Log360 helps you track file and folder changes and alerts you upon suspicious activities.
Enterprises commonly use file-based systems to organize, store, and process information. Put simply, file integrity monitoring (FIM) is a change monitoring technique that helps you ensure the security of data stored in critical files and folders.
FIM is used to keep track of and validate changes made to files and folders. The files you mainly need to worry about are typically data, system, and log files—in other words, files that are critical for the business. A FIM solution ensures the accuracy of this data by preventing unauthorized changes. Changes include the creation, deletion, access, modification, or renaming of files and folders along with any failed attempts to perform any of these actions.
A FIM solution continuously monitors files and folders for unexpected or unauthorized changes, and it instantly collects important contextual information, including who made the change, when, and from where.
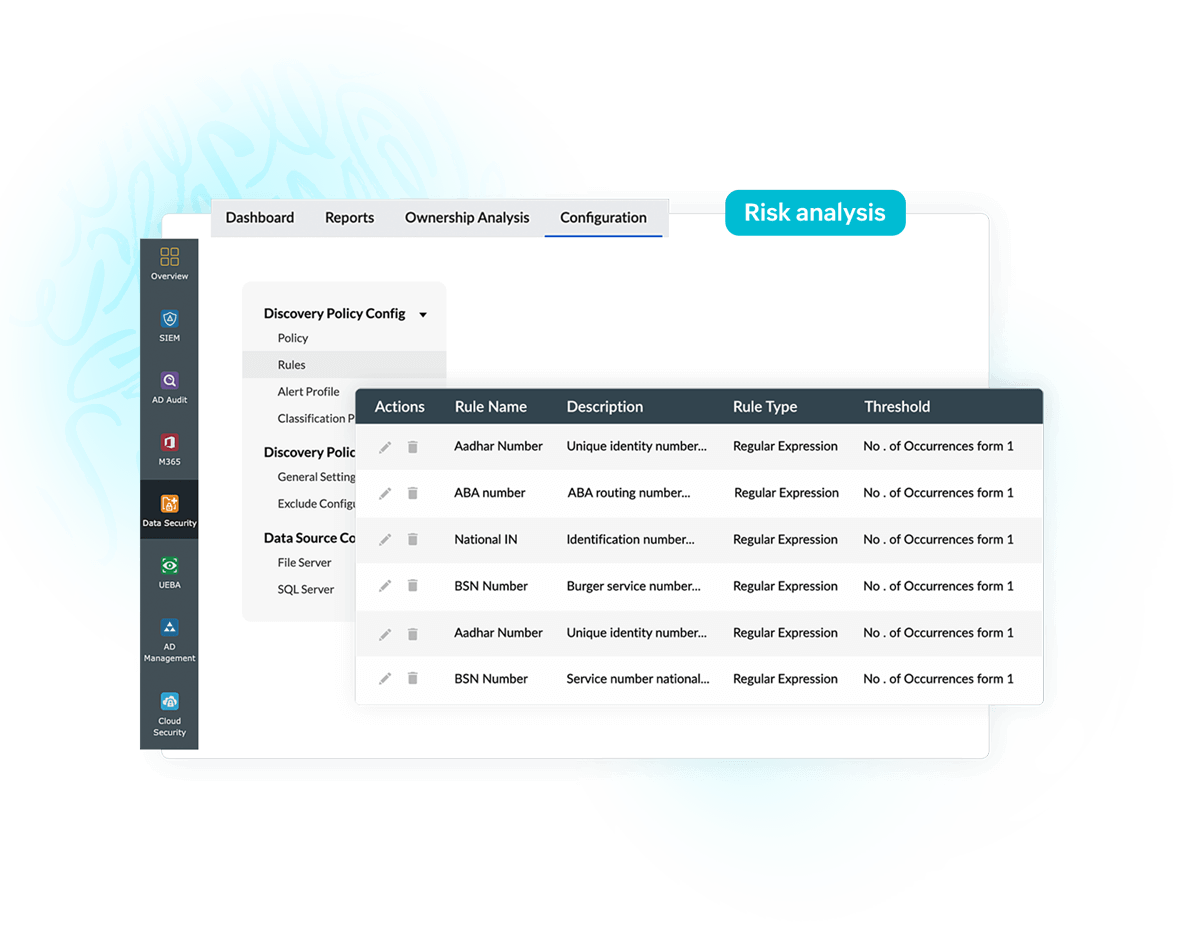
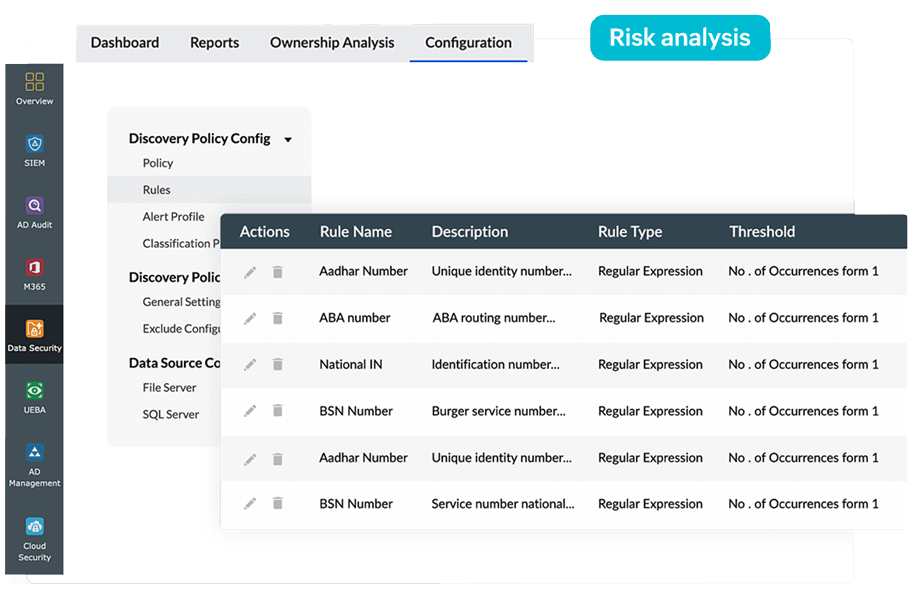
Log360, the unified SIEM solution from ManageEngine that comes integrated with DLP and CASB capabilities, offers a powerful FIM module that helps organizations meet their security and compliance objectives. It thoroughly audits file and folder activities to provide actionable insights.
Log360 employs both agent-based and agentless mechanisms for FIM, giving security teams the flexibility to choose their implementation as per their requirements. Log360 generates reports to track every access, creation, deletion, modification, and permission change made to files and folders and triggers alerts via SMS or email about unauthorized actions.
Log360's FIM module is augmented by its built-in user behavior analytics (UBA) module that can raise alarms for anomalies based on count, time, and pattern of events. UBA helps security teams spot anomalies in user behavior to detect threats that might have been missed otherwise.
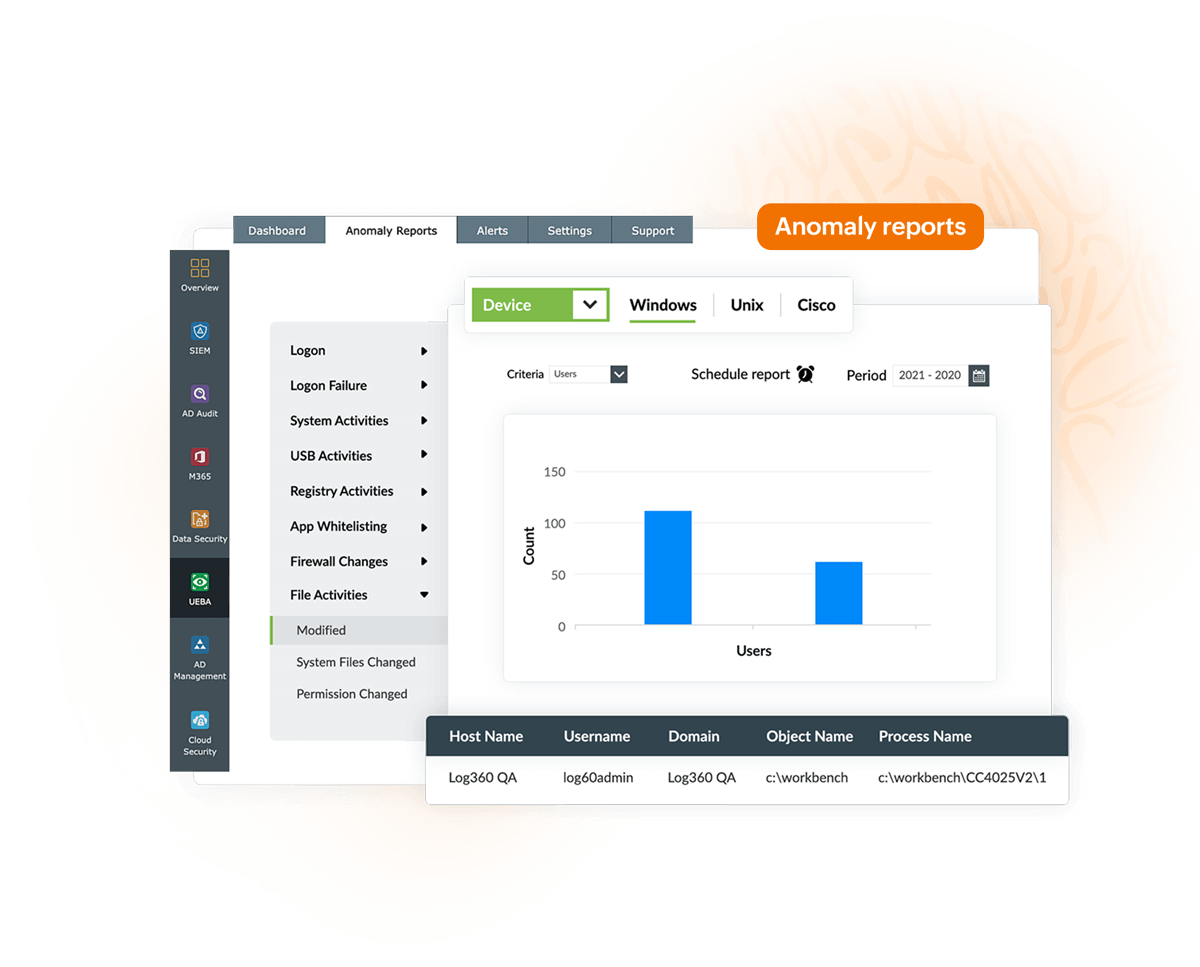
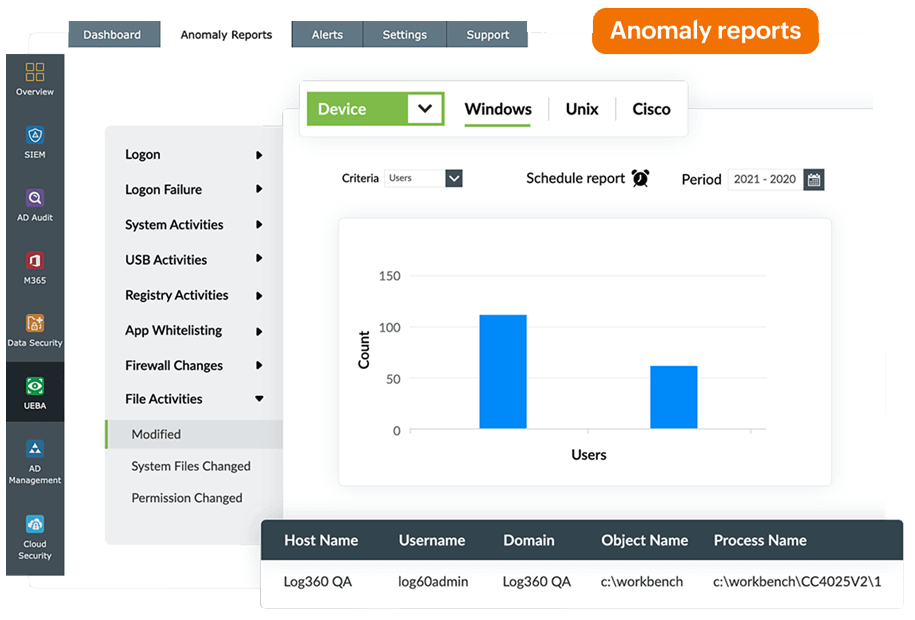
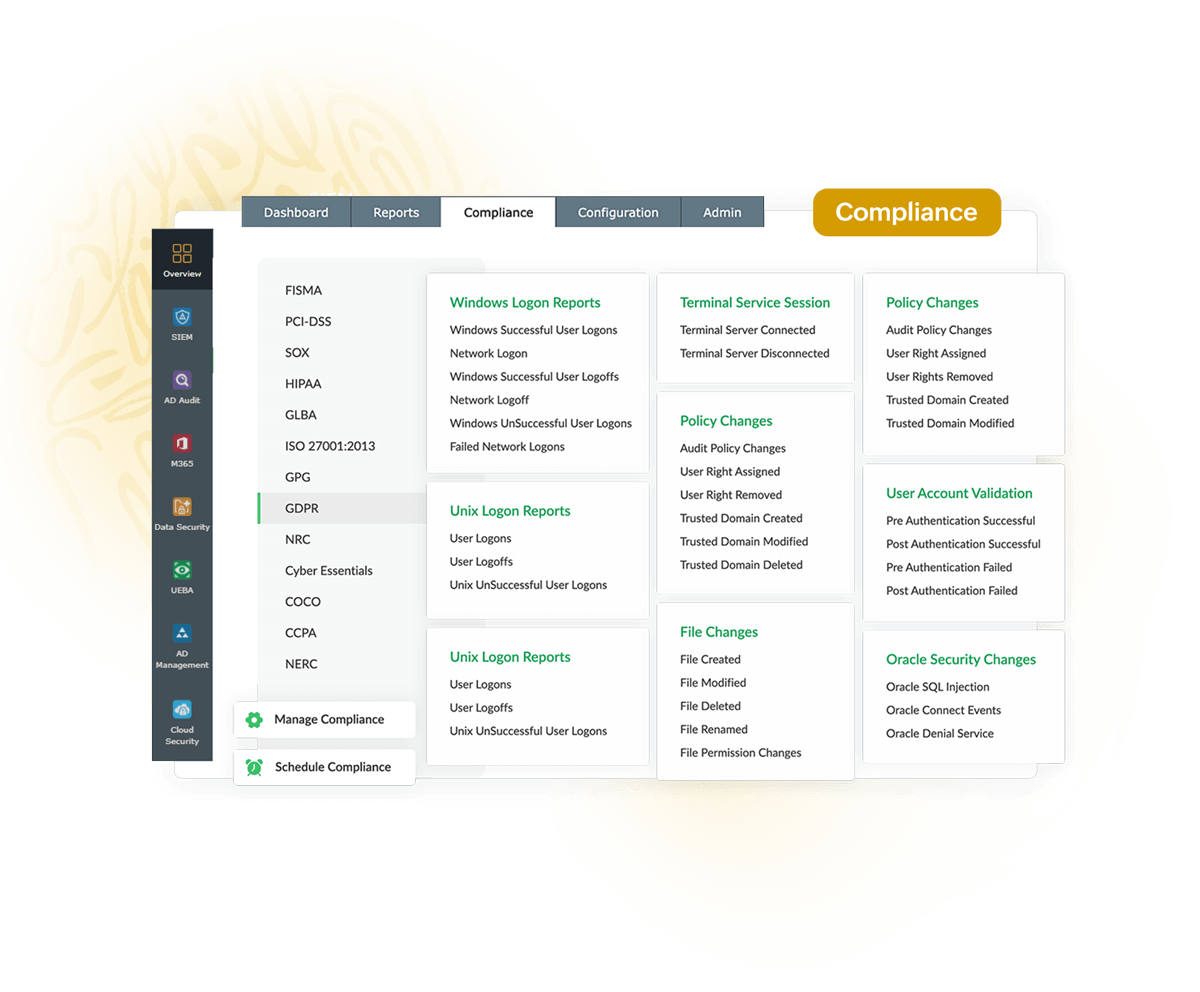
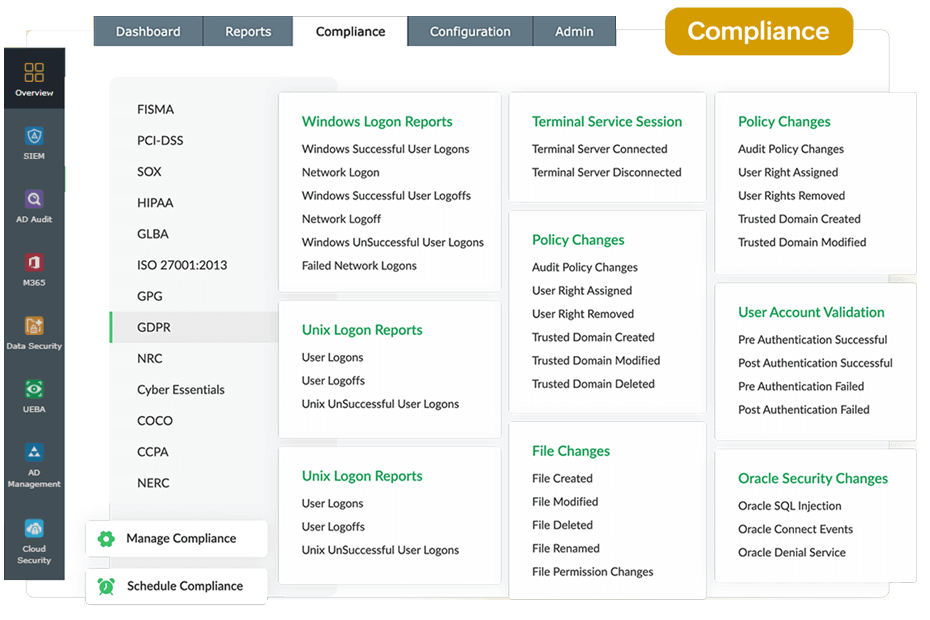
Generate predefined compliance reports for various policies, including PCI DSS, FISMA, HIPAA, and the GDPR while getting details about various file operations as mandated.
Setting up FIM using Log360 requires minimal user effort. You can configure multiple devices simultaneously, and the required FIM agents will be automatically installed on these devices. All necessary audit policies, agent updates, and SACL settings are automatically updated.
You can exercise control over the files and folders you wish to monitor using templates and filters. Create templates to group the file and folder locations you want to monitor and apply them to as many devices as needed. By modifying these templates once, you can apply the change to all devices. Using filters, you can choose to include or exclude subfolders, specific files, or file types.
The FIM dashboard gives you an overview of all changes made to files and folders you're monitoring. Reports and alerts are also available for each independent device being monitored.
Log360 supports a wide range of log sources, including domain controllers, databases, web servers, and firewalls. It comes with over 1,000 prebuilt audit reports that can be associated with alerts.
Log360 helps meet compliance standards such as the GDPR, HIPAA, and PCI DSS by providing prebuilt reports on modifications or changes made to the database.