Direct Inward Dialing: +1 408 916 9890

Secure delegation isn't just a feature—it’s a necessity, especially in a cloud environment as vast as Microsoft 365. Whether you're a MSP supporting dozens of client tenants or a business entrusting your digital environment to one, the stakes around identity, access, and administrative control are higher than ever.
MSPs need to manage multiple tenants efficiently—ensuring no data gets mixed up, while maintaining client trust at every step. Meanwhile, clients face a delicate balance: grant too much access and risk exposure; grant too little, and compromise efficiency.
To meet this challenge, Microsoft Entra ID introduced granular delegated admin privileges (GDAP). GDAP gives MSPs targeted access to customer environments—no more blanket permissions, no more “all-or-nothing” delegation. For customers, that means tighter oversight. For MSPs, it signals a shift toward more responsible, role-based management.
But understanding how GDAP works, and how it fits into your operational model, can be challenging. In this blog, we’ll explore what GDAP is, and how it redefines MSP-customer trust through a high-level view of how it’s set up, and how this approach can be improved.
GDAP allows MSPs to request specific roles—like User Administrator, Helpdesk Administrator, or Directory Reader—and apply them only to the customers and users they manage. The result is least privilege access: partners receive exactly what permissions they need over their customers' tenants, no more, no less.
This benefits both sides:
GDAP integrates into Microsoft’s broader identity framework. Roles are scoped and assigned through Microsoft Entra ID, and access is managed via the Microsoft Partner Center using a secure, invitation-based workflow.
GDAP refines how MSPs interact with customer tenants through role-scoped access, identity separation, and explicit consent workflows.
Each GDAP relationship is established through a delegation offer, sent via the Microsoft Partner Center. Once accepted, a security group in the partner tenant is granted specific Entra ID roles—scoped only to the customer tenant in question. These roles are assigned through Microsoft Entra ID and governed by an RBAC system.
These GDAP-linked security groups are nested within the Admin agent group, which Microsoft uses to map partner access across services. This grants Owner permissions across all Azure subscriptions associated with the customer tenant. GDAP access can be configured to expire, allowing time-bound permissions that reduce long-term exposure. MSPs can manage multiple GDAP relationships simultaneously, each with different scopes and duration for each customer.
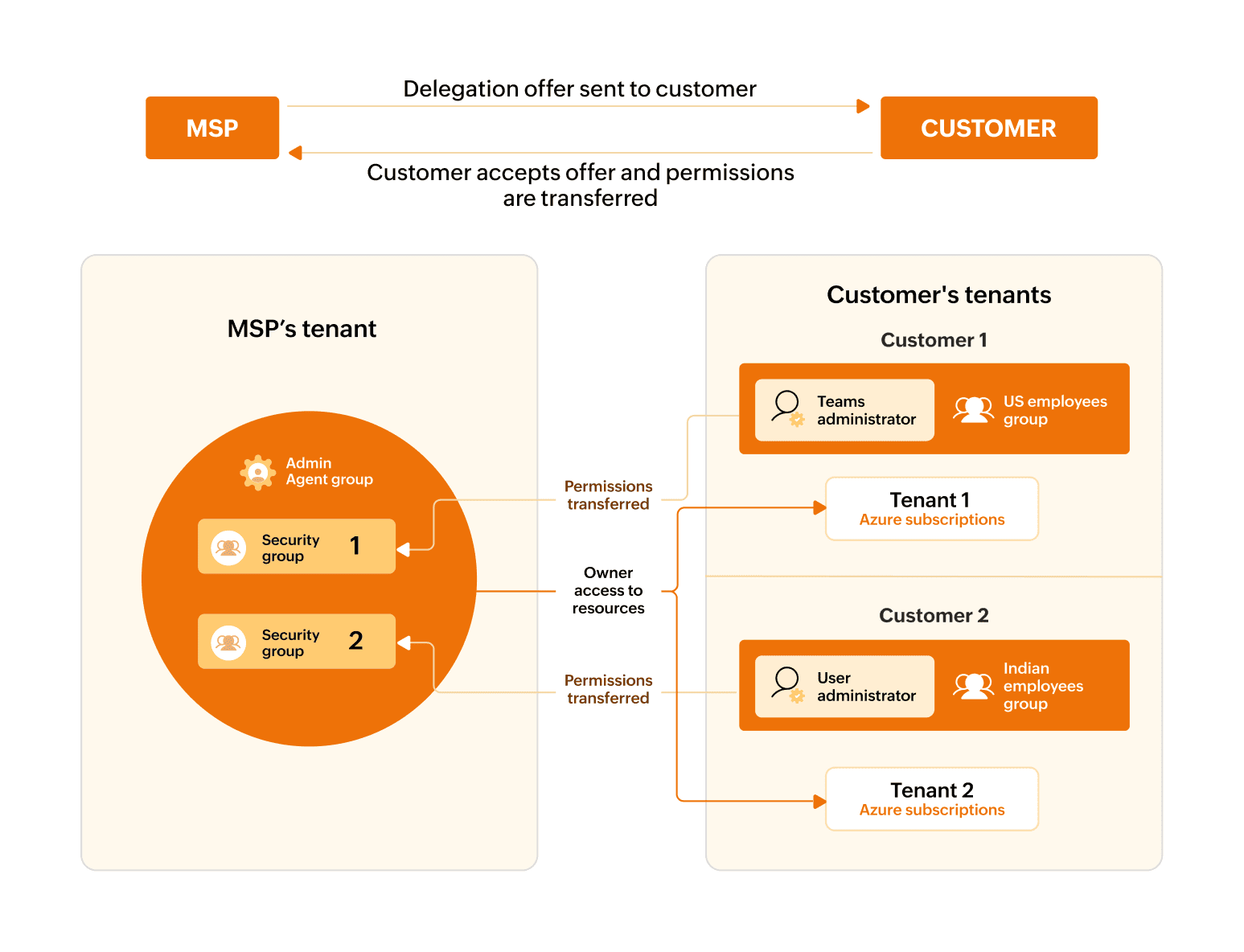
Customers retain administrative control over these relationships. They can view GDAP assignments in the Microsoft Entra Admin Center, review role scopes, and revoke access at any point—without partner involvement. This reinforces access transparency as a technical and operational baseline.
Setting up GDAP requires coordination between the MSP and the customer tenant, and alignment with Microsoft’s Partner ecosystem. The process spans both Microsoft Partner Center and Microsoft Entra ID, and must be repeated for each customer and each role configuration. Here are the steps to set up a GDAP relationship between a MSP and a customer's tenant.
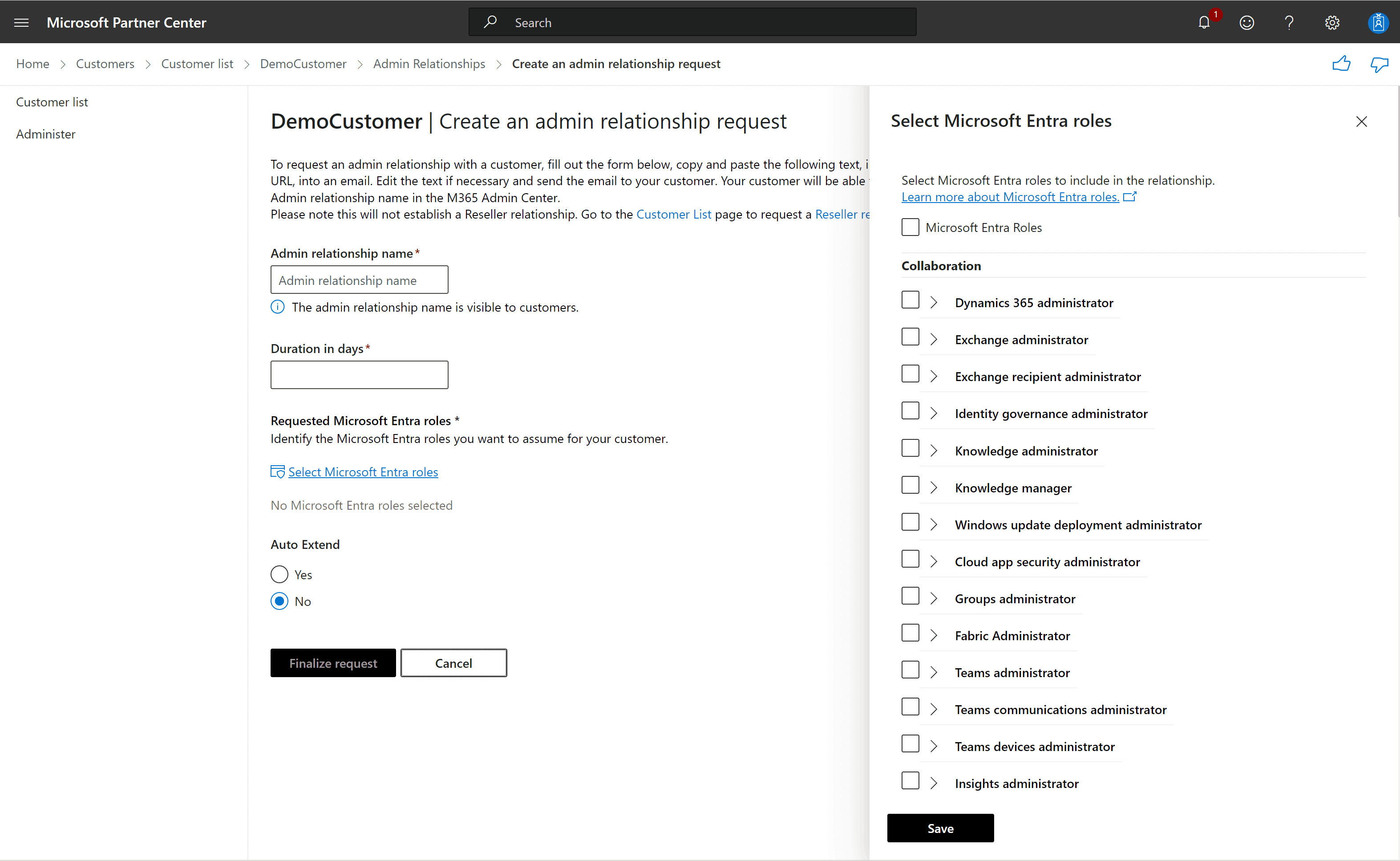
The MSP begins by creating a delegation offer for the target customer tenant. This offer includes a list of Entra roles being requested, a defined access duration, and an approval link. The roles requested should reflect the operational needs of the MSP’s technicians, such as Helpdesk Administrator, User Administrator, or Directory Reader.
The offer is inactive until the customer manually approves it. Microsoft does not notify the customer; the MSP has to to share the request link manually with their clients.
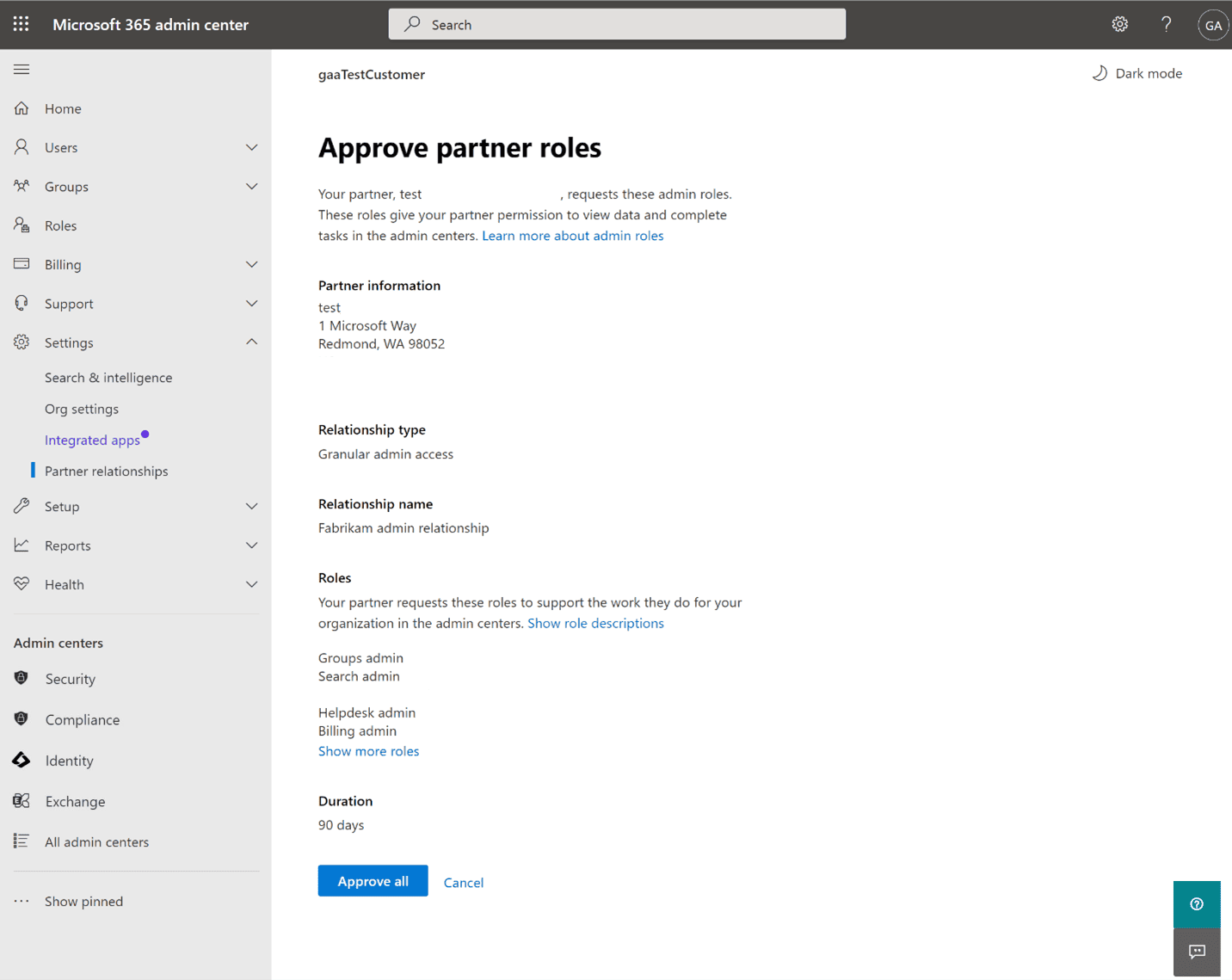
The customer opens the request link and authenticates using a Global Administrator account. They are presented with the exact role scopes, access duration, and relationship metadata. Once approved, the GDAP relationship becomes active and visible in both tenants.
If the customer does not agree to the roles mentioned in the link, the offer cannot be edited to include the roles and has to be declined. The MSP then has to create a new delegation offer based on the requirements of the customer.
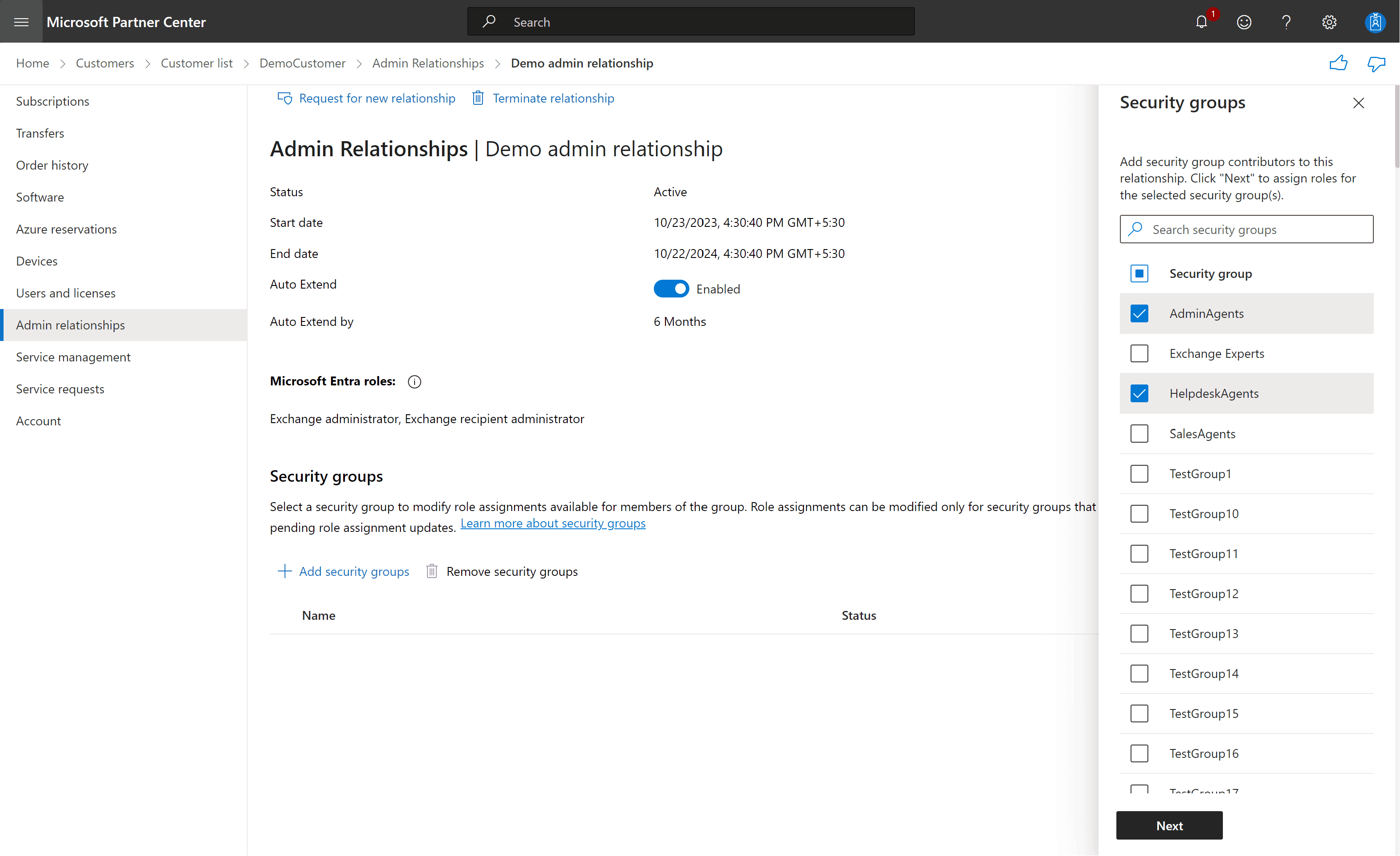
After approval, the MSP must assign the approved roles to security groups in their own Microsoft Entra tenant. Each role is linked to a specific group, and only members of that group inherit the delegated access when operating within the scope of the customer tenant.
These security groups are nested under the Admin agent group, which defines the access boundary for GDAP-related operations. Role assignments are effective only when this structure is correctly configured.
GDAP relationships are configured with expiration dates to ensure that access is reviewed periodically. By default, Microsoft sets a two-year validity for relationships, but custom duration can be defined at the time of offer.
Partners also have the option to enable auto-extension, which renews access just before expiry. Without this, all permissions will expire unless manually renewed, and access to the customer tenant will be revoked.
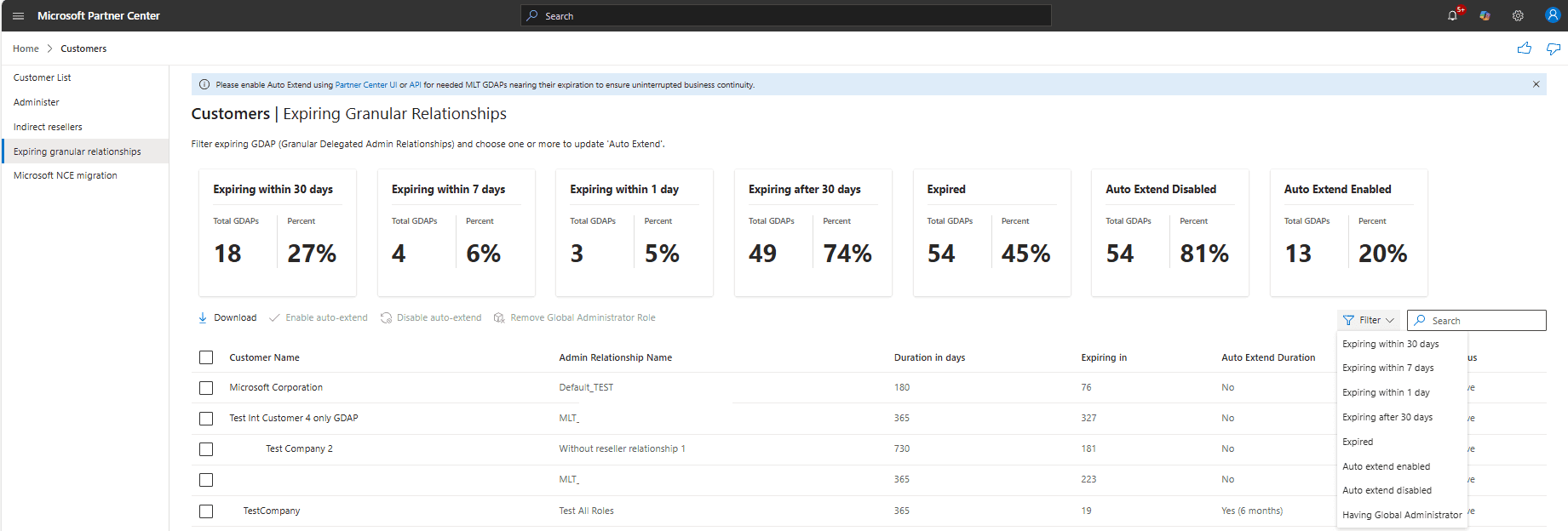
All GDAP-related events are logged and accessible through the Partner Center by the MSPs. These include relationship creation, approval, role assignment, and expiration events. Activity logs can be exported for auditing, troubleshooting, or internal review.
The activity log displays the following columns:
GDAP is a step forward from legacy DAP. It introduces clarity, enforces least privilege, and aligns with modern Zero Trust practices. But for MSPs managing multiple customer tenants, scaling GDAP comes with real operational cost.
Each GDAP relationship must be created individually. For every customer, the MSP must define roles, generate approval links, wait for manual acceptance, and map roles to security groups. This process has to be repeated for each tenant or for new roles and permissions.
There’s no native support for bulk onboarding or automation of role mapping across tenants. Without custom scripting or third-party tooling, managing dozens of GDAP relationships becomes time-intensive and error-prone.
All delegation flows are tied to the Partner Center. This creates a dependency on Microsoft’s tooling ecosystem—not just for setup, but for ongoing management. MSPs must maintain partner status, eligibility, and Microsoft compliance just to keep GDAP operational.
While GDAP offers more control to your MSPs, role scoping is still tied to Microsoft Entra ID’s predefined admin roles and custom permissions which are not granular. MSPs cannot define task-specific permissions beyond those boundaries—for example, limiting a technician to only reset passwords, but not modify attributes.
GDAP is secure—but rigid. For MSPs managing a growing client base, its structure adds complexity where flexibility is often needed. Alternative delegation models can help reduce this overhead—without sacrificing control.
For MSPs seeking more granular control than what GDAP roles allow, ManageEngine M365 Manager Plus, a comprehensive Microsoft 365 administrative solution, is an efficient alternative. It is built for individual organizations and MSPs alike, combining granular delegation, multi-tenant management, automated reporting, and detailed auditing within a single unified interface.
Its capabilities extend far beyond the Partner Center and Microsoft 365 Admin Center—enabling partners to provision users, execute tasks, track changes, generate reports, and enforce role boundaries without relying on Microsoft’s native role model or delegation flows.
Some of these capabilities include:
M365 Manager Plus supports multi-tenant management from a single console, with no dependency on Microsoft Partner Center. MSPs can onboard all customer tenants centrally and manage them in parallel—eliminating the need to recreate delegation flows tenant by tenant.
The delegation model in M365 Manager Plus goes beyond predefined Microsoft Entra roles. Admins can define custom scopes based on:
This enables precise control over what each technician can access and do—without relying on fixed Microsoft admin roles.
M365 Manager Plus introduces the concept of Virtual Tenants: logical groupings that allow scoped delegation within or across real Microsoft 365 tenants. This means MSPs can isolate workloads, restrict visibility, and enforce internal or customer-specific boundaries—down to the user level.
All actions performed by M365 Manager Plus technicians are automatically logged and can be audited. MSPs can track who did what, where, and when—across all tenants—without having to export logs from multiple Microsoft portals.
M365 Manager Plus is a stand-alone platform. It doesn’t require Microsoft Partner Center, GDAP offers, or Azure Lighthouse. This eliminates eligibility barriers, access delays, and the need to manage Partner Center compliance for each customer relationship.
Download the free, 30-day trial of M365 Manager Plus to explore these features and capabilities for yourself. Contact us for a free, personalized demo to discover how to best secure your Microsoft 365 environment using these features.