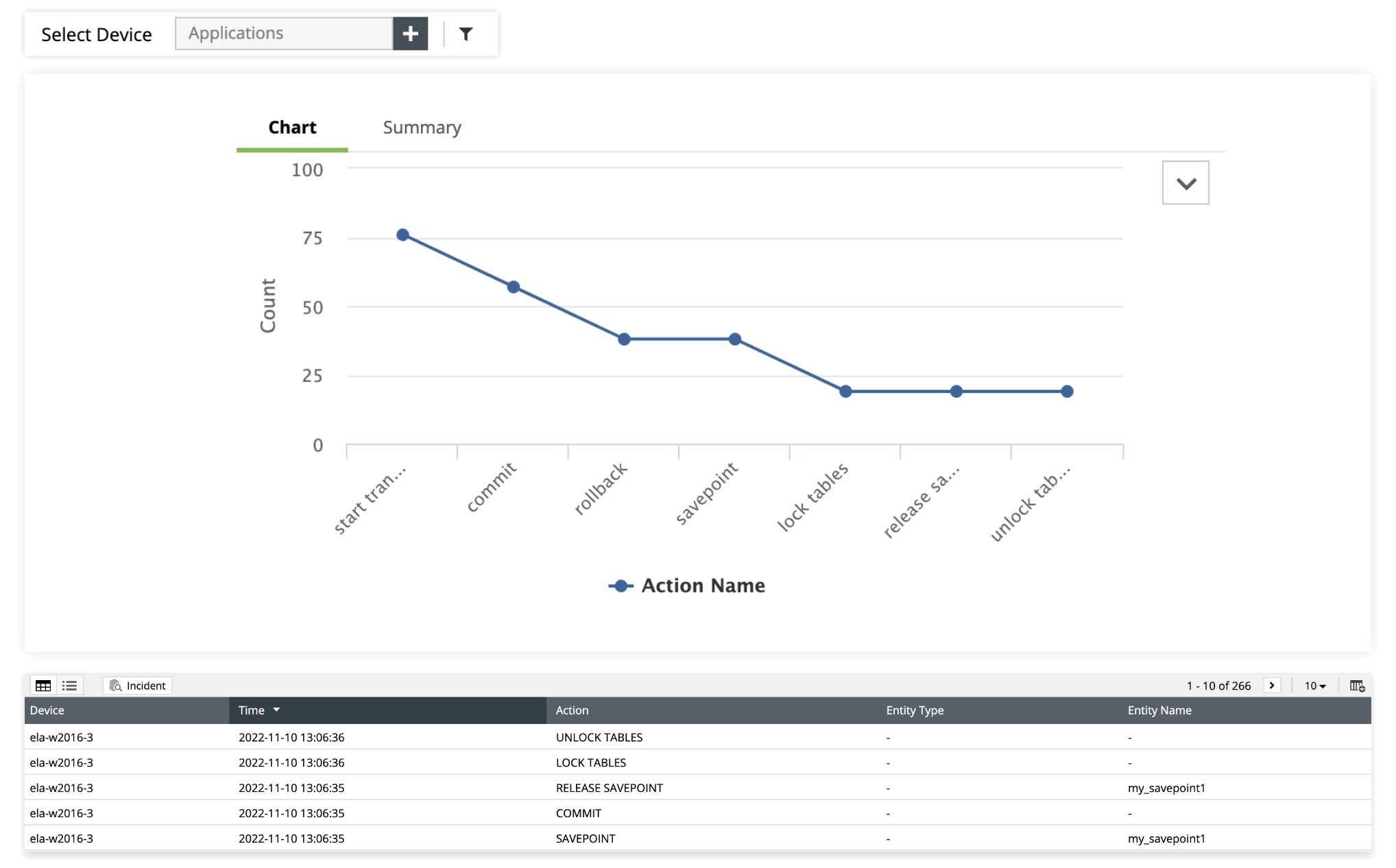
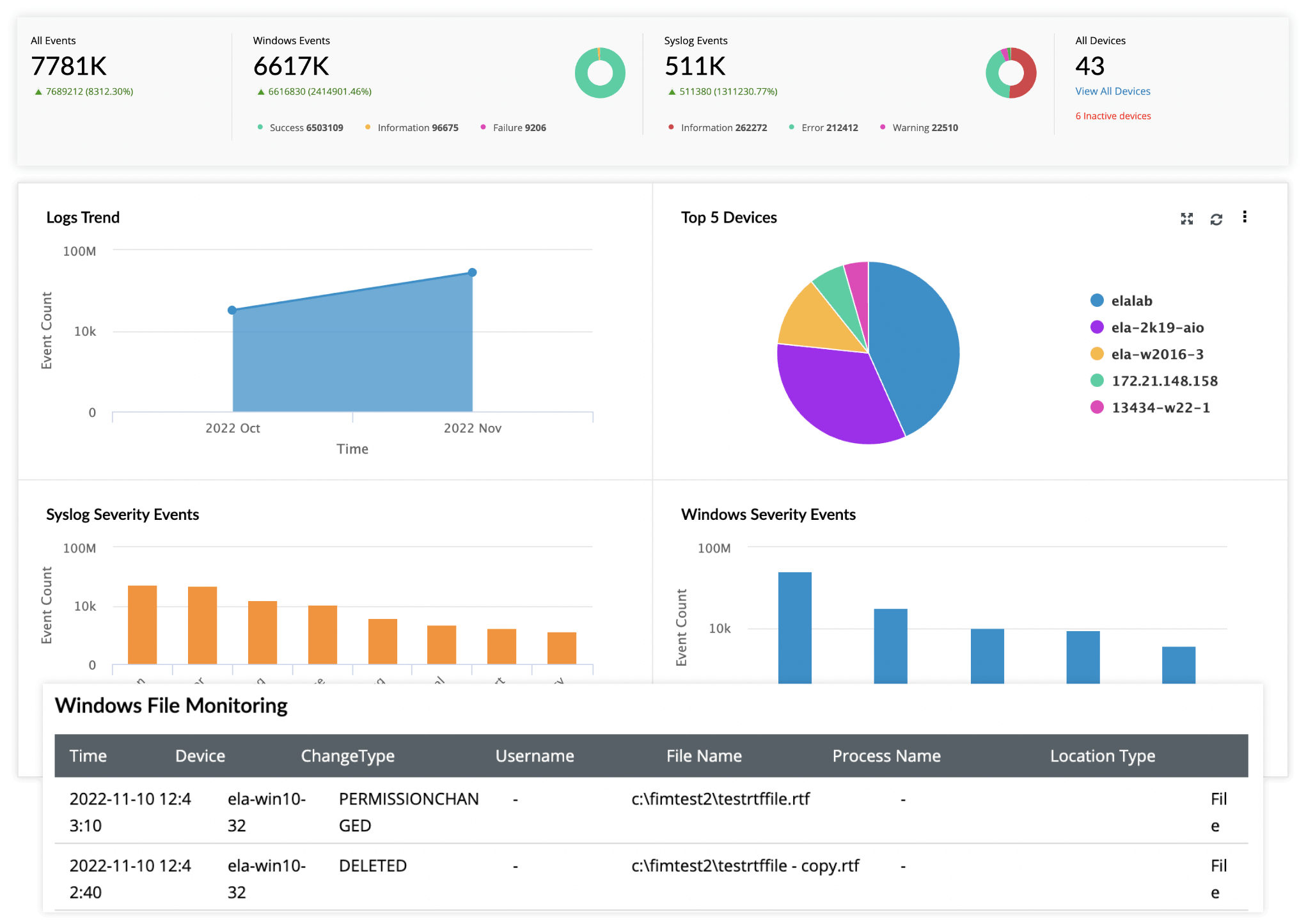
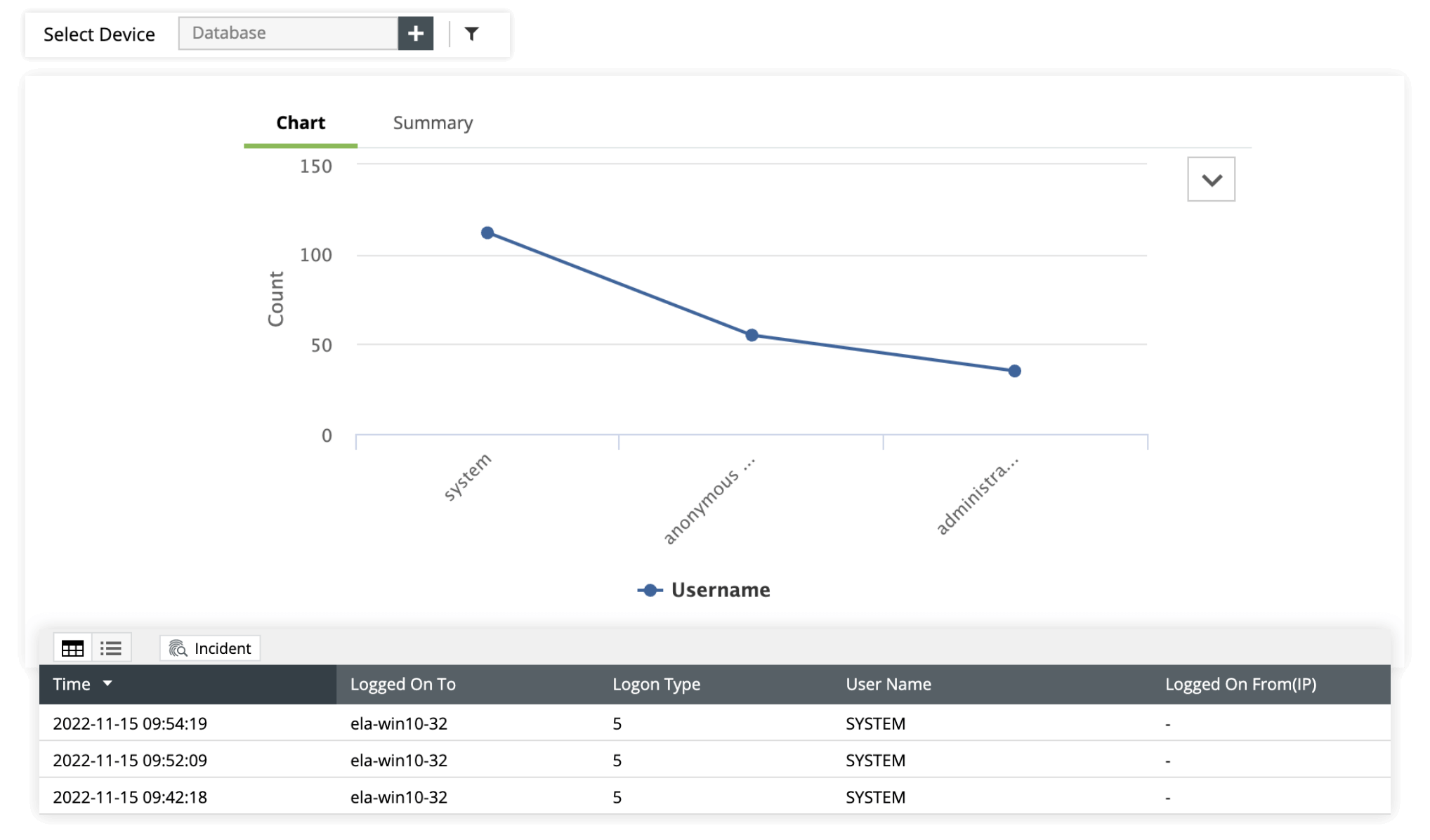
Protect students' educational records by efficiently auditing database and web server activities with EventLog Analyzer. It supports over 750 log sources, including Microsoft SQL Server databases, MySQL databases, Oracle databases, Apache web servers, and IIS web servers.
Audit changes made to sensitive files and folders with real-time, in-depth, graphical reports and intuitive dashboards. Customize compliance reports for internal audits, analyze logs comprehensively, and get real-time alerts when suspicious events are detected.
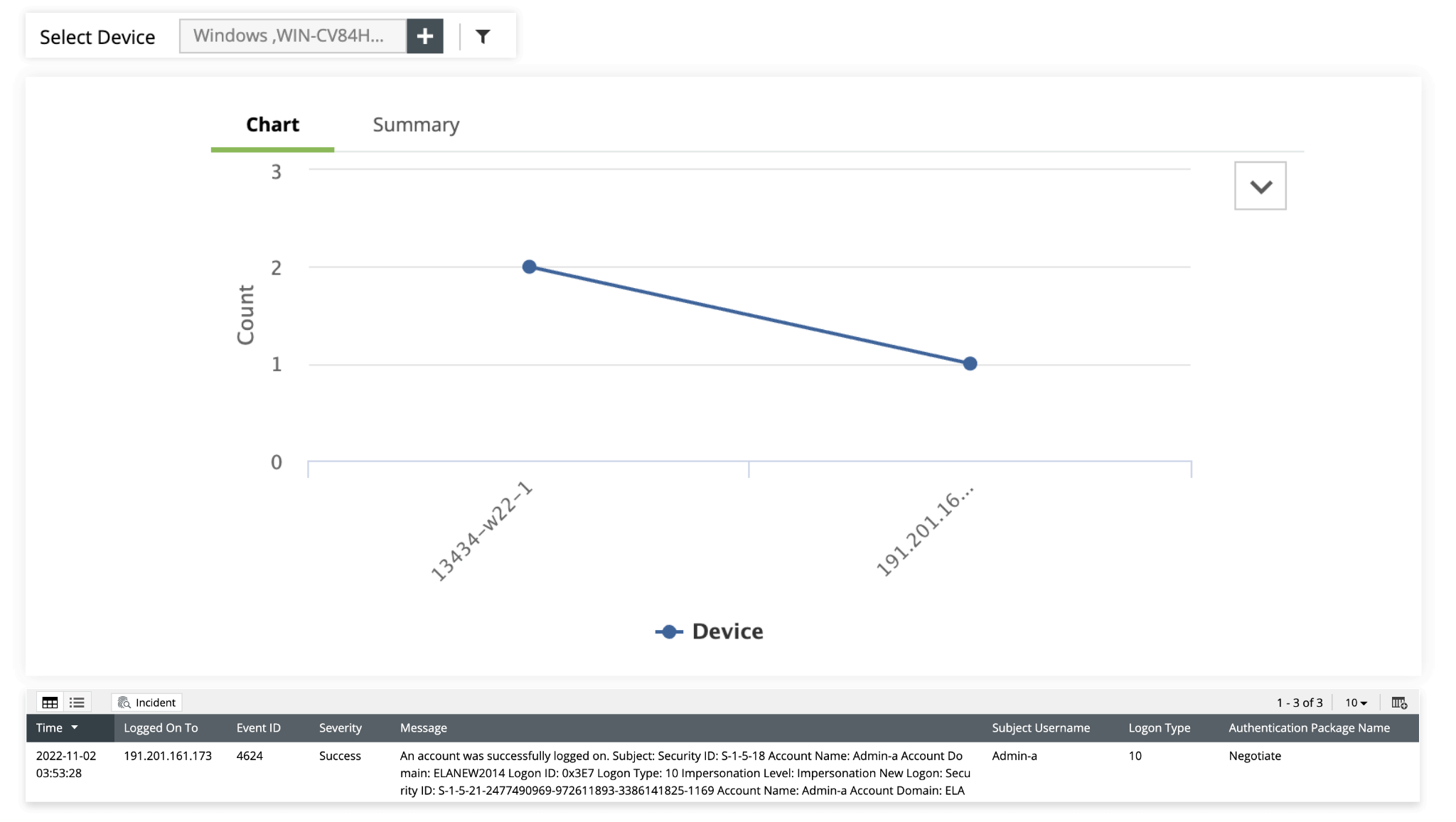
With over 30 predefined correlation rules, EventLog Analyzer's correlation engine identifies suspicious attack patterns in your network and notifies you immediately. With EventLog Analyzer's correlation reports, detect prominent threats, including brute-force, database, and web server attacks (such as malicious URL requests, SQL injection attempts, and DDoS).
With EventLog Analyzer's incident response workflows , perform quick, responsive actions, like disabling compromised accounts or terminating processes, when a suspicious event is detected.
By utilizing the latest threat information obtained from open-source and commercial threat feeds, EventLog Analyzer detects and mitigates malicious IP sources and URLs.