On this page
In upscale cosmetic clinics, privacy isn’t just part of the service—it’s the selling point. Every procedure, every image, and every consultation is meant to stay behind closed doors. While the scalpel work happens in sanitized rooms, the real vulnerabilities often lie elsewhere: buried in email chains, cloud folders, and sometimes even not-so-well- secured servers. These clinics don’t just shape appearances—they store them. And the digital files capturing those transformations are exposed to risks that are incredibly damaging.
For CISOs tasked with protecting plastic surgery hospitals and boutique aesthetic practices, the game is changing. What was once limited to safeguarding prescriptions and patient records has evolved. Now, patient image data—3D renderings of rhinoplasties, postoperative body part augmentations, and facial reconstruction maps—are the crown jewels that are in need of austere protection measures.
The new aesthetic: Data as identity, images as leverage
Every image snapped in the aesthetic world carries power—personal, emotional, and, for the cyber underworld, financial. Unlike general healthcare institutions where data theft might include diagnosis codes or prescription logs, cosmetic clinics are uniquely vulnerable to image-based breaches. These visuals, often stored in high-resolution formats, are not just clinical—they’re personal narratives. They reveal not only medical journeys but identities people may not want publicized.
Consider the recent breach at Vitenas Cosmetic Surgery in Houston, Texas. In early 2025, ransomware group Kairos infiltrated the clinic’s systems via a brute-force attack, exfiltrating over 700GB of sensitive data—including intimate patient photos, Social Security numbers, and medical records. The attackers didn’t just leak the data; they taunted the clinic, threatened to release more sensitive content, and allegedly negotiated for weeks before going public. But this wasn’t the first time the industry was shaken. Back in 2017, a Lithuanian cosmetic surgery clinic was breached by ransomware attackers. They didn’t stop at locking the system and demanding payment—they exfiltrated tens of thousands of intimate before-and-after photos. The leak involved celebrities, politicians, and socialites. Attackers even contacted patients individually, offering to withhold publication of their photos—for a price. The fallout? Public scandals, reputational ruin, lawsuits, and regulatory probes. The clinic never fully recovered.
Ransomware attacks these days are designed to inflict emotional trauma. In another chilling episode flagged by the FBI, hackers both demanded ransom from the clinic and targeted patients directly, offering options like:
- $3 to view what data was stolen
- $50 to ensure deletion of their own records
This hyper-personalized extortion strategy turns patients into victims of cyber abuse—often with lasting psychological consequences. For clinics, it becomes not only a business crisis but an ethical one.
These incidents are a preview of what CISOs now contend with: cybercrime turned extortion, data breaches turned identity assaults, and aesthetic clinics turned soft targets.
Why cosmetic clinics are on cybercriminals’ radars
Cyberattacks are often thought of as misfortunes that affect just banks, government agencies, and maybe some unlucky retailers, like Marks and Spencer, which recently fell victim to a ransomware attack. Healthcare data breaches now rank among the costliest, with IBM’s 2024 report revealing an average incident price tag of $9.48 million. And within healthcare, cosmetic clinics often sit at the intersection of wealth and secrecy—a sweet spot for attackers.
Here’s why:
- High net worth clients: Celebrities, executives, and influencers seek cosmetic services and expect absolute confidentiality.
- Sensitive media formats: These clinics store high-resolution visuals and surgical simulations, which require careful protection and privacy controls.
- Unprepared infrastructure: Smaller clinics may lack robust IT defenses or dedicated security staff, making them more vulnerable to cyber threats.
- Third-party sprawl: Reliance on external tools—such as cloud-based image storage, billing, and appointment platforms—can introduce additional security risks if not properly managed.
Add to that a troubling stat: 68% of breaches involve human error, often due to a lack of cybersecurity awareness among clinical staff. Whether it’s uploading images to unencrypted platforms or sharing files via personal email, the attack surface expands with every careless click.
Reputation: The currency of aesthetic medicine
For aesthetic practices, reputation isn’t just important—it’s existential. Patients choose providers based on trust and image. A single breach can devastate that equation.
Aesthetic clinics aren’t backed by sprawling hospital networks—they rely on word-of- mouth, influencer endorsements, and repeat clientele. One leaked photo isn’t just damaging—it’s a campaign killer.
Moreover, legal repercussions under data privacy laws like HIPAA (United States), the GDPR (European Union), and India’s DPDP Act are severe. The latter, when finally enforced, will allow for penalties up to ₹250 crore for mishandling personal data. And courts are increasingly sympathetic to victims of intimate digital exposure—especially when dealing with clinics that failed to implement basic protections.
Cybersecurity for cosmetic clinics
Let’s be blunt: Protecting cosmetic images is no longer an IT issue—it’s a clinical responsibility. Just as surgeons sanitize their tools and document informed consent, SOC teams must monitor networks, encrypt assets, and preempt intrusions. Failing to do so isn’t just a technical oversight—it’s a breach of care.
Enter SIEM. While not the centerpiece of this story, SIEM systems play a decisive role in fortifying cosmetic clinics against stealthy breaches.
SIEM: Watching the shadows, guarding the archives
A well-configured SIEM solution doesn’t just detect malware—it reads the room. It understands when an admin attempts to download hundreds of images at 3am. It correlates access logs from imaging servers with endpoint activity. It flags anomalies, triggers alerts, and offers the forensic trail needed for investigations.
In the context of aesthetic clinics:
- It can detect unauthorized access to sensitive folders—say, an archive containing facial reconstruction scans of a celebrity.
- It can block downloads from suspicious geolocations, especially if attackers use VPNs to disguise origin.
- It enables audit readiness, ensuring clinics stay compliant and defensible during legal disputes.
More importantly, it scales. Whether protecting a single clinic or a hospital network with aesthetic departments, SIEM solutions offer centralized, real-time visibility—a must when every leaked image could be tomorrow’s headline.
The human factor: Training, tools, and trust
Technology is only half the battle. CISOs must champion a cultural shift—one where cybersecurity becomes part of clinical hygiene.
That means:
- Conducting staff workshops on phishing, secure sharing, and access protocols
- Implementing role-based access controls so only authorized personnel can view sensitive images
- Enforcing offline storage policies or encryption standards for image archives
- Establishing incident response plans—complete with patient notification workflows and legal contingency maps
Remember: You can outsource billing, but you can’t outsource trust.
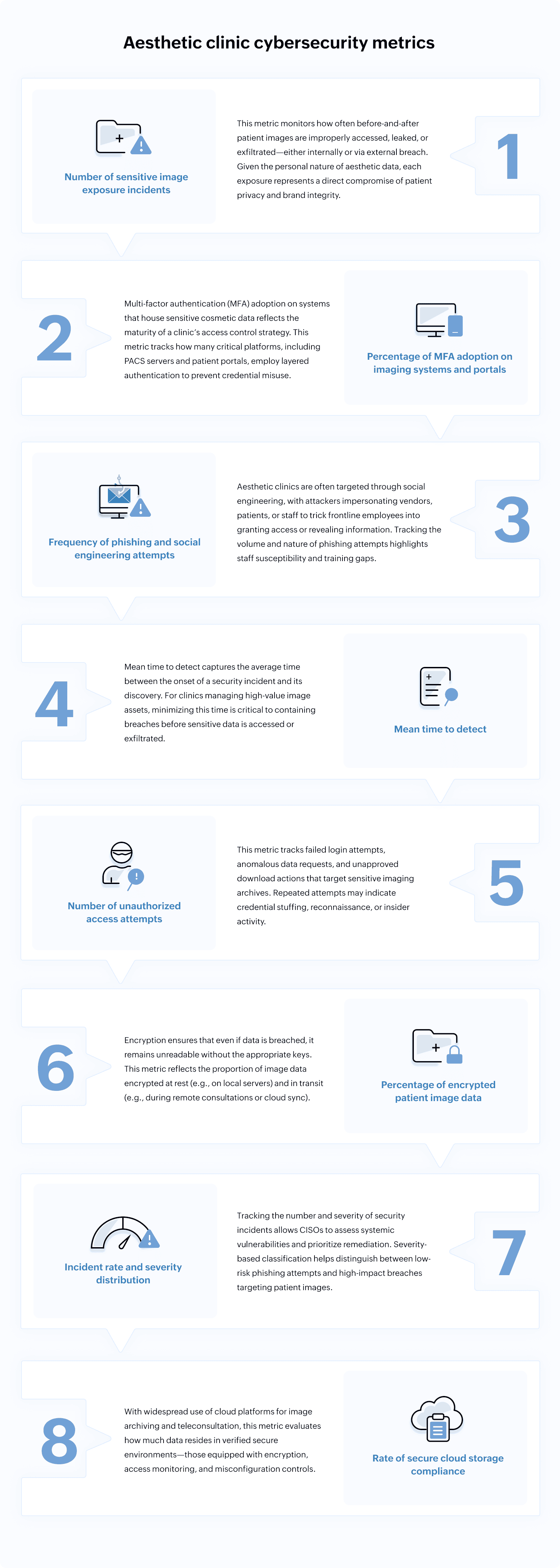
Aesthetic clinic cybersecurity metrics
For CISOs in aesthetic practices, tracking the right cybersecurity metrics is not just about performance—it’s about accountability. These metrics reveal where exposures lie, how fast threats are identified, and whether current strategies align with regulatory expectations and patient trust.
Below are eight metrics that form a robust framework for monitoring and improving data security—particularly when it comes to protecting sensitive cosmetic surgery images.
Insights gained from these metrics
Each of these eight cybersecurity metrics offers not just a lens for measuring technical success but deeper strategic guidance for CISOs in cosmetic clinics and aesthetic practices. Here’s how each metric translates into actionable insights and best practices for continuous data security improvement, regulatory compliance, and the preservation of patient trust:
1. Number of sensitive image exposure incidents
- Insight: A high or rising number of exposures indicates critical process, technology, or workforce gaps in safeguarding before-and-after patient photos, demanding urgent review of access controls, audit logging, and secure storage.
- Practice: After each incident, perform root cause analysis, tighten workflow oversight, update incident response playbooks, and enhance employee training on privacy protocols.
2. Percentage of MFA adoption on imaging systems and portals
- Insight: Low MFA coverage highlights privileged access vulnerability; high coverage signals a strong commitment to Zero Trust principles.
- Practice: Accelerate MFA rollout, prioritize adoption on systems housing the most sensitive image data, and consider biometric factors for VIP or high-profile image archives for added security.
3. Frequency of phishing and social engineering attempts
- Insight: Persistent targeting via phishing or social engineering reveals gaps in staff awareness and the effectiveness of current anti-phishing tools or email filtering.
- Practice: Regularly simulate phishing attacks, tailor security awareness training to current threat patterns, and adjust email protection rules based on the evolving tactics seen in real-world attacks.
4. Mean time to detect
- Insight: Slow detection times mean greater risk of damage and regulatory exposure; fast detection reflects effective monitoring and incident response processes.
- Practice: Invest in SIEM solutions tuned for healthcare workflows, streamline alert triage, and rehearse rapid escalation and containment steps. Benchmark detection speed against healthcare best-in-class organizations, which strive for detection within hours.
5. Number of unauthorized access attempts
- Insight: Repeated access attempts point to active threats—whether credential stuffing, bot activity, or malicious insiders—targeting image archives.
- Practice: Automate anomaly detection, enable adaptive authentication (such as escalating to MFA on flagged behavior), and use this metric to justify further controls (e.g., tighter IP allowlisting and device restrictions).
6. Percentage of encrypted patient image data
- Insight: Low encryption rates are a red flag for both compliance authorities and cyber insurers; achieving near-total encryption provides confidence that, if breached, core patient data is still protected.
- Practice: Audit all storage and transmission channels for encryption coverage, require strong key management, and integrate SIEM and DLP tools to alert on unencrypted data or failed encryption attempts.
7. Incident rate and severity distribution
- Insight: Tracking both count and severity enables prioritization—so urgent remediation targets breaches with highest potential for patient or reputational harm.
- Practice: Use impact-based severity scoring to prioritize incident response and ensure board reports reflect the true scale and urgency of each scenario. Track remediation time to ensure lessons learned result in concrete, timely action.
8. Rate of secure cloud storage compliance
- Insight: High compliance means clinics are proactively managing cloud risk; lapses highlight potential for shadow IT or misconfigured resources leaving patient photos exposed (as seen in prior industry breaches).
- Practice: Perform regular cloud security audits, enforce cloud security baselines (like encryption and access controls), and utilize a SIEM solution with cloud connectors for real-time exposure monitoring and rapid remediation when issues are detected.
In aesthetic medicine, there’s always the allure of transformation. But in today’s digital reality, transformation also means protecting the unseen—the pixelated, the archived, and the sensitive. When clinics invest in cybersecurity, they're not just defending data; they’re honoring identity, choice, and trust.
Related solutions
ManageEngine AD360 is a unified IAM solution that secures digital identities with adaptive MFA and role-based access control—helping prevent insider threats, even if credentials are compromised.
To learn more,
Sign up for a personalized demoManageEngine Log360 is a unified SIEM platform that combines UEBA, DLP, CASB, and SOAR to detect threats, protect networks, monitor the dark web, and automate response—reducing breach impact and compliance risk.
To learn more,
Sign up for a personalized demoThis content has been reviewed and approved by Ram Vaidyanathan, IT security and technology consultant at ManageEngine.
