Firewall Rule Suggestion - Rule Optimization Reports
The Rule Suggestion sub-section in Firewall Analyzer Rule Management > Policy Optimization sub-tab lists all the overly permissive firewall rules.
Refer the Rule Management Report Support page, for the list of firewall devices.
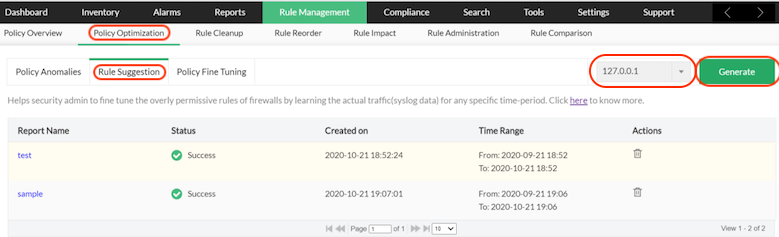
The rule suggestion reports are firewall device specific, so select a particular device. Click Generate button.
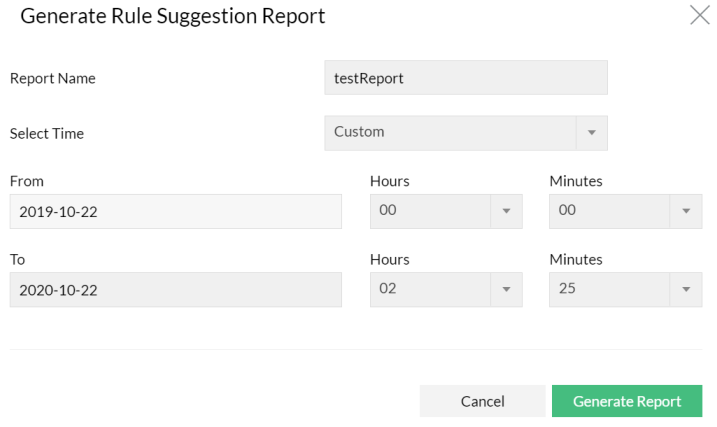
- Enter the Report Name.
- The options to select the time is given in Select Time drop down list. The options are: Today, Last 24 Hours, Last 7 Days, Last 30 Days, and Custom. Custom option details are: From: Date, Hours, Minutes and To: Date, Hours, Minutes. Select the time period.
- Click Generate Report button.
The report is generated and displayed in the report table.
In the Rule Suggestions sub-section, the table displays the following details of Overly Permissive Rules.
- Overly Permissive Rule Name
- Source
- Destionation
- Services
Overly Permissive Rule Name - Name of the overly permissive rule. Overly permissive rules typically contain large network object ranges or 'ANY' in the rule statements. In Policy fine tuning 'ANY' object rule statements are taken to suggest for replacement.
Source - Existing source objects in the rule to be fine tuned.
Destionation - Existing destination objects in the rule to be fine tuned.
Services - Existing service objects in the rule to be fine tuned.
You can export the suggestion report in to PDF, XLS, and CSV formats with respective icons. You can send the report by Email.
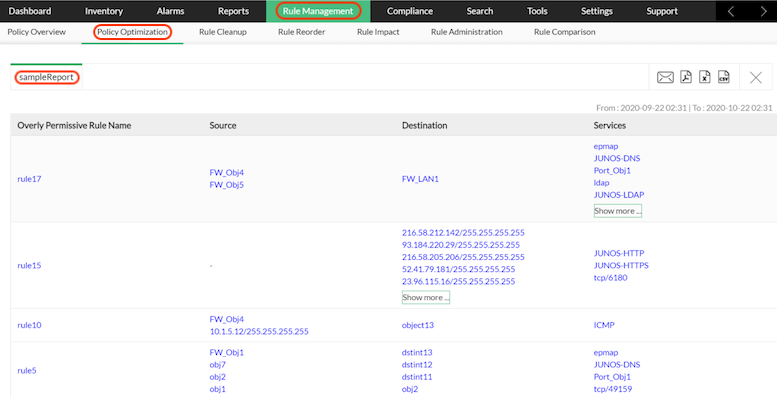
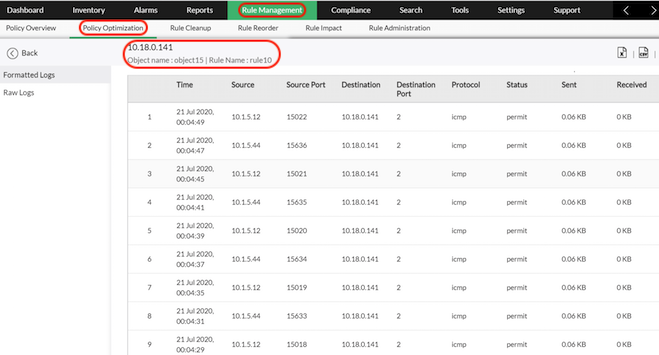
Click on the Source object to view the details of the object.
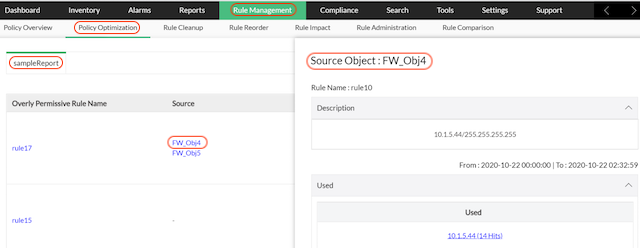
Click on the specific Used object. You can view the log report in which the used object is available.
Thank you for your feedback!