Identity360 ensures that the right users consistently have the right access across resources
31% of former employees still have access to company SaaS applications and resources.*
52% of organizations lack visibility into what resources their users can access.†
37% of organizations experienced a data breach as a result of improper privileged access management.‡
Identity360 simplifies access management across platforms for admins and end users.
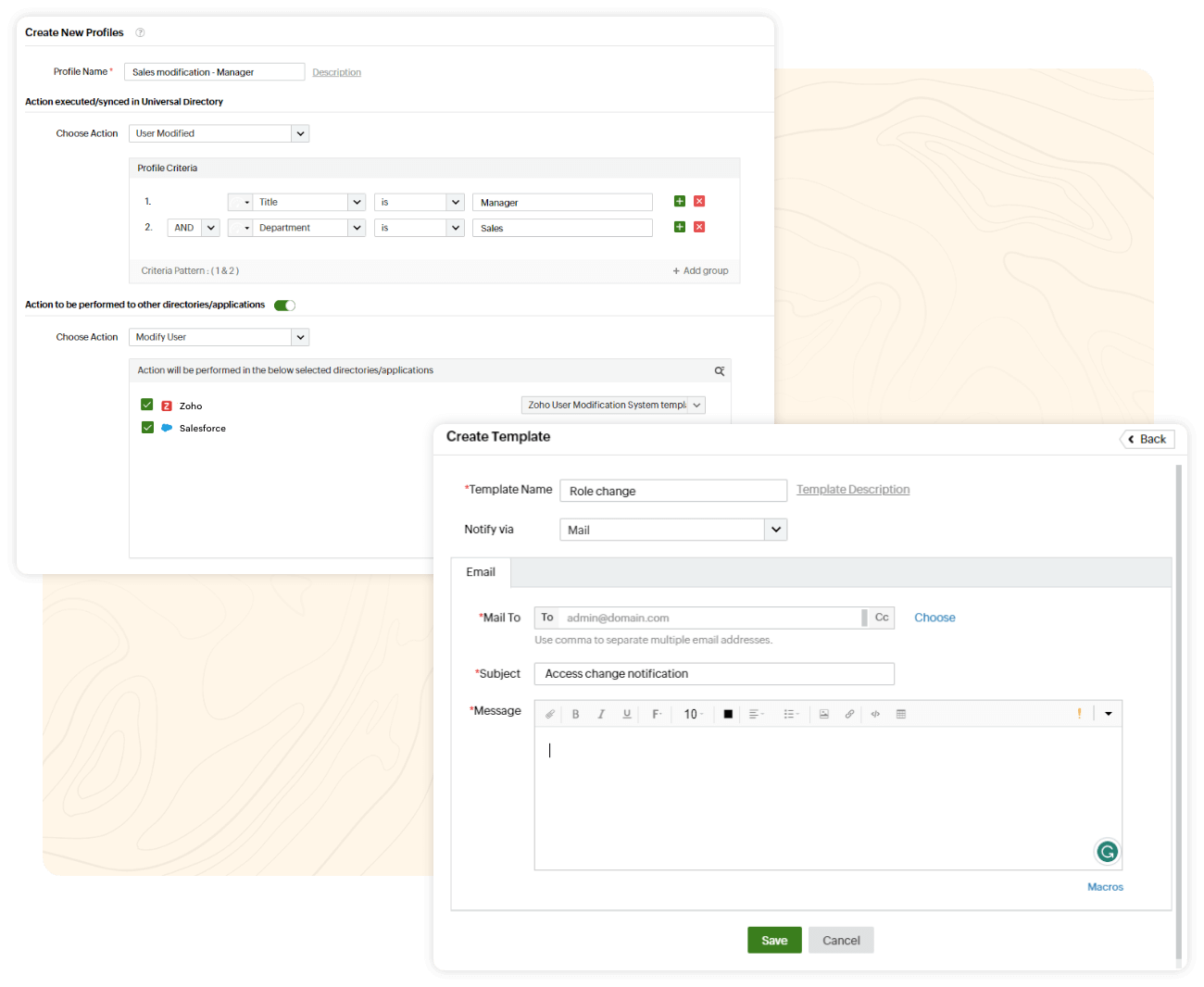
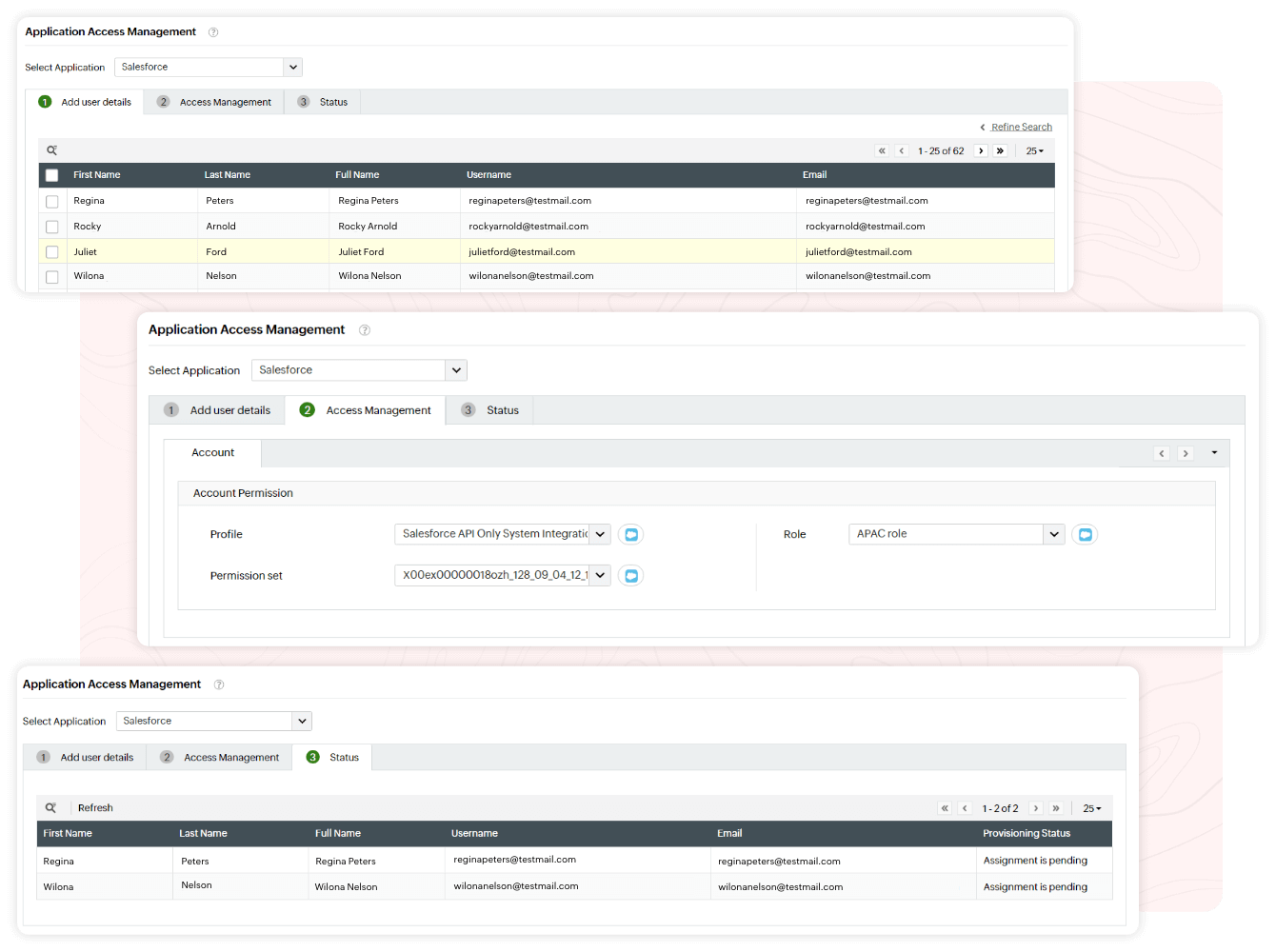
Here's how access to enterprise resources is managed using Identity360, throughout the organizational life cycle of a user:
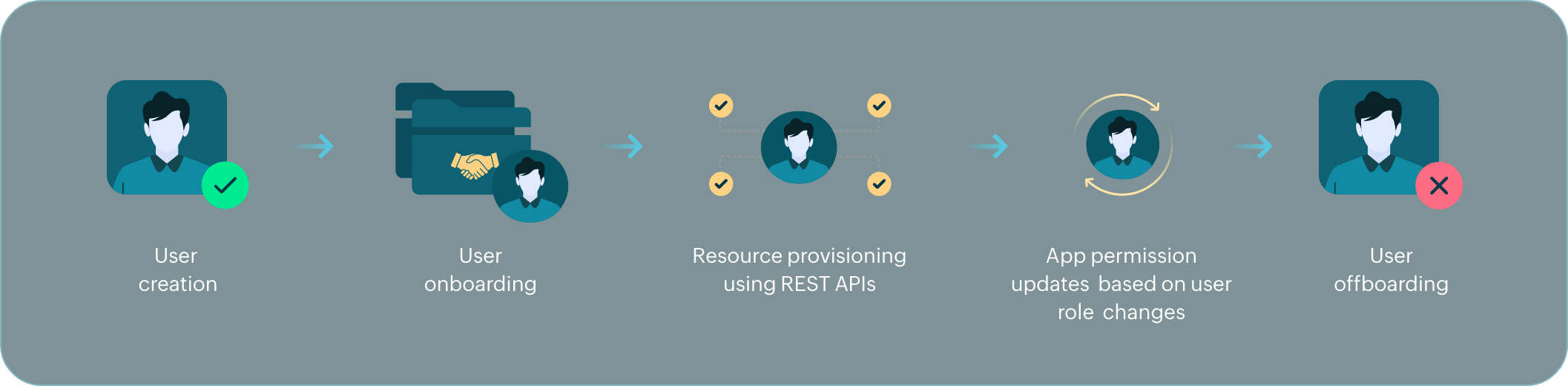
When a user joins the organization, they are onboarded using preconfigured orchestration templates and API-based provisioning.
Based on the configured template, accounts are created for the user in other linked directories and access is granted to the enterprise applications they need.
The user is given restricted access to each application by configuring necessary application roles and permissions.
As the user's title and responsibilities in the organization change over time, attribute sync and communication APIs are used to adjust resource access for them accordingly.
In due time, when the user leaves the organization, the configured conditions will promptly remove them from all linked directories, and all application access will be revoked.
Configure granular permissions and roles for end-user resource access that can be automated as users move across your organization's hierarchy.
Simplify access management by assigning access roles and permissions for end users in bulk.
Protect your resources from insider and outsider threats by granting the right access privileges to the right users.
Deploying an effective access management system provides your users with the right resources and protects your business against internal and external threats. Cloud-based identity and access management using Identity360 enables IT administrators to effortlessly manage user access permissions across enterprise applications in bulk. It also provides granular access settings, like selecting necessary app roles and permissions for your users as they journey with you in your business.
Access management or access control means managing the roles and permissions that users need to get the right amount of access to the right enterprise resources.
Access management is inevitable for all organizations since it streamlines end-user resource access privileges. Without an access management system, your users may end up having more or less resource access privileges than what they need to get their job done.
Allowing unrestricted end-user access to all your corporate resources can expose your business to potential threats, originating from internal and external sources. Managing and monitoring the appropriate resource access privileges granted to your users tightens organizational security while enhancing employee productivity.
You can implement bulk end-user resource access management easily with Identity360. It provides a user-friendly console with granular access control functionalities. You can configure the necessary roles, permissions, and license details for users in bulk across multiple applications. You can also automate the settings using templates so that users always have the right access. Identity360 provides enhanced access tracking capabilities for IT administrators via consolidated tables that display users' access assignment status for each enterprise resource.
To learn more about Identity360's access management capabilities, please schedule a personalized web demo with our solution experts.
Unlocking efficiency with Universal Directory
Leverage identity storage for your organization with Universal Directory.
Learn moreRobust MFA techniques to secure your organizational identities
Identity360 provides comprehensive MFA capabilities to secure your enterprise against threats.
Learn moreSecure, seamless SSO for your organization
Identity360 equips and empowers your organization with modern SSO capabilities.
Learn moreEnhance workforce productivity through effective identity management
Identity360 provides end-to-end identity life cycle management capabilities.
Learn moreEmpower your IT admins to focus on tackling critical issues
Identity360 assists you in achieving delegation of routine management tasks with ease.
Learn moreGain a comprehensive view of your organization's security and identity analytics through reports
Access valuable insights with detailed identity analytics reports.
Learn moreSource: *DoControl Article: SaaS Security Threat Landscape Report, †StackZoneArticle: Maximum Security - Achieving The Cloud Security Milestone, ‡Identity Defined Security AllianceArticle: Trends in Securing Digital Identities