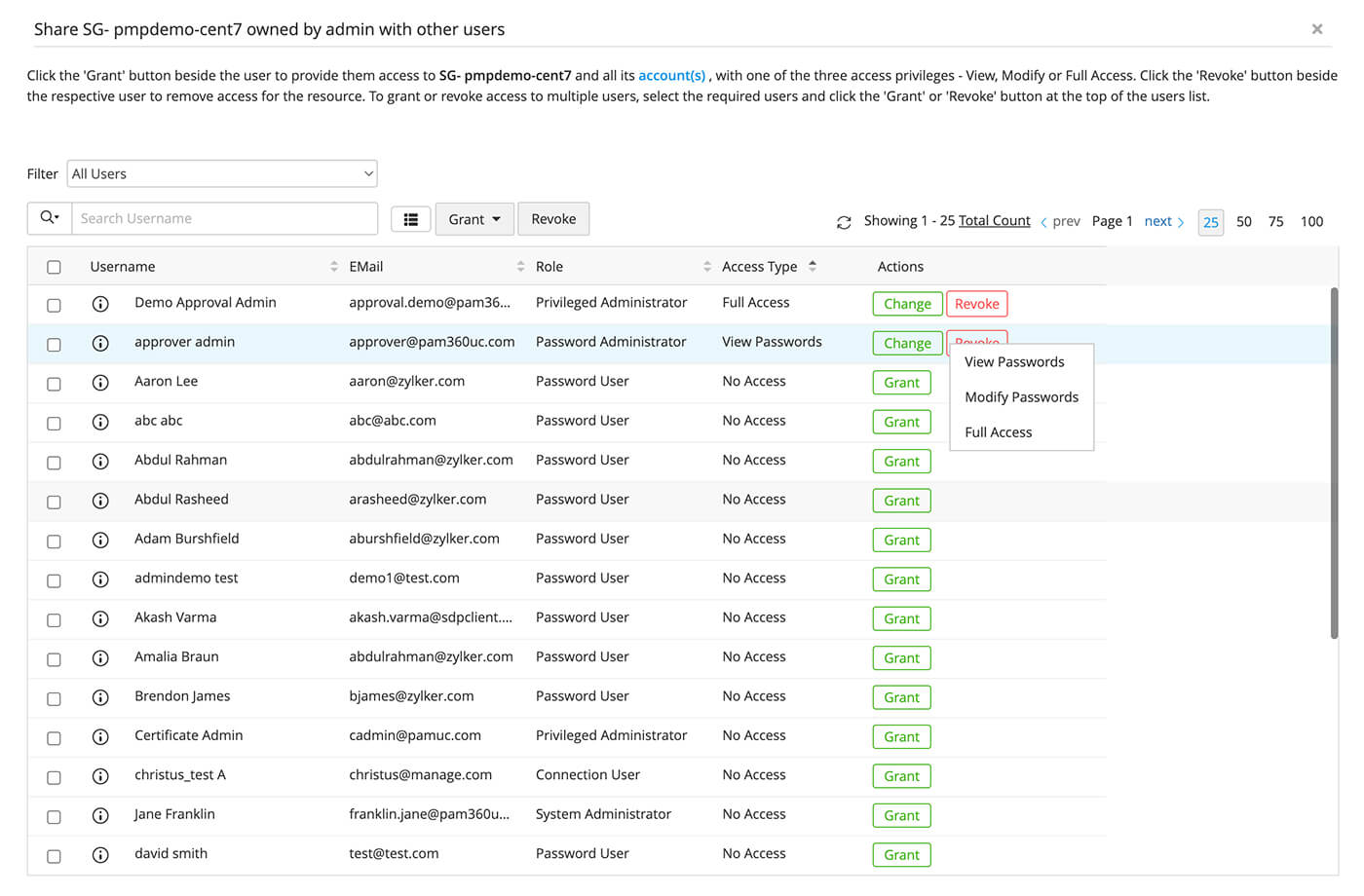
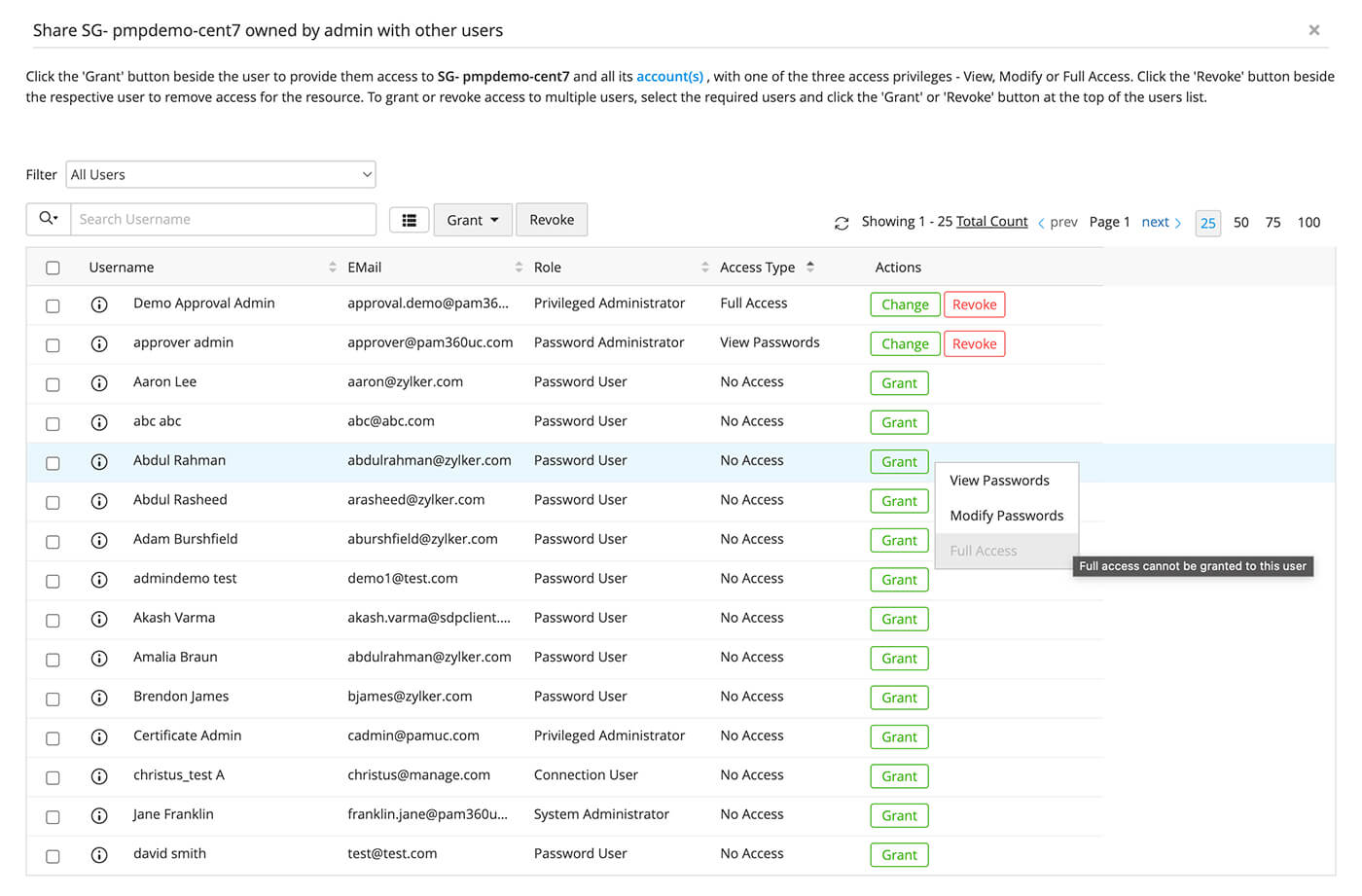
Enforce least privilege access with granular password sharing controls
- Assign user roles and grant role-based access to resources with varying permission levels—View, Modify, and Full Access.
- Create custom roles for bespoke access requirements and adjust access privileges accordingly.
- Validate and approve access requests with Request-Release workflows.
- Integrate with leading ITSM tools to automatically grant access to resources by validating ticket ID.
- Periodically scan and remove orphaned and dormant accounts and transfer privileges, if required.