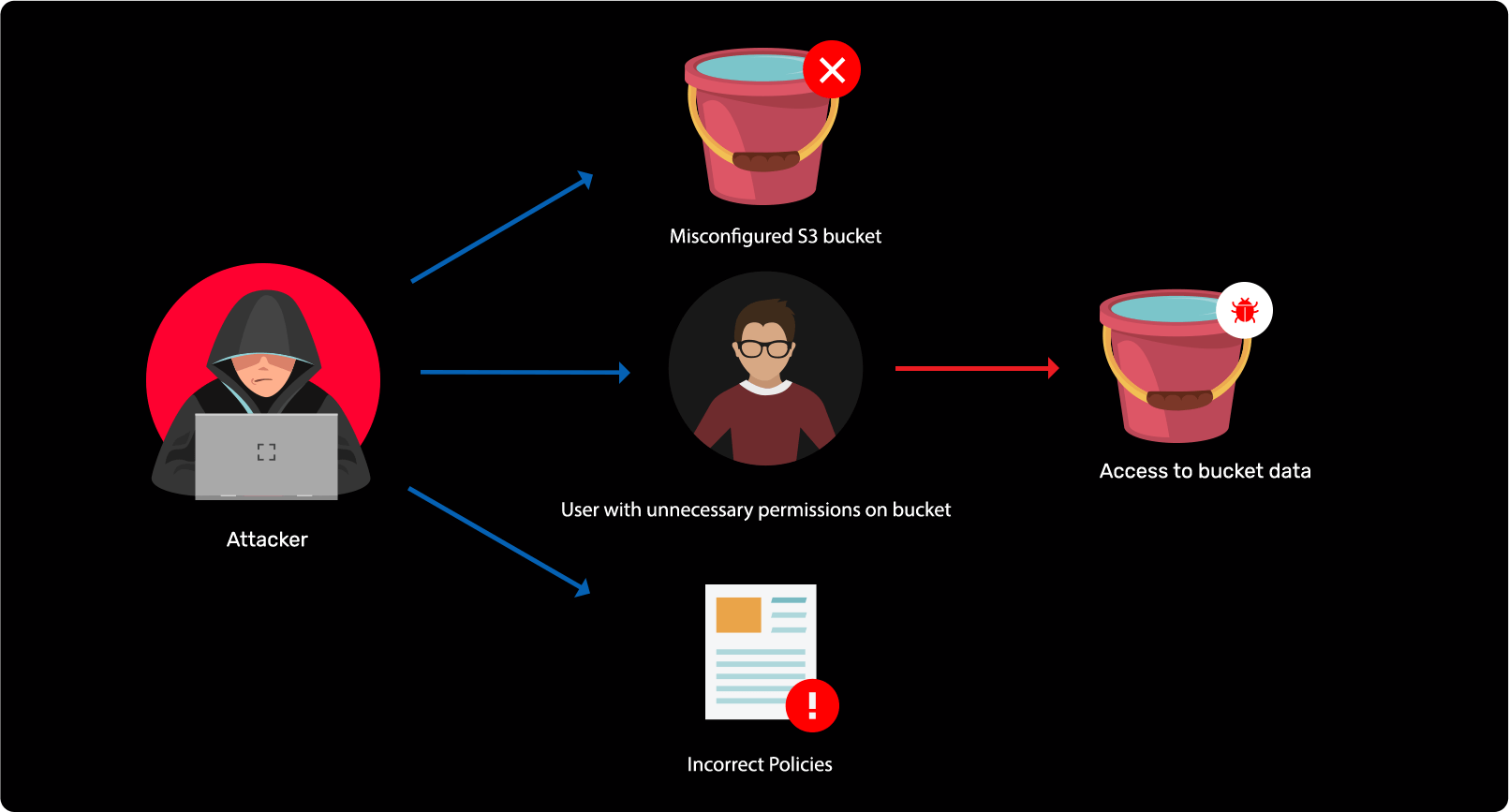
Flujo de ataque
Ataque técnico
Solución
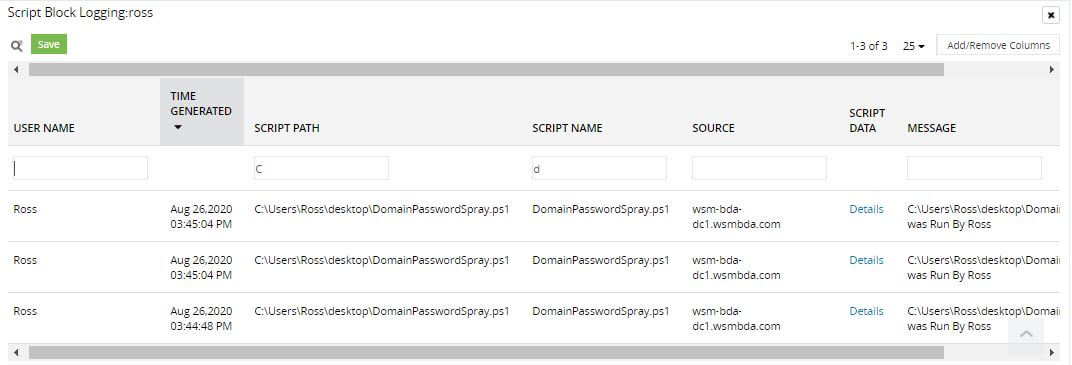
Password spray attack on Active Directory users
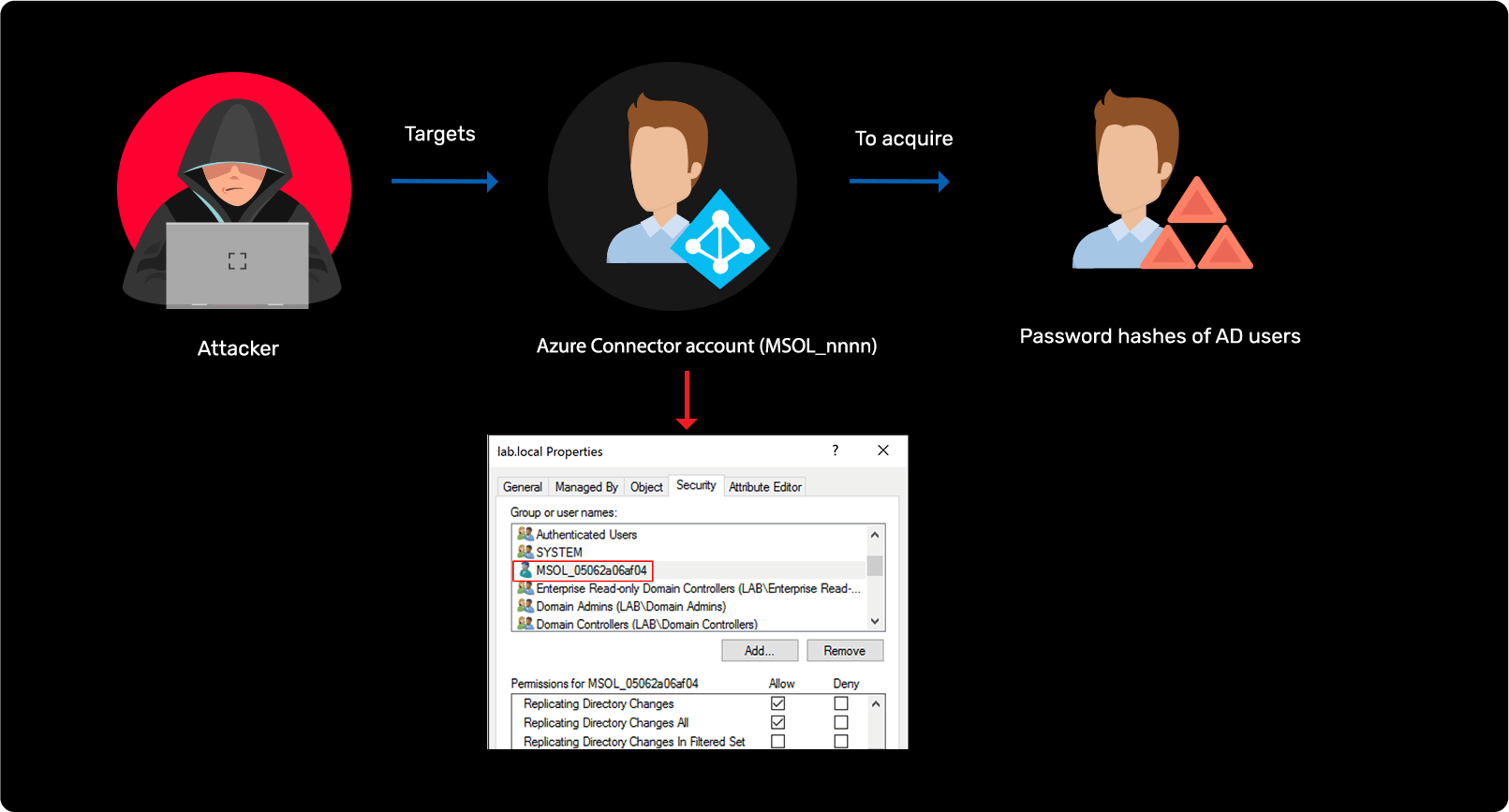
Attacking password hash synchronization in AD and Azure AD
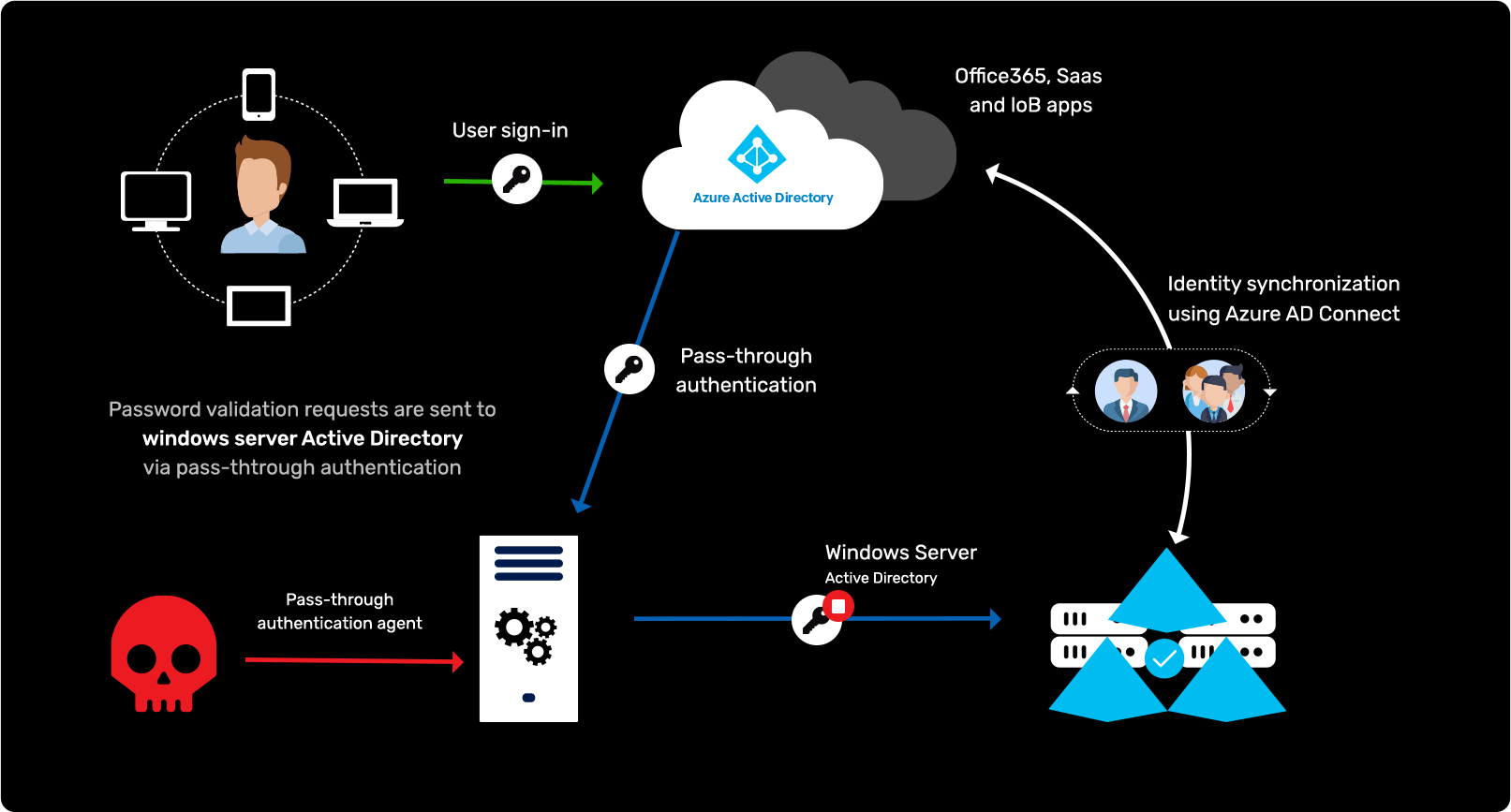
Attacking Pass-Through Authentication in AD and Azure AD
Attacking leaky S3 buckets in Amazon Web Services (AWS)
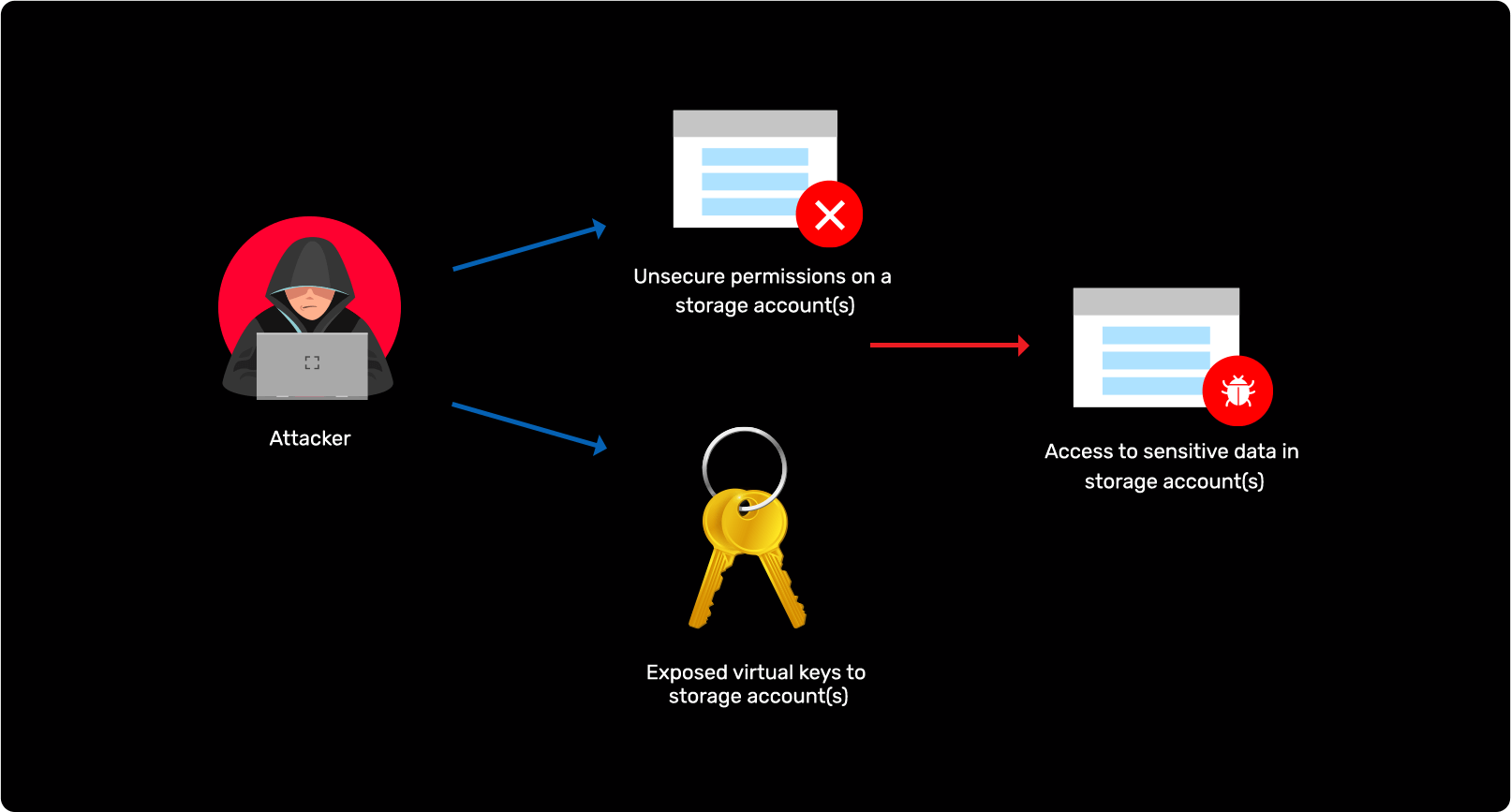
Attacking unsecure storage accounts in Azure AD
Password spray attack on Active Directory users
Password spray attack on Active Directory users
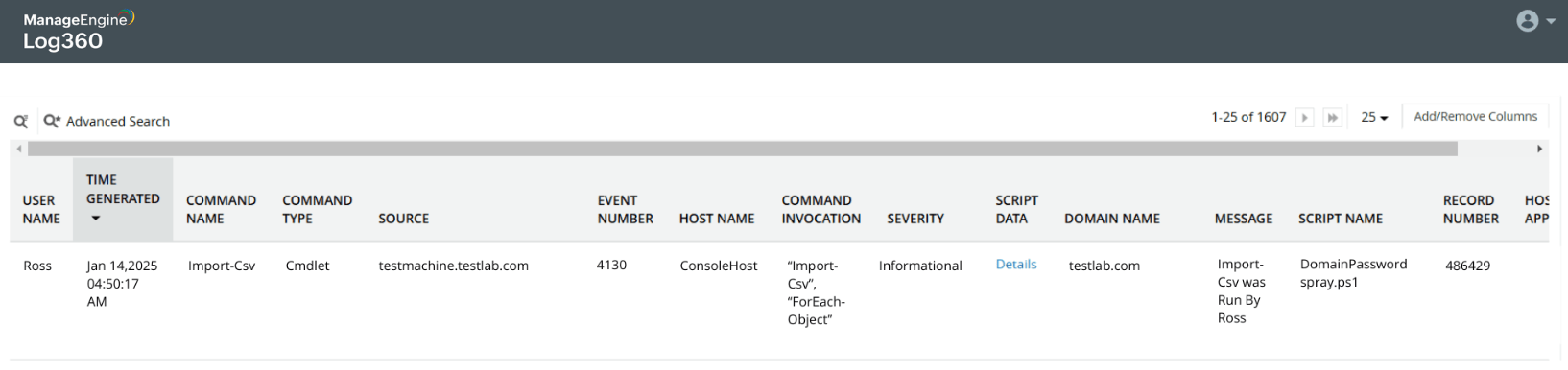
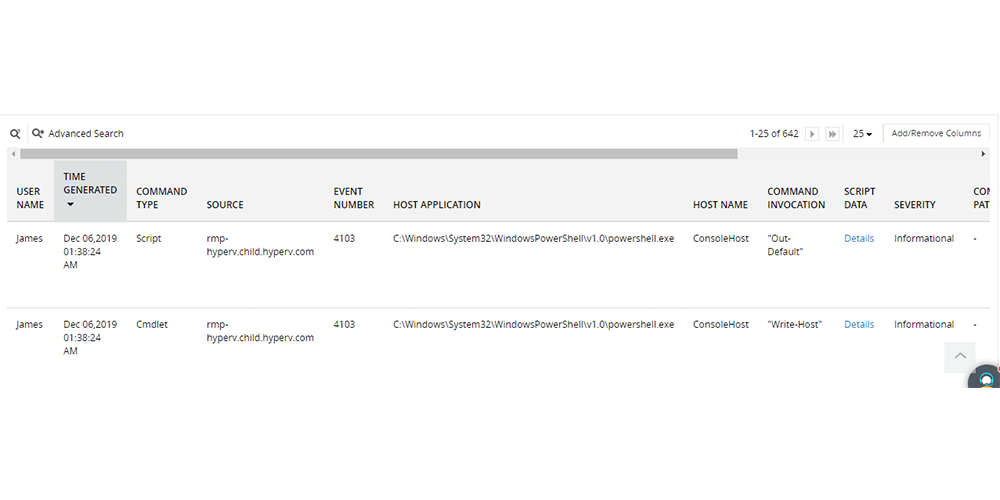
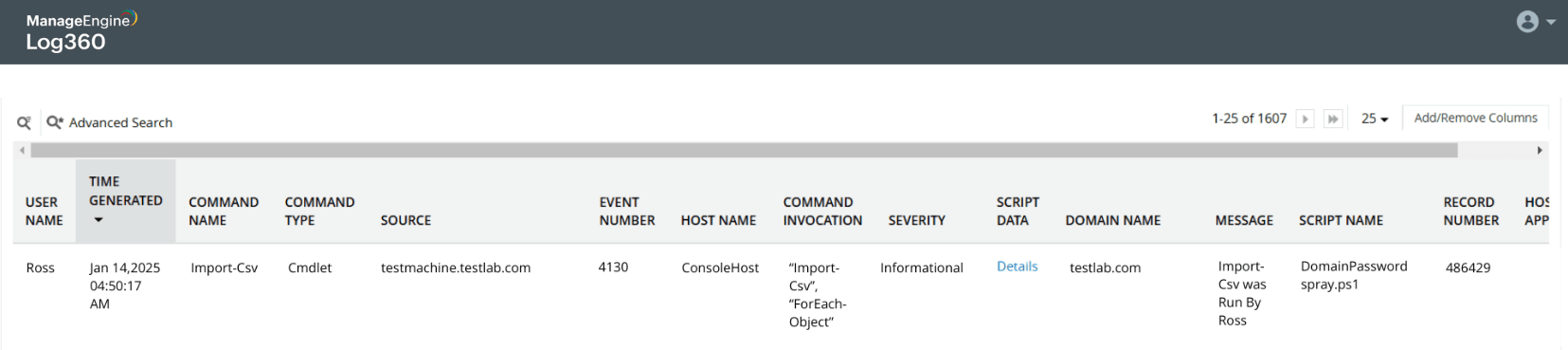
Read into script details
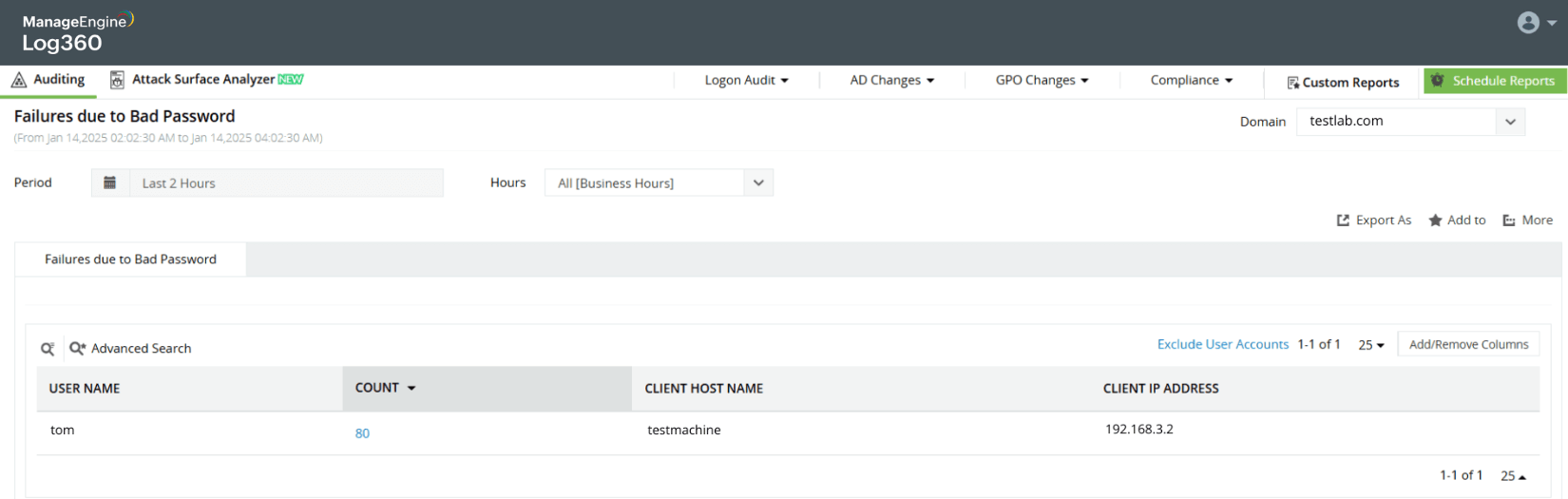
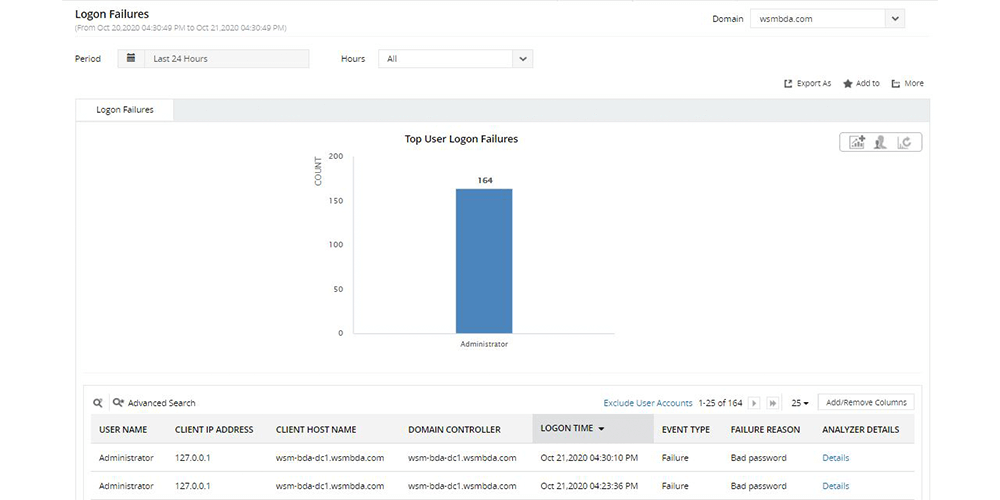
Capture logon failures
Detect scripts executed by end users
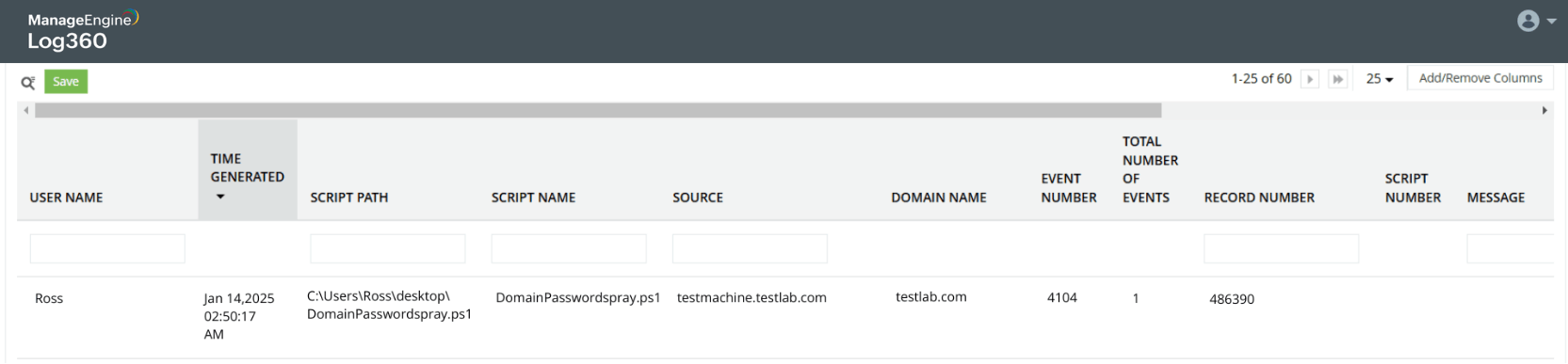
Detect execution of tools that will lead to pass the hash attack
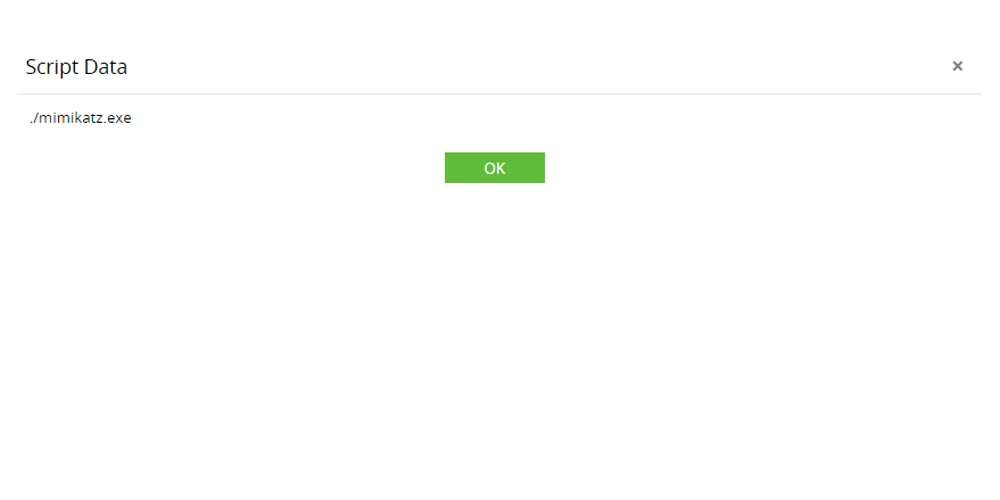
Detect brute-force attacks on Microsoft 365
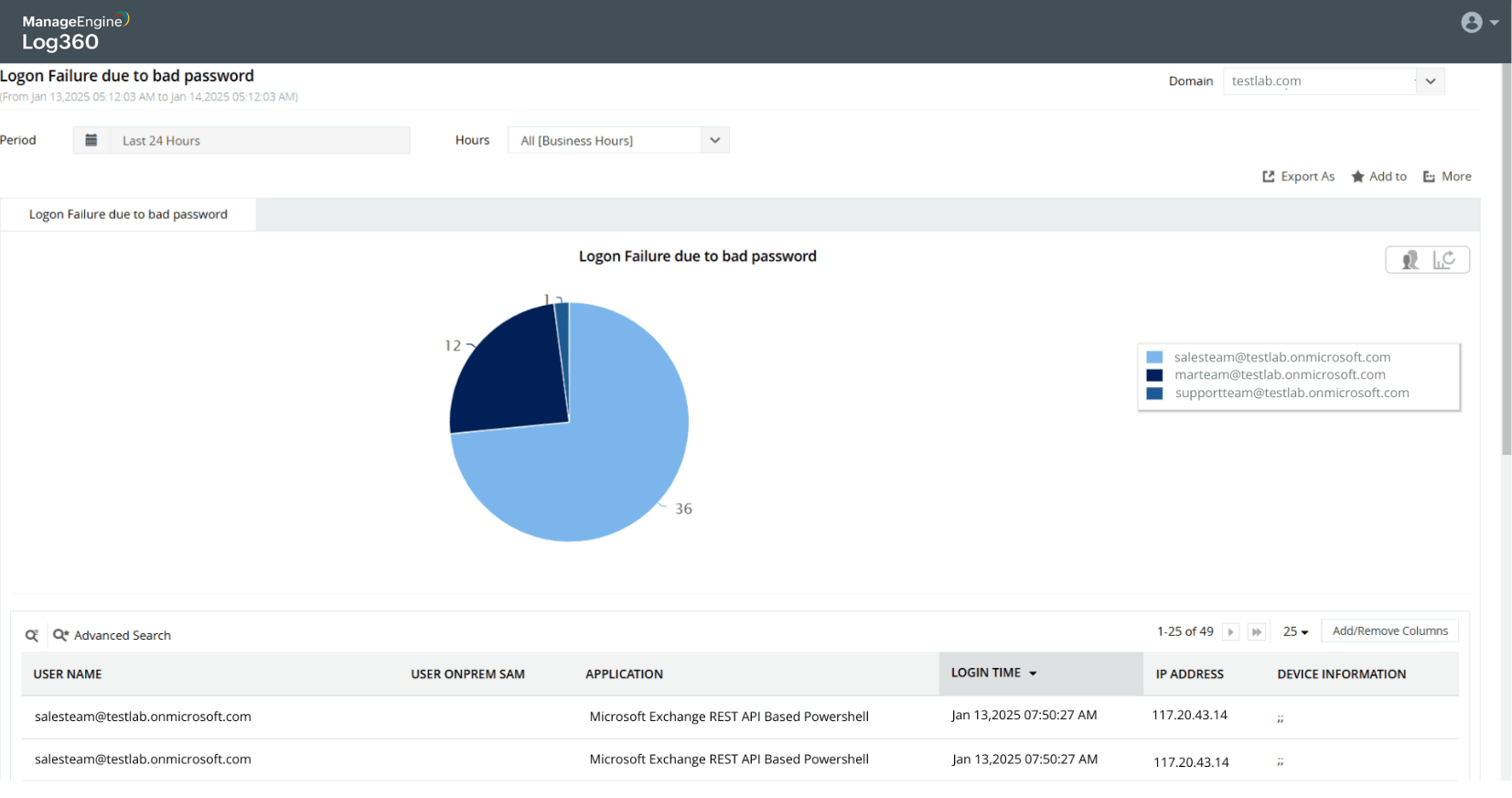
Capture details of malicious users, and see which network shares they accessed
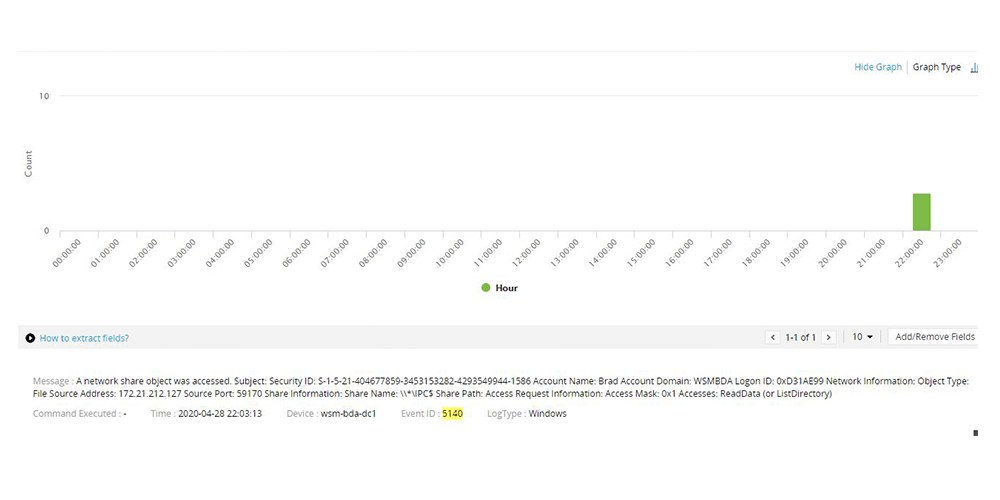
Detect illegal file copies using the expand process
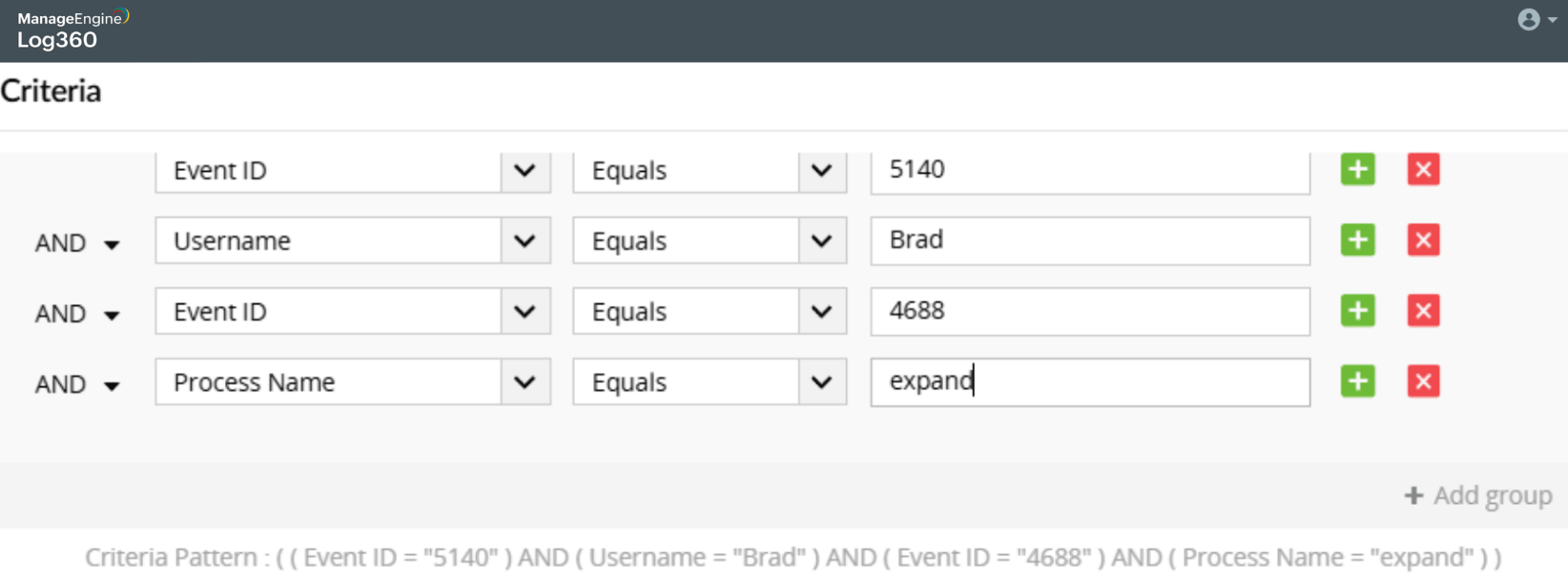
See the malicious service installation time

Detect malicious services
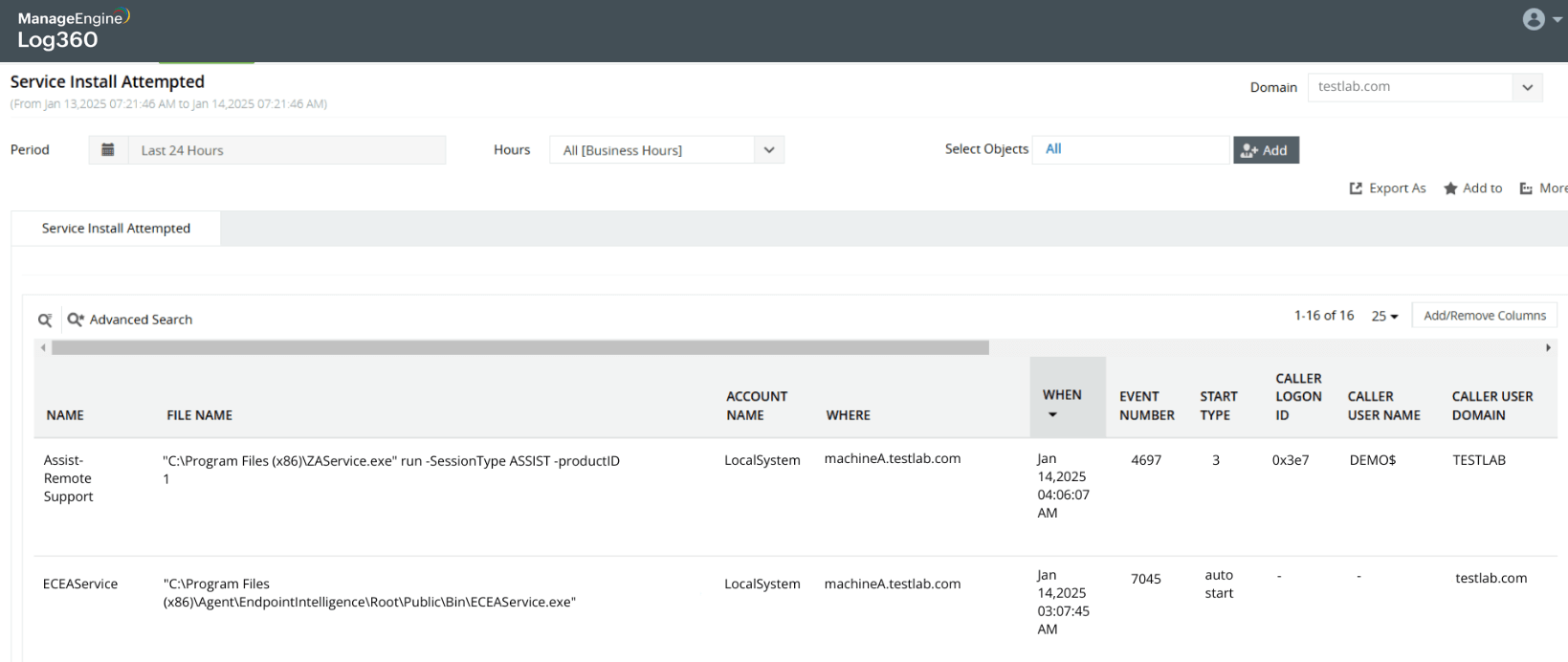
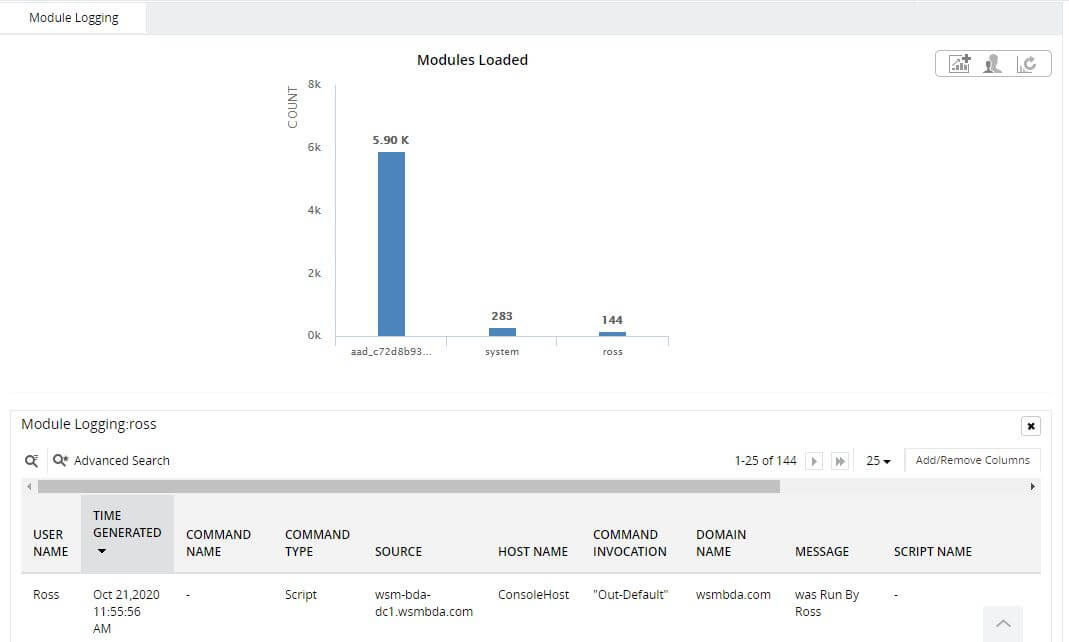
Capture malicious PowerShell modules and scripts
Find which users are trying to extract credentials from Local Security Authority Subsystem Service (LSASS) and when with timestamps.
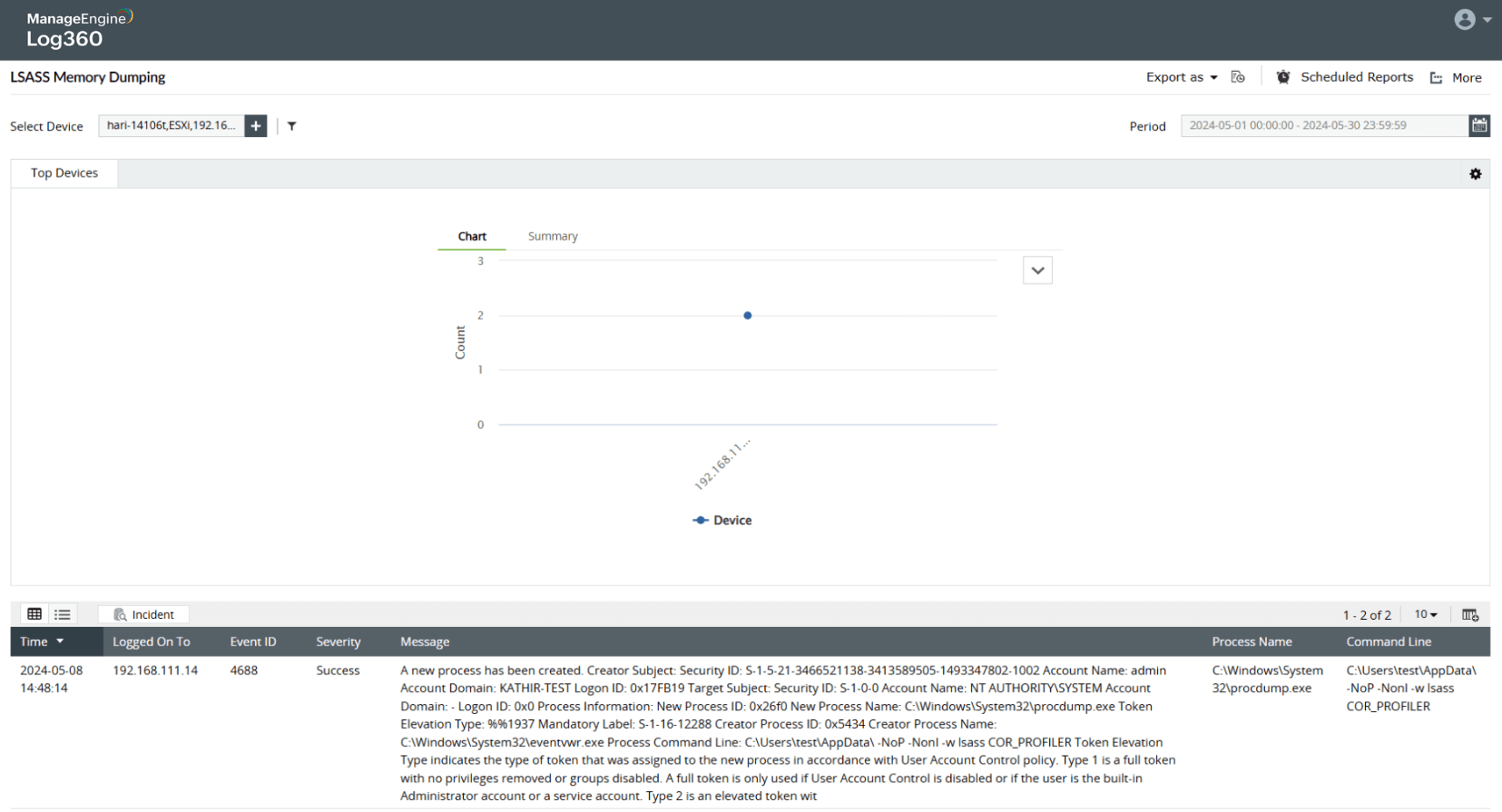
Filter events to detect LSASS dump attempts
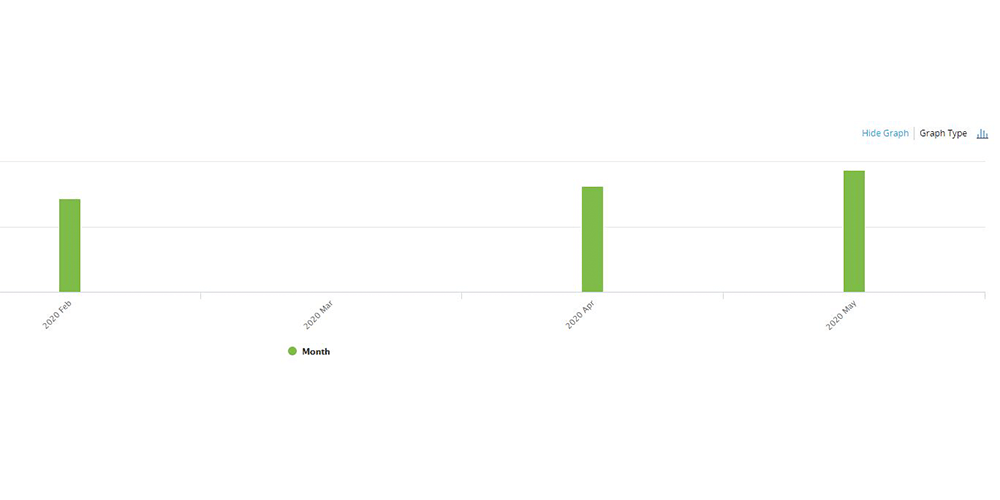
Discover malicious scripts
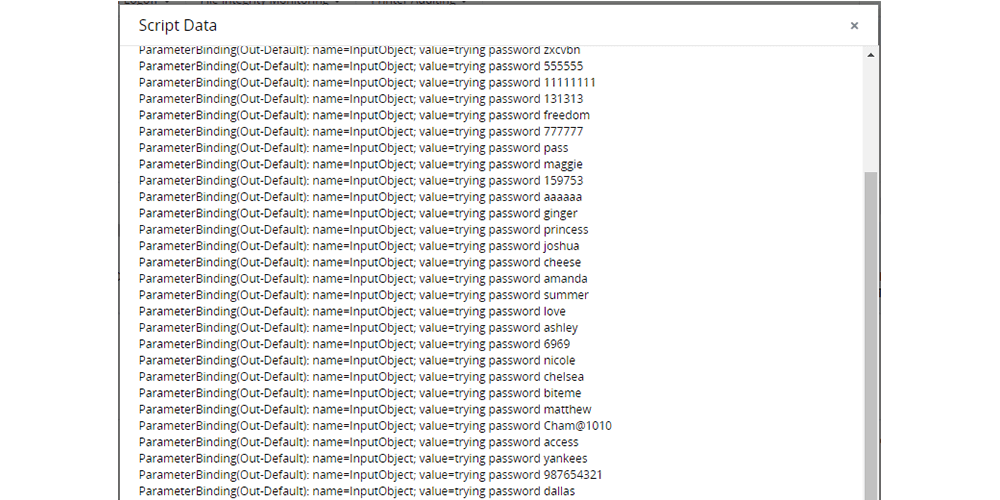
Detect scripts executed by users
Detect logon failures
Detect scripts that search for privilege escalation opportunities
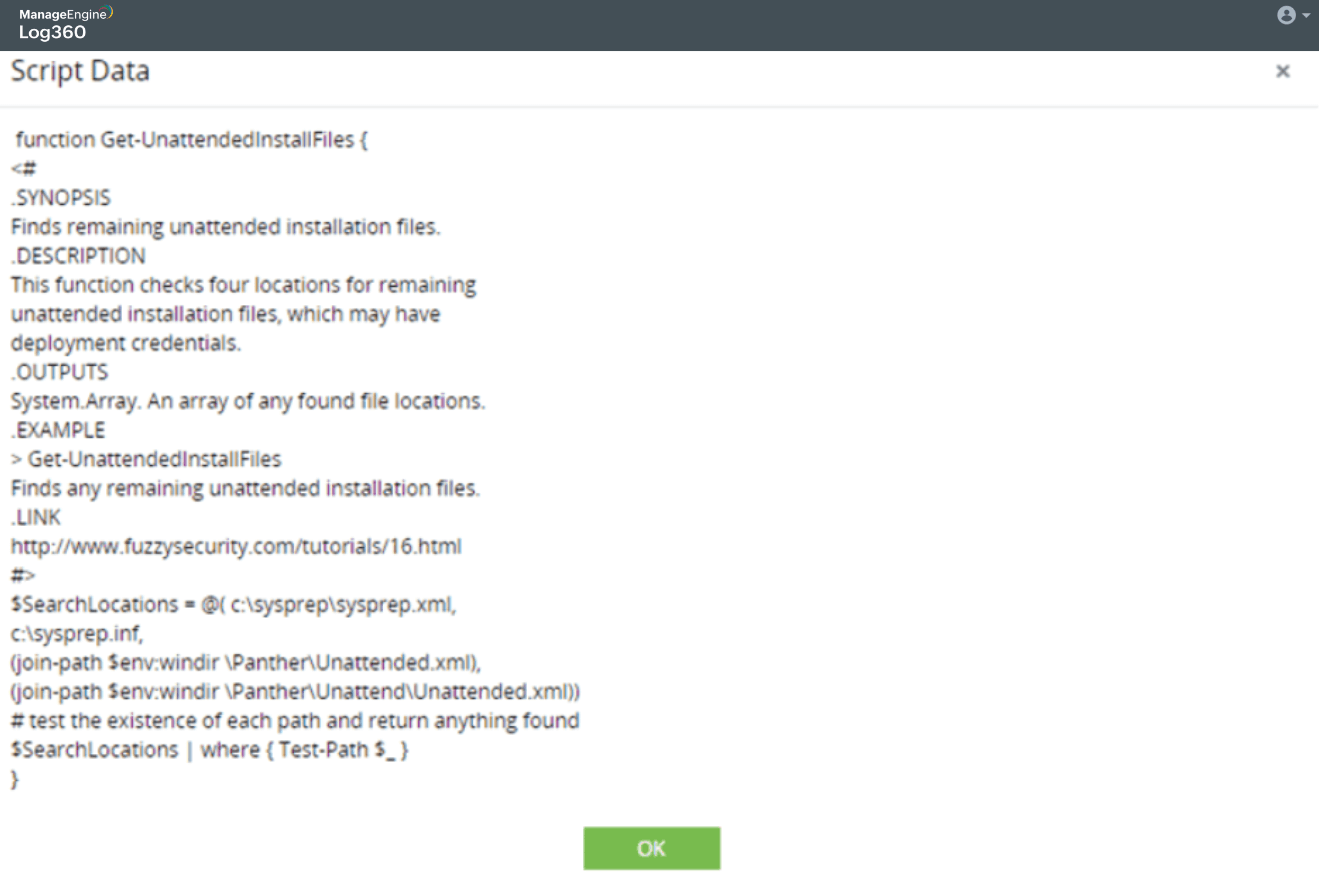
Detect scripts that install backdoor MSI apps
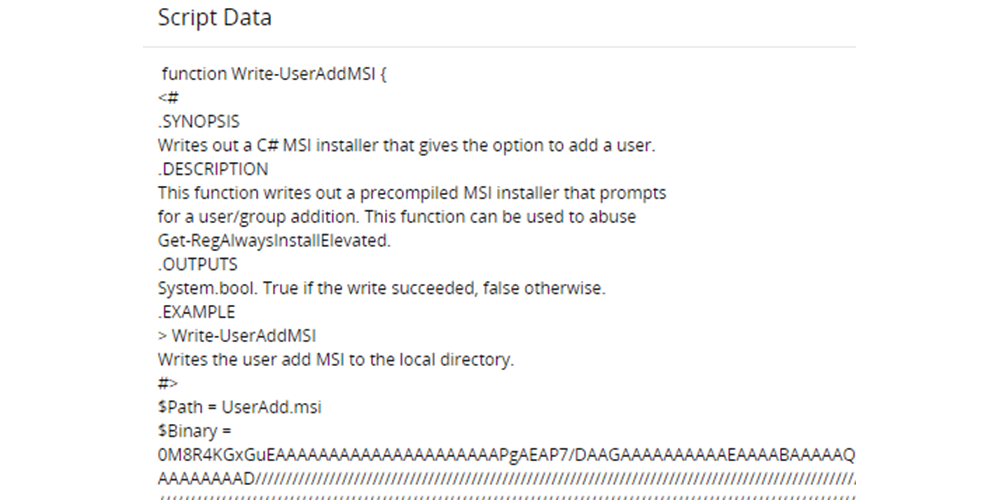
Discover the contents of the scripts executed by users
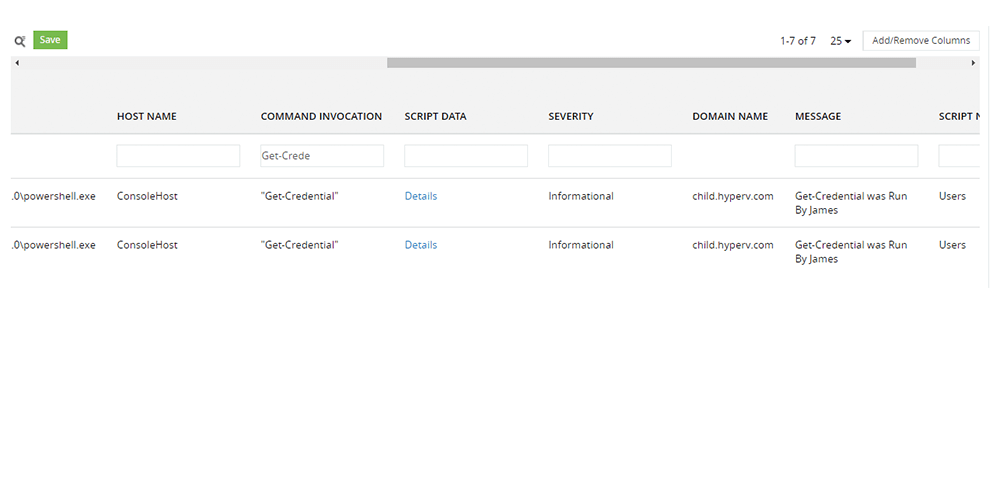
Discover login attempts to Exchange via command shells
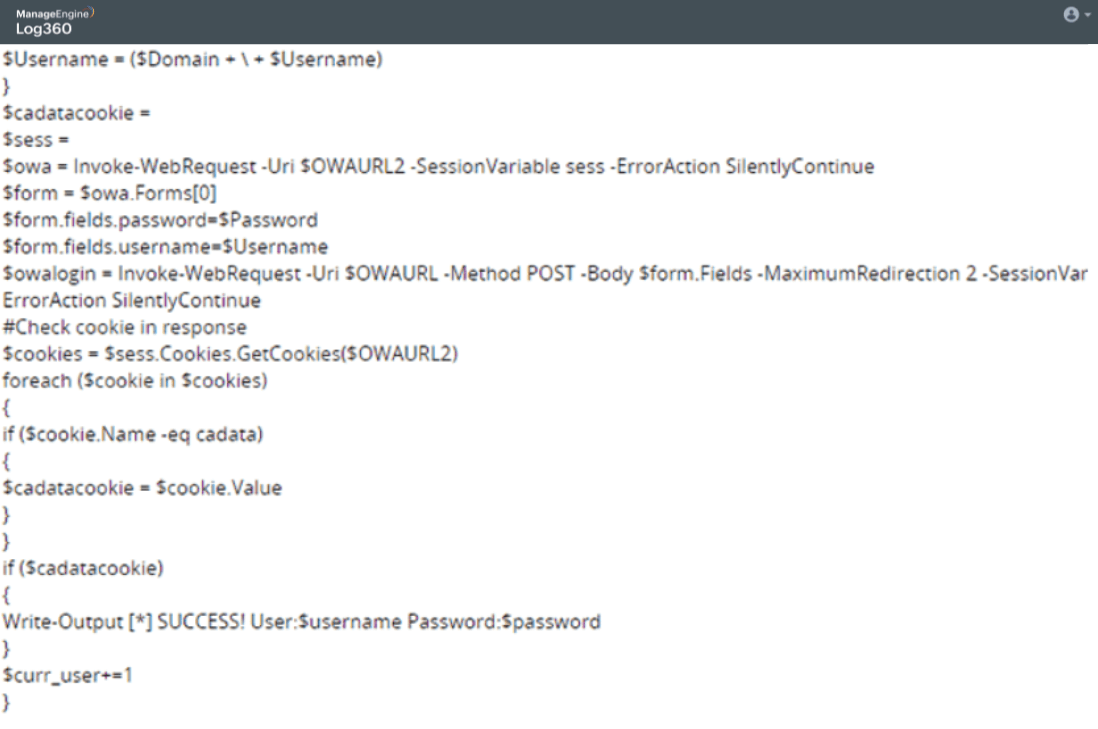
Capture suspicious commands invoked in PowerShell
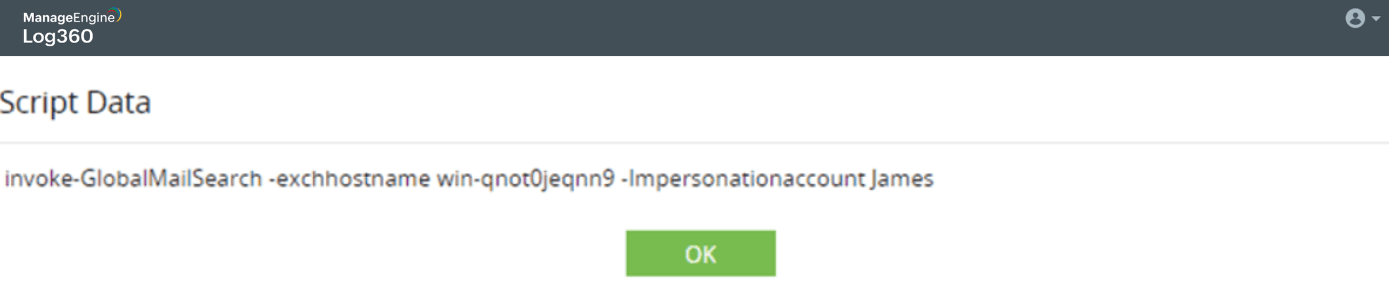
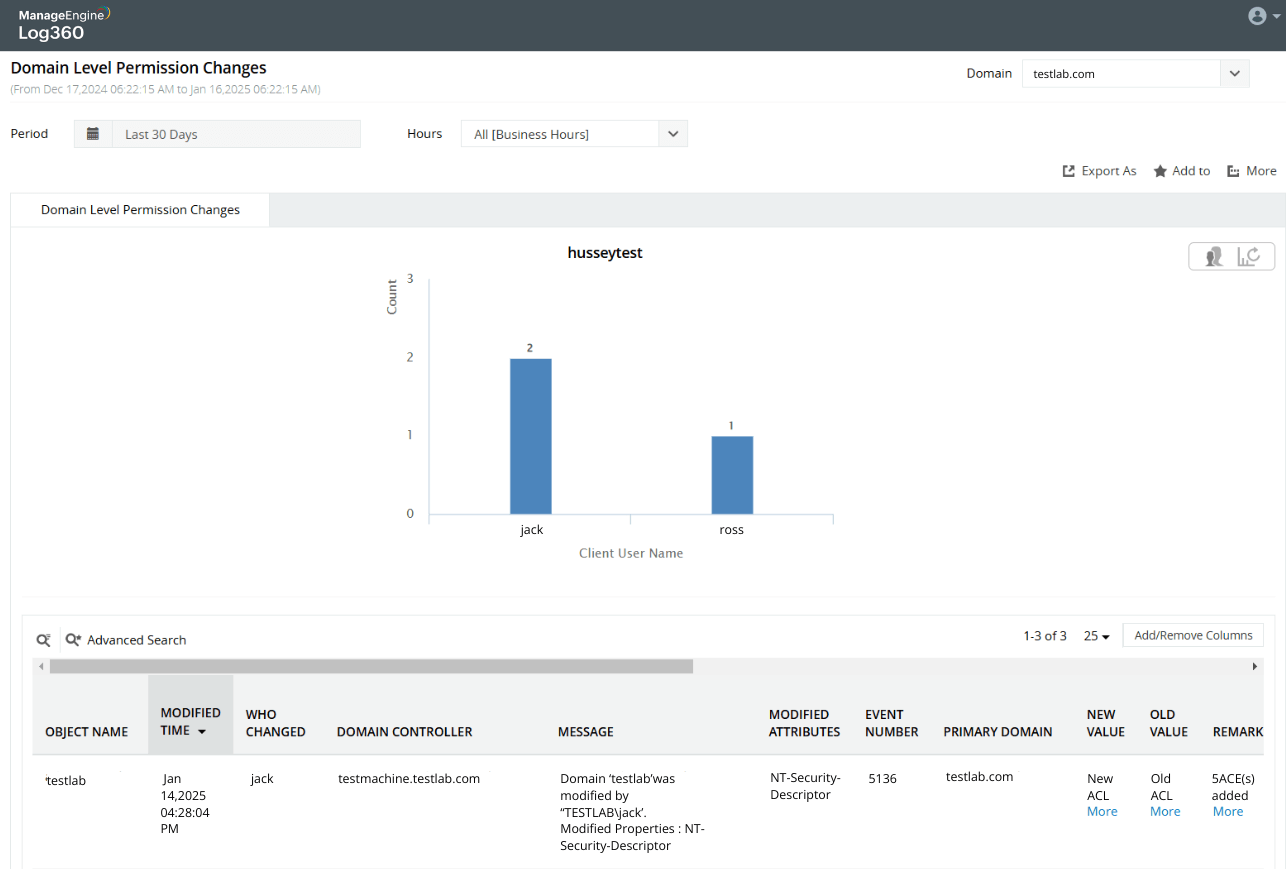
Capture permission changes on the domain
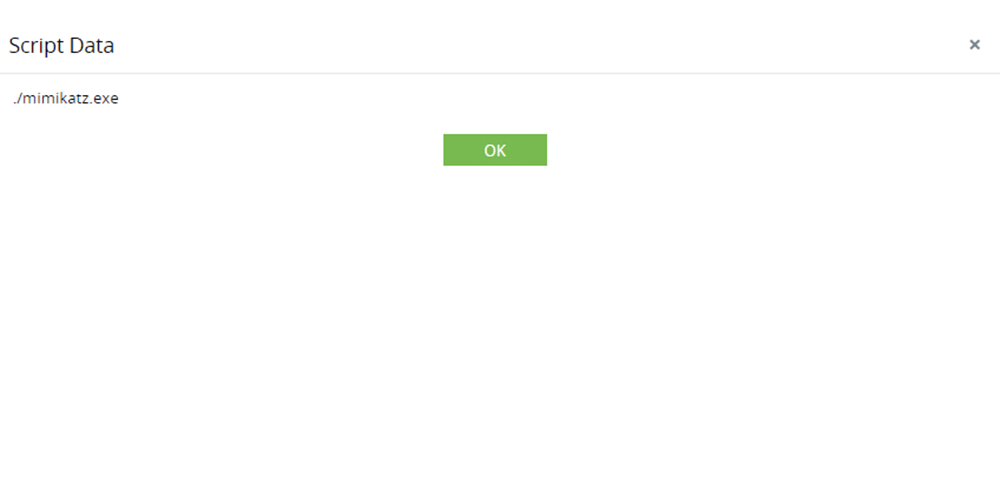
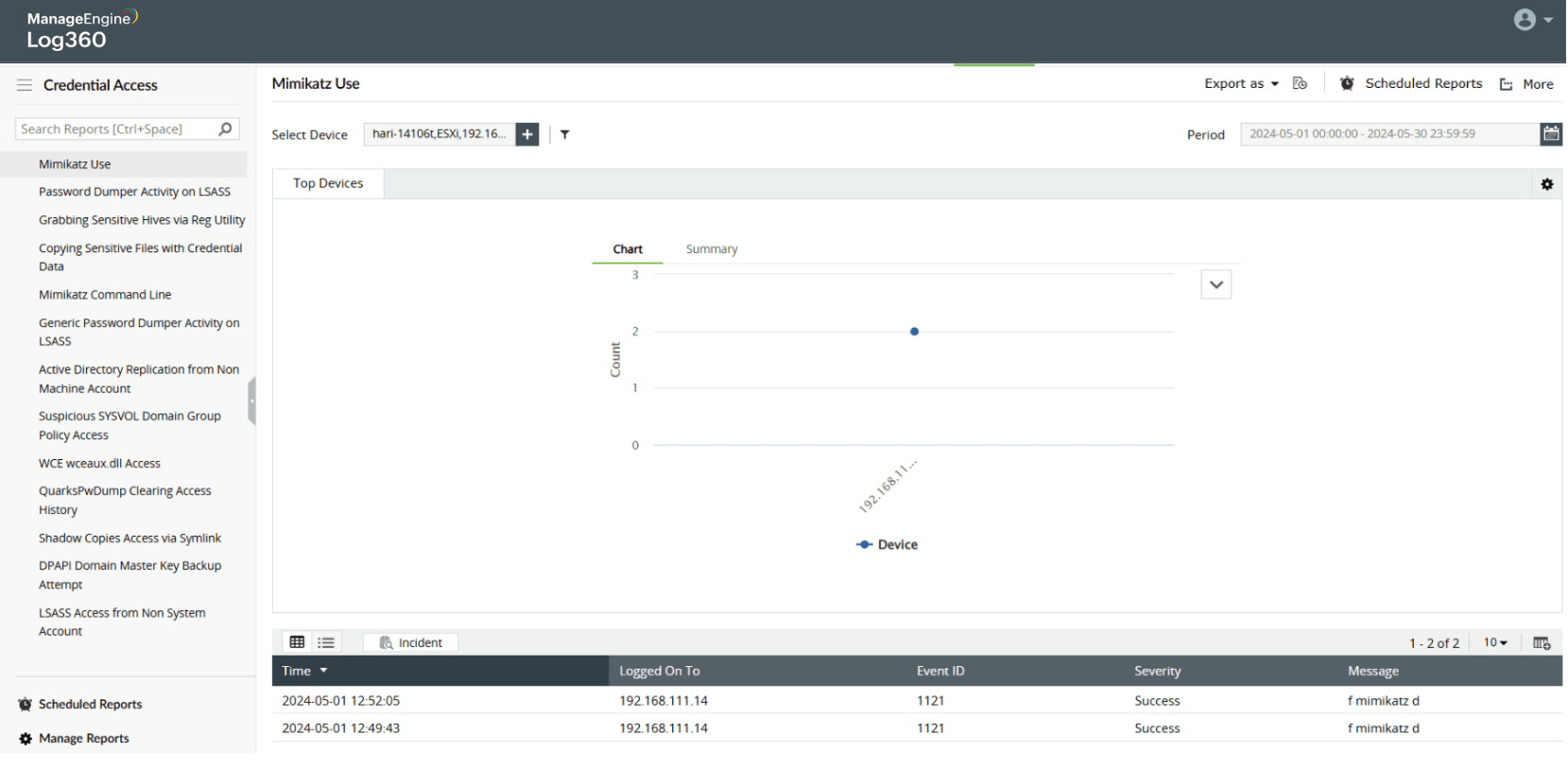
Detect execution of tools like Mimikatz
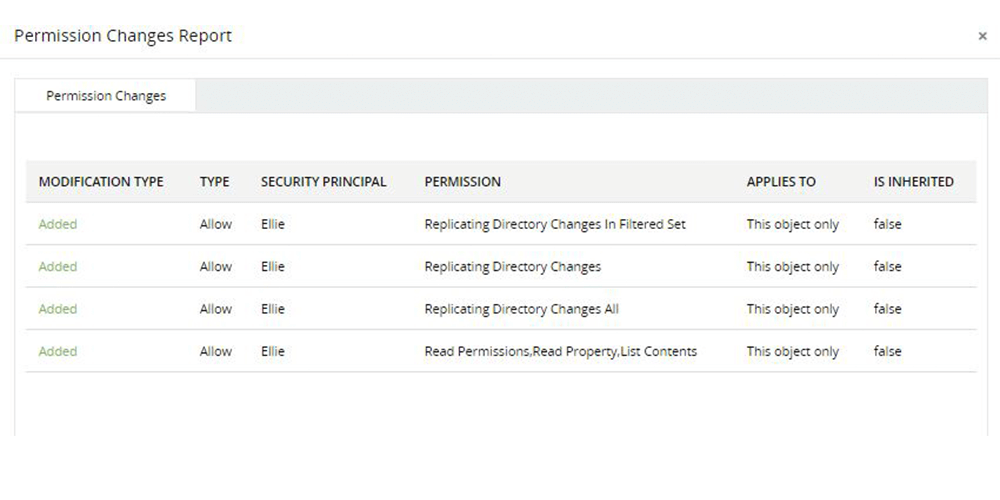
Determine the exact permission modified
Track service principal name (SPN) changes to computers, which can be an indication of rogue DCs
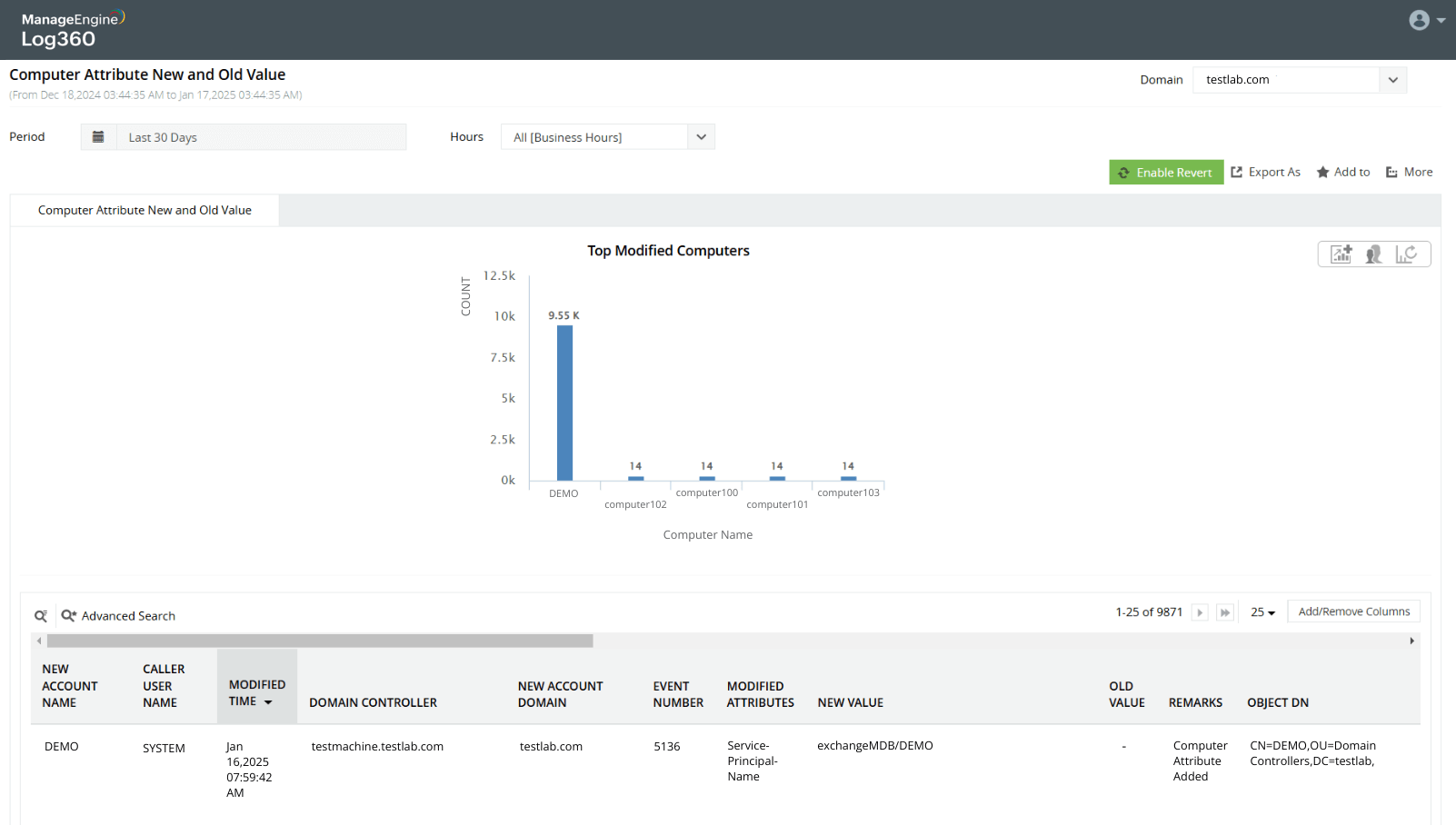
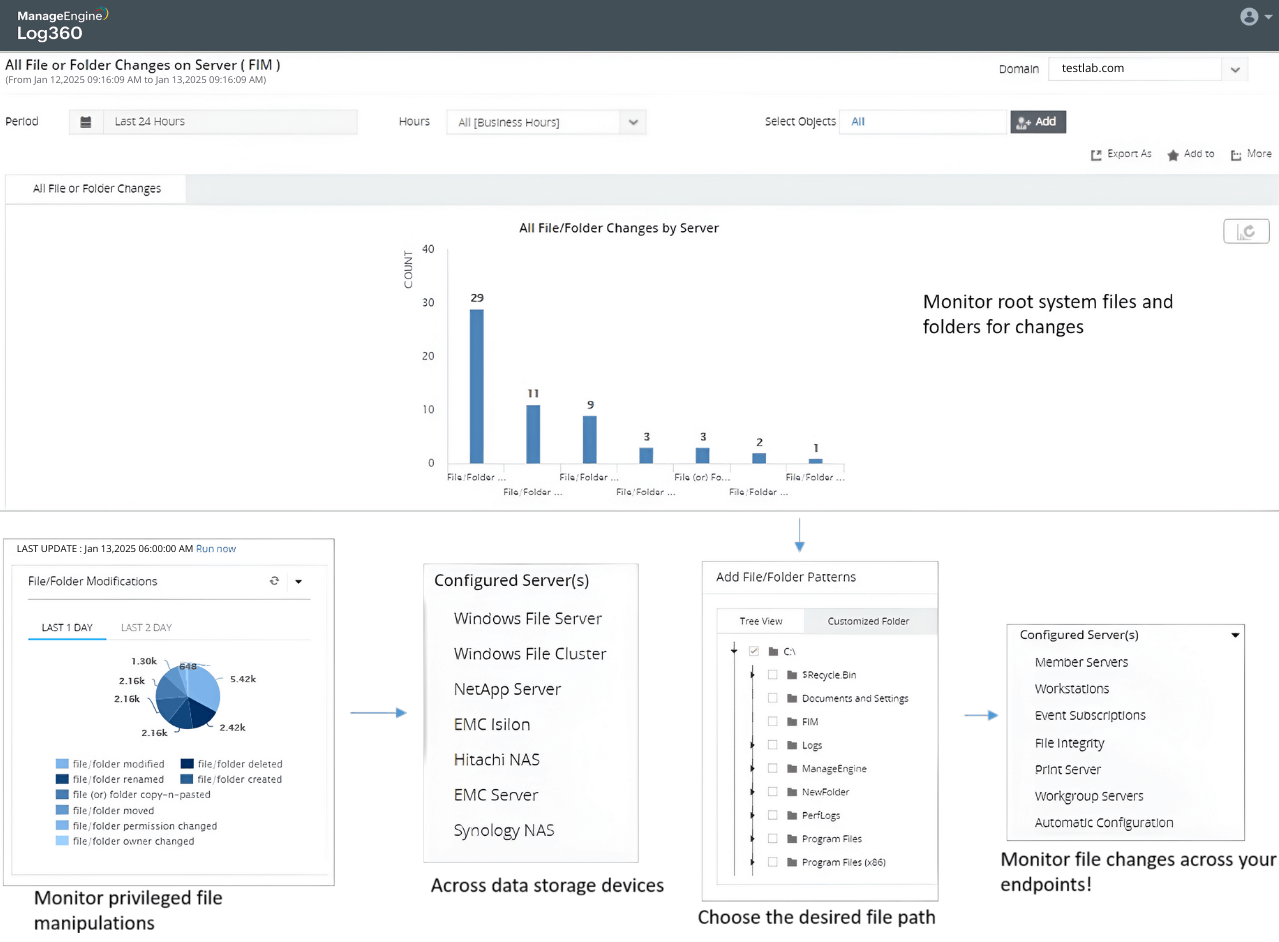
Monitor files and folders for unauthorized modifications
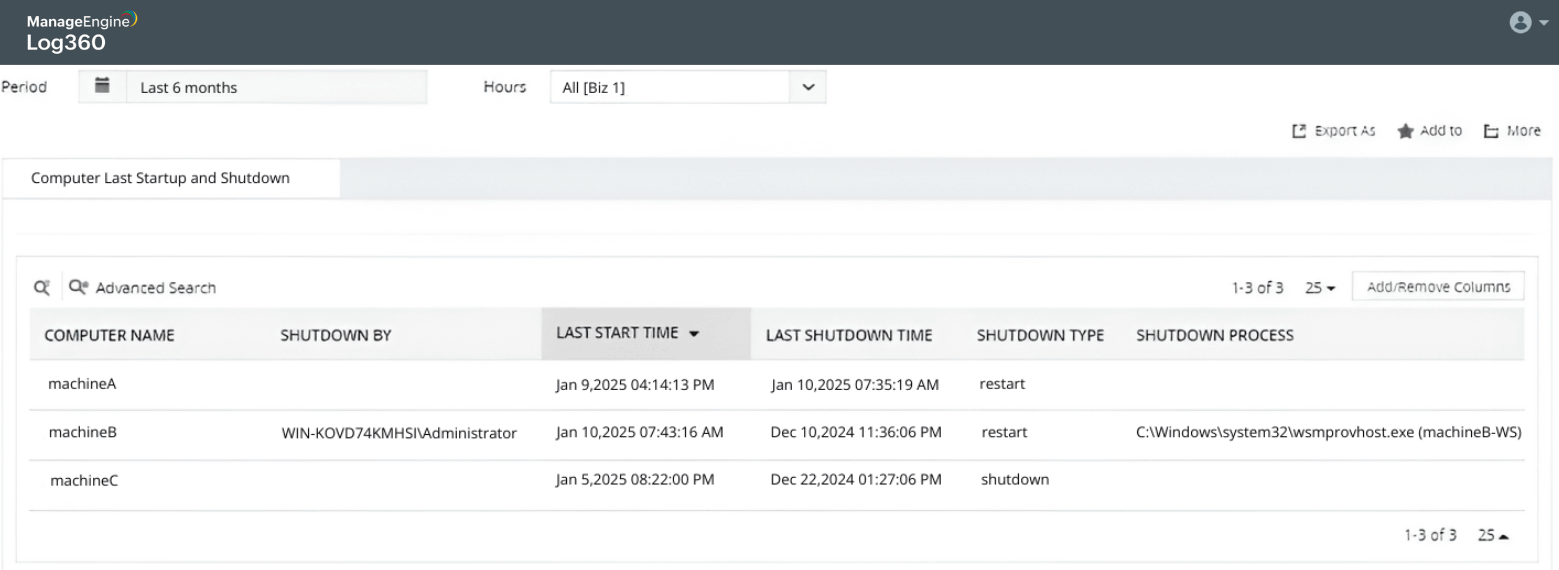
Detect computer startup and shutdown
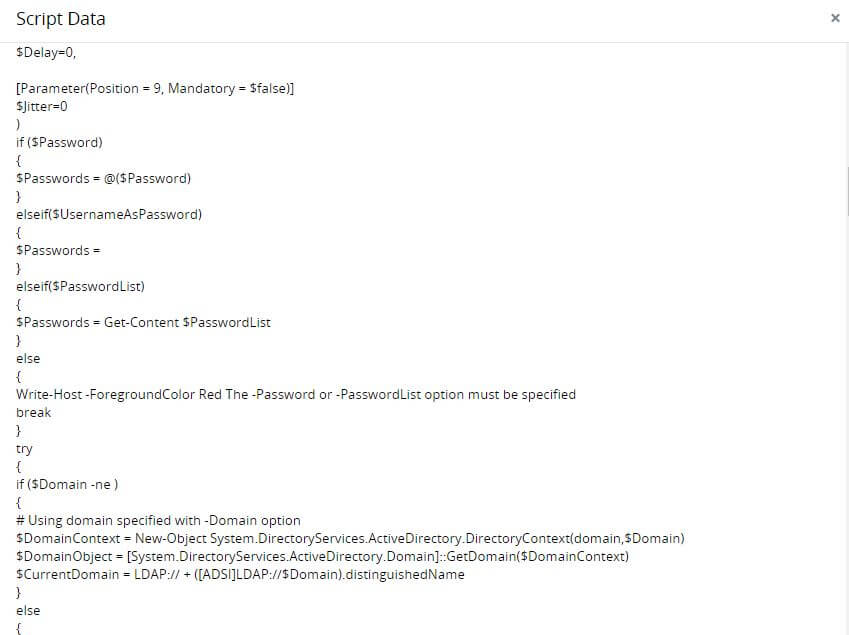
Read into script details
Detect scripts executed by end users
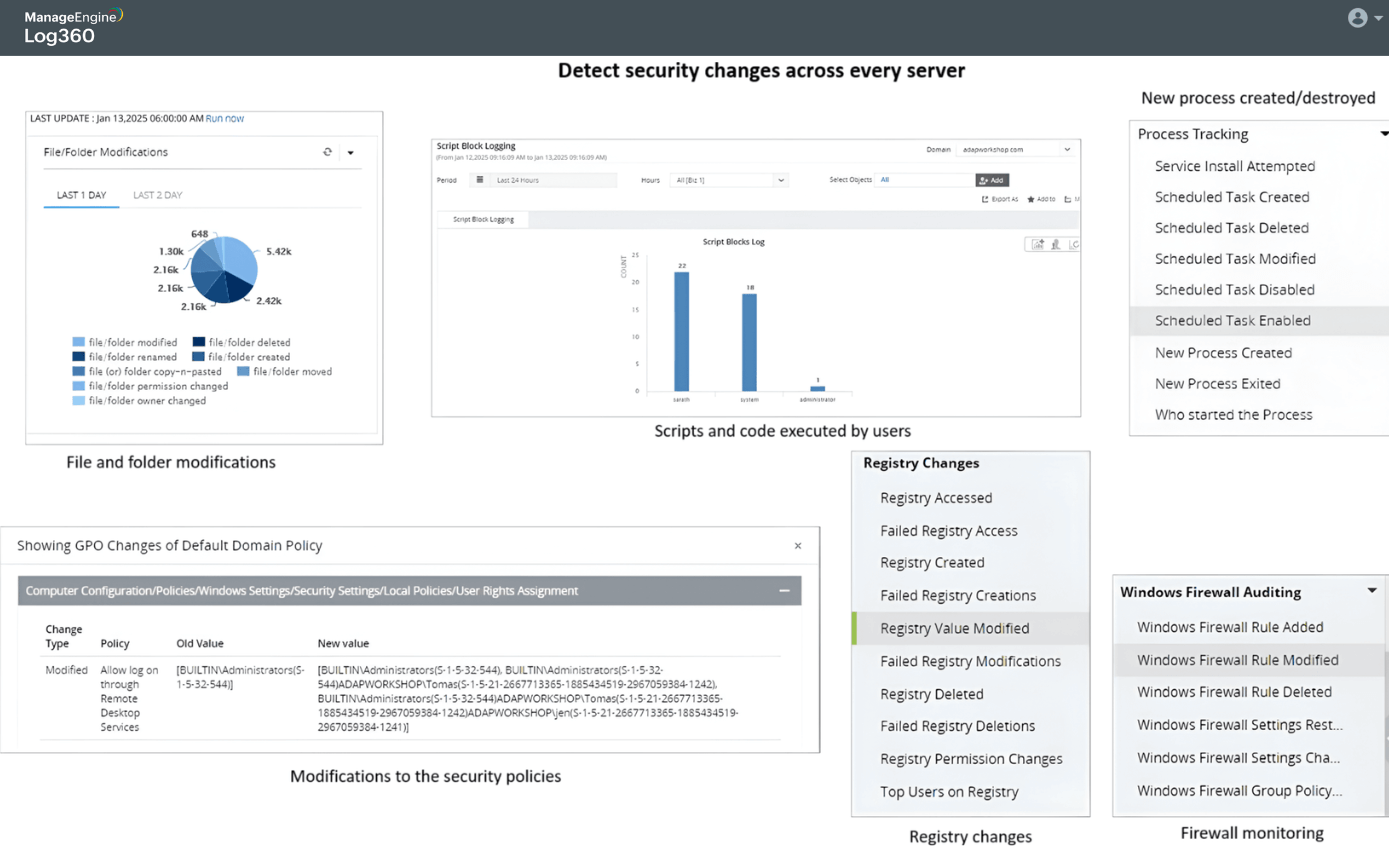
Detect Security Changes
Correlate security changes to detect ransomware attacks
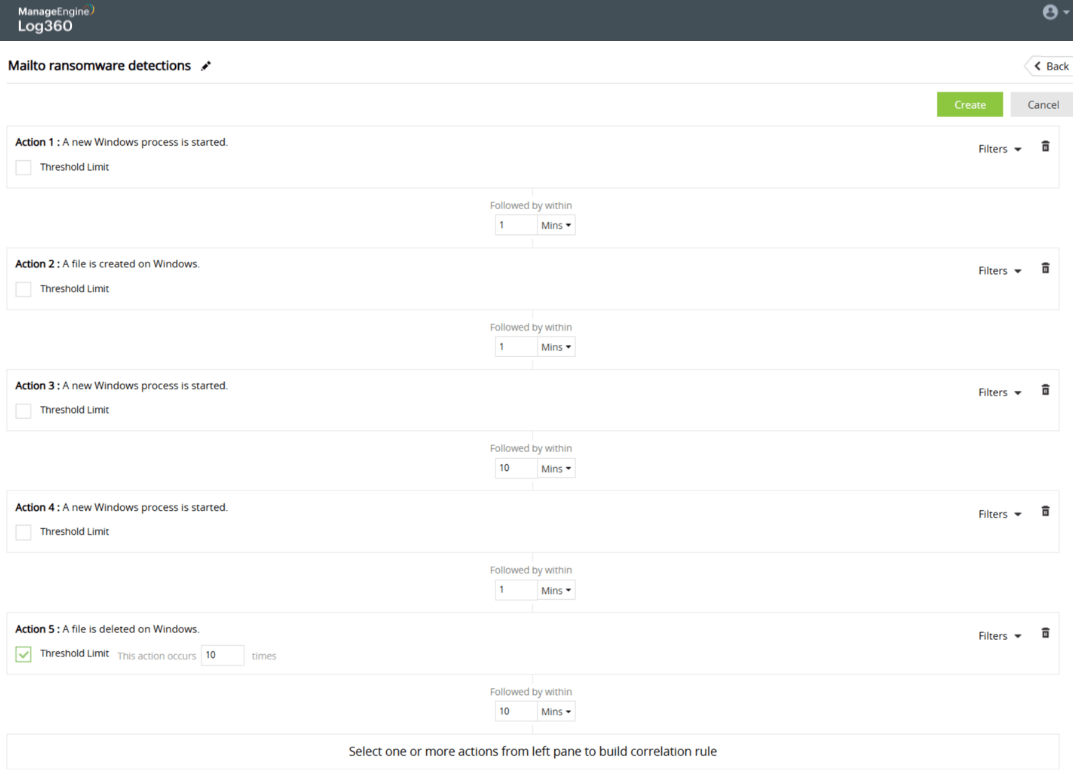
Correlate security changes to detect ransomware attacks
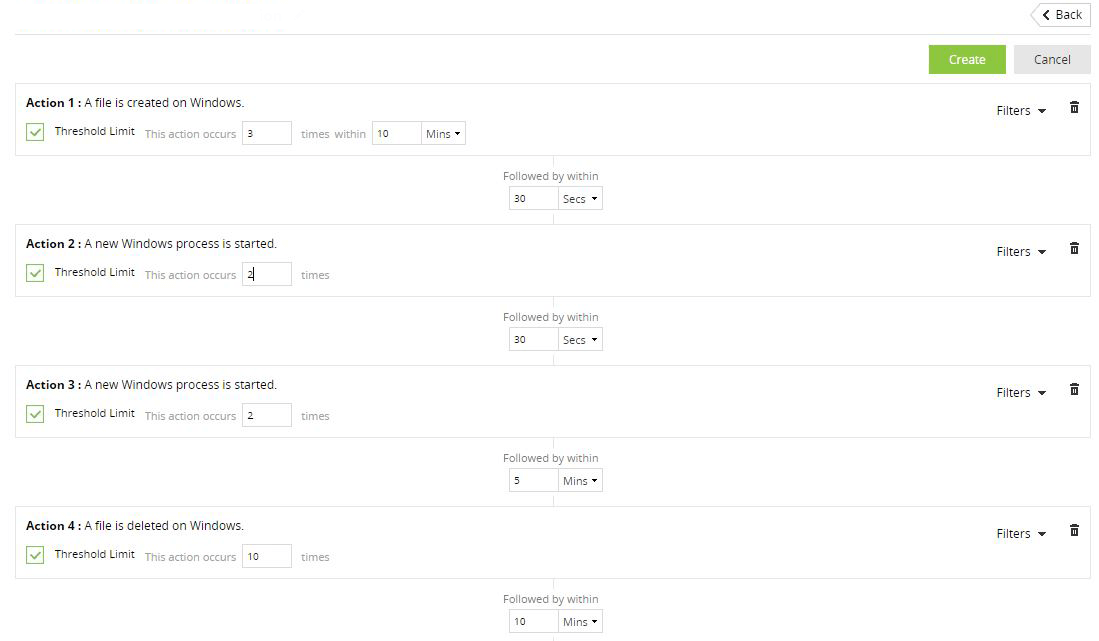
Determine the exact commands run by your users
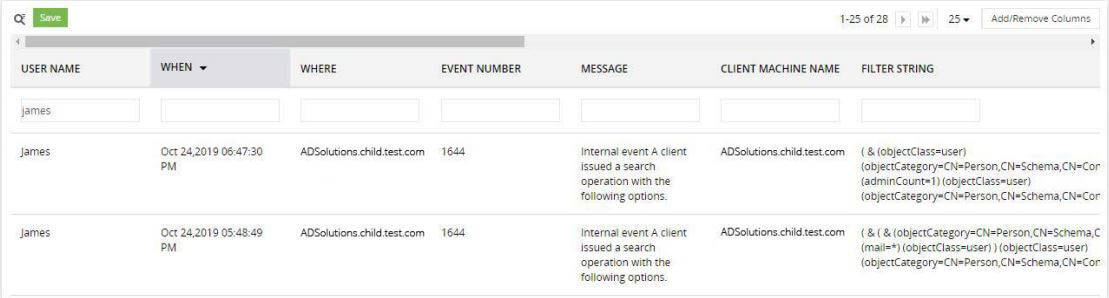
Build customized alerts based on recon commands or scripts
Detect recon commands invoked and scripts executed on command line interfaces (like PowerShell)
Alert on recon attempts
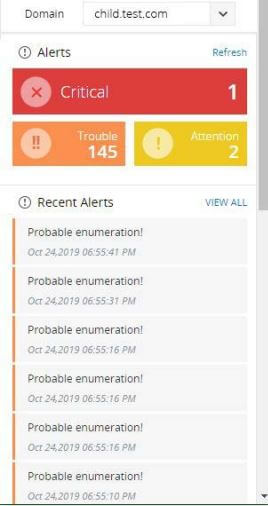
Discover password attacks on Azure environments by monitoring logons
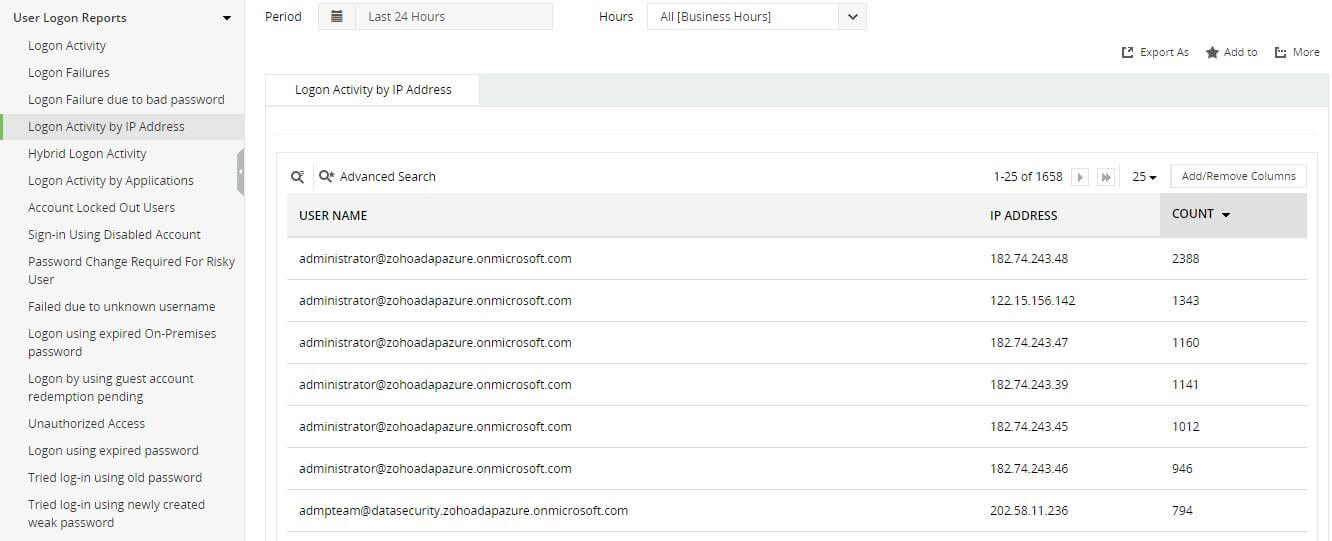
Detect the execution malicious tools used to obtain password of AD users via Azure sync account
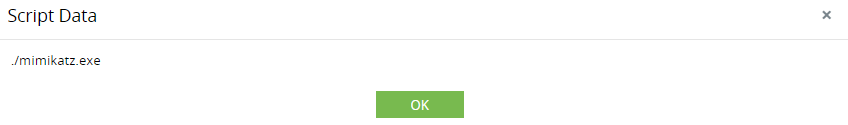
Detect attacker's attempts to obtain information on Azure tenants via command line shells
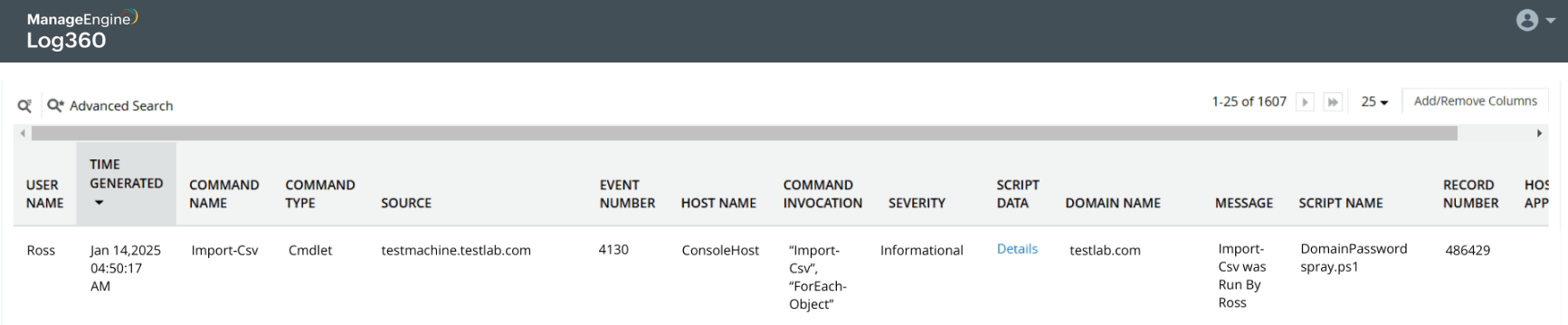
Capture backdoor script usage in Group Policy Objects (GPOs)(an attempt to capture user credentials)
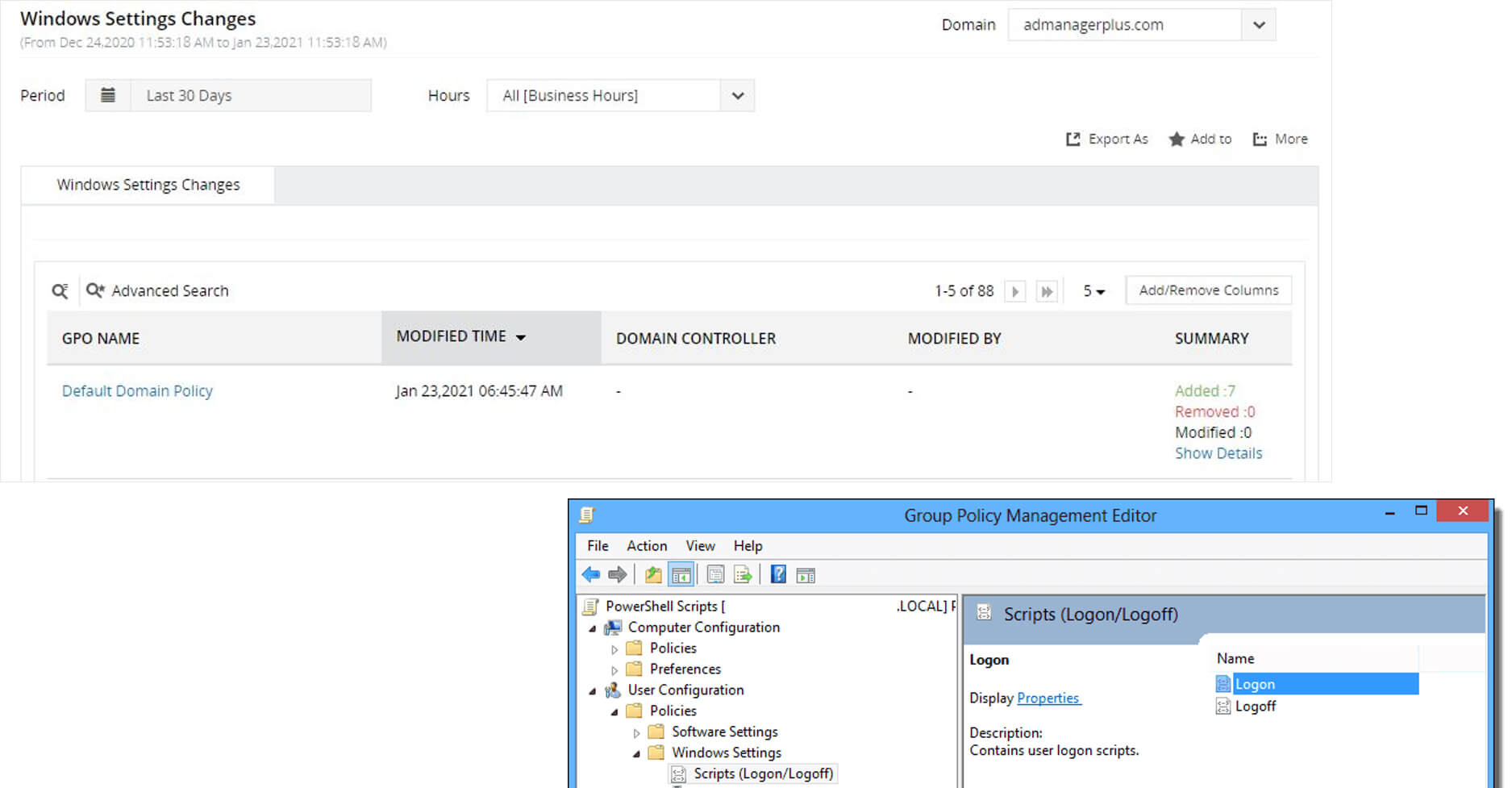
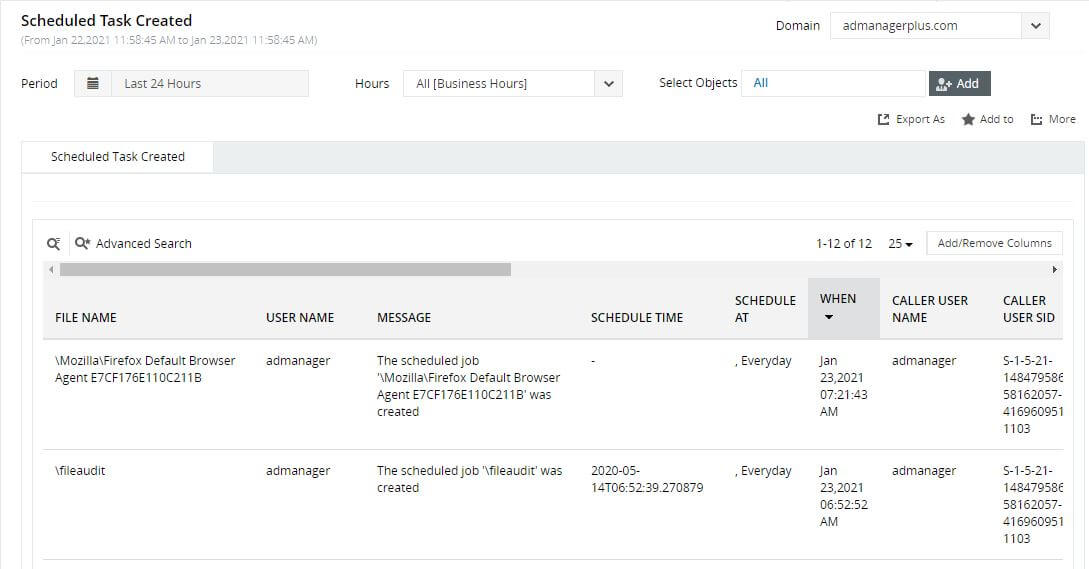
Detect creation and modification of scheduled tasks (often leveraged to introduce backdoor scripts to extract credentials)
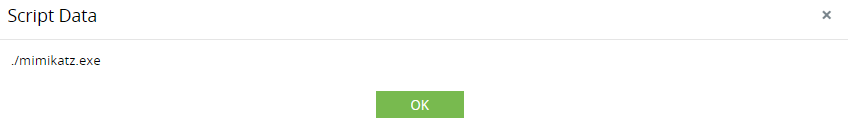
Detect the usage of malicious scripting tools used to dump credentials from a server
Capture the exact commands executed by attackers to discover accounts with SPN (Service Principal Name) values
Discover malicious scripting tools used to extract the targeted service account tickets
Monitor your AWS instance for unauthorized IAM activity like logon failures, Access key misuse and more
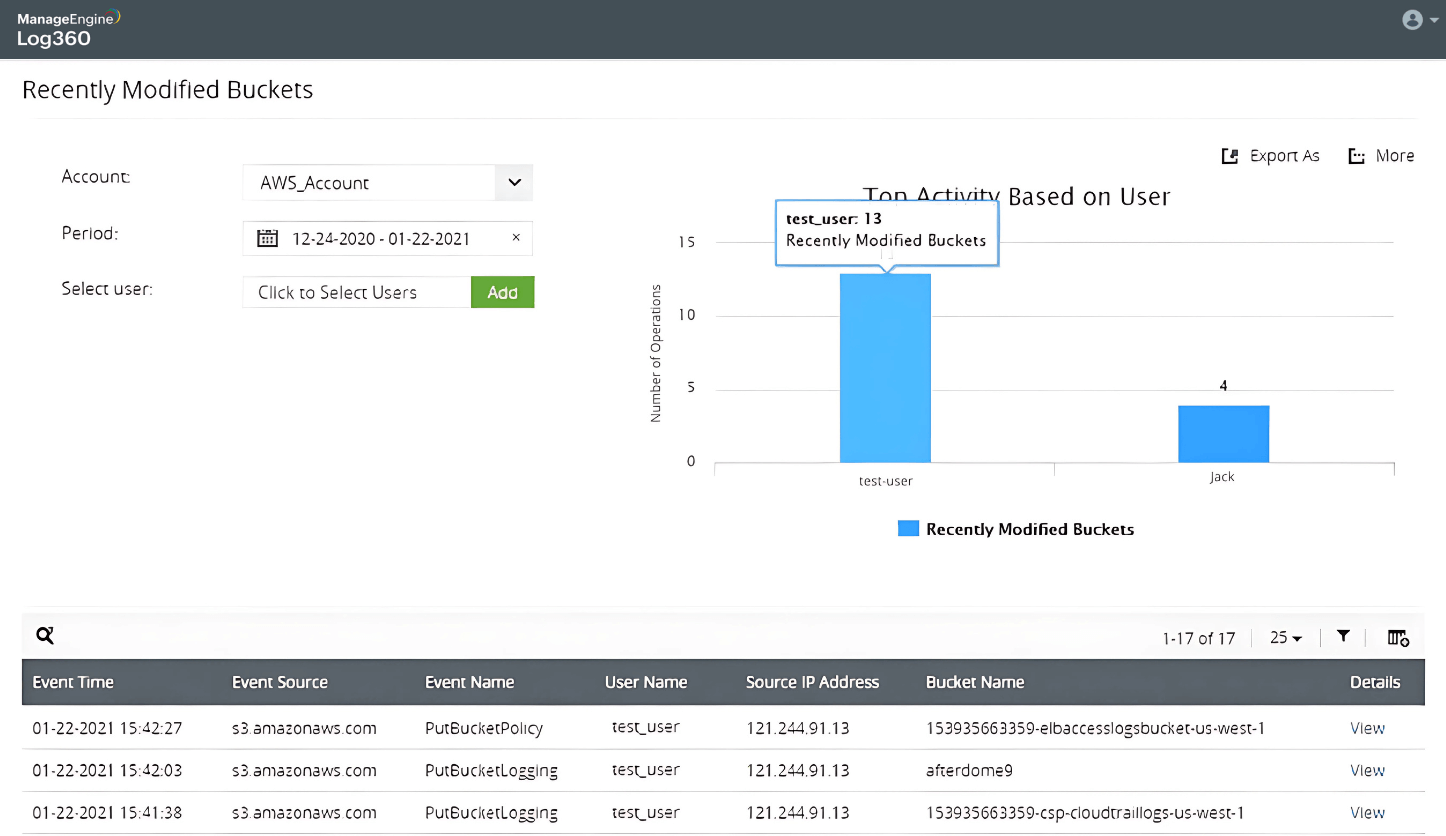
Detect permission changes on S3 buckets
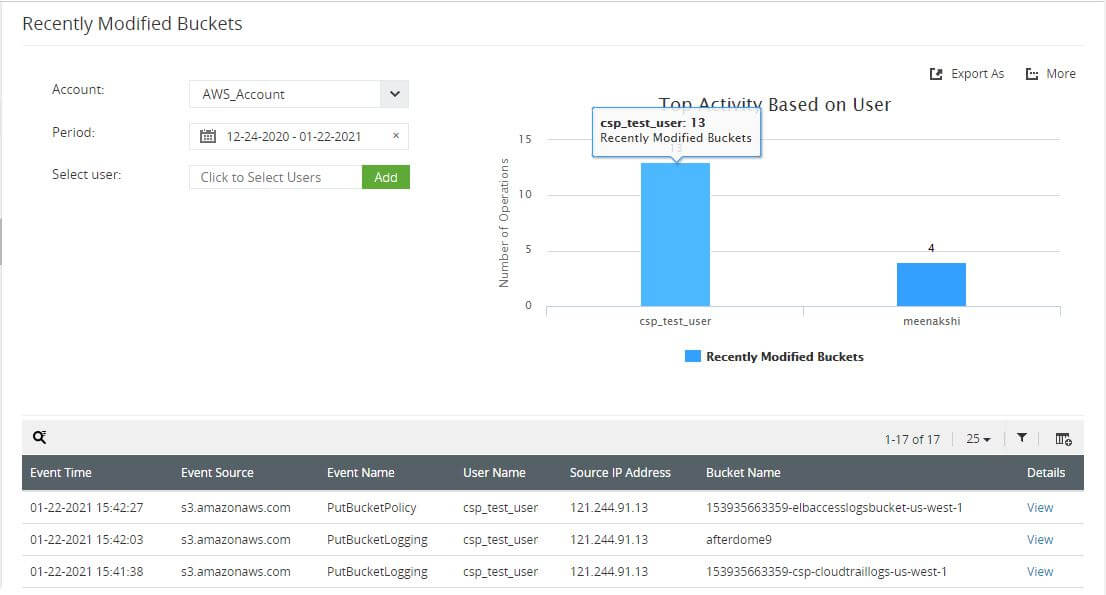
Capture ransomware attack attempts by detecting changes on the objects in S3 buckets
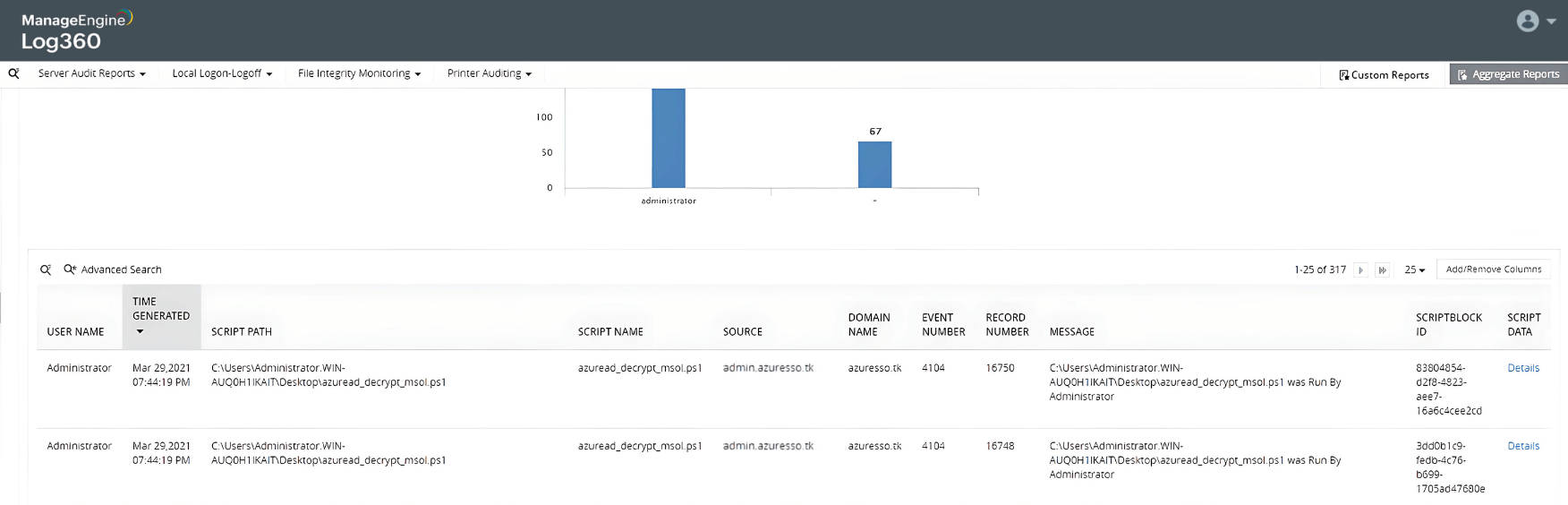
Detect scripts used to extract the credentials of Azure connector account (MSOL_nnnn)
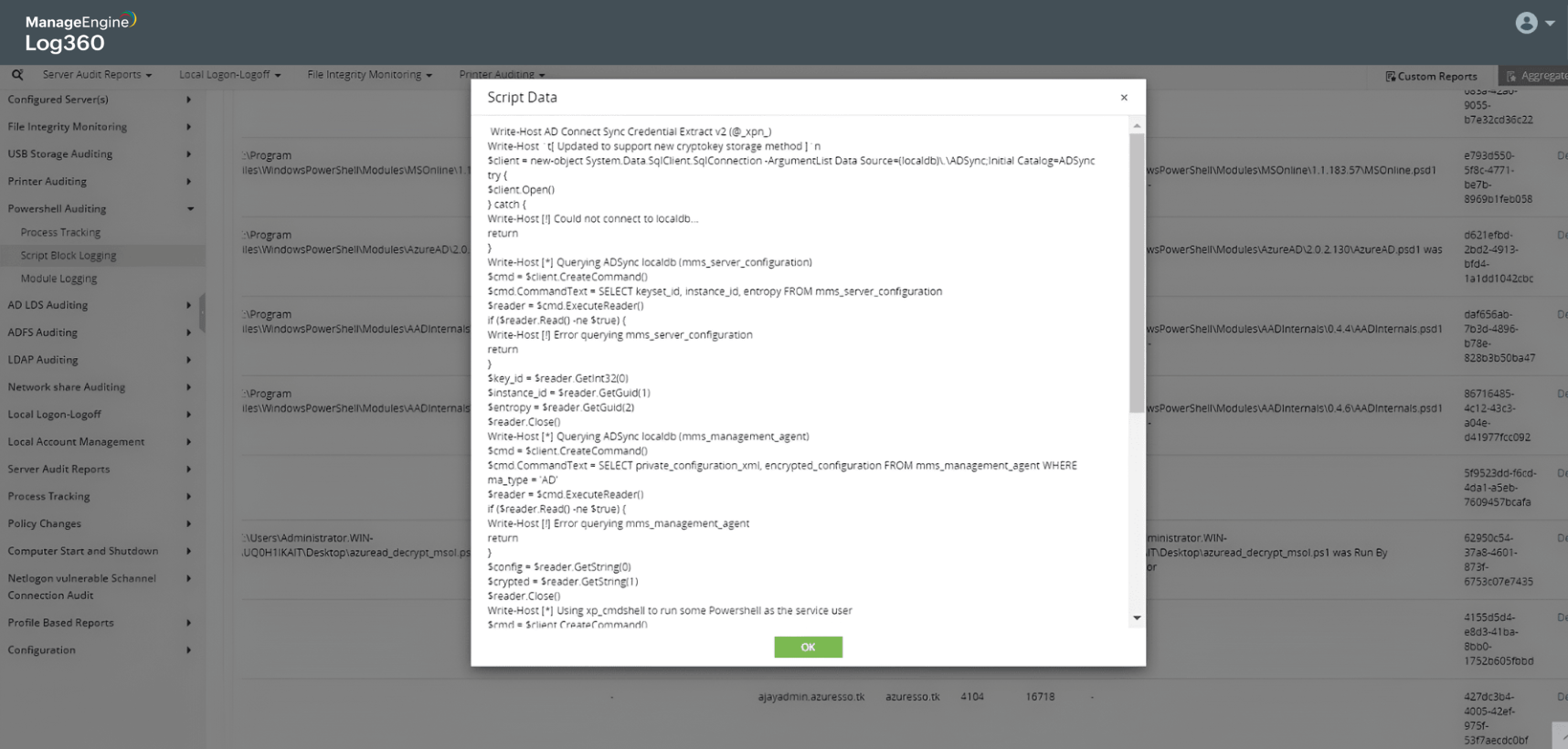
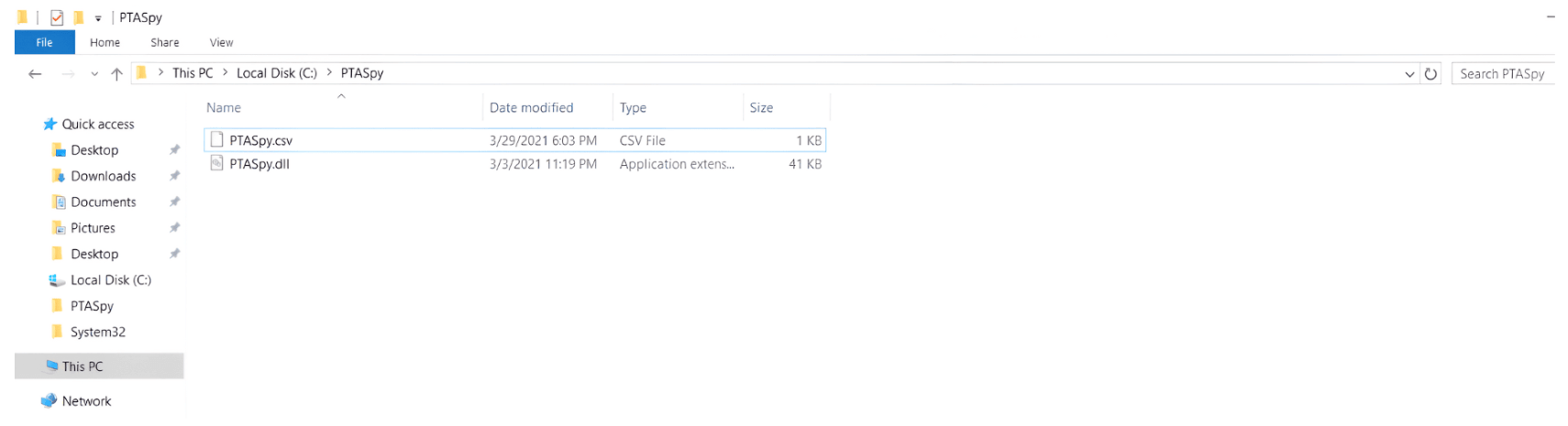
Detect attempts to intercept PTA agent and capture user passwords
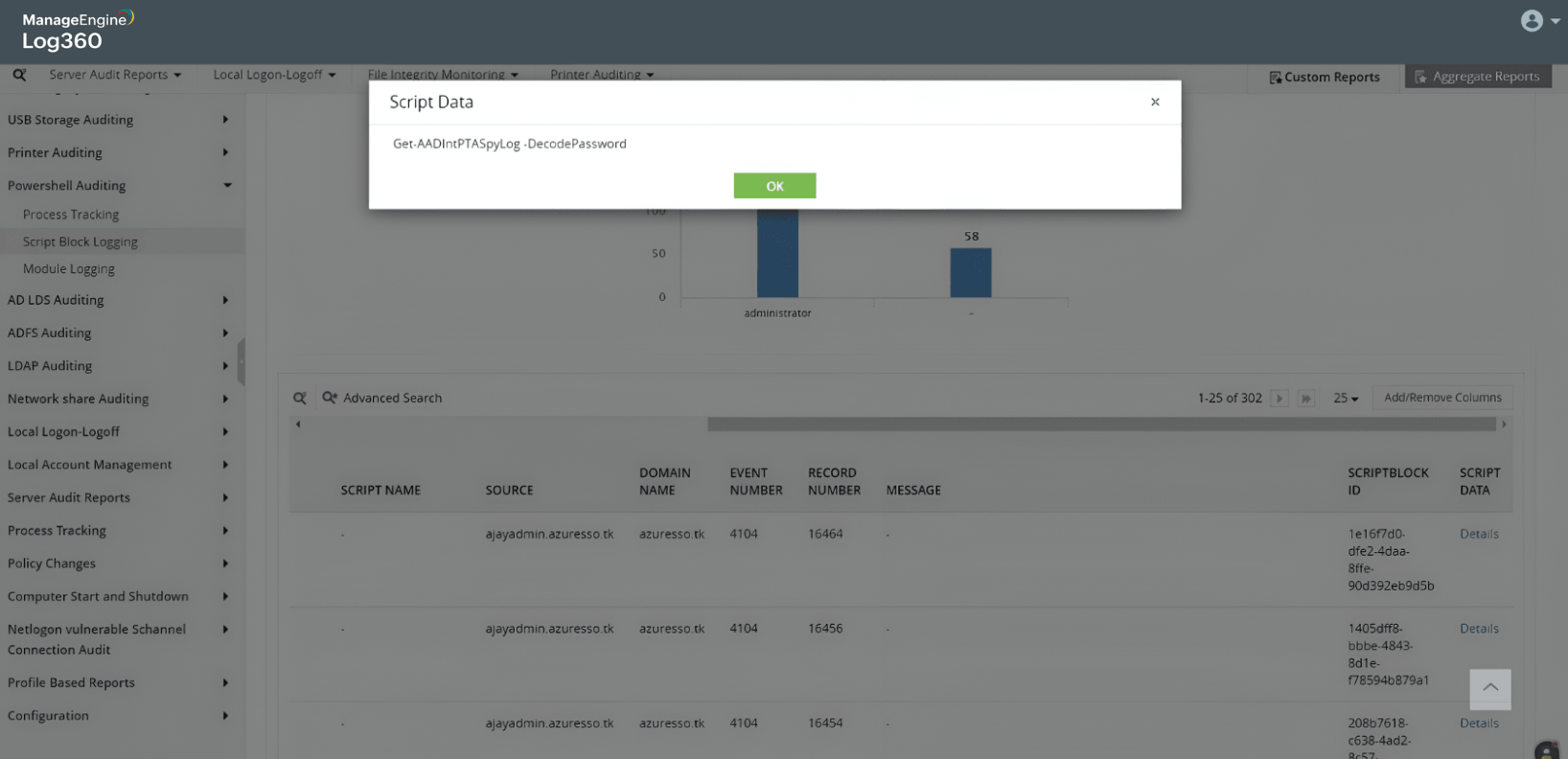
AADInternals - A malicious PowerShell module used in PTA interception attacks
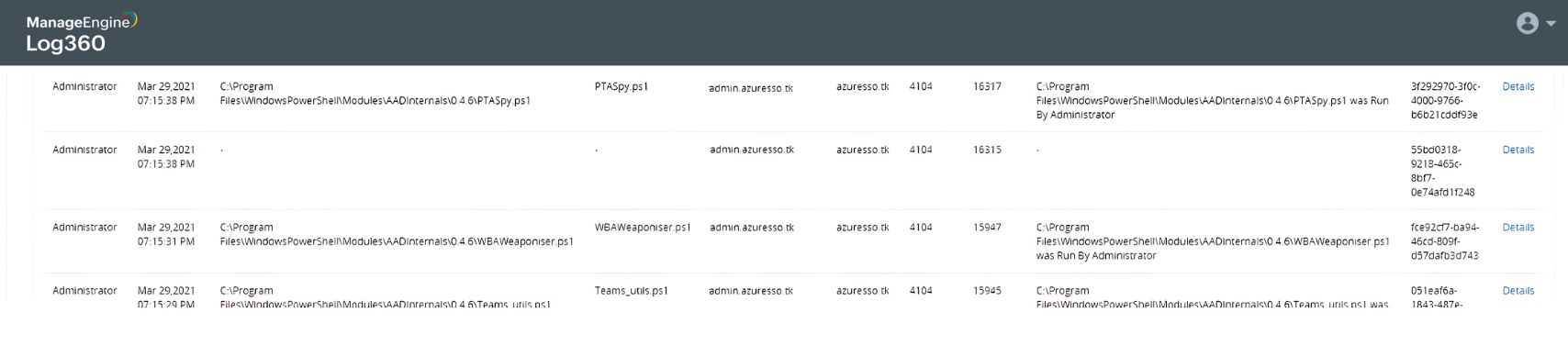
Detect attempts to decrypt the passwords of the MSOL_nnnn account
Detect file creations that record user passwords in PTA interception attack
Detect permission changes on Azure Storage Accounts
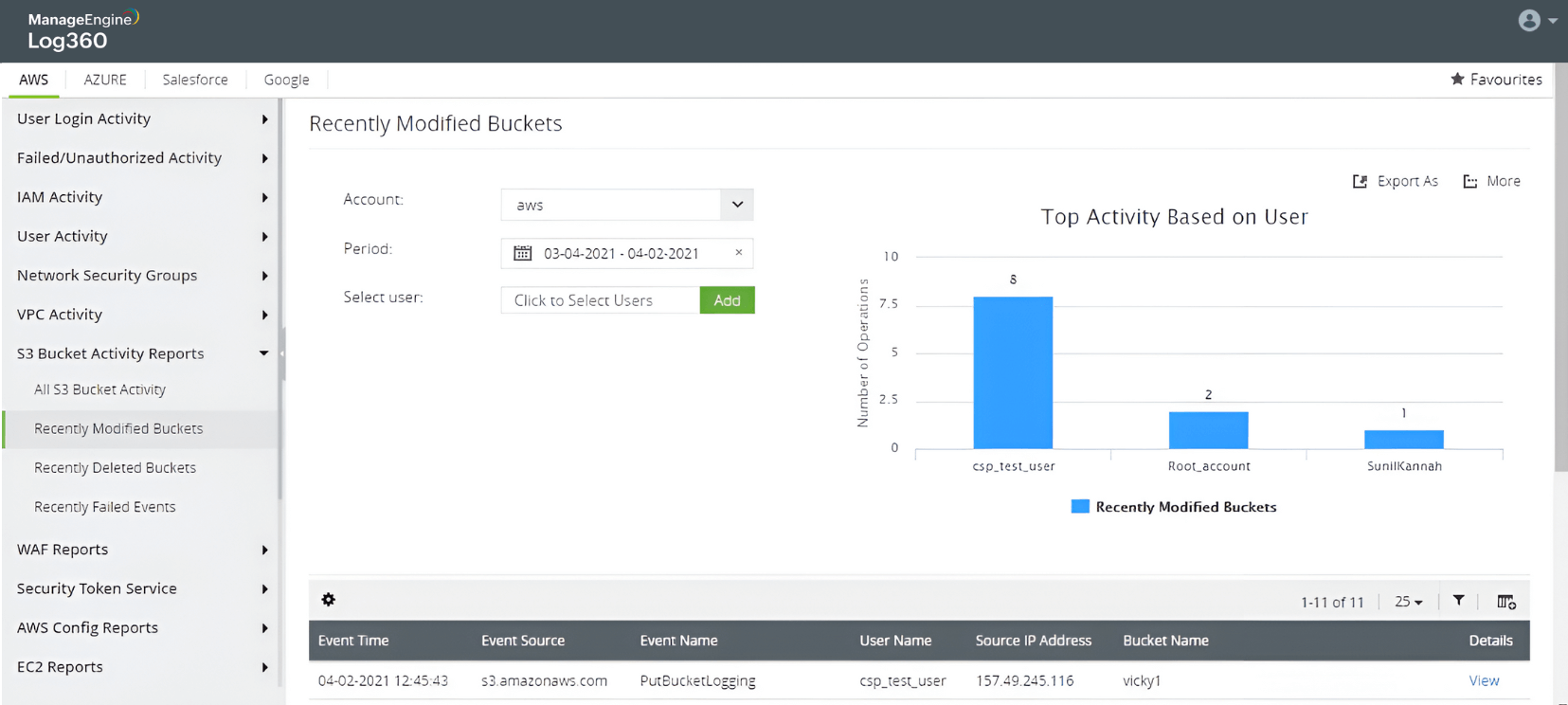
Detect users and hosts accessing the S3 bucket
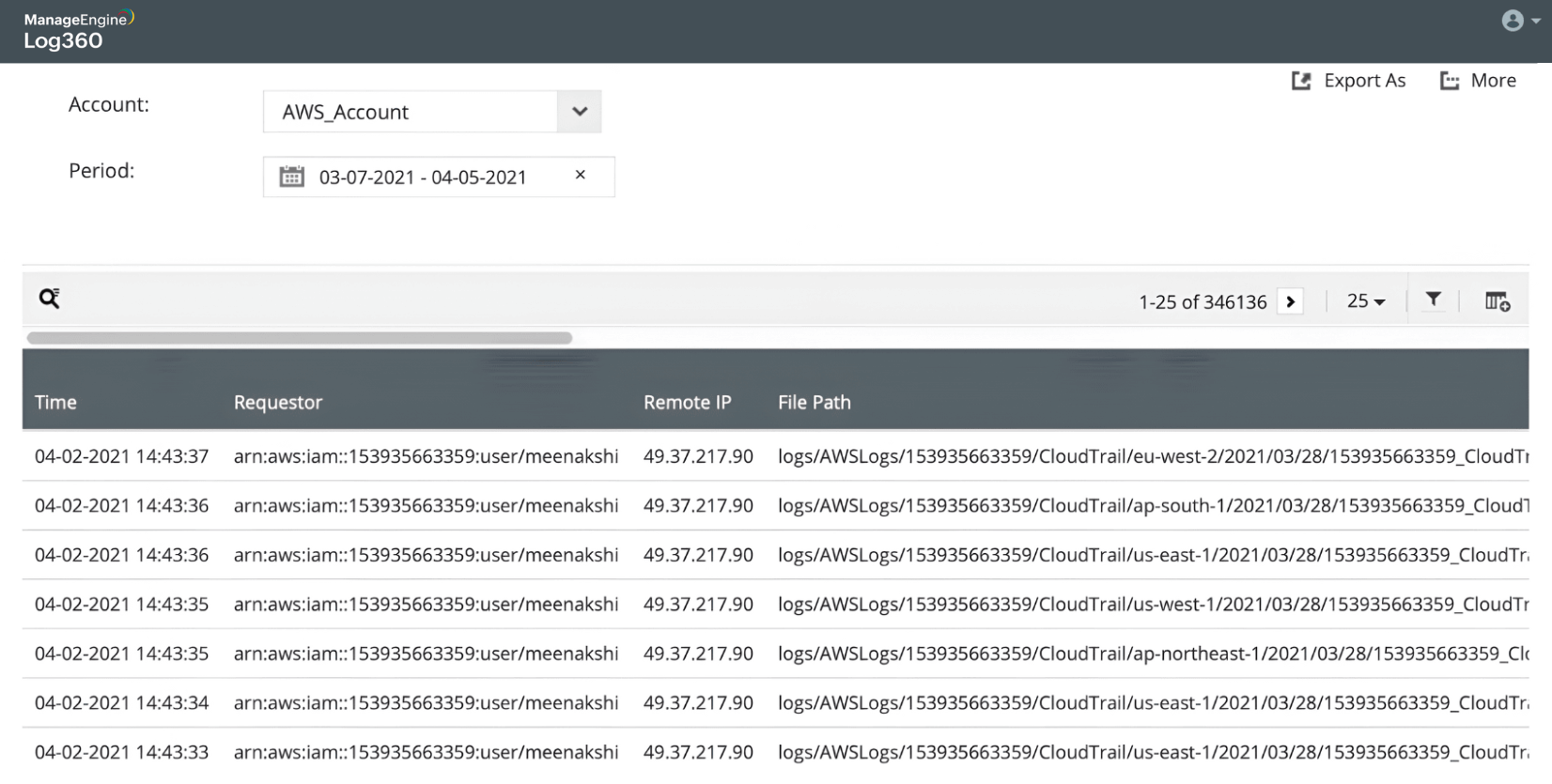
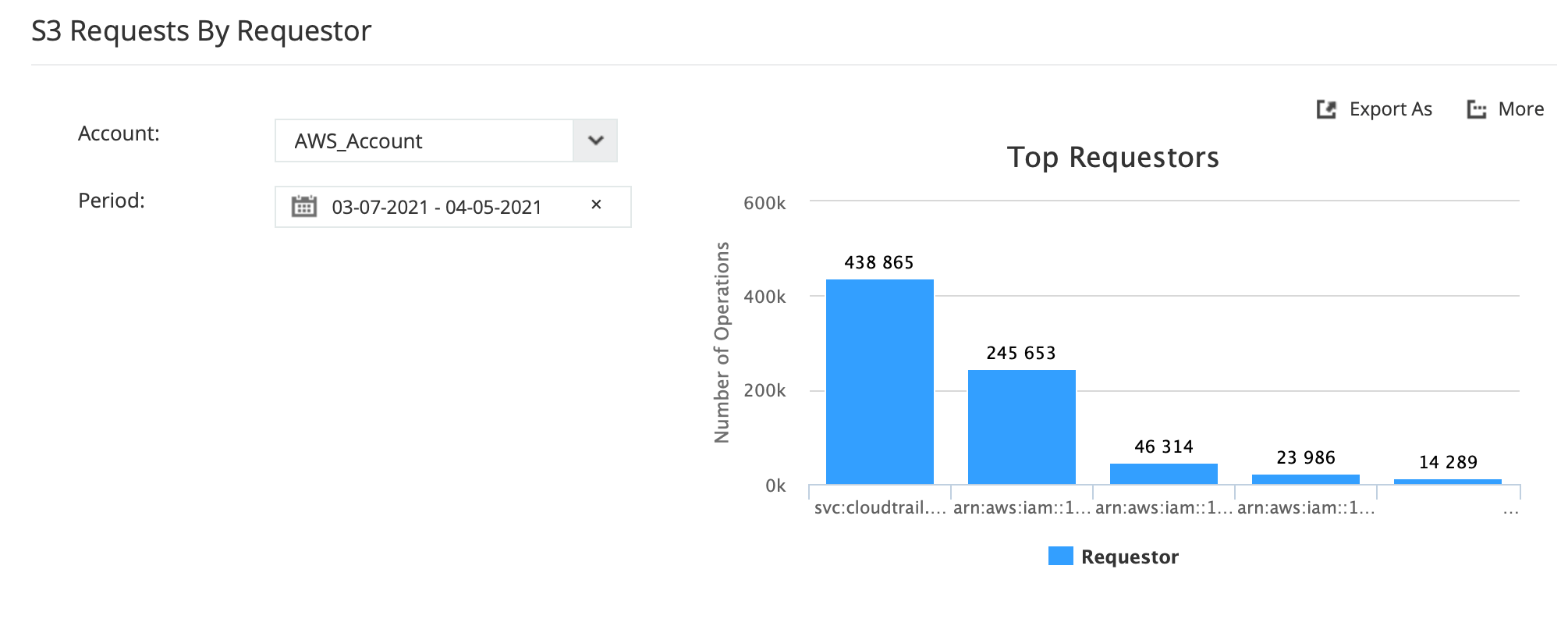
Detect users accessing the buckets
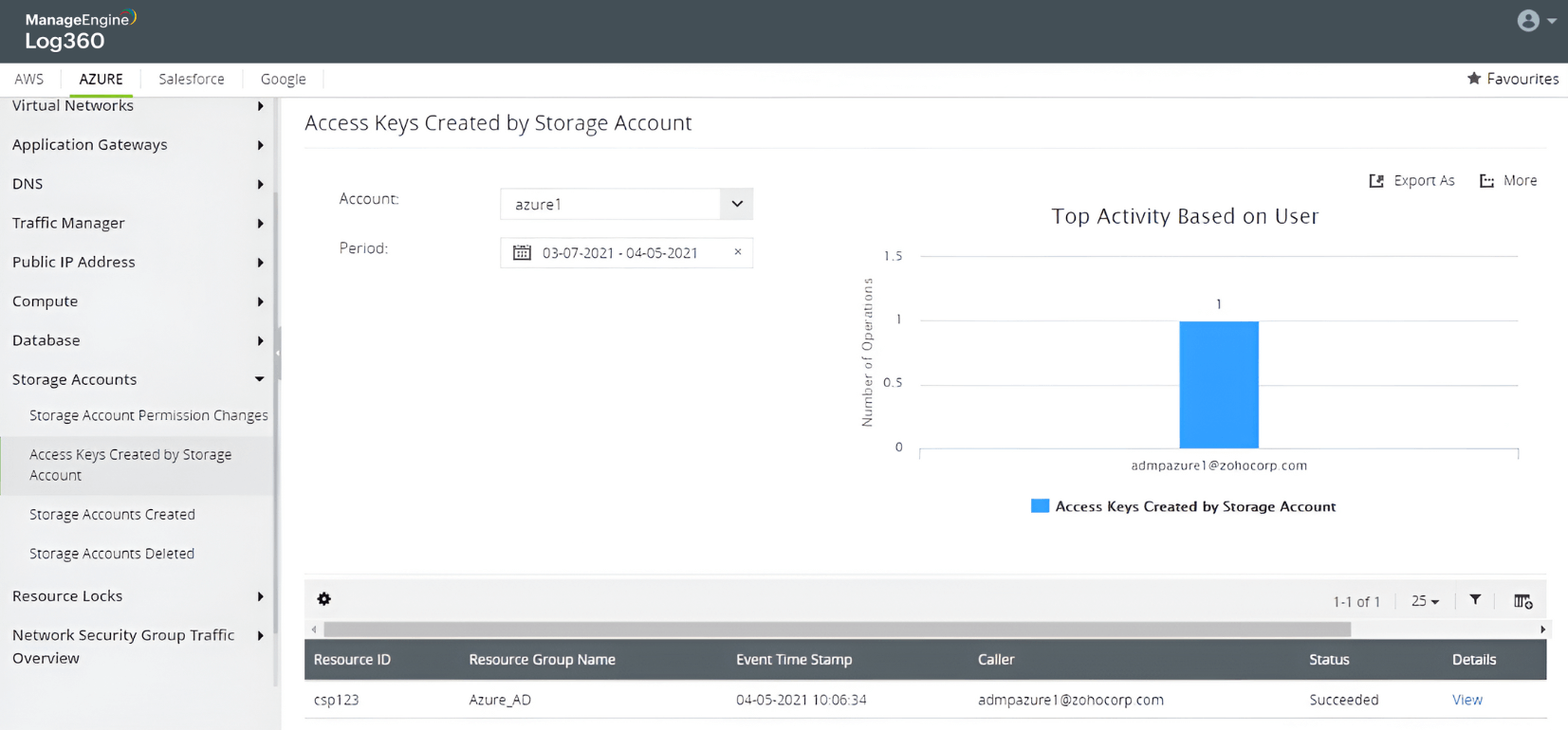
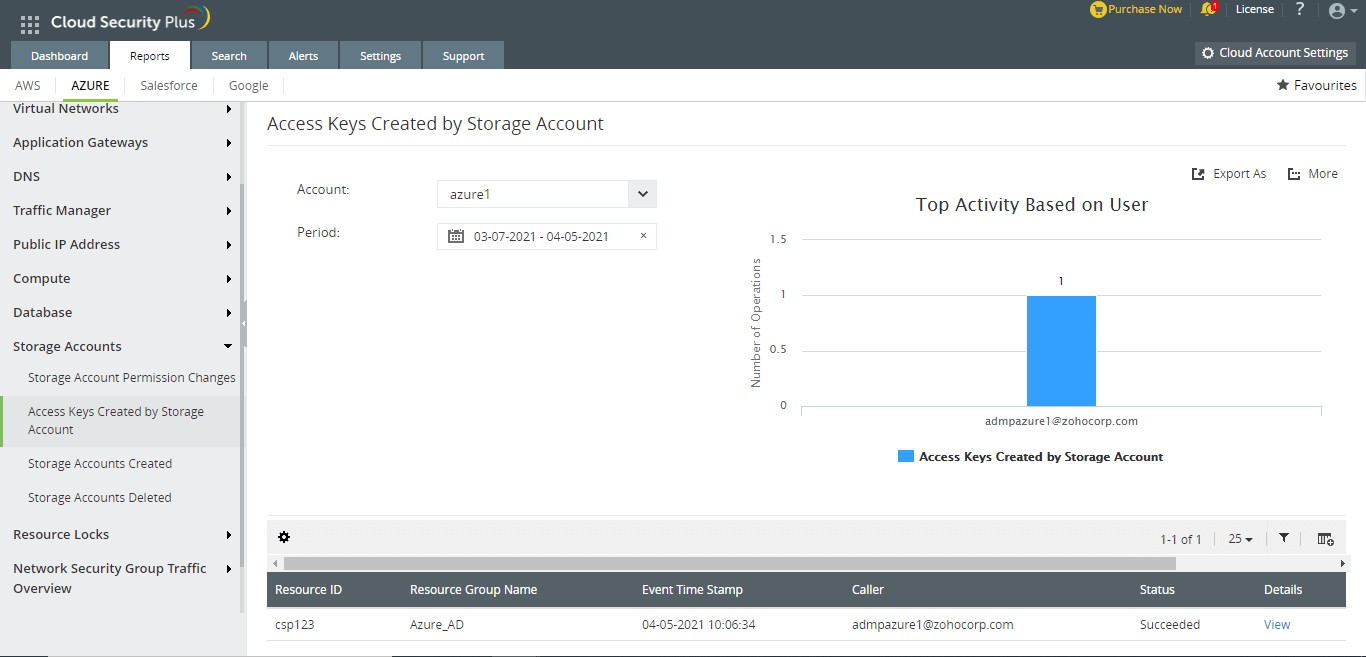
Track access keys created by Storage Accounts in Azure
Detect file modifications in buckets by tracking host IP addresses
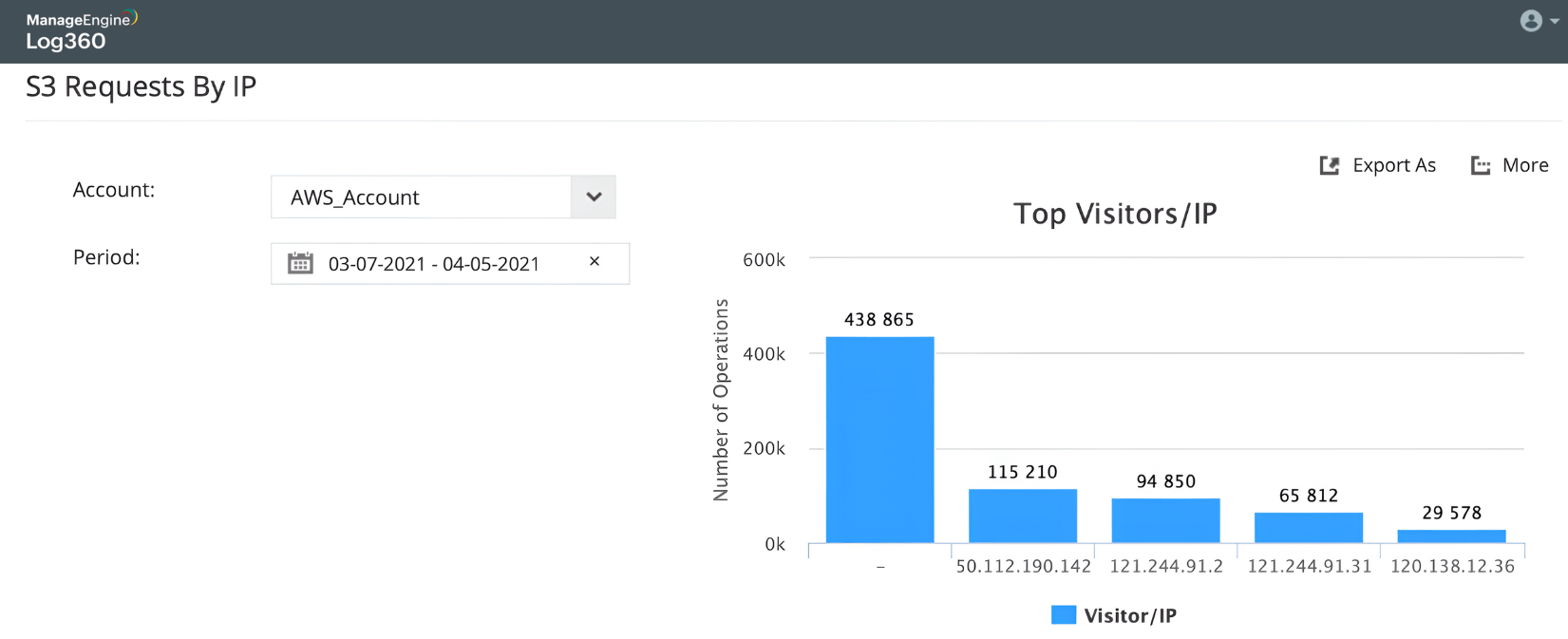
Find recently modified AWS S3 buckets