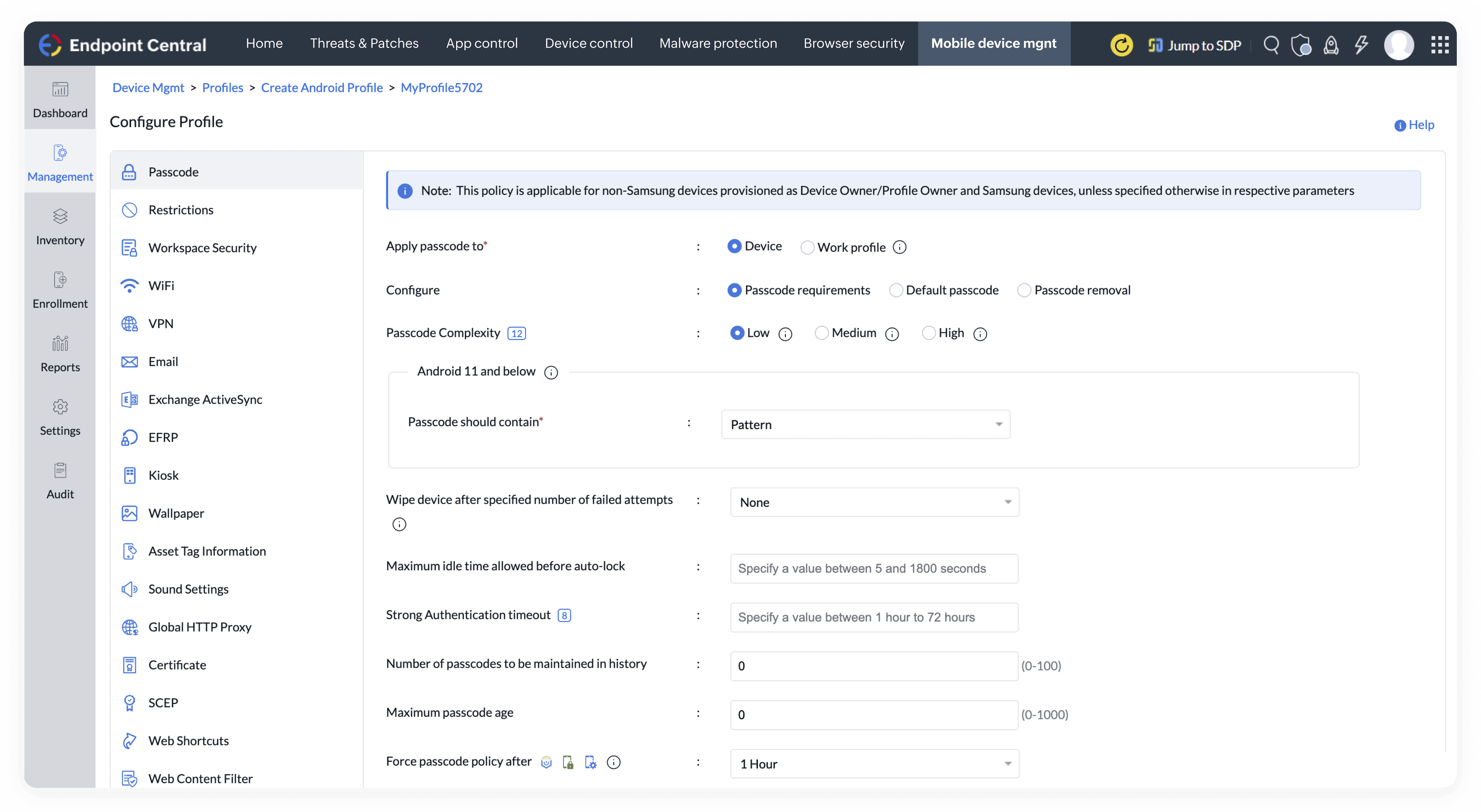
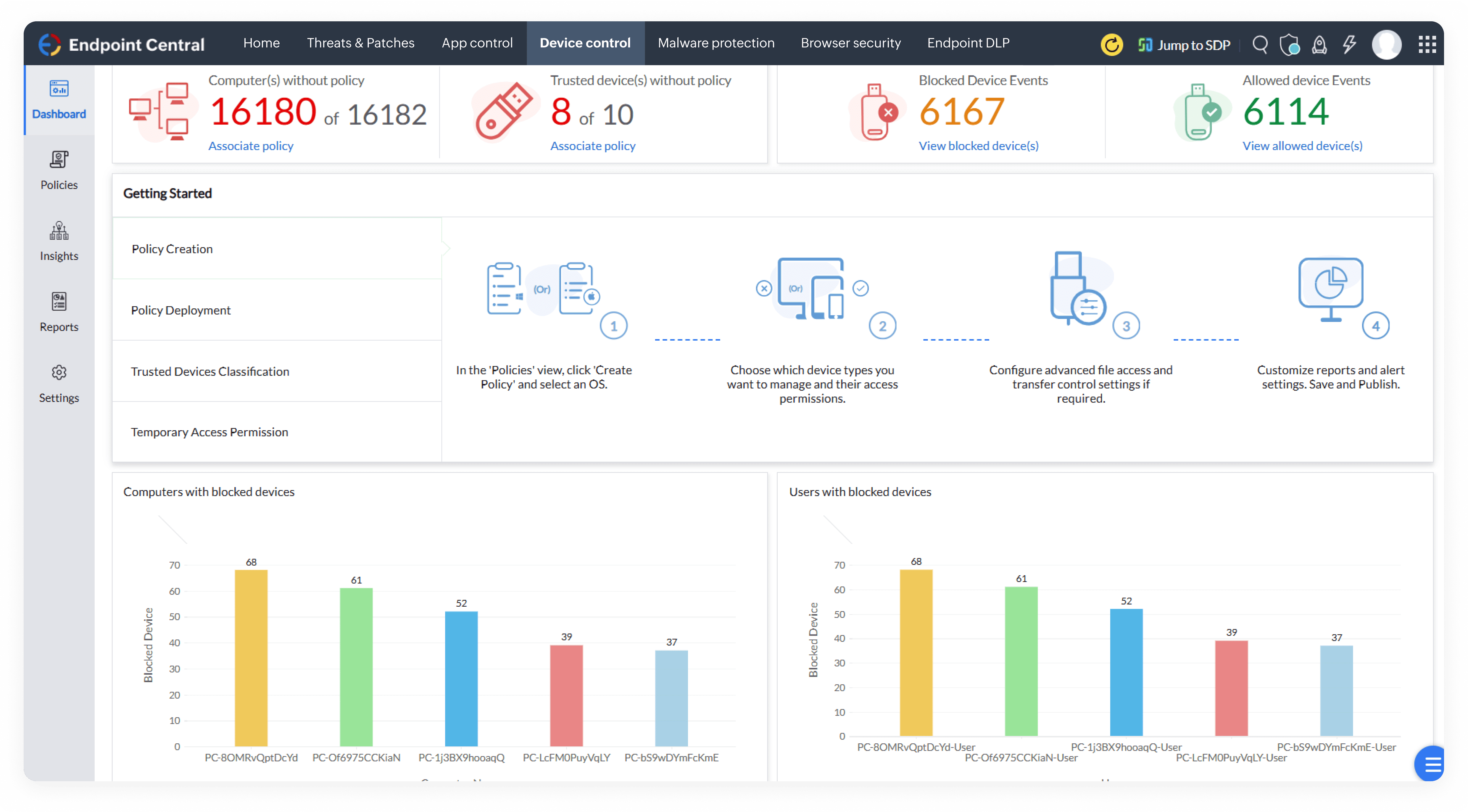
All-in-One Endpoint Security Solution for Cyber Threat Protection
Endpoint security solution
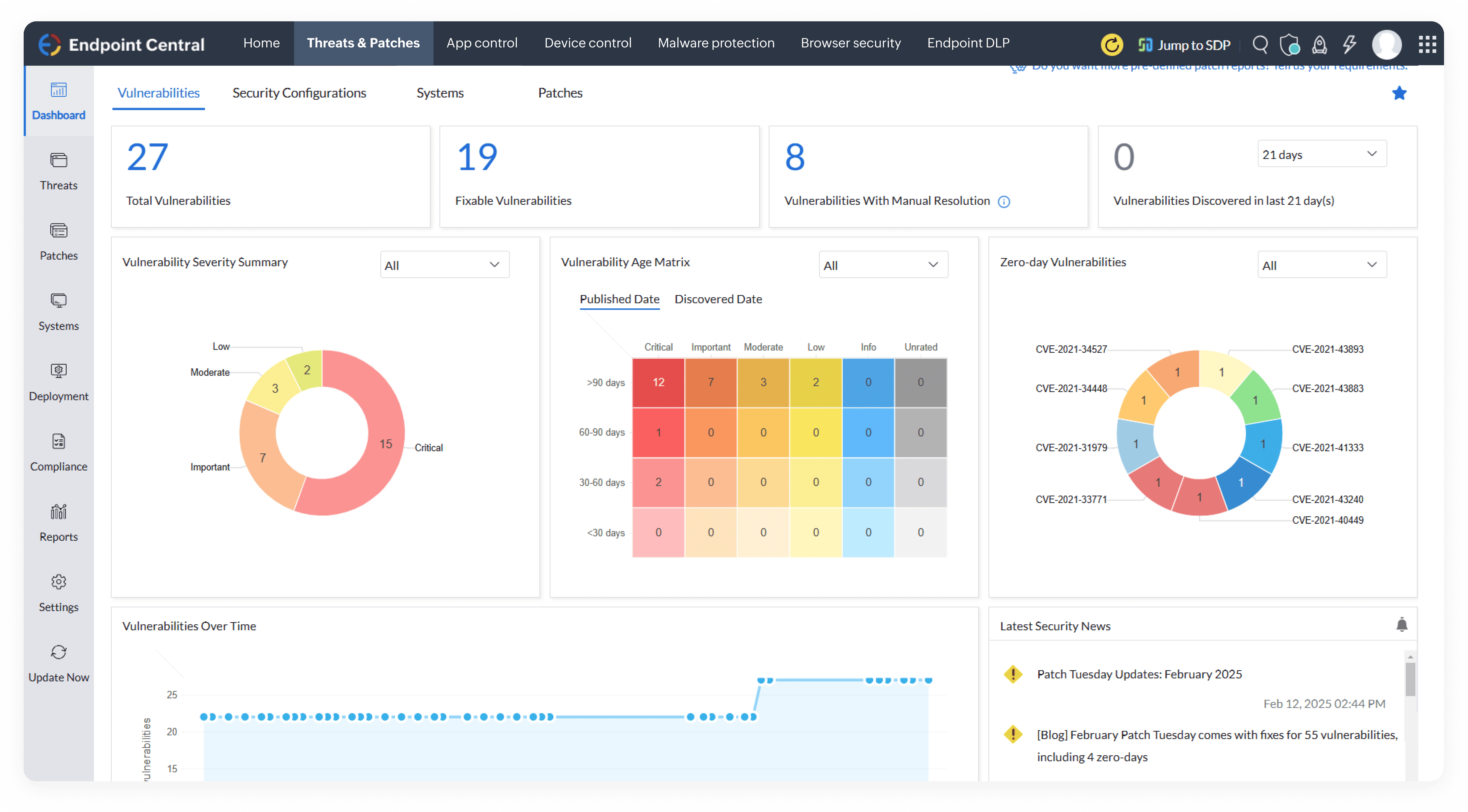
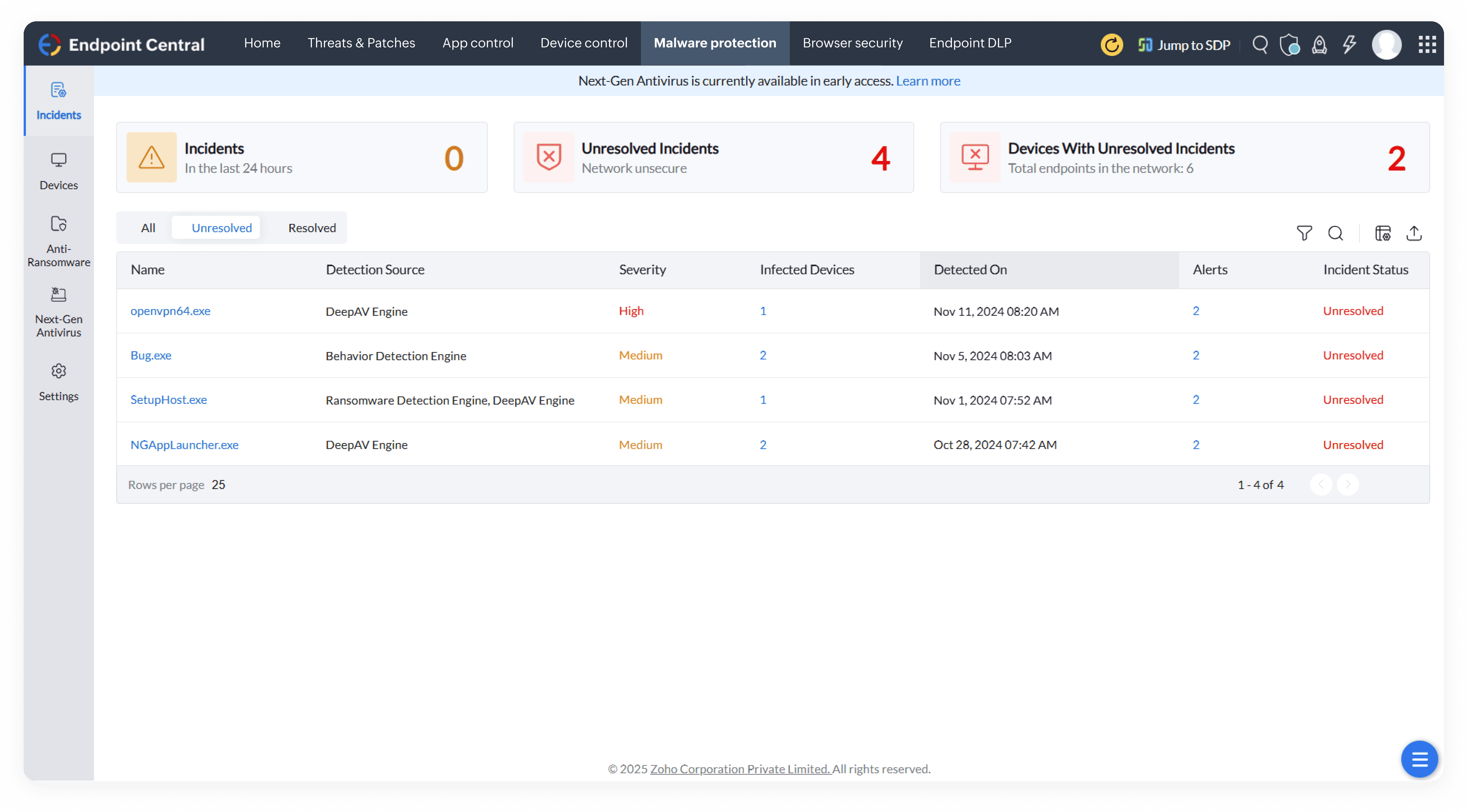
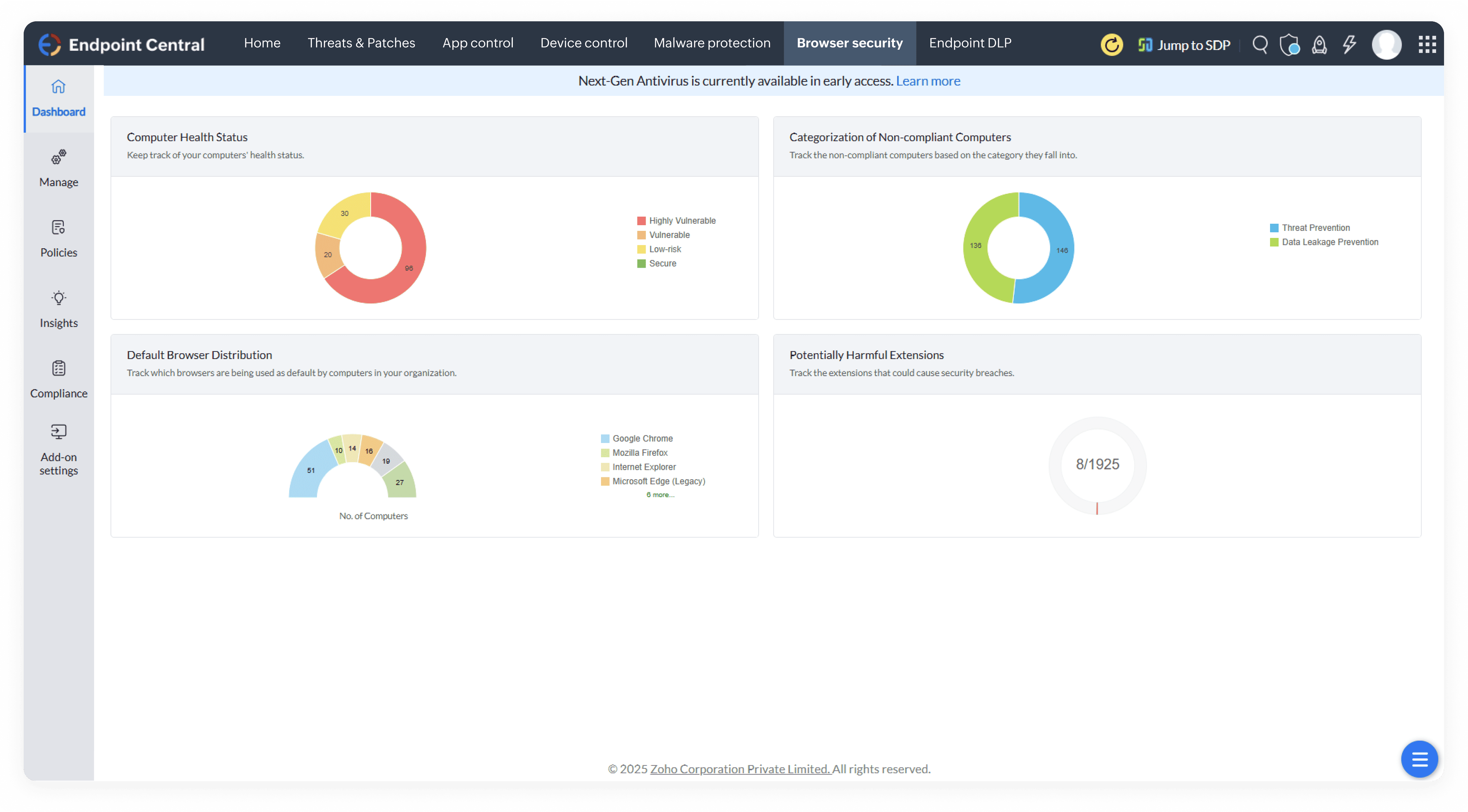
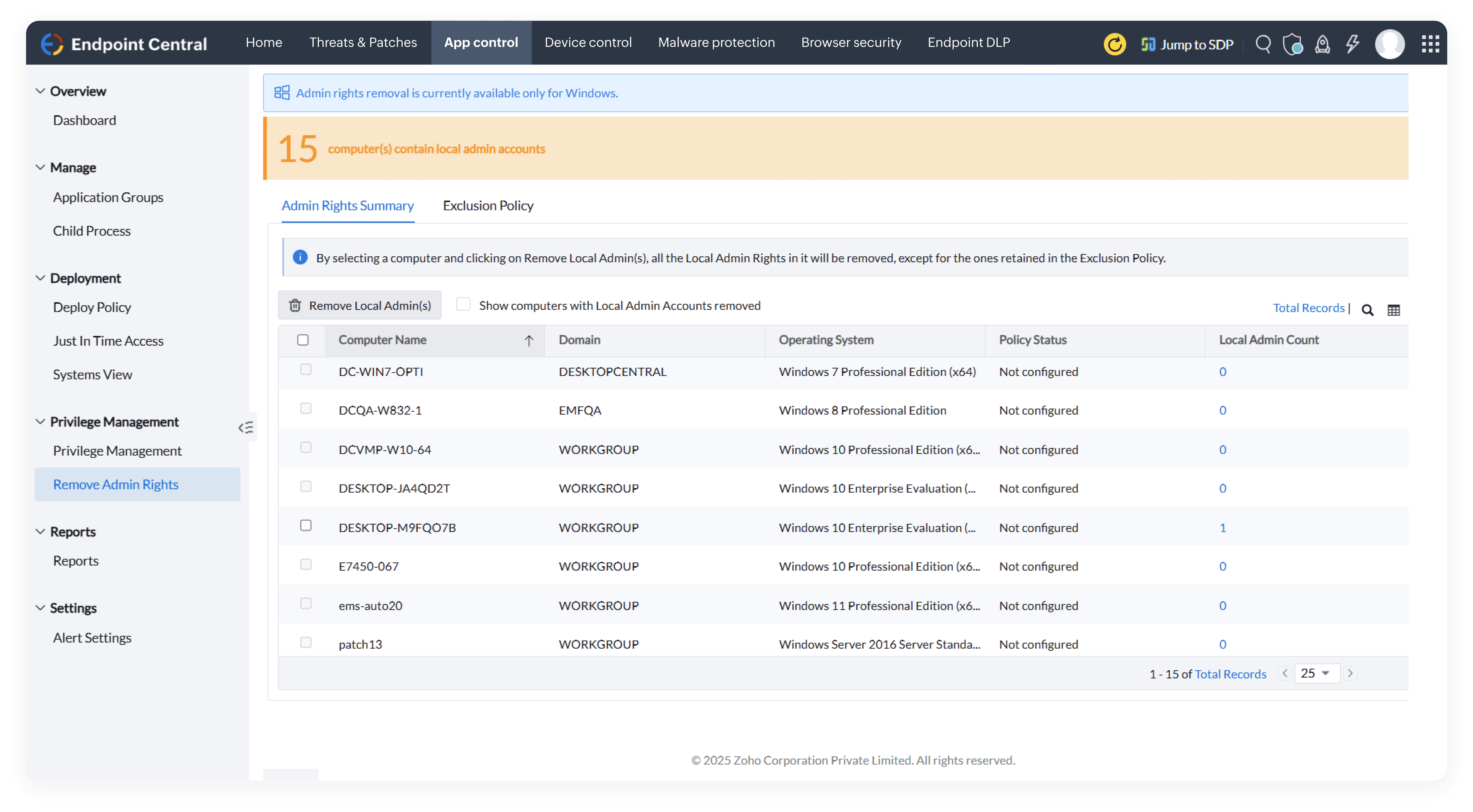
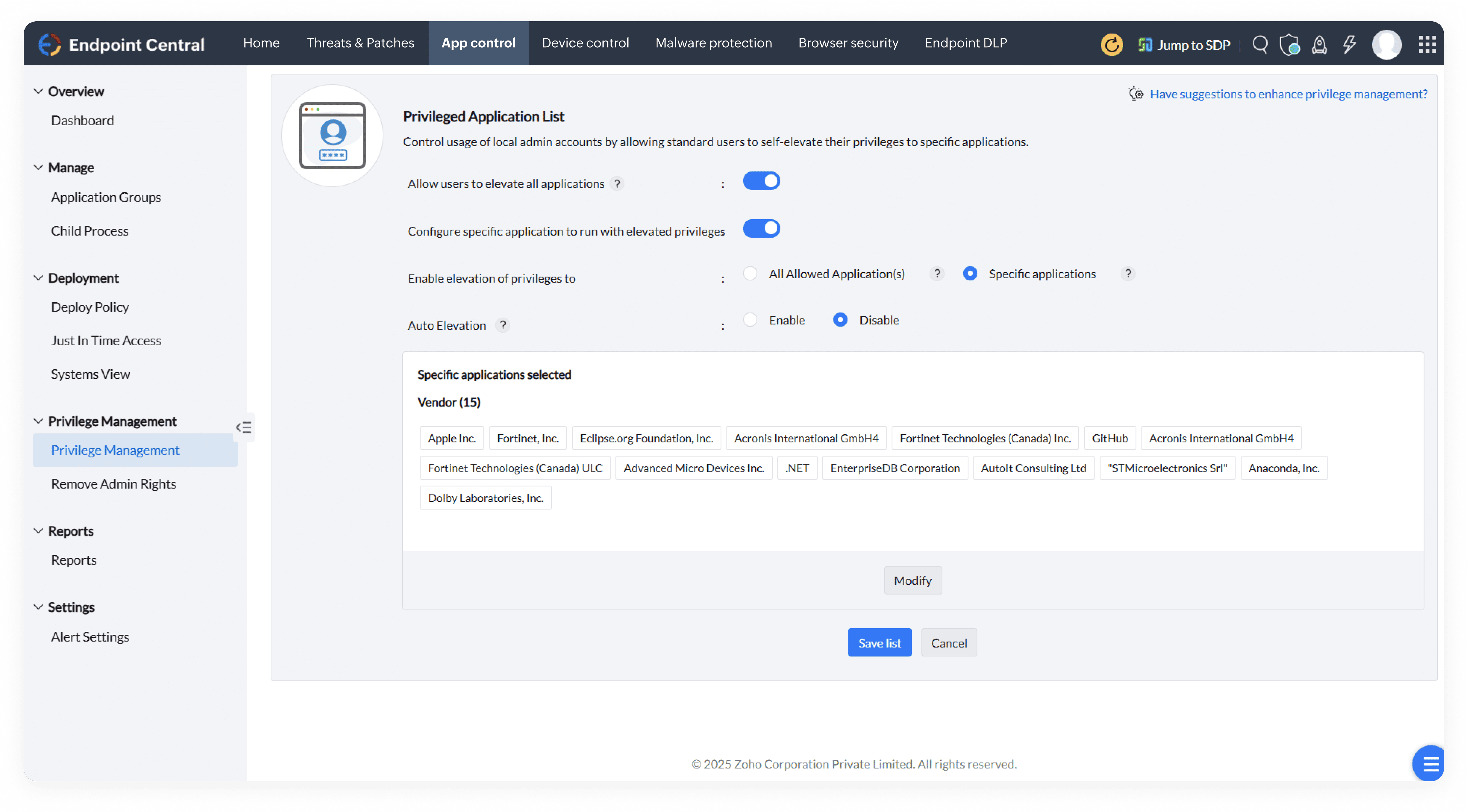
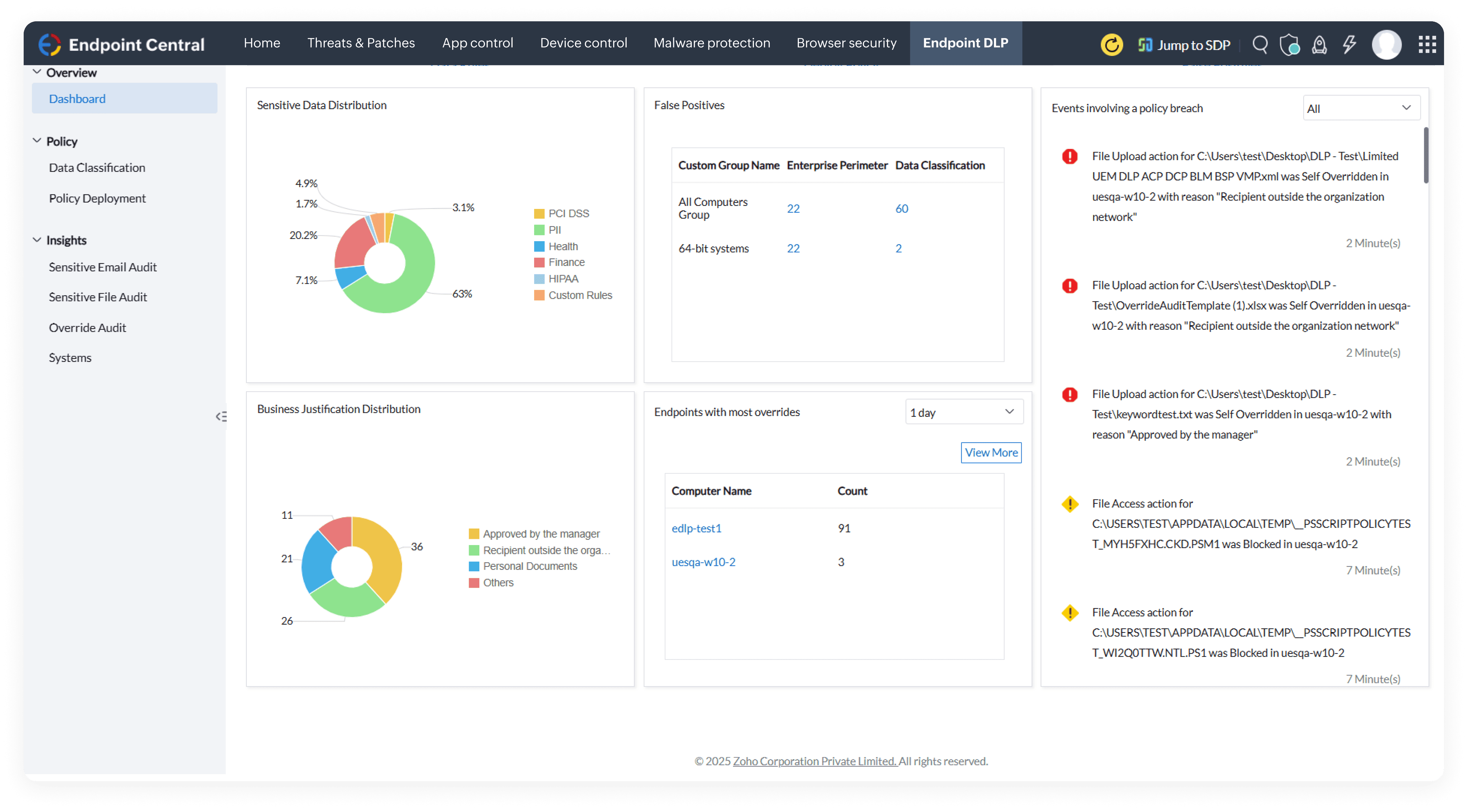
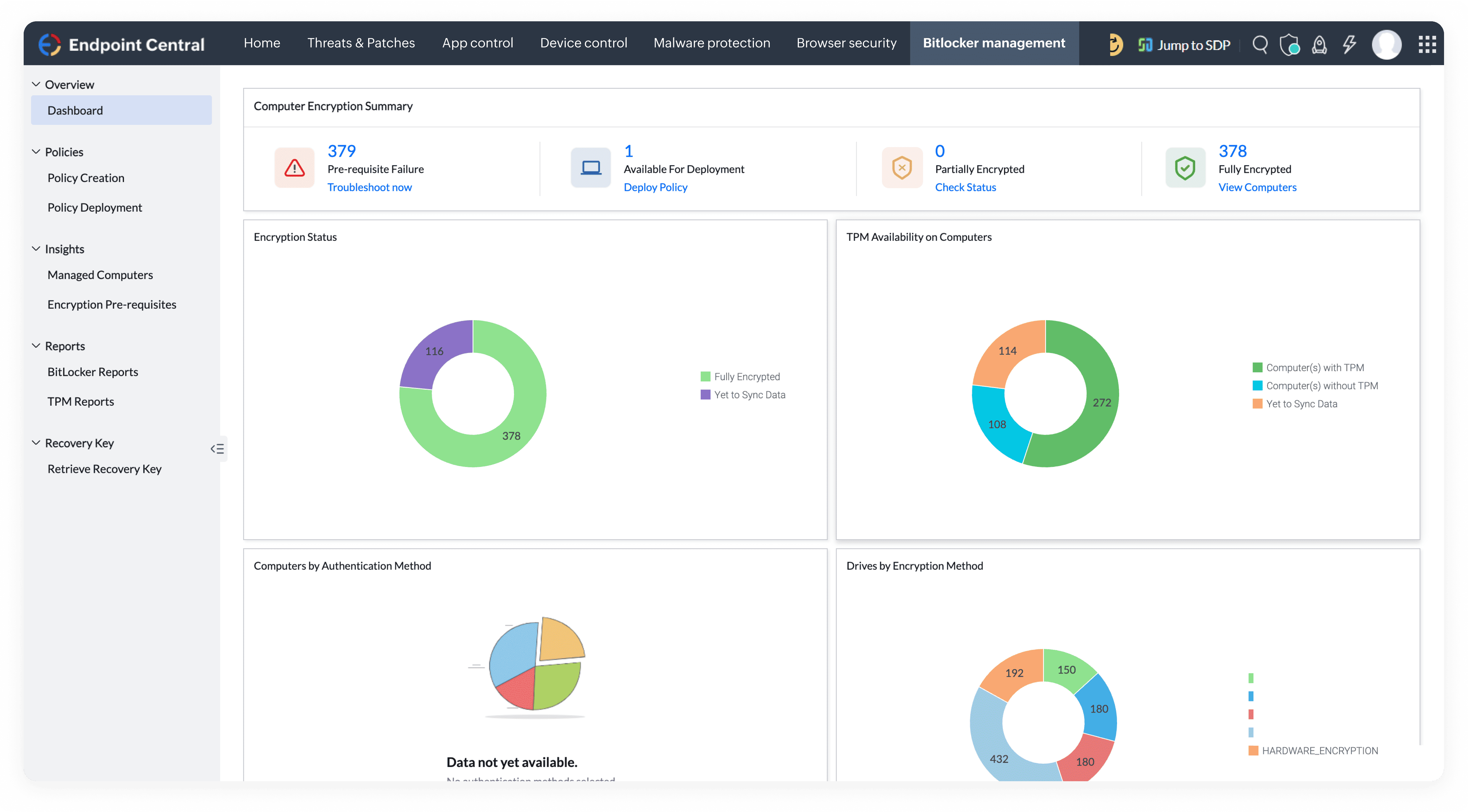
Discover a robust endpoint security solution built for modern enterprises. Prevent cyberattacks, secure remote endpoints, and ensure compliance with a single, unified platform.