Consolidated threat insights
Trusted multi-source threat intelligence
IoC spotlight: Threats under the microscope
DNS Detection and Response (DDR)
Consolidated threat insights
Trusted multi-source threat intelligence
IoC spotlight: Threats under the microscope
DNS Detection and Response (DDR)
Consolidated threat insights
Stop stitching data—see your threat landscape in a single view. Visualize the whole battlefield at a glance
Threats snapshot
- Threat volume at a glance
Track total and daily DNS-layer threats to quantify exposure instantly. - Trend lines that speak
Visualize threat growth over time with interactive charts for pattern recognition. - Snapshot of risk distribution
See the top 5 threats dominating your landscape—quick triage made easy.
- Threat source clarity
Break down where queries are spiking, so admins know where attackers are concentrating efforts. - Single pane of threat insight
All critical threat metrics surfaced on one screen—no need for swivel-chair analysis. - Actionable context in real time
Prioritize response based on the most queried domains, not static assumptions.
Impacted endpoints
Attackers slip through DNS, but threat intelligence exposes every hidden mole that gave them a foothold—in the blink of an eye.

- Compromised devices exposed
See which internal IPs are generating malicious queries, revealing infected or suspicious hosts immediately. - Connect threats to sources
Link devices directly to the external domains or IPs they queried—making attacker infrastructure visible.
- Visualize the spread with clarity
Snapshots and graphs segment top devices and sources, helping admins quickly gauge the infection scope across the network. - Visualize trends over time
Spot recurring offenders or repeated queries, helping admins distinguish isolated hits from persistent compromises.
Category and DNS footprints
Decode the anatomy of attacks—by category, by record, by intent.”

- Vendor-Curated categories, Admin-Ready context
Leverage TAXII feed classifications—malware, phishing, or C2—without rework, so admins immediately know what type of threat they’re dealing with. - Uncover record-level abuse
See exactly which DNS record types (A, MX, TXT, etc.) are being weaponized, shining light on attacker tactics hidden in plain traffic.
- Spot where abuse concentrates
Identify the categories and record types most targeted, revealing attacker focus areas and informing smarter investigations. - Spot shifts in attacker tactics
Track category and record-type trends over time to identify emerging behaviors—staying ahead of evolving threats.
Risk stratification
Your confidence compass—guiding you through the noise of countless IOCs.

- See risk concentration at a glance
Instantly visualize how many threats fall into critical, high, or medium categories—clear stratification without log-diving. - Spot high-risk exposure zones
Quantify how much of your DNS traffic maps to top-severity threats, giving admins a sense of where their infrastructure is most exposed.
- Validate feed-driven confidence
Rely on vendor-assigned scores to know which threats are most credible—no need for manual vetting or guesswork. - Track risk distribution over time
Use stratified counts to see whether high-confidence threats are rising or falling, helping gauge the shifting threat climate in your environment.
Trusted multi-source threat intelligence
From trusted vendors to curated Indicators of Comprimise (IOCs) — a continuously vetted, real-time blocklist.
Multi-vendor feed onboarding
- Centralized threat feed onboarding
Configure and manage multiple threat intelligence feeds—such as IBM X-Force, AlienVault, Cyware, and more—all from a unified, vendor-agnostic interface. - Broader threat visibility
Onboarding multiple vendors ensures multifaceted intelligence, helping admins spot diverse threat vectors that a single source might miss. - Reduced blind spots
Diversified feeds cross-validate each other, boosting confidence scores and minimizing reliance on any one vendor’s perspective.
- Bring your own intel
Easily onboard custom STIX/TAXII sources, including private, industry-specific, or partner-distributed feeds, enabling tailored and proactive DNS-layer threat prevention. - Frictionless feed registration
Minimal setup effort—just choose your provider, enter endpoint credentials, and go live. No scripting, no third-party collectors, no custom parsers required. - Always-On threat awareness
The toggle-based enablement ensures that once configured, feeds remain active continuously—helping ensure real-time updates with no manual intervention.
Secure feed synchronisation
Plug, Poll, Protect - Connect once, defend continuously with credentialed threat syncs.

- Deep integration with CloudDNS's threat intelligence engine
Leverage ManageEngine CloudDNS's advanced DNS threat intel engine, built for DDI Central, to deliver real-time IOCs directly into DNS enforcement workflows. - Secure credentialed access
Use OAuth 2.0-based client ID and secret for secure, tokenized access—ensuring credential rotation, session isolation, and vendor-compliant data retrieval.
- Fine-Grained feed control
Adjust polling frequency with precision to control the cadence of threat syncs—hourly, daily, or custom—to align with DNS resolution freshness needs. - Immediate threat feed activation
Instantly activate or pause the feed without losing your configuration—providing operational agility during maintenance windows or incident response.
Unified feed management
Consolidate, customize, and control your threat intelligence pipeline.

- All feeds. One command center.
Get a unified, real-time view of all threat intelligence sources—status, sync schedule, and vendor mapping—within a single dashboard. - Live feed status, At a glance
Instantly verify which feeds are active, when they last synced, and when they’ll update next—no log diving or guesswork.
- Precision scheduling for consistent protection
Schedule hourly or daily syncs per feed with confidence—keeping your DNS defenses in sync with the latest threat intelligence. - Sync on demand, Stay current
Admins can trigger an immediate feed sync when the last update is stale, ensuring threat data freshness even outside scheduled intervals. - Hands-on control over feed servers
Edit credentials, adjust polling intervals, or retire outdated or unrequired feed sources—giving admins policy-aligned control over every threat source without leaving the UI.
Threat intelligence hub
See threats before they strike — the Feed Hub as your watchtower, where every IOC flagged across vendors converge, clustered, classified, and confidence-rated for automated, intuitive blocking.

- Centralized threat feed onboarding
Configure and manage multiple threat intelligence feeds—such as IBM X-Force, AlienVault, Cyware, and more—all from a unified, vendor-agnostic interface. - Broader threat visibility
Onboarding multiple vendors ensures multifaceted intelligence, helping admins spot diverse threat vectors that a single source might miss. - Reduced blind spots
Diversified feeds cross-validate each other, boosting confidence scores and minimizing reliance on any one vendor’s perspective.
- Bring your own intel
Easily onboard custom STIX/TAXII sources, including private, industry-specific, or partner-distributed feeds, enabling tailored and proactive DNS-layer threat prevention. - Frictionless feed registration
Minimal setup effort—just choose your provider, enter endpoint credentials, and go live. No scripting, no third-party collectors, no custom parsers required. - Always-On threat awareness
The toggle-based enablement ensures that once configured, feeds remain active continuously—helping ensure real-time updates with no manual intervention.
IoC spotlight: Threats under the microscope
IOC Under the lens
Put a single IOC under the microscope and watch its risk unfold.
- Size up the threat in seconds
Use category, hit count, feed source, and last update to instantly gauge whether the IOC demands immediate action or routine monitoring. - Track malicious shifts over time
Follow confidence score history to see when a once-benign domain turned hostile—critical for retrospective investigations and timeline reconstruction. - Validate the Source of Truth
Know exactly which vendor feed flagged the IOC and when, helping admins build confidence in DDR enforcement policies.
- Prioritize using fresh intelligence
Rely on continuously updated scores and timestamps so response actions are based on current, vendor-vetted data—not stale lists. - Correlate traffic spikes with risk levels
Match sudden query surges against rising confidence scores to detect active exploitation attempts in your environment. - Export proof, Share with ease
Generate PDF or CSV reports to justify enforcement actions during audits, compliance checks, or SOC escalations.
Scope of Compromise
Trace how deep the breach runs—from the flagged domain to the last querying device.
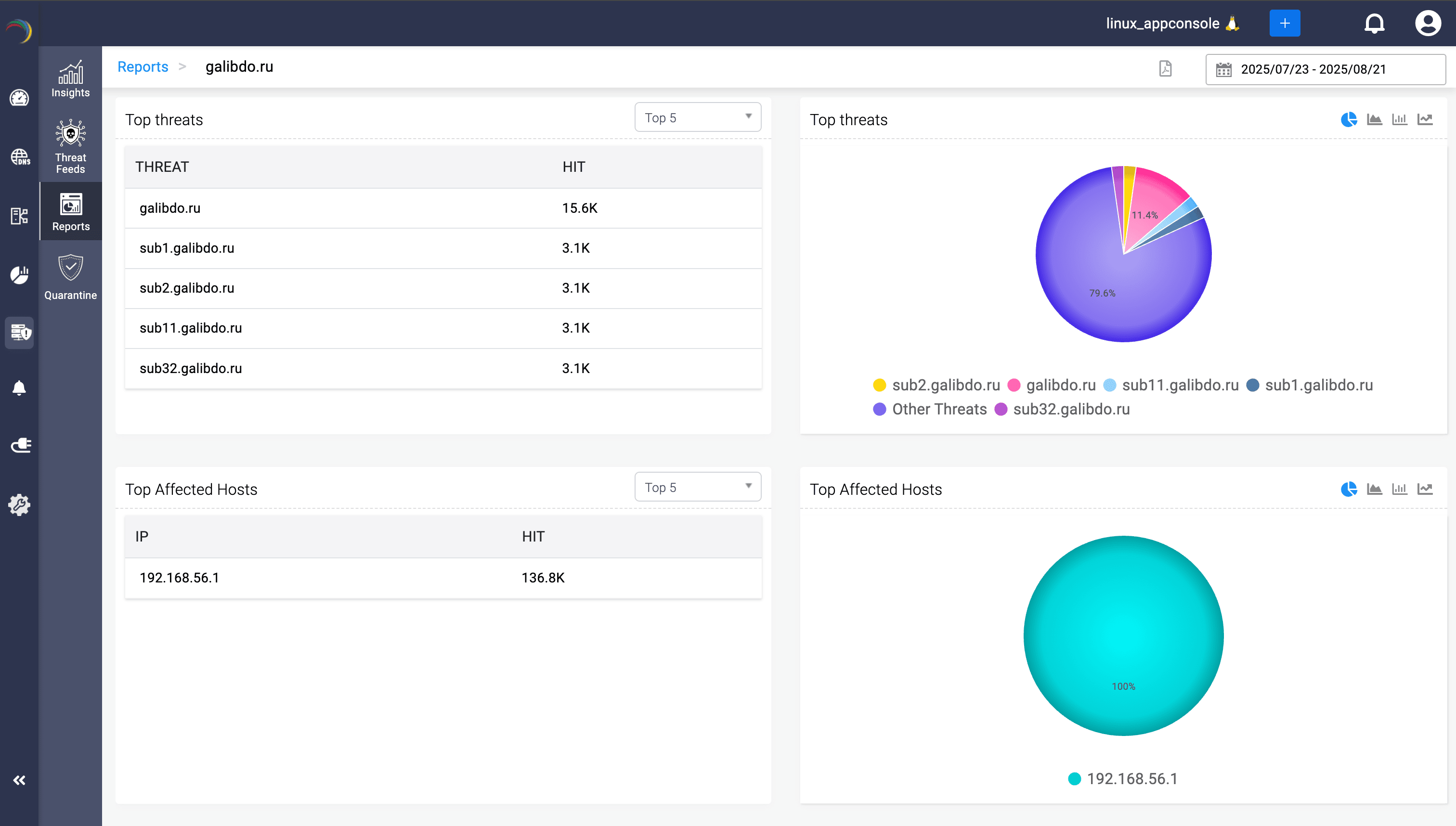
- Trace the blast radius
See exactly which internal hosts are contacting the flagged IOC, mapping the spread of compromise across your environment. - Prioritize host-level response
Rank affected endpoints by query volume, so admins know which systems to isolate, patch, or remediate first.
- Link subdomains to a campaign
Drill down into related subdomains under the same IOC to uncover broader malicious infrastructure tied to the attack. - Accelerate forensic investigations
Turn IOC hits into actionable evidence—connecting external domains to internal devices for automated containment and forensic clarity.
See which records attackers abuse
Break down threats by DNS record type (A, TXT, MX, etc.) to expose attacker tactics.

- Pinpoint abused DNS records
Spot which record types (A, TXT, MX, etc.) attackers are exploiting, enabling admins to tighten policies exactly where abuse is happening. - Prioritize remediation by record impact
Focus security and access controls on the record types with the highest hit volume, ensuring resources are directed to the biggest risks first.
- Correlate records with attack campaigns
Link record-level activity to broader threat patterns, helping admins recognize whether attacks are phishing-based, malware-driven, or C2-related. - Refine DNS security policies
Use record-level insights to decide where stricter resolution rules, response rate limiting, or custom enforcement should be applied.
DNS Detection and Response (DDR)
DNS-based quarantine
DNS doors slam shut for compromised devices.
- Block at first sight
DDI Central uses DNS ACLs on Linux and Client subnet-based isolation on Windows to immediately cut off compromised devices from making further DNS queries, stopping the spread of malware at the earliest stage. - Containment without delay
Admins don’t have to manually isolate infected endpoints—DDI Central’s automated DDR engine enforces quarantine rules the moment threat-domain lookups are observed, slashing response times.
- Know What was blocked, When, How, and Why
The Quarantine dashboard offers detailed attribution, including service (DNS), quarantine type (ACL or Client Subnet), cluster, and timestamp—empowering informed decisions and audit-friendly records. - Powerful filters for rapid triage and cleanup
Drill down by cluster, IP, or quarantine method to review and release entries as needed—all from a unified console. Streamline investigations and restore legitimate devices quickly.
DHCP-based quarantine
From MAC address to MAC arrest—Containment that sticks.

- MAC flagged. Network locked.
Leverages MAC filtering for Windows clusters to permanently block infected endpoints from receiving new IP leases—ensuring rogue devices can’t sneak back into the network through DHCP requests. - One scope to isolate them all.
In Linux clusters, compromised MACs are funneled into a restricted DHCP reservation pool, locking them inside a subnet built for quarantine—ensuring zero lateral movement.
- No Lease. No Lurking. No Leakage.
Prevents misbehaving devices from reacquiring IPs, whether by dynamic lease or manual reconnect—cutting off their ability to communicate across the network. - Catch, Contain, and cut off—Automatically.
DDR triggers this quarantine instantly upon threat detection, without admin intervention, enabling real-time containment of infected endpoints based on DHCP activity.




