Infrastructure as Code in action: What IT leaders need to know

Summary
Infrastructure as Code (IaC) revolutionizes how IT infrastructure is managed by automating provisioning through machine-readable code, replacing manual configuration processes. Popular tools like Terraform, AWS CloudFormation, and Ansible allow teams to define, store, and apply infrastructure code, ensuring consistency, scalability, and faster deployments. IaC improves speed, reduces errors, and enables seamless collaboration by integrating infrastructure management into the software development life cycle.
With benefits such as improved governance, cost optimization, and more agile infrastructure, IaC is essential for modern DevOps and cloud-native engineering. To avoid common pitfalls and implement best practices, it's crucial to adopt modular coding, integrate IaC into CI/CD pipelines, and prioritize security. For a deeper understanding of how IaC can transform your IT operations, learn more from the full article.
Gone are the days when spinning up infrastructure meant logging into a server, running a few scripts, and hoping nothing broke. In the age of cloud, containers, and rapid development cycles, manual provisioning just doesn’t cut it. Enter Infrastructure as Code (IaC)—a game-changing practice that’s reshaping how teams build and manage IT infrastructure.
But what exactly is Infrastructure as Code, how does it work, and why is it such a big deal? Let’s dive in.
What Is Infrastructure as Code (IaC)?
Infrastructure as Code (IaC) is the practice of managing and provisioning IT infrastructure—like servers, networks, and databases—through machine-readable configuration files, rather than manual processes.
Think of it like this: instead of setting up a server by clicking through a cloud provider’s web UI, you write code that defines the server configuration. That code is stored in version control (like Git), reviewed, and deployed the same way you’d manage application code.
Popular IaC tools include:
- Terraform
- AWS CloudFormation
- Ansible
- Pulumi
- Chef and Puppet
How IaC works: Transform your team’s approach to infrastructure management
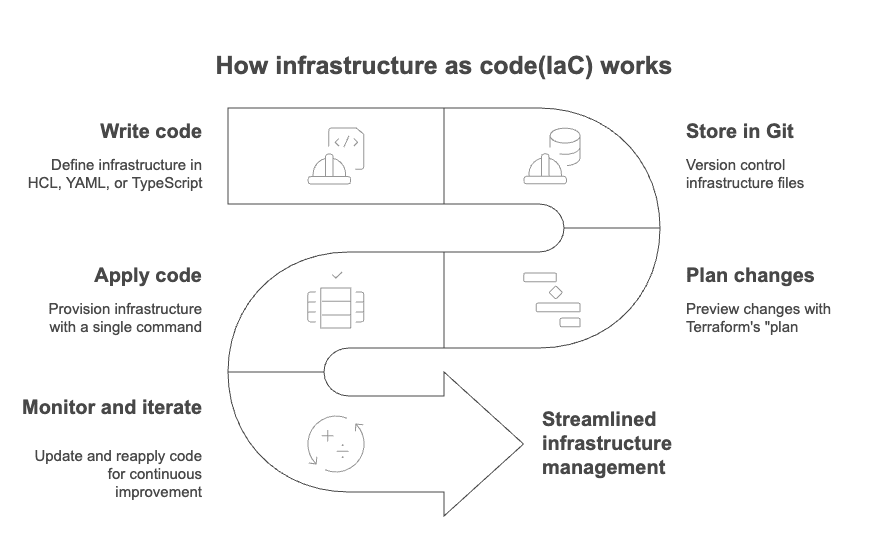
- Write code:Define infrastructure as a software
Instead of manually configuring infrastructure through cloud consoles or scripts, teams define infrastructure using code—written in languages like HCL for Terraform, YAML for CloudFormation, and TypeScript or Python for Pulumi.
Strategic advantage: This codification empowers your teams to standardize configurations, eliminate manual errors, and rapidly replicate environments across development, test, and production, all while reducing dependency on tribal knowledge.
- Store in Git:Treat infrastructure like application code
Infrastructure code is stored in a version-controlled system like Git, enabling collaboration and change management. This enables tracking who changed what, when, and why to enforce policies and approvals before infrastructure changes go live.
Strategic advantage: This brings governance, auditability, and traceability to infrastructure, helping you meet compliance requirements and internal control standards.
- Plan changes:Preview before you deploy
Before making any changes, tools like Terraform Plan or Pulumi Preview simulate the impact of proposed changes. Use what-if analysis to see what resources will be created, modified, or destroyed. This helps catch misconfigurations or costly mistakes before execution.
Strategic advantage: This reduces operational risk by eliminating guesswork and improving visibility into the downstream impact of every infrastructure change.
- Apply code:Provision infrastructure automatically
With a single command, the defined infrastructure is provisioned across your cloud or hybrid environment. The IaC tool communicates directly with provider APIs to create or modify cloud resources. Also, these tools maintain a record of what's been deployed to ensure alignment between code and infrastructure.
Strategic advantage: This accelerates time to market, ensures consistency across environments, reduces manual toil, and frees up engineering resources to focus on higher-value work.
- Monitor and iterate:Evolve infrastructure through code
As business needs evolve, so does your infrastructure. Updates are made by modifying the code and reapplying it. Your team can modify infrastructure safely via pull requests and peer reviews and apply optimizations, security patches, and scaling adjustments with minimal disruption.
Strategic advantage: This enables agile, iterative infrastructure improvements—helping your organization respond faster to changing demands, optimize cloud costs, and enhance security posture over time.
Declarative vs. imperative IaC: Which one should your team use?
Now that we've seen how IaC would work in your network, let's see the two major approaches to writing IaC:
- Declarative: You declare the desired end state. The tool figures out how to get there. So, you can use declarative when you want predictable, scalable, and maintainable infrastructure.
- Imperative: You specify the exact steps to reach the desired state. Use imperative when you need fine-grained control or are handling configuration tasks within an existing environment.
| Aspect | Declarative IaC | Imperative IaC |
|---|---|---|
| Abstraction level | High-level focus on outcomes | Low-level focus on procedures and tasks |
| Ease of use | Easier to read, maintain, and reason about at scale | More verbose, but familiar to those with scripting backgrounds |
| Control | Less control over execution order (tool decides) | Full control over execution flow and logic |
| State management | Typically manages state automatically (for example, Terraform state files) | Often stateless unless explicitly managed |
| Debugging | Might require understanding how the engine resolves dependencies | Easier to debug step-by-step execution |
| Scalability | More scalable across teams and environments due to idempotency and modularity | Can be harder to manage at scale without strict discipline |
| Use case fit | Ideal for infrastructure provisioning and environment management | Best for configuration management, patching, and procedural tasks post-deployment |
Benefits of IaC: Why infrastructure as a code (IaC) a game changer?
Adopting Infrastructure as Code (IaC) fundamentally changes how IT teams manage and scale infrastructure. Rather than relying on manual processes or isolated scripts, IaC introduces a programmable, repeatable approach that integrates directly into your software development life cycle.
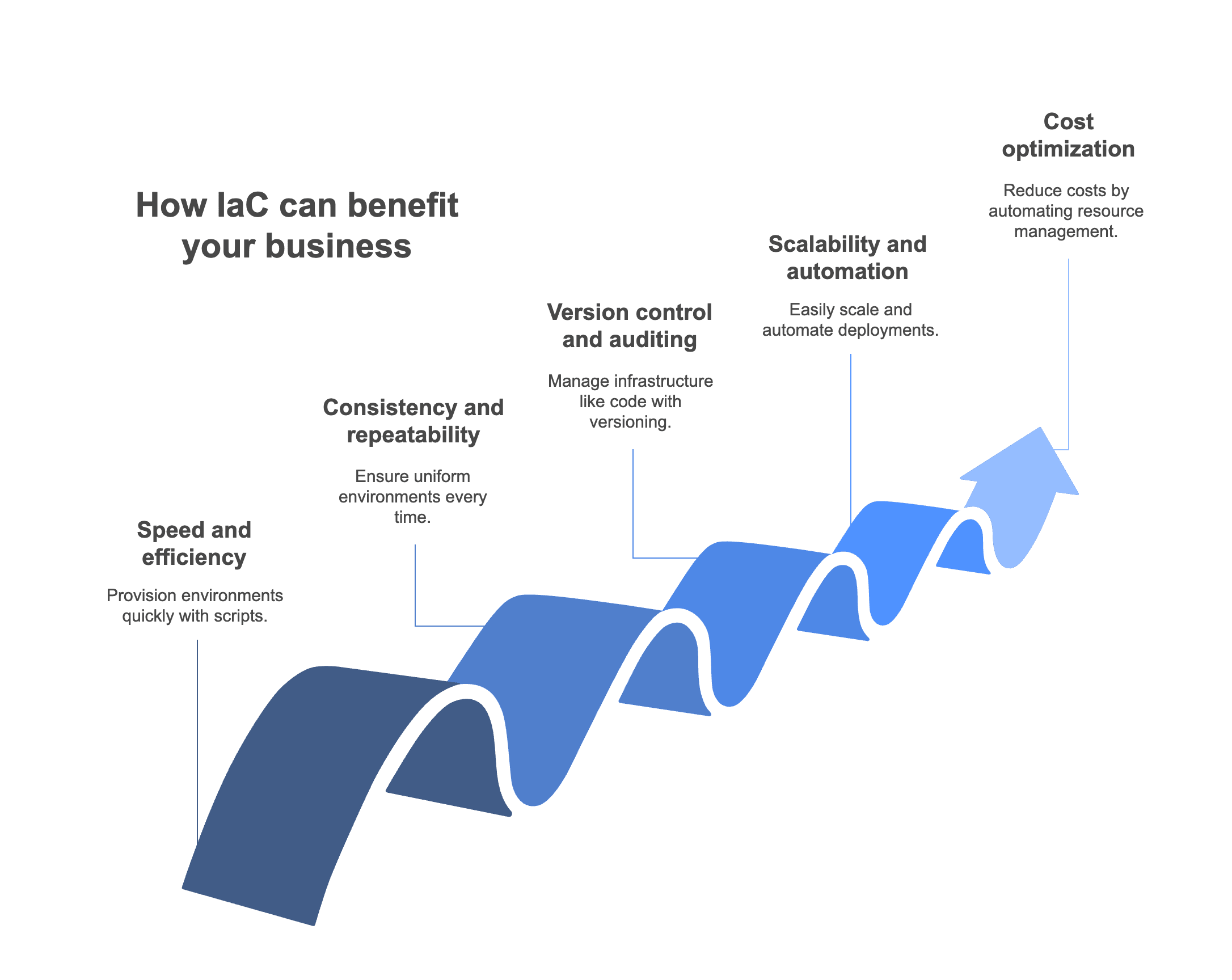
Speed and efficiency
IaC enables teams to provision complex infrastructure in seconds using declarative configuration files. Need 10 Elastic Compute Cloud instances spread across multiple availability zones, each behind an elastic load balancer, attached to auto-scaled target groups, and configured with custom IAM roles? A single terraform apply does the heavy lifting, eliminating the need for manual console clicks or brittle shell scripts.
Business impact: Faster time-to-market. Teams can experiment, test, and release features more quickly without being bottlenecked by infrastructure delays. This agility enables businesses to respond to customer needs, market shifts, or competitive threats in real time.
Consistency and repeatability
Say goodbye to snowflake servers. IaC enforces idempotency, meaning you can run the same configuration multiple times and get the same result. Every environment—from development to production—is defined in code, reducing drift and human error. No more last-minute surprises because someone changed a setting manually in staging but forgot to do it in production evironment.
Business impact: Fewer outages and production issues caused by inconsistent environments. This boosts customer trust, reduces firefighting, and frees up engineering time to focus on delivering value instead of fixing deployment-related bugs.
Version control and auditing
IaC turns your infrastructure into code—literally. Using tools like Git, you can commit changes, open pull requests, run linters, and perform peer reviews just like you would for application code. This brings transparency and traceability: you know exactly when a subnet was resized, who approved the change, and why. And if something breaks, you can roll back to a known good state with a simple Git revert or state reversion.
Business impact: Enhanced governance and risk management. For organizations in regulated industries like finance and healthcare, this supports compliance with frameworks like SOC 2, HIPAA, and ISO 27001. It also reduces the risk of unapproved changes making their way into production.
Scalability and automation
Scaling infrastructure manually doesn’t scale with your app. IaC makes it trivial to define horizontal scaling policies, auto-healing groups, and infrastructure modules that can be reused across projects. Want to deploy identical Kubernetes clusters across three regions? Use a module and pass different variables. Need to deploy CI/CD pipelines to three environments with unique configs? IaC automates the entire process.
Business impact: More efficient operations with a lower headcount. Teams can support larger, more complex infrastructure footprints without linear increases in Ops resources. It also improves resilience and uptime by making infrastructure self-healing and auto-scaling.
Cost optimization
IaC helps enforce infrastructure hygiene. You can script automatic resource tear down for ephemeral environments like dev or QA using life cycle hooks and CI jobs. Tagging policies can be enforced via policy-as-code frameworks like Open Policy Agent (OPA), ensuring visibility into cloud spend. The result? No more paying for idle RDS instances or orphaned EBS volumes nobody remembers spinning up.
Business impact: Direct reduction in cloud waste and unnecessary spend. Businesses gain better visibility into their infrastructure costs and can allocate budget more strategically. It supports a FinOps mindset by making cost a first-class citizen in the development life cycle.
Planning to deploy IaC? Some common pitfalls to avoid
- Hardcoding values: Avoid hardcoding specific values such as resource names, and instance sizes directly in your infrastructure code. Instead, leverage variables and modules to enhance flexibility and reusability. This improves scalability across environments and simplifies maintenance, especially when scaling or deploying to multiple regions or accounts.
- Skipping state management: In Terraform, the state file is essential for tracking your infrastructure’s current state and ensuring consistency. Always use remote back ends such as AWS Simple Storage Service (S3) with state locking via DynamoDB to securely store state files, especially in collaborative environments. Failure to manage the state properly can lead to issues like inconsistent infrastructure or resource duplication.
- Not testing code: Relying on manual validation or deploying untested code can result in costly mistakes. Utilize testing frameworks to programmatically verify your infrastructure changes. These tools simulate the actual execution of Terraform plans, ensuring that resources are correctly configured and deployed before production.
- Ignoring drift: Over time, manual changes or external events can lead to drift between your desired infrastructure state and the actual state. Regularly use terraform plan or terraform refresh to detect and address discrepancies. Automated drift detection ensures your infrastructure remains aligned with the version-controlled configuration.
4 best practices to ensure your IaC is streamlined
- Keep your infrastructure code modular: Break down your infrastructure code into reusable modules. This encourages Don’t Repeat Yourself (DRY) principles and simplifies maintenance by enabling you to modify components in isolation.
- Use remote state back ends for collaboration: Storing your state remotely, for instance in AWS S3 or Google Cloud Storage, enables collaboration by allowing multiple users to access the same state file. Combine this with state locking to prevent race conditions during concurrent changes.
- Integrate IaC into your CI/CD pipeline: Automate the validation, testing, and deployment of infrastructure changes as part of your CI/CD pipeline. This reduces human error, improves consistency, and accelerates feedback loops.
- Perform security scanning on IaC code: Use tools to automatically scan your IaC code for potential security vulnerabilities. These tools check for misconfigurations that could expose sensitive data or create attack vectors, ensuring that security best practices are enforced.
- Document your IaC just like application code: Good documentation is crucial for collaboration and long-term maintainability. Comment on complex logic, provide context for key decisions, and ensure that team members can easily understand the intent behind your infrastructure setup. Treat your infrastructure code as an essential part of your project’s documentation.
Infrastructure as Code (IaC) isn’t just a buzzword—it’s a foundational practice for modern DevOps, cloud-native engineering, and scalable IT operations. It brings consistency, speed, and confidence to infrastructure management, turning your infrastructure into something as manageable and versionable as any codebase.
If you’re not using IaC yet, now’s the time to start. Because in today’s world, infrastructure should be code—not chaos.