-
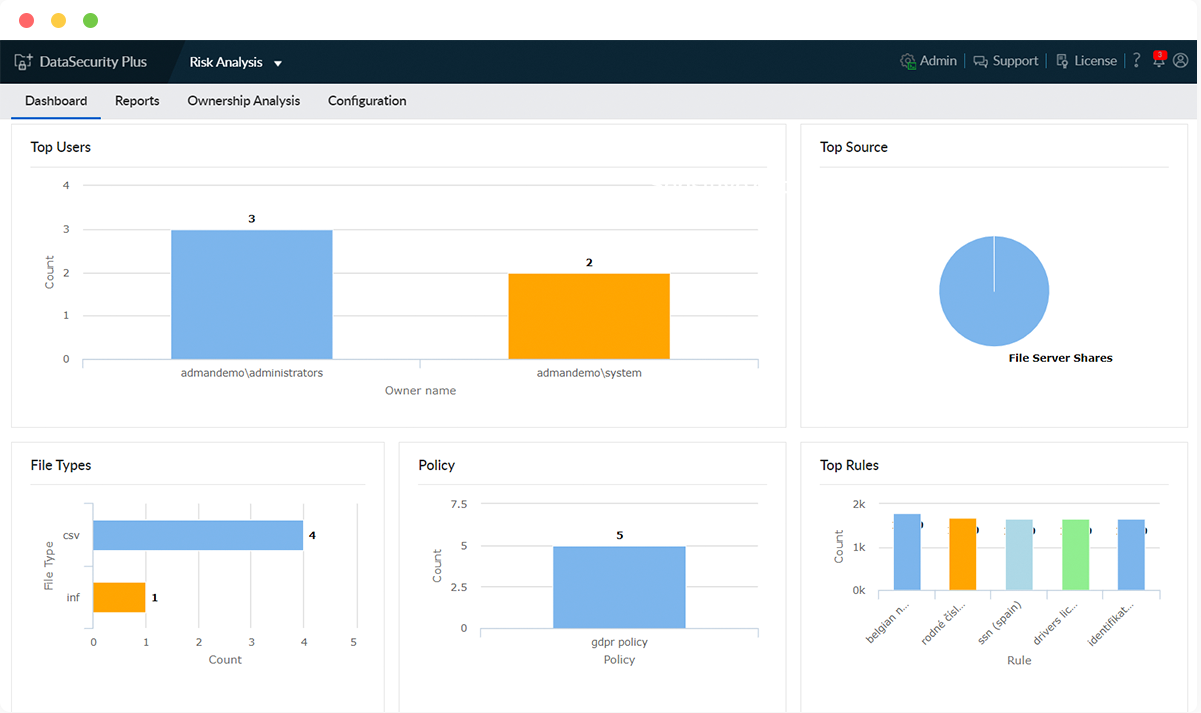
Detect and classify sensitive data
Locate the personally identifiable and business critical data most at risk from internal and external threats. Classify it based on its sensitivity to ensure safe usage.
-
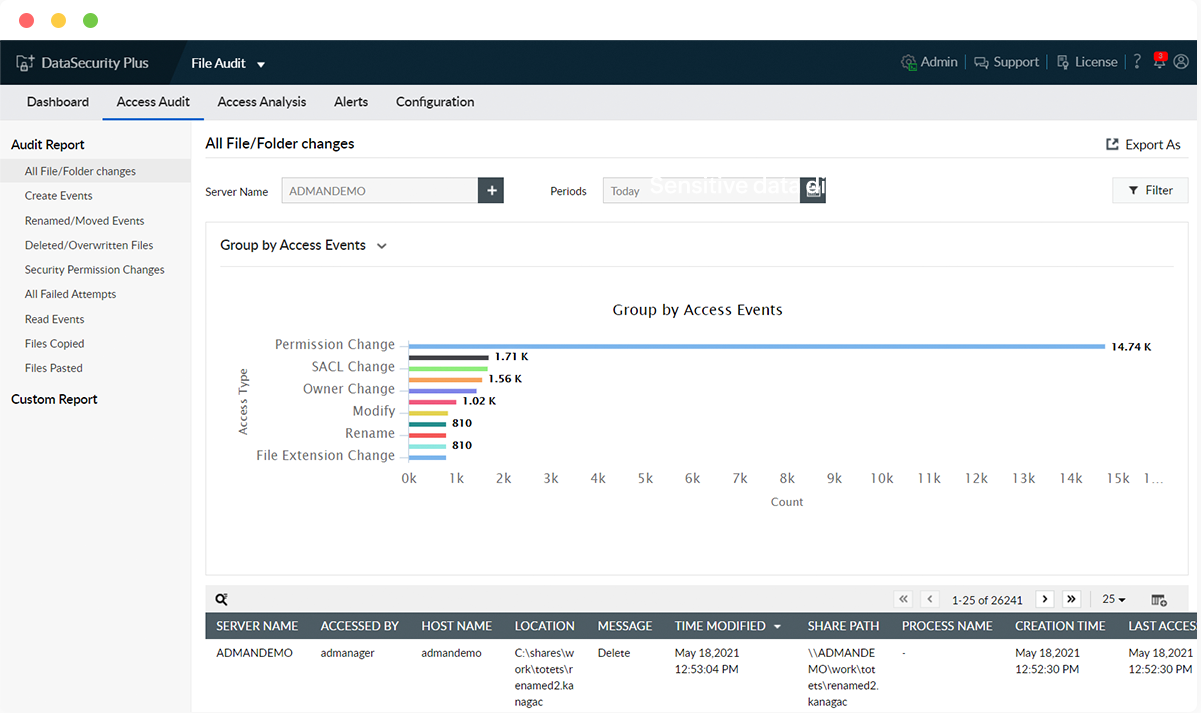
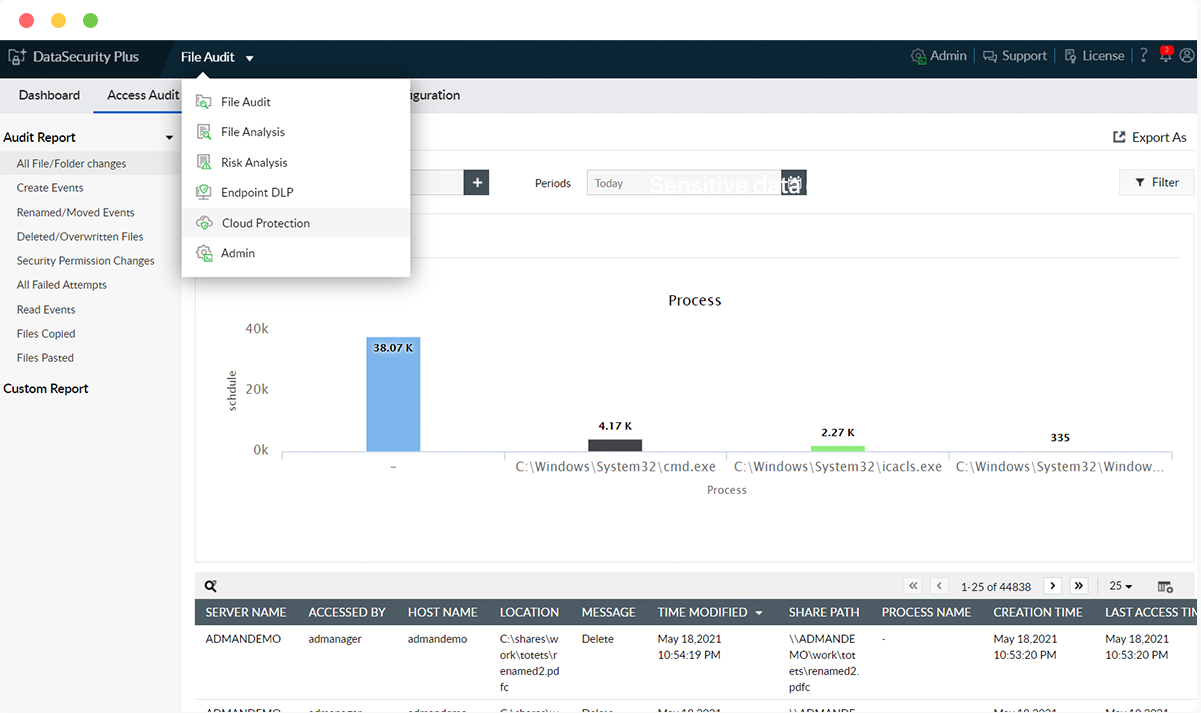
Monitor file transfer actions
Know who copied what file, when, and to which location by tracking file copy actions in network and local shares.
-
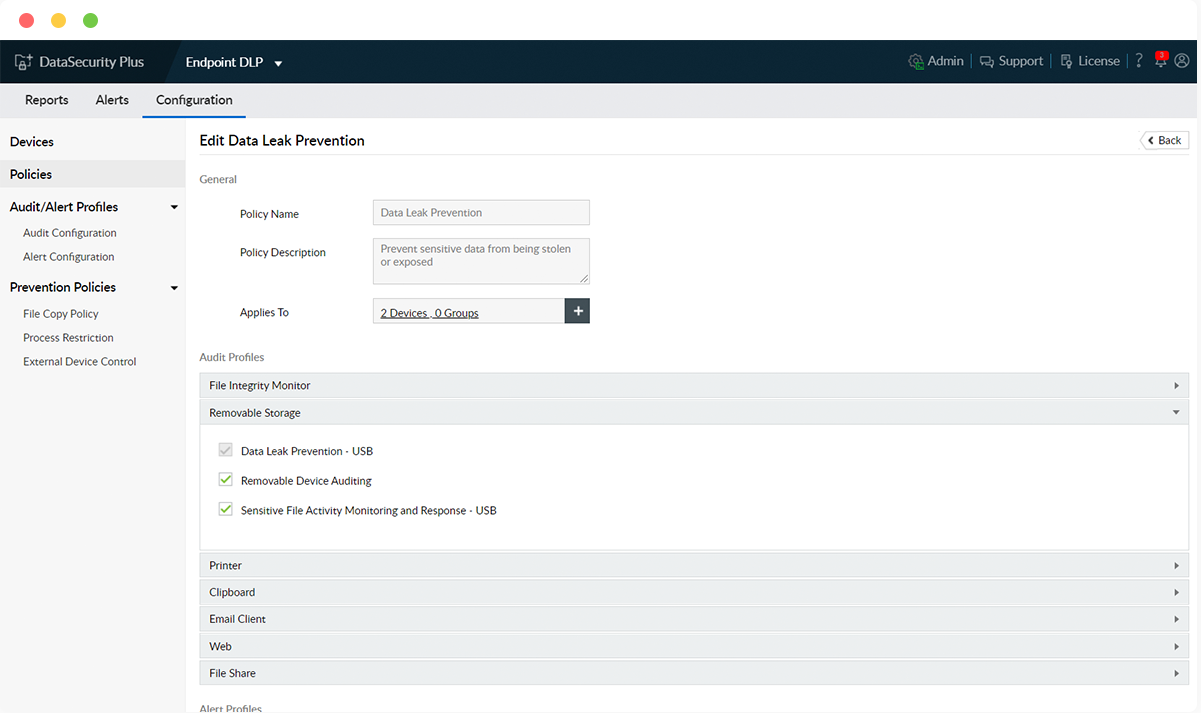
Control peripheral devices
Enable central device control policies to protect against data theft by restricting the use of high-risk USB devices, wireless access points, and CD/DVD drives.
-
Prevent data leakage
Leverage built-in DLP policies, allow and block listing capabilities, on-screen warnings about policy violations, and more to ensure the security of business-critical data.
Elevate enterprise data protection with data leak prevention software.