Schools hold massive volumes of sensitive PII—names, addresses, grades, health records, and even financial information. These records often belong to minors, making them even more valuable on the dark web. Additionally, schools rely heavily on third-party EdTech platforms that may not always have strong security controls.
On this page
Securing the education sector from modern identity-based attacks: An overview
Digital transformation in the education sector has yielded a plethora of benefits. Much like remote work, learning is no longer confined to a classroom. E-learning and assessment tools such as learning management systems and online collaboration enable learning from anywhere. This has made the learn-from-anywhere dream a reality. Digital learning, with its interactive modules and accessibility benefits, has ensured that teaching also becomes a less arduous process. Moreover, educational institutions leverage digital tools to scale administrative tasks such as record-keeping, attendance tracking, and payroll processing for staff members.
However, this rapid proliferation brings a common challenge across all sectors: the risk of cyberattacks targeting student identities and sensitive PII stored by organizations. A 2024 CIS report unearthed a startling statistic:between July 2023 and December 2024, 82 percent of K-12 schools have been victims of cyberattacks. The report also emphasized that credential attacks are a prevalent tactic used by malicious actors to gain unauthorized access.
With concerns regarding the digital safety of student privacy and intellectual property looming large, educational institutions have a security imperative to implement identity security frameworks that combat modern cyber threats.
Security risks affecting the education sector
Schools and universities are storing high-value PII and intellectual property, making the education sector a lucrative target for cyber attackers. Some of the prevalent security risks affecting the education sector include:
Social engineering
Phishing and social engineering campaigns that lure unassuming staff or students to click into malicious links happen to be the most prevalent attacks targeting educational institutions. A 2024 study by the UK government revealed that 92 percent of primary schools and 89 percent of secondary schools have reported a phishing attack.
Poor password hygiene
The use of poor passwords is rampant in the education sector, with a 2025 study uncovering that the industry is made vulnerable by guessable passwords ('123456' and 'password' being the most prevalent used credentials). According to Verizon's DBIR report, 86 percent of the web application breaches are initiated by compromised credentials. Additionally, students and staff tend to reuse passwords of their personal accounts to secure their school accounts.
Poorly deprovisioned accounts
Organizations that do not regularly deprovision obsolete accounts are running the risk of creating entry points for attackers. This is reflected in a 2023 survey, which reported that three out of four cyberattacks in the education sector are caused with compromised on-premises user or admin accounts. Obsolete staff accounts that retain a high level of privileges can be abused by insiders and malicious actors to perform privilege escalation and data exfiltration.
Unpatched systems
Rapid and consistent patching of systems is the shortest route towards a secure IT environment. A 2025 survey by TrendMicro revealed that organizations were able to thwart 34% of data breach attempts by reducing its patching time from 30 to seven days, underscoring the correlation between patching frequency and cyber protection. Education organizations that lack the alacrity, or the necessary IT budget, to implement regular upgrades are most vulnerable to zero-day attacks.
The tale of two cyberattacks: The West Lothian Schools attack and the PowerSchool data breach
2025 witnessed two large-scale cyberattacks in the education sector: the West Lothian Schools incident and the PowerSchool data breach. Both involved ransomware attacks, and these attacks led to the compromise of sensitive data, including PII.
The West Lothian Schools attack:
The 2025 West Lothian schools cyberattack was a major ransomware incident targeting the council’s educational network in Scotland. A ransomware gang, identified as Interlock, encrypted school systems and demanded a ransom for decryption. When their demands were not met by the school's management, the gang escalated their attack by dumping 3.3 million stolen files containing 2.63 TB of data on the dark web.
According to West Lohian Council's official statement, a small quantity of the files were of sensitive nature. According to the Comparitech article, the leaked files contained images of passports, driver's licenses, and various documents. West Lohian Council's official website stated, "It is possible that names, addresses, email addresses and learning materials were amongst the data taken from the affected schools."
Aftermath of the West Lohian cyberattack
- 3.3 million leaked files included sensitive records like social work reports, ID documents, and student/staff lists, raising serious privacy threats School IT systems were disrupted.
- Incident teams isolated threats, restoring operations while investigating the breach’s scope.
- Post-attack, stricter cybersecurity protocols such as enforcing the use of complex passwords, fine-grained user access controls, vendor reviews, and training for staff and students were implemented.
The PowerSchool data breach
In 2024, PowerSchool, a cloud-based provider of K-12 education software, detected unauthorized access to its systems via its community portal, allowing the attackers to reach the organization's student information systems (SIS). The threat actor exfiltrated sensitive data from school districts—including student, parent, and educator information—impacting millions of individuals.
What started as a data breach evolved as a ransomware incident, which resulted in PowerSchool paying a ransom to the attacker to delete the stolen data to prevent its public exposure. With PowerSchool's demands unmet despite paying ransom, the incident has affected schools across the United States and Canada.
Aftermath of the PowerSchool data breach
- PowerSchool and impacted districts notified families, authorities, and regulators, and began offering credit monitoring.
- The breach prompted emergency security audits, system upgrades—including roll-out of multi-factor authentication—and regulatory investigations.
- Law enforcement traced the attack to individuals in Massachusetts, who faced federal charges for the breach.
- The incident spotlighted the critical need for stronger password practices and robust security controls in educational technology sectors.
Impact of cyberattacks on educational institutions
In the context of the education sector, the impact of cyberattacks does not only stop from ceasing administrative processes but can disrupt the learning experience of students.
Examination delays
The disruption of organizational networks caused by DDoS attacks or the leakage of sensitive information (such as question papers) can put regular operations, such as examinations or online tuition, to a grinding halt. These delays put a strain on students and teachers alike by disrupting academic schedules, affecting learning continuity, and eroding trust in the institution’s ability to deliver secure, uninterrupted education.
Intellectual property and research theft
A cause of major concern for universities, intellectual property theft is at the epicenter of most nation-state attacks. A 2025 US House Committee report highlighted over 60 cases of espionage attacks carried out by Chinese nation-state actors targeting multiple critical sectors. The report also mentioned an executive order issued by Texas Governor Greg Abbott, which directed higher education institutions to secure IP, critical infrastructure, and PII from being exfiltrated by nation-state actors.
Compliance failures and legal issues
Regulatory bodies for the education sector hold organizations liable for failure to protect student data, maintain secure access controls, and promptly report breaches involving personally identifiable information (PII). In other cases, compliance bodies such as FERPA and COPPA may cut federal funding to schools that do not comply with their mandates.
- With schools holding sensitive data of pupils aged below 17, such as photographs, residential addresses, medical information, etc., failure to protect student privacy can lead to legal troubles.
- In 2019, Datatilsynet, Norway's Data Protection Authority, ordered a school to pay NOK 1,200,000 after a third-party mobile application breach exposed the sensitive information of 63,000 pupils.
Key Takeaways for CISOs
CISOs and IT security leaders in the education sector should take the following lessons from recent breaches:
- Identity is the most vulnerable entity: Weak or reused credentials are low-hanging fruit for threat actors.
- Supply chain exposure is a critical risk: Security postures of third-party vendors directly affect your organization.
- Ransomware recovery is costlier than prevention: The cost of breach recovery, legal actions, and reputational damage far outweighs the cost of implementing preventive identity and access security solutions.
- Awareness is critical: Staff and students alike must be educated on identifying phishing attempts and practicing good cybersecurity hygiene.
How to protect educational institutions from cyberattacks
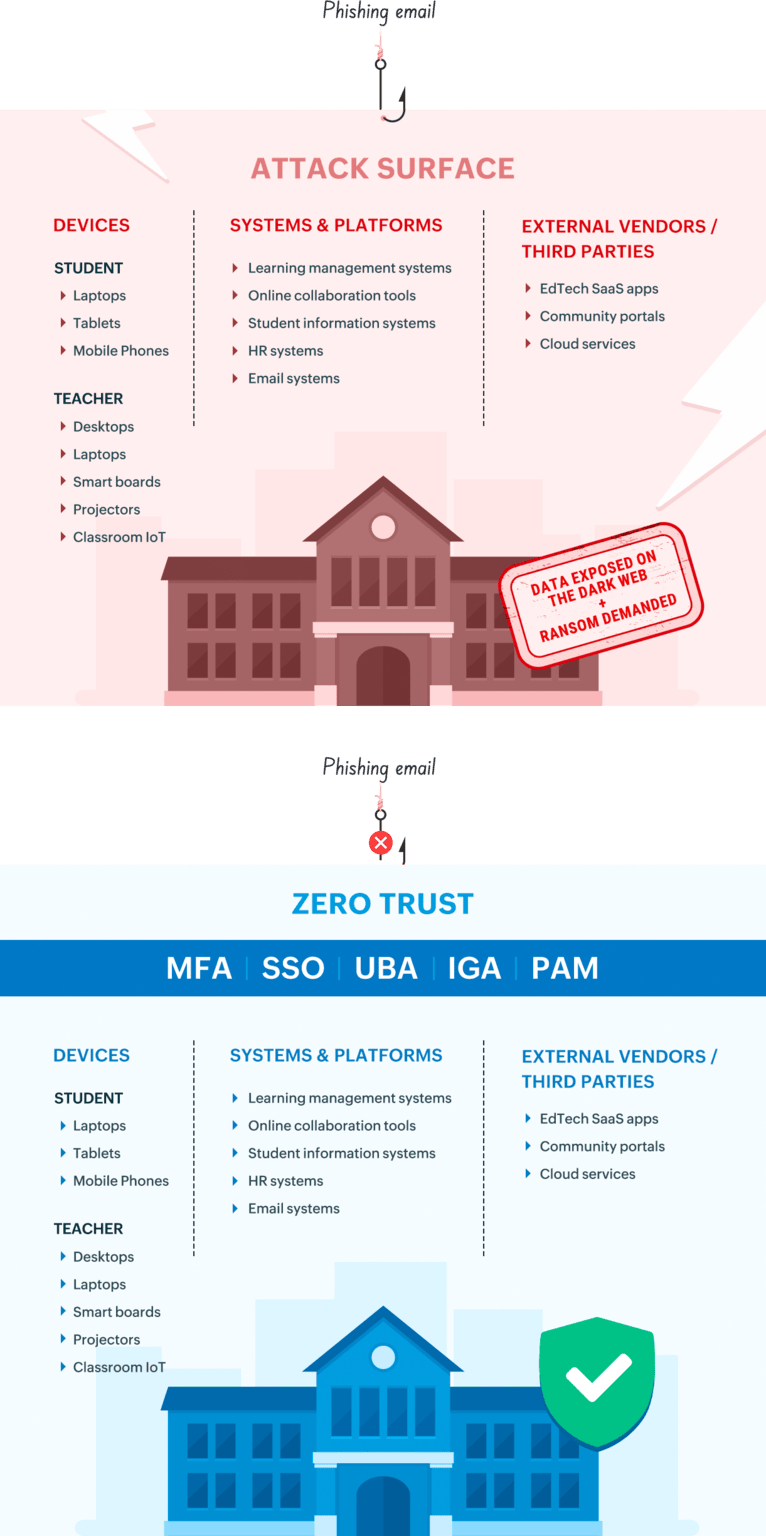
To effectively safeguard student and faculty identities, educational institutions should adopt a consolidated identity security strategy that comprises adaptive multi-factor authentication, access controls, and continuous monitoring.
Enforce risk-based MFA and SSO
Schools manage diverse user identities across multiple applications, making password-only security inadequate. Implementing identity and access management (IAM) with risk-based Multi-Factor Authentication (MFA) ensures adaptive protection, challenging suspicious login attempts while streamlining access for legitimate users. Integrating Single Sign-On (SSO) with centralized IAM reduces password fatigue and enforces uniform access policies. This combination prevents credential theft, limits unauthorized access to student and staff data, and strengthens compliance.
Monitor and audit user behavior
Granting access is only the first step in maintaining a secure environment. Schools need User Behavior Analytics (UBA) to detect anomalies, such as unusual login times, mass data downloads, or attempts to access restricted records. Centralized IAM solutions with UBA capabilities help analyze identity-related activities and flag deviations from normal patterns in real time. Regular reviews of user behavior allow early detection of compromised accounts and insider threats. This approach strengthens visibility, enables faster incident response, and ensures sensitive student and staff information remains protected.
Promptly deprovision and delete obsolete accounts
Students graduate, staff leave, and contractors frequently change in schools, leading to obsolete accounts that often persist unnoticed. An identity governance and administration (IGA) framework automates user provisioning, modification, and deprovisioning processes, immediately revoking access once a user departs. This proactive identity governance approach removes orphaned and duplicate accounts, shrinking the attack surface and preventing unauthorized access. Automated user lifecycle management within IGA ensures only verified, active users retain access to educational systems, improving security posture and compliance readiness.
Monitor privileged account activity
Privileged accounts belonging to the teaching and administrative staff have elevated access to critical school systems, making them prime targets for attackers. Continuous monitoring of these identities is essential to detect unusual activity that could signal abuse or compromise. Real-time alerts on privilege escalation attempts or unauthorized configuration changes help administrators respond swiftly to potential threats. Strong oversight of privileged identities, combined with centralized IAM controls, protects core IT infrastructure and sensitive student data, ensuring accountability and minimizing risks from misuse or breaches.
Enforce password policies
By enforcing stringent password guidelines, some of which include reuse of breached credentials or dictionary words, and consistently applying these standards for every user, organizations can overcome credential stuffing attacks. Combined with MFA, robust password policies significantly reduce unauthorized access attempts. Embedding these policies into identity governance ensures uniform enforcement, enhancing both user security and institutional data protection.
Backup IT environments periodically
Cyberattacks such as ransomware can disrupt digital learning environments. Regular, automated backups of hybrid IT environments enable quick recovery and business continuity. A centralized backup strategy that encompasses IdP and application-level environments ensures uninterrupted operations while also making IT ecosystems resilient to encryption-based attacks.
Enforce a Zero Trust environment
With the prevalence of multiple applications being part of the student and educator's learning journey, IT administrative teams benefit from the Zero Trust security framework, which eliminates implicit trust on users and devices, regardless of their location or network. Every access request is verified continuously using contextual signals such as user identity, device health, location, and behavior patterns. This approach helps prevent unauthorized access, mitigate insider threats, and enforce granular access controls across cloud, on-premises, and hybrid learning environments.
FAQs on Identity Security in Education
Risk-based MFA applies extra verification only when login behavior looks unusual (e.g., a student logging in from a new country). For day-to-day logins, users may just need their standard credentials, keeping the learning experience smooth while still blocking suspicious access.
Identity governance ensures that when a student graduates, a staff member leaves, or a contractor’s work ends, their access is revoked automatically. Without this, orphaned accounts can remain open for months — a perfect backdoor for attackers.
Yes. Zero Trust doesn’t mean making everything harder; it means continuously verifying identity and device health. For example, a teacher logging into the grading system from their classroom device may be granted seamless access, but the same login attempt from an unknown device or location would trigger extra checks.
Start with essentials:
- Enforce stronger password policies
- Enable MFA on high-value systems (email, SIS, payroll)
- Regularly patch systems and software
- Train staff and students on phishing awareness
These low-cost measures drastically reduce the attack surface, even before larger IAM investments are made.
Related solutions
ManageEngine AD360 is a unified IAM solution that provides SSO, adaptive MFA, UBA-driven analytics, and RBAC. Manage employees' digital identities and implement the principles of least privilege with AD360.
To learn more,
Sign up for a personalized demoManageEngine Log360 is a unified SIEM solution with UEBA, DLP, CASB, and dark web monitoring capabilities. Secure multi-cloud infrastructure and get audit-ready reports for HIPAA, GDPR, and NIST CSF with Log360.
To learn more,
Sign up for a personalized demoThis content has been reviewed and approved by Ram Vaidyanathan, IT security and technology consultant at ManageEngine.
