Identity360 secures access to enterprise applications with MFA.
It is estimated that 96% of bulk phishing attempts are stopped by implementing an MFA solution. *
Without MFA, a data breach can cost a company up to $4.45 million on average, versus $3.26 million with MFA.†
Implementing MFA can prevent 80–90% of cyberattacks. ‡
Identity360 provides comprehensive MFA capabilities to secure your enterprise against threats.
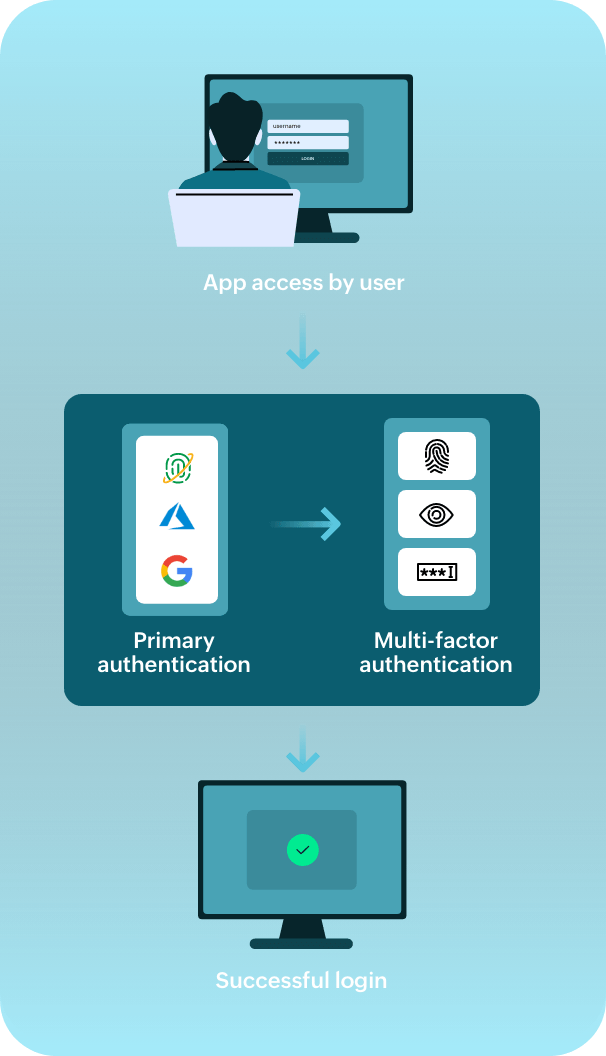
Here's how MFA works when a user tries to access Identity360 or any enterprise application.
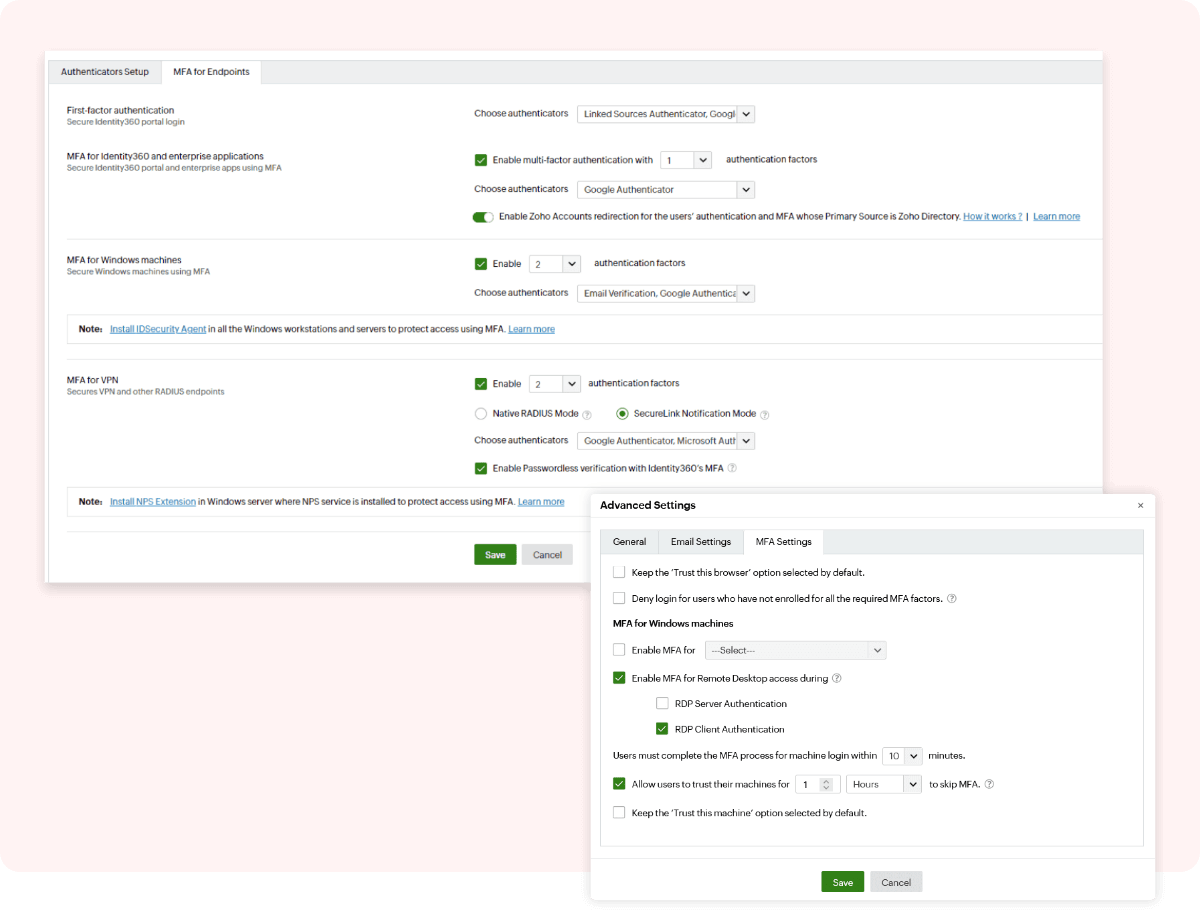
Identity360 provides MFA to secure a wide range of enterprise applications and endpoints, including machines, servers, and workstations, with strong authenticators.
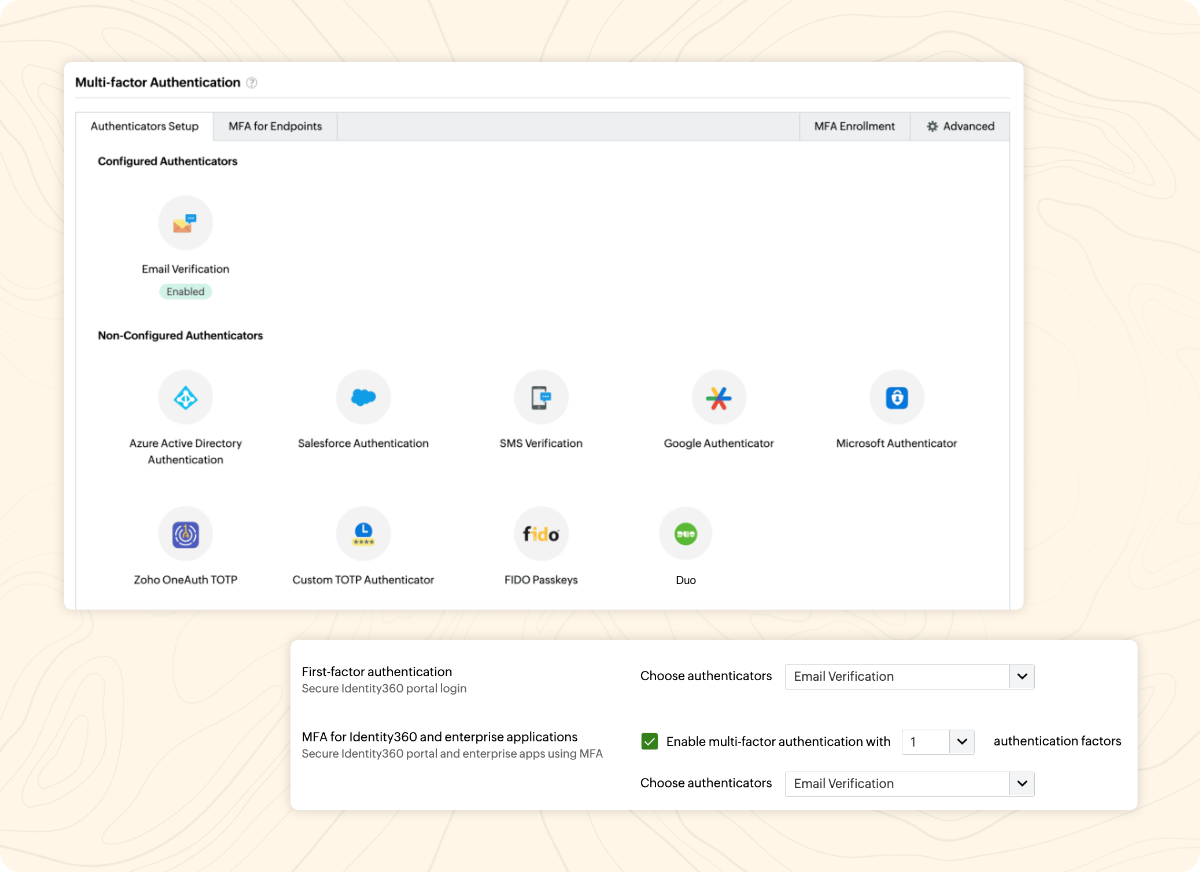
Identity360 makes MFA configuration and enrollment easy for admins and end users with a simple and easy-to-understand UI.
Identity360's MFA for endpoints and enterprise applications helps defend against various cyberattacks while providing easy resource access to employees.
Having unsecured user identities can expose your enterprise's resources to risk. MFA can thwart unauthorized access and protect your organization's sensitive data against attacks. Identity360 secures organizational identities and safeguards end user access to your enterprise's applications and endpoints with modern MFA techniques.
Multi-factor authentication (MFA) is an identity security measure where a resource, like an application, is secured using multiple authentication methods, and any user accessing the resource must authenticate themselves with those methods to gain access to it.
Single sign-on (SSO) is the process of granting users access to multiple resources after a single round of identity verification. After initial authentication, they can directly access all resources assigned to them for a stipulated time without reauthentication.
Since SSO provides one-click access to multiple resources after a single round of identity verification, it is essential that this identity verification process is completely secure. Implementing MFA secures SSO with additional authentication methods beyond usernames and passwords and defends against potential attacks.
A user may try to access a resource—either directly or through the identity provider (IdP)—using SSO. In both cases, they will have to verify their identity with multiple authenticators, which may differ in number and type based on the organization's settings. Upon successful completion of MFA, the user gains access to that particular resource and other resources assigned to them through SSO.
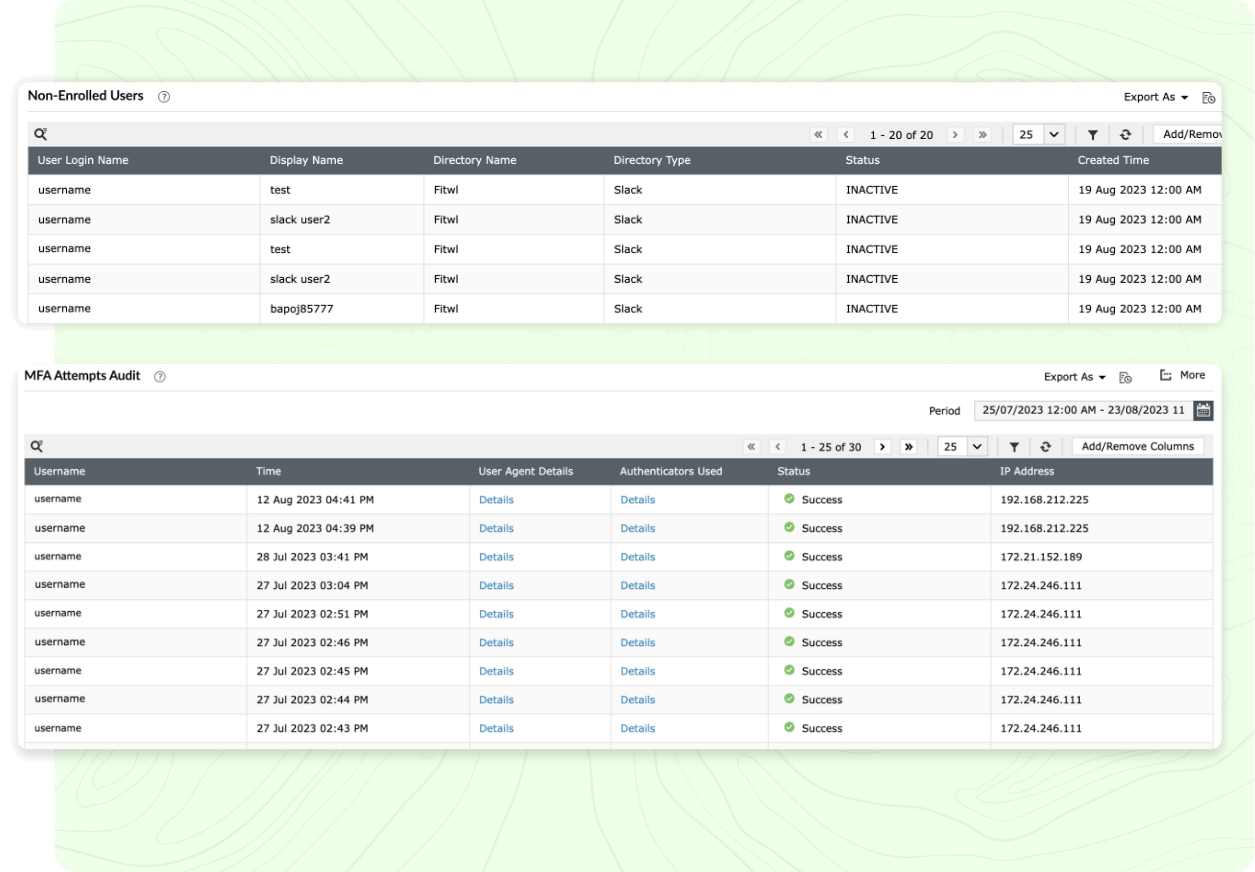
You can implement MFA using Identity360, which employs strong authenticators, such as Zoho OneAuth, Google Authenticator, and custom TOTP authenticators, to safeguard enterprise applications and endpoints. It provides fine-grained controls—like allowing browser trust for a desired limited period and usage of CAPTCHA codes during identity verification—to tailor the MFA for your organization. For primary authentication, you can choose your preferred directory, like Azure AD, Google, and Salesforce, which your users may already be a part of. With the help of MFA reports, you can track details like users' MFA enrollment status and all MFA attempts made by users along with timestamps. To learn more about Identity360's endpoint MFA, see the Endpoint MFA page.
To gain a better understanding of Identity360's MFA capability, please schedule a personalized web demo with one of our solution experts.
Unlocking efficiency with Universal Directory
Leverage identity storage for your organization with Universal Directory.
Learn moreSecure, seamless SSO for your organization
Identity360 equips and empowers your organization with modern SSO capabilities.
Learn moreEnhance workforce productivity through effective identity management
Identity360 provides end-to-end identity life cycle management capabilities.
Learn moreEmpower your IT admins to focus on tackling critical issues
Identity360 assists you in achieving delegation of routine management tasks with ease.
Learn moreCross-platform access management capabilities
Identity360 streamlines cross-platform access management for admins and end users.
Learn moreGain a comprehensive view of your organization's security and identity analytics through reports
Access valuable insights with detailed identity analytics reports.
Learn moreSource: *Google Article: Evaluating Login Challenges as a Defense Against Account Takeover, †IBMArticle: Cost of a Data Breach Report, ‡and United States National Security CouncilArticle: Press Briefing by Press Secretary Jen Psaki and Deputy National Security Advisor for Cyber and Emerging Technologies Anne Neuberger