ManageEngine PAM360
A Unified Privileged Access Management Platform
Modern enterprise IT environments extend far beyond traditional data centers. Organizations operate across on-premises systems, cloud platforms, SaaS applications, APIs, and DevOps pipelines, each hosting critical systems and sensitive data. Managing privileged access across these distributed environments is complex and high risk. Privileged accounts can bypass standard security controls, making them a primary target for misuse, insider threats, and external attacks. A compromised privileged access can allow attackers to laterally move across IT environments, escalate permissions, disable security controls, and attain persistent control over the organization’s digital medium.
To reduce these risks, enterprises should shift to proactive security controls, policy-driven privileged access governance. This requires organizations to:
- Enforce centralized control over how privileged access is requested, approved, provisioned, and revoked
- Govern who can access what, when, for how long, and under what conditions
- Secure administrative access paths to prevent unauthorized elevation, misuse, and credential-based attacks
- Continuously monitor, record, and audit all privileged activities performed by employees, contractors, applications, and third-party vendors
Enforcing effective privileged access governance is difficult in large enterprises with diverse teams and complex infrastructures. Privileged access is often scattered across systems, embedded in CI/CD pipelines, shared among teams, or stored insecurely for operational convenience. This fragmentation results in limited visibility and control, increasing the risk of insider threats, external attacks, and regulatory non-compliance.
This is where a Privileged Access Management solution becomes essential. This document explains how PAM360 addresses these challenges and outlines its key capabilities and use cases.
- Securing Privileged Access with PAM360
- Key Features and Core Capabilities of PAM360
- A 360-Degree Approach in Securing Privileged Access
Securing Privileged Access with PAM360
ManageEngine PAM360 is a unified Privileged Access Management (PAM) solution that helps organizations secure, control, monitor, and automate privileged access across their entire IT infrastructure. It centralizes privileged access governance and enforces policy-driven controls to eliminate unmanaged, persistent, and high-risk administrative access. PAM360 replaces uncontrolled privileged access with time-bound, policy-based, purpose-specific, and fully monitored access. All privileged credentials are securely stored in an encrypted vault and are never exposed directly to users or applications. Privileged operations are executed through PAM360, ensuring complete visibility, traceability, and accountability.
With PAM360, organizations can:
- Enforce least-privilege and Zero Standing Privilege models by granting elevated access only when required, for a defined duration, and strictly for approved activities
- Control privileged access based on user identity, role, context, and risk, ensuring access is limited to what is necessary for each task
- Implement just-in-time (JIT) access to dynamically provision and automatically revoke privileged rights once the task is completed
- Strengthen access verification by integrating multi-factor authentication (MFA), adaptive authentication, and conditional access policies
- Secure privileged credentials through centralized vaulting, automated password and key rotation, and the elimination of hard-coded or shared credentials
- Detect and respond to suspicious privileged activity using behavioral analytics, policy enforcement, and real-time alerts
- Enable secure remote privileged access to critical systems without exposing passwords, keys, or secrets to end users
- Monitor, record, and audit all privileged operations to maintain real-time visibility, enforce accountability, and support forensic investigations
- Meet regulatory and compliance requirements such as NIS2, ISO/IEC 27001, HIPAA, PCI DSS, DORA, NERC CIP, LGPD, and internal governance mandates through comprehensive audit logs and reporting
With all above capabilities, ManageEngine PAM360 is being a trusted solution used by over 5000 organizations and government agencies across continents.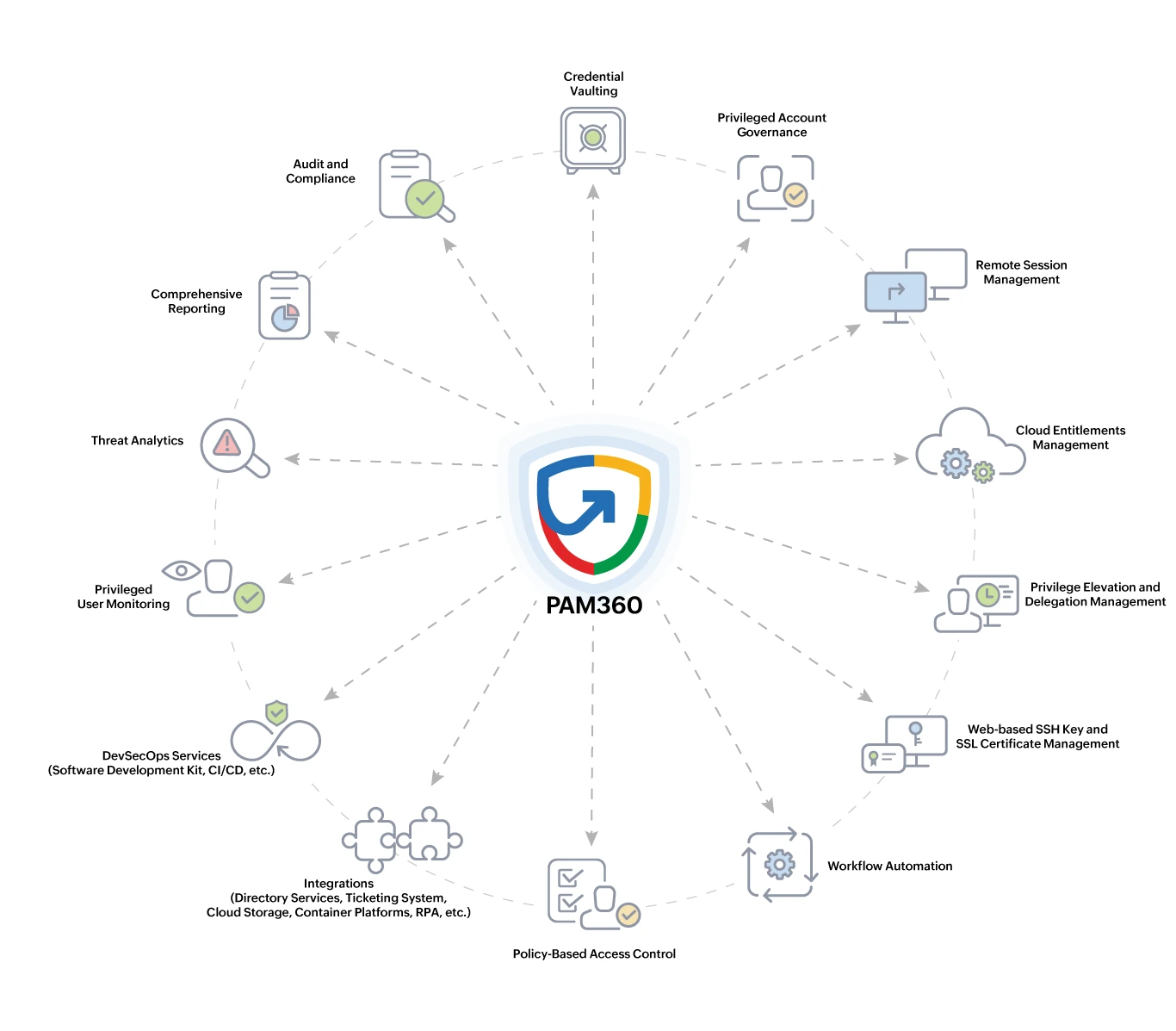
Key Features and Core Capabilities of PAM360
- Enterprise Credential Vault - Securely stores and manages privileged credentials in an encrypted vault with automated rotation, access control, and zero credential exposure to users or applications.
- Endpoint Privilege Management - Controls and governs privileged access on endpoints by eliminating local admin rights and enforcing least-privilege workflows.
- Privilege Elevation and Delegation Management - Provides Just-In-Time privilege elevation, application and command-level controls across Windows and Linux systems, enforcing fine-grained delegation and least-privilege execution to ensure users operate strictly within approved privilege boundaries and prevent unnecessary administrative access.
- Zero Trust Controls - Implements least-privilege and Zero Standing Privilege principles using identity, context, policy, score-based, and risk-based access enforcement.
- Secure Remote Access - Enables secure, password-less remote access to servers, endpoints, network devices, and applications without exposing credentials, keys, or secrets to end users.
- Universal Connectors - Provides broad integration support for operating systems, databases, network devices, cloud platforms, and third-party applications through RESTful APIs, SDKs, and SCIM connectors, enabling automated privileged actions, seamless identity provisioning, elimination of hard-coded credentials, and centralized audit visibility.
- Privileged Session Monitoring - Monitors and records all privileged sessions in real time, enabling full visibility, accountability, and forensic investigation capabilities.
- System Events and Keystroke Logging - Records critical system events and all keystrokes during privileged sessions to provide complete visibility into privileged activity, support forensic investigations, detect misuse or policy violations, and meet audit and compliance requirements.
- Context-Aware Event Correlation - Correlates privileged access events across users, systems, and sessions to provide contextual insights and faster threat detection.
- Privileged User Behavior Analytics - Uses AI and ML-driven analytics to detect anomalous or risky privileged behavior and trigger alerts based on deviations from normal activity.
- Application Credential Security - Secures and rotates credentials used by applications, scripts, and services to prevent hard-coded secrets and credential leakage.
- SSH Key Management - Discovers, manages, rotates, and audits SSH keys to eliminate key sprawl and prevent unauthorized access.
- SSL Certificate Management - Manages the complete SSL/TLS certificate lifecycle, including discovery, renewal, and deployment, to prevent outages and impersonation attacks.
- DevOps Protection - Secures secrets and privileged access across CI/CD pipelines, automation tools, and orchestration platforms without disrupting workflows.
- Privileged Task Automation - Automates privileged operations through policy-controlled workflows, eliminating manual intervention and reducing human error.
- IT and Security Platform Integrations - Integrates with ITSM and ticketing systems to validate access requests, approvals, and session execution; connects with IGA platforms for credential management and rotation; and integrates with SIEM and threat analytics tools for centralized log collection, monitoring, and security analysis.
- Business Continuity - Ensures continuous access to passwords in mission-critical environments by providing high availability and disaster recovery models beyond basic failover, including Application Scaling and Read-Only servers.
- Audit and Compliance - Supports regulatory and internal compliance requirements through detailed audit trails, access logs, and enforcement of security controls.
- Comprehensive Reporting - Generates detailed, exportable reports covering access activities, session data, policy enforcement, and compliance readiness.
- Interactive Dashboards - Provides real-time, visual dashboards offering insights into privileged access activities, risks, compliance status, and system health.
Refer to this page to learn more about the key features and core capabilities in detail.
360-Degree Approach to Securing Privileged Access
ManageEngine PAM360 brings together administrative access controls, activity oversight, and security enforcement into a single system that enables organizations to govern high-risk access in a consistent and auditable manner across their environments. It standardizes how elevated access is controlled providing end-to-end visibility into actions performed on critical systems, databases and cloud resources. Through integrations with ITSM and security platforms, policy-controlled task automation, enforcement of time-bound access, and Zero Standing Privilege, PAM360 ensures privileged activities are tied to validated business context and automatically withdrawn after use. By incorporating CIEM capabilities to continuously identify excessive permissions and risk exposures across cloud accounts from a centralized dashboard, PAM360 helps organizations proactively reduce compliance gaps and demonstrate adherence to internal controls and external regulatory requirements.
By bringing these capabilities together, PAM360 delivers a robust and reliable approach to securing privileged access operations, making it a critical component of modern enterprise security architectures.
Navigate through the help documentation to learn more about PAM360 features, deployment, configuration, and usage.