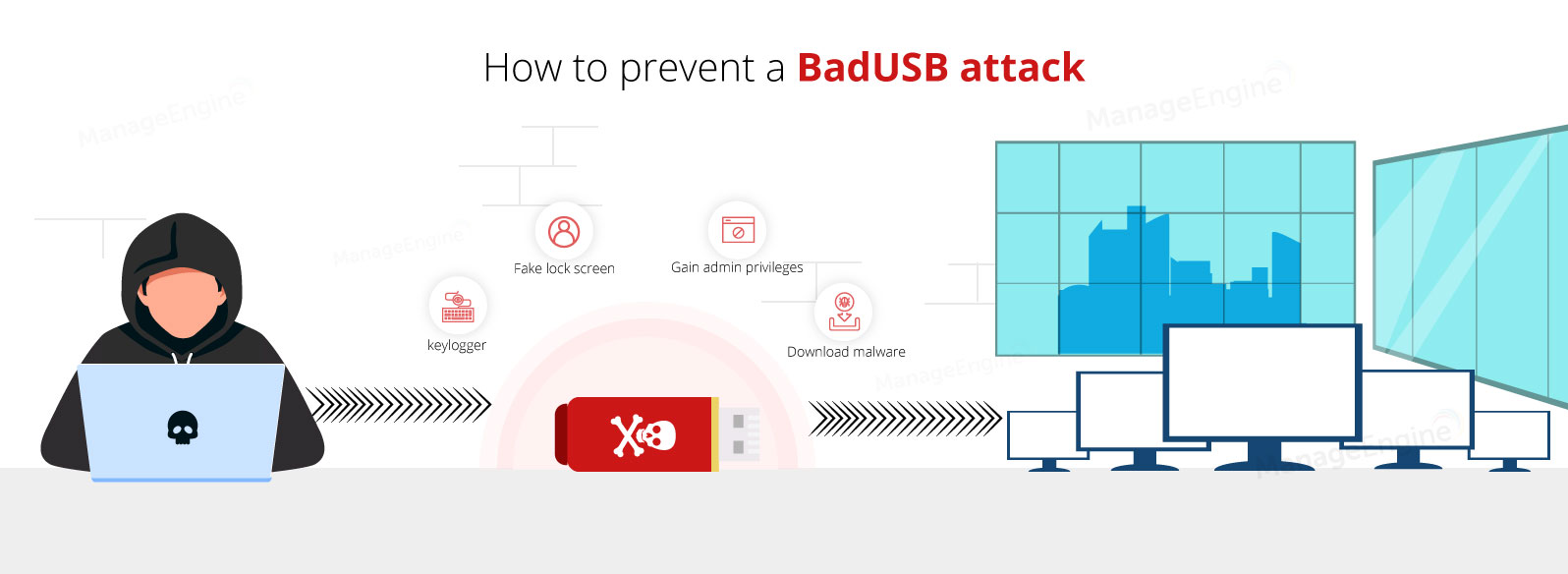
BadUSB, as named, is quite a crafty cybersecurity attack acting as a puppeteer controlling your USB devices at its will. BadUSB attack is when a USB device has an in-built firmware vulnerability that allows itself to be disguised as a human interface device. Once connected to its target computer, a BadUSB could then discreetly execute harmful commands or inject malicious payloads.
A common type of BadUSB attack is the Rubber Ducky. It can be carried out by using a flash drive created with a hidden exploit, that allows it to mimic a keyboard. This device can be pre-programmed to then inject numerous keystrokes into the unsuspecting users' computer.
Within organizations, a preventative measure such as USB blocking software is a necessity because BadUSB attacks, if undetected or stopped, could result in the unauthorized execution of commands that instigate security bypass incidents, privilege escalation, DDoS attacks, or malware infections of the host computers which could then spread to target entire networks.
This page covers the following:
A badUSB is a flash drive with embedded firmware that can be used to re-program the device and allow it to act as a human interface gadget such as a keyboard, mouse, or headset. They are used to perform a broad range of actions on a computer by effectively posing as a human interface device (HID). In other words, BadUSBs are virtual keyboards that can be programmed in advance to type out characters on a computer without physically doing so.
Once plugged in, they get straight to work, executing even complex keystrokes that require the use of two or more keys simultaneously. For example, the Run command, which requires you to hold down Win + R keys together.
BadUSB attack turns your existing USB devices into a form of attack vector, where the badusb exploits the behavior of the USB device and makes it act like a keyboard, mouse or even a network card. Once the USB device is inserted, badusb code is discreetly injected which has the potential to uproot the cyber network from within.
A badUSB security attack eases an attacker's workload by simulating the legwork of having to manually type in loads of commands. BadUSB attacks should not be treated as just another virus attack or a firewall breach, as it has the potential to be a threshold for badUSB ransomware attack. BadUSBs are a gateway to target the heart of your security system, manipulating the network devices bending them to the hacker's will and finally, the organization is brought to its knees.
BadUSBs are capable of typing out thousands of characters in an instant and quickly run through prompts, which is why penetration testers often use these devices to gain control over target computers without having to manually type out lengthy scripts.
Even system administrators often resort to BadUSB devices while setting up new computers. Why spend hours on end going through prompts when they can have a BadUSB do it for them? Apart from the legitimate uses of BadUSB, its potential to be weaponized when in the wrong hands is still a largely debated topic in the cyber community today.
Cybercriminals often use BadUSB as an external tool to inject malicious scripts that are designed to seek administrative privileges, steal passwords, or download malware to a computer.
The BadUSB stands for a vulnerability discovered back in 2006, which allowed computers to auto-run programs stored within CDROMs when they are inserted. This vulnerability paved the way for one of the earlier versions of BadUSB, called the USB Switchblade. The Switchblade could appear to a computer as if it were a CDROM, which means any programs stored inside the device would auto-run and execute payloads.
BadUSB devices today can be found equipped with more advanced features such as an SD card slot, better connectivity to support remote access, an on-board computer, and a better form factor, to make them seem like regular USB sticks. These devices have been the subject of numerous conferences and workshops over the years. One such occasion was the Black Hat conference held in 2014, where researchers Karsten Nohl and Jakob Lell demonstrated BadUSB security in detail.
BadUSB devices work on the premise that computers inherently trust keyboards as a valid source of input. Computers do not trust downloaded executables by default; instead, they run scans to validate their source and intent. If an executable file originates from an unknown developer or displays ill intent, chances are the computer will prevent it from running.
However, if a standard user were to open up Command Prompt and type in a command, their computer would blindly follow it without judging the intent. This means by emulating a keyboard, BadUSB devices can easily perform an array of functions that mimic actual user interactions on a system.
Any USB device with a microcontroller that allows for overwriting can easily be turned into a BadUSB. BadUSB devices use scripting languages that tell them what to do once plugged into a target system. While most of these devices use fairly simple scripts, some BadUSBs are even compatible with more complex programs such as JavaScript.
The different types of BadUSB found commercially available are:
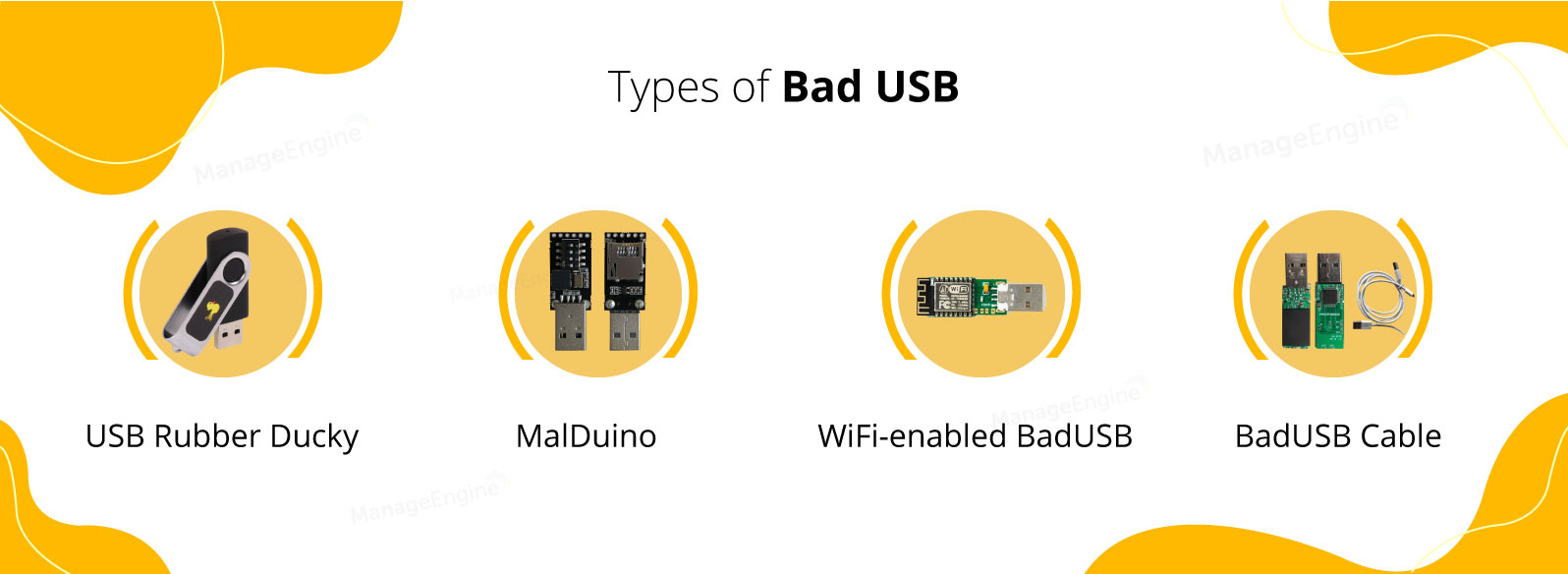
An infamous badusb security attack, a USB Rubber Ducky can swipe your password in less than the time taken for you to create it. The USB Rubber Ducky is built to act as BadUSB.
This hacker tool was introduced in 2011 by Hak5, an independent vendor that specializes in tool kits for penetration testers. Although there are multiple iterations of the device found in the market, this device remains the most prevalent BadUSB found today.
This USB device uses a special scripting language called Ducky Script, which can easily be written with little to no programming experience. Ducky Script uses simple string commands to tell the "duck" what to type. A simple example of Ducky Script can be found below.
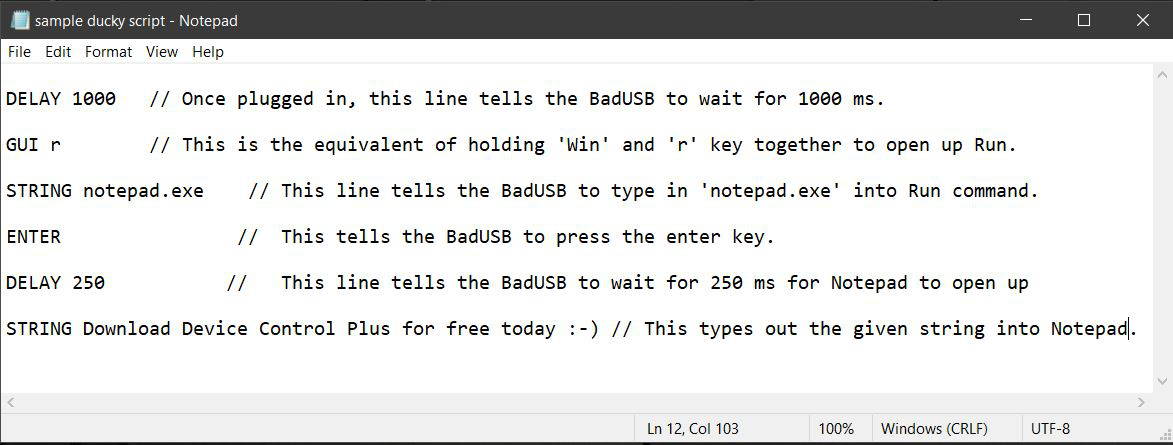
While this may appear harmless from the above example, it's easy to imagine how this device is only a few steps away from gaining administrative privileges through Command Prompt.
MalDuino is an open-source Arduino-based BadUSB that injects malicious payloads into a target computer. Gaining widespread attention in recent times, a MalDuino packs several more features compared to regular BadUSB devices by virtue of its onboard computer.
MalDuino devices that are commonly found today support Micro SD cards and also have a set of dip switches to help its user toggle between stored programs within the Micro SD card.
This type of BadUSB is similar to MalDuino in that an Arduino board serves as a base for the device but is specially designed to have WiFi capabilities. Once plugged into a target system, these devices allow attackers to introduce malicious payloads into a victim's computer using the WiFi protocol.
WiFi-enabled BadUSB can take different forms depending on the exact purpose and function they serve. The common iterations of this device used today are as follows.
These are the most common types of WiFi BadUSB found today. When plugged into a target computer, these devices remain dormant until an attacker makes further contact through a smartphone or a neighboring system. Connecting to this BadUSB is as simple as connecting to a WiFi access point.
Once connected, the attacker can introduce keystroke injections using a suitable scripting language. These devices often come with their own applications, which allow hackers to execute scripts from a remote location.
WiFi keyloggers are modern hacker hardware that particularly targets desktop computers. They work as a bridge between the keyboard's USB terminal and the computer itself. This BadUSB intercepts input signals from the keyboard and relays them to the hacker's computer.
WiFi keyloggers capture anything that the user types including sensitive information and passwords without raising any suspicion. In the case of desktop computers, these devices can be completely hidden from plain sight and do not affect the performance of the keyboard while in use.
WiFi Deauthers are malicious devices that leverage flaws present in the WiFi protocol to force all users of a WiFi network to disconnect automatically. Subsequently, WiFi Deauthers prevent users from connecting back to the network as long as the device is active.
WiFi Deauthers are different from other forms of BadUSB in that they do not affect the systems they connect to directly, but rather use them as a power source to disturb network connectivity and establish downtime.
Gaining widespread attention in recent times, BadUSB cables look and function similar to any other USB cables, but are secretly malicious devices that inject scripts and malware into a computer without the user's knowledge.
Also known by names such as USB Ninja and the USB Harpoon, these generic-looking cables hide a BadUSB within the internal circuitry and are more deceptive than any other variant found today. A BadUSB cable can facilitate functions such as charging and data transfer while all the malicious activity happens in the background.
BadUSB devices operate at speeds that are virtually impossible for standard users in an organization to detect. Various payload scripts are readily available for download from the internet. This allows even amateurs with little knowledge of computers to pull off a BadUSB attack.
Here are three measures that you can implement to counteract BadUSB vulnerability right away.
USB port blockers are an effective way to deter users from connecting unauthorized USB devices that may contain malicious payloads without their knowledge. In the case of a BadUSB attack, an attacker is less likely to target systems where USB port blockers are installed.
USB port blockers can be installed on crucial systems in a network that contains sensitive files and come with a special key that unlocks and locks the device once installed. For example, you can have port blockers installed across desktop computers in a network where USB ports are hidden from view.
However, the downside to USB port blockers lies in the fact that these devices are still subject to physical tampering if not monitored properly. Any user with ill intent and a few basic tools can easily remove port blockers from a target system.
Certain programs like DuckHunter are designed to run in the background and keep a close eye on the typing speed. Since BadUSB devices type at speeds that are practically impossible for humans to type at, the program effectively blocks keyboard input when a BadUSB attack is detected.
The disadvantage of using this method of prevention is that these programs take a few milliseconds to detect an attack. Depending on the length of the payload, it can still make its way into a target computer before being blocked by the program.
Running Command Prompt (CMD) as an administrator unlocks a whole set of actions that can be performed on a computer. On Windows, you can gain access to the elevated Command Prompt by first typing "CMD" in the Run command and then holding down Ctrl + Shift + Enter. These keystrokes can easily be programmed into a BadUSB device.
Setting a password for using an elevated Command Prompt stops any BadUSB programmed to seek administrative privileges dead in its tracks. Here's how you can set a password for running CMD as an administrator.
Note: This procedure involves making changes to the system registry and must be handled responsibly in order to avoid harming your computer.
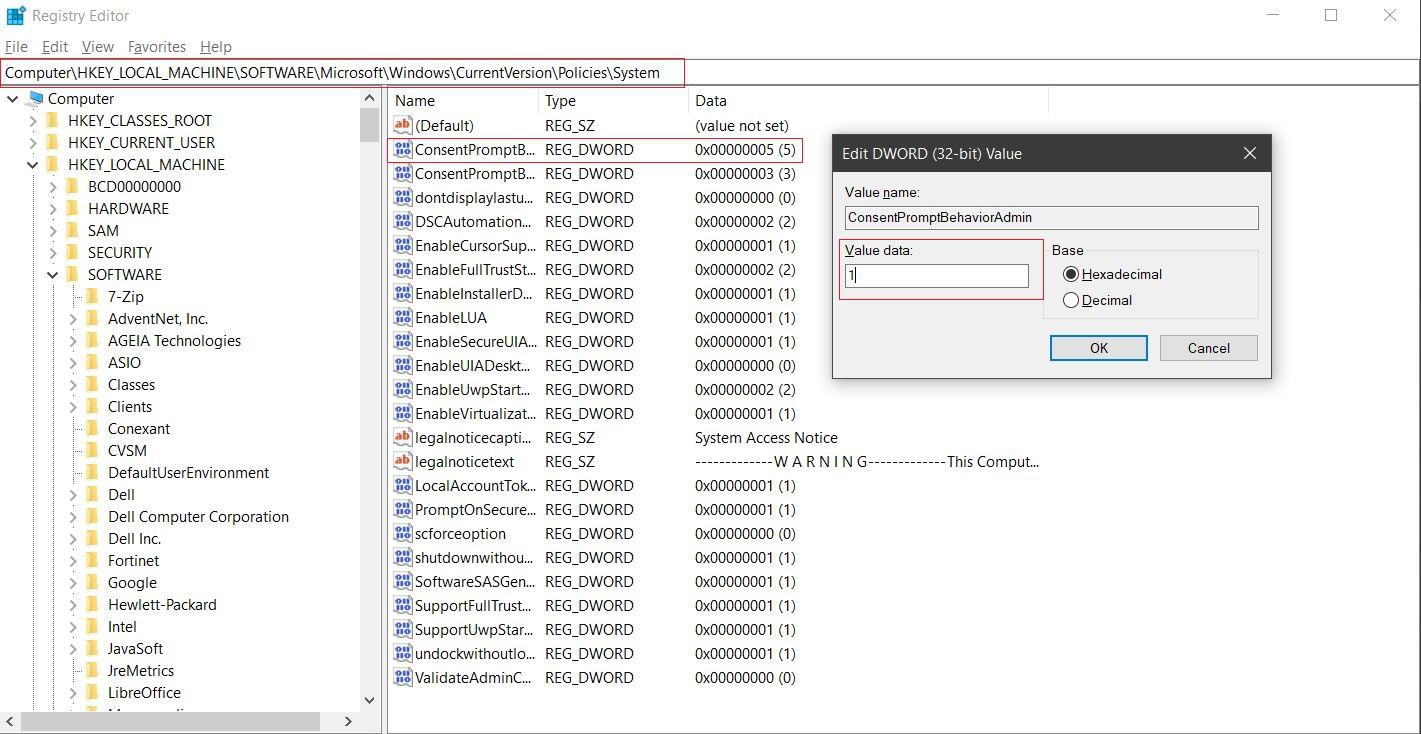
Step 1: Type Regedit in the start menu, and open the application.
Step 2: Follow the navigation to ConsentPomptBehaviorAdmin : Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System
Step 3: Once you find ConsentPromptBehaviorAdmin, right-click on it, and select Modify.
Step 4: Change the Value data to 1, and click OK.
Now, whenever you try to access the elevated Command Prompt, Windows will ask you for your system password.
Depending on your enterprise, it may be impractical to completely avoid using USB devices, as it may have an adverse effect on overall productivity. On the other hand, making changes to the registry can be a dangerous affair, as it involves interfering with core system components. This calls for a robust method to prevent BadUSB attacks.
The four pillars of protection against BadUSB threats are as follows
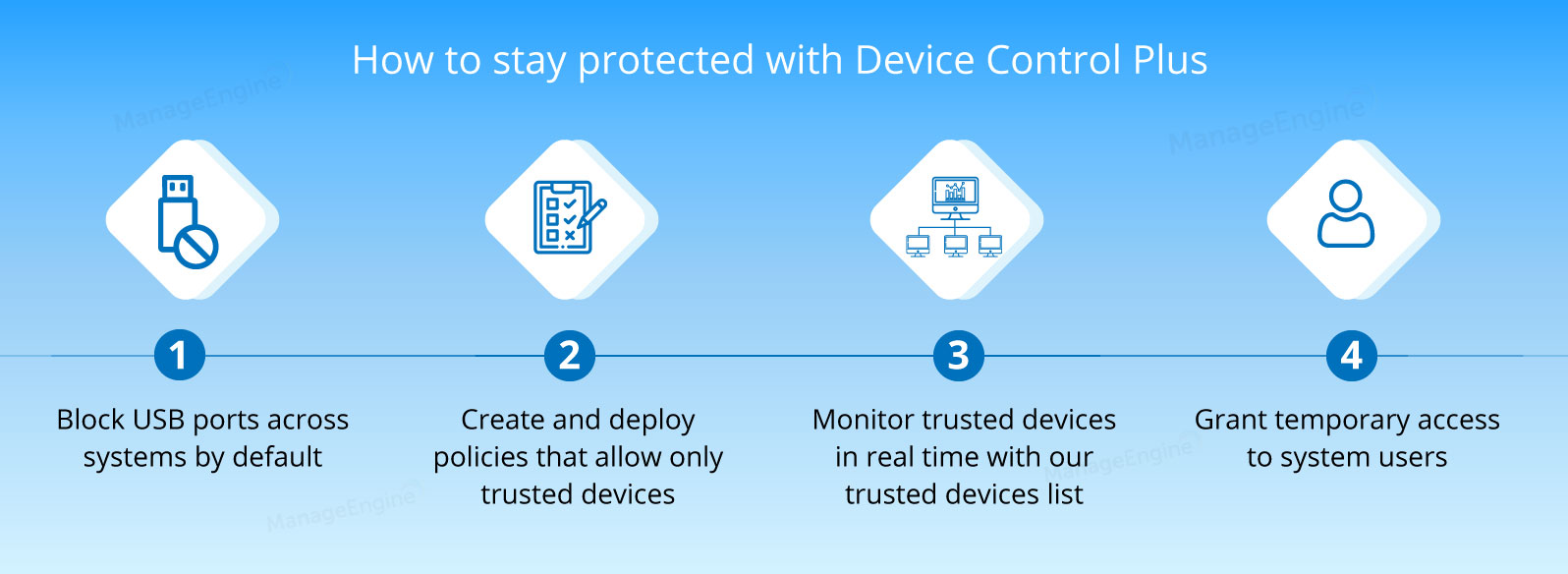
Device Control Plus is a proactive approach to safeguard endpoints across your enterprise. This solution conveniently solves the limitations found in common measures to counteract BadUSB attacks by keeping USB ports across all systems on lockdown by default.
From there on, you get to choose who has permission to use what devices to access endpoints in your network by creating policies that allow or block USB devices. Additionally, you get notified whenever a user plugs an unauthorized device into one of your endpoints.
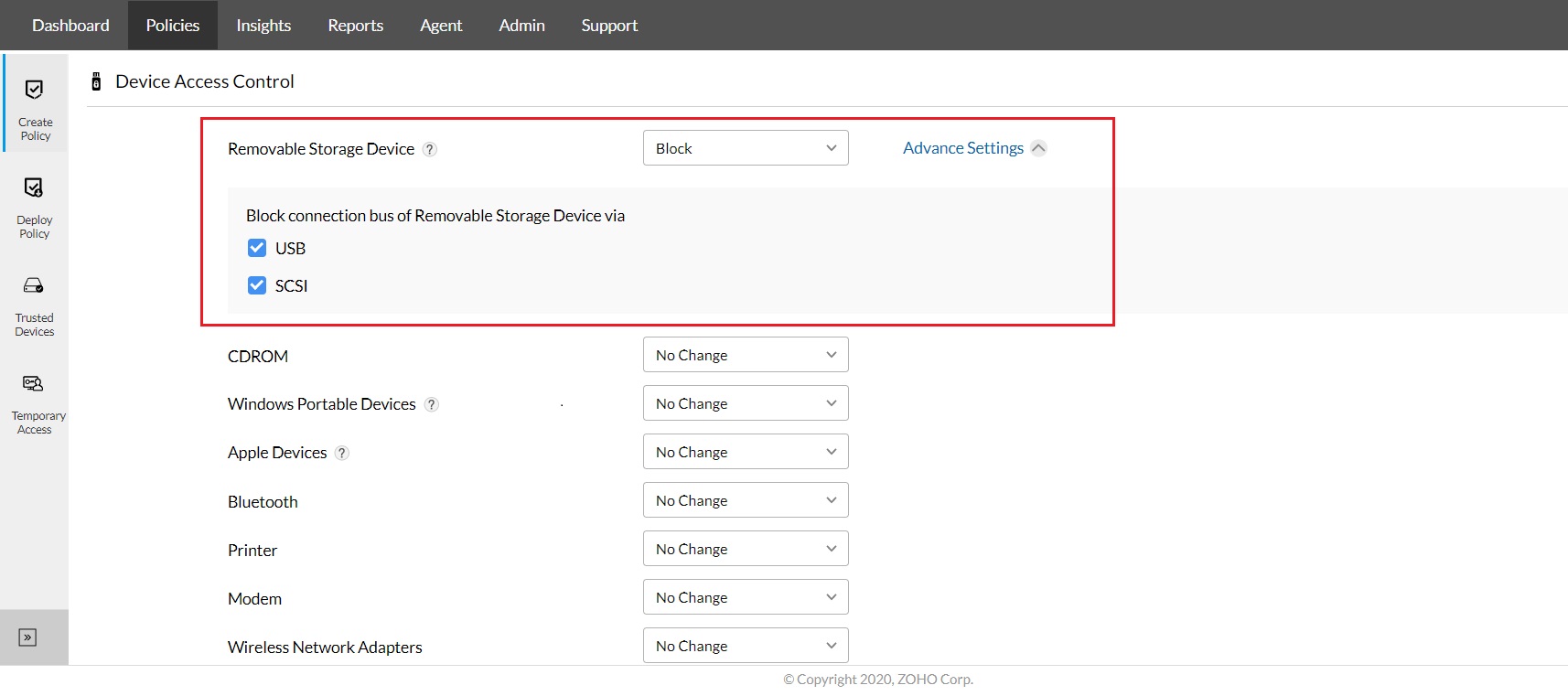
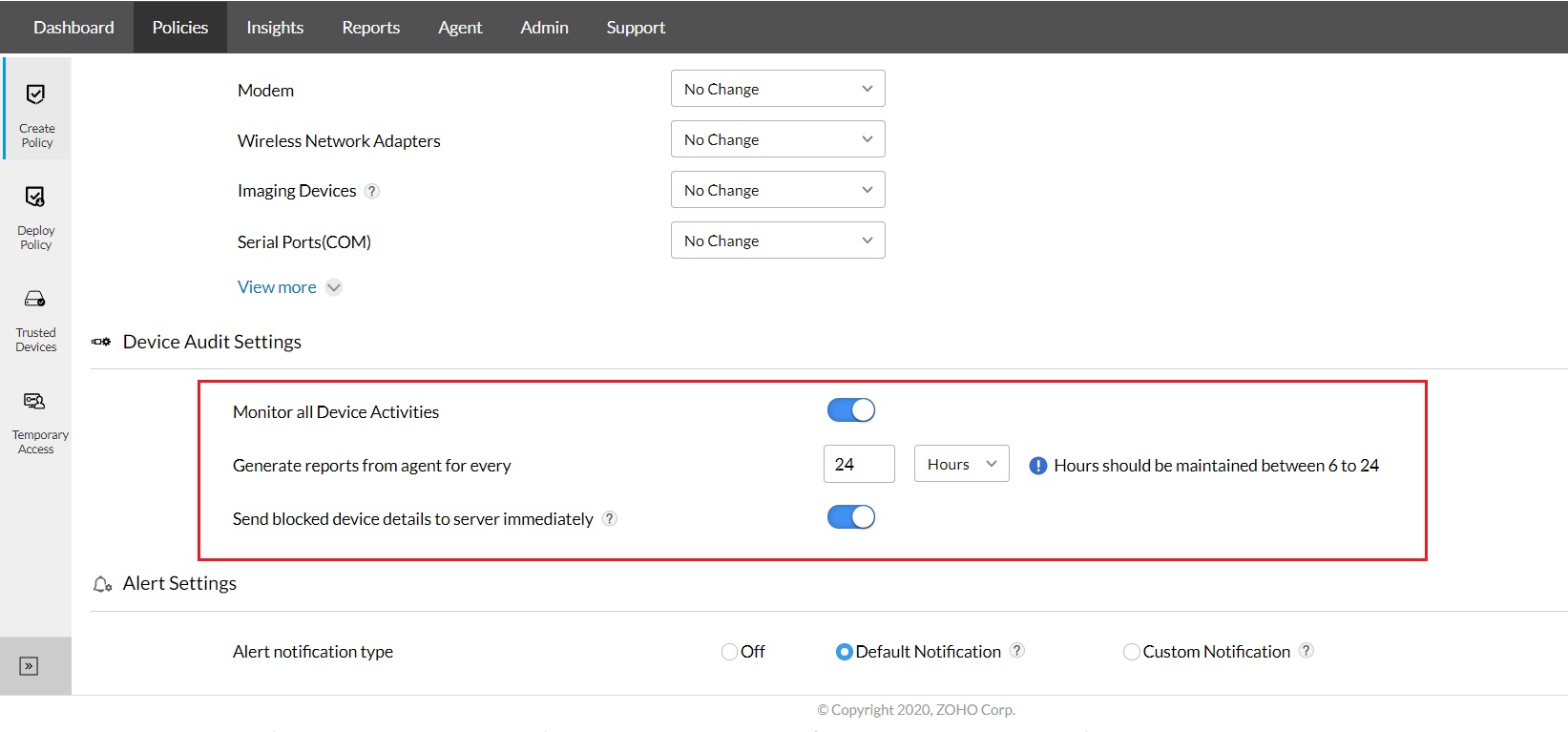
Device Control Plus helps you control USB devices and provides device management for up to 18 peripheral devices. Create trusted device lists, grant temporary access and much more! Download the trial version today.