Reinforce security in hybrid IT environments with network hardening

Summary
Network hardening is an essential component of a comprehensive cybersecurity strategy. As the threat landscape evolves, CXOs must ensure that their organizations adopt proactive security measures to mitigate risks, comply with regulations, and maintain operational resilience.
This article explores the best practices, tools, and strategic considerations for network hardening, helping CXOs make informed decisions that align security measures with business goals.
Networks are the backbone of enterprise operations. They are also the prime targets of cybercriminals and malicious threat actors that compromise IT operations' continuity. With hybrid cloud infrastructures, remote workforces, and IoT ecosystems, network perimeters are expanding, creating new vulnerabilities, and making the need to safeguard enterprise systems complex and critical.
This is why organizations are relying on network hardening.
Network hardening 101: What is it and how does it work?
Network hardening is the process of securing a computer network by reducing its vulnerabilities and strengthening its defenses against potential cyber threats. It involves implementing a series of measures designed to protect the network from unauthorized access, data breaches, malware, and other security risks.
At its core, network hardening aims to create a robust security posture by addressing weak points in the network's infrastructure. This process is crucial for businesses, government agencies, and individuals who rely on digital systems to store sensitive information and ensure smooth operations.
Types of network hardening
Understanding the key categories of hardening is essential for enterprises aiming to build a resilient security posture. Each type addresses a different layer of potential vulnerability, helping ensure that no entry point is left unprotected.
- Physical hardening: This is the foundation of security. It involves securing data centers, server rooms, and networking closets with controlled access, surveillance systems, and tamper-proof enclosures to prevent unauthorized physical access to critical infrastructure.
- Hardware hardening: Protecting the physical devices that run your network—such as routers, switches, firewalls, and load balancers—by disabling unused ports, applying firmware updates, changing default configurations, and enabling device-level encryption where applicable.
- Software hardening: Reducing the attack surface by disabling or removing unnecessary services, regularly applying patches and updates to operating systems and applications, and using security configurations that align with best practices and compliance requirements.
- Protocol hardening: Ensuring data in transit is protected by enforcing the use of secure protocols like HTTPS, SSH, SFTP, and TLS, and phasing out outdated or insecure protocols like FTP, Telnet, and older versions of SSL.
- Access hardening: Implementing strict access controls through the principle of least privilege, multifactor authentication, role-based access, and network segmentation to ensure that only authorized users and systems can access critical assets.
By addressing each of these areas, organizations can significantly reduce their attack surface and improve overall cyber resilience.
Network components to harden and secure
To effectively harden a network, organizations must secure all core components that form the backbone of connectivity and access. This includes:
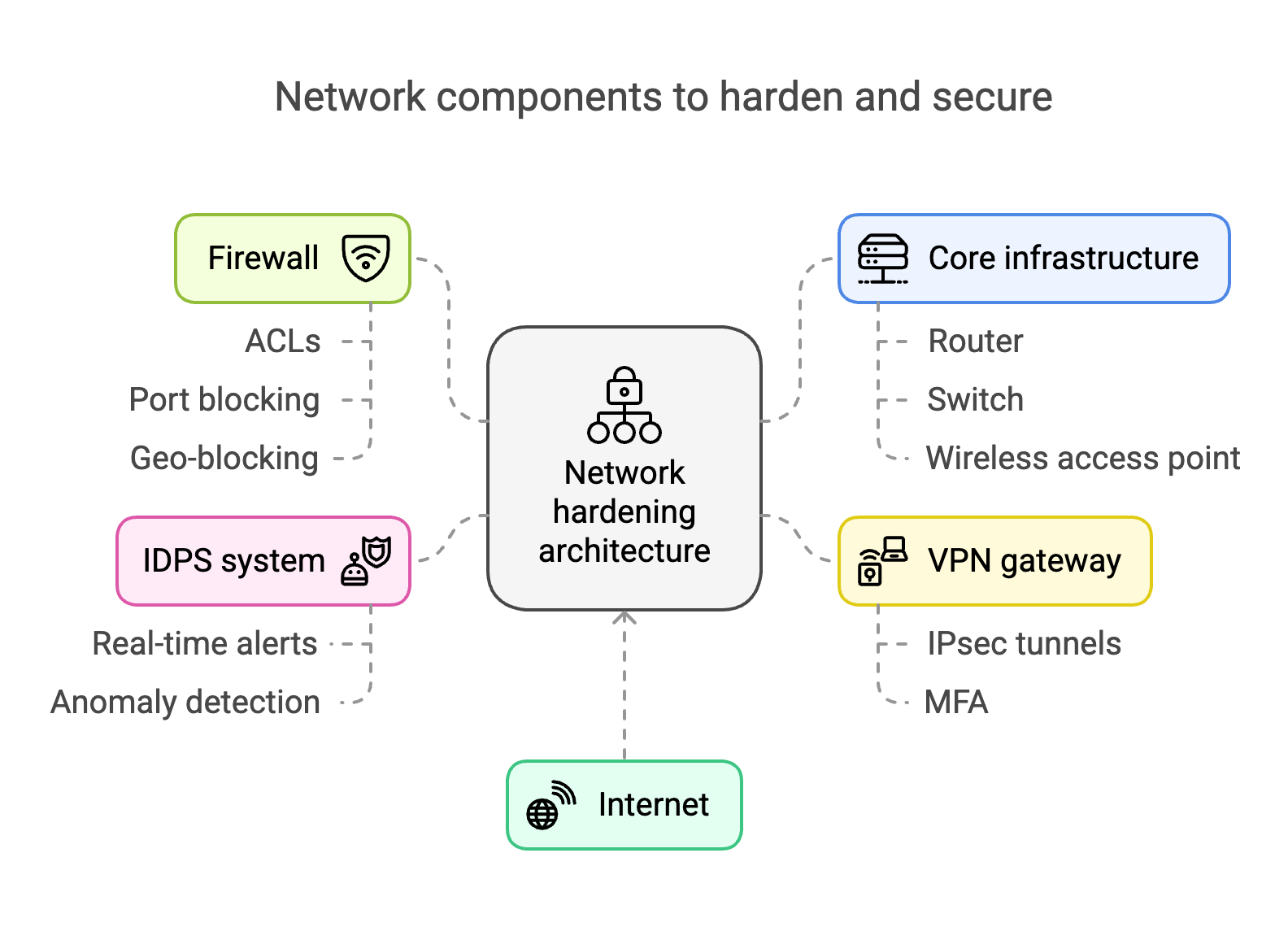
| Component | What to harden |
|---|---|
| Routers and switches | Disable unused ports/services, change default credentials, enable secure protocols (SSH over Telnet). |
| Firewalls | Define strict access control policies, regularly update rule sets, and monitor logs for anomalies. |
| Wireless access points (WAPs) | Use WPA3 encryption, disable SSID broadcasting for private networks, and apply MAC filtering. |
| VPN gateways | Enforce MFA, update firmware, and use strong encryption protocols (e.g., AES-256). |
| Servers | Disable unnecessary services, patch regularly, and monitor for unauthorized changes. |
| Endpoints (desktops/laptops) | Enforce endpoint protection policies, install antivirus/EDR, and limit admin access. |
| IoT devices | Isolate on separate VLANs, disable UPnP, and change default settings. |
Top threats and risks of unprotected networks
Without network hardening, organizations expose themselves to a wide range of cyber threats. Common attack vectors include:
| Threat | Risk description |
|---|---|
| Ransomware | Encrypts data and halts operations until a ransom is paid—often enters through unsecured ports or endpoints. |
| DDoS attacks | Overwhelms networks with traffic, causing service disruptions and downtime. |
| Man-in-the-middle (MitM) attacks | Intercepts network traffic to steal sensitive information—common in unsecured Wi-Fi networks. |
| Unauthorized access | Exploits weak credentials or open services to gain access to systems and exfiltrate data. |
| Lateral movement | Attackers spread from compromised devices due to a lack of segmentation or monitoring. |
| Unpatched vulnerabilities | Known exploits are used against systems that lack security updates or proper configuration. |
Traditional defenses are failing; network hardening can help
Enterprises today run increasingly interconnected environments where cloud applications, IoT devices, edge devices, and remote endpoints introduce new entry points for attackers.
Traditional perimeter-based defenses like firewalls are not effective in these environments and can no longer be sufficient as threats now come from both inside and outside the network.
This can lead to ransomware attacks, DDoS attacks, and data breaches propagating and causing significant financial losses, disrupting operations, and damaging brand reputation.
Network hardening, on the other hand, provides a multi-layered defense that helps mitigate risks. This ensures that the business remains operational and compliant with industry regulations.
2 key aspects of network hardening
1. Scanning and reducing the network's attack surface
Identifying and eliminating unnecessary services, ports, and applications can help eliminate common entry points for attackers and reduce the network's attack surface. For instance, identifying and closing open ports and unused services can prevent malicious actors from injecting service scripts into your network.
To reduce attack surfaces, use network scanning tools to identify exposed entry points. Disable any services that are not critical for business operations. Implement firewall rules to block inbound traffic and untrusted sources.
2. Implementing Zero Trust architecture with multi-factor authentication
Zero Trust architectures (ZTA) help eliminate the concept of trust within the network. In a ZTA model, every access request is verified regardless of whether it comes from inside or outside the network perimeter. This ensures that only authorized users and devices can access critical systems.
To effectively implement ZTA:
- Microsegmentation: Divide the network into smaller subnets to limit the lateral movement of attackers in case of a breach.
- Continuous monitoring: Use AI-powered tools to assess user behavior and detect anomalous activities in real time.
- Multi-factor authentication (MFA): Require MFA for all access requests to critical resources.
4 best practices for effective network hardening
1. Implement the principle of least privilege
The principle of least privilege ensures that users and systems have the minimum permissions required to perform their tasks. This ensures that users do not have access to unauthorized data and limits the potential damage in the event of a security breach.
Network access solutions offer capabilities such as role-based access controls and access control lists that enforce security policies by controlling which users or devices can access the network and how. They inspect devices for compliance with security policies before granting access and can quarantine non-compliant devices.
2. Encrypt network traffic and harden communicating devices
Encrypting data in transit prevents attackers from intercepting sensitive information. Use TLS or IPsec to secure communications between endpoints and devices.
Network devices such as routers, switches, and firewalls that play an active part in network communication are often targeted by attackers. Securing these devices is crucial for effective network hardening.
- Change default passwords: Replace default passwords with complex, unique credentials for all network devices.
- Disable unused interfaces and services: Limit potential vulnerabilities by deactivating unnecessary services on network devices.
- Enable secure management protocols: Use SSH instead of Telnet for secure remote management.
3. Conduct regular vulnerability assessments and secure configurations
Misconfigured systems and unpatched vulnerabilities are common entry points for attackers. Regular audits of network configurations and patch updates are critical to maintain a hardened network.
Regular vulnerability assessments identify and address weaknesses before attackers can exploit them. Conduct penetration testing to simulate real-world attacks and validate the effectiveness of security controls.
4. Configure network segmentation and isolation
Network segmentation divides the network into distinct zones, preventing unauthorized access to critical systems. For instance, placing IoT devices in a separate network segment ensures that a compromised device cannot access enterprise databases.
- Virtual LANs (VLANs): Use VLANs to separate network traffic logically.
- Firewall rules: Define strict firewall policies to regulate communication between segments.
- Intrusion detection and prevention systems (IDPSs): Provide real-time monitoring and automated responses to threats by detecting malicious activities within the network. They identify anomalies, policy violations, and known attack patterns to prevent breaches.
Network Hardening Checklist
Use this checklist to evaluate your current posture and guide your hardening strategy:
Access Control
- Enforce role-based access control (RBAC)
- Require multi-factor authentication (MFA)
- Apply the principle of least privilege
- Audit and remove stale user accounts
Device Security
- Change all default credentials on routers, switches, and WAPs
- Disable unused services and ports
- Apply firmware updates regularly
- Use SSH/SNMPv3 instead of insecure protocols
Traffic Protection
- Encrypt all network traffic with TLS/IPsec
- Segment traffic using VLANs and firewall rules
- Monitor network flow logs for anomalies
Monitoring and Maintenance
- Run regular vulnerability scans
- Conduct periodic penetration tests
- Enable intrusion detection and prevention systems (IDPS)
- Establish a clear incident response plan
Policy and Awareness
- Define a network security policy
- Train employees on phishing awareness
- Review and update security configurations quarterly
Pro Tip: Automate as much of the checklist as possible using network configuration management tools and SIEM/NDR solutions for continuous monitoring.
Recommendations for CXOs
- Adopt a layered security approach: Combine multiple security tools and strategies, such as firewalls, IDPSs, and network access control solutions, to create a comprehensive defense.
- Implement ZTA: Adopt a Zero Trust model to eliminate implicit trust and secure every access point.
- Invest in continuous monitoring and incident response solutions: Use AI-based tools to monitor network traffic in real time and develop an incident response plan to handle breaches effectively.
- Educate employees on security best practices: Conduct regular security awareness trainings to mitigate risks posed by human error and phishing attacks.
- Be prepared to manage insider threats: Deploy user behavior analytics tools to detect anomalies in user activities, and implement privileged access management solutions to control access to critical systems.
A secure network not only protects business operations but also enhances customer trust and brand reputation, creating a foundation for sustained growth in an increasingly digital world.