Steps to configure SAML SSO for Microsoft Entra ID
About Microsoft Entra ID
Microsoft Entra ID, previously known as Azure Active Directory (Azure AD), is a cloud-based identity and access management (IAM) solution that enables organizations to manage user identities and access permissions securely. Microsoft Entra ID provides users with a range of functionalities for efficient and secure access to organizational resources.
The following steps will help you enable SAML-based single sign-on (SSO) for Entra ID from Identity360.
Note:
- SSO can be enabled only for domains that are verified in Entra ID. By enabling SSO for the entire domain, any user within the domain can access Entra ID only via Identity360 SSO.
- SSO cannot be enabled for "onmicrosoft.com" domains that are created by Microsoft.
- Users will not be able to log in to their Microsoft Entra joined devices if Identity360 SSO is enabled.
- SSO cannot be enabled for the default domain (the primary domain in which users are created). It can only be configured for custom domains. Entra ID prohibits SSO configuration for default domains to ensure that administrators can log in to Entra ID regardless of issues with the identity provider (IdP). If your organization does not have a custom Entra ID domain, you need to create one to configure SSO. Additionally, you can have the Global Administrator within the default domain to handle any IdP-related issues.
Updating the ImmutableID value in Entra ID
To enable SSO to Entra ID through Identity360, it is mandatory to have the ImmutableID attribute as the unique identifier in Entra ID. You can create new users with the ImmutableID attribute or update existing users' ImmutableID attribute value in Entra ID using the following PowerShell commands.
Note: You can now use the user’s email ID as the value for ImmutableID. If you need to use a different attribute or face any issues while updating the ImmutableID for existing users, please reach out to
support for assistance.
Prerequisites
- Open PowerShell with administrator privileges.
- Run the following command to install the Microsoft Graph PowerShell, if it is not already installed:
Command to install the Microsoft Graph PowerShell
Copy
Install-Module Microsoft.Graph -Scope CurrentUser
- Command to connect to Microsoft Graph PowerShell:
Command to connect to Microsoft Graph PowerShell
Copy
Connect-MgGraph -Scopes "Directory.AccessAsUser.All"
Note: Sign in with a Microsoft Entra ID account that has Global Admin privileges.
- Command to update ImmutableID attribute for existing users:
Command to update ImmutableID attribute
Copy
Update-MgUserByUserPrincipalName -UserPrincipalName "<user_mailID>" -OnPremisesImmutableId "<immutable_id>"
- Command to create new users with the ImmutableID attribute
Command to create new users
Copy
New-MgUser -AccountEnabled:$true -UserPrincipalName "user01@mycompany.com" -MailNickname "user01" -OnPremisesImmutableId "<immutable_id>" -DisplayName "user01" -GivenName "user" -Surname "S"
- Command to confirm whether the ImmutableID attribute update was successful
Get-MgUserByUserPrincipalName -UserPrincipalName "<user_mailID>" -Property UserPrincipalName, OnPremisesImmutableId | select UserPrincipalName, OnPremisesImmutableId
- PowerShell access with administrative rights is required in order to set up SSO in Entra ID.
- The MFA and SSO license for Identity360 is required to enable SSO for enterprise applications. For more information, refer to the pricing details.
- Log in to Identity360 as an Admin or Super Admin, or Technician with a role that has Application Integration and Single Sign-on permissions.
- Navigate to Applications > Application Integration > Create New Application and select Azure Active Directory from the applications displayed.
Note: You can also find Azure Active Directory from the search bar located at the top.
- Under the General Settings tab, enter the Application Name and Description.
- Under Choose Capabilities, select SSO, then click Continue.
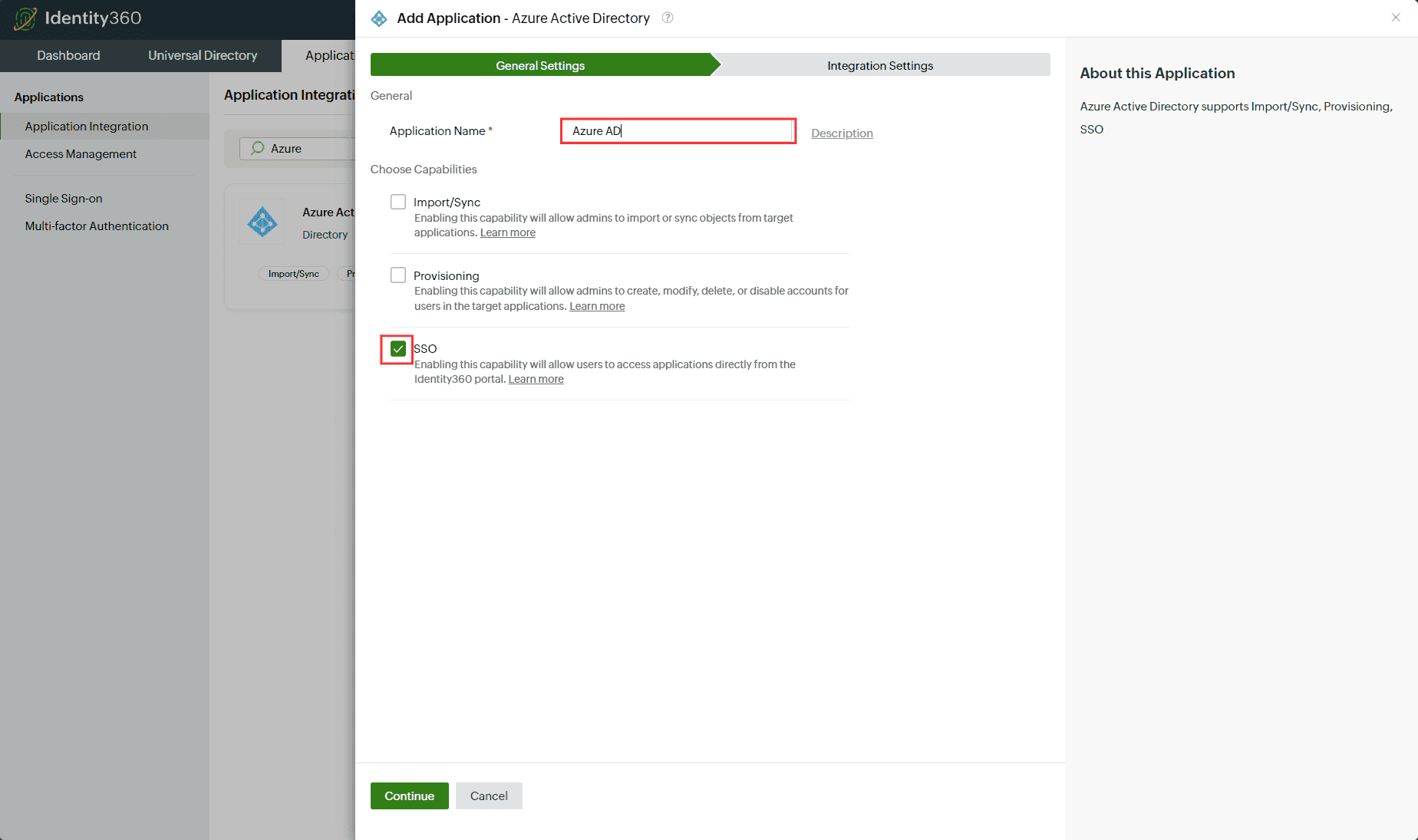 General Settings of SSO configuration for Entra ID
General Settings of SSO configuration for Entra ID
- Under Integration Settings, navigate to the Single Sign On tab and click Metadata Details.
- Copy the Login URL, Logout URL, Entity ID/Issuer URL, and Signing Certificate values, which will be used during the configuration of Entra ID.
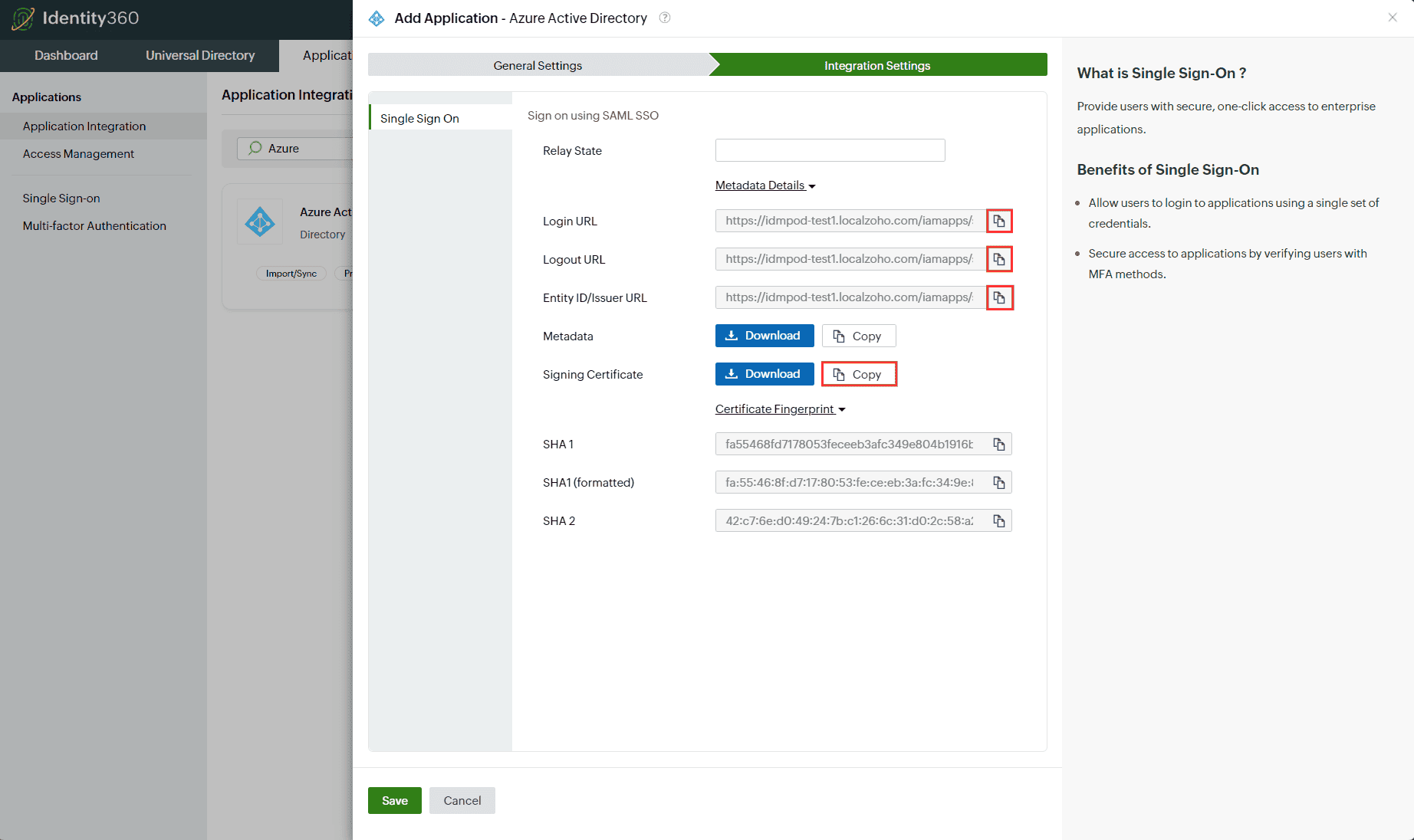 Integration Settings of SSO configuration for Entra ID
Integration Settings of SSO configuration for Entra ID
Entra ID (service provider) configuration steps
- Open PowerShell with administrator privileges.
- Run the following command to install the Microsoft Graph PowerShell, if it is not already installed:
Command to install the Microsoft Graph PowerShell
Copy
Install-Module Microsoft.Graph -Scope CurrentUser
- Connect to Microsoft Graph PowerShell using the command below. Sign in with a Microsoft Entra ID account that has Global Admin privileges:
Connect to Microsoft Graph PowerShell
Copy
Connect-MgGraph -Scopes "Directory.AccessAsUser.All"
- Retrieve a list of domains by running:
Retrieve a list of domains
Copy
- Specify the domain for which you want to enable SSO:
- Define the Login URL, Entity ID, and Logout URL from step 7 of the prerequisites for $url, $uri and $logouturl commands.
- Now copy the SSO certificate file content and assign it to the $cert variable as shown below:
$cert = "MIICqjCCAhOgAwIBAgIJAN..........dTOjFfqqA="
 Configuring Identity360's SSO in Microsoft Entra ID
Configuring Identity360's SSO in Microsoft Entra ID
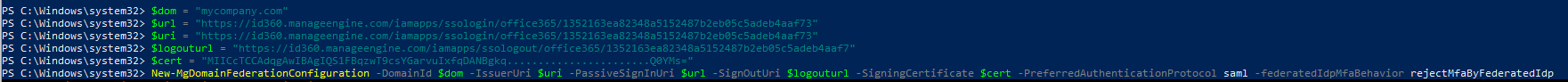
- Run the following command to enable SSO in Microsoft Entra ID:
Command to enable SSO in Entra ID
Copy
New-MgDomainFederationConfiguration -DomainId $dom -IssuerUri $uri -PassiveSignInUri $url -SignOutUri $logouturl -SigningCertificate $cert -PreferredAuthenticationProtocol saml -federatedIdpMfaBehavior rejectMfaByFederatedIdp
- To test the configuration, use the following command.
Command to confirm the SSO setup
Copy
Get-MgDomainFederationConfiguration -DomainId $dom | Format-List
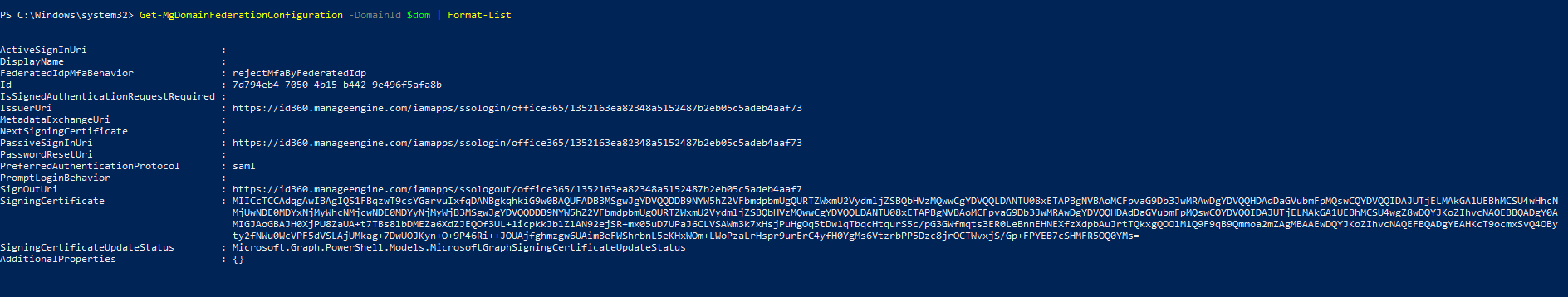 Confirmation of SSO setup in Microsoft Entra ID
Confirmation of SSO setup in Microsoft Entra IDNote: If you have already enabled Microsoft Entra ID SSO using another IdP or want to update Identity360' SSO settings, then you must first disable SSO in Microsoft Entra ID, and then follow the steps given in this guide. To disable SSO in Microsoft Entra ID, use the command given below:
Command to confirm the SSO setup
Copy
$dom = "mycompany.com"
$federations = Get-MgDomainFederationConfiguration -DomainId $dom
Remove-MgDomainFederationConfiguration -DomainId $dom -InternalDomainFederationId $federations.Id
 Confirmation of SSO setup in Microsoft Entra ID
Confirmation of SSO setup in Microsoft Entra ID
Please note that the above change may take some time to get implemented in Microsoft Entra ID.
Identity360 (identity provider) configuration steps
- Switch back to Identity360's Integration Settings tab.
- Enter the Relay State parameter, if necessary.
Note: Relay State is an optional parameter used with a SAML message to help you remember where you were or to direct you to a specific page after logging in.
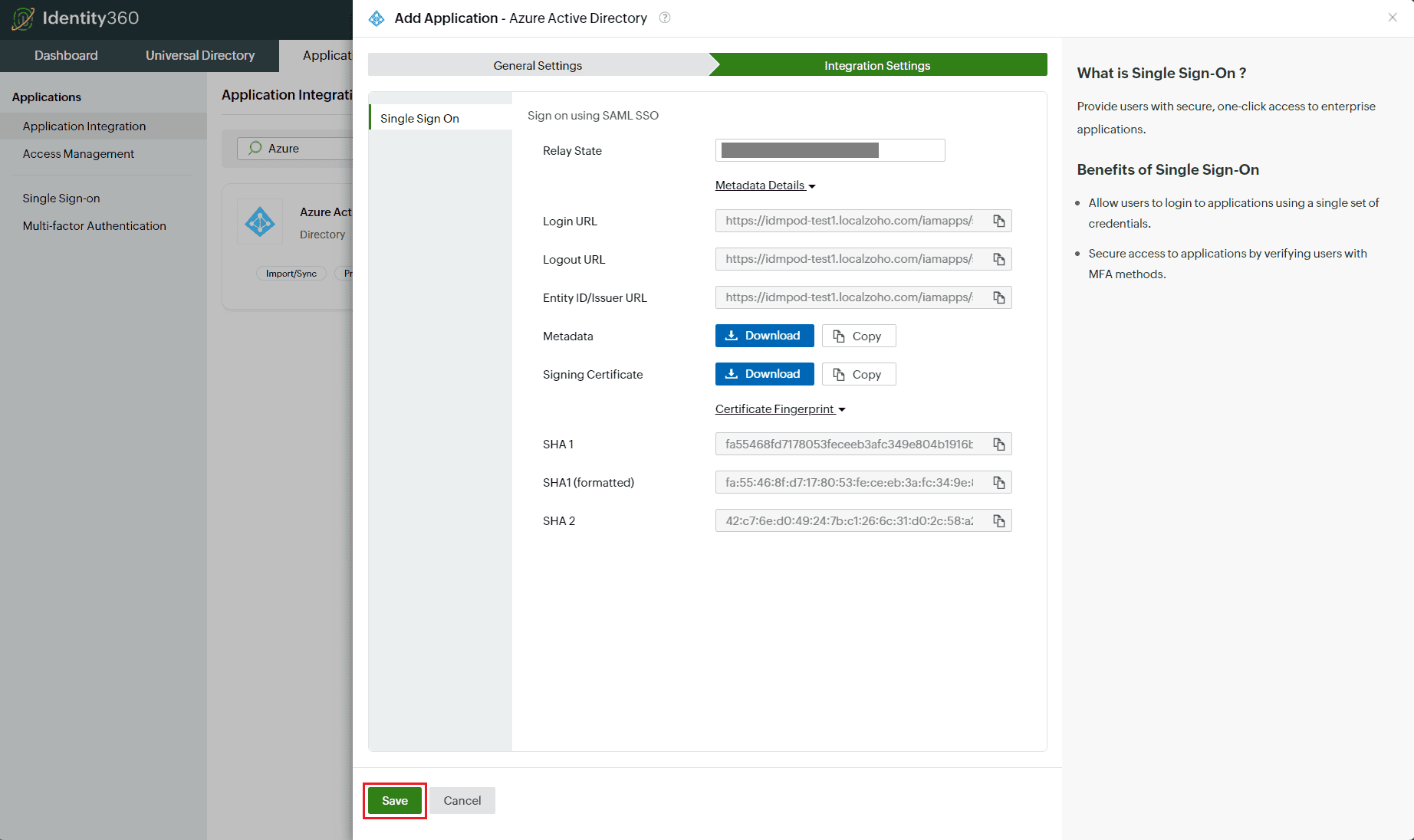 Integration Settings of SSO configuration for Entra ID
Integration Settings of SSO configuration for Entra ID
- Click Save.
To learn how to assign users and groups to one or more applications, refer to this page.
Your users should now be able to log in to Entra ID through the Identity360 portal.
Note: For Entra ID, both SP-initiated and IdP-initiated flows are supported.
Steps to enable MFA for Entra ID
Setting up MFA for Entra ID using Identity360 involves the following steps:
- Set up one or more authenticators for identity verification when users attempt to log in to Entra ID. Identity360 supports various authenticators, including Google Authenticator, Zoho OneAuth, and email-based verification codes. Click here for steps to set up the different authenticators.
- Integrate Entra ID with Identity360 by configuring SSO using the steps listed here.
- Now, activate MFA for Entra ID by following the steps mentioned here.
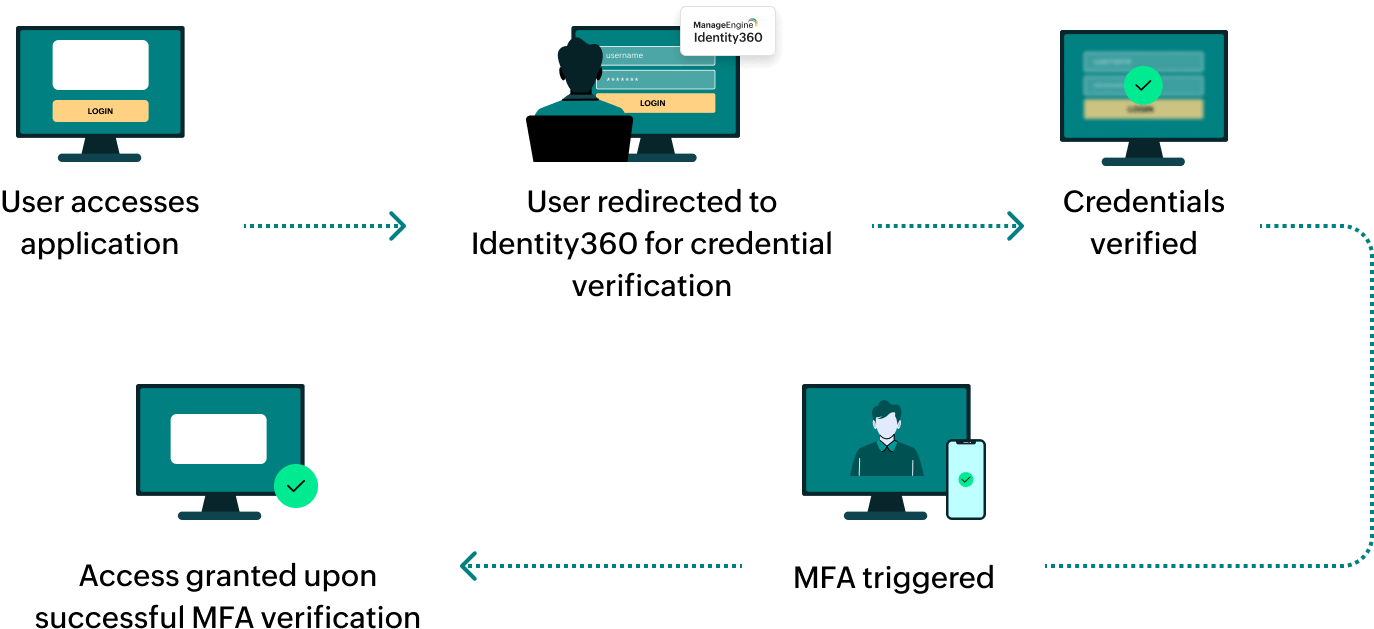
How does MFA for applications work in Identity360?
 General Settings of SSO configuration for Entra ID
General Settings of SSO configuration for Entra ID Integration Settings of SSO configuration for Entra ID
Integration Settings of SSO configuration for Entra ID Configuring Identity360's SSO in Microsoft Entra ID
Configuring Identity360's SSO in Microsoft Entra ID Confirmation of SSO setup in Microsoft Entra ID
Confirmation of SSO setup in Microsoft Entra ID Confirmation of SSO setup in Microsoft Entra ID
Confirmation of SSO setup in Microsoft Entra ID Integration Settings of SSO configuration for Entra ID
Integration Settings of SSO configuration for Entra ID