What's inside?
- Chapter 1
- Chapter 2
- Chapter 3
- Chapter 4
- Chapter 5
What is DDI?

Topics covered:
- Domain Name System (DNS)
- Dynamic Host Configuration Protocol (DHCP)
- IP Address Management (IPAM)
Domain Name System (DNS) - The Resolver
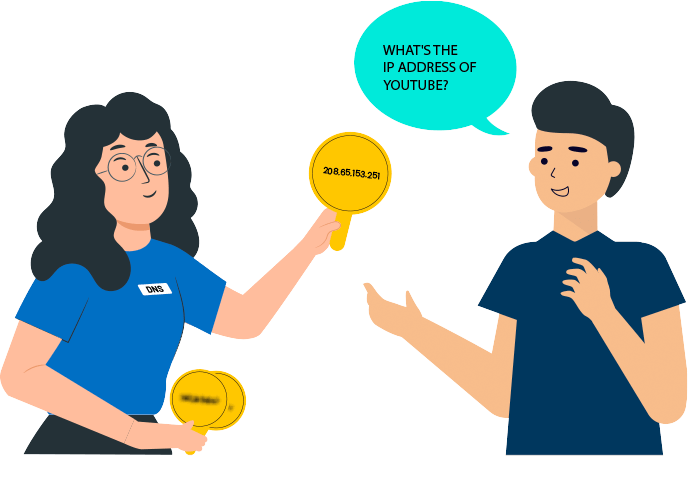
Topics covered:
2.1 What is the DNS?
2.2 How does the DNS work?
2.3 Threats to the DNS
2.3.1 DDoS
2.3.2 DNS cache poisoning
2.3.3 DNS tunneling
Dynamic Host Configuration Protocol (DHCP) - The Assigner
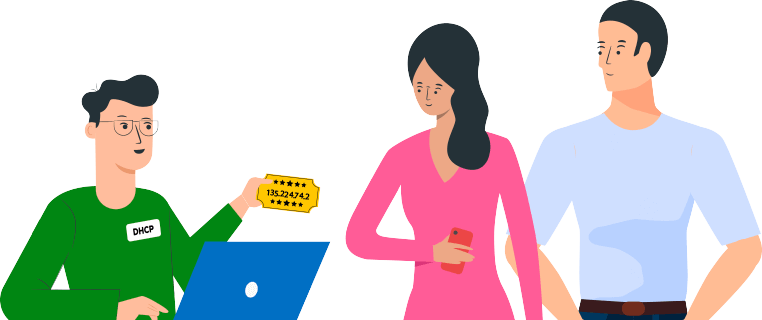
Topics covered:
3.1 What is DHCP?
3.2 How does DHCP work?
3.3 Threats to DHCP
3.3.1 DHCP starvation
3.3.2 DHCP spoofing
IP Address Management (IPAM) - The Administrator
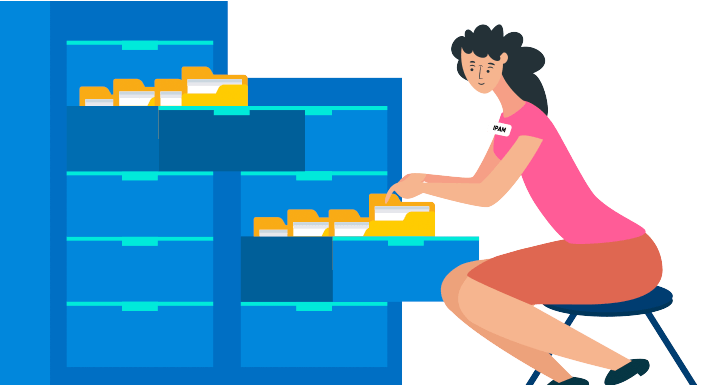
Topics covered:
4.1 What is IPAM?
4.2 Is IPAM essential?
Defending DDI
Topics covered:
5.1 Measures to protect an organization's DNS, DHCP, and IPAM infrastructures
5.2 How can Log360 help?