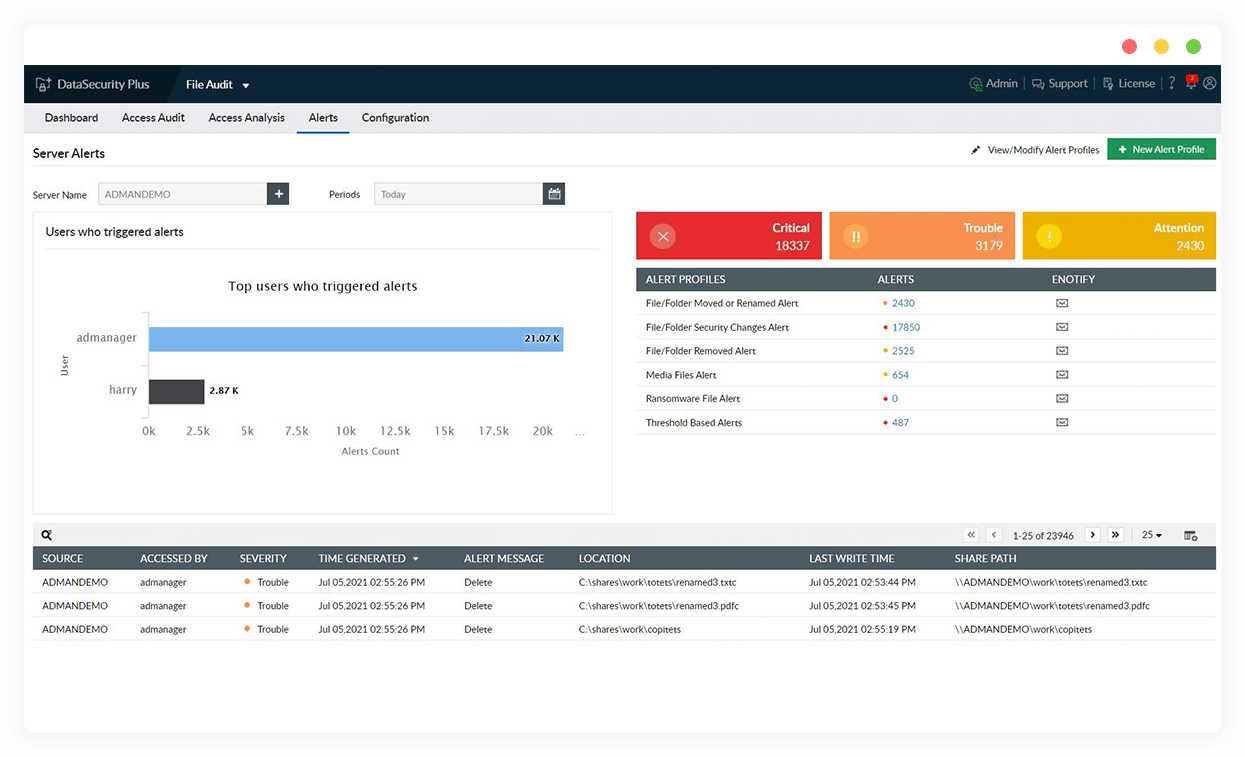
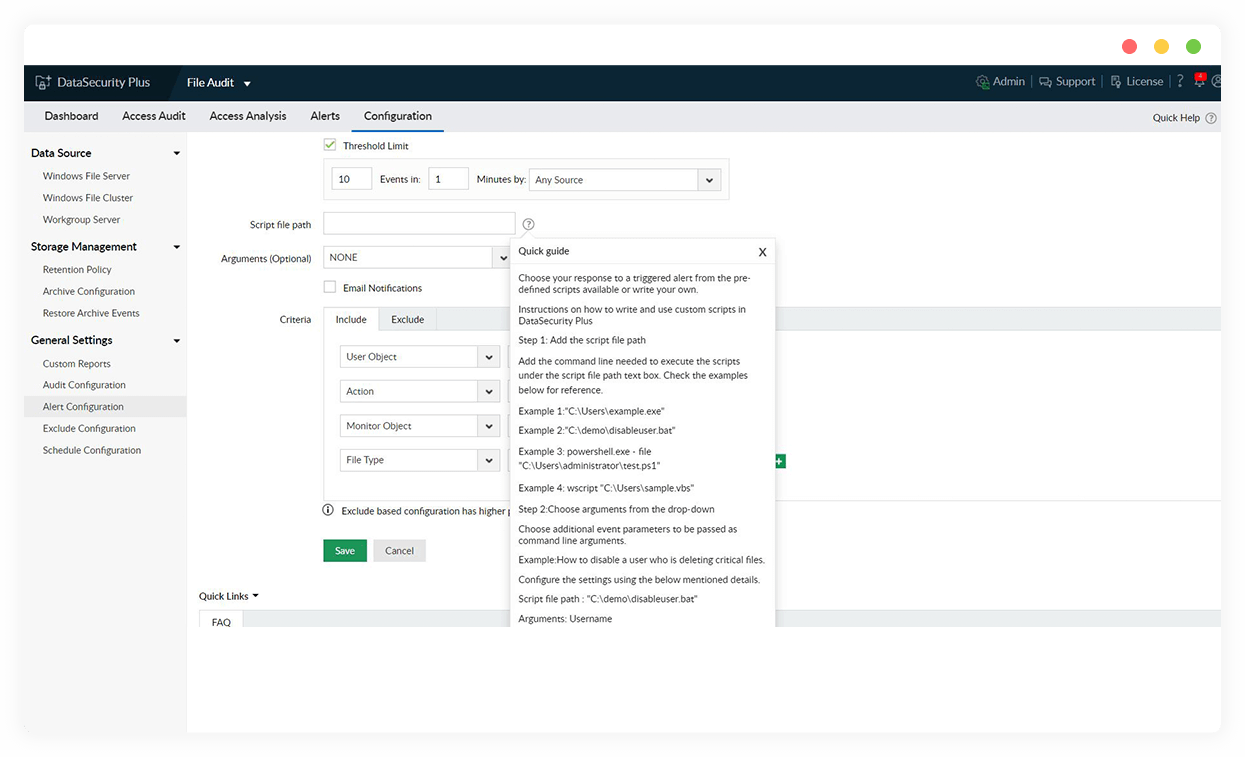
Detect and respond to sudden spikes in file accesses or abnormal file modifications using real-time alerts and an automated response mechanism.
-
Detect and quarantine ransomware
Combat malevolent threat patterns such as ransomware infections by shutting down infected machines, disconnecting user sessions, and more.
-
Comply with regulatory standards
Log user actions 24x7 and demonstrate compliance with regulatory standards including PCI DSS, HIPAA, SOX, GDPR, FISMA, and more.
Enable threat detection and monitor file integrity using our file server auditing software.