ITDR is a capability and strategy, not a standalone product. Vendors deliver ITDR features via IAM, PAM, SIEM, or XDR platforms.
On this page
ITDR as the control plane for threat defense
Breaches today rarely start with a vulnerability scan or malware—they start with a login. In modern enterprises, the password has become both the most common point of entry and the weakest security link. Attackers don’t need to break in by exploiting technical vulnerabilities; they can simply log in using stolen or misused credentials. Phishing kits, infostealers, dark web marketplaces, and token theft have made valid credentials the attacker’s weapon of choice.
Yet most enterprise security tooling still activates after access has already been granted. Endpoint detection and response (EDR), extended detection and response (XDR), and SIEM solutions assume that authentication has already done its job correctly. But what if the authentication system is being tricked? What if the account itself is the weapon? This is the silent blind spot in most organizations’ defenses.
The problem is compounded by today’s realities: over-permissioned accounts, legacy trust assumptions in Active Directory (AD), and token sprawl across hybrid cloud and SaaS applications. These conditions allow attackers to move laterally, escalate privileges, and maintain persistence for months—without tripping the alarms of traditional defenses.
Identity threat detection and response (ITDR) has emerged not as a nice-to-have enhancement, but as a necessary correction to these blind spots. ITDR focuses directly on the identity control plane—the accounts, entitlements, and trust tokens that determine who gets access to what. Rather than waiting for malware or network anomalies, ITDR shines a light on misuse at the earliest possible stage: the moment an identity begins acting abnormally.
Origins and evolution: The gap that made ITDR necessary
Historically, security operations centers (SOCs) didn’t monitor identity misuse. Their telemetry came from IP addresses, endpoints, firewalls, and packets—not from authentication flows or privilege assignments. As AD, Microsoft Entra ID, and SAML and OIDC brokers became the new front door for attackers, security teams were still watching the windows and back doors.
Attackers realized this first. In 2020's SolarWinds compromise, nation-state actors infiltrated software build systems by using stolen credentials and SAML tokens. Because these tokens appeared valid, they bypassed detection by EDR and SIEM solutions, which lacked visibility into token life cycle or entitlement drift. For months, attackers moved laterally through United States government agencies, undetected, showing how valid identities could undermine traditional defense layers.
Similarly, the MGM Resorts breach in 2023 demonstrated how attackers weaponized social engineering at the help desk level to reset accounts and abuse identity recovery workflows. No malware was deployed; no firewall was breached. Yet the impact cascaded into massive operational disruption and financial loss. This case highlights that identity abuse is not only a technical gap but a socio-technical one, where human processes and weak recovery mechanisms are leveraged by attackers for entry.
This IAM-SOC disconnect created a gray zone: once access was granted, nobody monitored what the identities did next. IAM teams assumed provisioning and MFA meant safety; SOCs assumed valid logins equaled legitimacy. In reality, attackers exploited this visibility gap to achieve stealth and persistence.
ITDR closes that blind spot. By extending monitoring into the identity layer, ITDR enables real-time behavioral insights—tracking not just who logged in, but how, when, from where, and with what entitlements. It marks a shift from infrastructure-centric detection to identity-centric defense, recognizing that identity is the true control plane of enterprise security.
Why now? Market catalysts for ITDR
Several forces have converged to make ITDR adoption not only relevant, but urgent:
Credential-based attacks have surpassed malware-based attacks
According to the 2024 Verizon Data Breach Investigations Report, 74% of breaches involve the human element, with stolen or misused credentials being the most common cause. Unlike malware, credentials provide “clean” access that bypasses traditional defenses and blends seamlessly into legitimate activity.
Cloud and SaaS adoption drive identity sprawl
Enterprises now juggle multiple identity providers—Microsoft Entra ID, Okta, Ping Identity—alongside thousands of SaaS applications. Each system introduces inconsistent access controls, often leaving behind shadow accounts, orphaned identities, and forgotten test users. These accounts become silent back doors.
Machine identities outnumber human identities
APIs, service accounts, bots, and non-human identities now exceed human users in most large organizations. These identities often rely on static credentials, rarely rotate secrets, and are excluded from regular audits. For attackers, a compromised service account is more valuable than a human account, as it often carries higher privileges and less monitoring.
Misconfigurations and shadow access are rampant
The Colonial Pipeline attack (2021) underscored this risk. A single unused VPN account—without MFA—was compromised, allowing attackers to paralyze fuel supply across the Eastern United States. The breach wasn’t due to advanced malware but to a poorly governed identity with unchecked access.
SOC visibility remains post-compromise
Despite Zero Trust initiatives, most SOCs still rely on detecting malware traces, C2 communications, or endpoint anomalies. By the time alerts are generated, attackers may have already exfiltrated sensitive data or escalated privileges. ITDR flips the paradigm, enabling detection at the identity layer, where the attack truly begins.
The result: Enterprises are realizing that without ITDR, their Zero Trust strategies remain incomplete.
The ITDR adoption landscape
Adoption of ITDR varies across sectors, but common patterns are emerging.
Financial services
Banks and insurers are often first movers because they manage tens of millions of human identities and millions more service accounts across hybrid infrastructures. Regulatory scrutiny is intense, and breaches directly affect customer trust and market stability. ITDR is increasingly viewed as essential for compliance with DORA and for reducing systemic financial risk.
Healthcare
Hospitals and biotech organizations operate under HIPAA and similar frameworks, where identity misuse can jeopardize not just data but patient safety. The ransomware attack on Ireland’s Health Service Executive in 2021, which began with a phishing incident leading to compromised accounts, caused weeks of disruption to care. ITDR offers healthcare providers the ability to detect unusual privilege use before it disrupts clinical operations.
Critical infrastructure
Utilities, energy providers, and manufacturers are digitizing operations at scale, blending IT with operational technology (OT). This creates risk: A single over-permissioned OT account could lead to physical consequences.
One real-world example occurred in February 2021 in Oldsmar, Florida, when a remote intruder accessed the town's water treatment plant’s control system and manipulated the dosing rate of sodium hydroxide. They temporarily increased the chemical by a dangerous amount, demonstrating how a compromised account could threaten public health.
ITDR provides visibility into hybrid identity environments where operational downtime translates to public concerns.
Across industries, the key drivers are consistent:
- The explosion of human and non-human identities.
- The need for Zero Trust visibility across hybrid and multi-cloud environments.
- Increasing regulatory pressure that's emphasizing detection at the identity level.
Definition and scope of ITDR: What it is—and what it’s not
ITDR is a detection and response strategy centered on identity context. It is not a replacement for IAM, SIEM, or EDR. It’s a distinct discipline built to close the visibility gap between IAM provisioning and SOC monitoring.
IAM vs. ITDR
IAM provisions, authenticates, and governs access. ITDR continuously monitors account usage, detects misuse, and triggers intervention. IAM ensures that the right account exists; ITDR ensures that the account isn’t being abused.
SIEM/UEBA vs. ITDR
SIEM correlates logs, and UEBA identifies anomalies, but both lack entitlement awareness. Without understanding role hierarchies, group memberships, and trust paths, they struggle to distinguish between legitimate privilege escalation and malicious misuse. ITDR bridges this gap with entitlement-level awareness.
EDR/XDR vs. ITDR
Endpoint and network tools detect threats after an identity is already compromised. ITDR intervenes earlier by spotting abuse at the identity layer. This preemptive lens is the crucial differentiator.
In short: ITDR shifts the detection lens to the very root of access—who has it, how it’s used, and whether it’s being abused.
Core capabilities that define mature ITDR
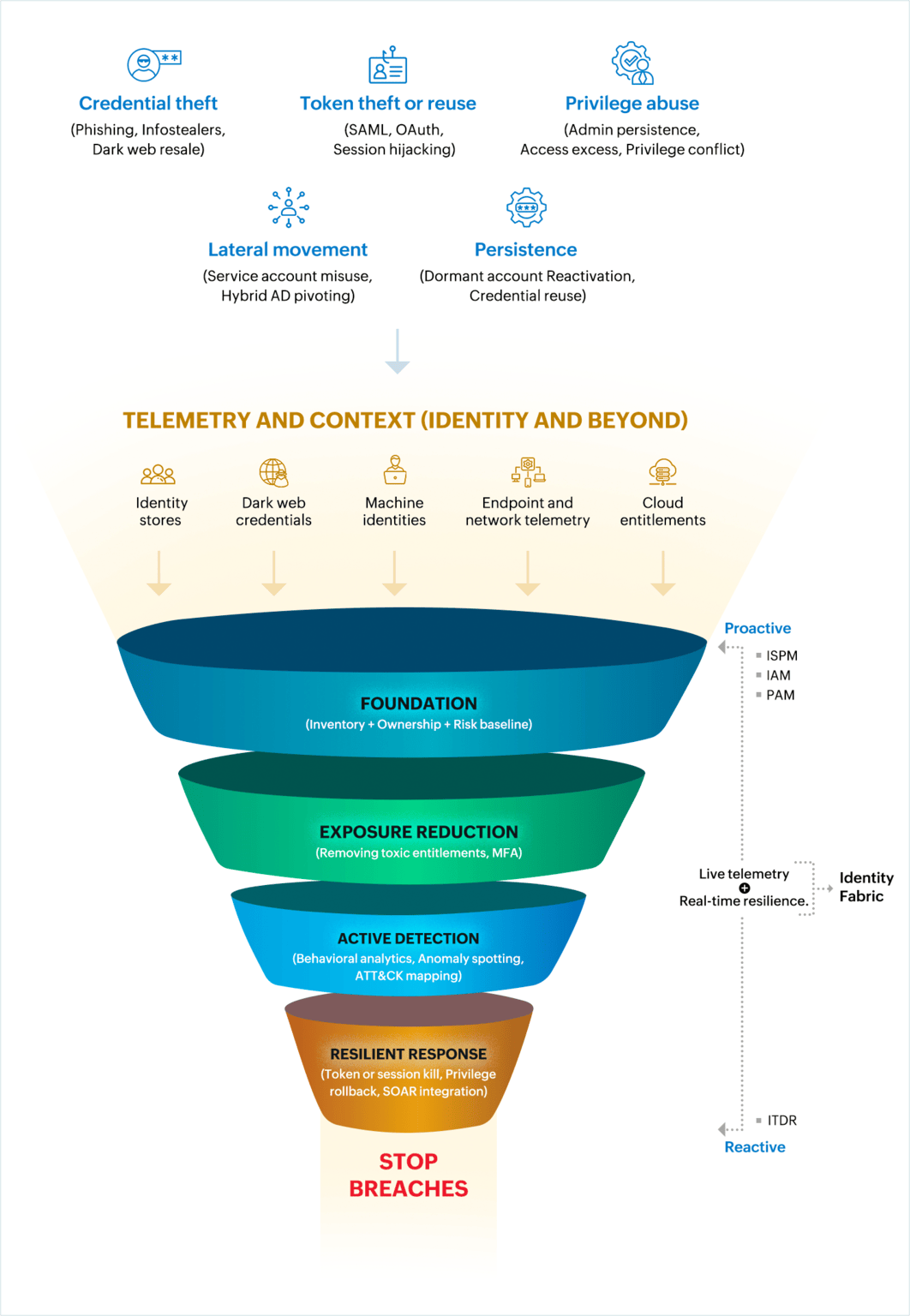
A robust ITDR program incorporates several interlocking capabilities:
Identity behavior analytics and baselining
Instead of treating all logins equally, ITDR builds behavioral fingerprints: time-of-day activity, frequency of resource access, device types, and peer comparisons. For instance, a service account suddenly logging in from a new geolocation or accessing new resource classes raises a flag.
Detection at the identity layer
Privilege escalations, anomalous logon patterns, dormant account reactivation, token misuse, and abuse of over-permissioned service accounts—all are red flags ITDR is designed to catch in real time.
Threat hunting and investigation
Mature ITDR tools allow SOCs to visualize attack paths across identities, showing lateral movement potential, historical access patterns, and privilege graphs. This supports proactive threat hunting rather than reactive firefighting.
Automated response and remediation
Detection without response is noise. ITDR automates responses: step-up authentication, session revocation, forced password resets, or account disablement based on policy. These actions shorten dwell time and contain damage.
Workflow and recovery integration
ITDR doesn’t operate in isolation. It integrates with SOAR platforms for automated playbooks, ITSM systems for incident management, and IAM platforms for rollback and remediation of entitlements. This ensures incidents are both stopped and cleaned up.
ITDR in practice
Consider the SolarWinds compromise:
- Without ITDR: Attackers gained access with stolen credentials, inserted a backdoor into Orion network management system, and moved laterally using over-permissioned service accounts. The logins looked valid, so SIEMs and EDRs didn’t flag them. Stolen SAML tokens let attackers access cloud environments undetected. It took months to discover, by which time 18,000+ organizations—including U.S. federal agencies—were affected.
- With ITDR:
- Behavior analytics flag unusual logins from service accounts tied to Orion builds.
- Token issuance patterns, including SAML tokens reused outside scope or from atypical IPs, trigger alerts.
- Dormant accounts suddenly showing privilege activity require step-up MFA or are disabled.
- Posture monitoring detects toxic entitlement combinations (e.g., developer accounts with product access).
The result: The attack chain is interrupted early, not months later. ITDR doesn’t prevent the initial credential theft, but it stops privilege abuse from going unnoticed.
Implementing ITDR: How to get started
Rolling out ITDR is less about installing another security tool and more about building an operational discipline around identities. Instead of copying the old discover–detect–respond cycle, enterprises should think about ITDR as a layered practice that matures over time. A practical approach can be broken down into four overlapping pillars: foundation, exposure reduction, active detection, and resilient response.
1. Build the foundation: Full-spectrum identity awareness
You cannot defend what you don’t know. The first step is creating a living inventory of identities—not just human accounts but the far larger universe of APIs, workloads, bots, and service accounts.
- Aggregate data from AD, Microsoft Entra ID, SaaS IdPs, and cloud providers into a single view.
- Tie each account—human or non-human—to an owner to avoid orphaned identities.
- Merge duplicate accounts across hybrid environments so activity attribution is clear.
- Apply baseline risk scores based on entitlements, exposure, and sensitivity.
This stage turns a fragmented identity sprawl into a defendable surface.
2. Reduce exposure before attackers exploit it
Before monitoring, shrink the attack surface by hardening what’s already visible. This step is about making privilege abuse harder to pull off.
- Retire dormant accounts and credentials that attackers love to exploit.
- Enforce MFA on sensitive accounts and reduce standing admin privileges.
- Strip away over-permissioned SaaS roles and risky entitlement combinations.
- Rotate service account credentials and set clear rules on where they can log in.
The goal isn’t perfection but measurable reduction of low hanging fruit for attackers that would otherwise be invisible until too late.
3. Move from passive logs to active identity detection
Detection is where ITDR departs from traditional SOC tooling. Instead of looking at packets or malware traces, ITDR asks: Is this identity behaving in a way that makes sense?
- Monitor for chained events, like a suspicious password reset followed by a privilege escalation.
- Flag parallel logins from impossible geographies or devices.
- Detect anomalous activity from service accounts, especially lateral movements into new environments.
- Align abnormal identity activity with frameworks like MITRE ATT&CK® to recognize attacker TTPs quickly.
This isn’t about flooding analysts with more alerts; it’s about surfacing the few identity signals that matter before an attacker gains persistence.
4. Embed response into everyday operations
The last step is making sure detections lead to action, not noise. The best ITDR programs are tightly integrated into existing SOC workflows.
- Automate real-time actions like logging out risky sessions, revoking tokens, or disabling accounts.
- Route alerts into SIEM, SOAR, and XDR pipelines so identity detections don’t sit in a silo.
- Integrate with ITSM and case management tools so incidents are tracked and audited.
- Maintain investigation context through long-term logs and historical access graphs.
This transforms ITDR from an alerting layer into an operational safety net, reducing dwell time and giving SOC analysts a clear path to act.
This progression—from building visibility to embedding response—does more than strengthen day-to-day operations. It also sets the stage for the next evolution of identity security, where ITDR becomes part of a larger architectural shift.
ITDR and the future of identity fabric
The push toward identity fabric is about more than connecting IAM, PAM, and governance into a unified architecture. It’s about creating a living system where identity is not just provisioned and governed, but continuously defended.
This is where ITDR plays a pivotal role. It brings the live telemetry and response capabilities that a static identity fabric cannot deliver on its own. By monitoring human and non-human identities, tracking token life cycles, and containing abnormal activity in real time, ITDR ensures that the fabric remains intact even when adversaries are already inside the environment.
Think of it this way: without ITDR, an identity fabric is strong in design but passive in execution. With ITDR, the fabric gains adaptability. It can identify when an entitlement is exploited, when a token is hijacked, or when a service account behaves abnormally—and then automatically adjust policies, restrict access, or trigger investigations.
The path forward for enterprises is clear. ITDR must now integrate into the broader identity ecosystem to create an operational identity fabric—one that is not only unified, but resilient under pressure. This convergence is not theoretical; it is already happening, and it will define how enterprises secure identity in the years to come.
Frequently asked questions
IAM provisions and governs access. ITDR monitors ongoing use and intervenes when misuse is detected.
Yes. MFA stops many attacks, but attackers still bypass it via phishing-resistant malware, token replay, or helpdesk social engineering. ITDR detects these bypasses in real time.
Finance, healthcare, and critical infrastructure lead adoption, but any enterprise with hybrid cloud and thousands of identities will benefit from ITDR.
By monitoring service accounts, API keys, and certificates for misuse, drift, or privilege escalation—capabilities traditional IAM lacks.
No. ITDR complements them, enriching SIEM with identity context and strengthening PAM by monitoring privileged account behavior.
Frameworks like DORA and NIS2 emphasize real-time detection of identity misuse. While not always named explicitly, ITDR aligns directly with compliance expectations.
Yes—by monitoring abnormal behavior from valid accounts, including privilege misuse, lateral movement, and unusual access patterns.
A basic ITDR program can be launched in months by integrating with existing IAM and SIEM systems. Full maturity takes longer, depending on identity sprawl.
Key metrics include mean time to detect, reduction in dwell time, percentage of identities covered, and number of privilege misuse incidents caught pre-compromise.
Related solutions
ManageEngine AD360 is a unified IAM solution that provides SSO, adaptive MFA, UBA-driven analytics, and RBAC. Manage employees' digital identities and implement the principles of least privilege with AD360.
To learn more,
Sign up for a personalized demoManageEngine Log360 is a unified SIEM solution with UEBA, DLP, CASB, and dark web monitoring capabilities. Detect compromised credentials, reduce breach impact, and lower compliance risk exposure with Log360.
To learn more,
Sign up for a personalized demoThis content has been reviewed and approved by Ram Vaidyanathan, IT security and technology consultant at ManageEngine.
