What is malware mitigation?
Malware mitigation is a set of frameworks, processes, and best practices used to detect, contain, and neutralize malicious software before it can cause widespread harm. From a business standpoint, this includes:
- Early detection of a malware or its malicious activity through behavioural analysis.
- Threat containment to prevent lateral movement across systems.
- Post-incident forensics to strengthen defenses against future attacks.
Malware mitigation strategies for enterprises
Effective threat mitigation requires a layered security approach:
- Endpoint hardening: This includes deploying advanced endpoint protection solutions such as real-time scanning and anomaly detection, implementing device control to prevent unauthorized USB/media usage etc.
- Advanced threat protection (ATP): Use AI-powered threat intelligence to identify new attack patterns and proactively block suspicious processes and file executions.
- Incident response: Configure a quarantine policy and endpoint isolation. You can also integrate with SIEM and SOAR tools for unified cyber threat response.
- Continuous malware analysis: Breakdown a malware attack from its first entry point to resolution via forensic process trees. Correlate attack indicators with global threat feeds and repositories such as VirusTotal and MITRE.
How Malware Protection Plus aids in threat mitigation
Threat Detection & Prevention
- Real-time process monitoring
It continuously observes process behaviour, quickly identifying anomalies such as code injection or unusual memory access patterns.
- Pre-emptive process termination
Halt malicious processes in their tracks before they can execute harmful payloads, effectively preventing ransomware deployment, data encryption, or lateral movement within your network.
- Exploit protection
Stop memory corruption attempts, thwarting exploits that are often used in fileless malware and advanced persistent threats (APTs).
- Zero-day exploit shielding
By monitoring kernel-level activity, the system detects and blocks previously unknown exploits targeting software vulnerabilities.
- Ransomware behavioral lockdown
The software can identify and terminate ransomware based on unusual file encryption patterns, such as mass file modifications within a short time frame.
- Repeat-attack defense
By leveraging Machine Learning, Malware Protection Plus recognizes evolving attack patterns, preventing adversaries from reusing infiltration methods.
- Trusted executable safelisting
If you’re tired of false alarms in your malware scans, you can exclude trusted and verified executables, scripts, and apps, to cut down on these interruptions, letting you focus on what truly matters.
- Decoy file monitoring
Deploy disguised files (honeypot tactics), to attract ransomware or spyware, revealing attacker behavior.
- Early-warning system
Security teams are alerted as soon as decoys are interacted with, enabling them to take preemptive countermeasures before real data is affected.
Incident containment & response
- Automated remediation
Tackle malware by restoring corrupted system files, registry entries, and configurations to their original, clean state automatically, eliminating the need for manual intervention as the solution autonomously disinfects malware.
- Active kill mode
Automatically terminate malicious processes, quarantine files, and deploy recovery efforts to limit further damage.
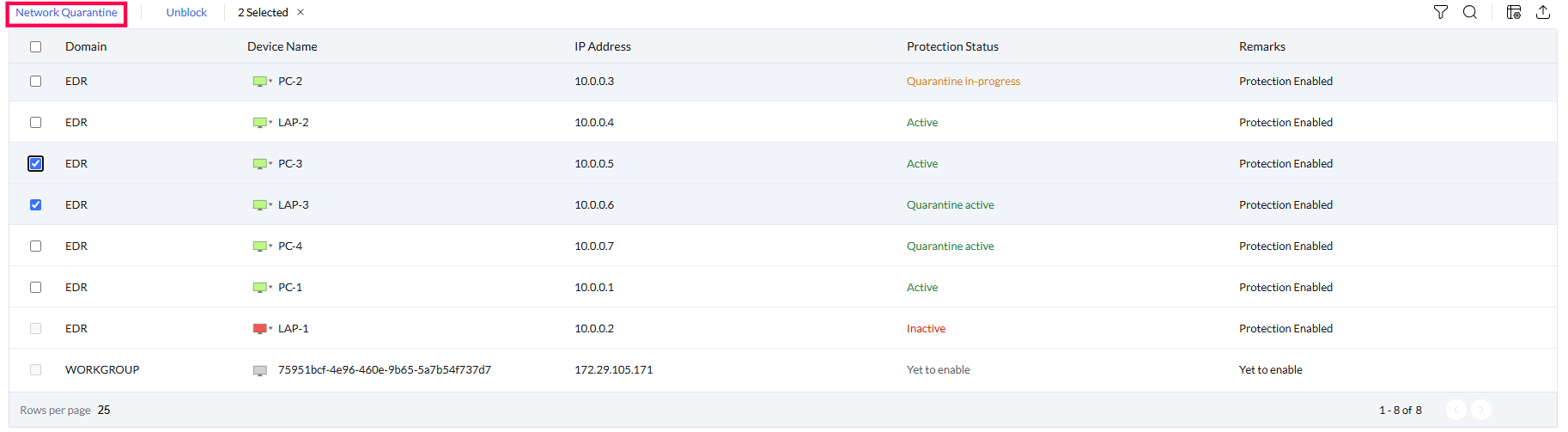
- Device isolation and network Segmentation
With just a click, compromised devices can be quarantined to stop the lateral movement of threats within your network.
- Investigative audit mode
Log and analyze malicious activities without triggering an immediate response, allowing security teams to carefully evaluate and decide on the best course of action.
- Group-based security management
Tailor your security measures to fit the unique needs of different departments, ensuring vital business applications run without a hitch while maintaining a robust security stance.
Recovery & continuity
- Rollback capabilities
Undo any unauthorized changes made by malware or file encryption by ransomware ensuring the system integrity while minimizing downtime and disruption.
- Secure backup integrity
Maintain tamper-proof backups of critical files, ensuring that you can recover your files even in the event of a ransomware attack.
- Encrypted File restoration
Using incremental backups and volume shadow copies, systems can be reverted to their pre-infection states within minutes.
- Ransomware rollback
Revert unauthorized encryption by ransomware. Effortlessly restore your files from secure, untouched backups, ensuring your operations can continue without disruptions.
Frequently Asked Questions
01. How is malware mitigation different from malware removal?
+-Malware mitigation focuses on preventing and containing threats before they can cause significant harm, whereas malware removal deals with eliminating infections after they have occurred. Mitigation strategies aim to reduce the risk and spread of malware through proactive measures.
Read more02. Can malware mitigation stop zero-day threats?
+-Yes. By leveraging AI-driven anomaly detection, behavior monitoring, and proactive blocking mechanisms, malware mitigation can identify and halt many zero-day attacks before they are executed, providing protection against unknown or emerging threats.
Read more03. How does threat mitigation tie into incident response?
+-Threat mitigation plays a critical role in incident response by reducing the scope and severity of an attack. Effective mitigation limits the damage, isolates compromised systems, and contains the threat, enabling the incident response team to act faster and with greater precision.
Read more