Encryption is the process of securing data by converting it into a format that can only be understood by a specific audience. During this process, plain text is converted into non-readable ciphertext using specialized encryption algorithms. Encryption keys are used to encode and decode this text. These keys are unique and made available only to authorized parties, preventing loss of data due to data breaches.
Encryption of data can be based on two common data states:
Encryption prevents data breaches when the data is at rest and in transit. In transit, encryption ensures secure transfer of sensitive information through enforced TLS, preventing man-in-the-middle attacks. In case of a lost or stolen device, if the stored data is encrypted, it is inaccessible even in the hands of attackers.
Most data transmission happens through emails and chats. Encryption ensures that the transferred data can only be read by the receiver and sender. This prevents cybercriminals, internet service providers, etc. from gaining access to sensitive data.
Websites that are issued an SSL certificate can be trusted with exchanging sensitive data.
Regulations such as HIPAA, PCI DSS, and the GDPR require companies that handle customer information to keep that data encrypted.
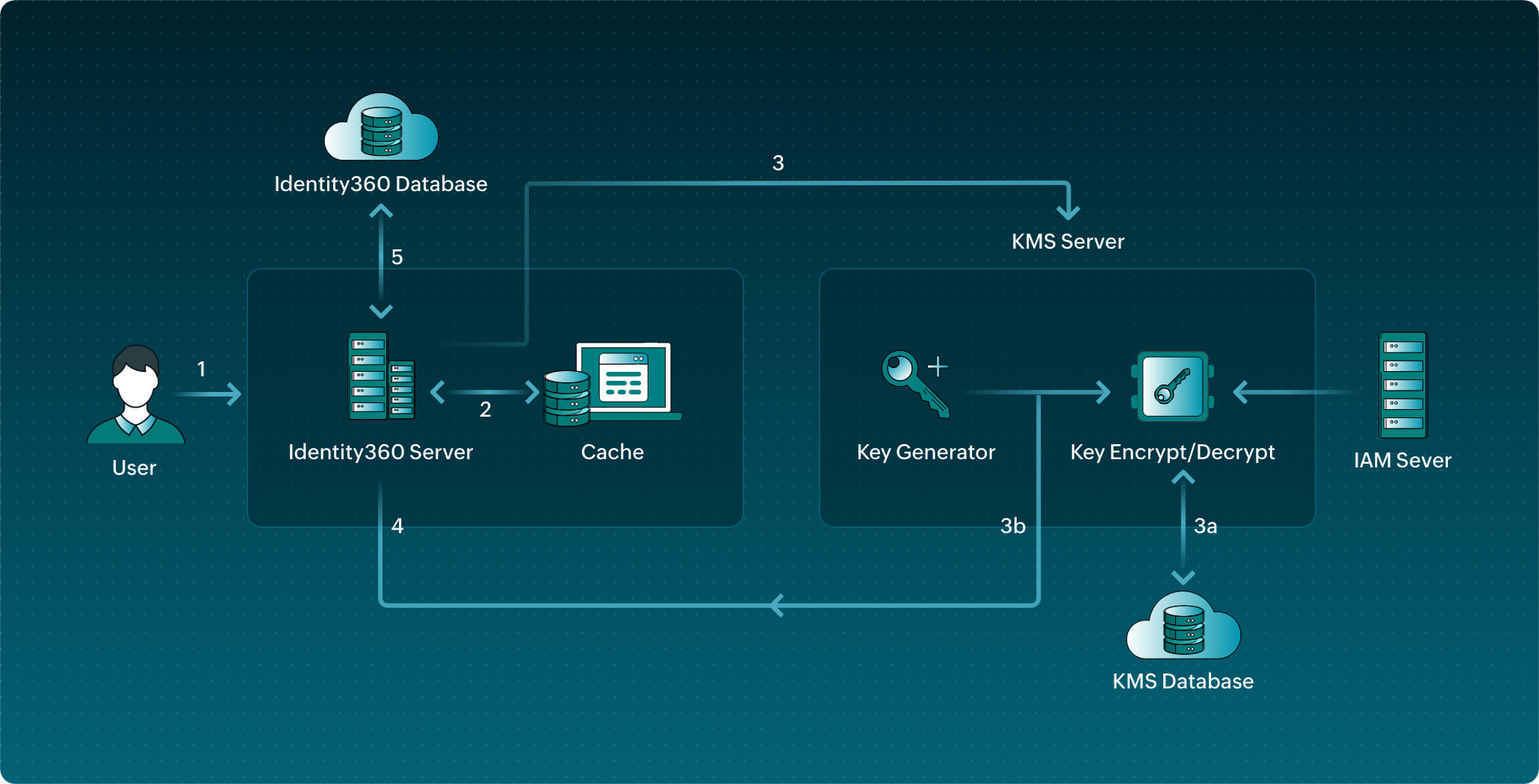
Data such as directory tokens and directory properties are encrypted at rest in Identity360 using the AES-256 algorithm. This algorithm has a key length of 256 bits, supports the largest bit size, and is practically unbreakable by brute force based on current computing power, making it the strongest encryption standard. Identity360 encrypts data using AES’s Cipher Block Chaining mode.
Keys are the means through which you can retrieve encrypted data. The key used to convert the data from plain text to ciphertext is called the data encryption key (DEK). The DEK is further encrypted using the key encryption key (KEK), adding another layer of security.
Data in Identity360 has three layers of protection:
Since the retrieval of data goes through three levels of security, data transmission in Identity360 is considerably more secure.
The invite links sent out to users via email may contain sensitive data in the URLs. To secure this communication, any part of the URL that’s identifiable is encrypted.