Active Directory (AD) serves as the nerve center for most organizations, playing a pivotal role in managing authentication and authorization processes. This makes AD an irresistible target for cybercriminals eager to exploit vulnerabilities and steal critical data. To protect your AD environment from infiltration, it’s crucial to understand how successful AD attacks unfold and to devise a robust defense strategy to combat them. Read on to explore the 10 most common AD attacks and find out how you can quickly detect them in your environment and protect your AD resources.
Password-based attacks
Most AD systems rely on passwords as their first line of defense against compromise. But weak, easy-to-guess passwords often leave accounts vulnerable to attacks. As a result, bad actors are always on the prowl for opportunities to exploit poor password practices. The two most common ways they do so are through brute-force and password spraying attacks.
Brute-force attacks
In this popular attack, hackers try to guess an account's password by systematically testing every possible combination. With the help of automated tools like hashcat and John the Ripper, attackers can try thousands or even millions of passwords in minutes, turning what would take years manually into a rapid, much easier process.
How to detect brute-force attacks
Look for repeated failed login attempts from a single account or IP and investigate unusual login patterns to detect possible brute-force attacks.
Password spraying attacks
Password spraying is stealthier than brute-force attacks. Instead of trying multiple passwords on one account, attackers try a single, commonly used password (like Password123) on many accounts. This minimizes the risk of triggering account lockouts and, as a result, does not draw attention.
How to detect password spraying attacks
Keep an eye out for multiple failed logins that occur across different accounts but originate from the same source. This is a telltale sign of a potential password spraying attack.
How to protect against password-based attacks
Enforce strong password and account lockout policies across your organization and educate users on best practices to mitigate password-based attacks.
NTLM-authentication-based attacks
New Technology LAN Manager (NTLM) is an authentication protocol that uses password hashes to verify user identities. While it provides basic security, attackers can exploit it through methods like pass-the-hash and NTLM relay attacks to gain unauthorized access to accounts.
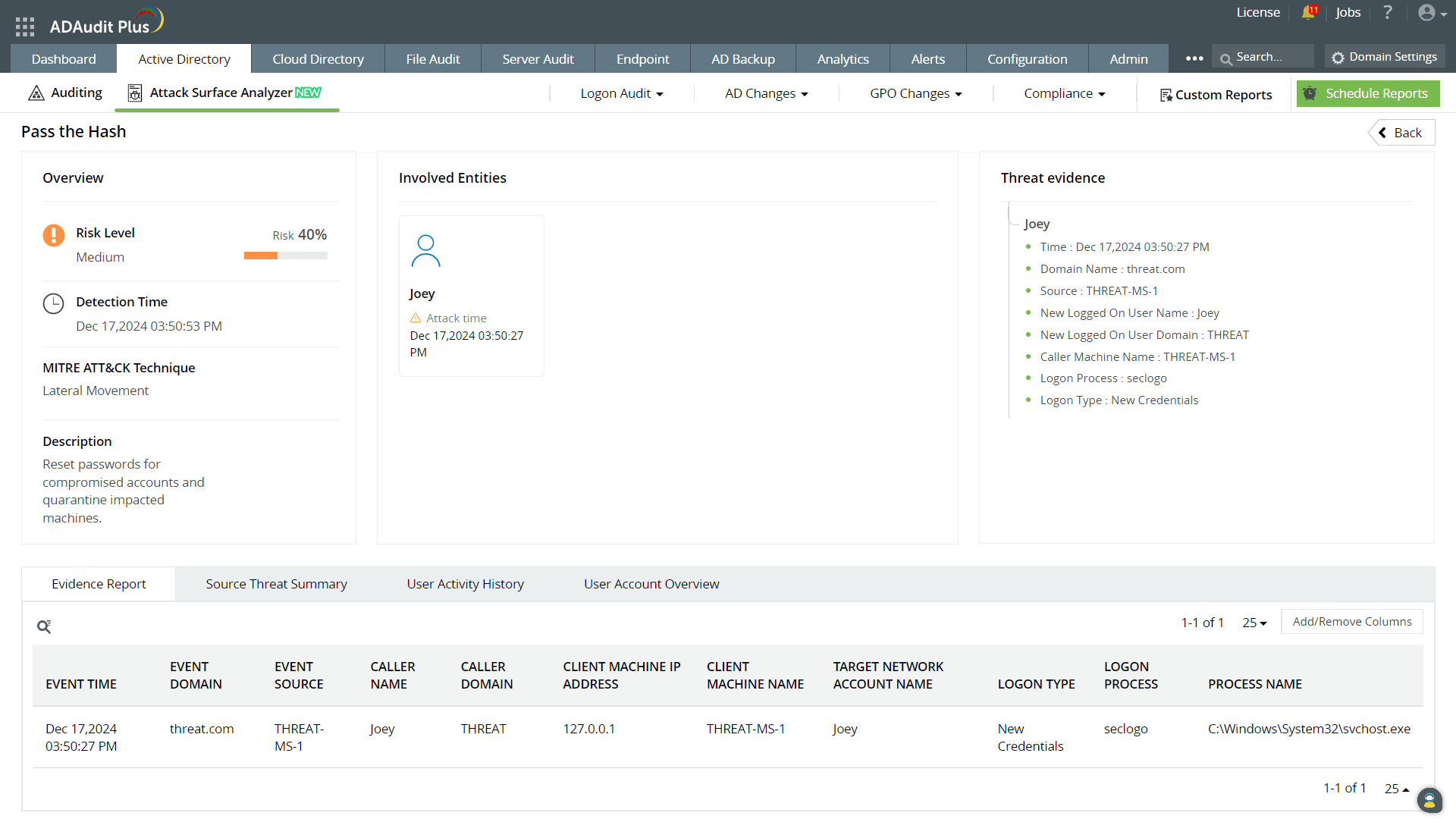
Pass-the-hash attacks
In a pass-the-hash attack, attackers steal the hashed version of a password (instead of the plaintext password) and use it to authenticate as the user. Since NTLM doesn’t validate the source of the hash, it treats the hash like a legitimate password. This allows the attackers to bypass password authentication entirely and impersonate users to move laterally across your network.
How to detect pass-the-hash attacks
Abnormal user behavior, such as logins occurring outside business hours from unexpected locations or devices and sudden spikes in authentication requests, are likely indicators of pass-the-hash attack attempts.
NTLM relay attacks
The NTLM relay attack is a type of manipulator-in-the-middle attack where a malicious actor intercepts and forwards authentication requests and their valid responses to gain access to AD resources illegitimately. Unlike pass-the-hash attacks, NTLM relay attacks do not require the attackers to crack passwords or hashes—but to simply relay the intercepted information.
How to detect NTLM relay attacks
Authentication requests from suspicious devices or IP addresses followed by abnormal service activities suggest possible NTLM relay attacks.
How to protect against NTLM-authentication-based attacks
Minimize NTLM usage and instead use Kerberos authentication wherever possible to combat NTLM-based attacks. In cases where NTLM authentication cannot be avoided, make sure to audit the activities while also profiling user behavior patterns to easily identify anomalies.
Kerberos-authentication-based attacks
Kerberos replaced NTLM as the default authentication protocol in Windows. Despite being more secure than NTLM, Kerberos authentication has its own vulnerability that attackers exploit to carry out Kerberos-based attacks such as Kerberoasting, Silver Ticket, and Golden Ticket attacks.
Kerberoasting attacks
Kerberoasting is a common cyberattack targeting service accounts in AD. It exploits an inherent weakness in Kerberos' ticket-based authentication, allowing attackers to request service tickets that contain an account's encrypted password hash. When extracted and cracked offline, these hashes give attackers control of service accounts, potentially enabling privilege escalation and broader network compromise.
How to detect Kerberoasting attacks
Flag Kerberoasting attempts by constantly monitoring for event ID 4769, which corresponds to Kerberos authentication events. If you find 0X17 next to the Ticket Encryption Type field in the event details, it could signal a possible Kerberoasting attack.
Silver Ticket attacks
In a Silver Ticket attack, hackers use the NTLM hash of a compromised service account to forge Kerberos service tickets. These forged tickets (aka Silver Tickets) allow attackers to access specific services without interacting with the domain controller (DC), making the attack harder to detect. Its stealthy nature has made the Silver Ticket attack a preferred method for attackers wanting to move laterally across AD without being noticed.
How to detect Silver Ticket attacks
Correlate service account activities with Kerberos logs and identify discrepancies that could point to possible Silver Ticket attacks.
Golden Ticket attacks
The Golden Ticket attack also exploits Kerberos authentication by compromising the special krbtgt account responsible for issuing and validating Kerberos tickets. Obtaining its hash allows attackers to create forged Kerberos tickets (aka Golden Tickets) to gain unrestricted access to the domain. Unlike Silver Tickets, which target specific services, Golden Tickets allow attackers to bypass normal authentication entirely, impersonate any user (including administrators), and maintain long-term control over the network. What makes this attack especially dangerous is its persistence as its effects remain even after all user passwords are reset.
How to detect Golden Ticket attacks
Monitor all Kerberos activities and investigate tickets with unusually long lifespans to detect potential Golden Ticket attacks.
How to protect against Kerberos-authentication-based attacks
Use strong, complex passwords (containing more than 20 characters) for service accounts and regularly update them to minimize risks. Reset the krbtgt account's password twice to invalidate forged Kerberos tickets. Enable Kerberos logging (for event ID 4769) and continuously monitor Kerberos events to detect anomalies.
Replication-based attacks
Replication-based attacks exploit AD's replication process, which is critical for DCs to sync directory data and changes between them. By targeting this core mechanism, attackers can extract sensitive information or introduce malicious changes that are difficult to detect. Two common replication-based attacks are DCSync and DCShadow attacks.
DCSync attacks
In a DCSync attack, attackers mimic a DC and make legitimate replication requests to retrieve sensitive AD data such as the password hashes of high-privilege accounts. By obtaining the krbtgt hash or other admin credentials, they can escalate privileges further or even forge Golden Tickets.
How to detect DCSync attacks
Monitor for event IDs 4928 and 4929 to identify unusual replication activities such as replication requests from non-DC machines.
DCShadow attacks
In a DCShadow attack, hackers register a rogue server as a DC and use replication to push malicious changes into the AD domain. Since the changes are introduced through replication, a normal AD process, traditional detection strategies fail to spot these attacks. If successful, attackers can establish long-term control by erasing traces of their activities.
How to detect DCShadow attacks
Flag unauthorized changes to critical objects by auditing event IDs 4672 and 5136. Look for suspicious updates to the AD replication topology and unapproved DC registrations.
How to protect against replication-based attacks
Monitor all AD replication activities and limit replication permissions to essential accounts only to protect against replication-based attacks.
Ransomware attacks
Ransomware attacks hold an organization’s sensitive data hostage by encrypting critical files and demanding a ransom for their release. Attackers often start with brute-force, phishing, or social engineering tactics to inject malware into an AD user's system. Once inside, the malware spreads through the network, encrypting business-critical files and folders and rendering them unreadable. At this stage, the attackers demand a ransom and often threaten to expose sensitive information if their demands are not met.
How to detect ransomware attacks
Look for red flags like a surge in file renaming and deletion actions or unusual process activities, which are indicators of an active ransomware attack.
How to protect against ransomware attacks
Continuously audit AD and file server activities to monitor all changes made to critical AD objects and sensitive files. Enforce strong password policies, educate users about email security, and provide training on recognizing social engineering tactics.
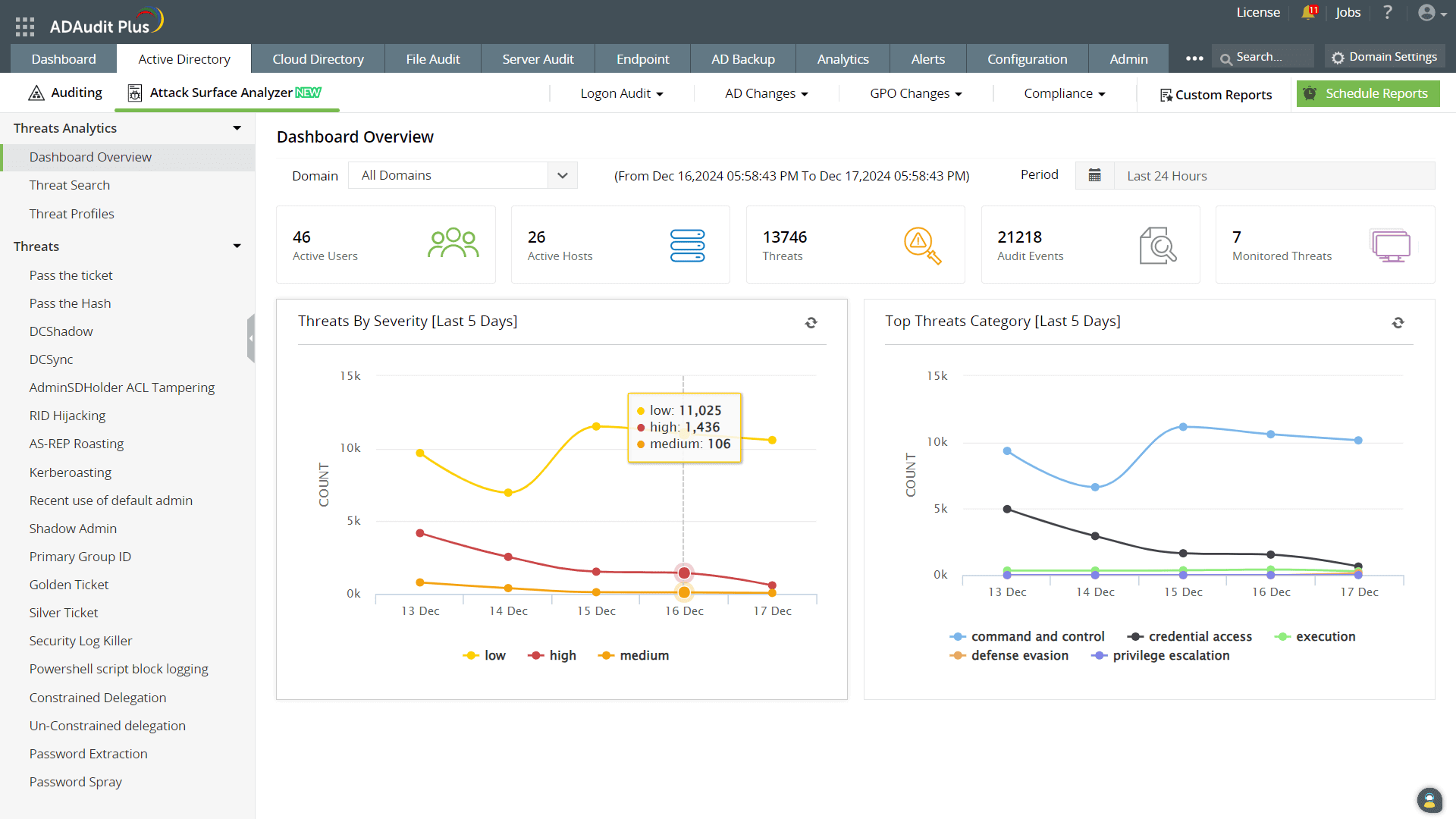
How ADAudit Plus can help you detect and mitigate AD exploits
ADAudit Plus' Attack Surface Analyzer delivers crucial insights into potential threats and misconfigurations across your on-premises, cloud, and hybrid AD environments. Besides intuitive threat dashboards, the Attack Surface Analyzer offers exclusive reports for over 25 common AD attacks, including brute-force, pass-the-hash, Kerberoasting, and DCSync attacks, to help you stay on guard and ensure complete AD security.
Start protecting your on-premises and cloud AD resources with ADAudit Plus
Detect over 25 different AD attacks and identify potential misconfigurations within your Azure, GCP, and AWS cloud environments with the Attack Surface Analyzer.
See the Attack Surface Analyzer in actionWe're thrilled to be recognized as a Gartner Peer Insights Customers' Choice for Security Incident & Event Management (SIEM) for the fourth year in a row.
On this page
- Password-based attacks
- NTLM-authentication-based attacks
- Kerberos-authentication-based attacks
- Replication-based attacks
- Ransomware attacks