What is required for compliance?
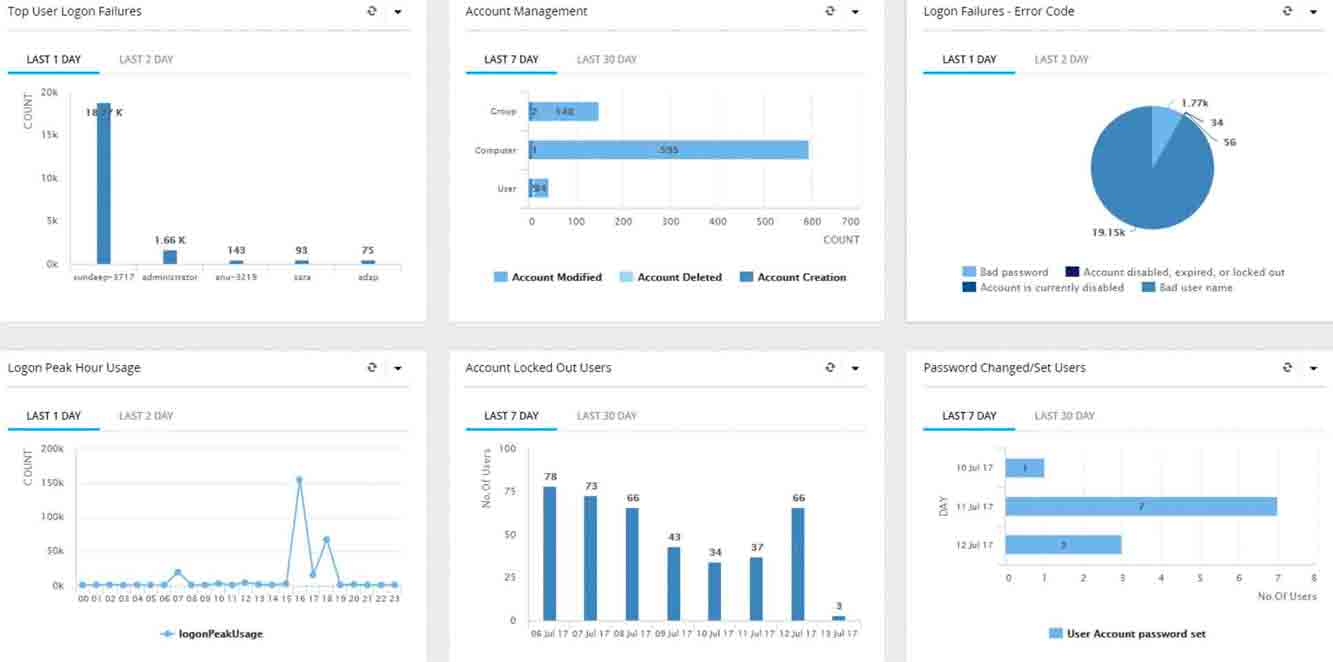
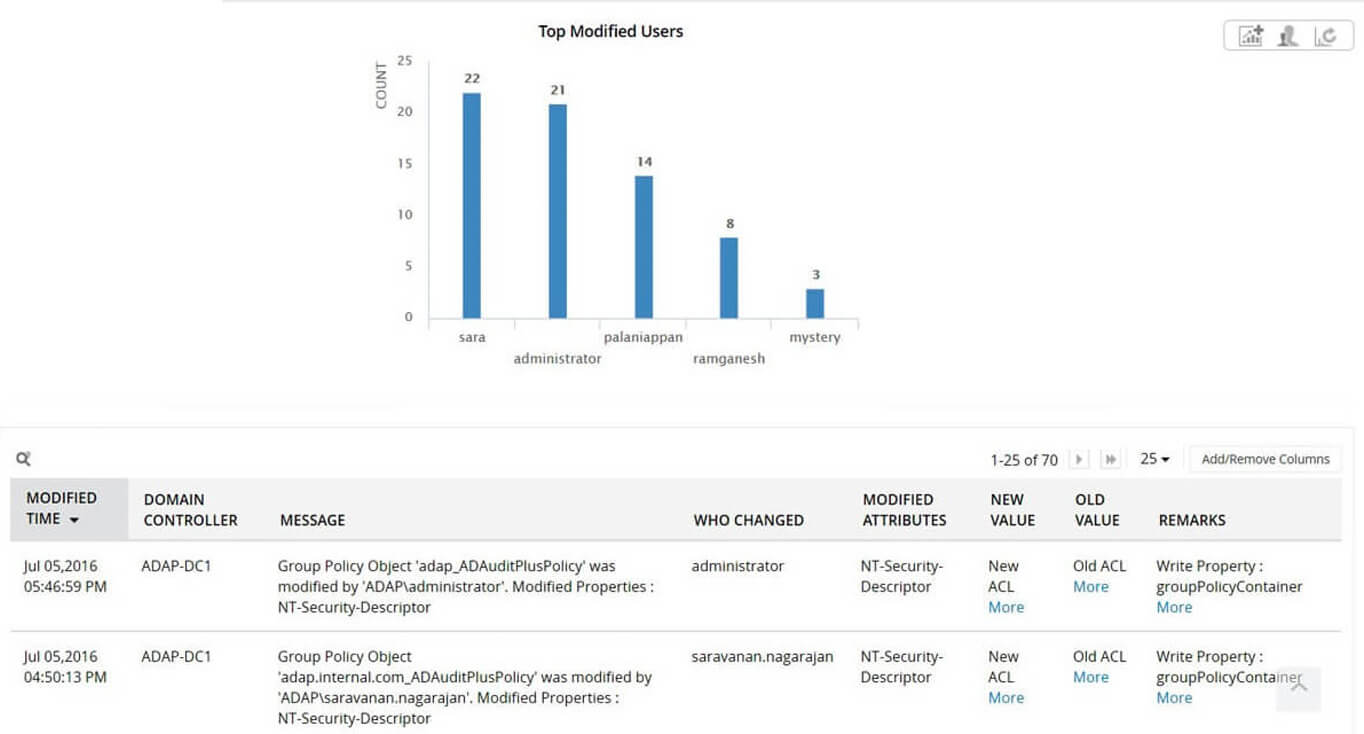
To comply with Articles 27 and 28, a real-time auditing solution that audits users, groups, Group Policy, membership changes, and other changes in Active Directory is required. Businesses also need solutions to analyze logs from multiple sources in real-time. This solution needs to raise alerts to mitigate both identity theft incidents and cyberattacks. ManageEngine Log360 can fulfill all of these requirements.
Why you should use Log360 to comply with the Dominican Republic's regulations.
Log360 is a one-stop solution for all your log management and network security challenges. You'll be able to audit Active Directory changes, network device logs, Microsoft Exchange Servers, Microsoft Exchange Online, Azure Active Directory, and your public cloud infrastructure all from a single console, and gain complete control over your network.