Spot potential ransomware intrusions by tracking sudden spikes in file rename and permission change events.
Shut down infected devices to contain the ransomware spread in your network quickly.
Generate an audit trail to preserve legal evidence and to perform post-incident analysis.
Detect a ransomware attack at its onset. Audit file servers for sudden spikes in file rename and delete events, which most commonly prelude a ransomware attack.
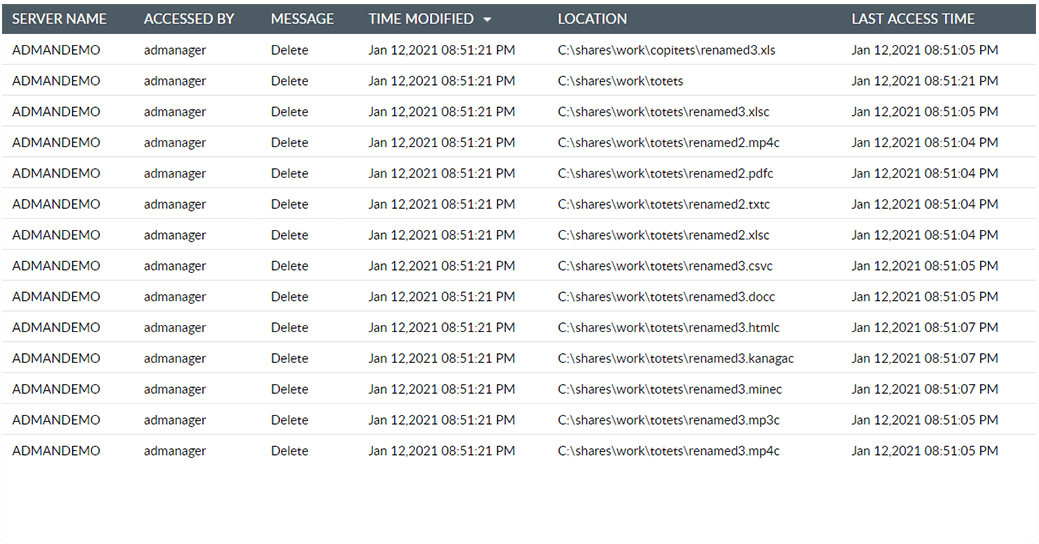
Prioritize ransomware detection by setting up real-time alerts and threat responses. Get notified as soon as suspicious file changes take place.
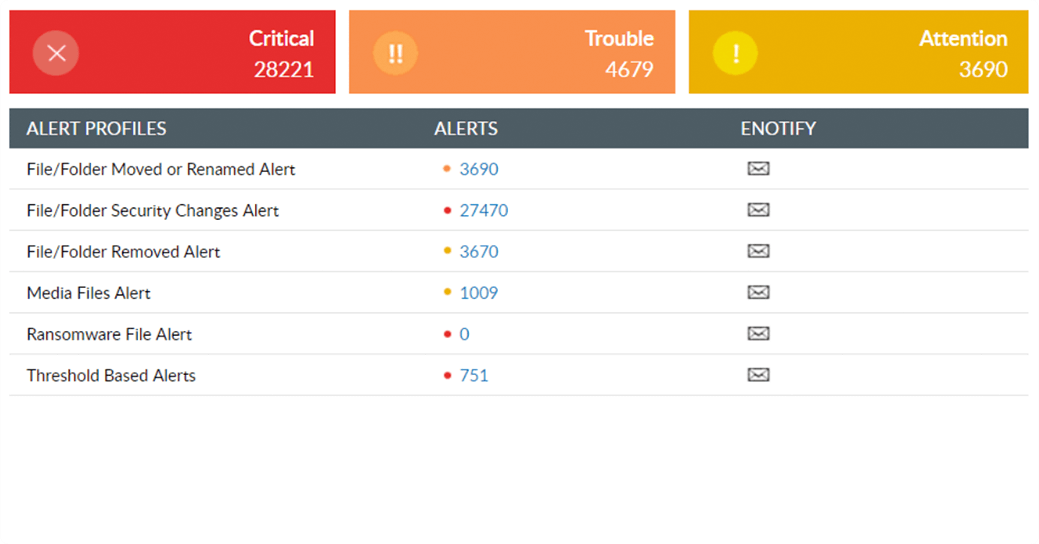
Quickly halt the ransomware infection from snowballing into a massive data breach. Shut down infected devices to isolate them and mitigate the damage.
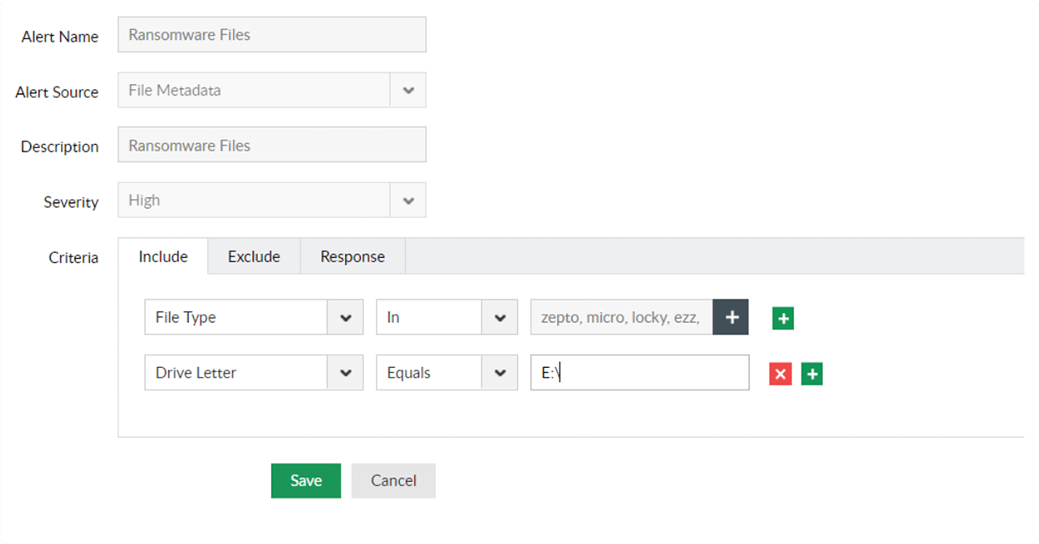



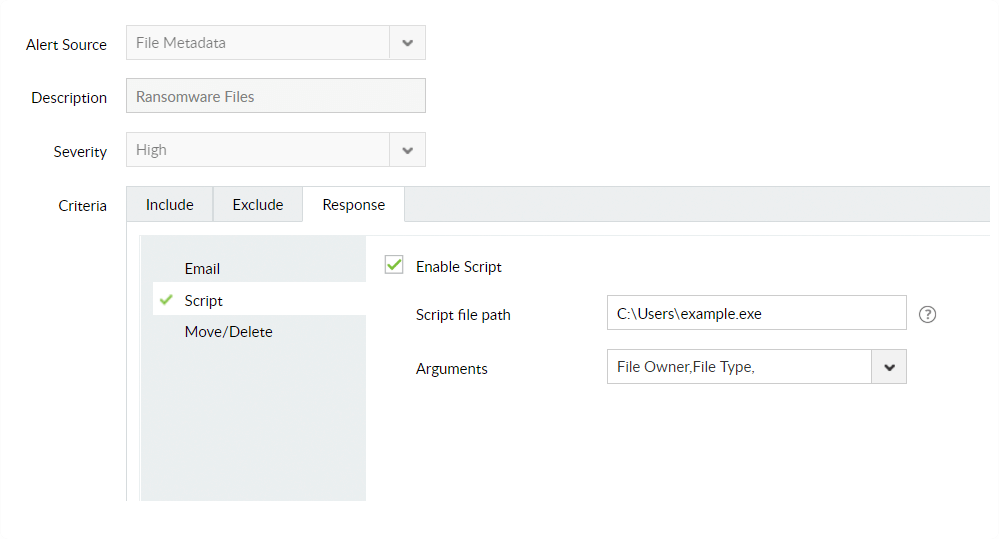
Minimize the impact of a ransomware attack by using an automated, predefined threat response mechanism. Disconnect the session of compromised user accounts to stop further spread of ransomware.

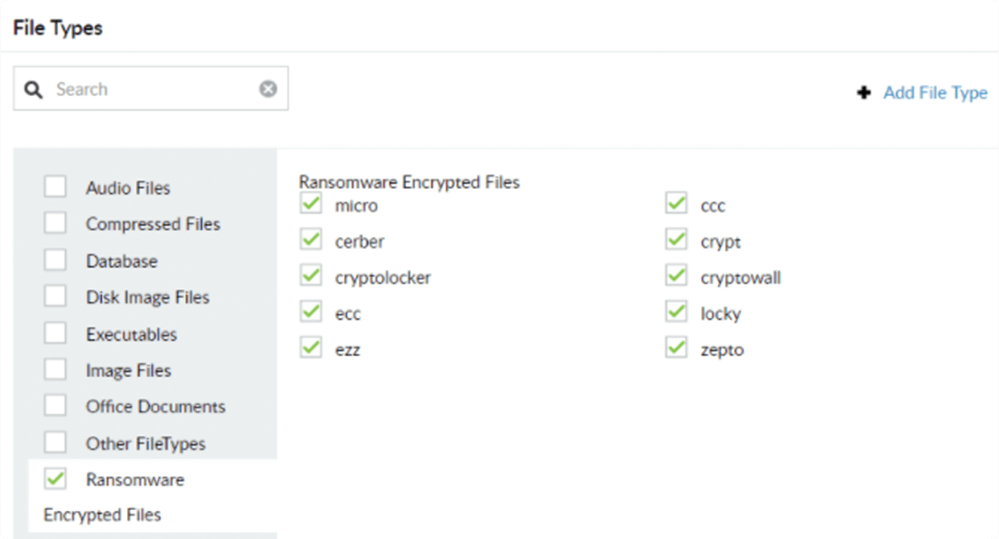
Spot attacks by known ransomware variants like Petya, Locky, etc. with our built-in threat library. Secure your data by deleting these ransomware encrypted files for good.

Generate audit trails to facilitate forensic investigation and to preserve legal evidence. Retain and analyze audit data to anticipate and block future threats.

Download the datasheet to learn more about DataSecurity Plus, including its full list of features.
One of our solution experts will get in touch with you shortly.