How a 911 center cut alert noise by 90% with Log360
As part of Log360's beta program, ECSO 911, the emergency communications center serving Southern Oregon, tested Log360's reengineered detection engine with one goal: Reduce alert noise while preserving threat visibility.

“With Log360's optimized detection rules and filtering techniques, we have reduced false or low-priority alerts by 90%, allowing our analysts to focus on the threats that matter most.”
- Corey Nelson, IT manager, ECSO 911From alert overload to laser focus
Before Dozens of daily false positives flooding the SOC.
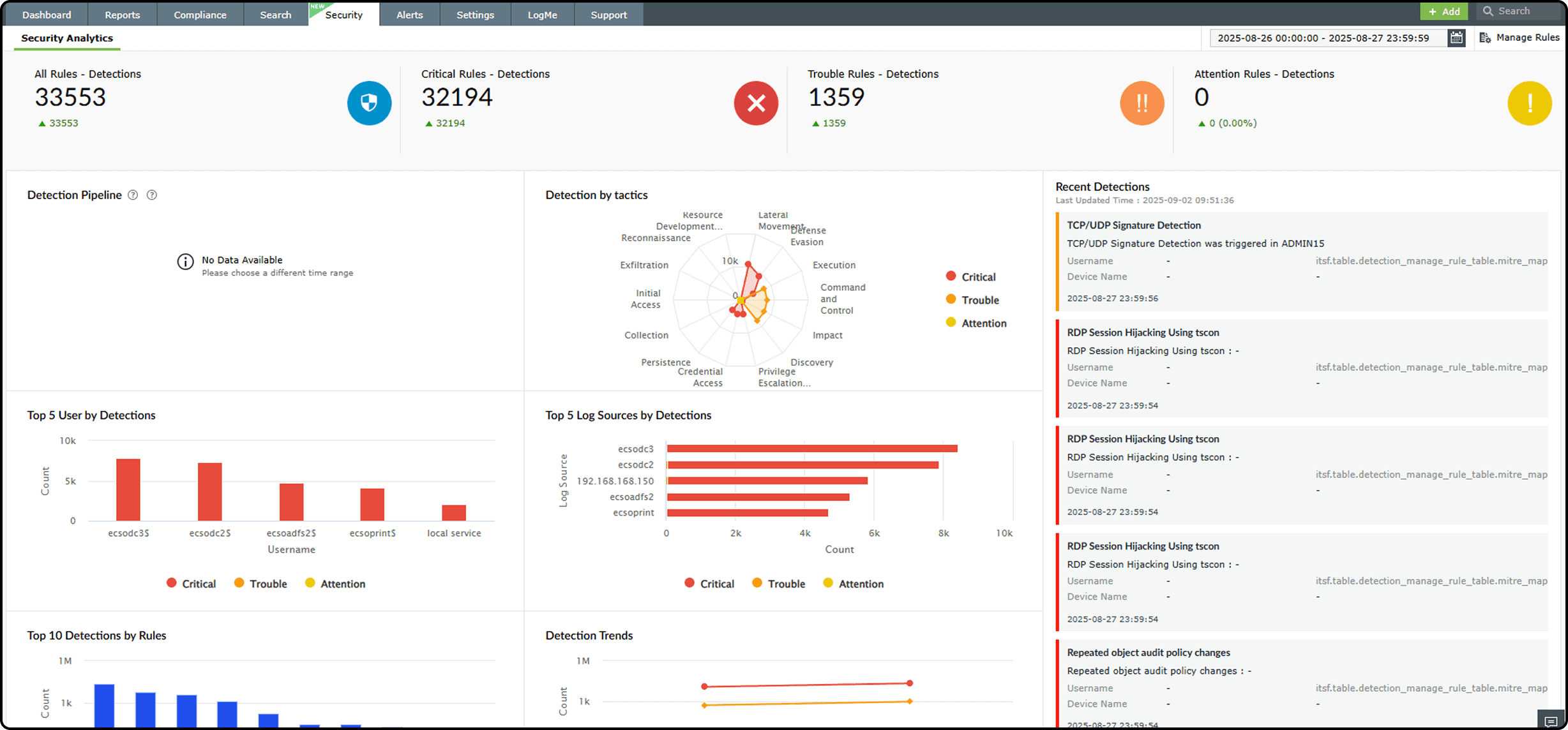
After 90% fewer false positives, providing a clear focus on genuine threats.
The numbers that tell the story
False positives
90%
Threat coverage with
2000+ rules
Multi-layer defense across AD, Windows, network devices and M365

A 911 center's journey to smarter detection
ECSO 911 mission log: Three weeks to 90% noise reduction
The baseline
Applying object filters
Validation and continuous filtering
The baseline
Objective
Establish existing alert volume and noise ratio.
Setup
Default AD detection rules enabled including Member added to a Security-Enabled Global Group and Standard User in High Privileged Group.
Observation
- 30,000+ alerts per day.
- 70% categorized as false positives.
- Majority triggered by routine admin activity across test and service accounts.
Challenge identified
Analysts were losing visibility in noise generated from non-critical OUs and service identities.
Applying object filters
Objective
Scope detections to high-value assets and critical OUs.
Action Taken:
- Object-level filters configured for domain-critical user groups (e.g., Domain Admins, IT Supervisors).
- Lower-tier OUs, test groups, and staging servers excluded from detection scope.
Rules applied:
- Member Added to Security-Enabled Global Group
- Member Removed from Security-Enabled Global Group
- Enabled User Right in AD to Control User Objects
- Standard User in High Privileged Group
Result
- Immediate reduction in redundant alerts.
- SOC analysts reported a 60% drop in false positives.
Key takeaway
Scoping rules by identity and OU hierarchy delivers faster, cleaner detection outcomes.
Validation and continuous filtering
Objective
Sustain accuracy under live operational load.
Action Taken
- Continued monitoring across Windows and AD event sources.
- Added rules for Defense evasion and Persistence.
- Monitored rule hit ratios and validated event accuracy.
Result
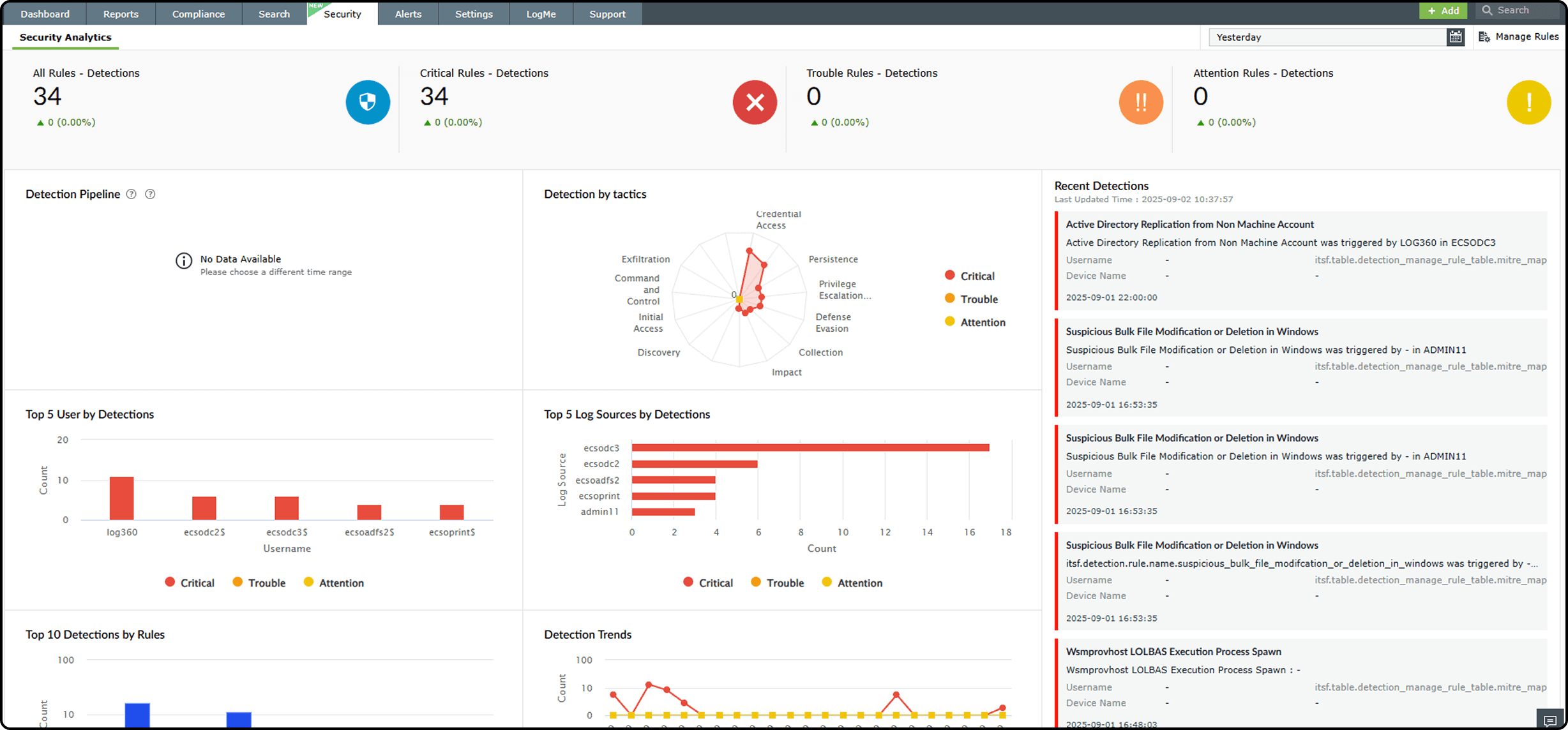
- 90% reduction in false or low-priority alerts across AD detections.
- No missed detections during the test period, confirmed with cross-log correlation.
Outcome
Object-level filtering proved critical in tuning detections to the organization's operational reality, catching what matters, ignoring what doesn't.
Ready to cut through the noise?
See Log360's detection engine in actionWant to see a walkthrough of Log360's new capabilities?
Schedule a personalized demo2023 Zoho Corporation Pvt. Ltd. All Rights Reserved.