Log Management: Goals, Tools, and Best Practices
- What is log management?
- Getting started with log management
- How log management tools can help
- Log management processes
- How to choose log management solution
- Benefits of log management software
- Log management challenges
- Log management best practices
- Top log management tools
What is log management?
Log management is the systematic practice of collecting, storing, analyzing, and disposing of the log data generated by IT systems. This vital function provides insights for networking professionals to troubleshoot issues and optimize IT infrastructure performance, and helps security professionals with crucial insights to identify threats, conduct forensic analysis, and maintain compliance with regulatory standards.
Getting started with log management
Effectively managing log data is crucial for maintaining system health, ensuring security, and gaining operational intelligence. This section delves into the steps to getting started with log management. By following these steps, you can transform your log data from a burden to a valuable asset. This drives proactive troubleshooting and informed decision-making.
Define your log management goals
Identify what you hope to achieve with the implementation of a log management process. Define your goals, whether your focus is on strengthening security, ensuring regulatory compliance, addressing troubleshooting needs, or a combination of these objectives. Defining your objective is crucial as it helps align your business priorities and helps you select the right set of tools and technologies.
Inventory your logs
Upon goal definition, the next step is to discover and catalog your log sources. This could be your servers, network devices, business applications, cloud sources, workstations, endpoint devices, and more. Understand the volume and type of logs being generated from each of the sources. According to your goals, select and audit the logs from specific sources. Identifying your log sources and determining the volume of log data to manage is crucial when choosing log management software. For instance, if user monitoring is one of your goals, you need to enable access and security logging in workstations, servers, and domain controllers. The volume of log data to be analyzed from these sources will be huge.
Click here to know more about how EventLog Analyzer can efficiently monitor usersSelect the right log management tool
Choosing the suitable log management tool depends on a lot of factors including your IT budget, log management goals, and log source catalogs. These factors determine whether you need to go for a free or open-source log management tool or a commercial log management software. Let's work this out with an example.
Business goal: User access monitoring.
Log sources to audit: Workstations, servers, cloud applications, network devices, databases, web servers, and other business-critical applications.
Events to be monitored from the above log sources: User logins/logouts, application usage, file accesses, print activity, activity within cloud-based applications used by the organizations, configuration changes, data transfer activities, policy modifications, file changes, and more.
Enabling logging in the sources above will generate a huge volume of data, especially as the volume varies with cloud application logging. Further, to achieve the business goals, choose a log management solution that is scalable. It should be able to handle flexible log volume and come with predefined reports, alerts, and detection rules. These should cover suspicious user activities, failed logons, abnormal file access, unauthorized access attempts, and policy modifications.
Log collection
Once you deploy the right log management solution aligned with your business goals and requirements, the next step is to configure it to collect the necessary log information from your environment. Keep the log source inventory ready and configure the log management tool to collect and process log data from those sources. Most log management tools come with three different options for log collection: agent-based, agentless, and API-based log collection method. Depending on your requirements, choose the log collection method offered by the tool and get the process started. Use the tool to standardize or normalize the logs from various sources for effective analysis. As a log collection best practice, configure log filters to collect only relevant data and avoid information overloads.
Log analysis
After collecting log data, the next step is to analyze the collected logs to extract insights and identify patterns or anomalies that may indicate security incidents, compliance issues, or performance issues. This process helps you proactively detect and address potential threats, ensure regulatory compliance, and optimize system performance for smooth operations.
Alerting and reporting
Every log management tool comes with predefined report templates, automated report generation, and real-time alert notifications. To avoid alert fatigue and speed up the analysis process, it is recommended to pick and enable the alert profiles aligning with your business goals and network environment. Tweak the alert functionality of the log management tool to notify stakeholders of critical events or anomalies detected in log data and generate reports to provide stakeholders with a comprehensive overview of log activity, security posture, and compliance status. This ensures that key stakeholders stay informed and can take necessary actions promptly.
Continuous improvement
The final and most important step in the log management process is continuous monitoring. Constantly reviewing your business goals, realigning strategy, and continuously fine-tuning your log management tool to leverage it to the best. By performing routine maintenance tasks such as log rotation, archival, and system updates, you can ensure the reliability and effectiveness of your log management software. This proactive approach ensures that your log management system remains robust and responsive to evolving needs and challenges.
How log management tools can help business:
Log management software acts as a digital guardian, safeguarding your IT infrastructure and empowering data-driven decision-making for a healthy and secure business landscape. These tools go beyond simply collecting log data from servers and applications. They transform this data into actionable insights allowing faster identification of security threats, performance bottlenecks, and operational anomalies. They provide a real-time, unified view of your IT infrastructure, allowing you to address security problems proactively and optimize resource utilization.
Log management processes
Centralized logging and retention
Your network consists of numerous log sources including workstations, servers, applications, network devices such as firewalls, routers, switches, and IDS/IPS, security tools such as data loss prevention systems, antivirus tools, antimalware solutions, and more. The primary function of a log management software is to collect security, access, and system logs from necessary sources, securely store them in a central location, and provide a centralized console to analyze and access all these logs. Several compliance mandates such as PCI DSS, HIPAA, FISMA, GDPR, SOX, and more also requires enterprises to centrally retain log data for specific time periods for effective forensic analysis.
Learn how to centralize logging and retention in ManageEngine EventLog Analyzer- Centralized logging
- Log retention

Parsing, indexing, and searching
Log parsing is the process of analyzing raw log data, breaking it down into its individual formats and identifying its key elements like timestamps, keywords, user IDs, and event types. Log parsing makes it easier to organize and analyze the logs for the next stage, indexing. Most log management tools come with built-in parsers, thus supporting the analysis of different log formats right out-of-the-box. Further, they also have custom log parsers that provide users with the option to extract additional elements from the raw log data. Indexing is the process of creating a structured catalog. It takes the parsed data and creates a structured index allowing for rapid search and retrieval of specific events within vast log volumes. Indexing is the process of having predefined categories and summaries for each log entry, making them easily discoverable through search queries. Log management software often has high speed indexing and searching capabilities because they deal with voluminous log data.
Learn how to parse, index, and search log data using EventLog Analyzer- Custom log parser
- Indexing and searching
Real-time log monitoring
One of the critical capabilities of log management systems is transforming passive logs into active insights with real-time log monitoring. Imagine a live feed of your entire IT infrastructure, constantly analyzing log data streams as they're generated. Live log monitoring of critical systems such as database servers can help you deal with slow query executions or unauthorized access attempts to sensitive folders and web servers can help you detecting slow response times or launch of a DoS attack. This enables immediate identification of anomalies, potential security threats, and performance issues.
Learn how to monitor logs using EventLog Analyzer- Real-time log monitoring
Cloud logging
Centralized logging has become essential especially in multi-cloud environment. Cloud logging capabilities of log management tools act as a central hub, gathering log data from diverse cloud infrastructure including AWS, Microsoft Azure, GCP, and other cloud providers. This eliminates the need to manage multiple log repositories and provides a single platform for all your cloud logs. Imagine having a unified dashboard where you can access logs from your cloud servers, databases, containerized applications, and more, all in one place.
- Cloud logging
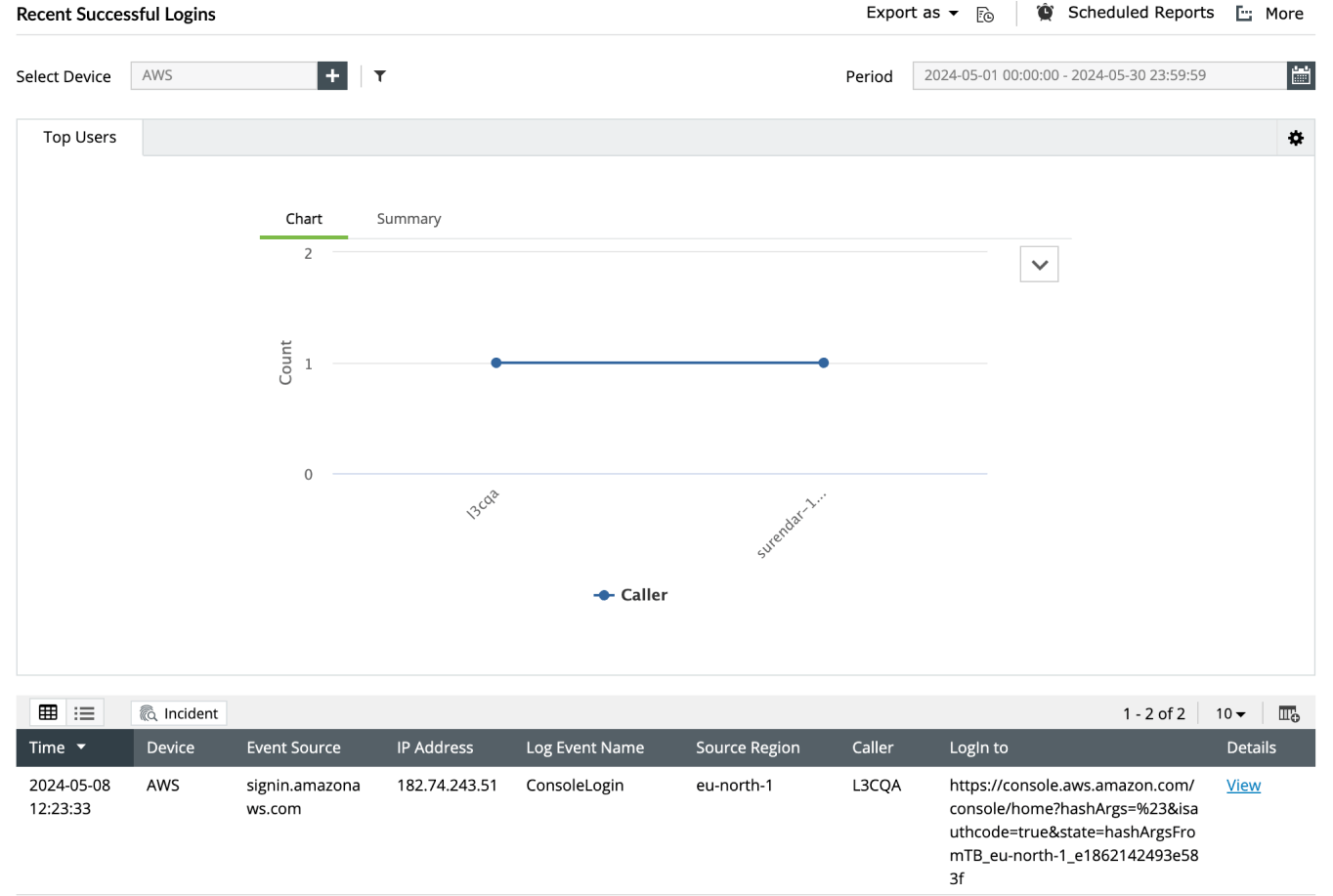
Log analytics
While log monitoring is about real-time monitoring of log data for minimizing downtime, ensuring security, and optimal system health. Log analysis is about searching, filtering, and correlating through the collected logs over time to detect security or operational issues. Log analytics enables you to uncover trends, root causes of issues, and hidden patterns that might escape real-time monitoring. Log monitoring provides immediate alerts, while log analysis helps you understand the "why" behind events. Together, they empower you to not just react to problems, but proactively prevent them and optimize your IT environment.
Learn how to analyze logs using EventLog Analyzer- Log analytics
Automated reporting and real-time alerting
Log management tools extend beyond just data collection, storage, monitoring, and analysis. They offer functionalities that transform you from a reactive observer to a proactive decision-maker. Automated reporting and real-time alerting are two such capabilities that empower you to take control of your IT environment, transforming logs from passive records to a valuable tool for proactive management and data-driven decision-making.
Automated reporting allows you to define report templates with specific data, such as security events or performance metrics and formats (charts and tables). These reports can also be generated at set intervals (daily or weekly), saving time and ensuring consistent data insights. These auto-generation also helps track user audit trails and system monitoring for compliance management.
Real-time alerts empowers you to define criteria that trigger automated alerts over email or SMS for critical events like security threats, performance issues, or application errors. This ensures you're aware of situations demanding swift action.
Often, log management tools come with predefined report templates and alert criteria that are needed for effective functioning of network and security operations. They also allow you to customize these templates or create a new one depending on your needs.
Learn how to generate reports/alerts using EventLog Analyzer- Automated reporting
- Real-time alerting
AI/ML and automation
These capabilities within log management software transform how you analyze vast quantities of log data. AI/ML algorithms can identify anomalies, predict potential issues, and automate repetitive tasks like log filtering and alert generation. They ease and improve the efficiency of network and security operations by automatically flagging unusual spikes in errors or suspicious login attempts, freeing you to focus on further investigations or other critical events. By analyzing historical patterns, AI can even predict potential problems before they occur, enabling proactive maintenance and minimized downtime. These functionalities empower you to move beyond manual log analysis, allowing you to focus on strategic tasks, optimize your cloud environment, and make data-driven decisions for a more secure and efficient IT landscape.
- AI/ML and automation
- Threat Analytics
Log management solutions - What to choose and why
Choosing a log management solution predominantly depends on your budget and your needs. This section elaborates two different perspectives of choosing a log management solution based on the budget and needs.
Choosing log management solution based on budget: Open source vs commercial log management tools
Open source log management solutions are free to use, which makes them a budget-friendly option for small to medium-sized businesses with limited resources. However, deploying and maintaining open source log management tools can be complex and resource-intensive, demands strong technical expertise. Scalability can also pose challenges, as some platforms may not be optimized to handle large-scale log data efficiently. Additionally, while community-driven support is beneficial, it may lack reliability. Some popular open-source log management tools available in the market include Graylog and Fluentd.
On the other hand, commercial log management solutions, though more expensive, offer advanced features and professional support. These solutions are designed to be user-friendly and scalable, providing robust analytics, security integrations, and dedicated customer support to ensure smooth operations. They are ideal for businesses that need comprehensive features and reliable assistance to handle large-scale log data efficiently.
Choosing log management tools based on deployment options: On-premises vs Cloud log management solution
IT resources, scalability, and log management goals are some of the other critical factors that determine the selection of a log management tool. These factors help you determine a log management tool based on the deployment options. If you have less IT resources, need to monitor more sources with high scalability, you can opt for a cloud-based log management solution. On the other hand, if you have security restrictions in log handling, you can prefer on-premises installation. On-premises solutions provide more control over data and customization but can be resource-intensive and require substantial ongoing maintenance. They may be suitable for organizations with specific security or compliance requirements that necessitate keeping data on-site.
Cloud-based log management solutions help collect, store, analyze, and manage logs generated from various cloud services, applications, and infrastructure. These solutions reduce the costs associated with purchasing on-premises hardware and infrastructure. The main advantage of cloud log solutions is their ability to scale with your log volume based on your growing business needs. They offer comprehensive capabilities to ensure seamless monitoring, security, and compliance in cloud-centric setups. Additionally, they can seamlessly integrate with other cloud services, DevOps tools, and IT management systems. Cloud solutions provide automatic updates, backups, and security patches, ensuring that the system is always up to date.
Choose how you would like your log management tool to be deployed
Benefits of deploying a log management software:
Improved visibility and insights
A log management software provides a centralized view of all your log data, offers real-time monitoring, and advanced analytics. This comprehensive visibility allows you to gain deeper insights into system performance and user activities, enabling you to make informed decisions.
Enhanced security posture
With log management software, you can effectively detect threats and enhance your incident response capabilities to protect your assets and sensitive data, while ensuring adherence to compliance standards to reduce the risk of legal penalties.
Streamlined operations and troubleshooting
Log management tools streamline operations by facilitating faster problem resolution and reducing downtime. By improving resource management, you can enhance operational efficiency and productivity.
Cost savings
By implementing log management software, you can achieve significant cost savings through the automation of log collection and analysis processes. This automation reduces the need for manual intervention, lowering operational costs and improving your return on investment.
Scalability
Log management tools are designed to scale with the growing data volumes of enterprises. This scalability ensures that you can effectively manage your log data as your operations expand, without compromising performance.
Improved collaboration
Centralized log data and comprehensive reporting capabilities foster better collaboration among different teams within an organization. Enhanced communication and shared insights lead to more effective problem-solving and project management.
Common log management challenges
Data volume
As your systems scale, the amount of log data increases exponentially. At times, due to security attacks or operational errors, events generated per second may become multifold. This rapid growth necessitates efficient storage solutions and powerful processing capabilities to handle the influx of data. Without adequate strategies in place, you may struggle with data overload, making it difficult to extract meaningful insights and maintain optimal system performance.
Log complexity
Logs come from diverse sources and in various formats, which can complicate the process of effective parsing and normalization. Use common log formats like JSON or Syslog to simplify parsing, analysis, and correlation across different systems and applications to standardize the data for meaningful analysis.
Security concerns
Logs often contain sensitive information such as usernames, passwords, and IP addresses. This necessitates robust security measures to prevent unauthorized access and ensure the integrity of your log data. Implementing encryption, access controls, and regular audits are essential to safeguard this sensitive information.
Alert fatigue
Continuous monitoring of logs is essential, but it inevitably leads to the generation of numerous alerts. This can result in alert fatigue, where you and your team may become overwhelmed by the sheer volume of notifications. As a consequence, critical alerts might be ignored or overlooked, compromising the effectiveness of your log management system.
Log retention costs
Storing log data for a extended period of time can be costly, especially when compliance and regulatory requirements mandate long-term retention. Balancing the need for retaining log data with the associated storage costs is a critical challenge. Efficient data archiving solutions and tiered storage strategies can help you manage these expenses.
Cloud logging challenges
Cloud-based infrastructure adds complexity to log collection and management, necessitating new strategies for gathering logs from distributed systems. Traditional log collection methods may falter in cloud environments due to their inability to scale and adapt to the dynamic nature of cloud-based systems. To manage logs efficiently, you require cloud-native solutions.
Log management best practices
- Network operations
- Security operations
- IT compliance
Goal
Leverage log management tools to ensure smooth network performance and troubleshoot issues efficiently.
Best practices
Collect logs from critical network devices
Ensure you gather data from perimeter network devices such as routers, switches, firewalls, and servers, along with applications that directly impact network performance. This comprehensive approach provides you with a holistic view of your network environment, enabling thorough analysis and effective troubleshooting.
Monitor key metrics
Keep an eye on key metrics such as latency, packet loss, throughput, and resource utilization closely. These metrics offer valuable insights into the health and performance of your network, allowing you to identify potential issues before they escalate and impact operations.
Alert on critical events
Setting up alerts for critical events is vital for timely response and mitigation. Configure alerts for:
- Network outages
- Server performance degradation
- Configuration changes
- Suspicious user activities
- Slow query execution
By promptly addressing these issues, you can minimize downtime and ensure uninterrupted network operations.
Integrate network monitoring tools
Integrating your log management software with network monitoring tools enhances your ability to analyze network traffic effectively. This integration streamlines log analysis processes, making it easier for you to identify the root cause of network issues. By leveraging the capabilities of both systems, you gain deeper insights into network behavior and can take proactive measures to optimize performance and enhance security.
EventLog Analyzer's integration with ManageEngine's powerful network monitoring software, OpManager, enables forwarding critical logs for thorough analysis. This integration enables a comprehensive understanding of user behavior, anomaly detection, and threat identification, ensuring a secure and efficient network environment.
Goal
Use log management tools to detect threats, conduct forensic analysis, monitor user activities, and respond to incidents.
Best practices
Collect security-focused logs
Ensure comprehensive coverage by including logs from critical security components such as firewalls, intrusion detection systems (IDS)/intrusion prevention systems (IPS), user authentication systems, and application security logs. This holistic approach provides a robust foundation for threat detection and forensic analysis.
Monitor key security metrics
Continuously monitor key security metrics to proactively identify potential threats and vulnerabilities. Track security events detected by your systems, login attempts, and any suspicious resource access, enabling rapid response to security incidents.
Alert on critical security events
Implement alerts for critical security events to enable timely response and mitigation. Set up alerts for indicators of compromises, such as:
- Malware detection
- Unauthorized data or resource access attempts
- Denial of service (DoS) attacks
- Privilege escalations
- Lateral movements
- Data exfiltration
These alerts serve as early warning signals, helping to minimize the impact of security breaches:
Utilize SIEM systems
Integrate log management systems with security information and event management (SIEM) solutions for advanced threat detection, correlation, and incident response capabilities. SIEM systems provide sophisticated capabilities for log analysis and visualization of security events across your infrastructure, empowering security teams to detect and respond to threats more effectively.
Maintain log integrity: Ensure the integrity of your log data to support reliable forensic analysis and compliance requirements. Implement measures to safeguard logs from tampering or unauthorized alterations, such as implementing cryptographic hashing or digital signatures. Maintaining log integrity is essential for preserving the authenticity of forensic evidence during incident investigations.
Goal
Utilize log management software to monitor user activity, financial transactions, system configuration changes, and sensitive data access to meet compliance requirements.
Best practices
Track compliance metrics
Regularly generate detailed audit reports to gain insights into your compliance status and identify areas for improvement. Maintain comprehensive audit trails to track changes, access, and actions within your systems, ensuring accountability and transparency. Continuously monitor data access statistics to detect anomalies or unauthorized access attempts, proactively addressing potential compliance issues.
Alert on compliance violations
Configure alerts for data access control breaches, suspicious activities involving sensitive data, and deviations from compliance standards to enable timely response and mitigation.
Map logs to compliance requirements
Regularly review and update log configurations to ensure that logs capture data relevant to specific regulatory requirements, facilitating accurate compliance reporting and audits.
How to choose the best log management tool?
To find the best log management tool for your organization, consider factors such as your budget, the size and complexity of your IT infrastructure, and your desired level of customization when making your decision.
First, check scalability, whether the tool can accommodate your current and future log volume. Ensure whether it fits with your existing IT infrastructure should be evaluated to ensure seamless deployment and interoperability. Security features, including compliance reporting, must meet regulatory requirements. Check whether the tool is user-friendly, easy to integrate, and its adoption rate among IT staff. Performance and reliability are essential for continuous log monitoring and analysis. Cost and licensing models should be compared for affordability and flexibility. Lastly, assess the quality of support and documentation provided by the vendor to troubleshoot issues effectively. By carefully considering these factors, you can select the best log management tool that fits your organization.
Top log management tools
Here are some of the best log management tools on the market, each with its own strengths and weaknesses:
- EventLog Analyzer
- SolarWinds
- Graylog
- Datadog
- Elastic Stack
EventLog Analyzer
ManageEngine EventLog Analyzer is a comprehensive log management and IT compliance solution that automates the log management process, including log collection, analysis, correlation, search, and archival, all from a single console. With over 750 supported log sources, including Windows/Unix servers, databases, web servers, applications, and network devices such as firewalls, routers, switches, and IDS/IPS, it ensures thorough log coverage. Its advanced analysis capabilities generate over 1,000+ out-of-the-box audit reports and alert profiles, making it a top choice for meeting security, auditing, and compliance needs.
Pricing
ManageEngine EventLog Analyzer not only offers top-notch log management capabilities but also comes at an incredibly affordable price. The professional edition starts at just $595 for up to 50 log sources, with flexible pricing for larger environments and added features.
Pros
Scalability
EventLog Analyzer efficiently handles large volume of log data to accommodate the growing needs of your organization.
Ease of use
EventLog Analyzer offers a user-friendly interface with customizable dashboards, predefined reports, alert profiles, and correlation rules.
Cost-effective
EventLog Analyzer stands out as an affordable log management software compared to other solutions in the market. It offers the most value for your money with its wide range of features.
Customizable
You can easily customize the software to your organization's specific needs and requirements, enhancing its effectiveness in meeting your unique challenges.
Cons
Complexity in advanced features
The initial setup and configuration may be complex for some users, and utilizing advanced features may require additional resources and expertise.
Other rich features
Real-time log analysis
Process log data at 25,000 logs per second to detect attacks in real-time. Continuously monitor logs with real-time analysis to identify and respond to security threats and operational issues.
File integrity monitoring
It continuously monitors critical system files and directories in real-time, detecting any unauthorized changes.
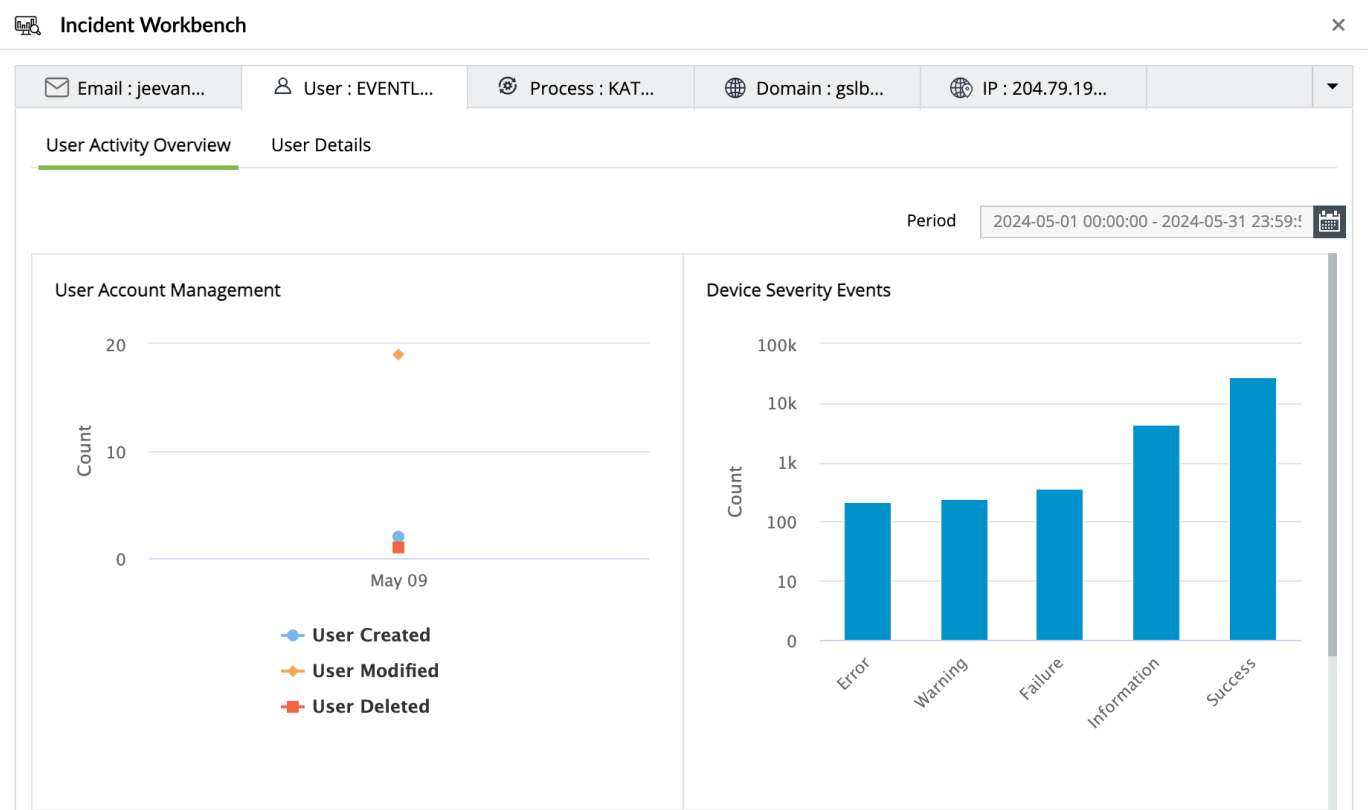
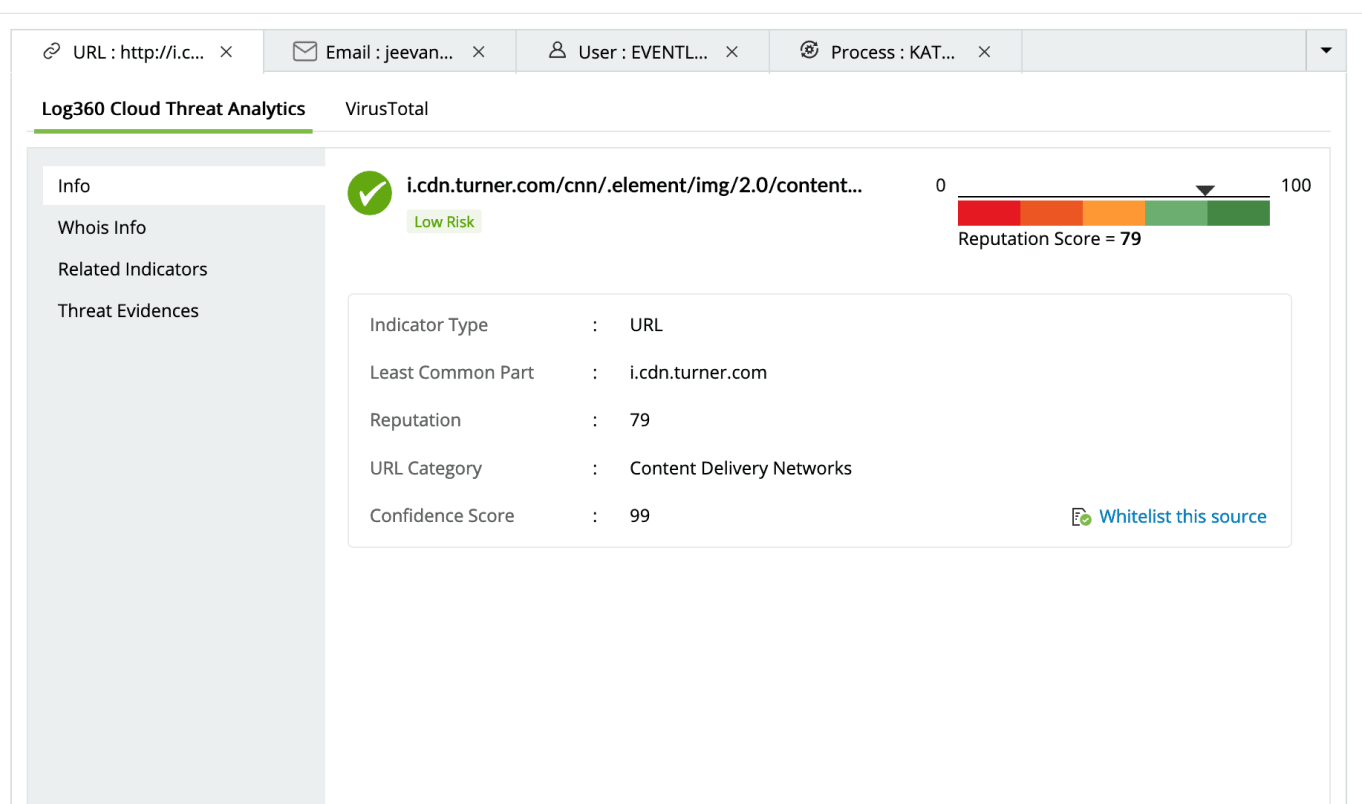
Advanced threat analytics
Assess threat severity including reputation scores for IPs, URLs, and domains. Gain insights into user behavior, threat severity, and process events for comprehensive security monitoring.
Threat intelligence
Receive instant alerts via SMS or email when your network encounters malicious IPs or URLs, leveraging global threat intelligence feeds from STIX, TAXII, and AlienVault OTX.
Compliance management
Access out-of-the-box compliance reports for 25+ regulations. Meet forensic analysis and log archival needs with powerful search and secure archival capabilities.
SolarWinds Log Analyzer
SolarWinds Log Analyzer is a robust log management solution designed to collect, analyze, and visualize log data in real-time. It is particularly suited for IT operations and infrastructure monitoring, helping organizations quickly identify and resolve issues.
Pricing
SolarWinds Log Analyzer offers a subscription-based pricing model. It starts at approximately $1,495 per year for smaller deployments. Larger environments and additional features may increase the cost.
Pros
Integration
It seamlessly integrates with the broader SolarWinds ecosystem, ensures smooth operation with existing infrastructure.
Real-time analysis
With its real-time log analysis capabilities, you can promptly resolve issues as they arise.
Alerting system
Its comprehensive alerting and notification system ensures that you're always aware of critical events.
Cons
Cost
While it offers robust features, SolarWinds Log Analyzer may be more expensive compared to some open-source alternatives.
Complexity
Setting up and configuring SolarWinds Log Analyzer for large environments may require some effort due to its complexity.
Resource intensive
For optimal performance, it can be resource-intensive, requiring significant CPU and RAM.
Graylog
Graylog is a powerful log management and analysis tool that offers real-time log monitoring, parsing, and visualization. It is designed to be user-friendly and scalable, making it suitable for organizations of various sizes.
Pricing
Graylog offers a free open-source version with core functionalities. For more advanced features and enterprise-level support, Graylog enterprise pricing is based on the number of nodes and data volume, with costs starting around $1,500 per node per year.
Pros
Real-time log monitoring
Graylog provides real-time log monitoring and alerting, enabling prompt responses to issues as they arise.
User-friendly interface
The interface is intuitive, with customizable dashboards and visualizations, making it accessible for users of varying technical expertise.
Scalability
Graylog is scalable and can handle large volumes of log data, suitable for both small and large organizations.
Cons
Feature limitations in the free version
The open-source version lacks some advanced features available in the enterprise edition, which might be necessary for larger or more complex environments.
Configuration complexity
Initial setup and configuration can be complex and may require technical expertise, especially for larger deployments.
Resource requirements
While efficient, managing large-scale Graylog deployments can require significant computational resources and careful planning to maintain performance.
Datadog
Datadog is an integrated log management, monitoring, and analytics platform. It provides real-time log analysis and alerting, with extensive integrations for cloud services, applications, and DevOps tools.
Pricing
Datadog’s log management starts at $1.27 per million log events ingested per month, with additional costs for extended retention and advanced features.
Pros
Advanced analytics
Datadog provides advanced analytics and machine learning capabilities, allowing for more sophisticated insights and anomaly detection.
Integration ecosystem
It has an integration ecosystem, supporting a wide range of cloud services, applications, and DevOps tools.
Real-time analysis
The solution enables real-time log analysis and alerting, helping organizations respond quickly to issues.
Cons
Expense
The service can become expensive with high log volumes, especially as additional features and extended retention are utilized.
Learning curve
There is a steeper learning curve for advanced features, which might require additional training and time to master.
Ecosystem dependence
It depends heavily on Datadog’s ecosystem, which might be a limitation if there is a need to integrate with tools and services not supported by Datadog.
Elastic Stack (ELK Stack)
ELK Stack is an open-source log management tool. It offers centralized log collection, storage, and analysis through its three core components: Elasticsearch, Logstash, and Kibana. Elasticsearch provides a robust search and analytics engine, Logstash handles flexible log collection and processing, and Kibana offers intuitive data visualization and dashboard creation.
Pricing
Elastic Stack is free for self-managed deployments. For hosted services, Elastic Cloud starts at $16 per month, with custom pricing for enterprise solutions through Elastic Cloud Enterprise.
Pros
Customizable
Elastic Stack is highly customizable and extensible, supported by a strong community.
Scalability
It offers scalability, flexibility, visualization, and real-time search analytics capabilities.
Cons
Complexity
The complexity of setup and management can be challenging.
Performance issues
Performance issues may arise with very large datasets unless properly optimized.
Resource requirements
You will need significant resources for large-scale deployments.
Here's how businesses leverage EventLog Analyzer to protect themselves
How ManageEngine's EventLog Analyzer helped FMC by balancing security and efficiency
Learn more

Unsure about which log management tool to choose? Look no further.
Experience EventLog Analyzer in action - book a free web demo now!
Find the perfect plan for your business
Annual price starts at $595To assist your evaluation we offer:
- 30-day fully functional free trial
- No user limits
- Free 24*5 tech support
Thanks for your interest in ManageEngine EventLog Analyzer
We have received your request for a personalized demo and will contact you shortly.
Fill this form to schedule a personalized web demo
You can also check out this brief video on the features of EventLog Analyzer.

Considering the options provided, you'll notice that each log management tool has its strengths. However, EventLog Analyzer stands out for its scalability and ease of use. Its affordability and customization options make it a preferred choice among users. With its stellar reputation and comprehensive features, EventLog Analyzer stands out as the top contender in the market.
In conclusion, choosing the ideal log management tool entails a thorough examination of each solution's strengths, complexities, user-friendliness, and cost-effectiveness, aligned with organizational requirements. By meticulously evaluating these factors, you can confidently select the most suitable log management tool that best fits your needs.











