Password Policy Enforcer
The password policy settings enhance security by defining rules for creating strong passwords. You can establish standards to prevent users from using common passwords and ensure the passwords they create adhere to the security and compliance requirements of your organization. From a security standpoint, this approach offers several advantages:
- Enhanced protection: Implementing password policies strengthens the overall security of your systems and data. It ensures that passwords are not easily guessable, adding an additional layer of security against unauthorized access.
- Complexity: Password policies often mandate complexity, requiring the use of a combination of uppercase and lowercase letters, numbers, and special characters. This complexity makes it harder for attackers to crack passwords through brute force or dictionary attacks.
- Preventing common passwords: Policies can include checks to ensure that commonly used and easily guessable passwords, such as, "password" or "123456" are not allowed. This helps safeguard against predictable choices.
- Compliance: Many regulatory requirements and security standards mandate the implementation of strong password policies. Adhering to these policies ensures compliance.
How the password policy will be applied
- For users registered in Identity360's Universal Directory, the password policy configured in Identity360 will be enforced.
- Identity360 enables administrators to enforce robust password policies, ensuring that even if Azure AD has weaker password requirements, when an admin resets a user's password, it will align with Identity360's strong password policy, validating that the organization's security standards remain consistent.
To configure the password policy
- Navigate to the Settings tab > Management Settings > Password Policy Enforcer.
- In this section you can manage:
- Characters: Limit the use of special characters, numbers, uppercase and lowercase letters, and unicode characters in passwords. You can also specify the initial character requirement and prohibit the use of numerals as the last character.
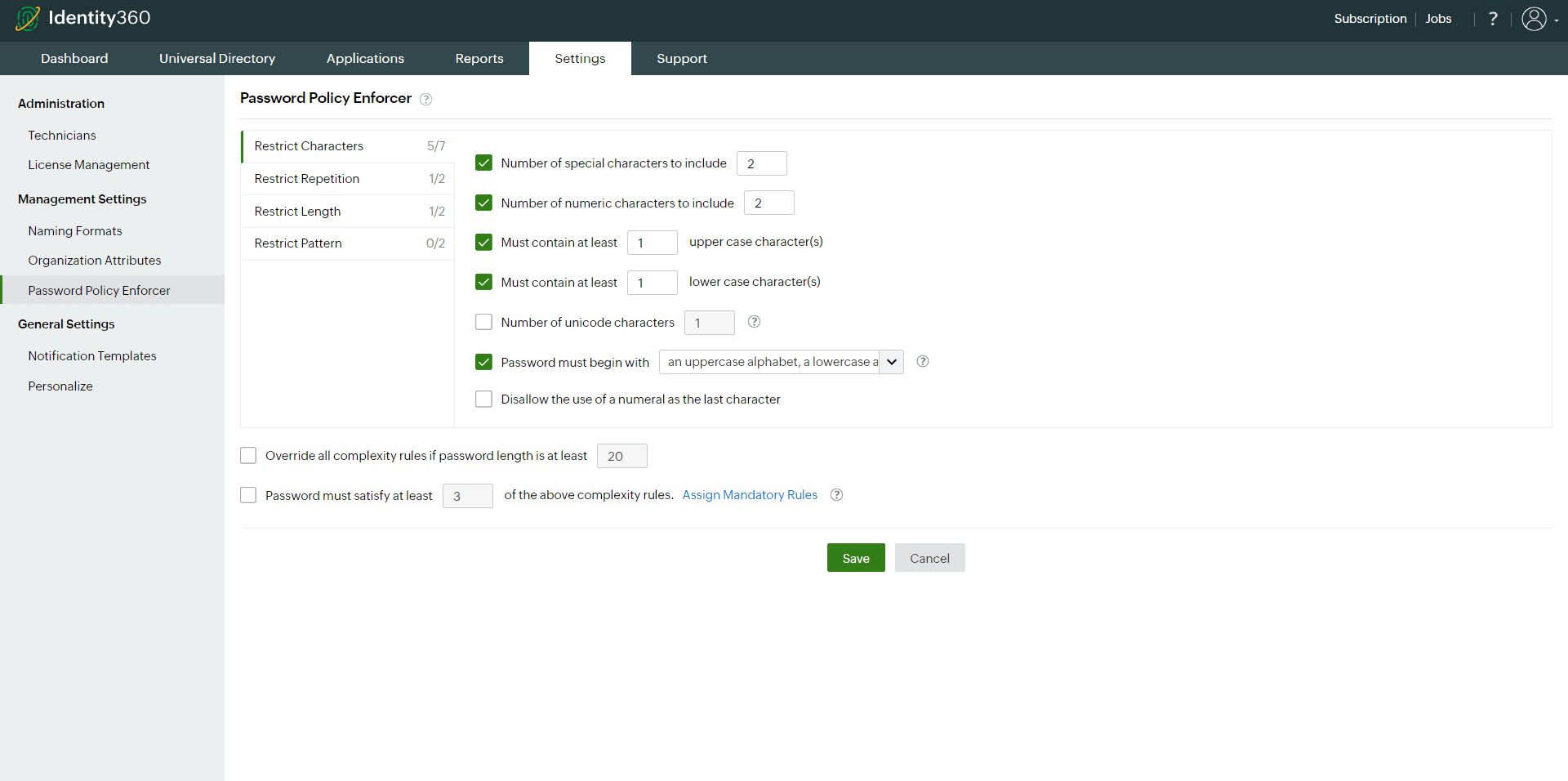
- Repetition: You can restrict the use of consecutive characters from the username or the repetitive use of characters. Additionally, you can restrict users from incorporating three or more sequential characters such as abc, ABC, CbA, 123, and 321. Sequential characters can be upper case, lower case, or mixed case, and they can occur in either forward or reverse sequence. This applies to both letters and numbers.
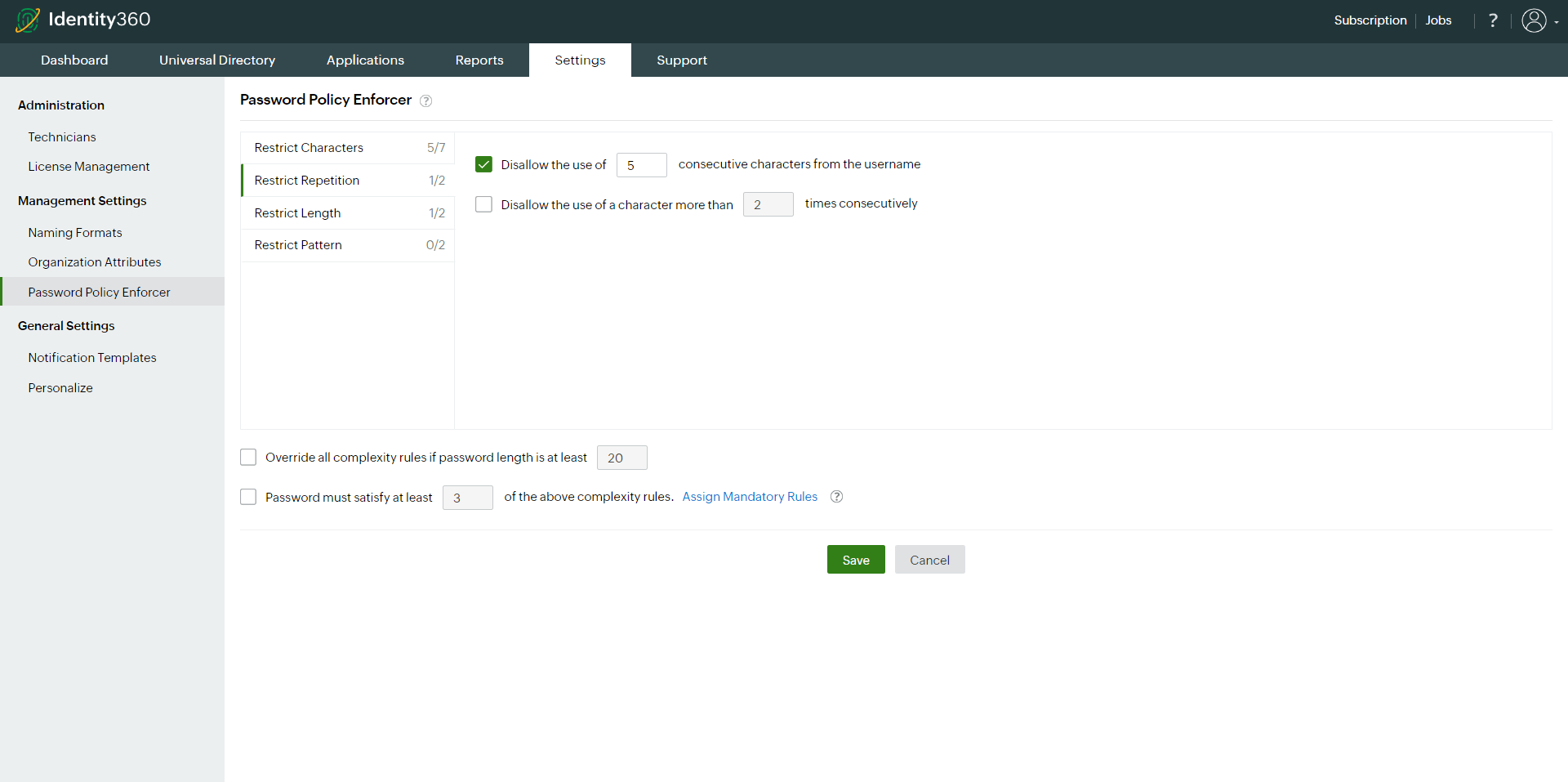
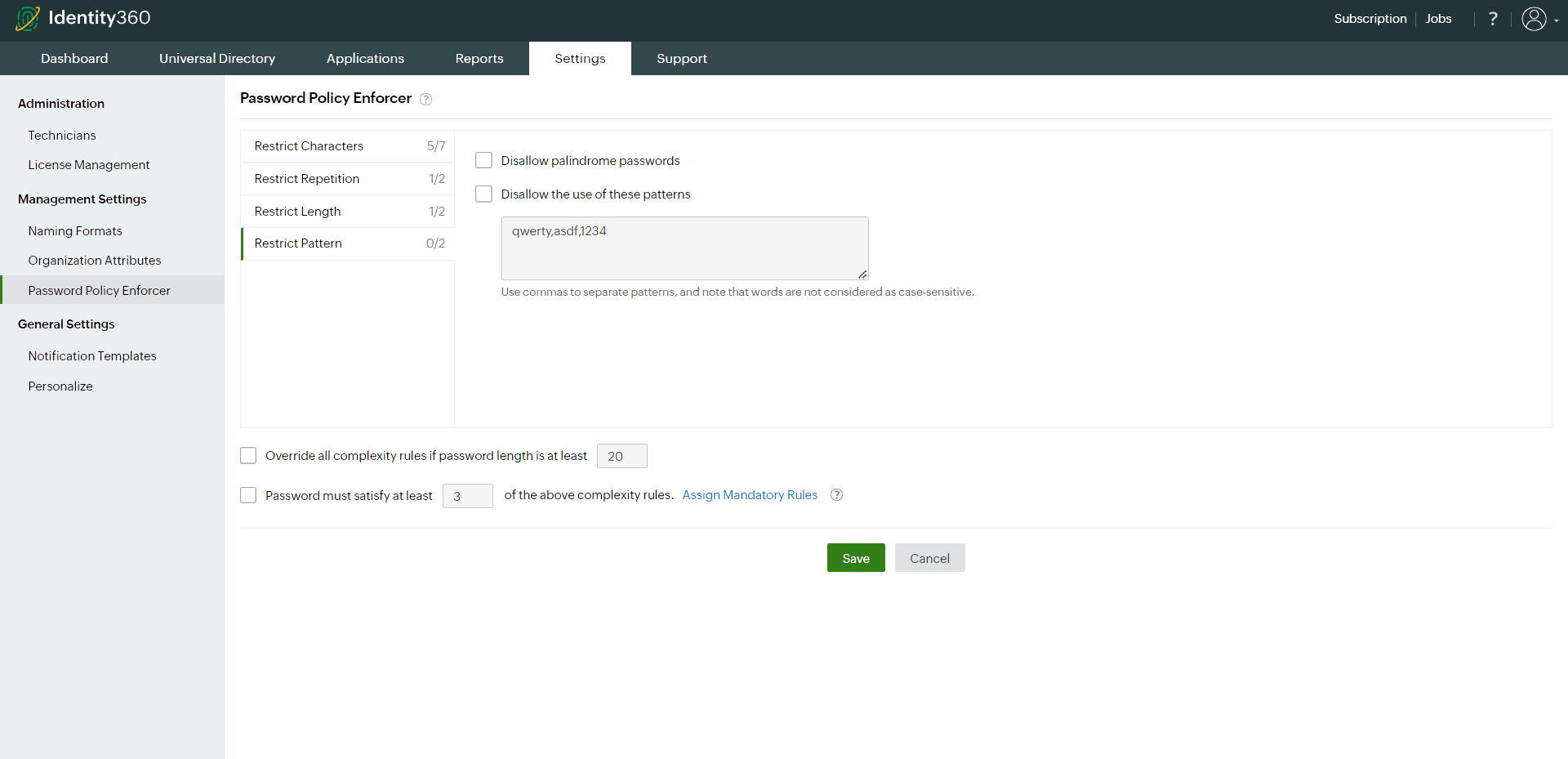
- Patterns: You can choose to restrict certain patterns, such as keyboard sequences, and disallow the use of palindromes.
- You can prevent the usage of palindromes as passwords. Palindromes are words, phrases, numbers, or other sequences of characters that read the same forwards and backwards.
- You can prevent users from using specific phrases when creating passwords by disallowing the use of words from the dictionary.
- The dictionary is a file that contains the phrases you want to restrict. You have the option to either upload a personalized file as the dictionary or use the default one provided. Choosing a new dictionary file will replace the old one.
- The file should be a text file of size less than 10MB.
- The words are case-insensitive. Additionally, ensure that each line in the file contains only one word.
- If the word qwerty is part of the dictionary, then passwords such as qwerty123 are also restricted.
- The words must be at least six characters long.
- You can also restrict users from using certain patterns in their passwords. Administrators can specify words or phrases that are not allowed within passwords. Separate each of these patterns (word or phrase) by commas, and they should range in length from two to 127 characters.
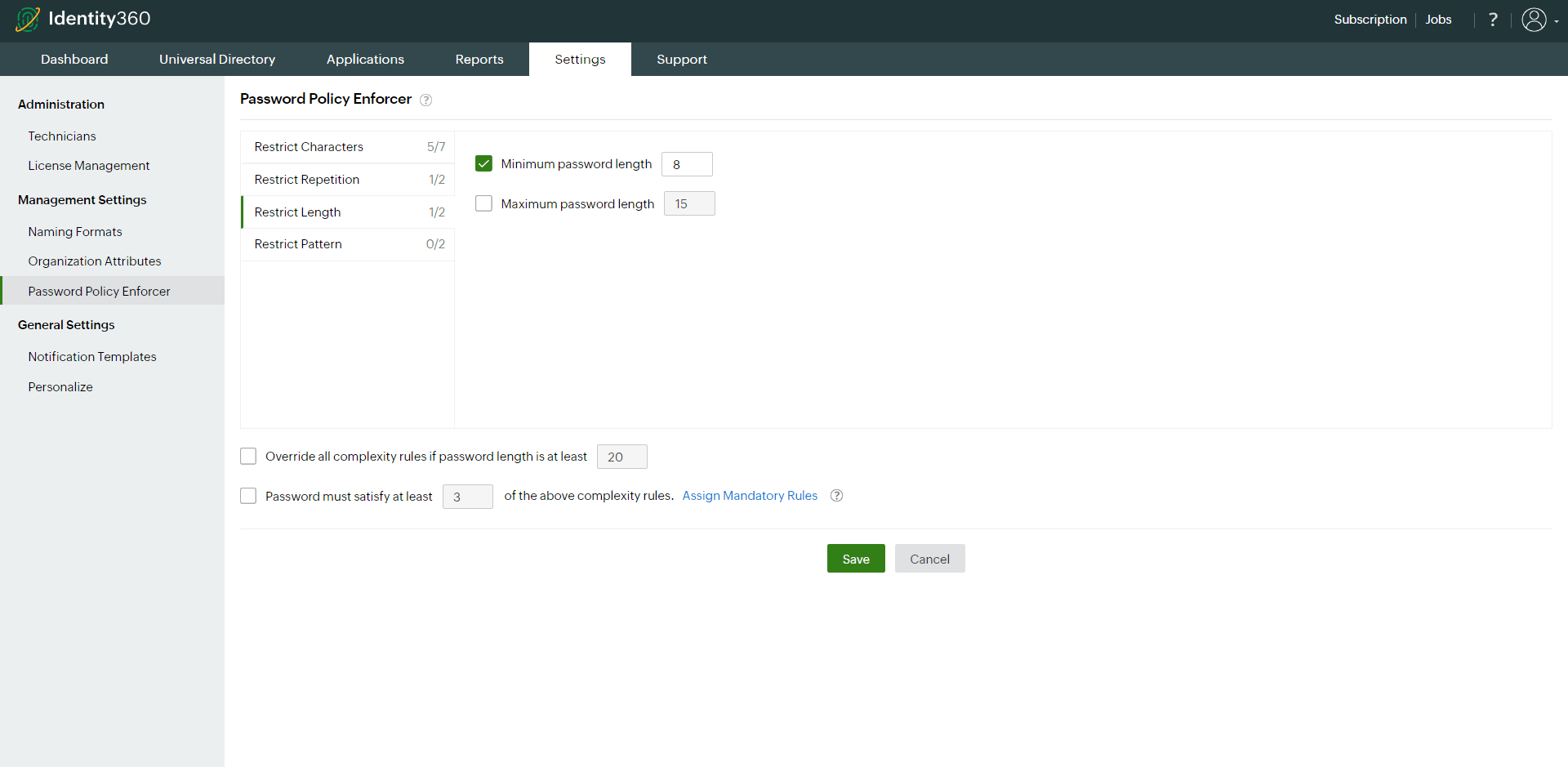
- Length: Specify the minimum and maximum password length.
- You also have the option to allow users to bypass password complexity requirements when the password length exceeds a predefined limit, for example, 20 characters.
- You can require passwords to meet a minimum number of complexity rules from the options provided above and opt to enforce specific rules as mandatory.
×
Thank you for the feedback!



