Application Blocklisting
On average, employees spend about five hours surfing on non-work-related sites every week. Ever wondered how this affects your enterprise's productivity? Studies in the United States reveal that a single social networking application can cause dips in productivity that can cost employers about $28 billion dollars every year. With the stakes so high, it's best to keep all such distractions far from your network. And what better way to do that than with application blocklisting? With the added advantage of threat circumvention, application blocklisting software ticks all the boxes when it comes to keeping applications under lockdown.
Application blocklisting is a technique used to prevent certain applications or executables from running in a network. If application allowlisting is a proactive threat prevention technique, then application blocklisting is more like damage control. ManageEngine Application Control Plus' application blocklisting software simplifies blocklisting by enabling policy-based list creation and updating. Refer here to know more about allowlisting and blocklisting.
Prioritize security and productivity.
Using application blocklisting, you can instantly block applications that might hamper either the security or productivity of your enterprise; top offenders include social media applications, games, and instant messaging apps. However, it's inadvisable to completely prohibit the use of such applications, as higher level employees may need some of these applications for work-related communications. To overcome this, Application Control Plus' application blocklisting feature enables you to associate an application blocklist with different custom groups while keeping in consideration a user's role in the enterprise, giving you the liberty to choose who is impacted by the blocklist rule.
Advanced persistent threats (APTs), zero-day attacks, and known malware intrusions can also be effectively tackled by using the application blocklisting feature. Zero-day vulnerabilities and APTs usually come without a fix, making them the most dangerous. Using an application blocklisting software, you will no longer have to wait around for patches while the vulnerabilities still thrive in your network; you can instantly prohibit the applications from functioning by blocklisting them until a fix arises.
How to blocklist applications using Application Control Plus?
Application Control Plus has applied an unconventional twist to traditional application blocklisting by adding policy-based list generation, offering comprehensive yet granular control. The following policies can be configured in Application Control Plus:
Application-level blocklisting
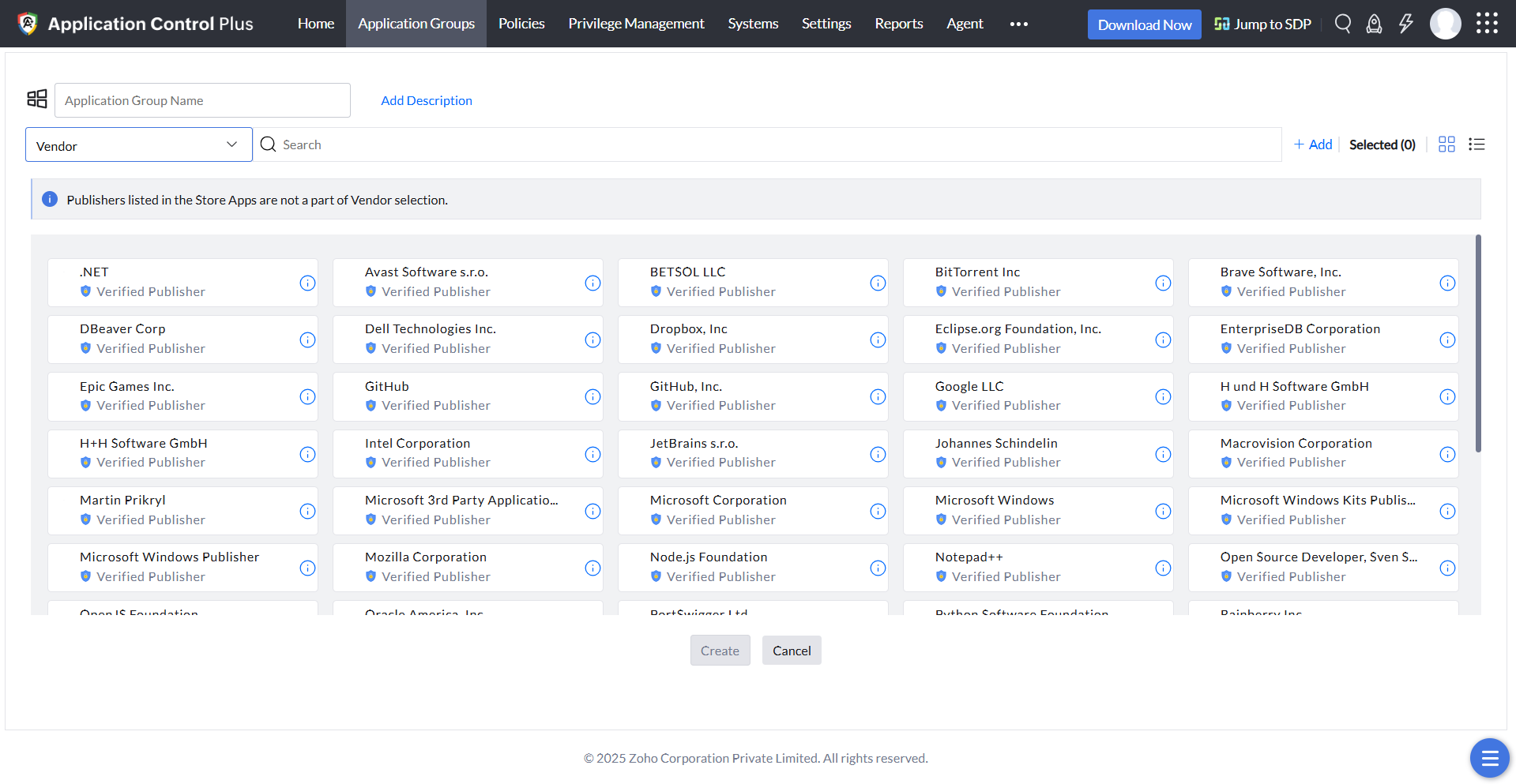
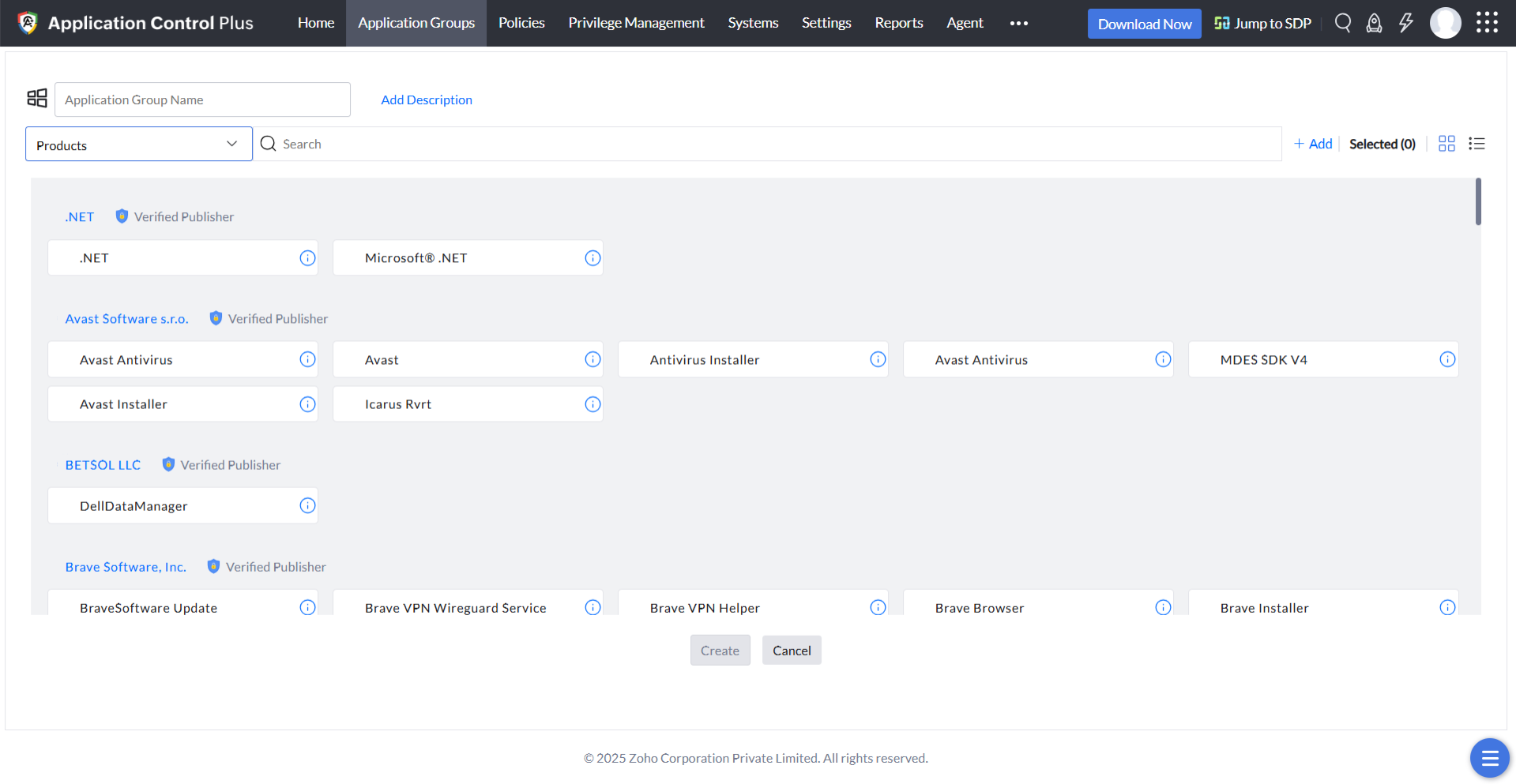
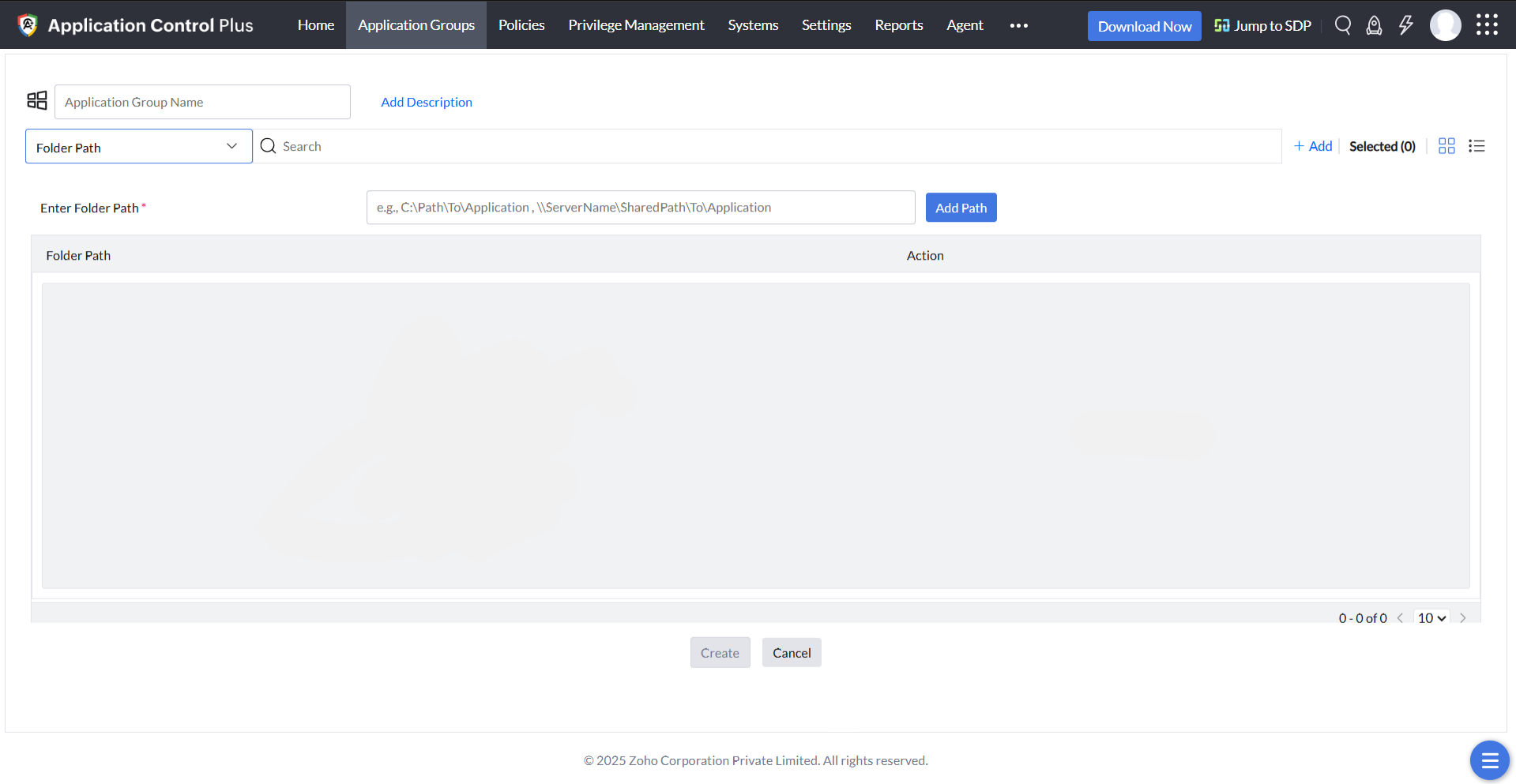
This policy can be built based on the software owner, vendor, product name, folder path of the discovered applications installed in your network. You can choose all the entities you distrust or deem unnecessary while creating the blocklist, so all the applications associated with those entities will be blocked instantly.
Vendor Rule
Product Name Rule
Folder Path Rule
StoreApps Rule
This rule facilitates the discovery of all installed storeapps in Windows 10 and 11 systems, from which you can select and blocklist the applications of your choice in just a few clicks.
Executable-level blocklisting
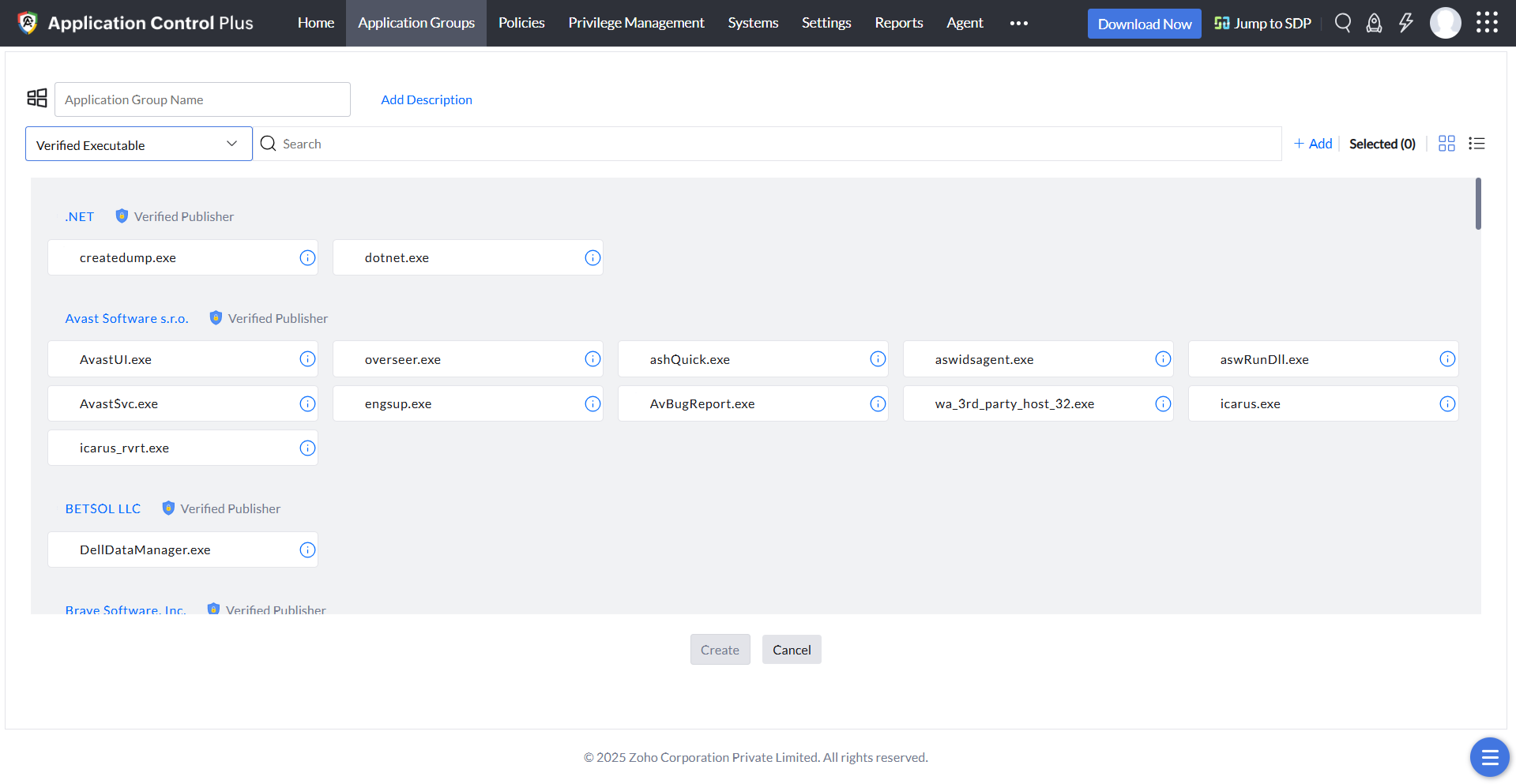
For tighter security, you can enable executable-level blocklisting. Executables compromised by malware or any other threats can be identified individually and be blocklisted without affecting the application's other executables. This level of blocklisting occurs on the basis of policies like Verified executables and File hash.
Verified Executable Rule
File Hash Rule
Custom policies
If an application or executable isn't currently installed, it will not be discovered during the agents' scan. Using a custom policy, you can define a criteria such as the vendor, product name, verified executable, or file hash, and can immediately be included in the application blocklist.
Cutting-edge features like Policy analyzer and Just-in-time access make application blocklisting seamless, enabling easy blocklist reversion and helping you provide need-based access to formerly blocklisted applications.
Try Application Control Plus free for 30 days to see the features yourself!
