PAM360 Software Development Kit
The PAM360 Software Development Kit (SDK) empowers developers with a predefined set of software requirements tailored for crafting their applications with the PAM360 ecosystem. By furnishing a collection of libraries and meticulous documentation, the PAM360 SDK aids developers in constructing applications compatible with specific platforms, operating systems, programming languages, or frameworks with the required privileged operation to be performed from PAM360.
Comprehensive in scope, the SDK encompasses a rich repository of PAM360 REST API coding examples, facilitating seamless integration of privileged access management functionalities into custom applications. Designed to streamline the development journey, SDKs furnish developers with reusable components and resources, simplifying intricate tasks such as resource access, account management, and user interaction within PAM360.
The SDK was created to allow users to write scripts for applications, microservices, etc, to access PAM360 privileged information without having to write code to directly access the REST APIs. By leveraging the SDK, developers can efficiently embed privileged access management capabilities into their applications, ensuring robust security and seamless functionality within the PAM360 environment.
This help document will walk you through the steps involved in setting up the SDK for the PAM360 users and deploying it on the desired endpoints. It covers the following topics:
- SDK Terminologies
- SDK Roles and Permissions
- SDK Environmental Requirements
- PAM360 SDK Files
- Registering a Policy in PAM360 for SDK
- Deploying PAM360 SDK in Services/Applications
- SDK Application Management
1. SDK Terminologies
| Term | Description |
|---|---|
Authentication Token | A unique token generated during the user creation to access PAM360 with allowed SDK functionalities. |
SDK Policy | A mapping method to provide users with the respective PAM360 access in the SDK deployed application. |
Registration Token | A token generated during policy creation. This token is used by the user to register their SDK deployed application with PAM360 to gain access to allowed PAM360 privileged actions in their applications. |
Application | Any software or service where the SDK will be deployed by the PAM360 users. |
2. SDK Roles and Permissions
PAM360 users can utilize the SDK if they have been granted access by the administrator and possess a registration token obtained through a registered policy mapped to their user accounts. To grant users SDK access, create a policy for SDK usage, and oversee deployed SDK applications in PAM360, individuals must hold one of the following roles:
- Privileged Administrator
- Administrator
- Custom role with 'SDK Application Management' operation enabled
3. SDK Environmental Requirements
To effectively utilize the SDK, ensure the following prerequisites are met as required:
- PAM360 Version: The SDK is compatible with PAM360 version 6700 and above, and requires SDK version 1.0.00 or later.
- Development Environment:
- Java SDK: Java SDK requires Java application of version 8 or higher.
- Python SDK: Python SDK requires Python application of version 3.12 or higher.
4. PAM360 SDK Files
PAM360 provides the following SDK files to empower the development endeavors:
4.1 Java SDK
Download the Java SDK from the PAM360 interface by navigating to Admin >> SDK Management.
SDK JAR: This core component includes precompiled Java classes and methods of PAM360 APIs that developers can integrate into their projects. It acts like a compressed package containing various class files, resources, and dependent libraries.
Note: This version downloads only the core SDK. Include the following JARS in your project's referenced libraries: commons-logging-1.1.jar, httpclient-4.5.13.jar, httpcore-4.4.9.jar, httpmime-4.5.3.jar and json.jar.
4.2 Python SDK
To access the PAM360 Python SDK, navigate to Admin >> SDK Management in the PAM360 interface and download the Python SDK.
SDK Package: The Python SDK is bundled as a compressed zip file containing the necessary installable SDK package structured within folders. The `pyproject.toml` file within the SDK package provides installation specifications. Additionally, within the `src` folder, you will find the Python SDK source files essential for integrating with PAM360 APIs.
Note: Post-installation of the SDK, ensure that the requests library version 2.31.0 or higher (https://pypi.org/project/requests/) is installed.
5. Registering a Policy in PAM360 for SDK
To integrate the PAM360 SDK into applications, users need to first obtain the necessary SDK files. Additionally, an administrator must register an SDK policy in PAM360 and map it to the PAM360 user's account. This mapping acts as a bridge to provide the required PAM360 access in the SDK-deployed applications. The registration token associated with the policy grants users authentication to PAM360 from the SDK-deployed application.
Caution
- The user for whom the policy is created should possess the user account with the PAM360 SDK access.
- The user can access the PAM360 APIs in their application using the SDK predefined classes and methods based on their role and scope provided in PAM360. For example, a user with the role of Password User can only use the API operations related to the resources and accounts shared with him by the administrator in their application/services.
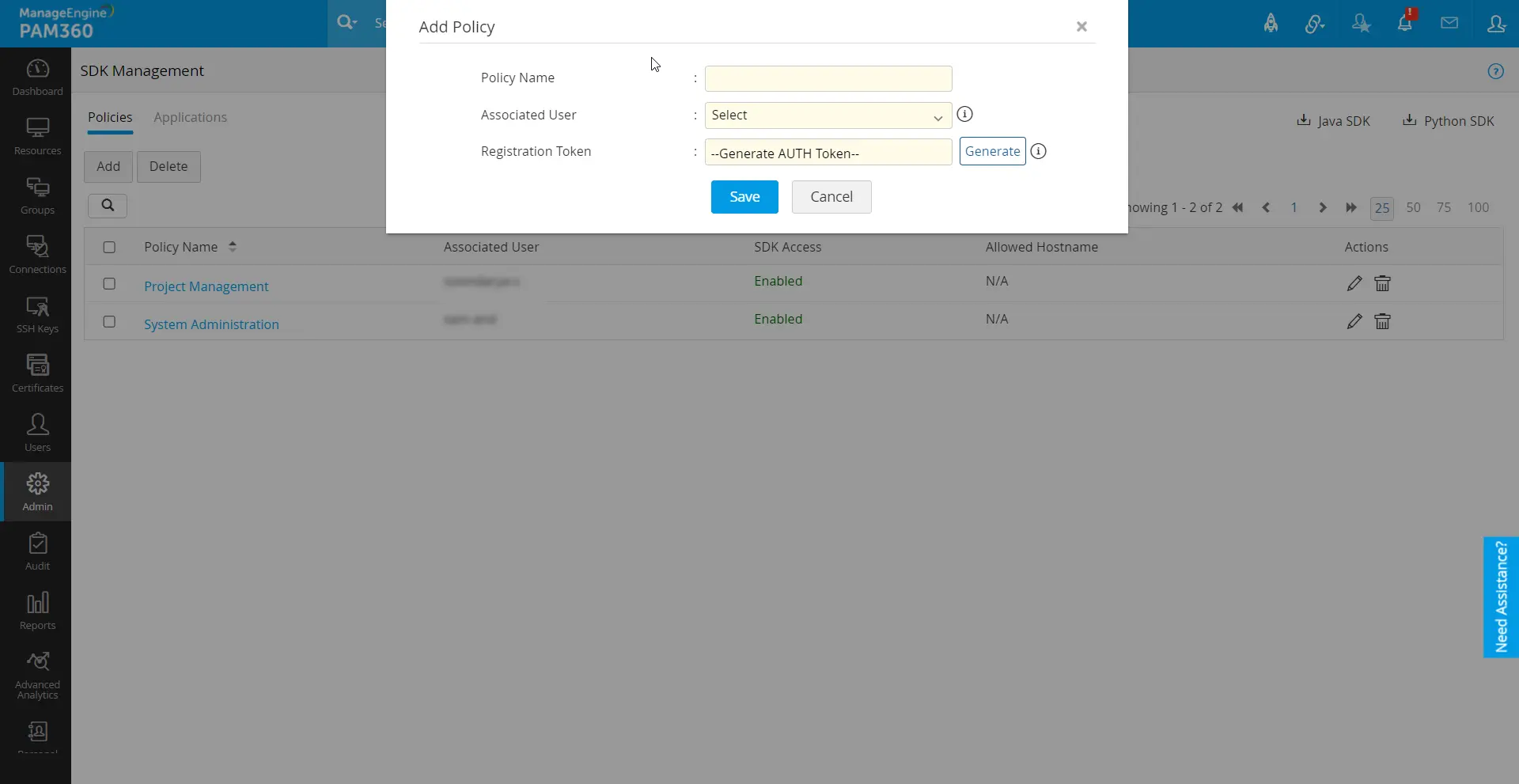
To register a policy for a user with SDK access,
- Navigate to Admin >> DevSecOps >> SDK Management. This page will display a list of existing policies with details such as the associated user, access status, and allowed hostnames.
- From the policy tab, click Add Policy to create a new policy.
- In the dialogue box that opens,
- Policy Name: Enter a descriptive name for the policy.
- Associated User: Select the user for whom the policy is created to perform the PAM360 operations in their application with the PAM360 SDK.
- Click Generate to create a registration token.
- Click Save. Upon saving the policy, the associated user will receive an email containing the registration token for further SDK usage.
5.1 SDK Policy Management
The PAM360 console allows administrators to perform the following actions on existing policies:
- Edit policy details
- Regenerate registration tokens
- Delete policies
Caution
- Deleting an SDK policy will remove all the registered applications associated with the policy.
- The number of applications per SDK policy is subject to limitations based on the users' roles in PAM360. Users with the Administrator Type roles can register a maximum of 3 applications per SDK policy. Users with the End-user Type roles can register a maximum of 10 applications per SDK policy.
5.2 How the SDK Policy Works?
Upon SDK deployment by the users, when the SDK sends a request from the deployed application, PAM360 verifies the source of the request associated with a registration token with the policy associated to the user in PAM360 and provides a legitimate and authorized access to the PAM360 interface.
6. Deploying PAM360 SDK in Services or Applications
After completing the administrative tasks mentioned above, users can proceed to use the PAM360 SDK within their desired programming services or applications. Below are the necessary documentation and guidelines for deploying and registering the PAM360 SDK with relevant DevSecOps services or applications, along with sample API codes.
PAM360 Software Development Kit for DevSecOps: Java | Python
7. SDK Application Management
All applications registered by users with the PAM360 SDK and a registration token are listed here, along with relevant information. Users with respective privileges can view and manage the list of PAM360 registered applications directly from the PAM360 interface.
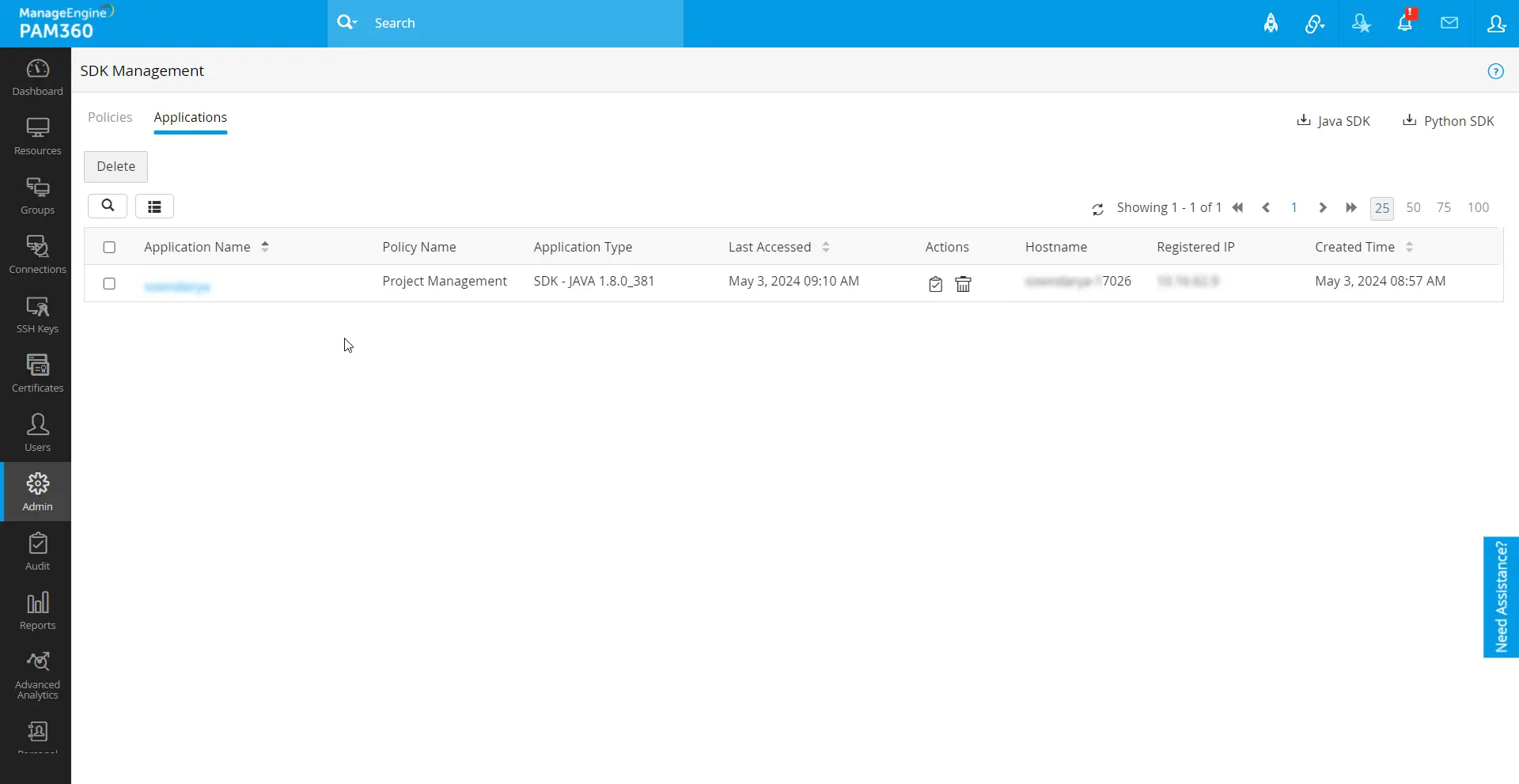
To access this feature in PAM360 , navigate to Admin >> DevSecOps >> SDK Management >> Applications.
- Upon navigation, the page will display a list of applications where the PAM360 SDK is deployed. Each application entry includes information such as the registered Policy Name, Application Type, Last Accessed, Actions, Machine Name, Registered IP, Created Time, and Notes.
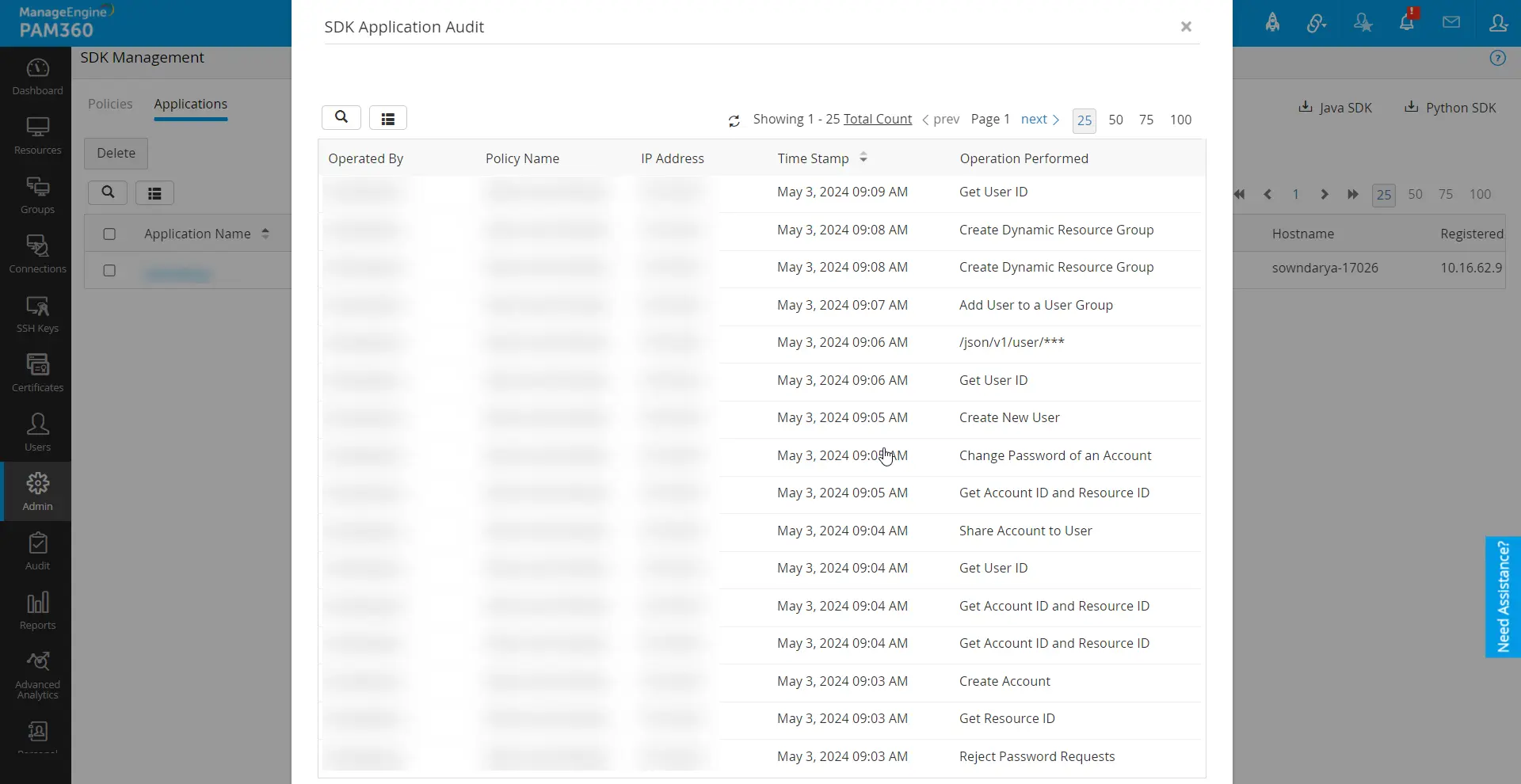
- Administrators can track all PAM360 operations performed in the applications using the SDK Audit button located under the Actions column. This provides an audit trail of activities performed directly from the SDK deployed applications.
- Administrators also have the ability to delete applications, which will unlink the SDK from the registered applications. Deleting an application removes the connection, preventing the application from retrieving data from PAM360 unless it is re-registered.
- Additionally, administrators can edit the application name and add notes for quick identification and reference.