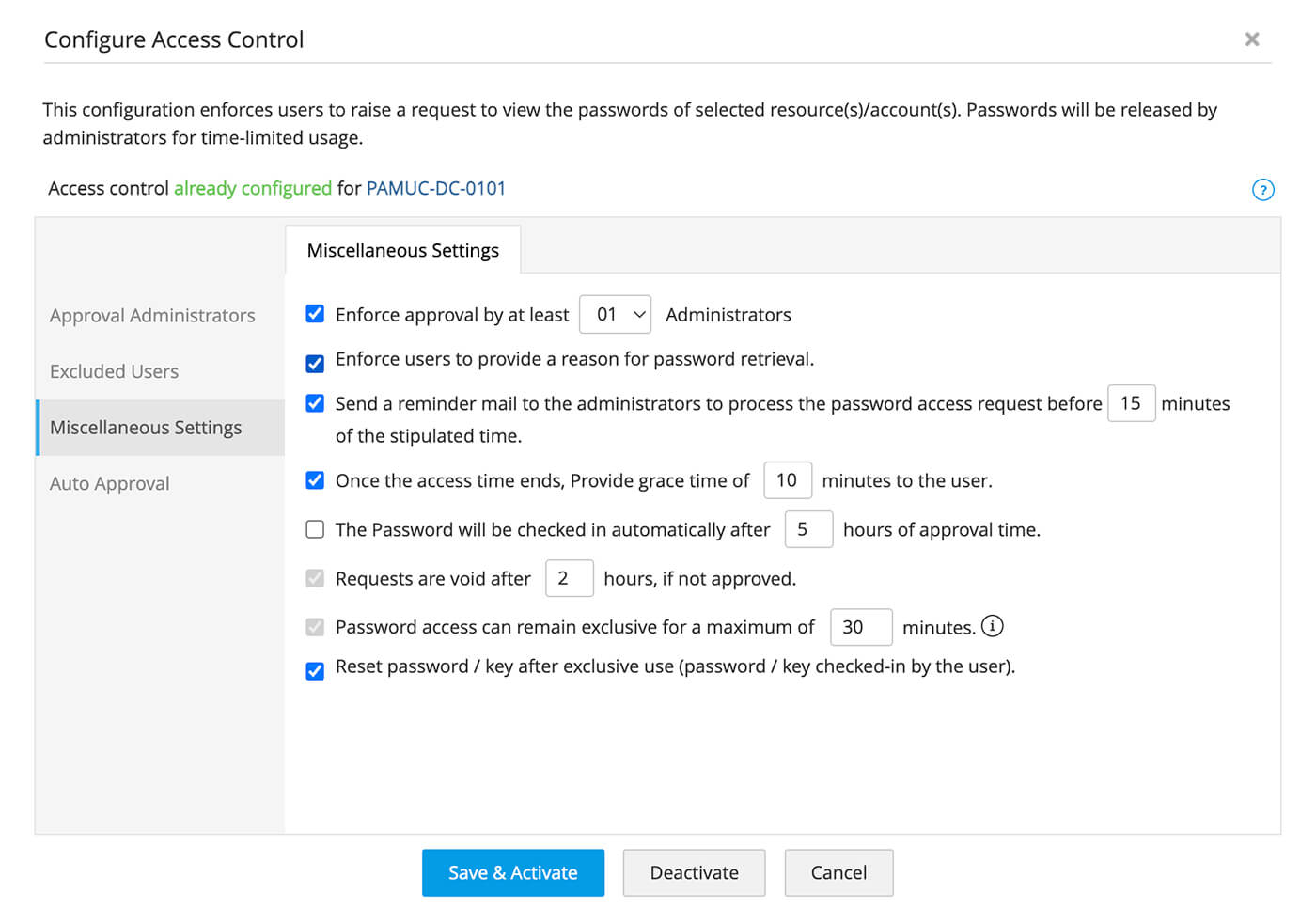
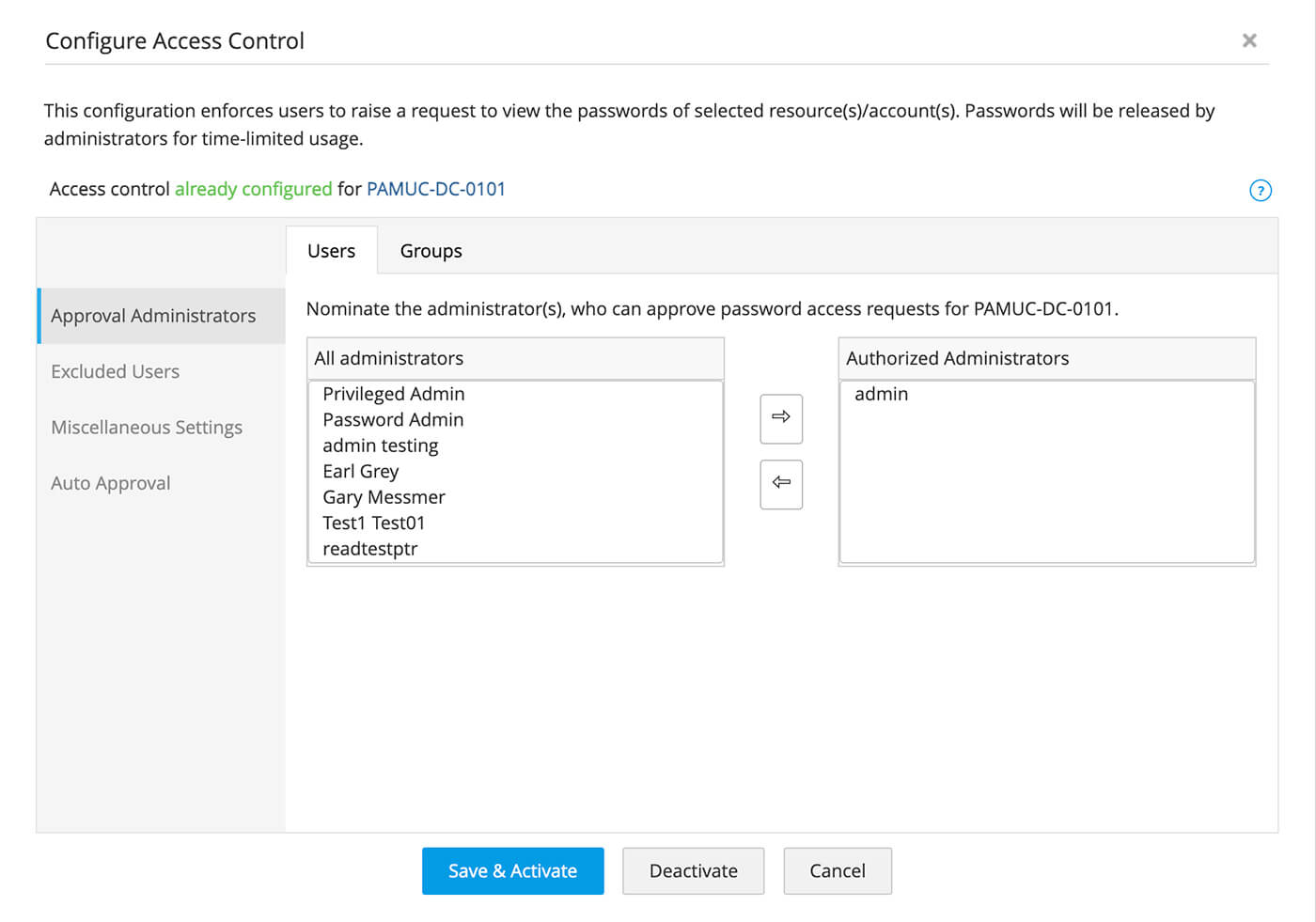
Mandate password request-release workflows
- Enforce password request-release workflows upon privileged endpoints as per your IT policy for all requests.
- Grant privileged users with just-in-time access with appropriate privileges to reduce the risk of standing privileges and unauthorized access attempts.
- Mandate an approval workflow for each access request with administrative approval from multiple individuals.
- Prevent unauthorized access by enforcing automatic password resets after a remote session ends.