SIEM en la nube de ManageEngine: Log360 Cloud
Obtenga una visibilidad incomparable, detecte amenazas en tiempo real y garantice el cumplimiento con la plataforma de análisis y monitoreo de seguridad.
¡Comienza tu prueba gratuita de 30 días!
Más de 280.000 organizaciones en 190 países confían en ManageEngine para gestionar su TI


Collect logs
Ingest log data from various sources, including Windows and Linux servers, endpoints, databases, business apps, cloud environment, and more.
Audit reports
Investigate critical security incidents thoroughly by examining who performed actions, their location, and the timestamps, all facilitated by predefined security audit reports

Detect threats
Instantly identify complex threats by correlating events across your entire network. The engine analyzes logs in real-time, triggering alerts on suspicious patterns and anomalies.
Behavior analytics
Proactively hunt for slow-moving and evasive attacks. ML-powered analytics continuously learns and adapts, identifying patterns that bypass traditional rule-based security

Investigate threats
Accelerate incident response with enriched context. The workbench consolidates user, device, and threat intelligence, providing a comprehensive view for rapid investigation.
Protect cloud apps
Track cloud app usage, detect shadow IT, and enforce security policies. Monitor both sanctioned and unsanctioned apps to safeguard sensitive data.

¿Qué es un SIEM en la nube?
Una solución SIEM basada en la nube proporciona funcionalidades de SIEM como un servicio. Las soluciones de SIEM en la nube protegen su red; proporcionan información sobre amenazas; ofrecen una consola para detectar, priorizar y resolver incidentes de seguridad; y le ayudan a cumplir con los mandatos normativos―todo desde la nube. Las soluciones SIEM en la nube ofrecen mayor flexibilidad y facilidad de acceso a la hora de gestionar la ciberseguridad tanto en entornos on-premises como en la nube.
Log360 Cloud es la solución SIEM basada en la nube de ManageEngine que tiene como objetivo proporcionar visibilidad integral y gestión de seguridad en entornos on-premises y en la nube en una sola plataforma.
Obtenga más información sobre los beneficios únicos de usar Log360 Cloud
SIEM basado en la nube para fortalecer su
seguridad y cumplimiento
- Gestión de logs en la nube
- Detección de amenazas
- UEBA
- Inteligencia de amenazas
- Cumplimiento de la nube
- Seguridad de la identidad
Visibilidad de seguridad incomparable gracias al análisis de logs
Experimente el poder de la gestión de logs en la nube con Log360 Cloud. Obtenga información detallada sobre los logs de seguridad, acceso, sistema y aplicaciones de su red. Con Log360 Cloud, puede:
- Optimice la recopilación y el almacenamiento de logs: Recopile y almacene de forma automática y segura logs de servidores Windows, fuentes de syslog, aplicaciones y plataformas en la nube.
- Realizar un análisis de logs exhaustivo: Aproveche las capacidades avanzadas de búsqueda y correlación para identificar e investigar rápidamente eventos de seguridad.
- Garantizar el cumplimiento: Archive de forma segura los datos de logs para análisis forense y cumplimiento normativo con nuestras opciones de almacenamiento flexibles.
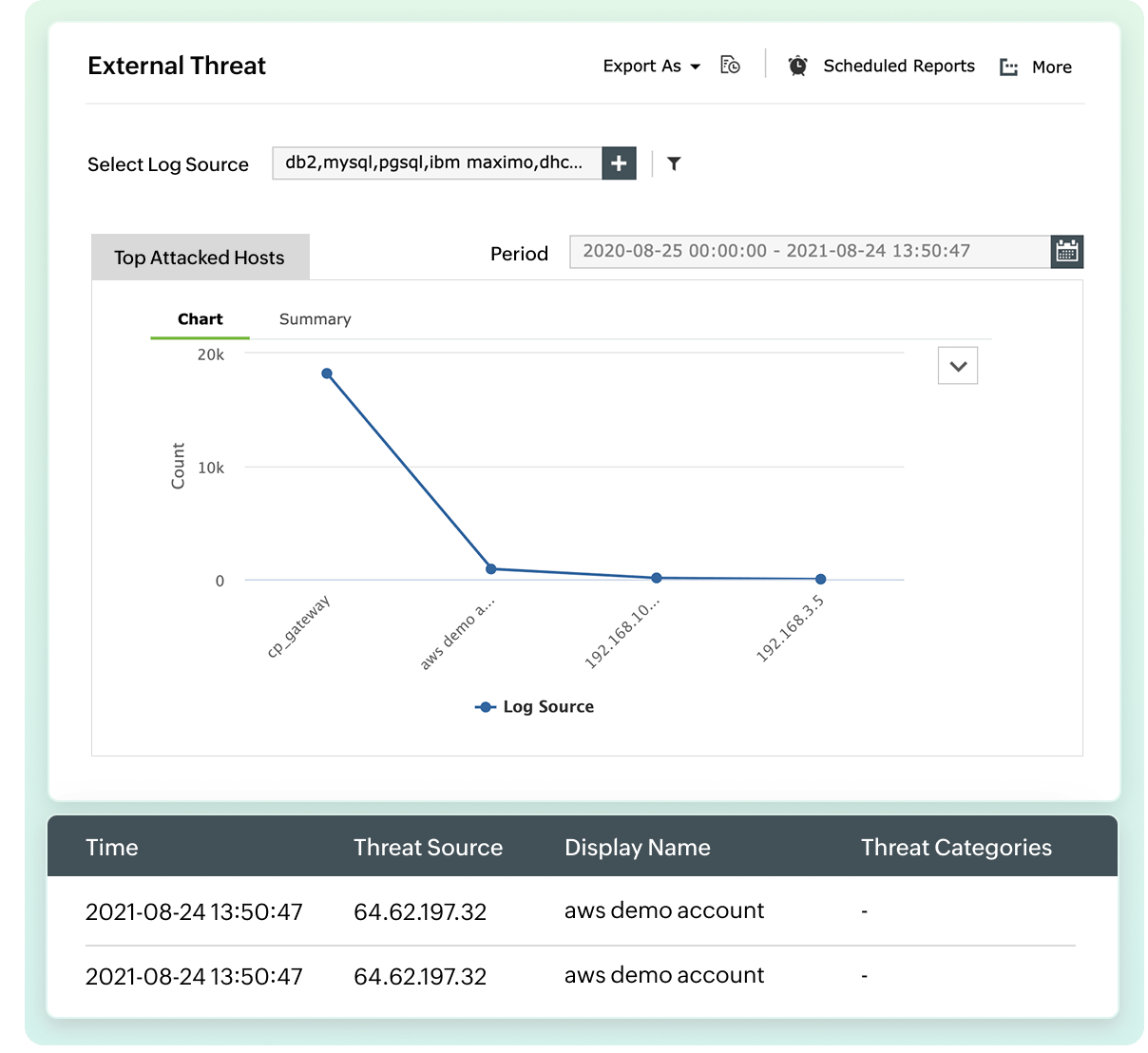
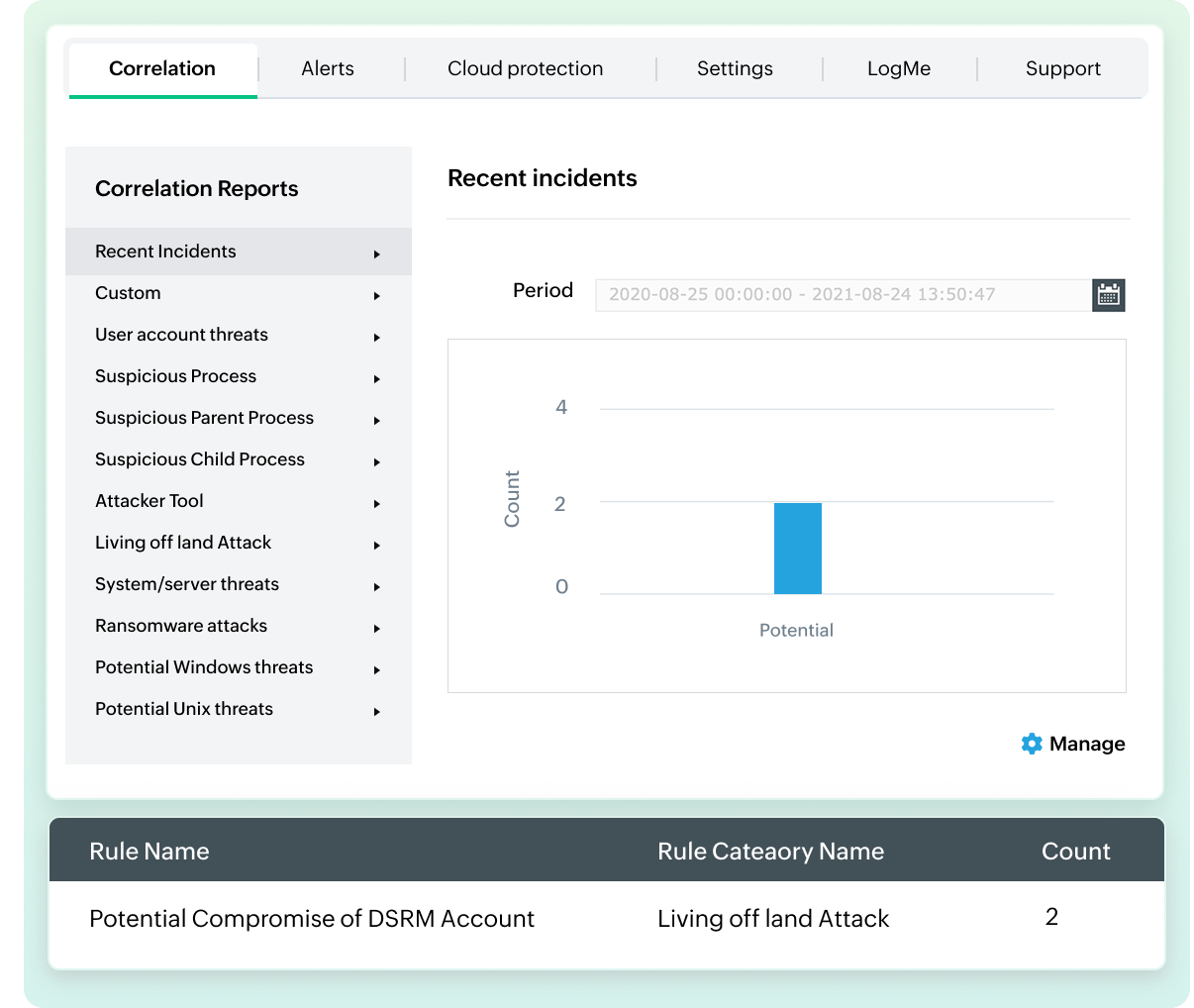
Reglas de detección plug-and-play para amenazas sofisticadas
Detecte amenazas, patrones de ataque y técnicas con una correlación de logs eficaz y reglas de anomalías. Con Log360 Cloud, puede:
- Reciba alertas en tiempo real: Reciba alertas instantáneas sobre amenazas conocidas e indicadores de compromiso a través de más de 100 reglas de correlación predefinidas.
- Aproveche la detección de anomalías: Aproveche las reglas de detección de anomalías predefinidas o personalice las suyas propias en función del tiempo, el patrón y el recuento para detectar un comportamiento inusual que podría indicar amenazas internas u otros ataques sofisticados.
- Optimice la ingestión de inteligencia sobre amenazas: Automatice la integración de fuentes de amenazas y personalice las reglas de correlación para una detección contextual precisa.
- Detección de amenazas a medida: Utilice nuestro intuitivo generador de reglas de correlación para crear o modificar reglas para detectar acceso no autorizado, movimientos laterales y otros ataques sofisticados.
Detección de anomalías
Vaya más allá de la detección tradicional basada en reglas al identificar desviaciones en los patrones de comportamiento de usuarios y entidades mediante reglas de anomalías. Detecte posibles amenazas internas, como anomalías de inicio de sesión, cuentas comprometidas e intentos de exfiltración de datos, antes de que se intensifiquen. Con UEBA, puede:
- Detección de anomalías basada en ML: Detecta automáticamente desviaciones del comportamiento normal utilizando algoritmos de aprendizaje automático.
- Detección precisa: Identifique amenazas en función del tiempo, el recuento y las anomalías de patrones para lograr una mayor precisión.
- Identificación proactiva de amenazas: Descubra de forma temprana comportamientos anómalos, como inicios de sesión inusuales o transferencias de archivos.
- Puntuación de riesgo integrada: Identifique usuarios y entidades de alto riesgo con puntuaciones basadas en anomalías activadas e indicadores de comportamiento predefinidos.
- Creación de reglas de anomalía personalizadas: Cree reglas de anomalías individuales o masivas adaptadas a su entorno.
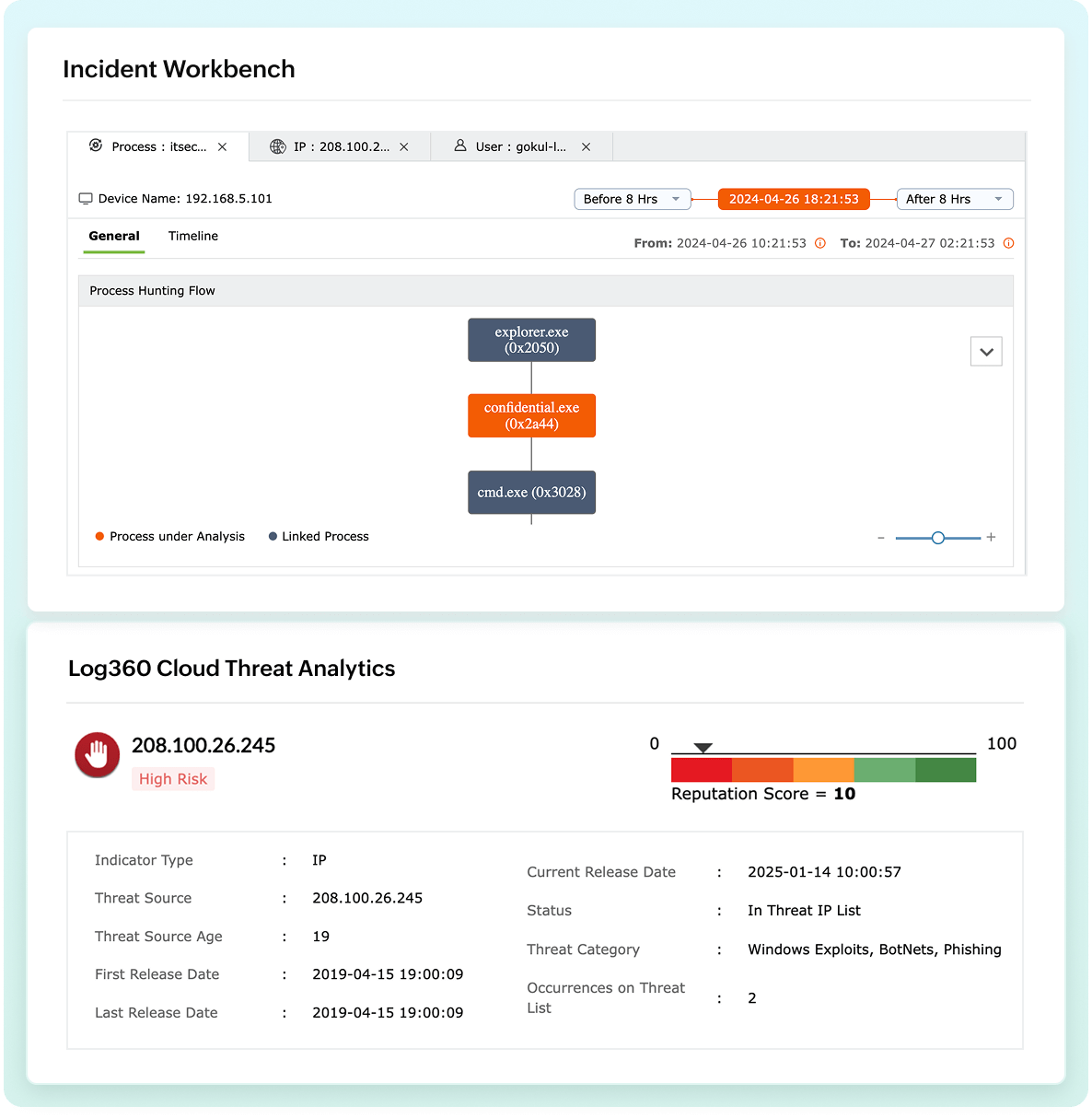
Inteligencia de amenazas preconfigurada y análisis de amenazas avanzado
Fortalezca sus defensas con una base de datos de inteligencia de amenazas que incluye más de 600 millones de URL, dominios y direcciones IP maliciosas. Con la plataforma integrada de Log360 Cloud, obtendrá:
- Integración perfecta con datos de amenazas: Conéctese sin esfuerzo con fuentes de amenazas en formato STIX/TAXII para obtener cobertura específica de la industria.
- Información en tiempo real: Benefíciese de los análisis impulsados por BrightCloud que proporcionan puntuaciones de reputación y tipos de amenazas para entidades maliciosas.
- Análisis de seguridad mejorado: Integre datos dinámicos de amenazas en nuestro motor de detección para obtener respuestas más rápidas y efectivas.
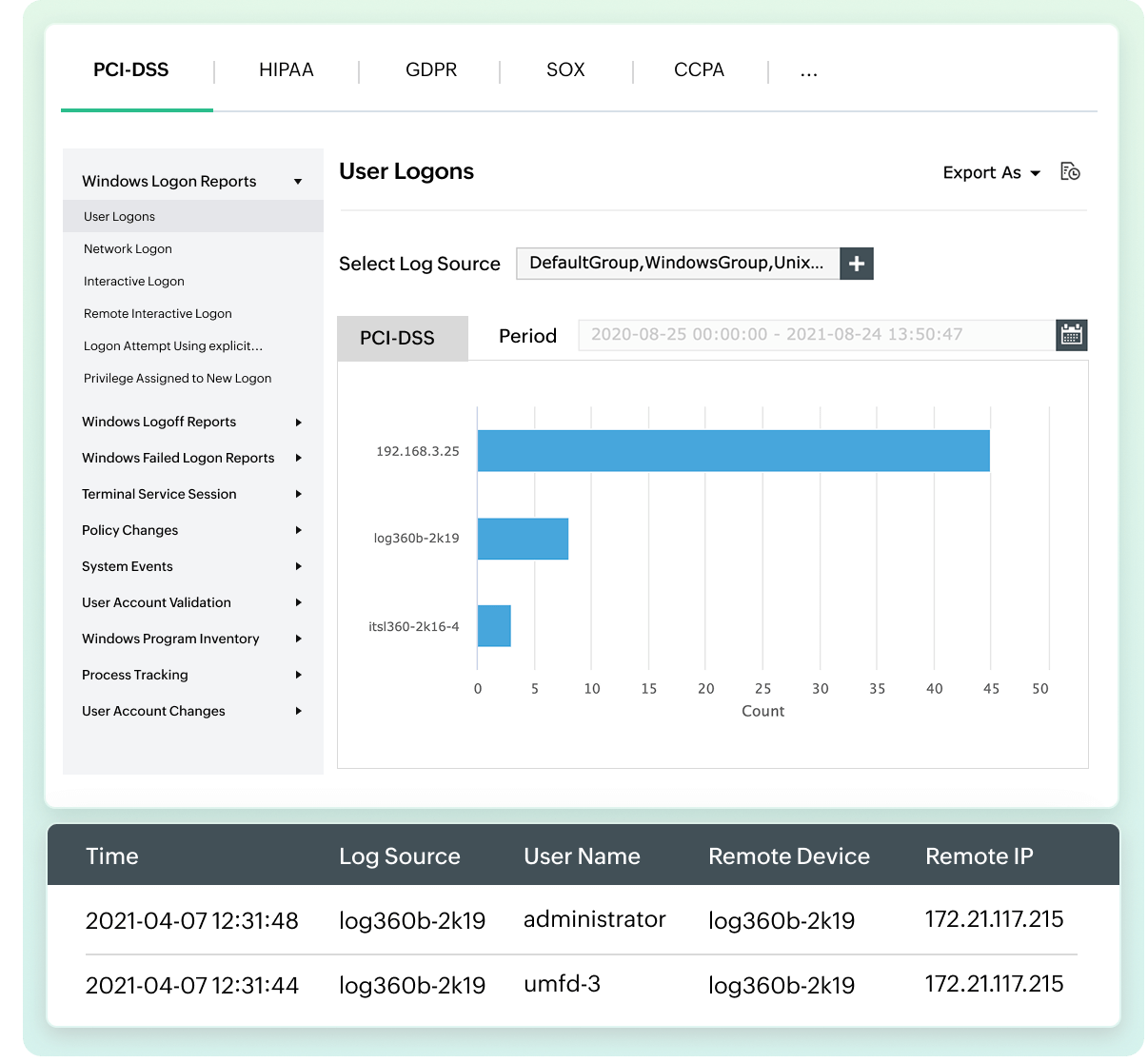
Informes de cumplimiento listos para auditoría y alertas de infracciones
Log360 Cloud optimiza el cumplimiento normativo y mejora su seguridad. Ofrece:
- Gestión eficaz del cumplimiento: Utilice plantillas de informes de auditoría prediseñadas (PCI DSS, GLBA, FISMA, SOX, HIPAA, ISO 27001, etc.) para demostrar el cumplimiento de los estándares de seguridad, al mismo tiempo que almacena de forma segura los datos de registro en la nube, eliminando así el hardware costoso.
- Monitoreo y remediación continuos:cSupervise de forma proactiva el cumplimiento con paneles dedicados, identifique brechas e implemente soluciones oportunas.
- Pistas de auditoría mejoradas: Mantenga logs detallados de la actividad del usuario para detectar y responder rápidamente a accesos sospechosos o violaciones de datos.
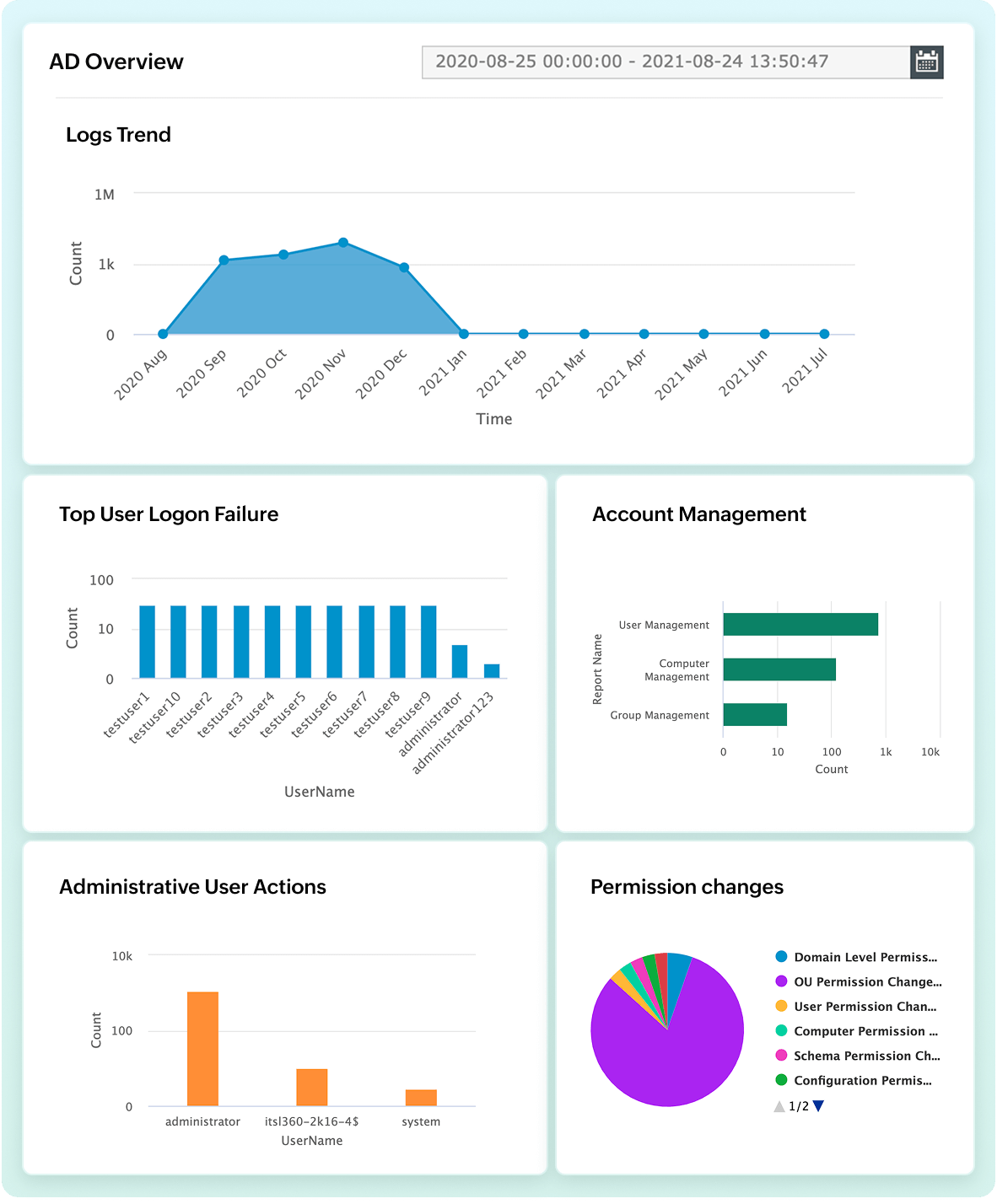
Auditoría y supervisión exhaustivas de Active Directory
Proteja las identidades durante su transición a la nube con Log360 Cloud. Al supervisar Active Directory, le ayuda a:
- Auditar granularmente la actividad del usuario: Obtenga una visibilidad profunda de los eventos de autenticación y detecte posibles intentos de intrusión o suplantación de identidad.
- Supervise los cambios críticos de AD en tiempo real: Identifique instantáneamente modificaciones en OU, GPO y permisos para anticiparse a las amenazas internas
- Detectar ataques basados en identidad: Supervise continuamente las escaladas de privilegios, los movimientos laterales y el robo de credenciales.
- Automatizar la monitorización del comportamiento del usuario: Marca automáticamente actividades inusuales en la cuenta (como bloqueos frecuentes o inicios de sesión desde diferentes ubicaciones) para detectar amenazas de forma temprana.
¿Es usted un MSSP?
Mejore sus servicios de seguridad con Log360 Cloud MSSP. Implemente una gestión centralizada de registros, análisis de amenazas y gestión del cumplimiento normativo a escala.
Pruébalo gratisEmpiece con 50 GB gratis
No se requiere tarjeta de crédito.
- 50 GB de almacenamiento de búsqueda predeterminado
- 150 GB de almacenamiento de archivo predeterminado (3 veces el almacenamiento de búsqueda)
- Retención de búsqueda de 7 días
- 15 días de conservación en archivo
- 50 GB de almacenamiento de búsqueda predeterminado
- 150 GB de almacenamiento de archivo predeterminado (3 veces el almacenamiento de búsqueda)
- Retención de búsqueda de 30 días
- 90 días de conservación de archivos
- 20 perfiles de alerta
- Nota: El almacenamiento de archivo es gratuito, triplicando el almacenamiento de búsqueda. Se puede adquirir almacenamiento de archivo adicional si es necesario.
Complementos
- 50 GB de almacenamiento de búsqueda predeterminado
- 150 GB de almacenamiento de archivo predeterminado (3 veces el almacenamiento de búsqueda)
- Retención de búsqueda de 60 días
- 180 días de conservación de archivos
- 50 perfiles de alerta
- 10 reglas de correlación
- Nota: El almacenamiento de archivo es gratuito, triplicando el almacenamiento de búsqueda. Se puede adquirir almacenamiento de archivo adicional si es necesario.
Complementos
- 50 GB de almacenamiento de búsqueda predeterminado
- 150 GB de almacenamiento de archivo predeterminado (3 veces el almacenamiento de búsqueda)
- Retención de búsqueda de 90 días
- Retención de archivos personalizable
- 70 perfiles de alerta
- 20 niveles de almacenamiento
- 20 reglas de correlación
- 20 reglas de anomalía
- Sobrescribir logs antiguos
- Nota: El almacenamiento de archivo es gratuito, triplicando el almacenamiento de búsqueda. Se puede adquirir almacenamiento de archivo adicional si es necesario.
Complementos
Para más de 20 000 GB (20 TB) de almacenamiento, comuníquese con nuestro equipo de ventas en latam-sales@manageengine.comObtenga una cotización personalizada
Principales ofertas de la tecnología SIEM de Log360 Cloud
Experimente el poder transformador de la gestión de logs basada en la nube con Log360 Cloud.
Saber másSolución SIEM unificada
Experimente una plataforma unificada de ciberseguridad que combina técnicas avanzadas de correlación para la detección de amenazas, robustas funciones CASB para la seguridad de datos en la nube y un cumplimiento normativo optimizado mediante auditoría y monitorización eficaces. Nuestro SIEM nativo en la nube permite a las organizaciones lograr operaciones de seguridad fluidas y proteger sus valiosos activos.
Información sobre amenazas basada en IA
Blinde a su equipo de seguridad para una respuesta más inteligente ante amenazas con Zia Insights en Log360 Cloud. Esta función basada en IA ofrece resúmenes concisos y contextualizados de eventos de seguridad, asigna las amenazas a las técnicas MITRE ATT&CK® y proporciona una guía precisa de mitigación, lo que permite una investigación y respuesta a incidentes más rápida y segura.
Más informaciónCASB: Visibilidad y control total sobre la nube
Obtenga control total sobre su entorno en la nube con CASB de Log360 Cloud. Supervise el uso de las aplicaciones en la nube para identificar operaciones no autorizadas en la sombra, obtener información detallada sobre la actividad de los usuarios y detectar rápidamente posibles amenazas. La integración de CASB con SIEM en la nube ayuda a descubrir aplicaciones no autorizadas y a generar contexto práctico sobre el comportamiento de los actores de amenazas..
Más informaciónPlataforma de seguridad: flexibilidad para construir la seguridad a su manera
Tome el control total de su seguridad con el enfoque de plataforma unificada de Log360. Integre fácilmente sus herramientas de seguridad mediante API abiertas, visualice los datos exactamente como los necesita y amplíe la funcionalidad con extensiones personalizadas para satisfacer sus necesidades cambiantes. Cree un ecosistema de seguridad que funcione exactamente como usted desea.
Más informaciónAlmacenamiento de logs en la nube: sin costos iniciales
Benefíciese de la recopilación, el análisis, la búsqueda y el almacenamiento intuitivos de logs con Log360 Cloud. Realice búsquedas de alta velocidad y cumpla con los requisitos de retención de cumplimiento normativo mediante un plan de precios flexible combinado con opciones de almacenamiento adaptables. Esta solución escalable y rentable elimina la necesidad de inversiones iniciales en hardware y el mantenimiento continuo de la infraestructura.
Más informaciónPreguntas frecuentes sobre Log360 Cloud SIEM:
¿Qué es SIEM?
Una solución de gestión de información y eventos de seguridad (SIEM) es un pilar fundamental de la ciberseguridad, ya que permite a los centros de operaciones de seguridad detectar, priorizar y responder rápidamente a las amenazas. Garantiza el cumplimiento normativo, refuerza la estrategia de seguridad y agiliza la respuesta ante incidentes. Al recopilar y analizar logs y telemetría de seguridad de toda la red, las herramientas SIEM emplean técnicas avanzadas como la correlación y el modelado de comportamiento para identificar y mitigar proactivamente los riesgos de seguridad.
¿Qué es SIEM-as-a-service?
SIEM-as-a-service (Security Information and Event Management) es una solución basada en la nube que proporciona análisis en tiempo real de las alertas de seguridad generadas por diversas aplicaciones y hardware de red.
Las características principales incluyen:
- Recopilación y agregación de logs de múltiples fuentes
- Detección y alerta de amenazas en tiempo real
- Capacidades de respuesta automatizada a incidentes
- Informes y gestión de cumplimiento
- Infraestructura de nube escalable administrada por el proveedor de servicios
Cloud SIEM elimina la necesidad de que las organizaciones mantengan una infraestructura SIEM local compleja, ofreciendo una solución de seguridad más flexible y, a menudo, más rentable.
¿Cuándo deberían las organizaciones elegir SIEM en la nube en lugar de SIEM local?
Las organizaciones deberían considerar SIEM en la nube en lugar de soluciones locales en los siguientes escenarios:
- Recursos de TI limitados: cuando hay una falta de experiencia interna para administrar una infraestructura SIEM compleja.
- Consideraciones de costos: para evitar grandes gastos de capital iniciales en licencias de hardware y software.
- Necesidades de escalabilidad: para empresas que experimentan un crecimiento rápido o una demanda fluctuante.
- Fuerza laboral distribuida: para brindar un mejor apoyo a los empleados en múltiples ubicaciones.
- Implementación más rápida: cuando existe la necesidad de implementar capacidades SIEM rápidamente.
- Deseo de actualizaciones continuas: para beneficiarse de la información sobre amenazas y actualizaciones de funciones más recientes sin intervención manual.
- Requisitos de cumplimiento: Para cumplir más fácilmente con los estándares regulatorios que requieren una gestión de logs sólida y un monitoreo de seguridad.
Para decidir entre un SIEM local y uno en la nube, lea nuestro blog detallado sobre el tema aquí.
¿Cómo garantiza Log360 Cloud la seguridad de mis datos de log?
Log360 Cloud employs multiple layers of security to protect your sensitive log data:
- Encryption: All data is encrypted both in transit and at rest using industry-standard encryption protocols.
- Access controls: Strict role-based access controls and multi-factor authentication are implemented to prevent unauthorized access.
- Data isolation: Each customer's data is logically segregated to ensure data privacy.
- Compliance: The service adheres to major compliance standards, including ISO/IEC 27001, 27017, and 27018; SOC 2 (including SOC 2 + HIPAA); SOC 1 (SSAE 18 & ISAE 3402 Type II); and ISO 9001:2015.
- Regular audits: Periodic security audits and penetration testing are conducted to identify and address potential vulnerabilities.
- Redundancy: Data is replicated across multiple secure data centers to ensure high availability and disaster recovery capabilities.
- Secure APIs: All integrations and data transfers use secure APIs with proper authentication mechanisms.
- Monitoring: Continuous monitoring of the cloud infrastructure for any security anomalies or potential threats.



