An all-encompassing, objective approach to PAM maturity
Not another one-size-fits-all PAM maturity model
As a recognized privileged access management (PAM) vendor in the global PAM market, ManageEngine has had the privilege to work with thousands of different PAM deployments. The one thing that remains the same throughout this diverse sample pool is that no two PAM deployments are the same, and they needn't be. This is due to several factors, including the organization's size, financial priorities, risk appetite, PAM requirements, and infrastructure.
With that philosophy as our blueprint, coupled with an intensive market study, our team has constructed this PAM maturity model to help you personalize the path to becoming PAM-mature.
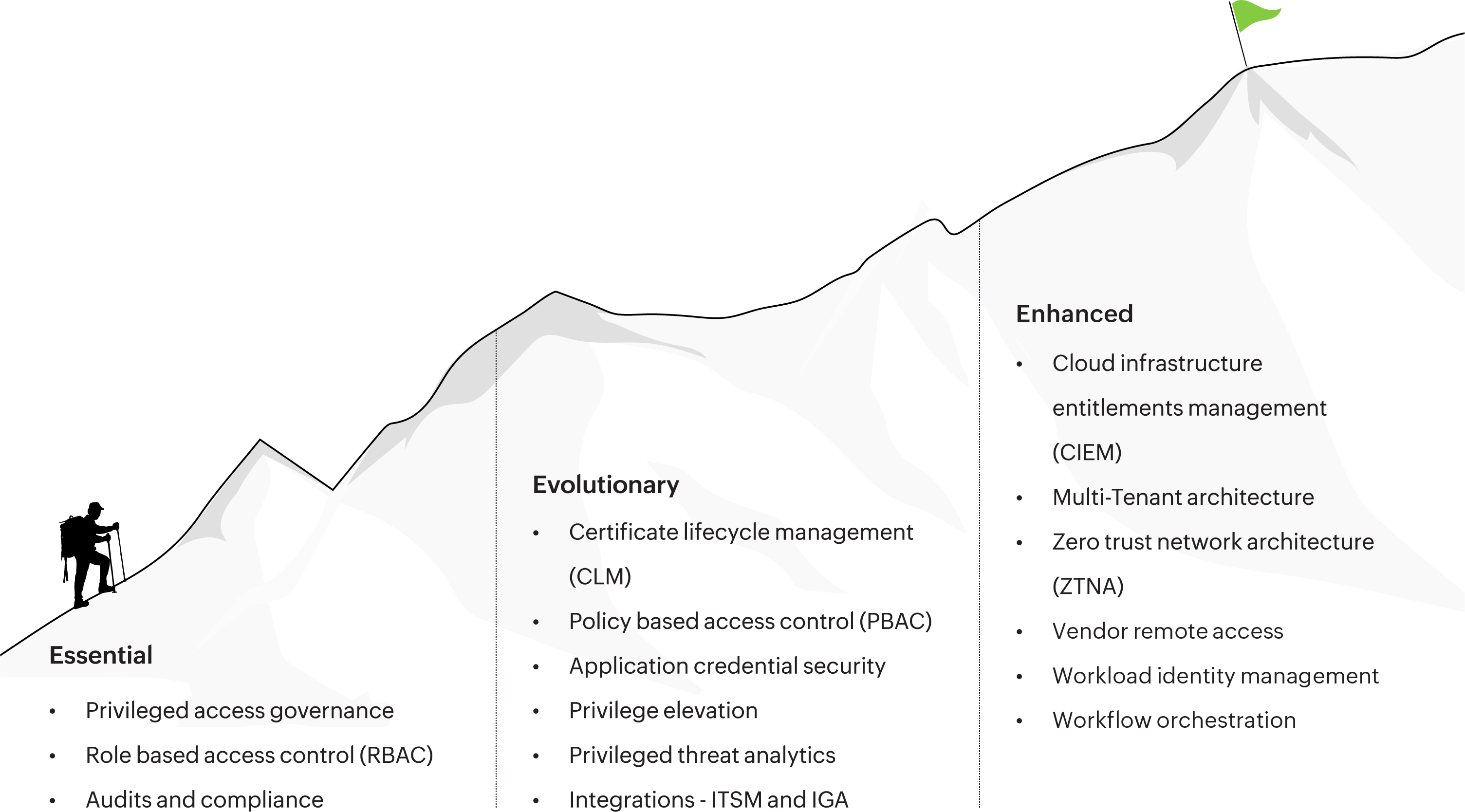
Not all PAM journeys are the same, but all PAM journeys start in the same place, which is adopting controls that help you govern privileged identities, minimize risk, and adhere to compliance standards.
Zero Trust is the foundation on which any PAM deployment should be implemented. The journey ahead may seem long, but donning Zero Trust access controls catalyzes your PAM journey and makes the ultimate goal of Zero Standing Privileges seem within reach.
Integration and automation are the supplements that your organization needs to keep itself sustained throughout its PAM journey. Implementing this dimension in your PAM portfolio helps you reduce manual overhead and increase productive admin hours.
| Maturity dimension | Controls |
|---|---|
| GRC |
A central vault to manage users' privileged identities A central inventory to manage privileged endpoints and secrets Regularization or rotation of privileged identities Automated auditing and recording of privileged sessions Compliance with federal IT standards such as HIPAA, SOX, and the PCI DSS |
| Zero Trust |
| Maturity dimension | Controls |
|---|---|
| GRC |
Real-time risk assessments (popularly in the form of trust scores) for all privileged accounts, dependent on various privileged actions performed Certificate life cycle management App-to-app credential management |
| Zero Trust |
Policy-based access controls to validate access sharing based on user and endpoint behavior Application and command controls for privileged endpoints |
| Maturity dimension | Controls |
|---|---|
| GRC |
Governance for legacy systems, multi-tenant infrastructures, SaaS, and internal applications Access governance and monitoring for cloud entitlements |
| Zero Trust |
Step-up authentication for layered privileged access policies ZTNA to manage network-, application-, and database-level privileged access One-click access through the PAM solution for third-party vendors and other collaborators who require privileged access |

PAM360 and Compliance

PAM360 and Cyber Insurance

The ultimate PAM buyer's guide