IT security under attack
Identify, mitigate, and prevent security risks.
- Attack Demos
- Security Sessions
- SOC insights
- Network security
- Application security
- Cloud security
- Endpoint security
- Information & Data security
- IAM security
- Defend with MITRE ATT&CK
-
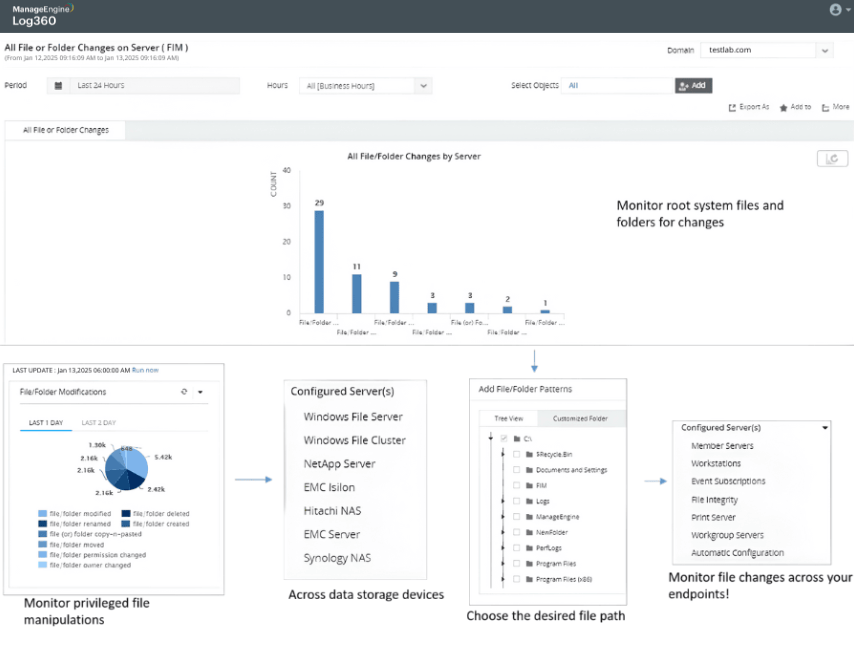
Secretly copying files from a remote location
Learn more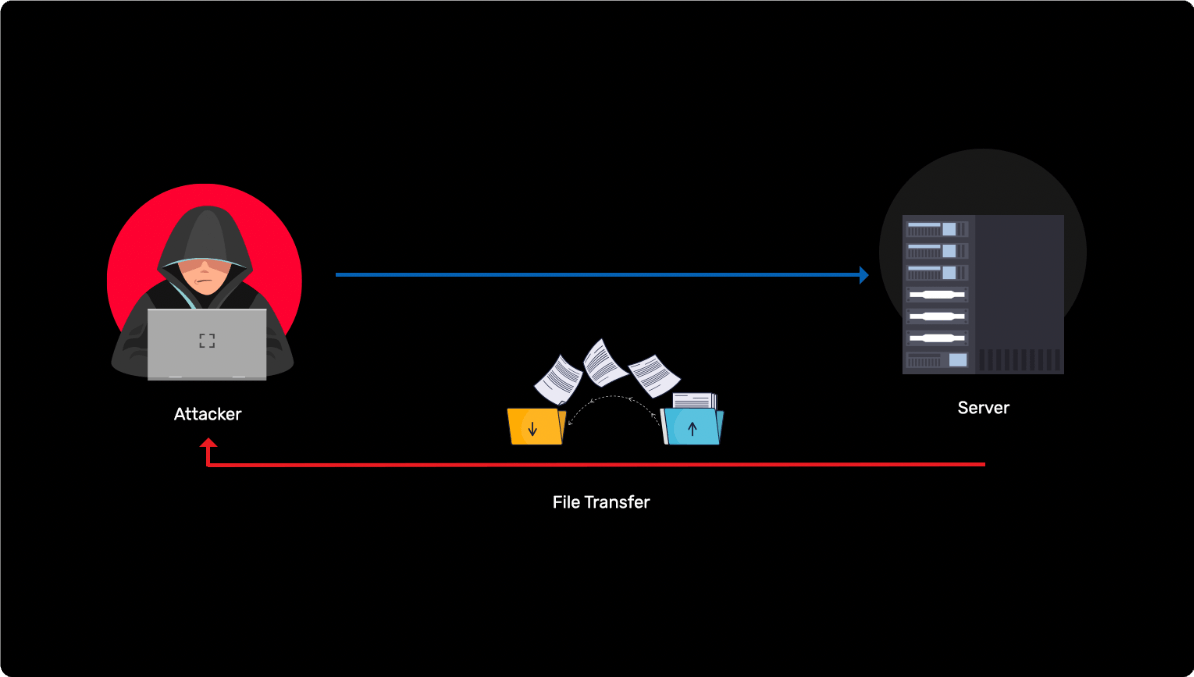
-
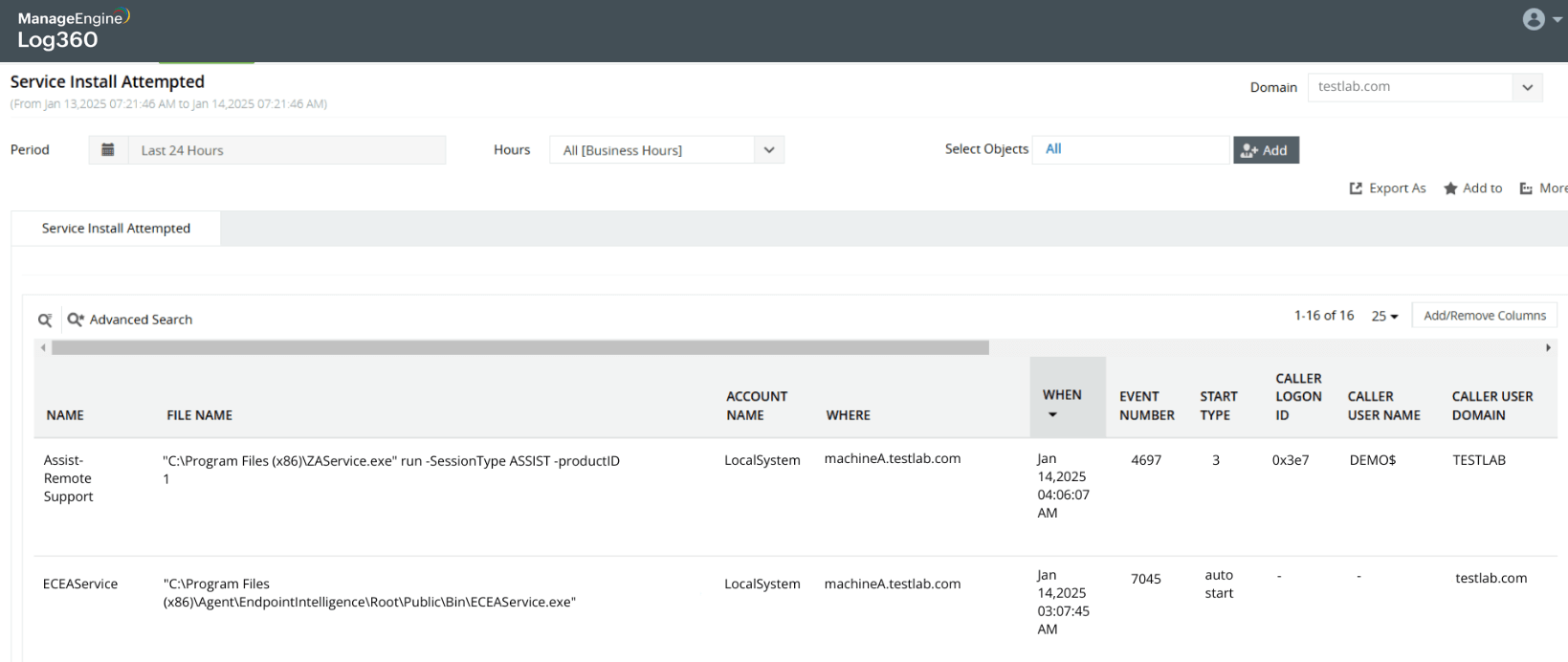
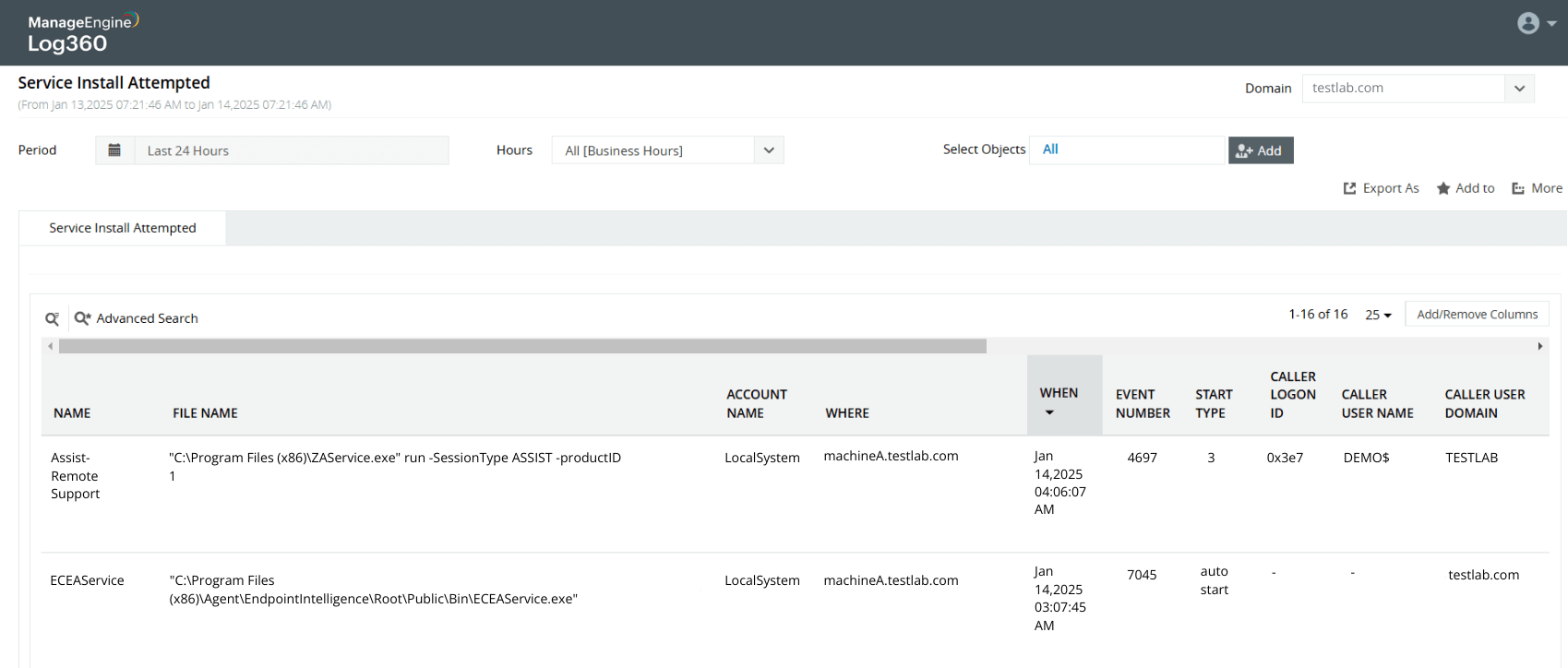
Installing a malicious backdoor service
Learn more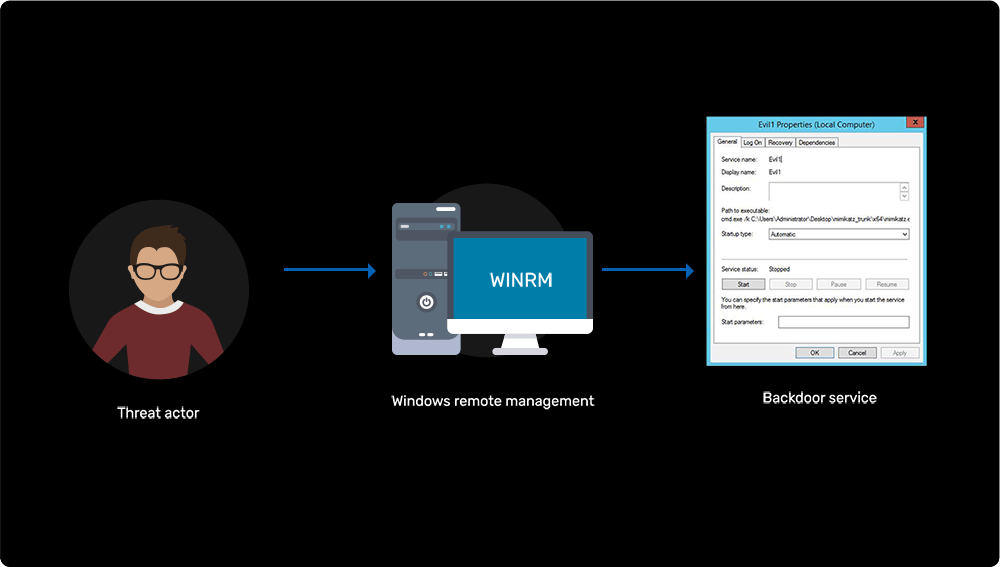
-
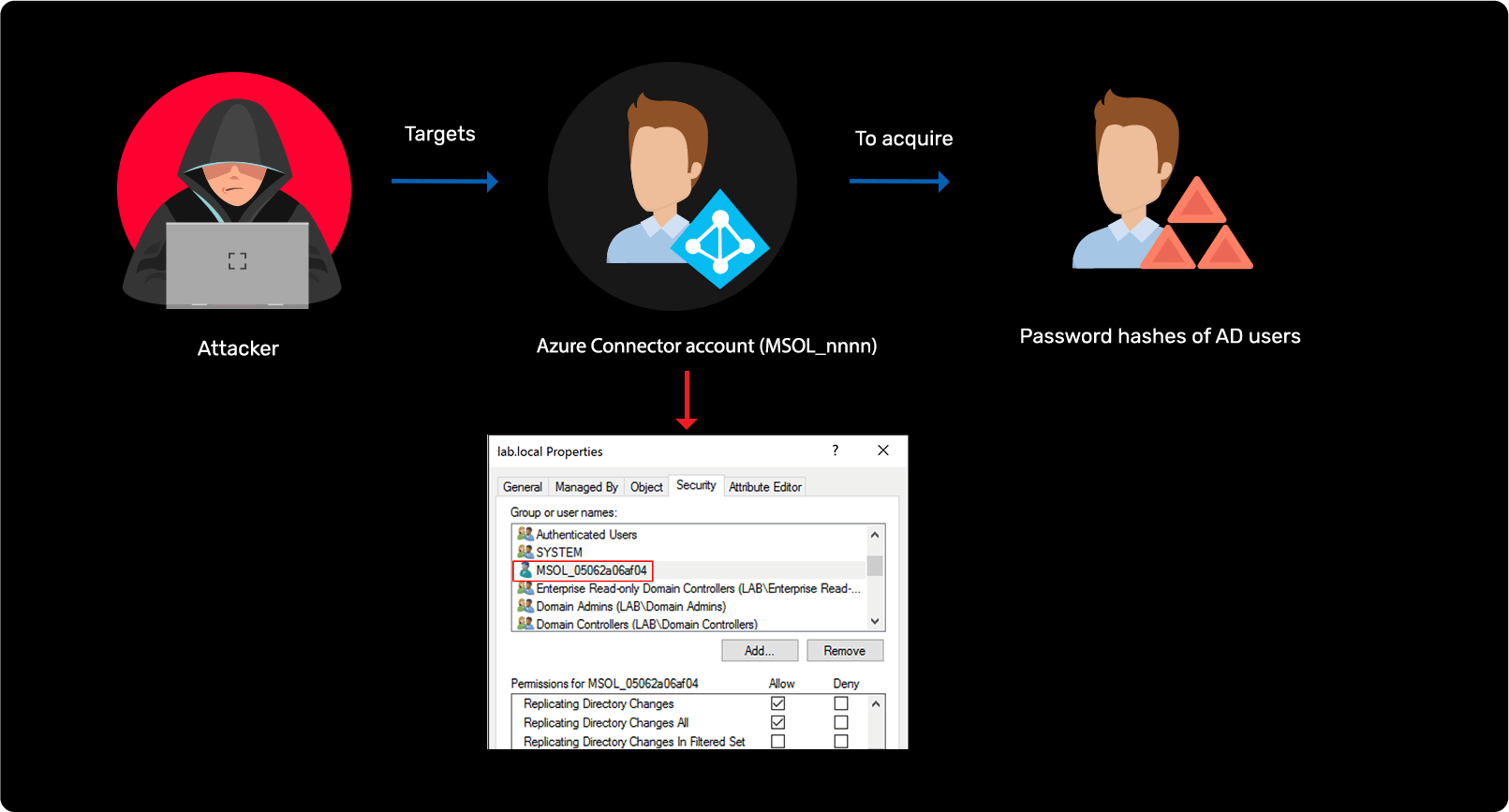
Hybrid AD reconnaissance
Learn more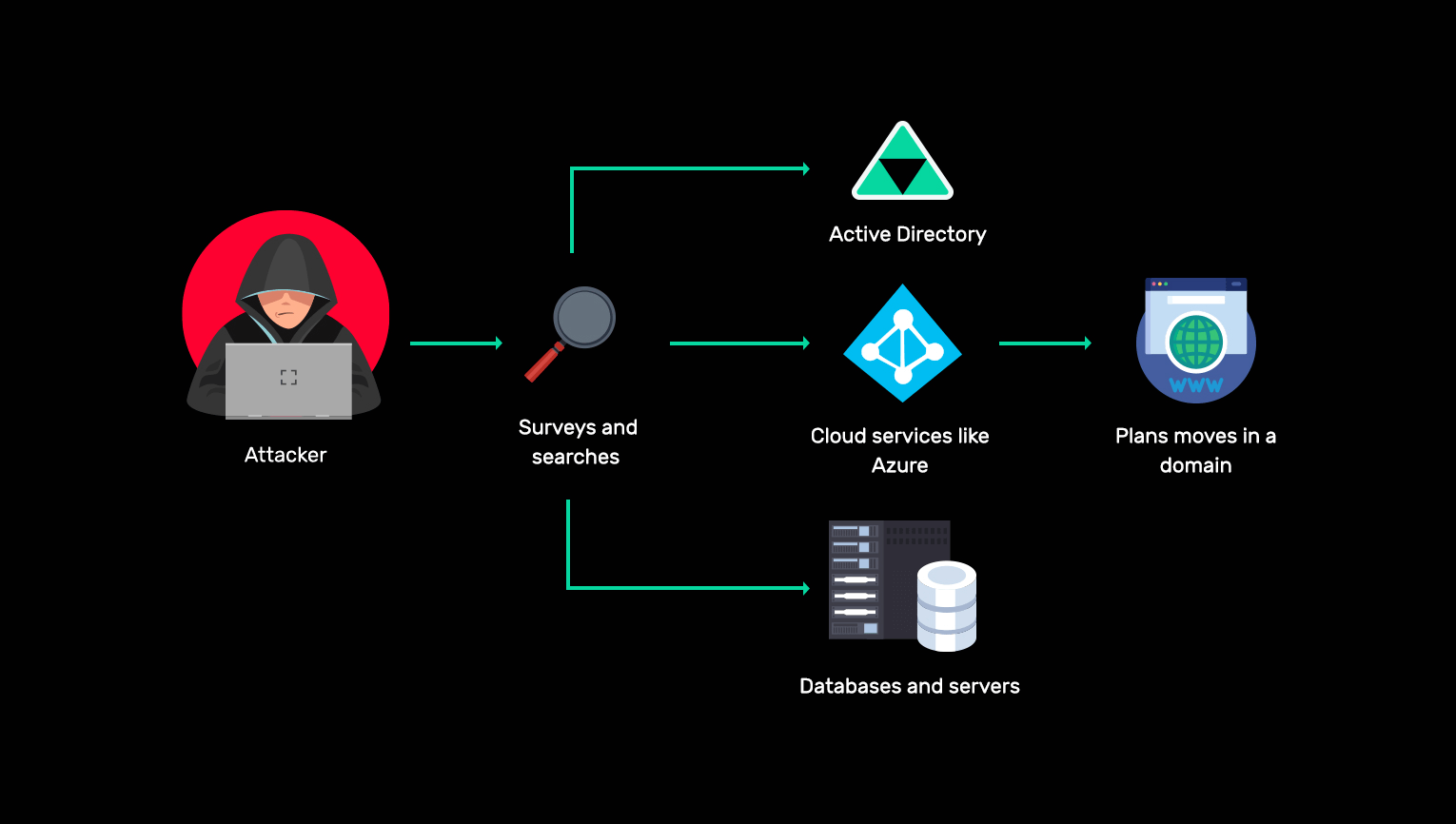
-
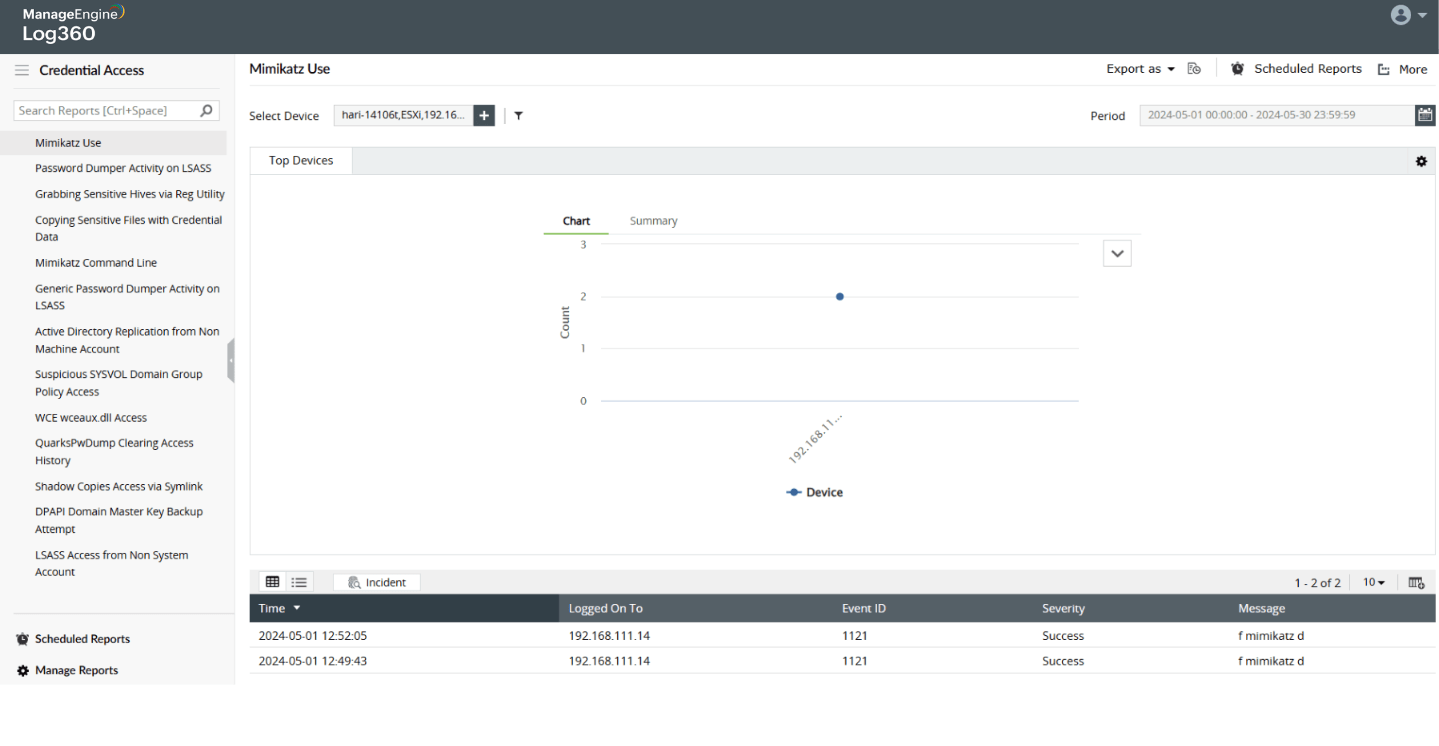
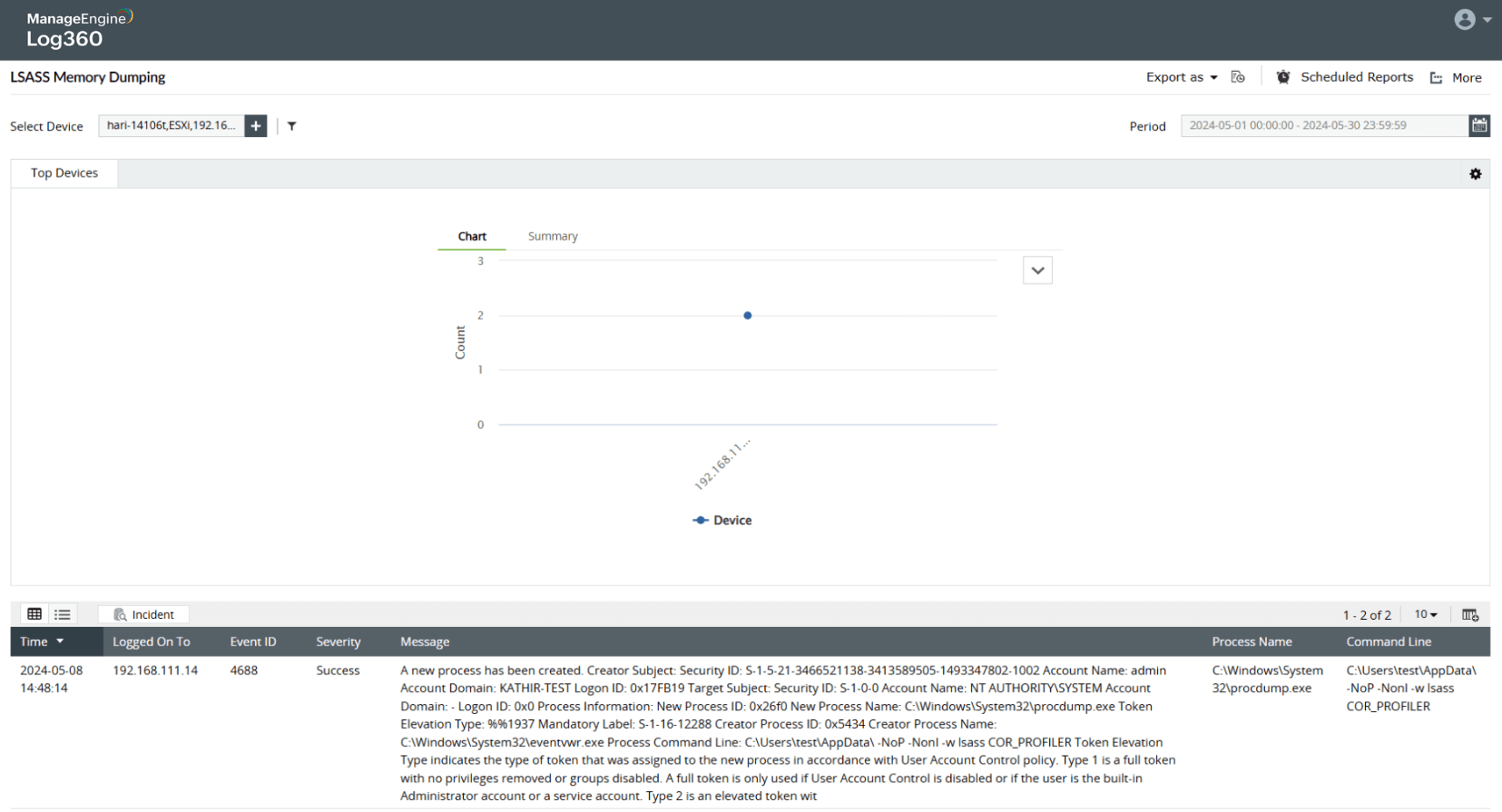
Dumping credentials from local memory of servers (LSA)
Learn more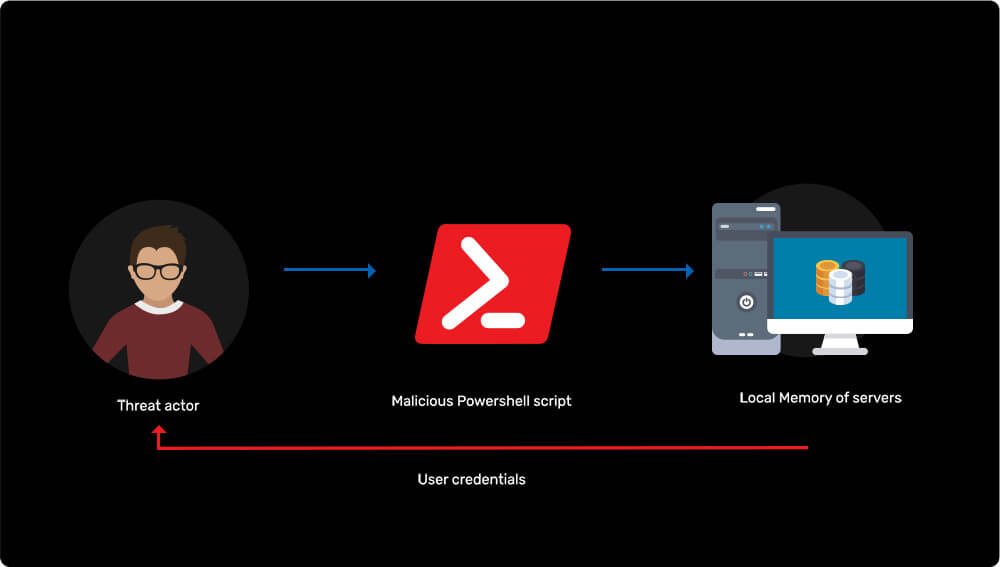
-
Simulating domain controller behavior to get Active Directory user passwords
Learn more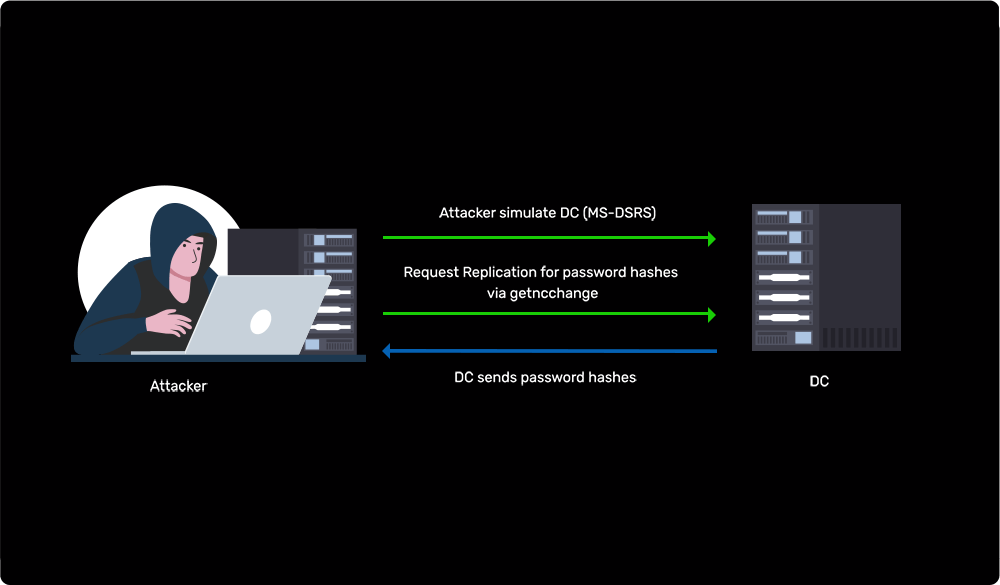
-
Registering a rogue domain controller to inject backdoor changes into Active Directory
Learn more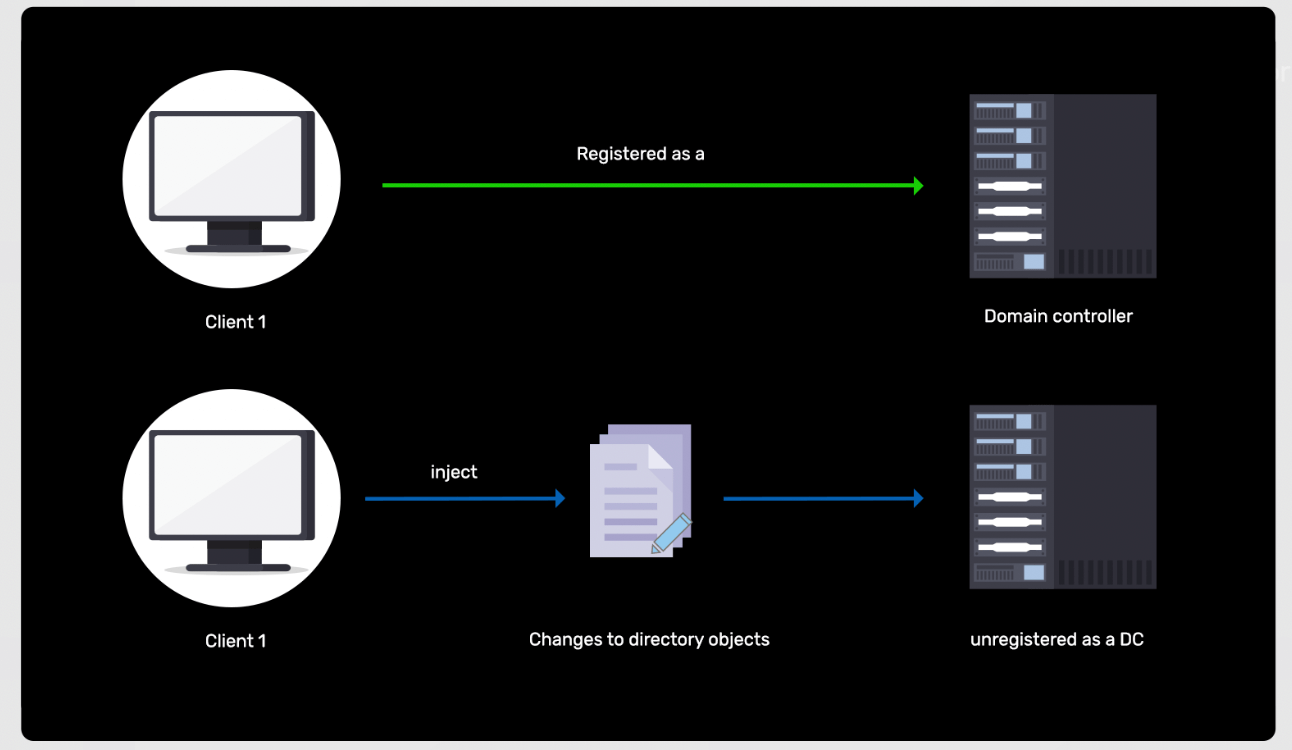
-
Malicious Microsoft Office macro creation
Learn more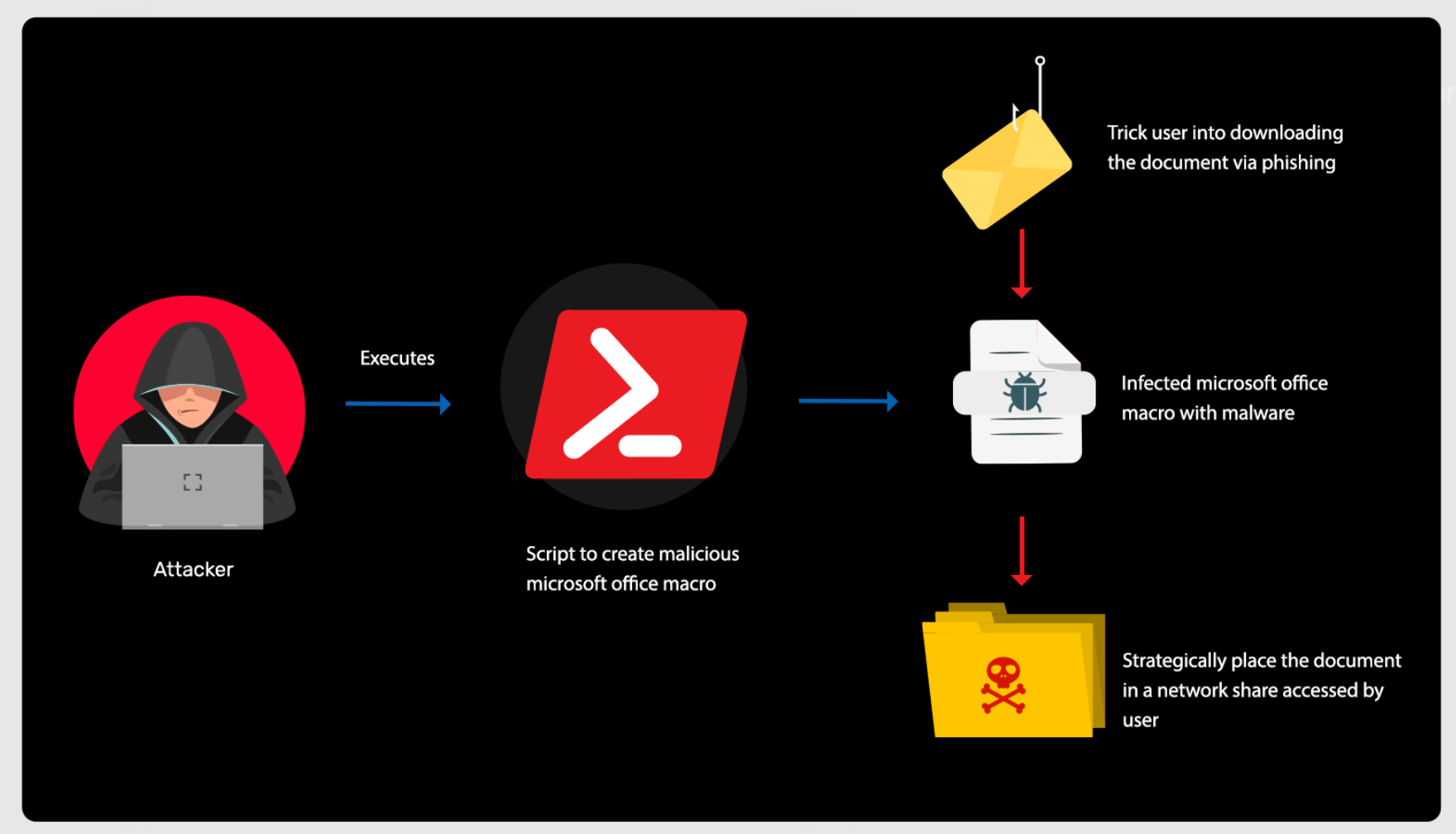
-
SEO poisoning attack flow
Learn more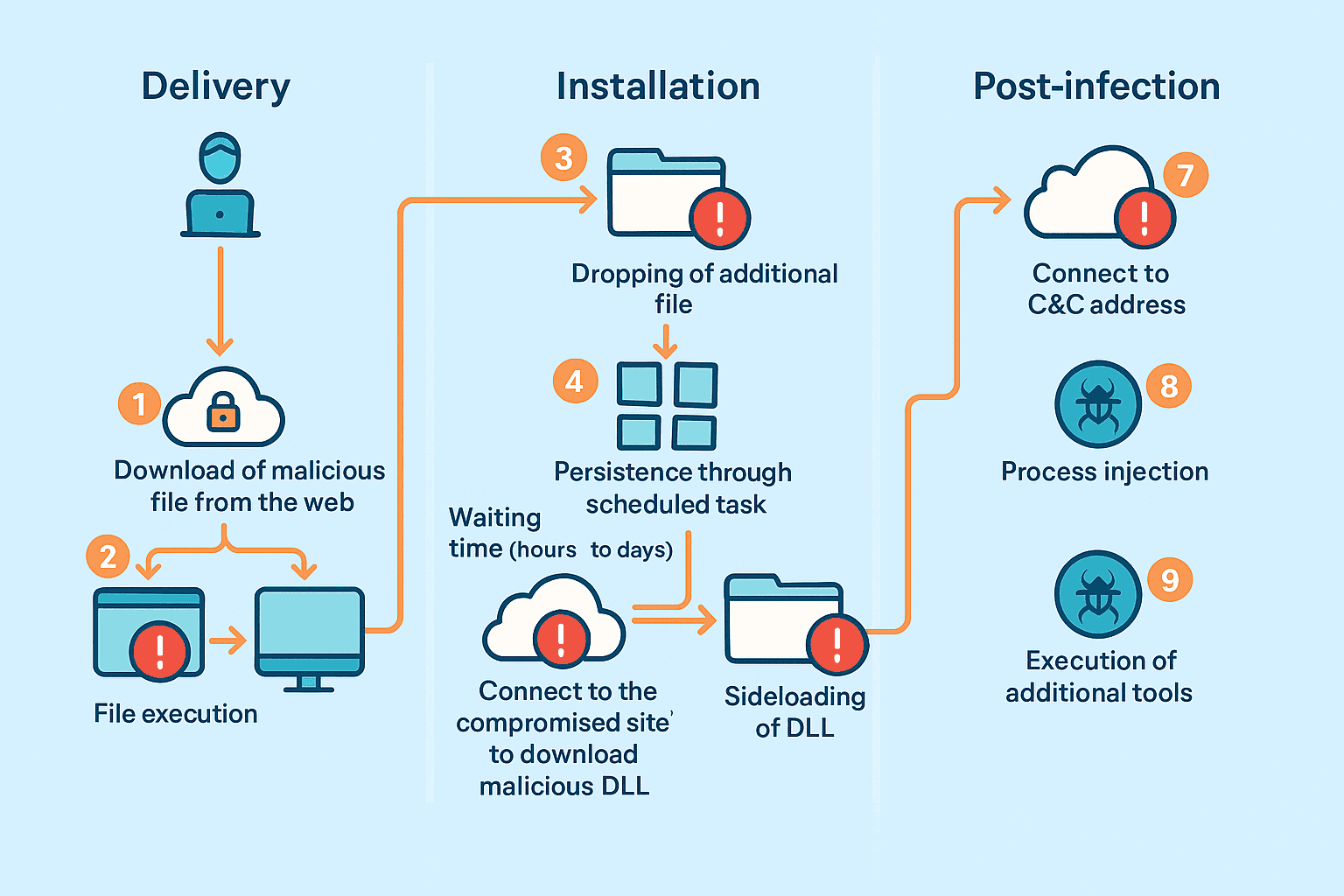
-
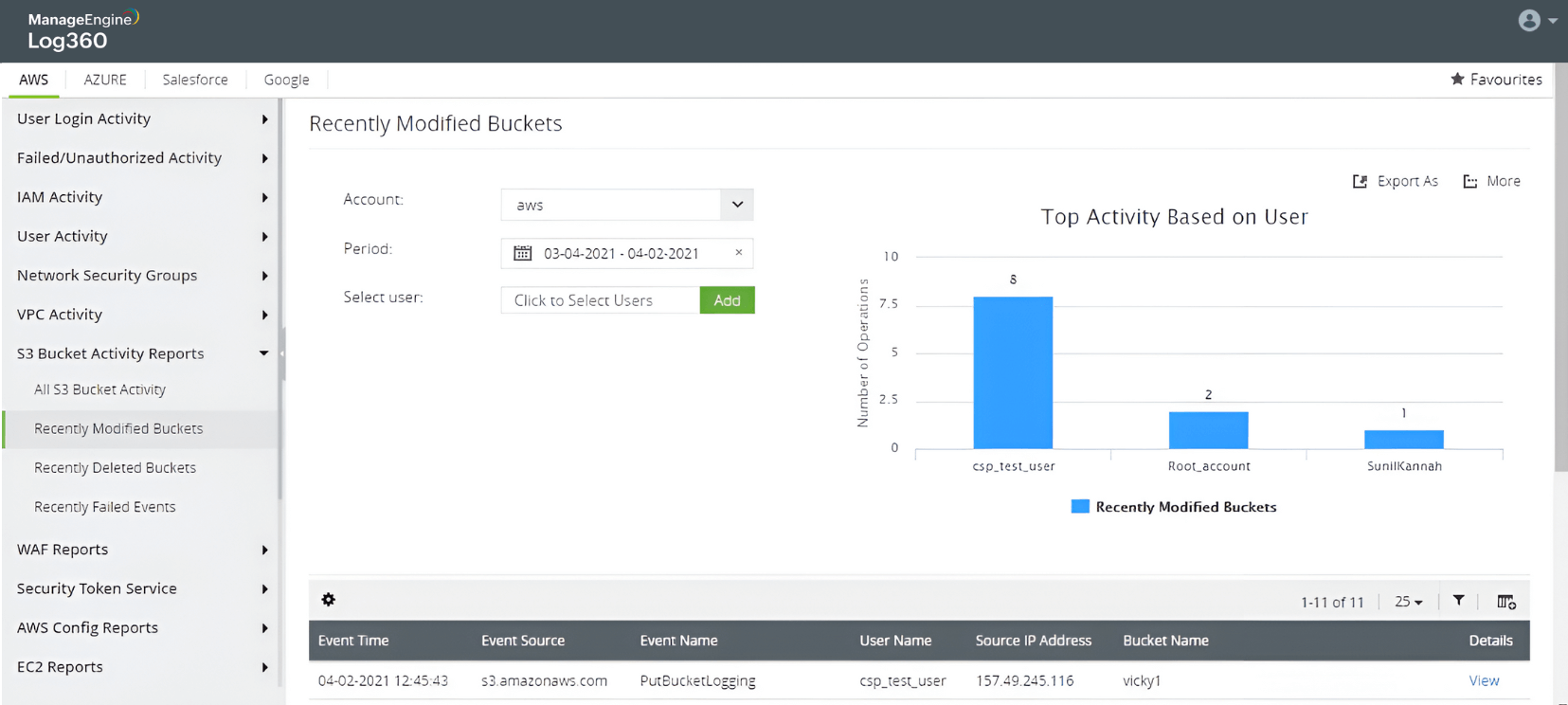
AWS ransomware attack
Learn more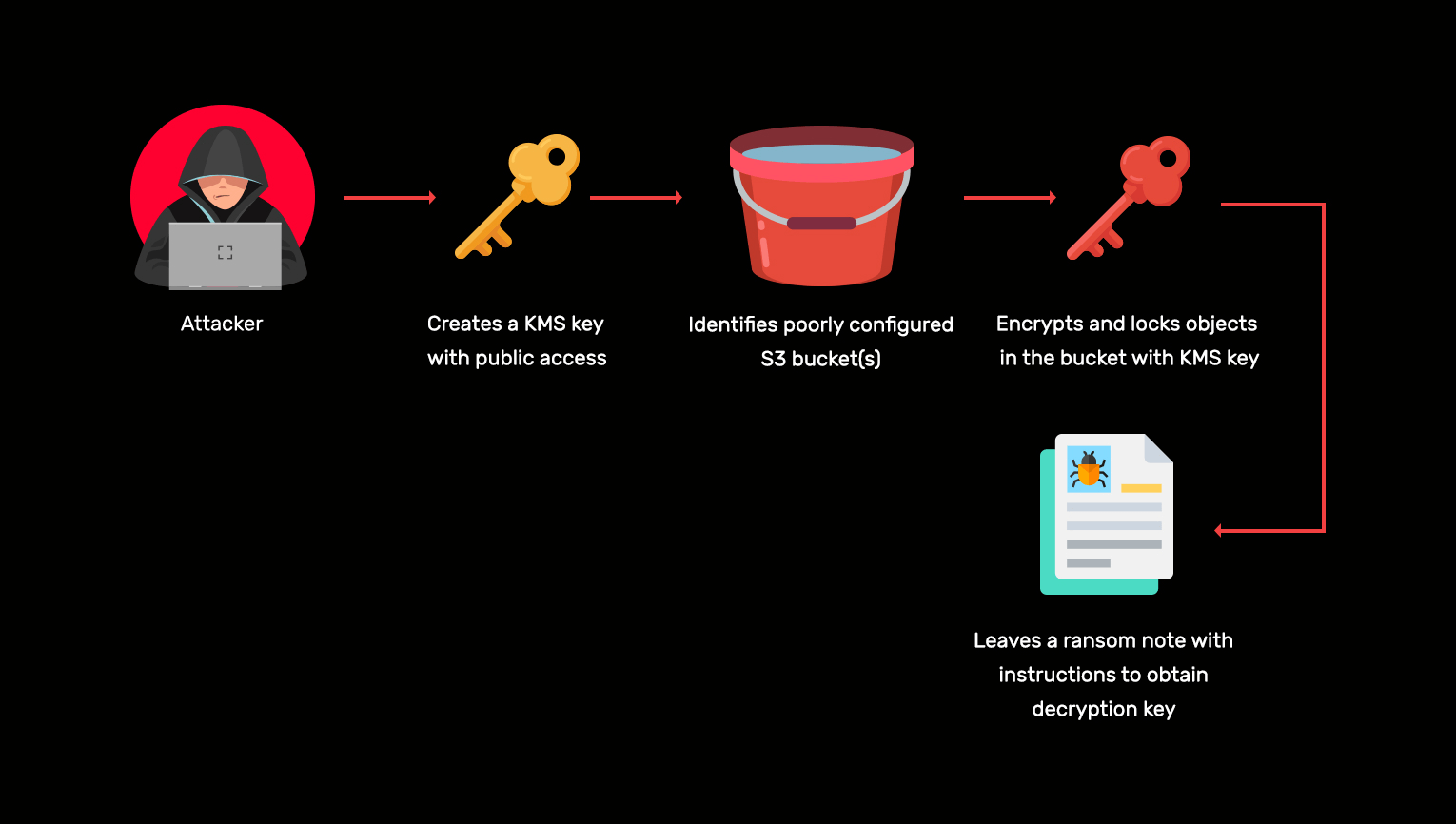
-
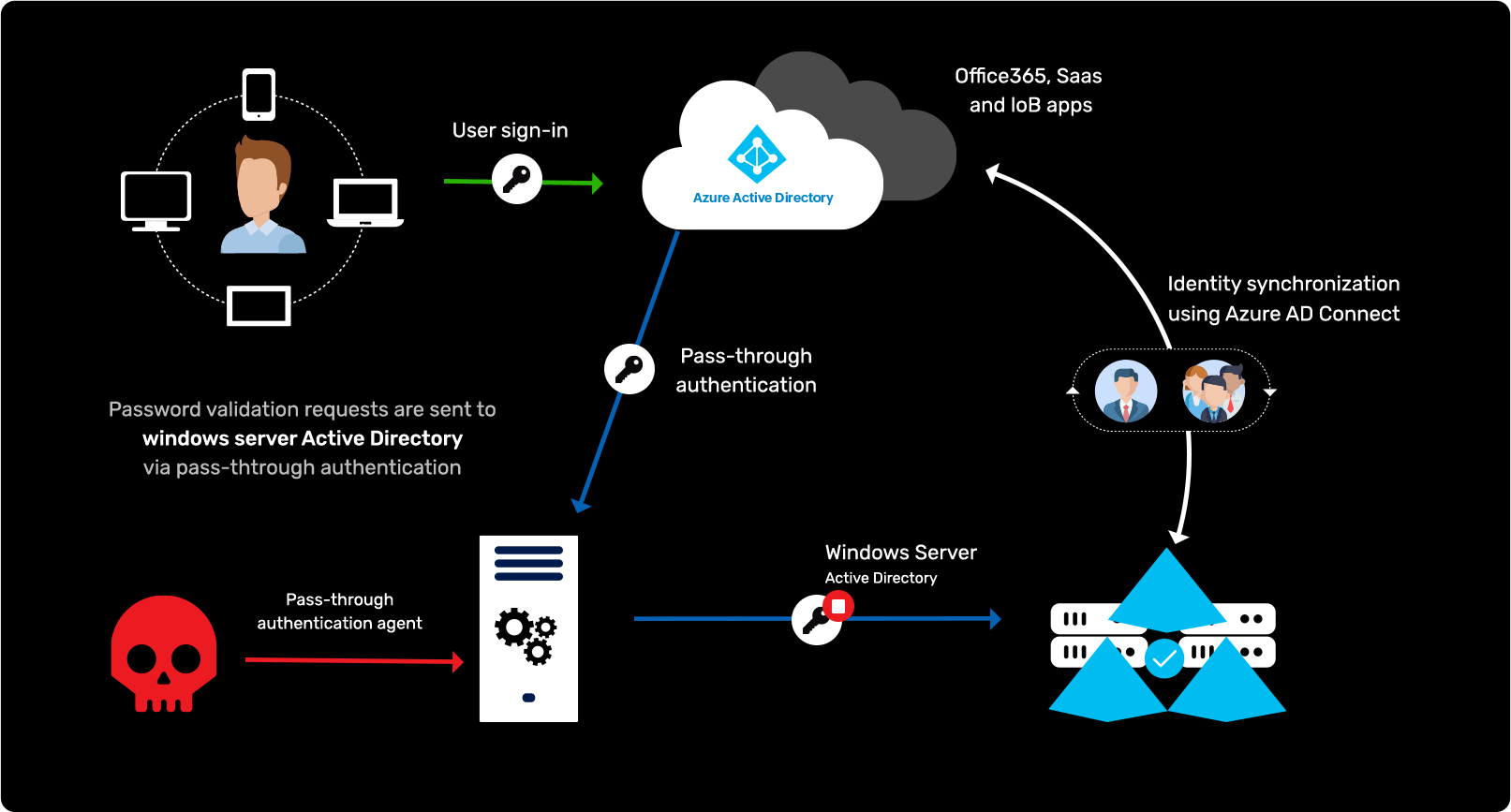
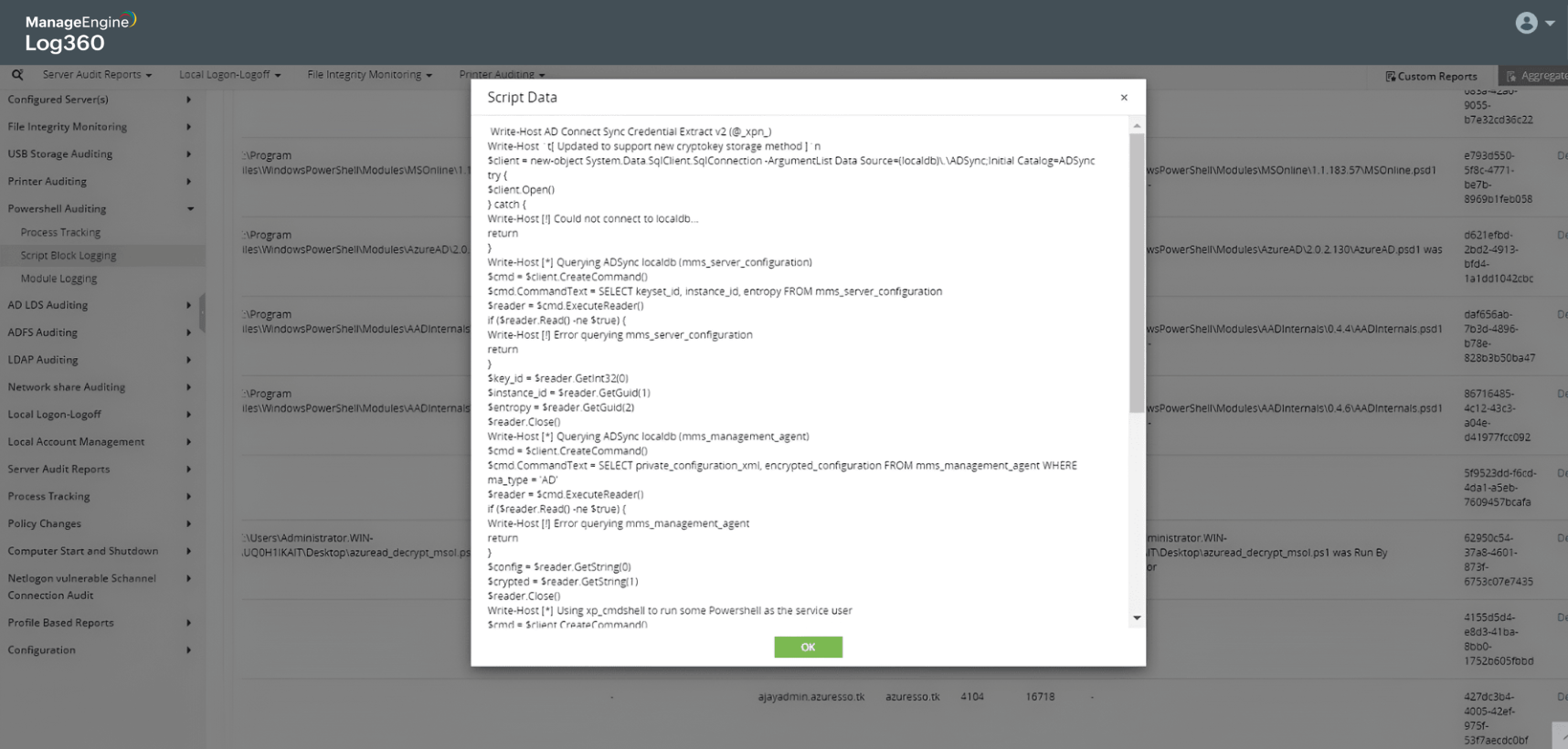
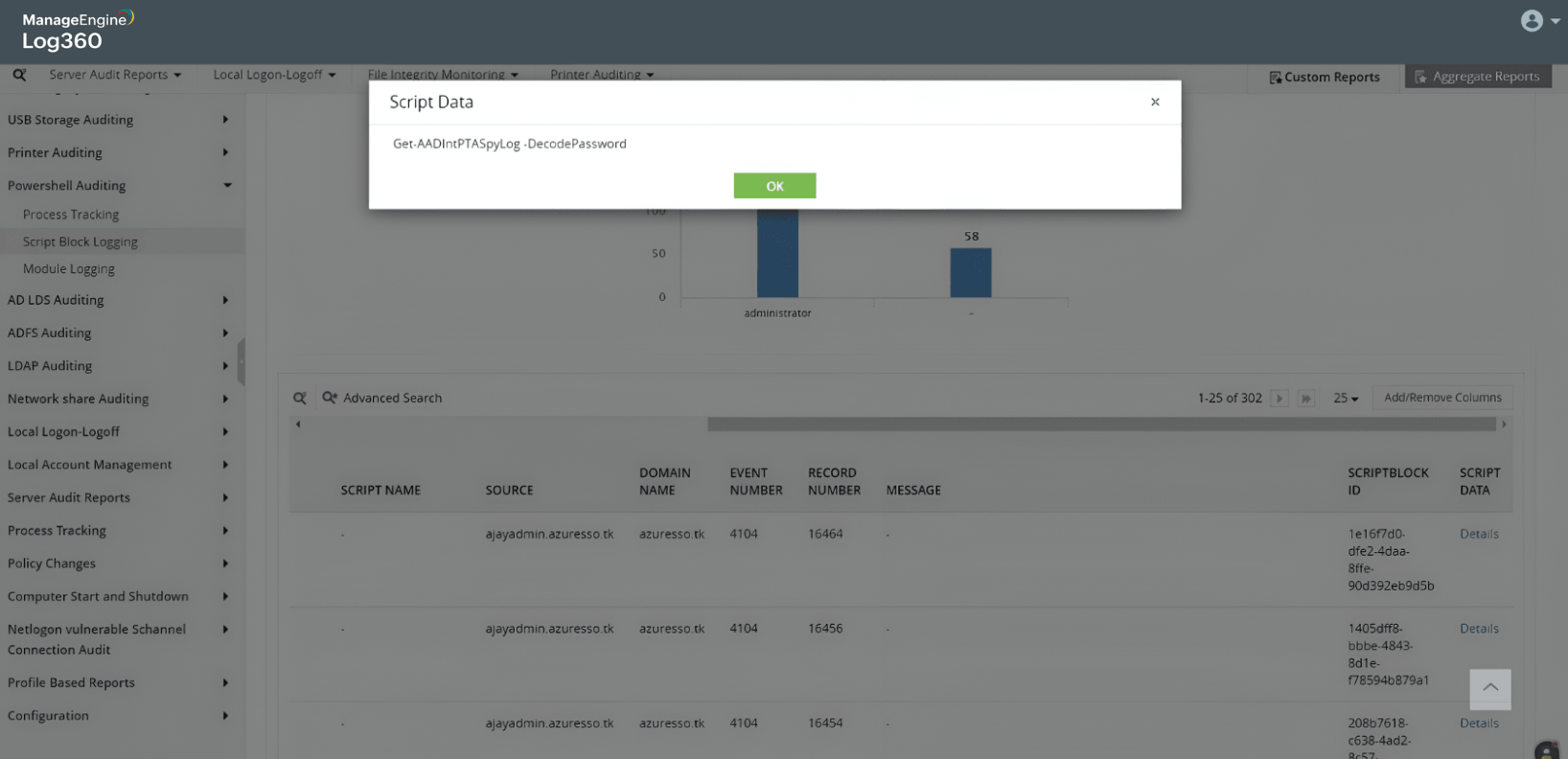
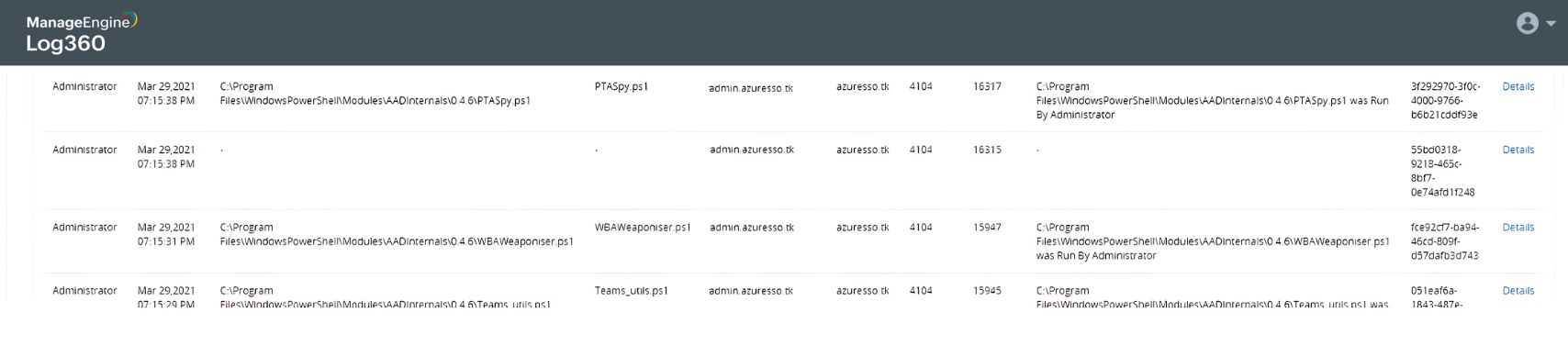
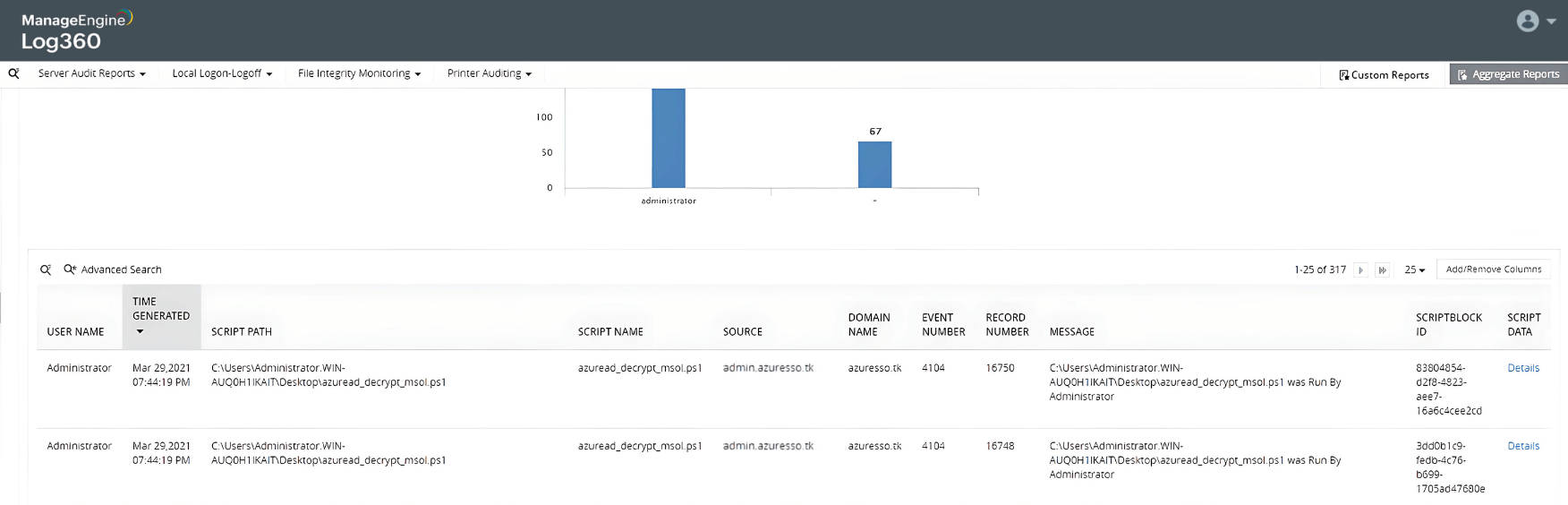
AD to Azure AD attack
Learn more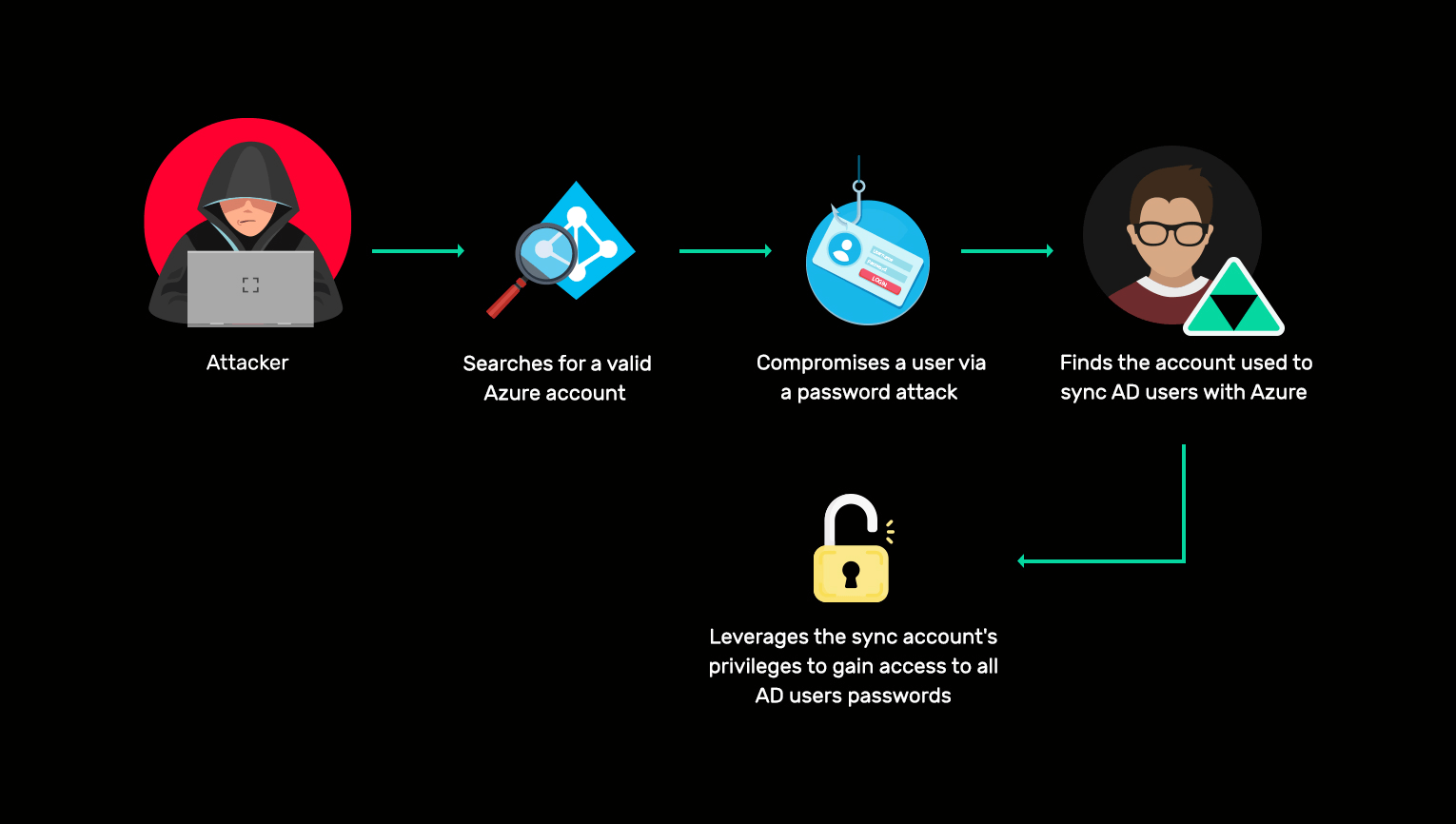
-
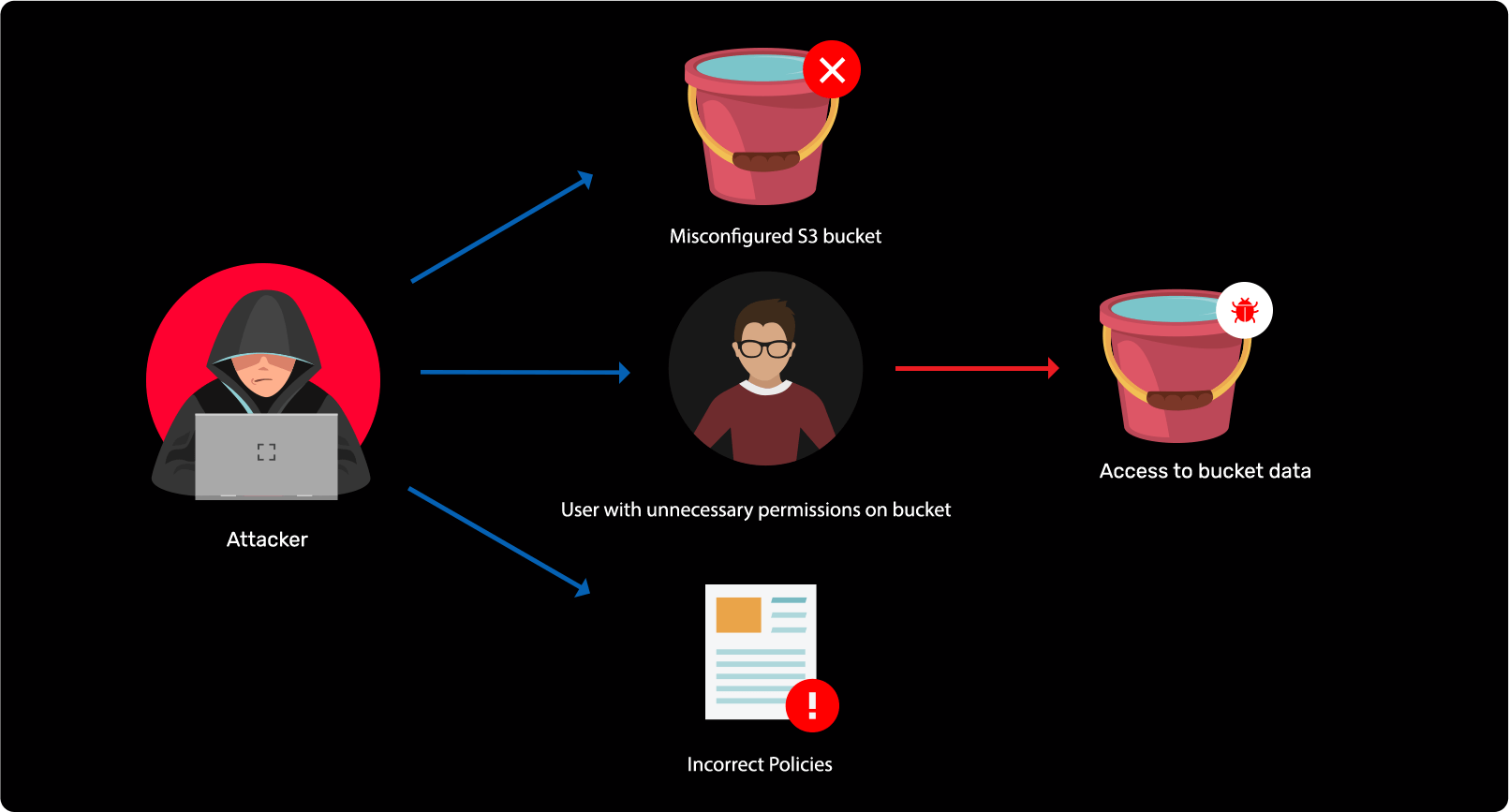
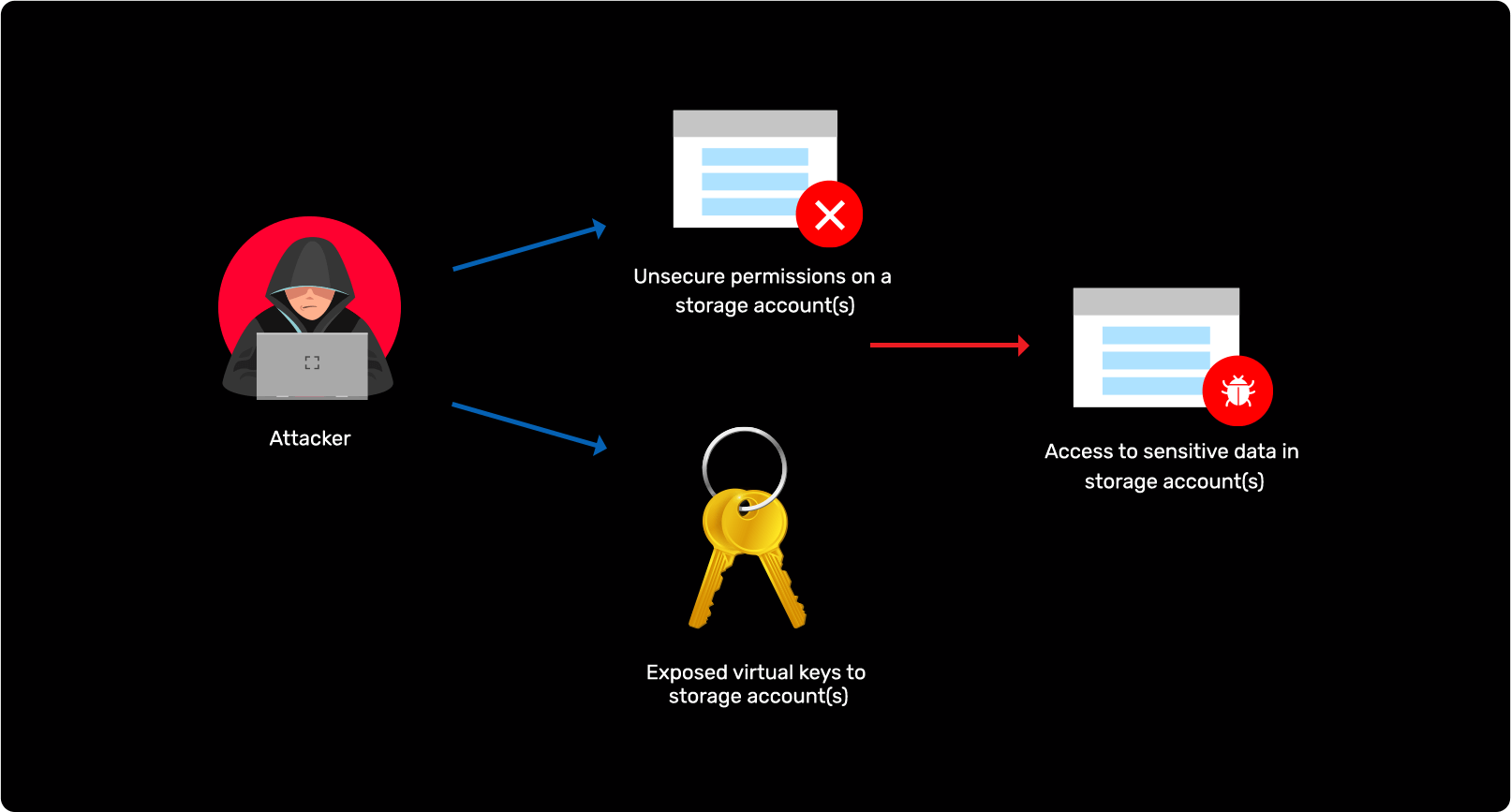
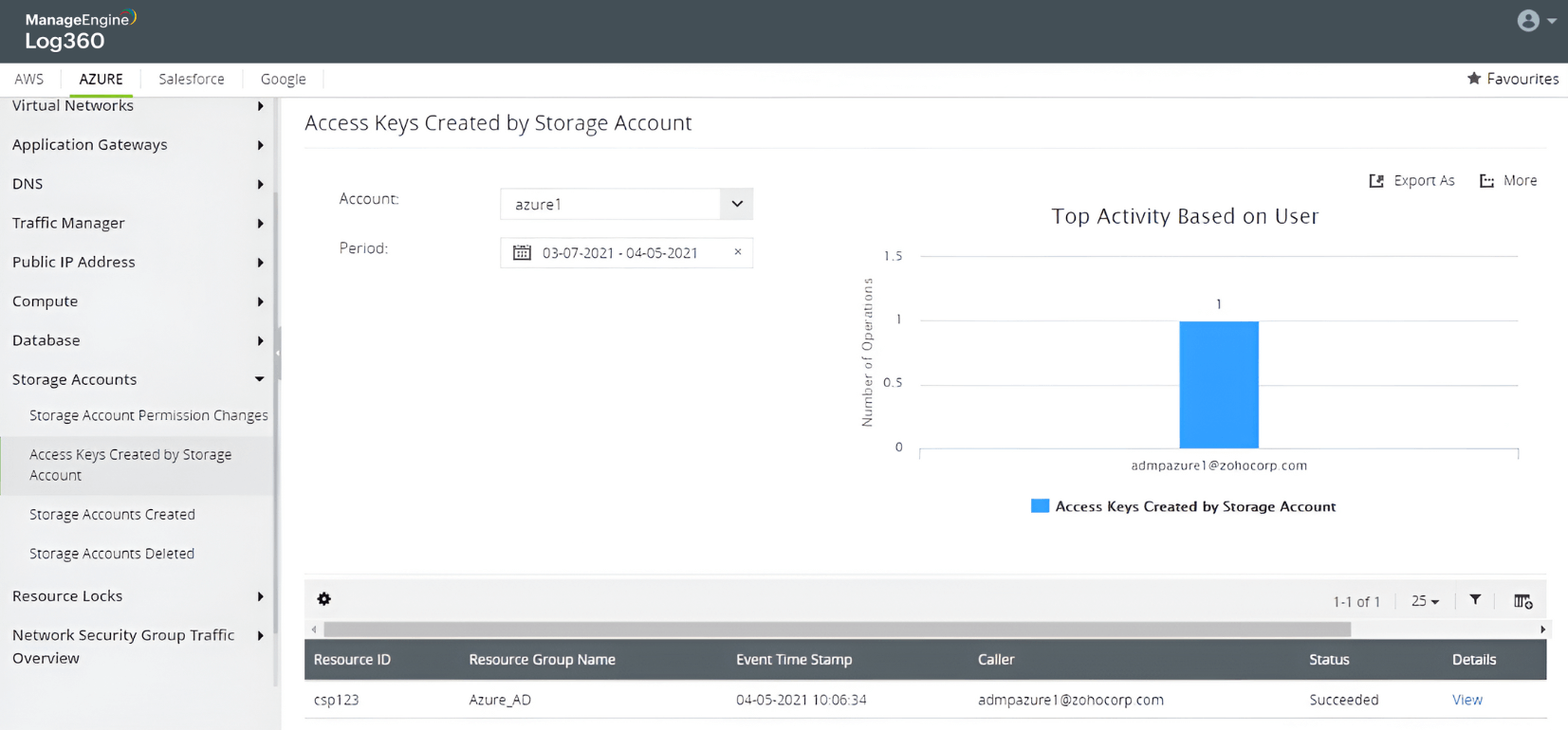
Storage attack in Azure and AWS
Learn more
-
New
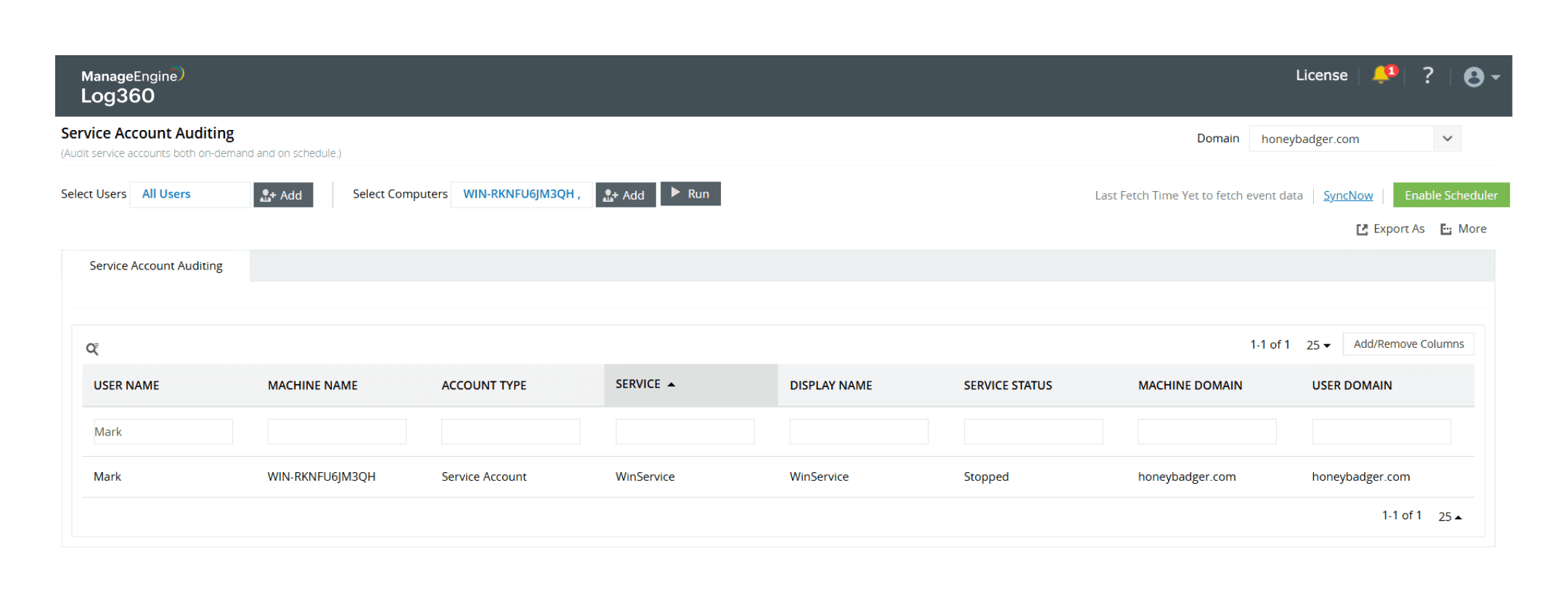
Securing Windows services
Learn more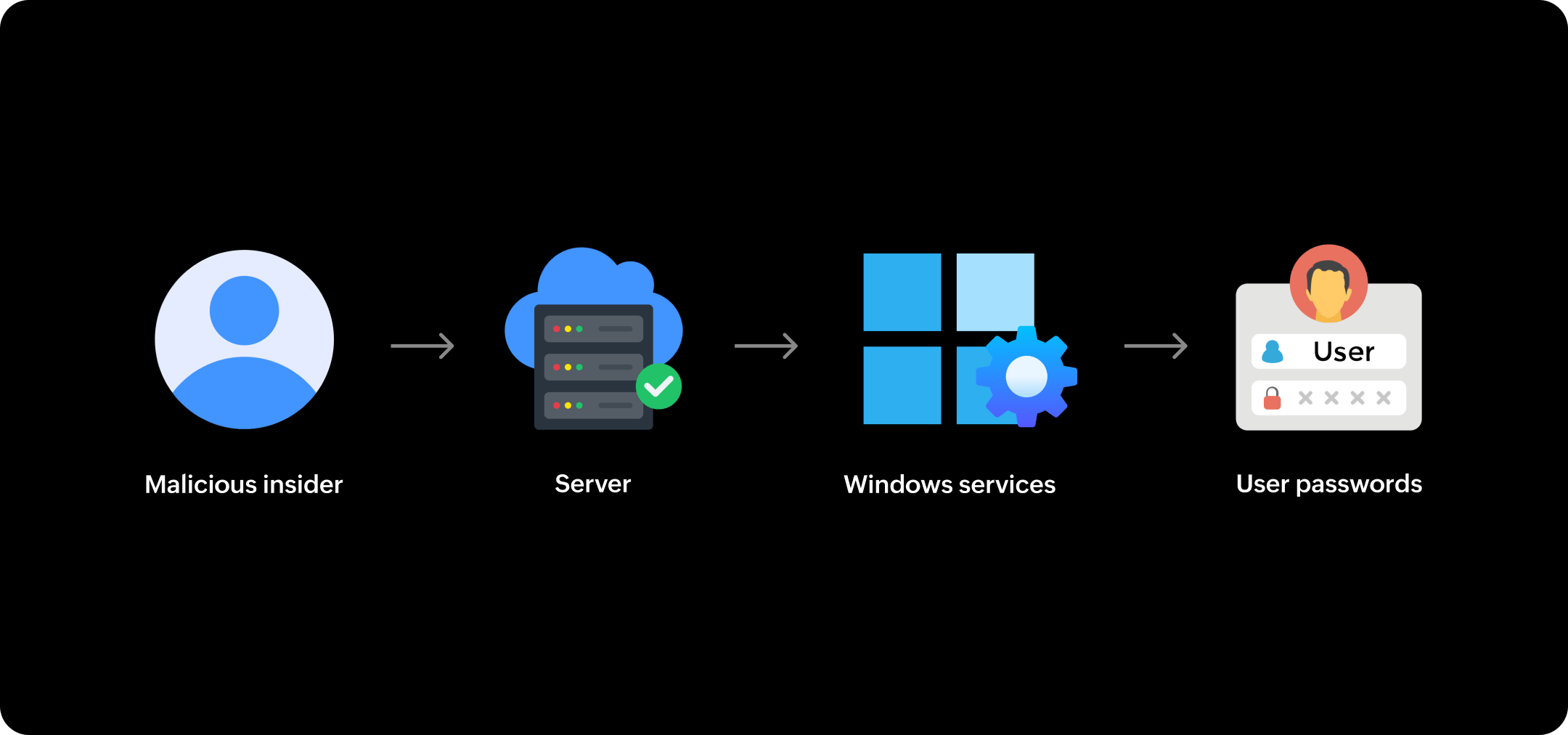
-
New
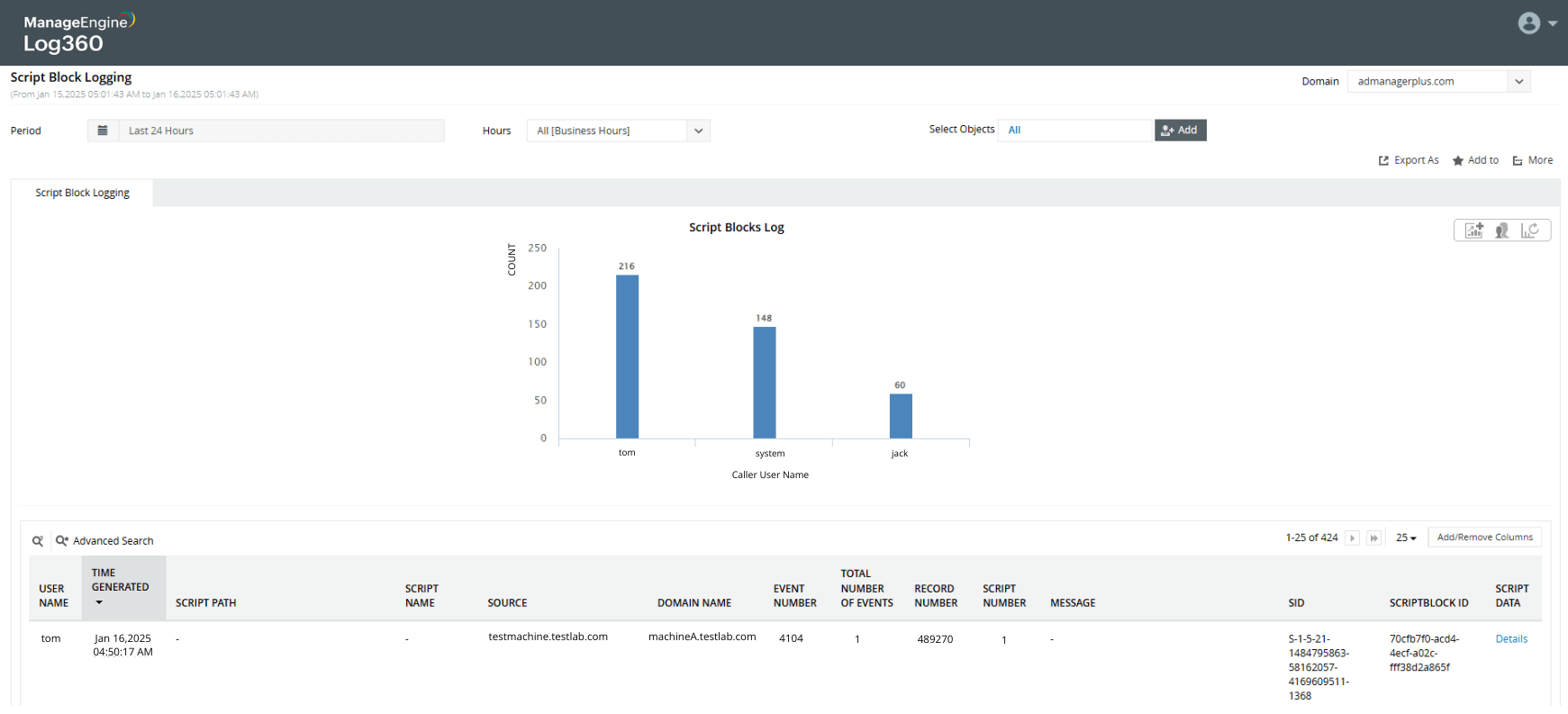
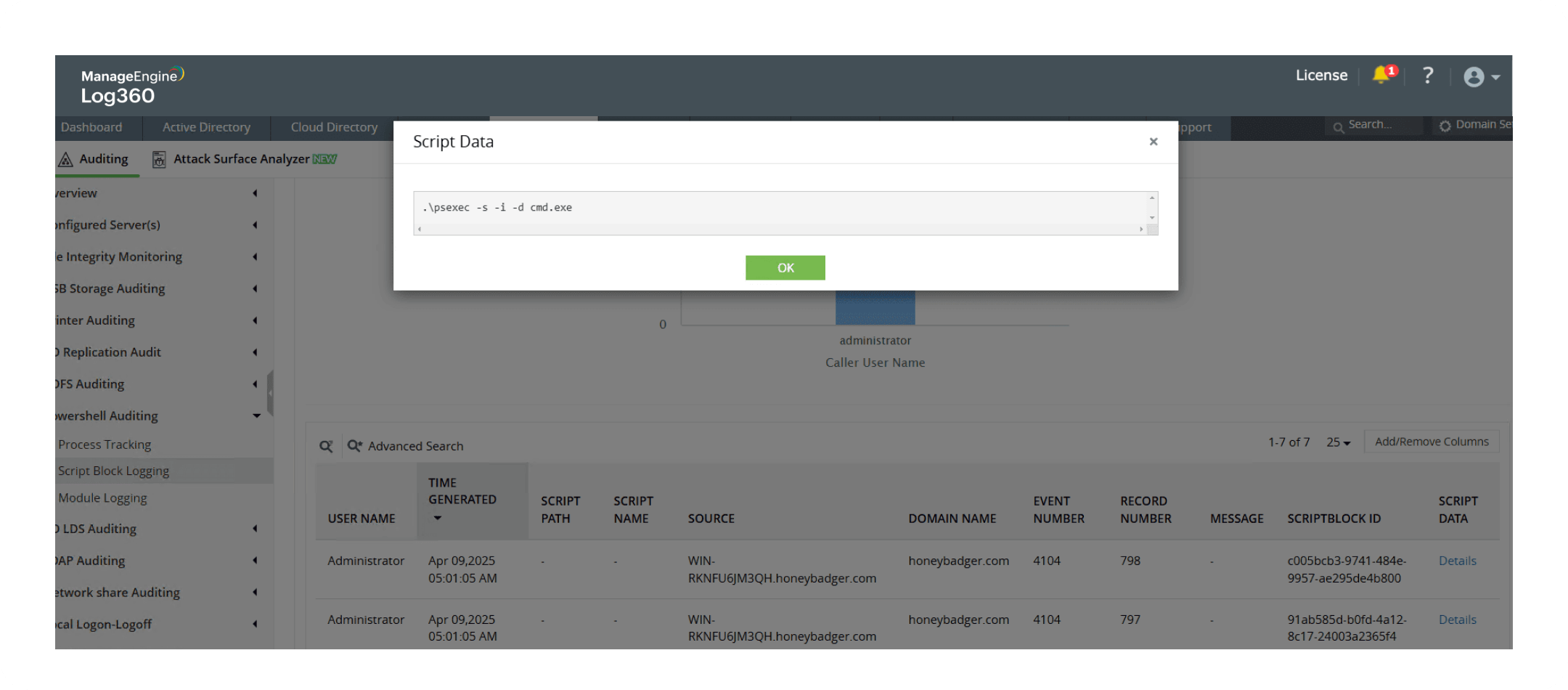
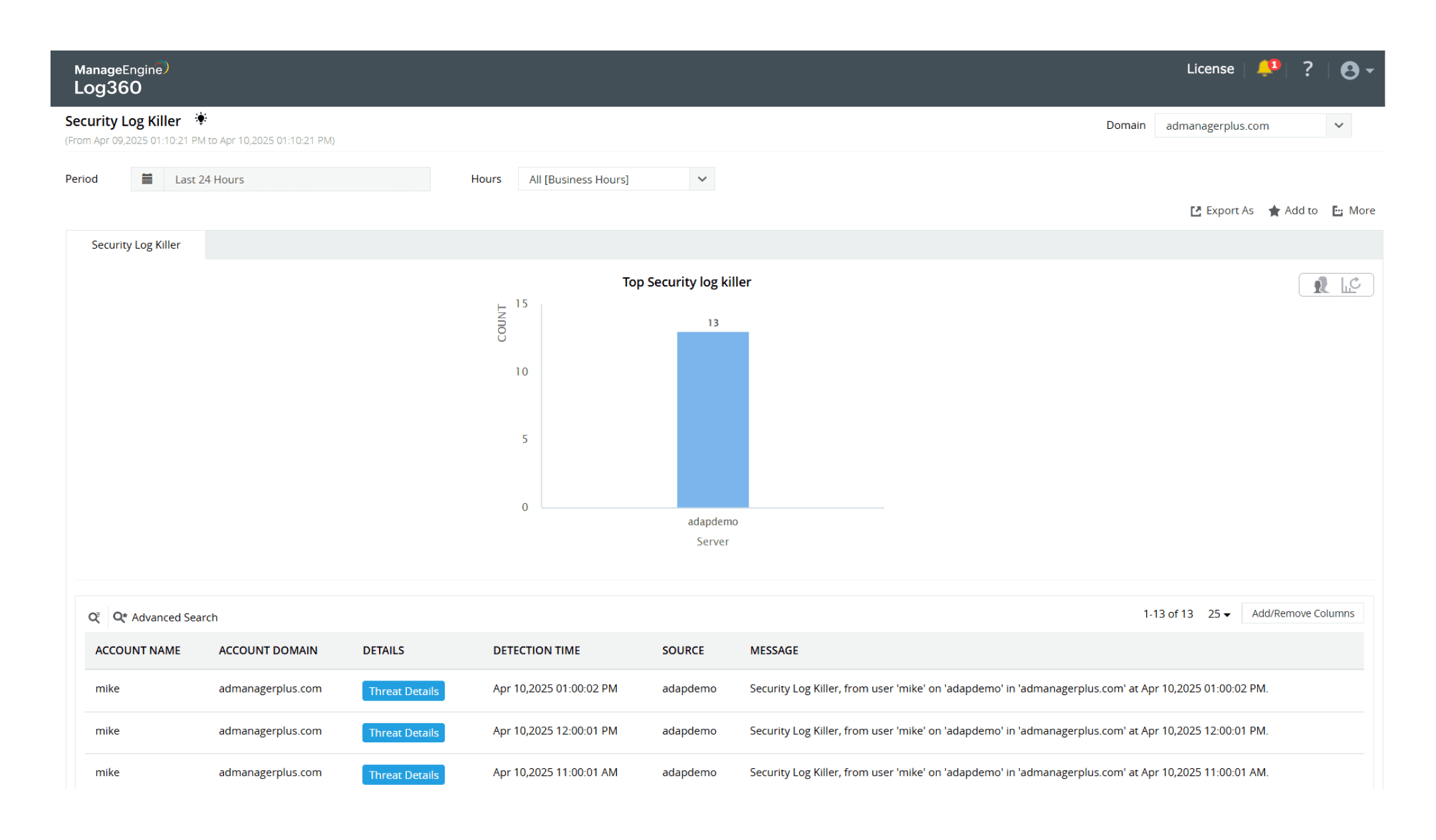
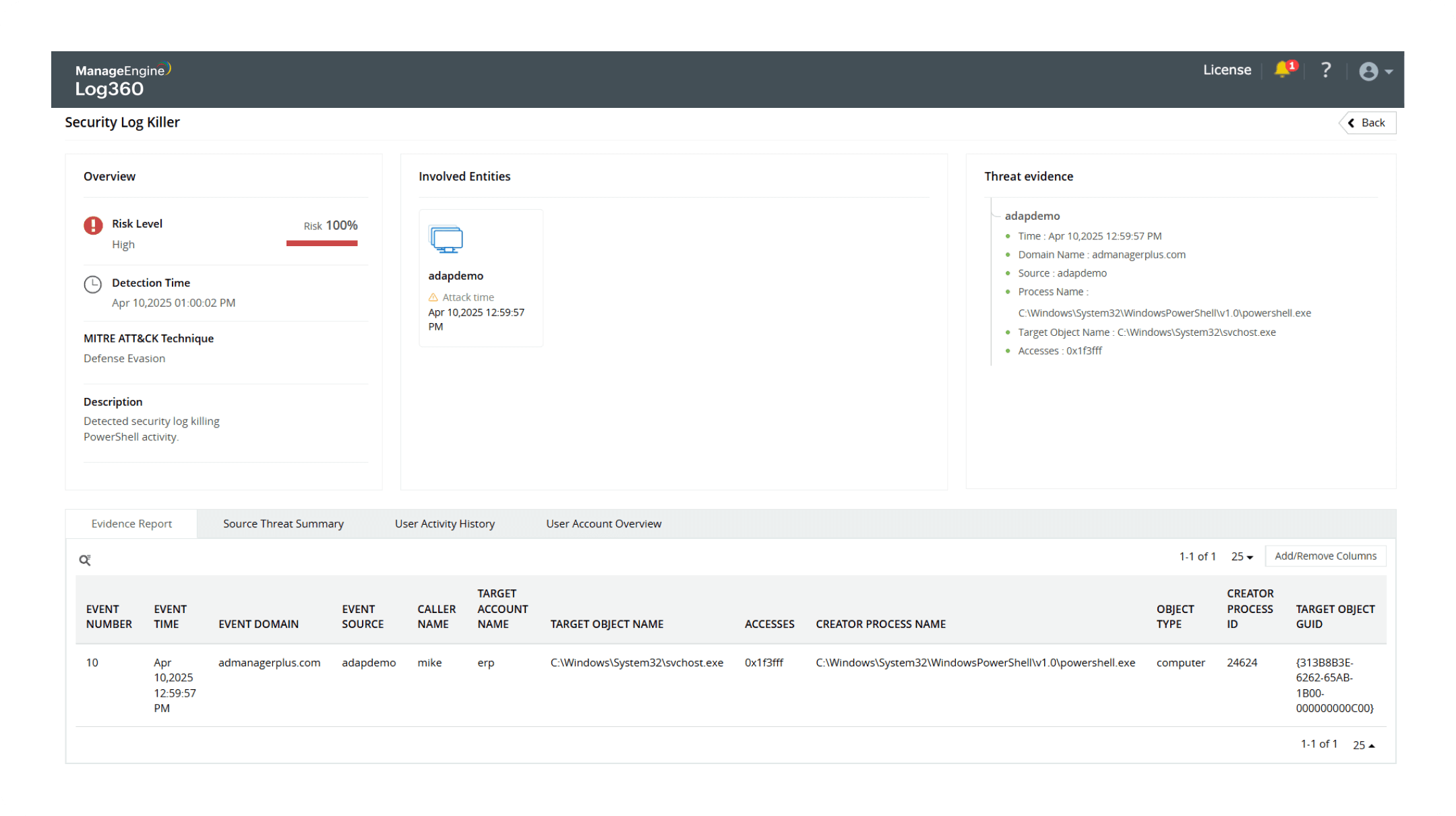
Security Log killer
Learn more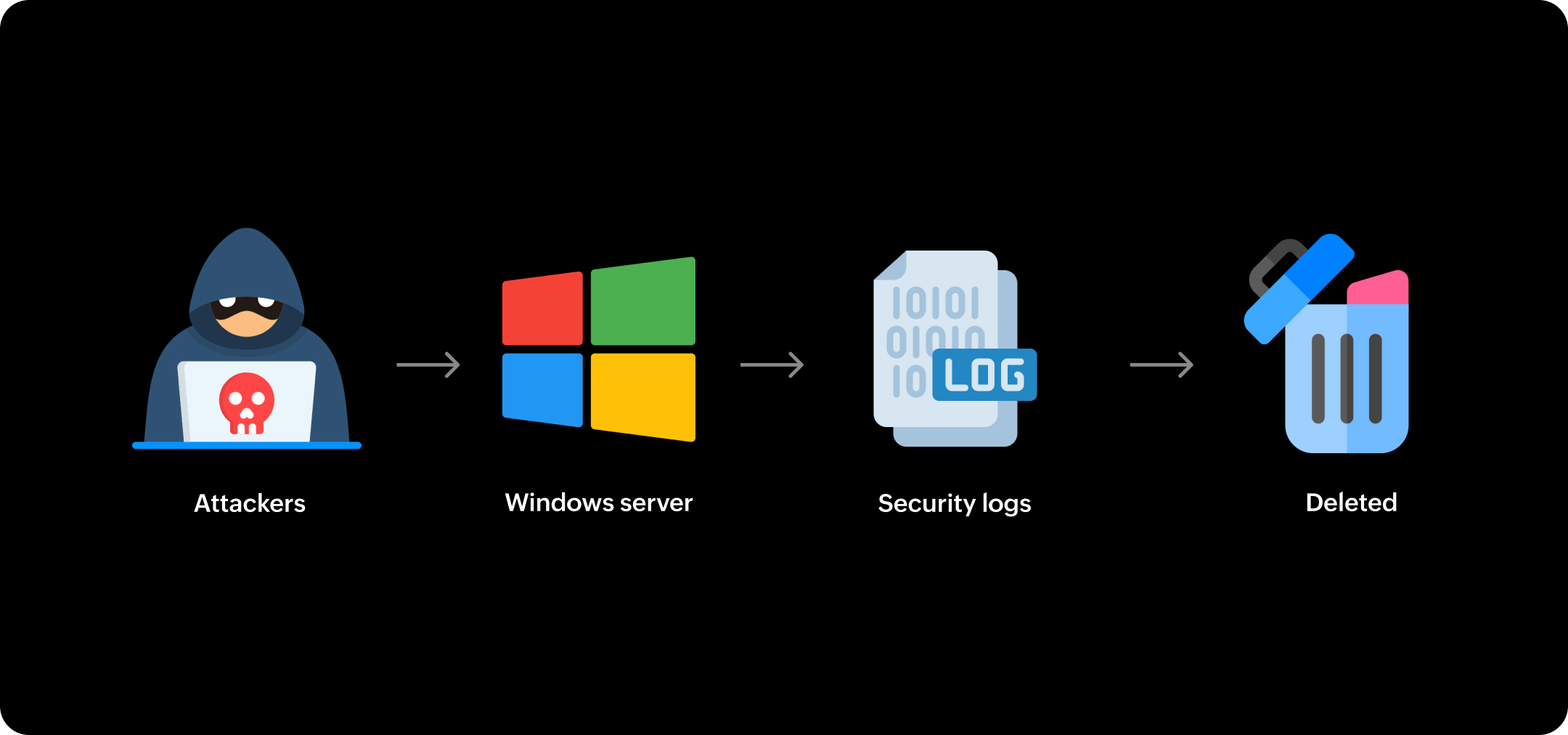
-
Detecting attacks in Linux environments
Learn more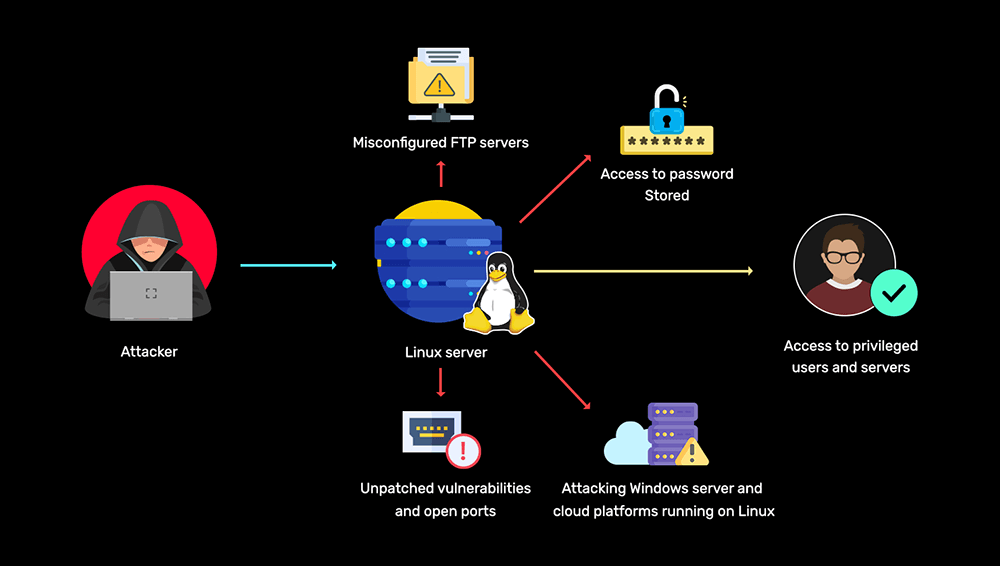
-
Detecting attacks in Windows environments
Learn more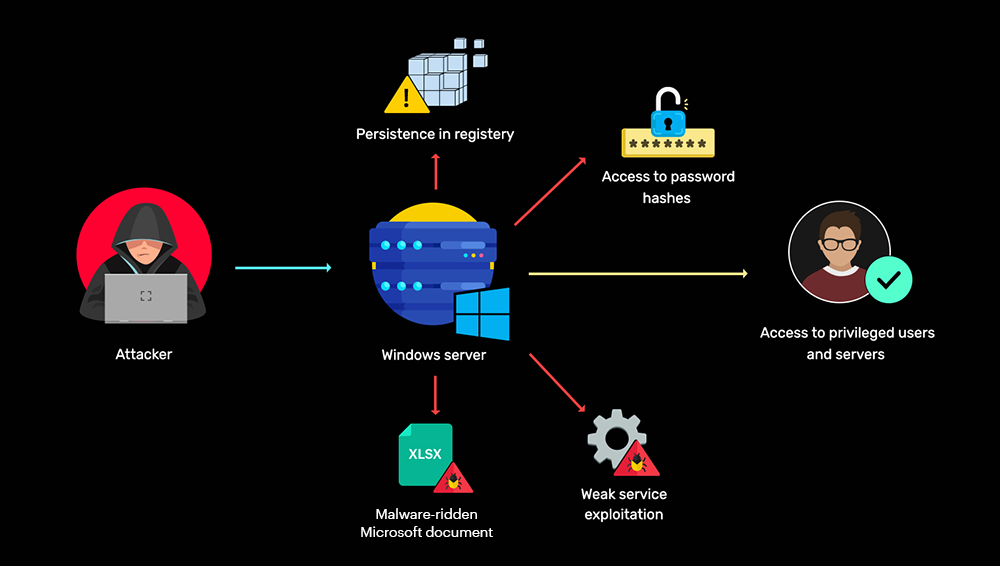
-
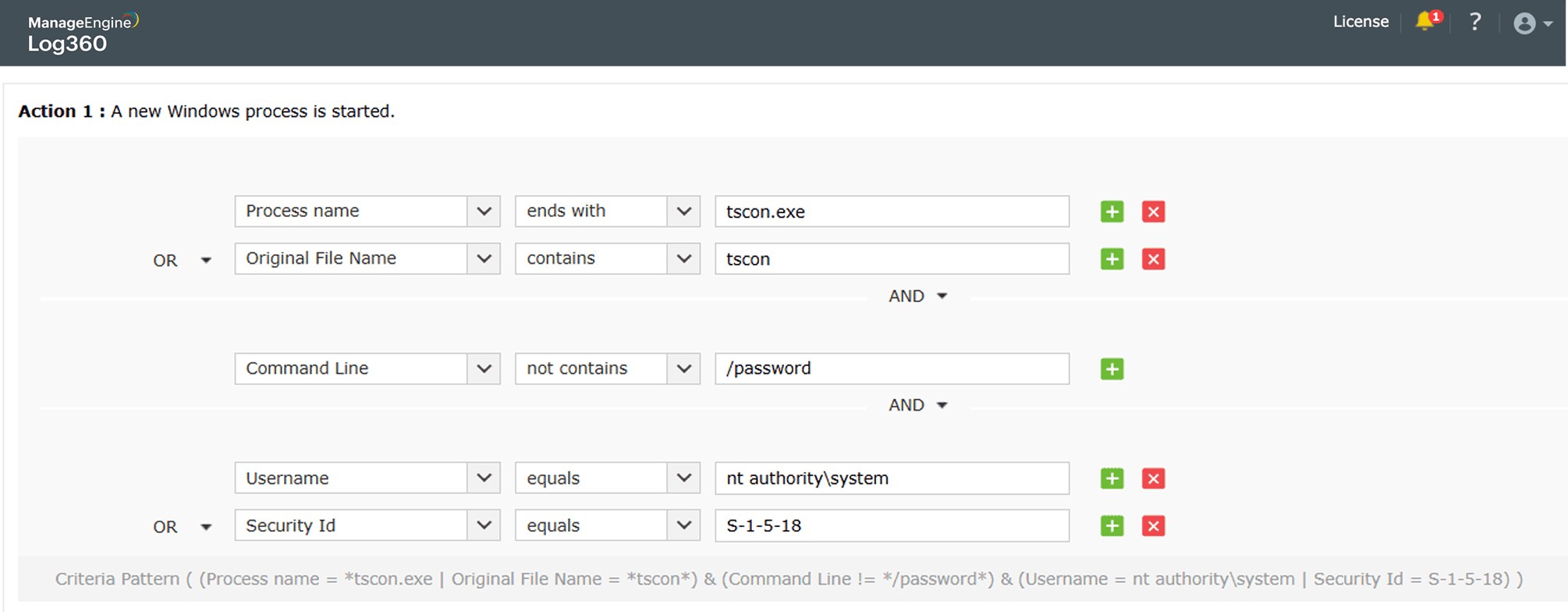
Bypass Windows Logons attack
Learn more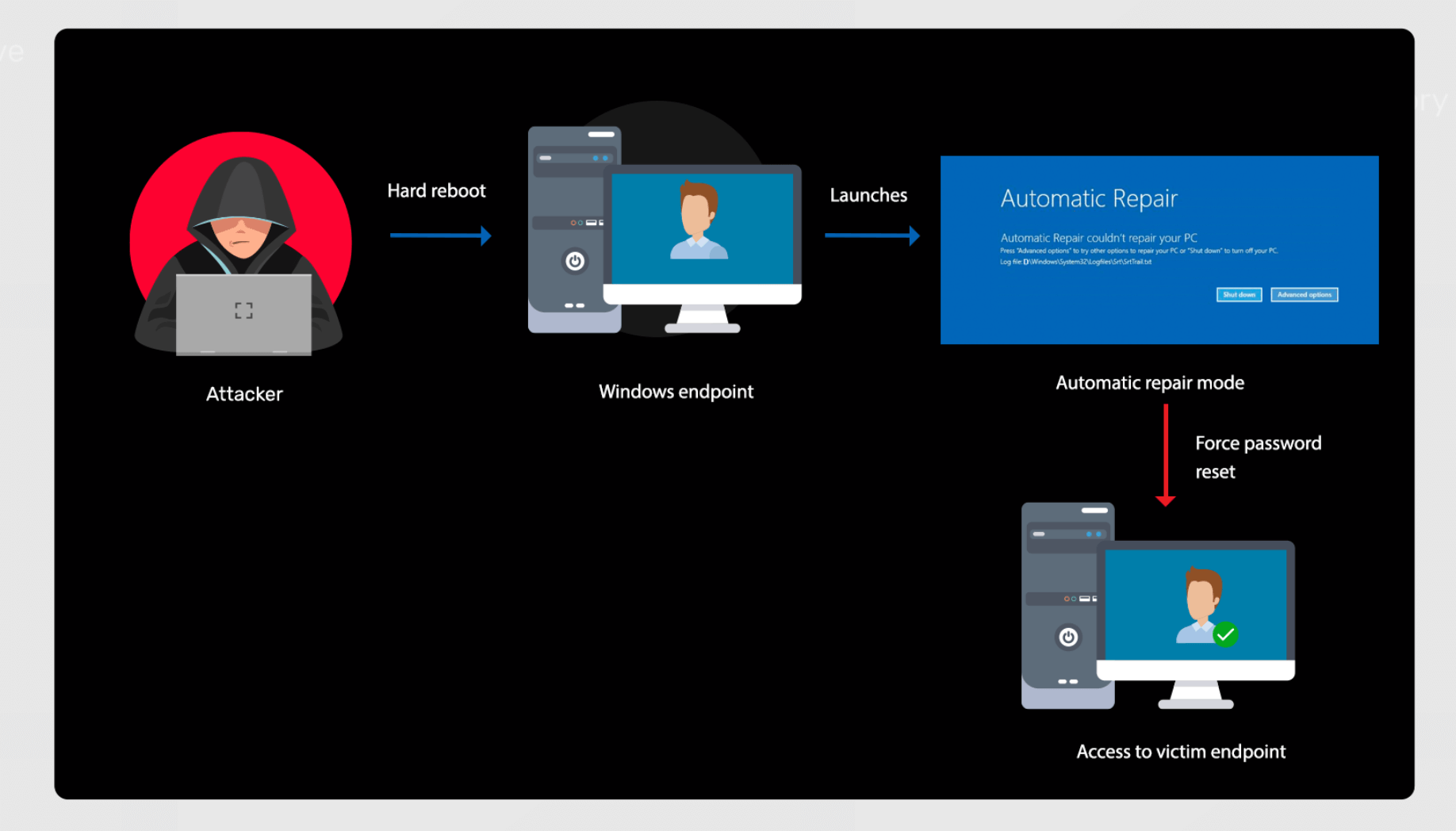
-
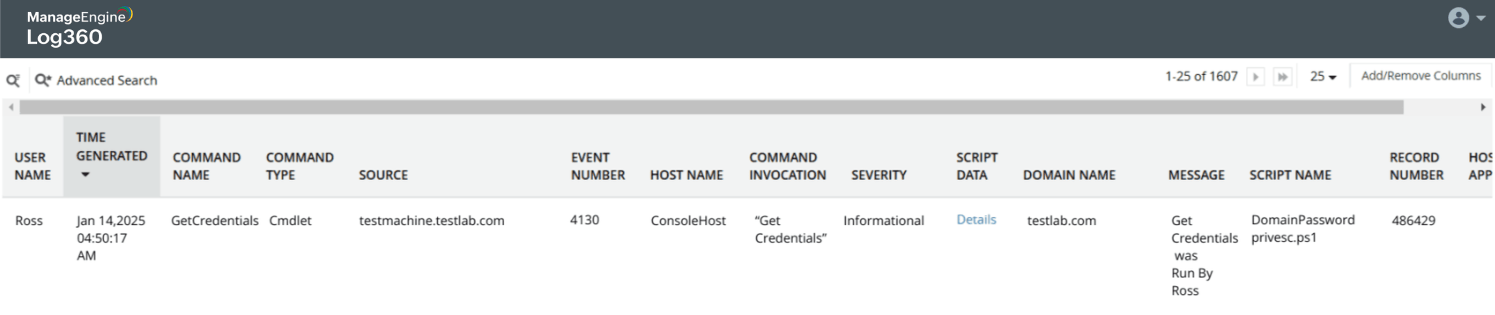
Credential dumping attack
Learn more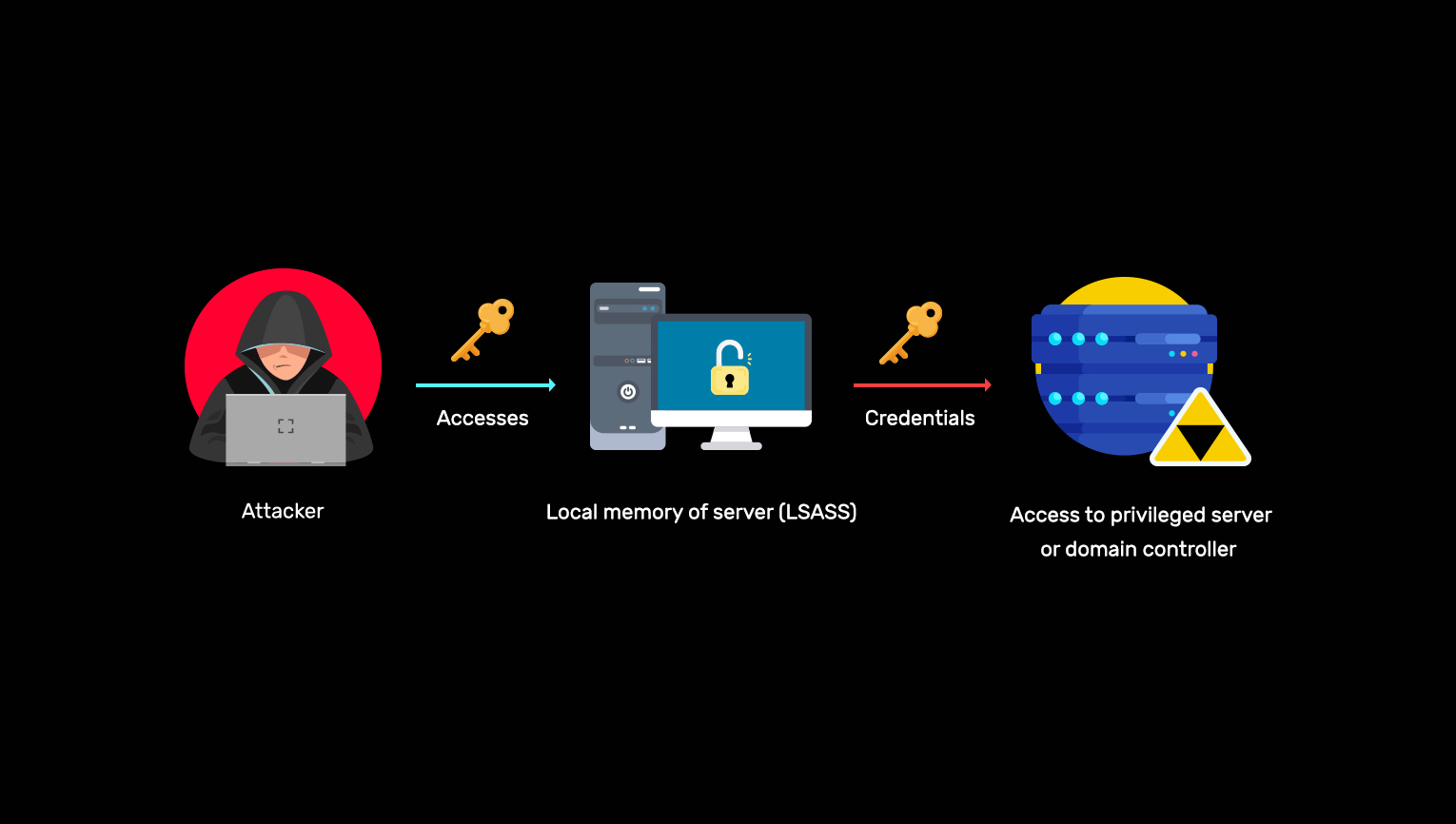
-
Kerberroasting attack
Learn more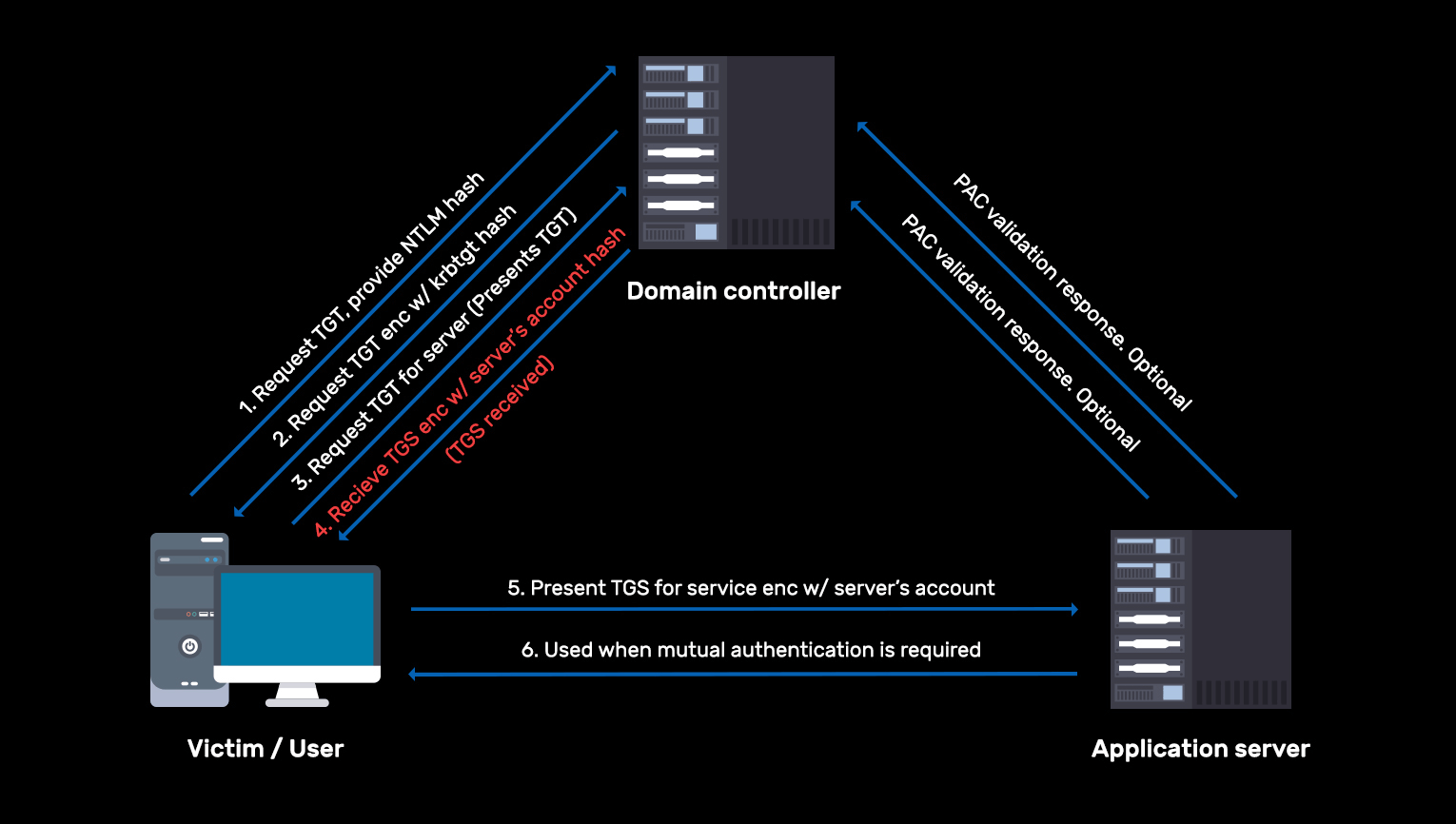
-
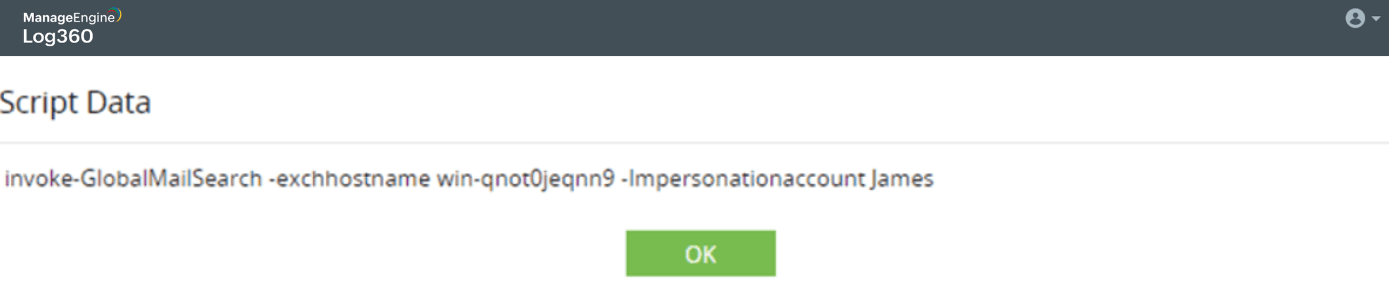
Compromising an exchange server and extracting sensitive emails
Learn more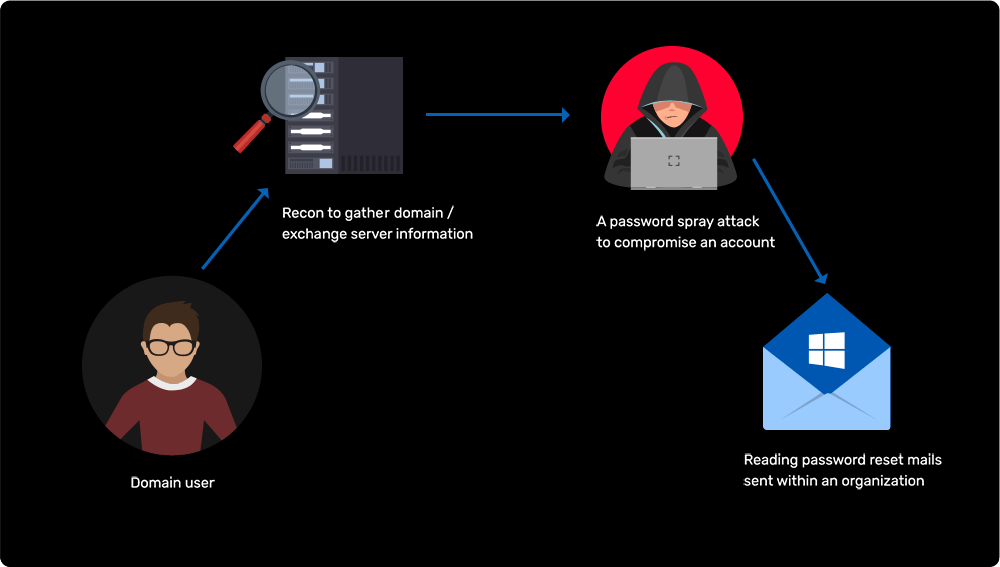
-
Ransomware attacks on organizations
Learn more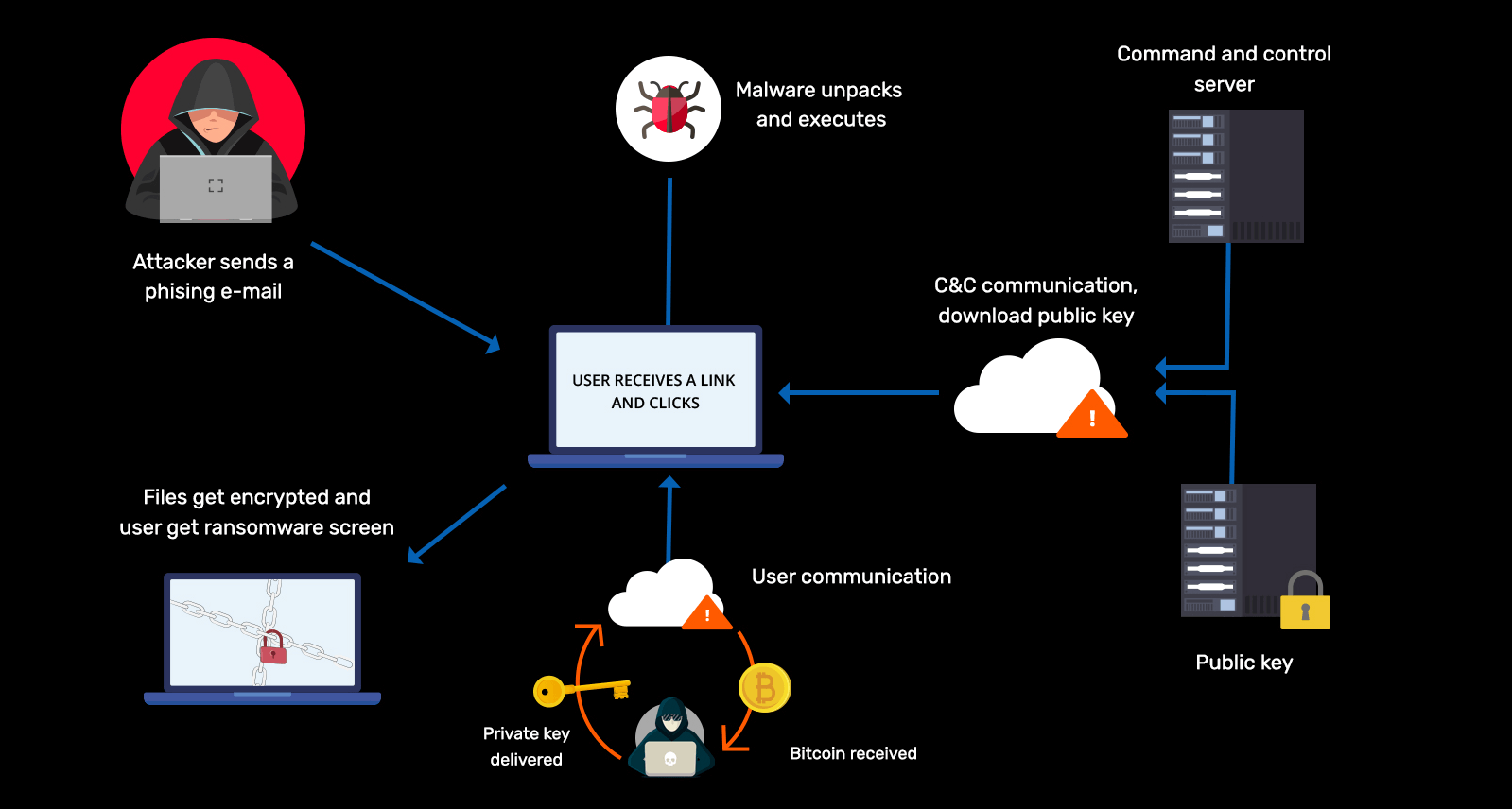
-
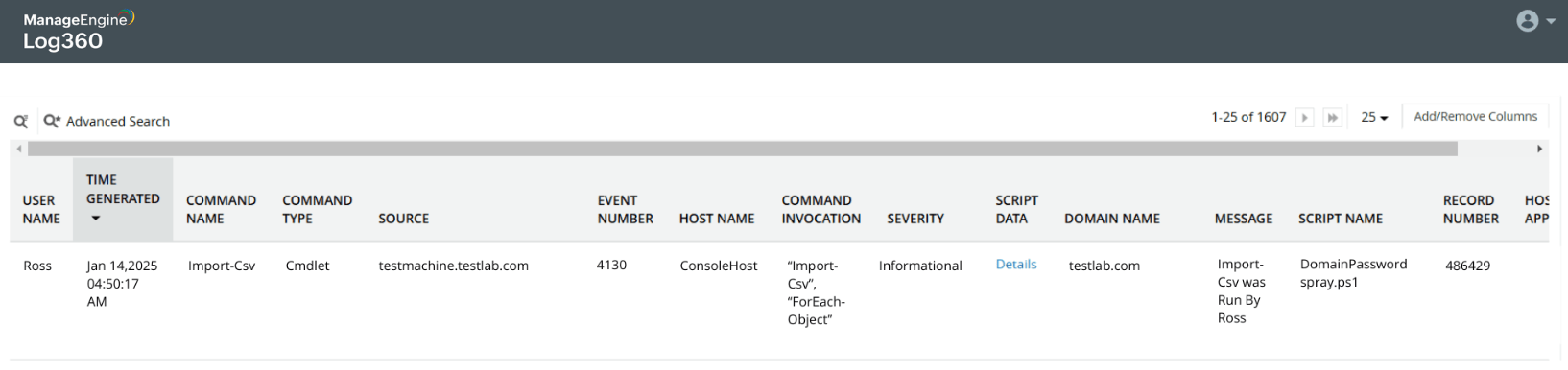
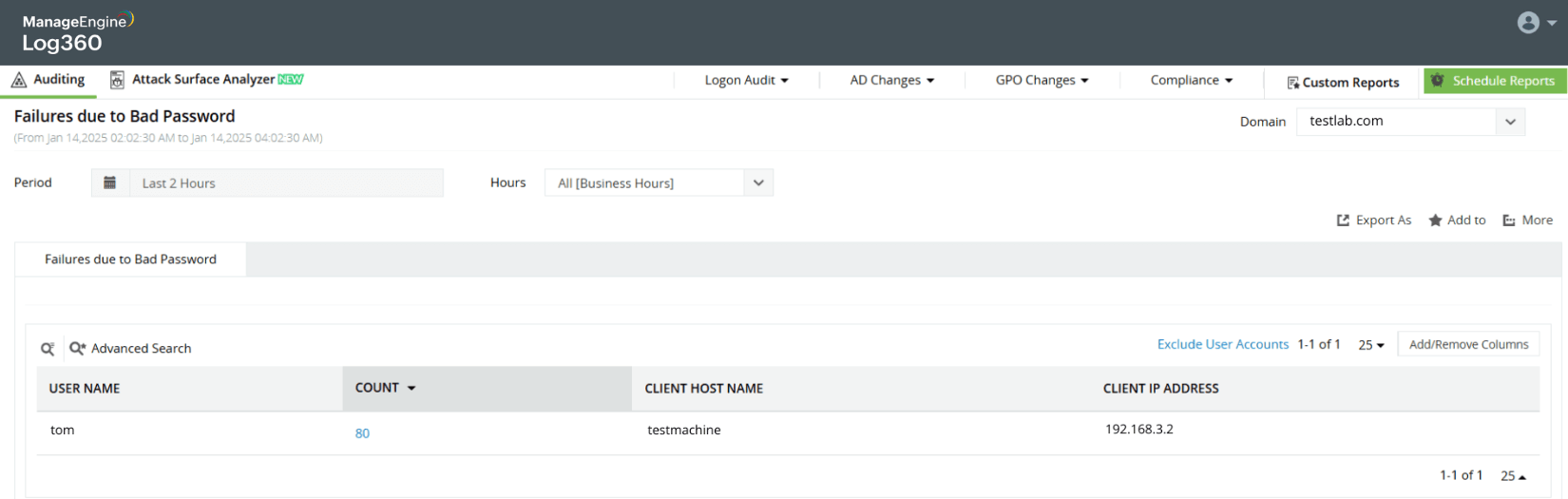
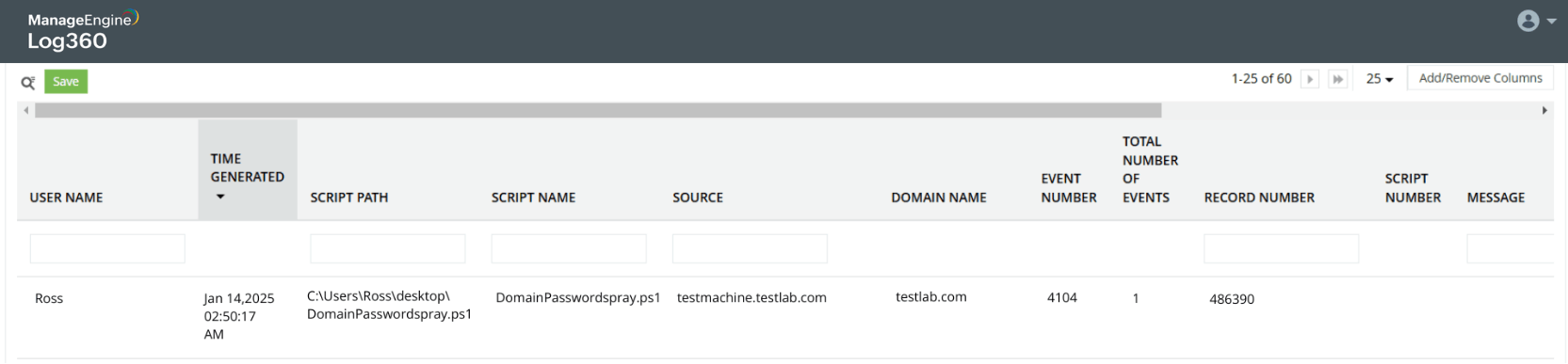
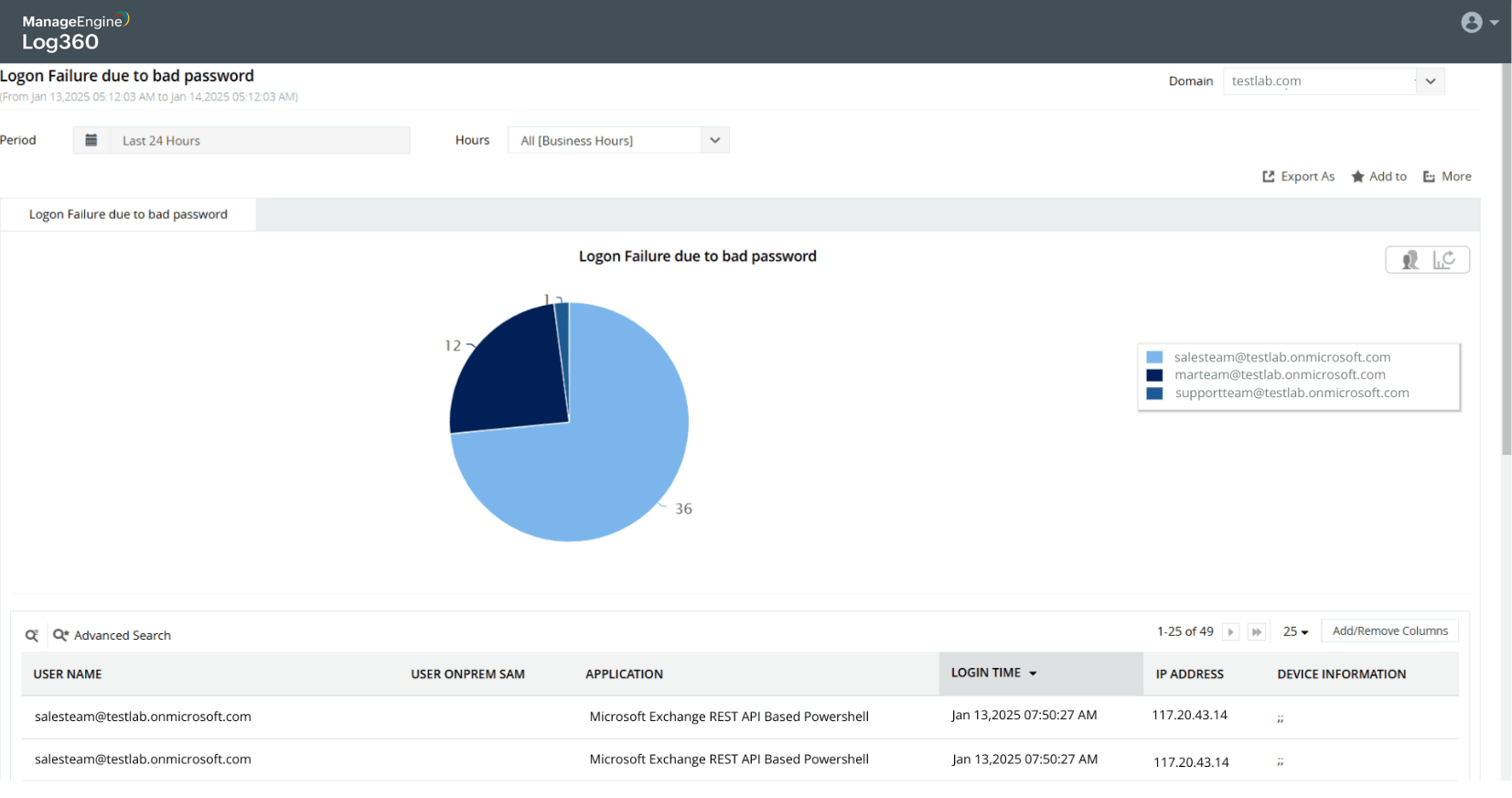
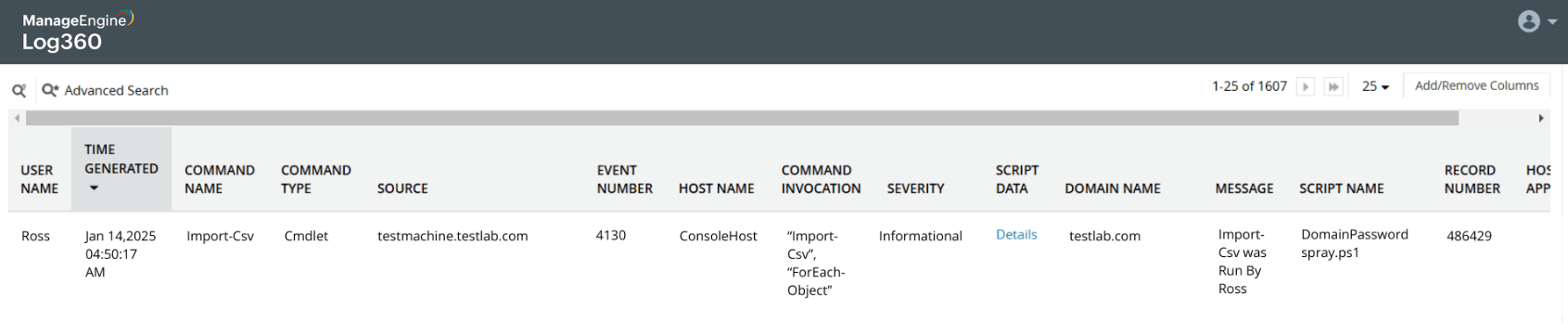
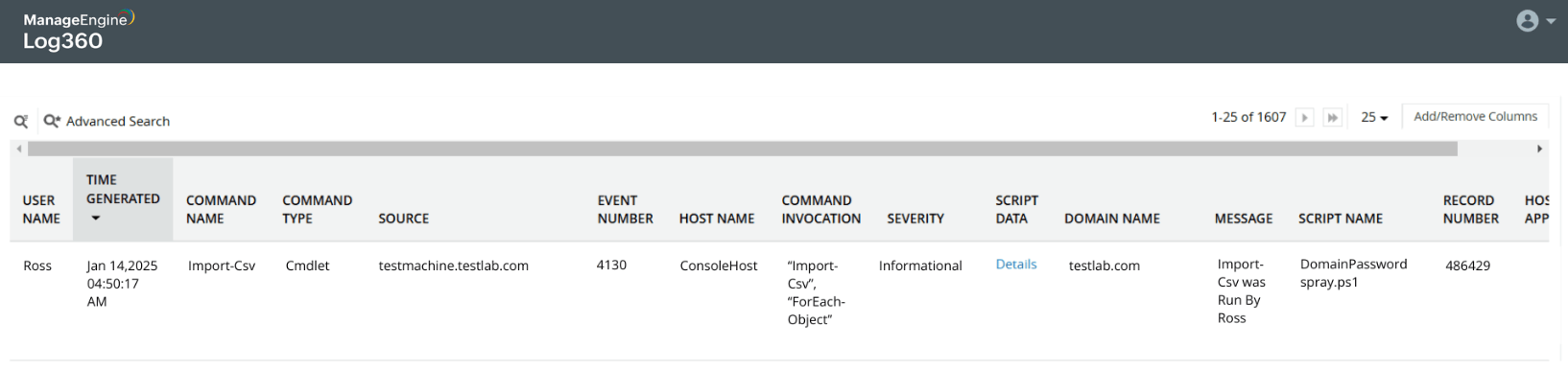
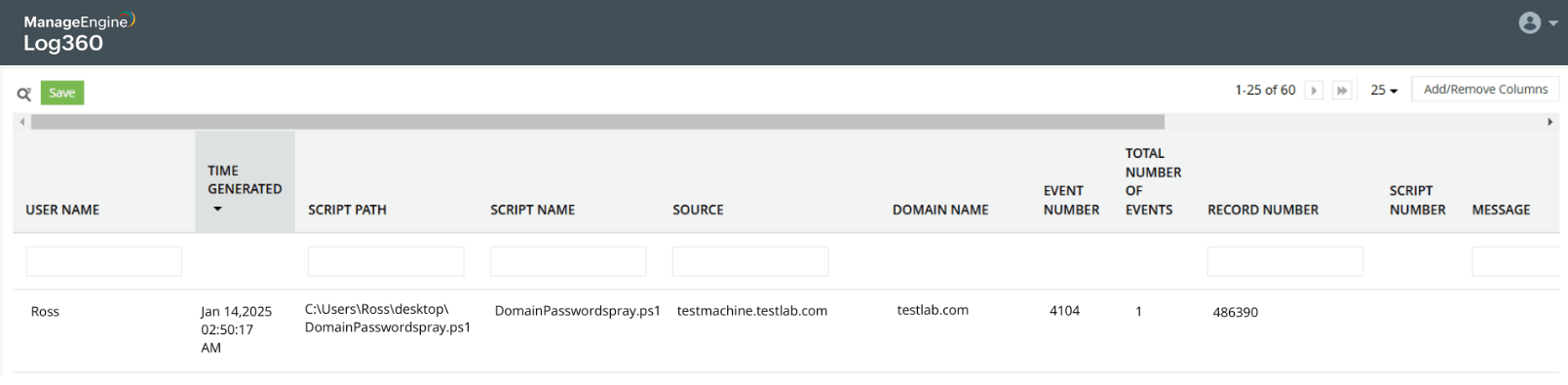
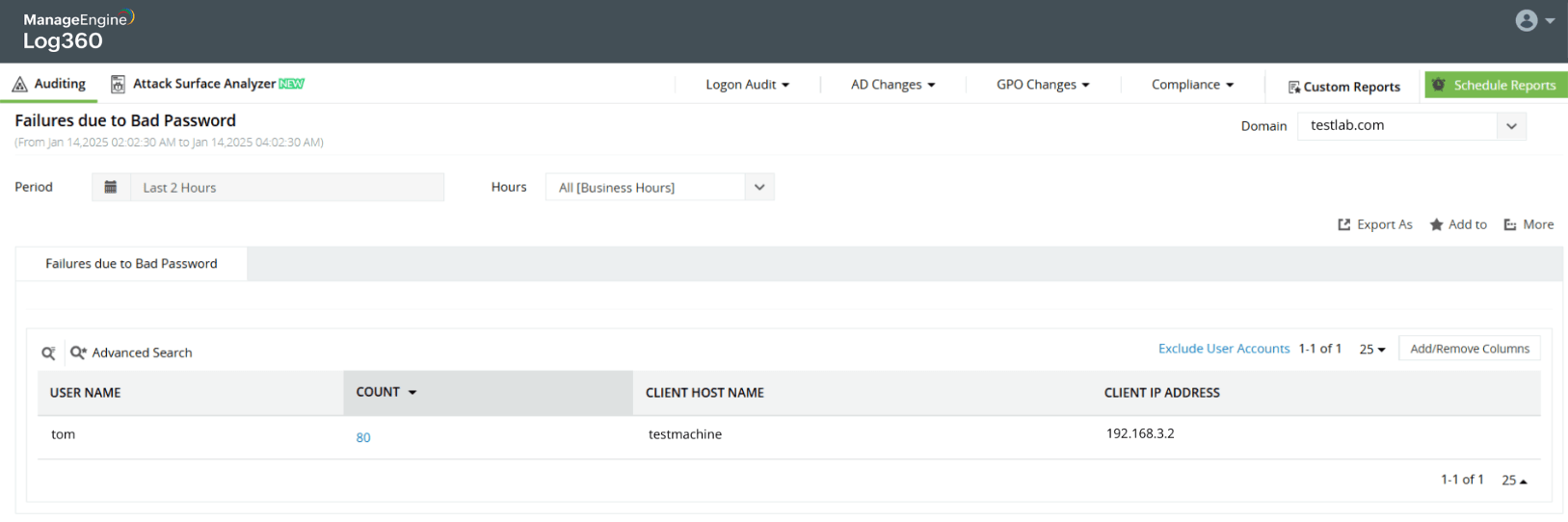
Password spray attack on Active Directory users
Learn more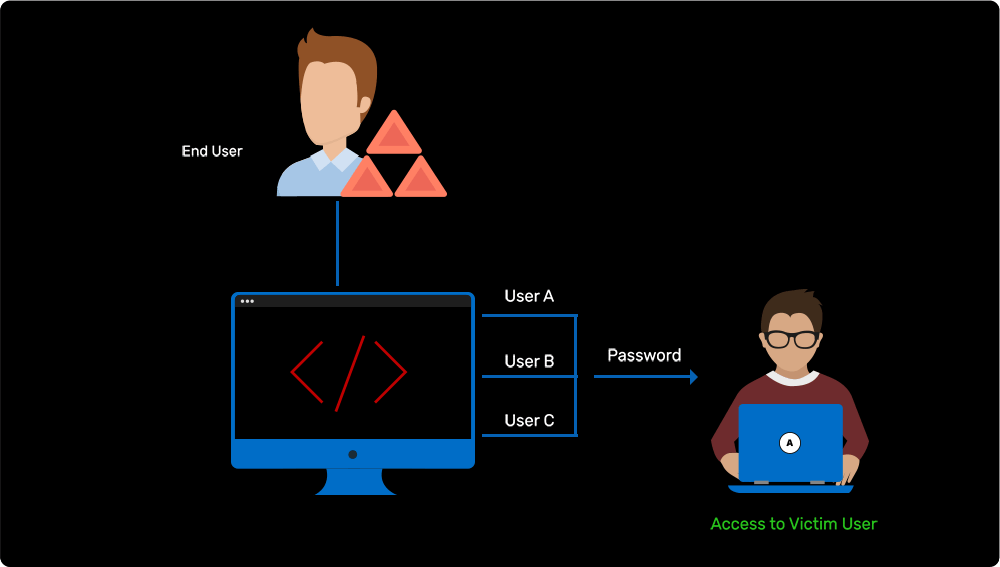
-
Attacking authentication in AD and Azure environments
Learn more
-
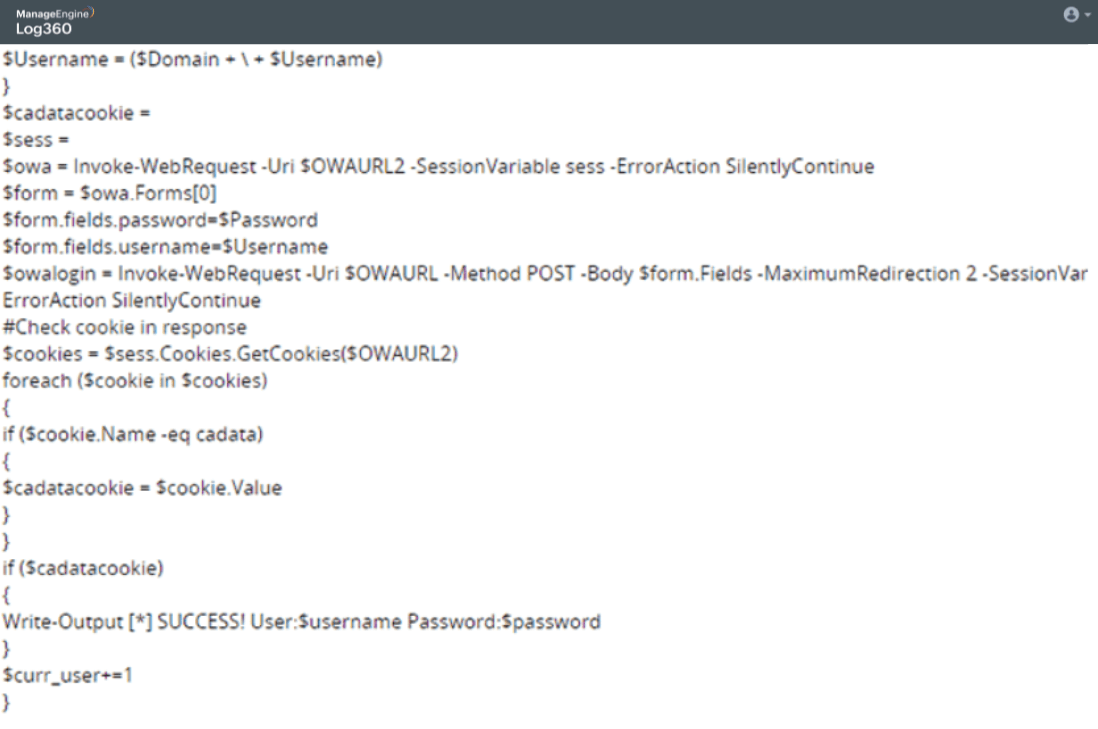
Passing the password hash of admin to gain instant privilege
Learn more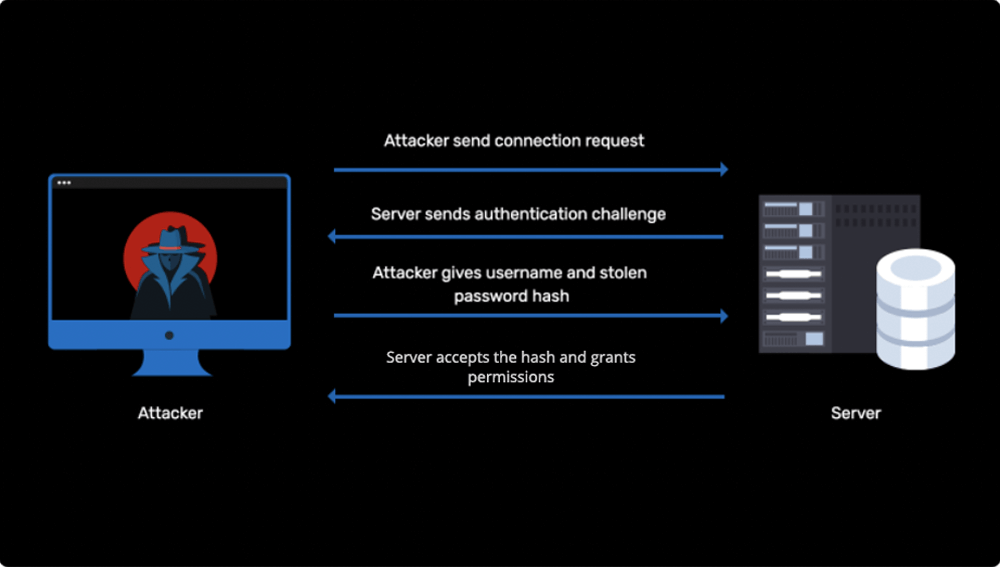
-
Brute forcing Active Directory administrator's password
Learn more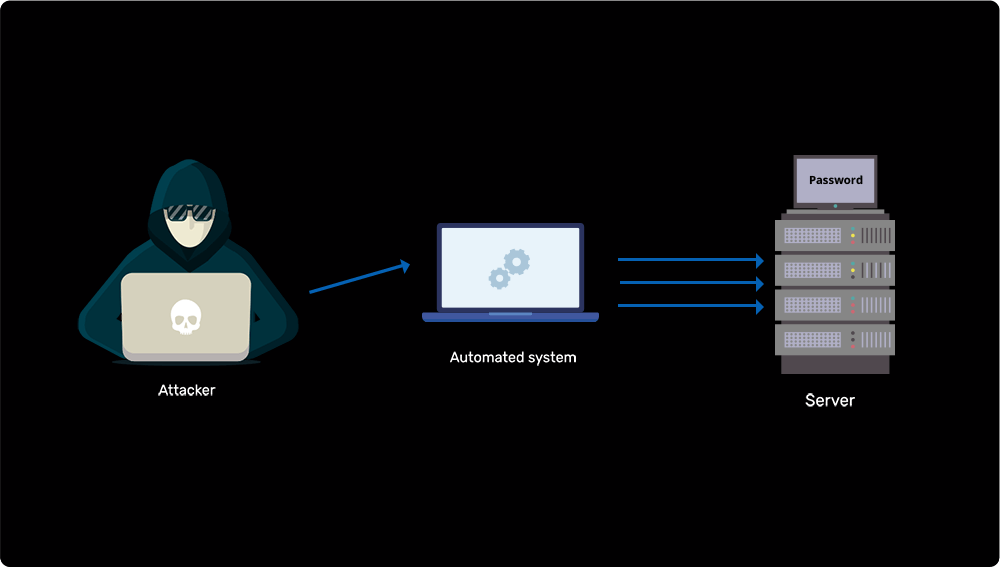
-
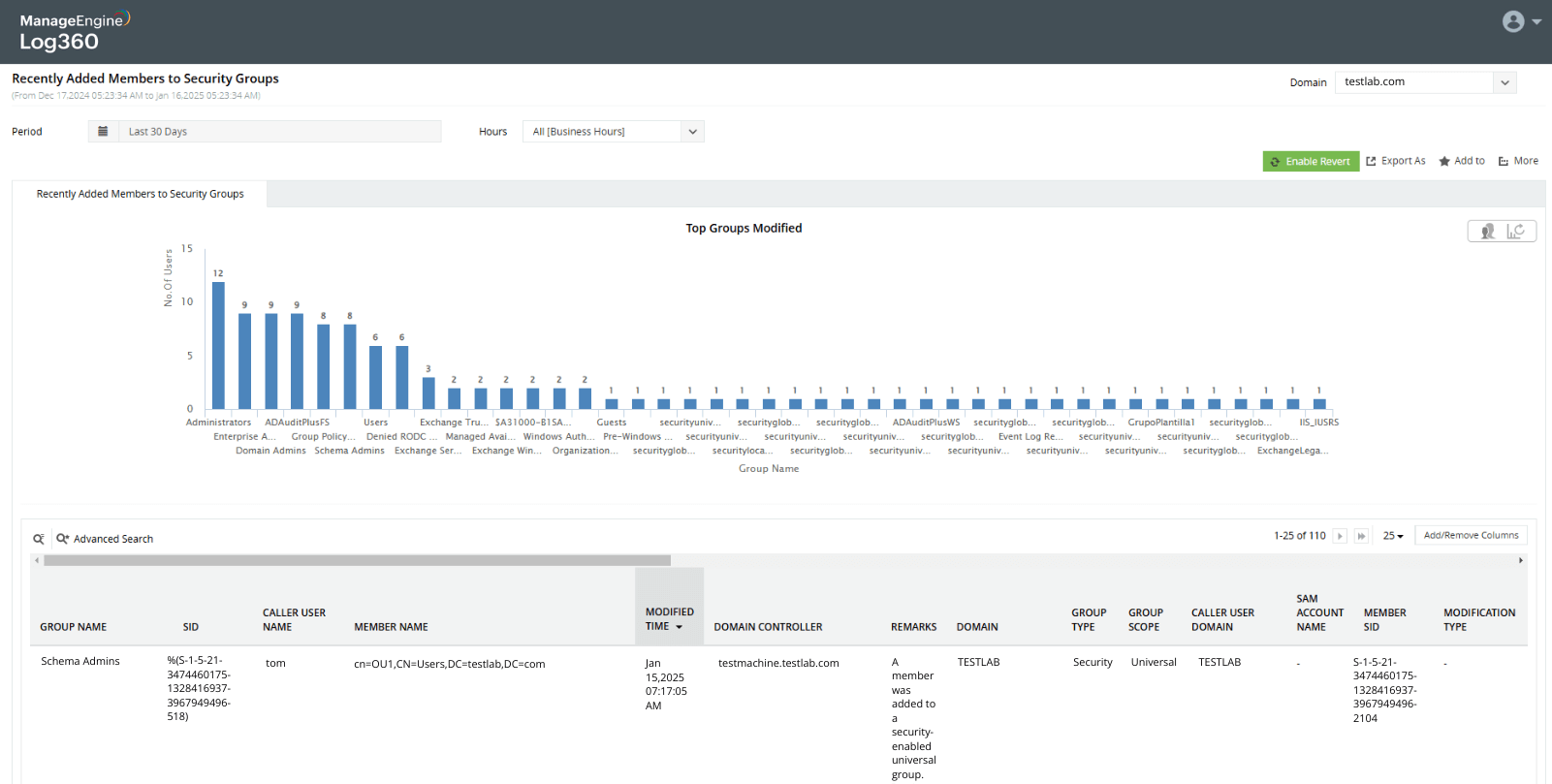
Backdooring users into privileged groups in Active Directory
Learn more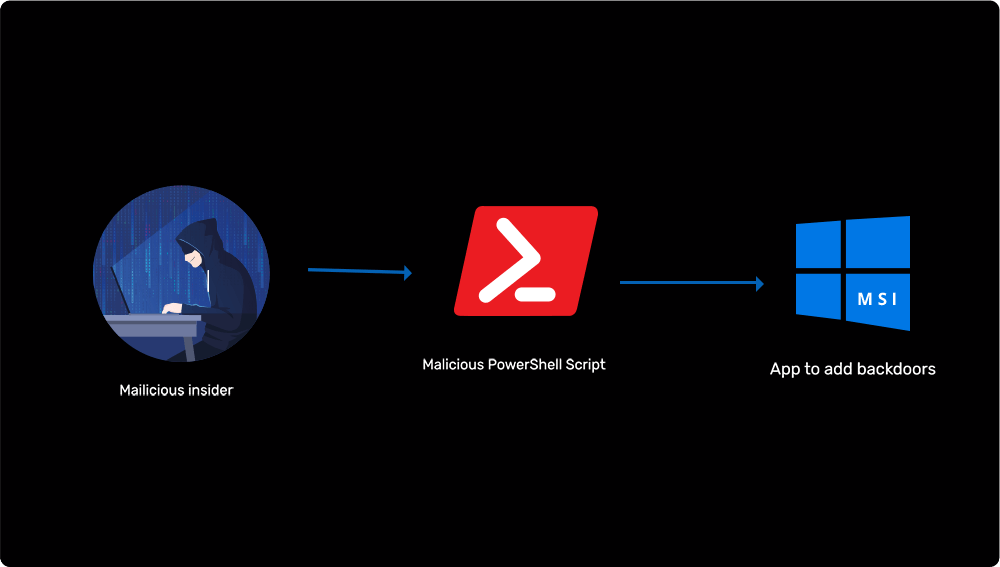
-
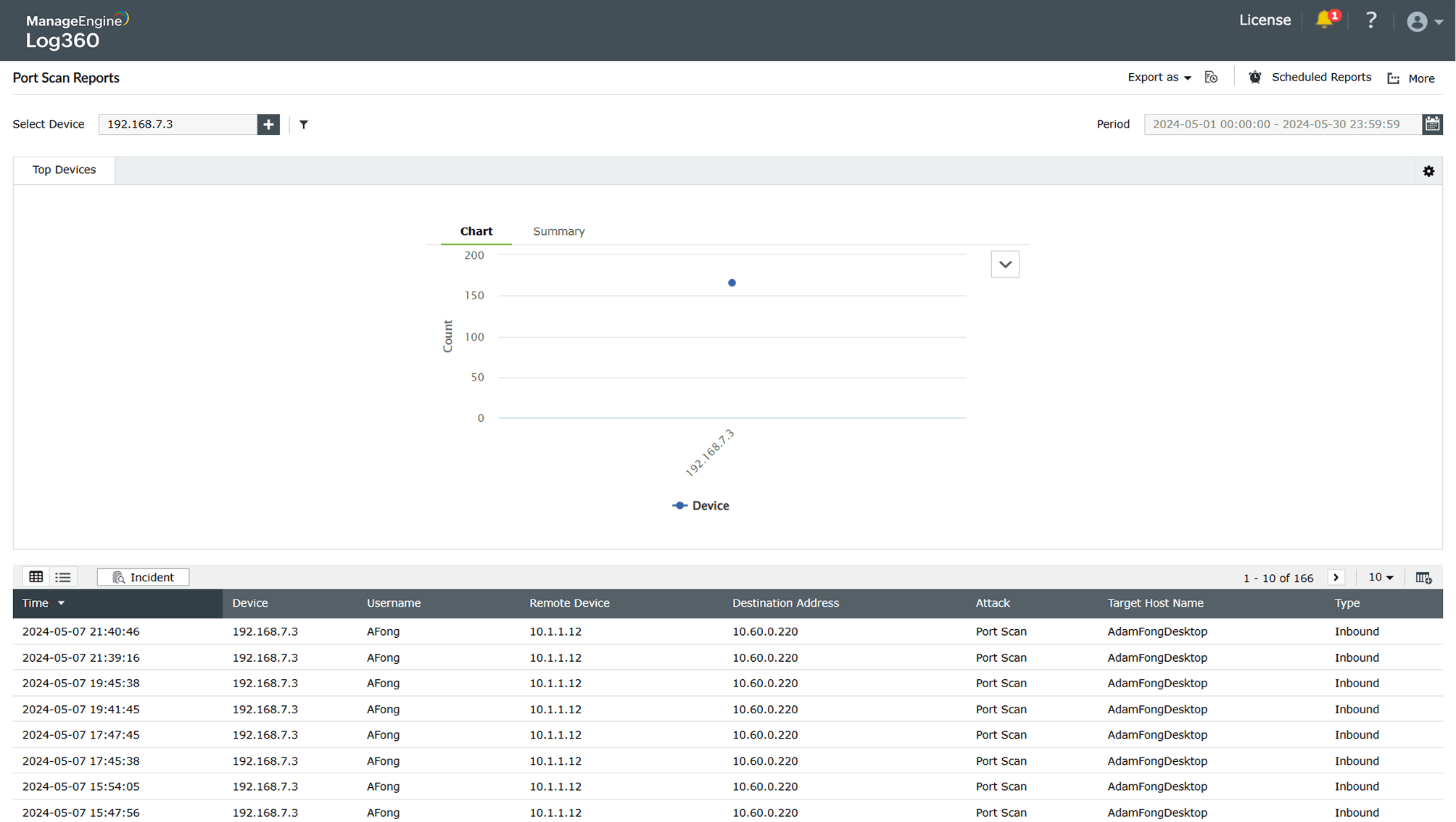
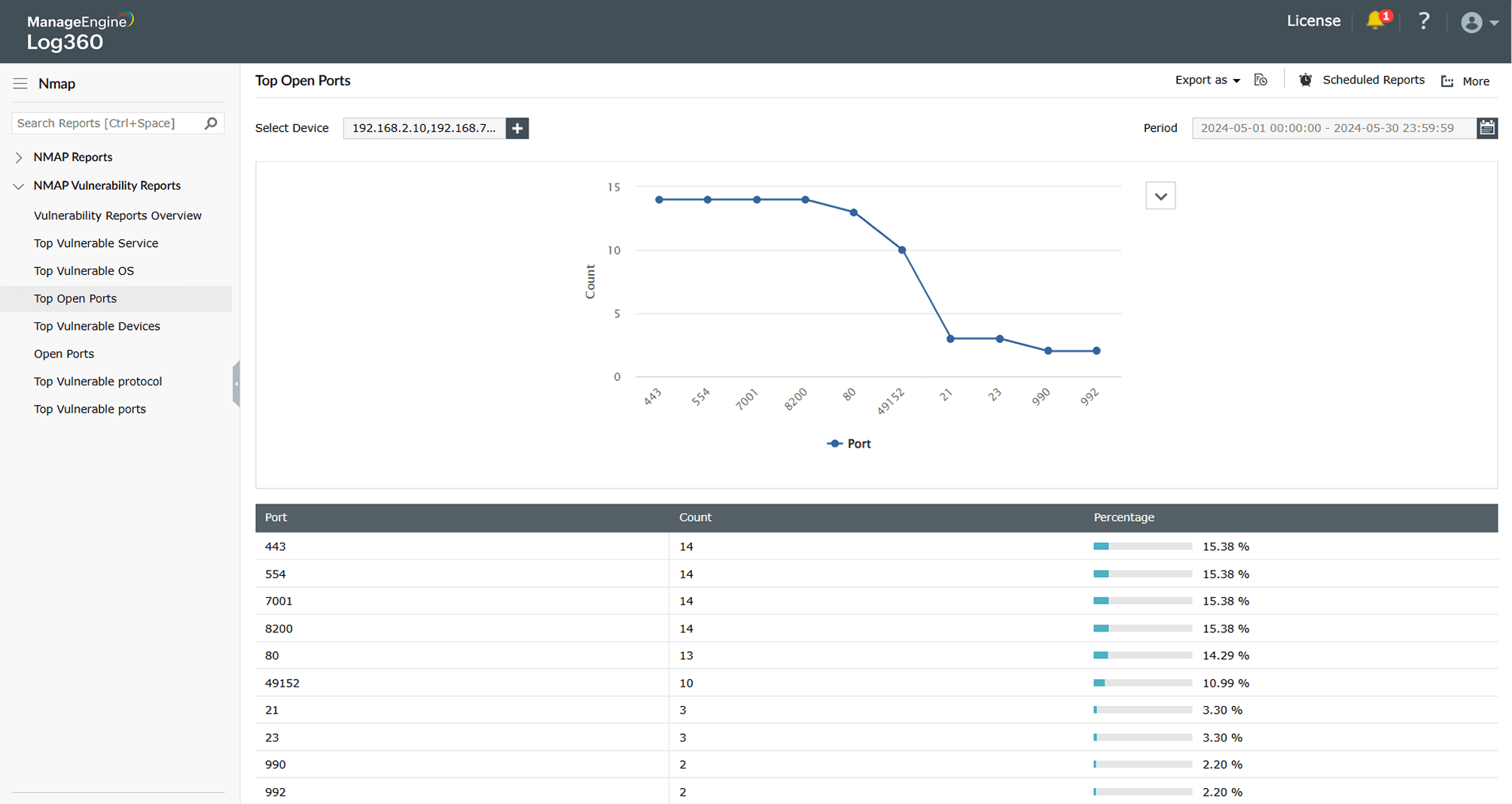
Reconnaissance to find open egress ports
Learn more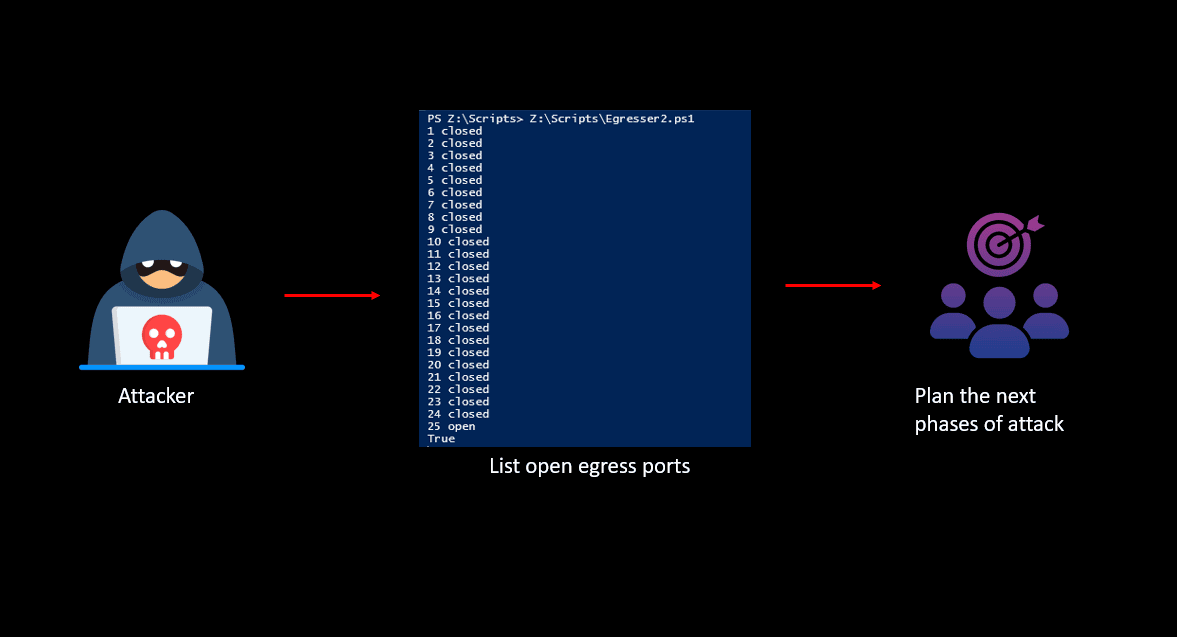
-
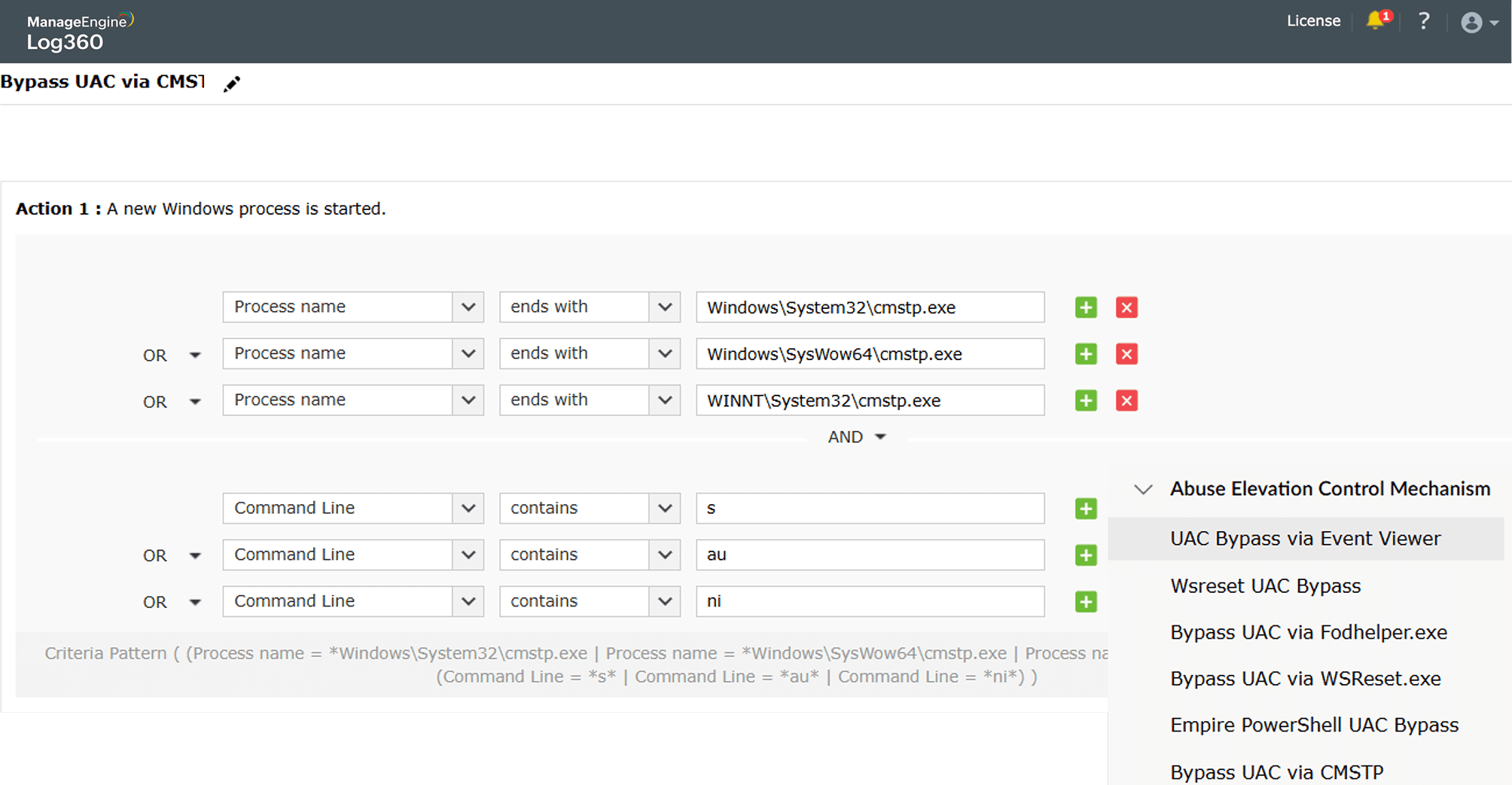
Bypass User Account Control (UAC)
Learn more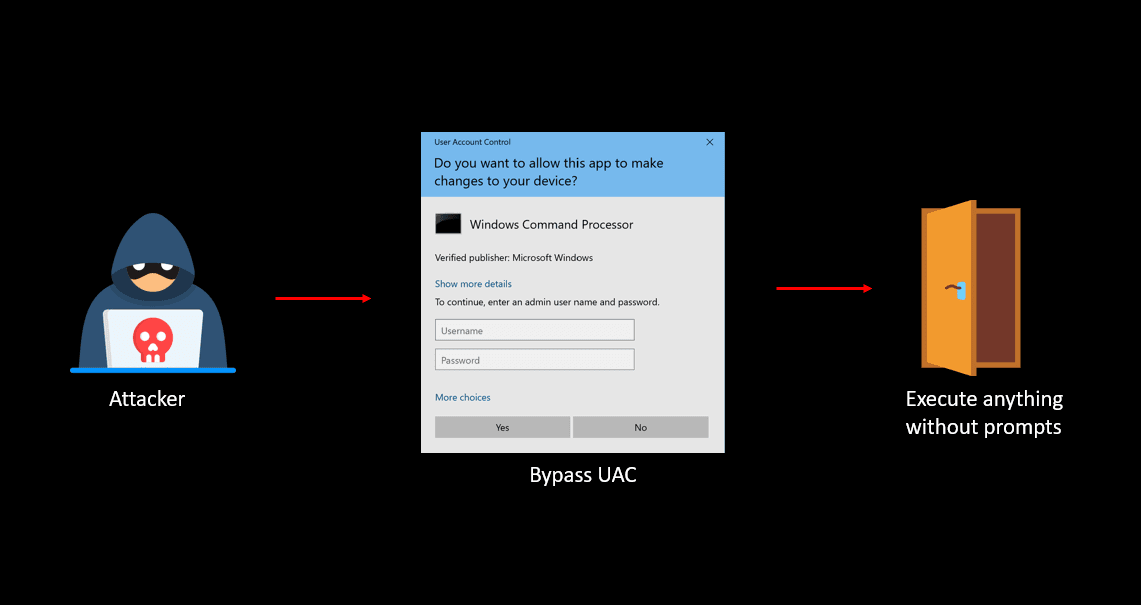
-
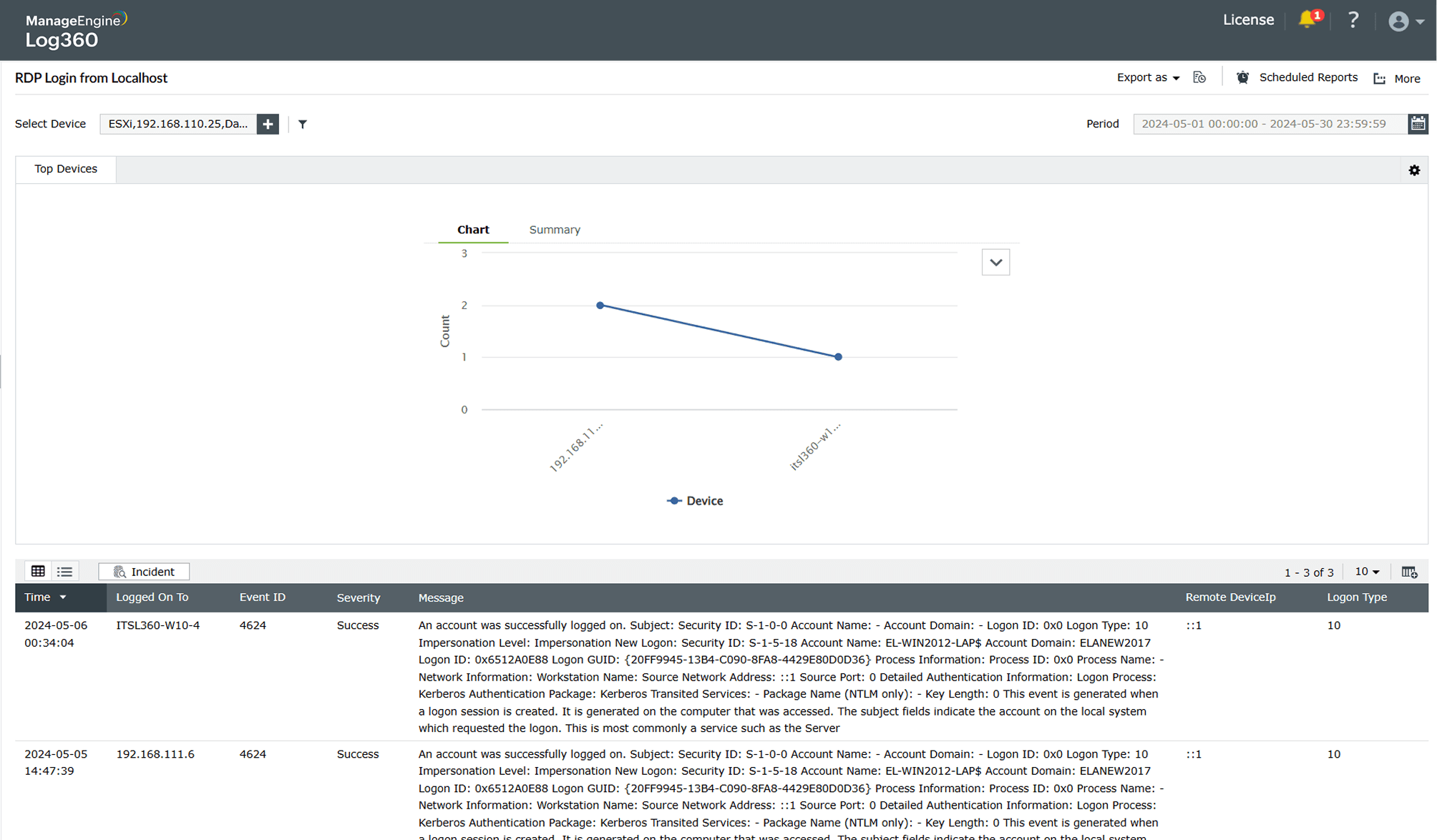
Enabling RDP on the target machine
Learn more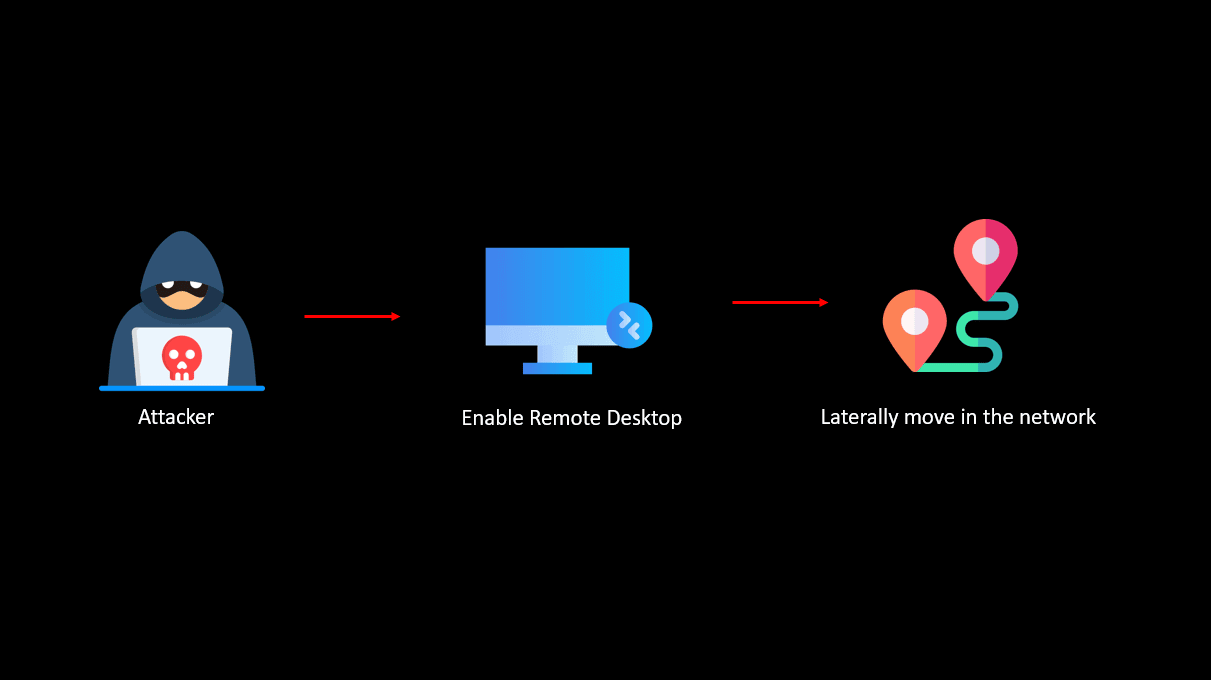
-
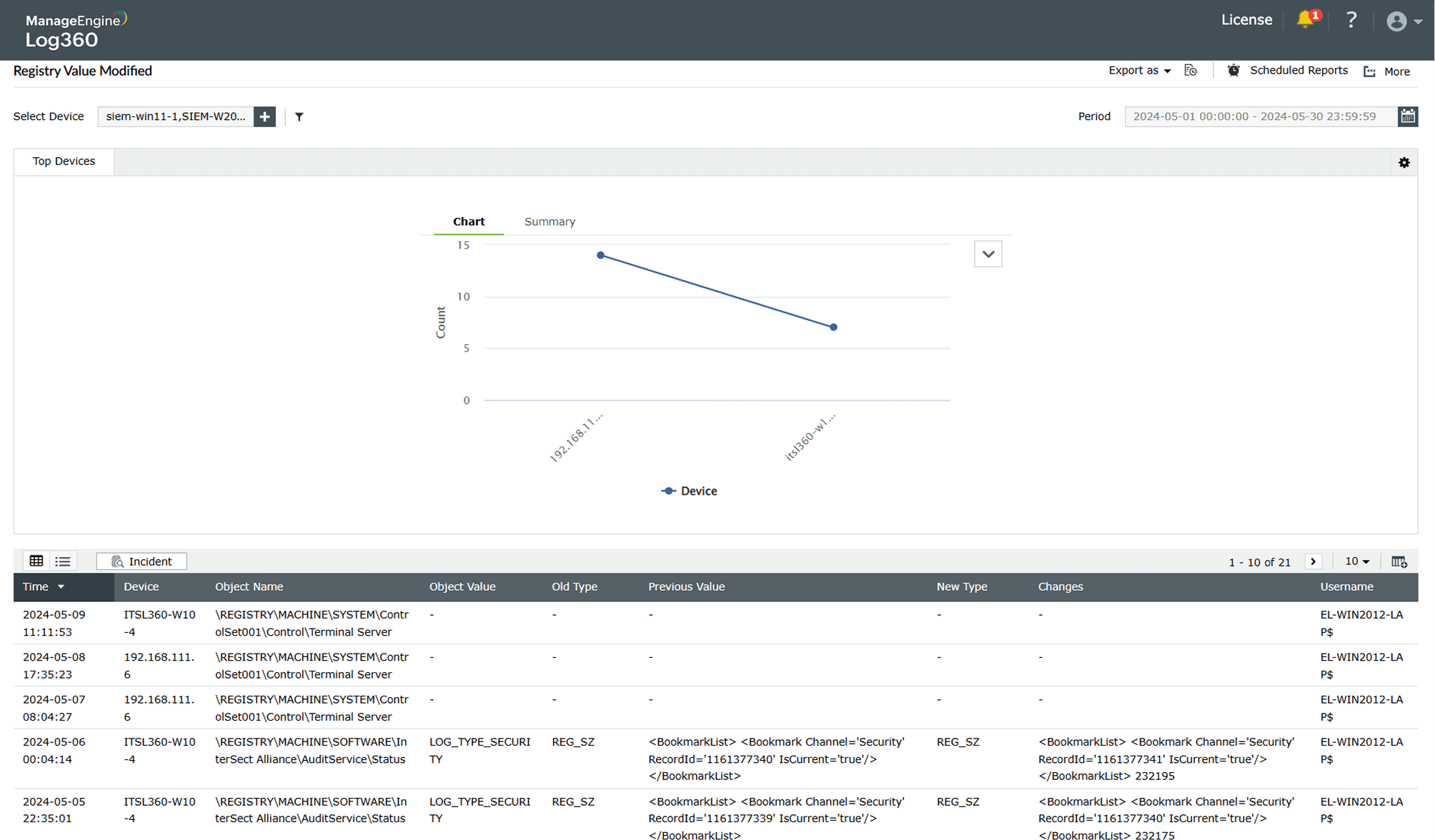
Persistence via registry key modification
Learn more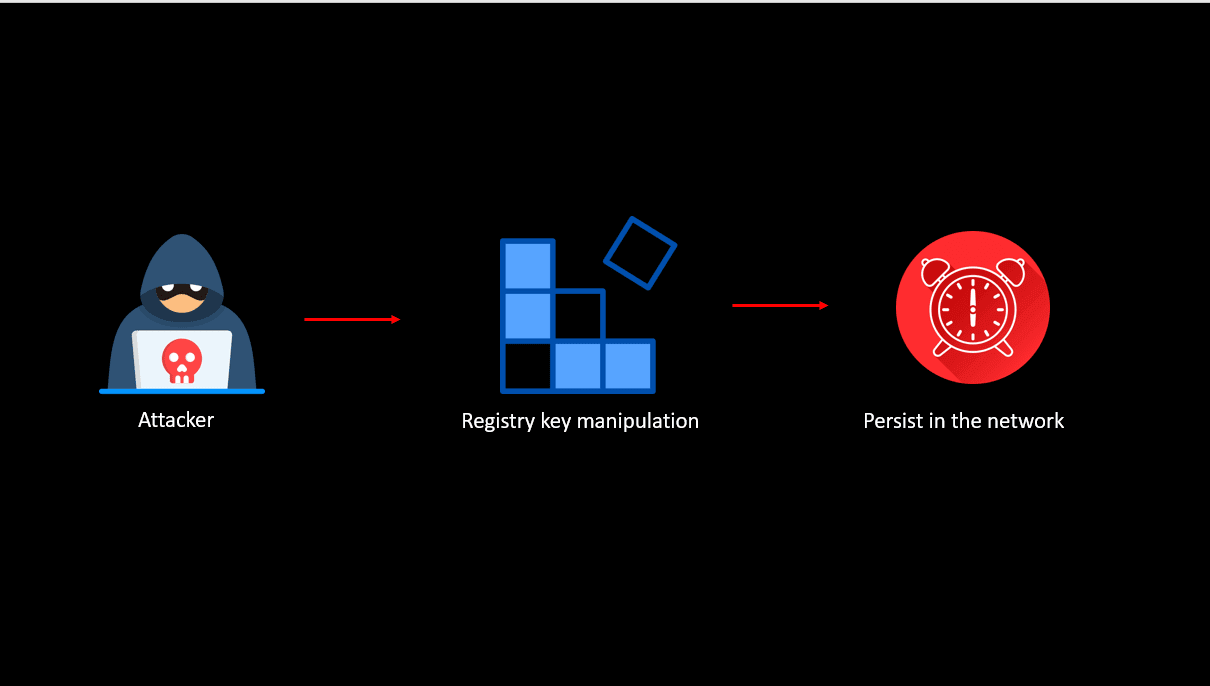
Virtual Sessions

Cloud and Windows data security

Zero access to domain in 40 minutes
Active Directory Security: Domain admin access before lunch

Password cracking techniques, how to protect against them

Choosing the right enterprise IAM strategy for AD and Azure AD
Securing the transition - Extending on-premise AD to AWS
Dangerous defaults that put your IT environment at risk

Everything you need to know to secure your Azure AD infrastructure
Mastering AD and Azure AD administration

Attacking AD and Azure AD environments

10 security vulnerabilities that excite hackers

Identity and Access Management: A prerequisite for security

Identifying security misconfigurations that can lead to breaches
Implementing a least privileged design for hybrid AD security

Active Directory Security Fundamentals

Hybrid IT essentials that you cant live without

Ten events you should audit in hybrid AD to prevent a breach

Embracing WFH, How to secure your remote workers from remote attacks
Core concepts of Azure AD - Demystifying identity governance

Improving security identity management for the hybrid cloud

The search for the perfect password, will it ever end?

Hardening password security across hybrid AD

Security hardening begins with a clean active directory

Combating snake ransomware: Detection and mitigation strategy

10 security vulnerabilities that excite hackers

Limit Active Directory attack radius with efficient management practices

Boost your IT productivity with secure password self-service

Unmonitored permissions and unchecked privileged access: An invitation to a security breach
Securing hybrid identities with 2FA and advanced password controls
Live Sessions
-
Blackhat asia 2025:
SingaporeYour Security Settings Are Talking—Are You Listening?
Many breaches stemmed from misconfigurations that enabled lateral movement. The session showed how attackers used built-in tools like PowerShell to stay hidden.
-
Tech Week 2024:
SingaporeCybersecurity essentials for securing your hybrid organizations 2024
The session focused on cybersecurity essentials for securing hybrid environments. It highlighted unified IAM, continuous monitoring, and Zero Trust as key pillars.
-
Convenzis UK - NHS 2025
SingaporeFireside chat
This panel explored security visibility and employee awareness in the healthcare sector. Discussions covered legacy risks, emerging tech, and threats like RaaS and supply chain attacks.
-
IDC, CSO & ManageEngine Executive Event 2025
SingaporeSecurity keynote
The session covered identity management challenges in hybrid UK environments. It stressed the shift toward unified platforms over siloed IAM and PAM tools to reduce risk.
-
GovWare Conference and Exhibition 2024
SingaporeAt GovWare Singapore, I discussed how detection engineering, SIEM, and IAM strengthen government cybersecurity. Tailored detections and strict access controls were key to enabling Zero Trust and visibility.
-
Blackhat MEA - Malham 2024
Riyadh, Saudi ArabiaI connected with cybersecurity professionals to discuss real-world threats and showcase ManageEngine’s SIEM. Mini-theatre sessions and hands-on POCs highlighted our detection engineering capabilities.
-
6D Security AI - CISO roundtable 2025
Sydney, AustraliaModernising Security @ the Core – the Next Cyber Frontier
At a Sydney roundtable, I discussed identity sprawl, tool fatigue, and the limits of MFA. We explored how AI and smart frameworks enhance Zero Trust and resilience.
-
Attack flow
-
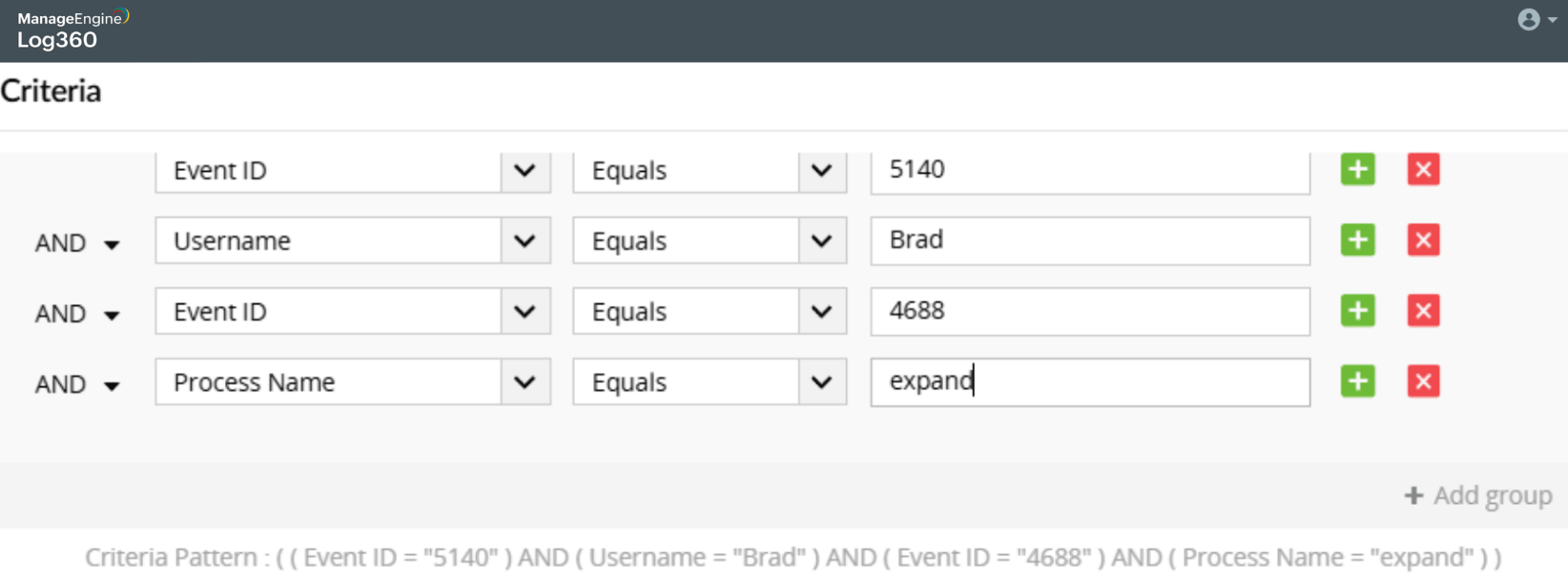
Technical attack
-
Solution
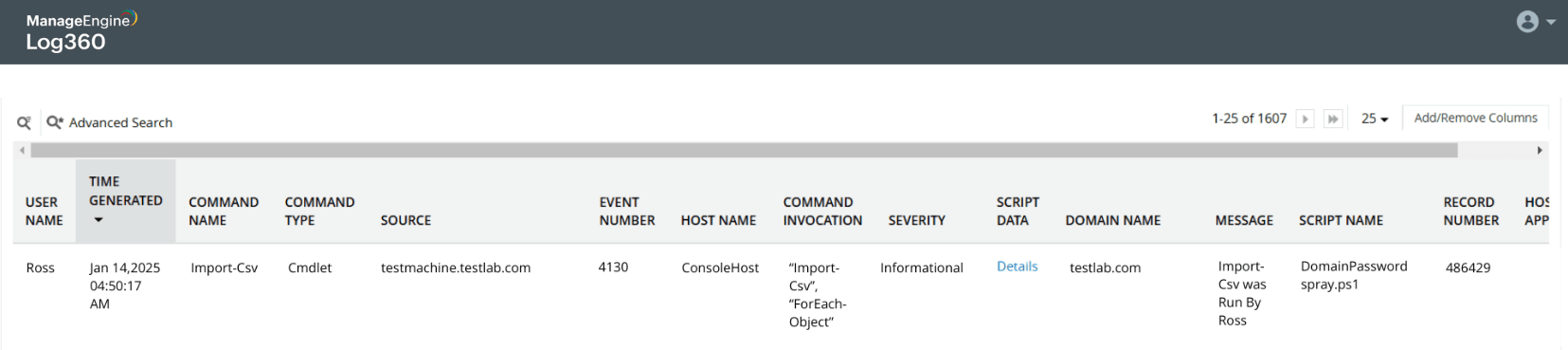
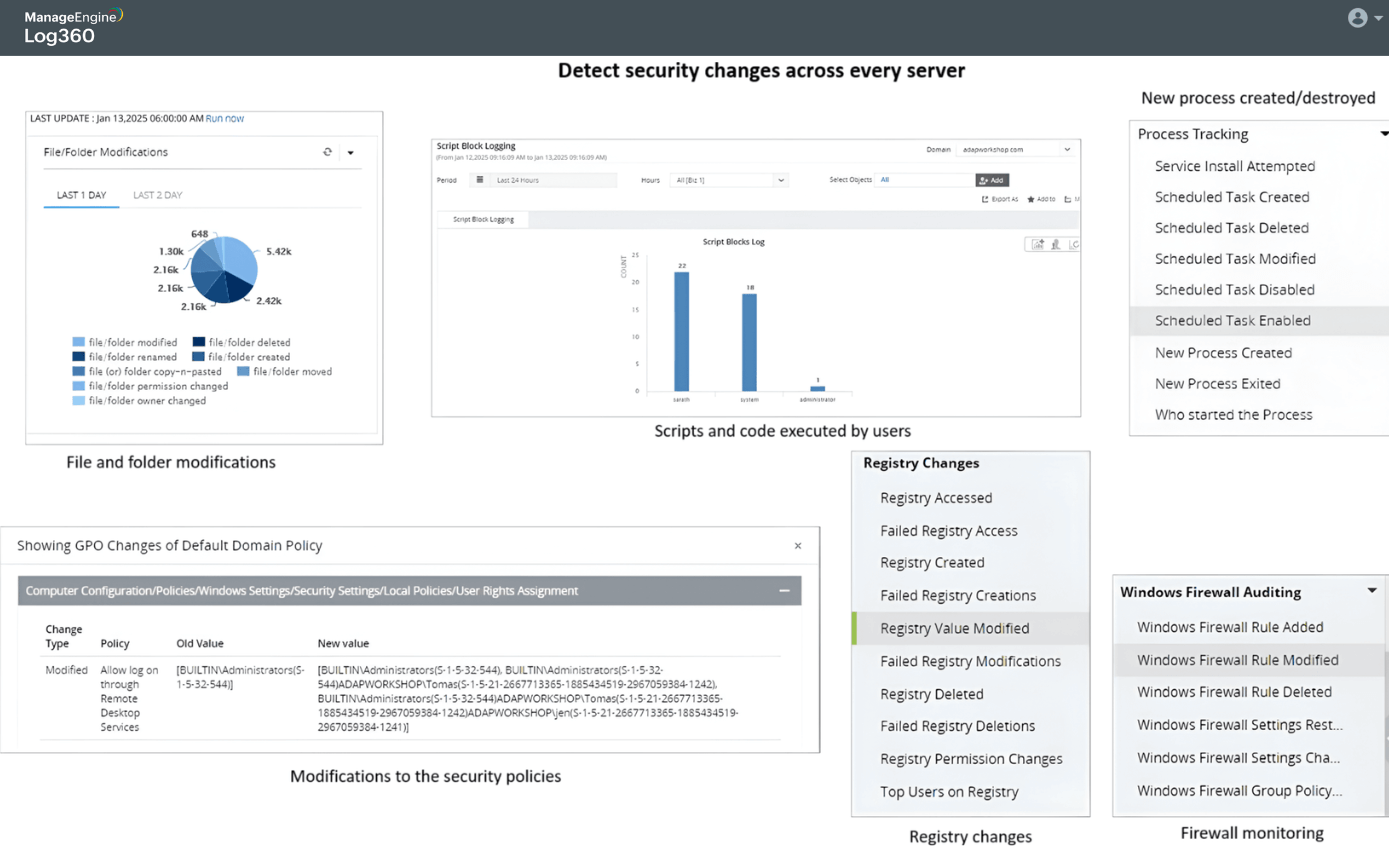
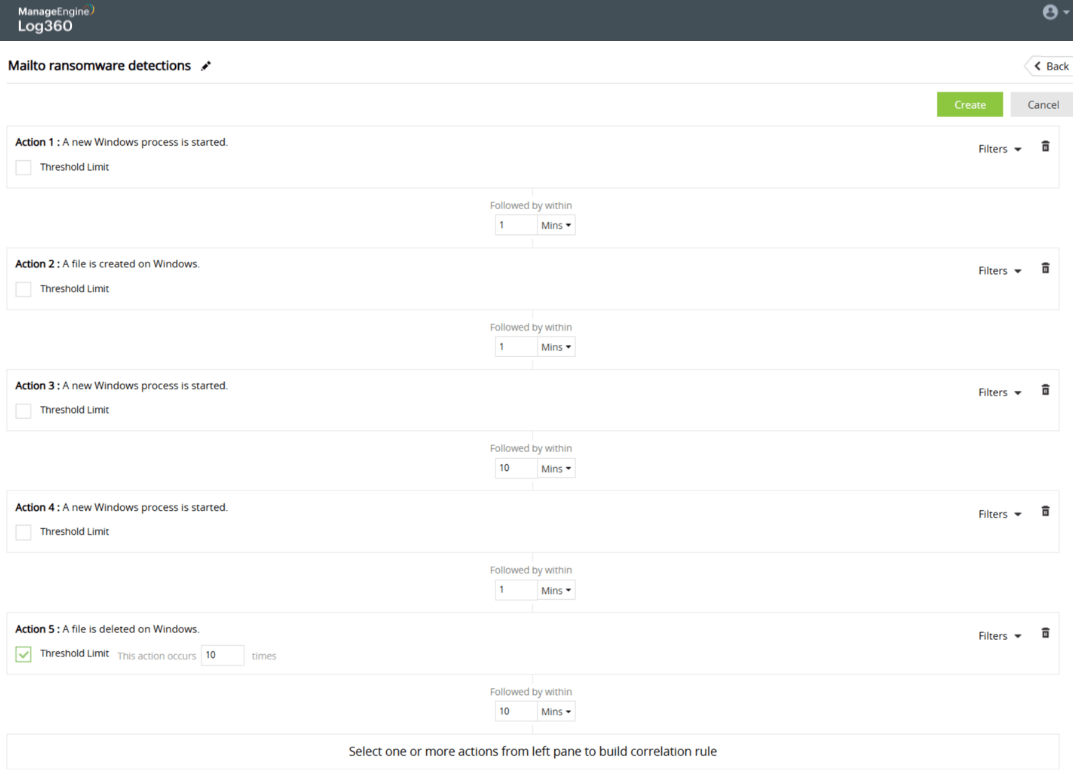
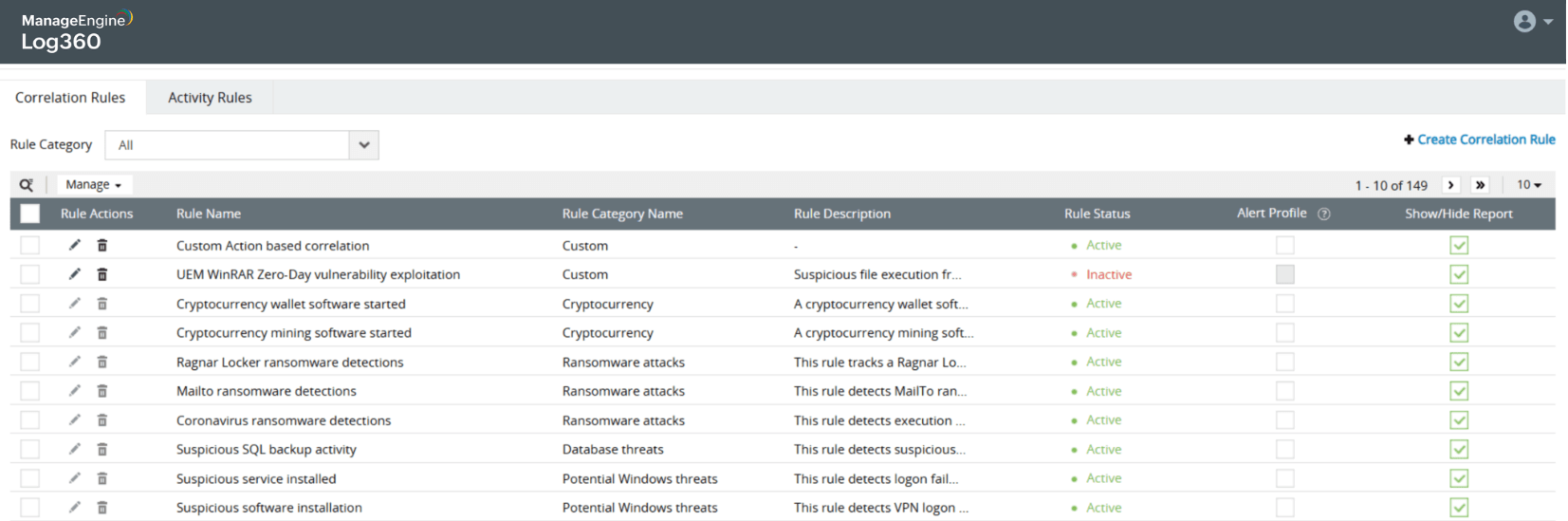
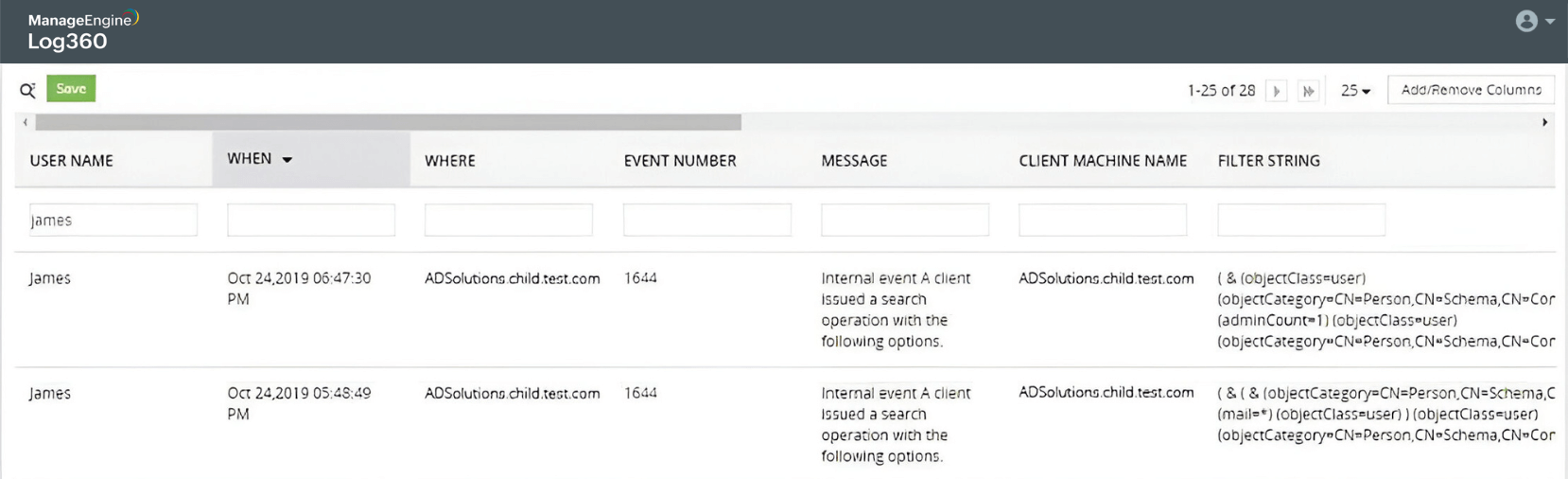
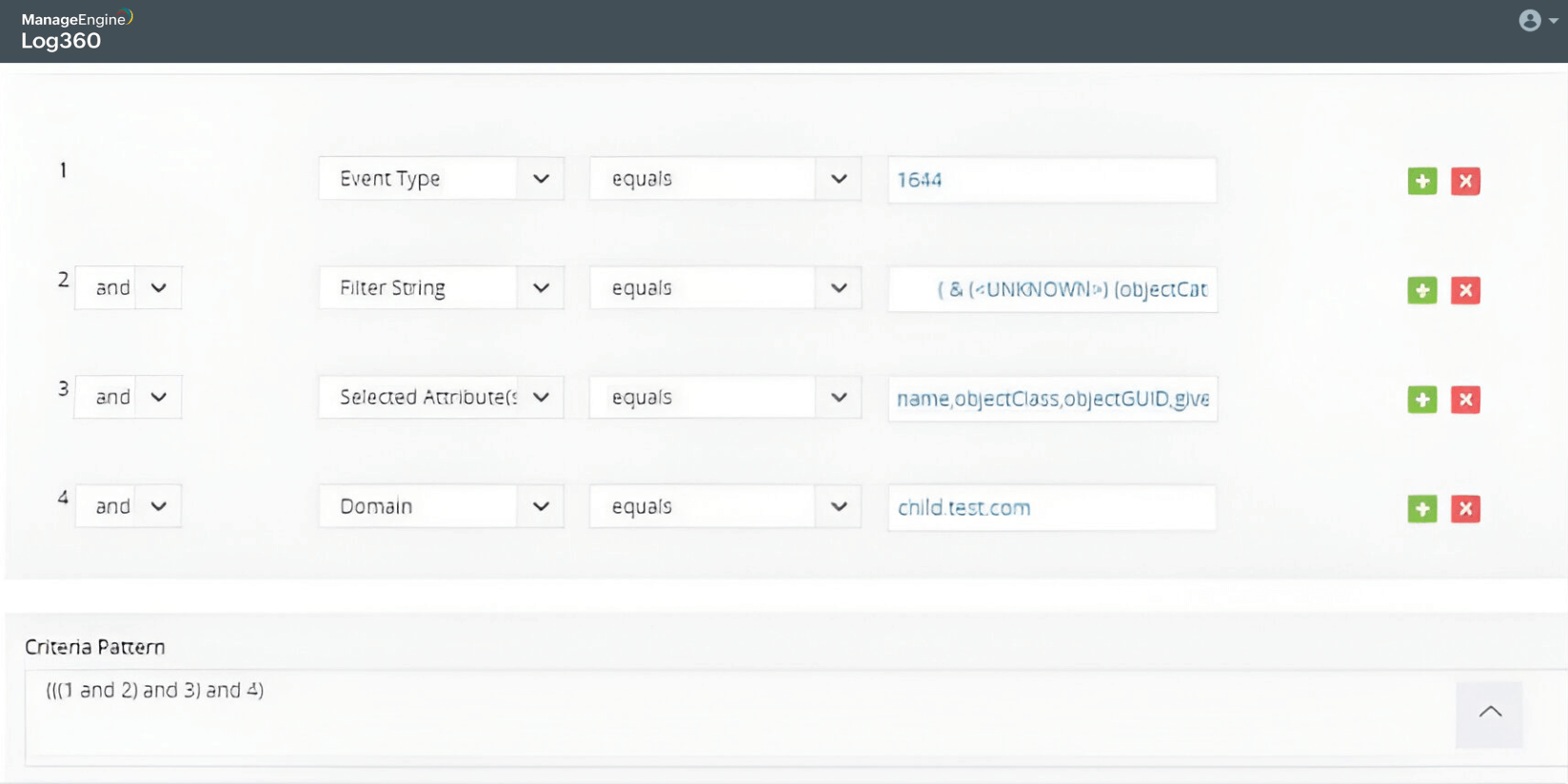
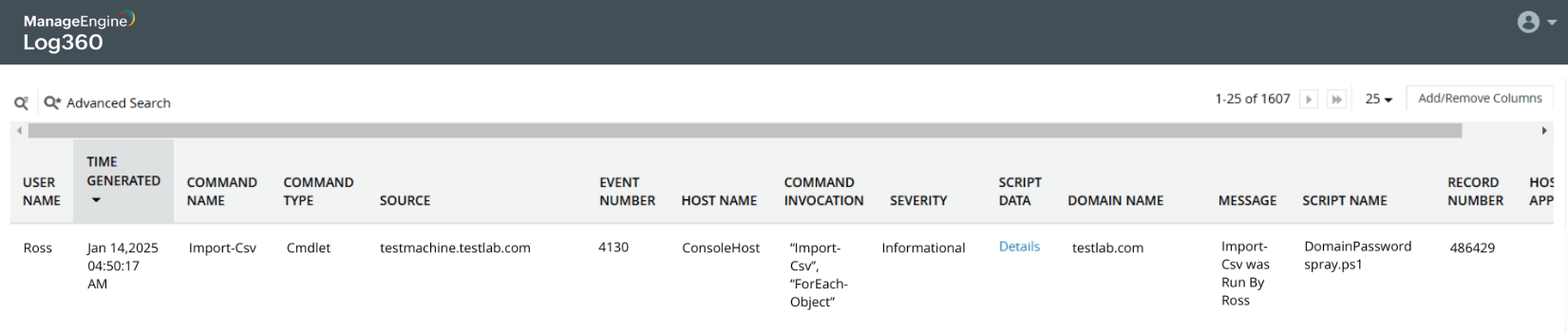
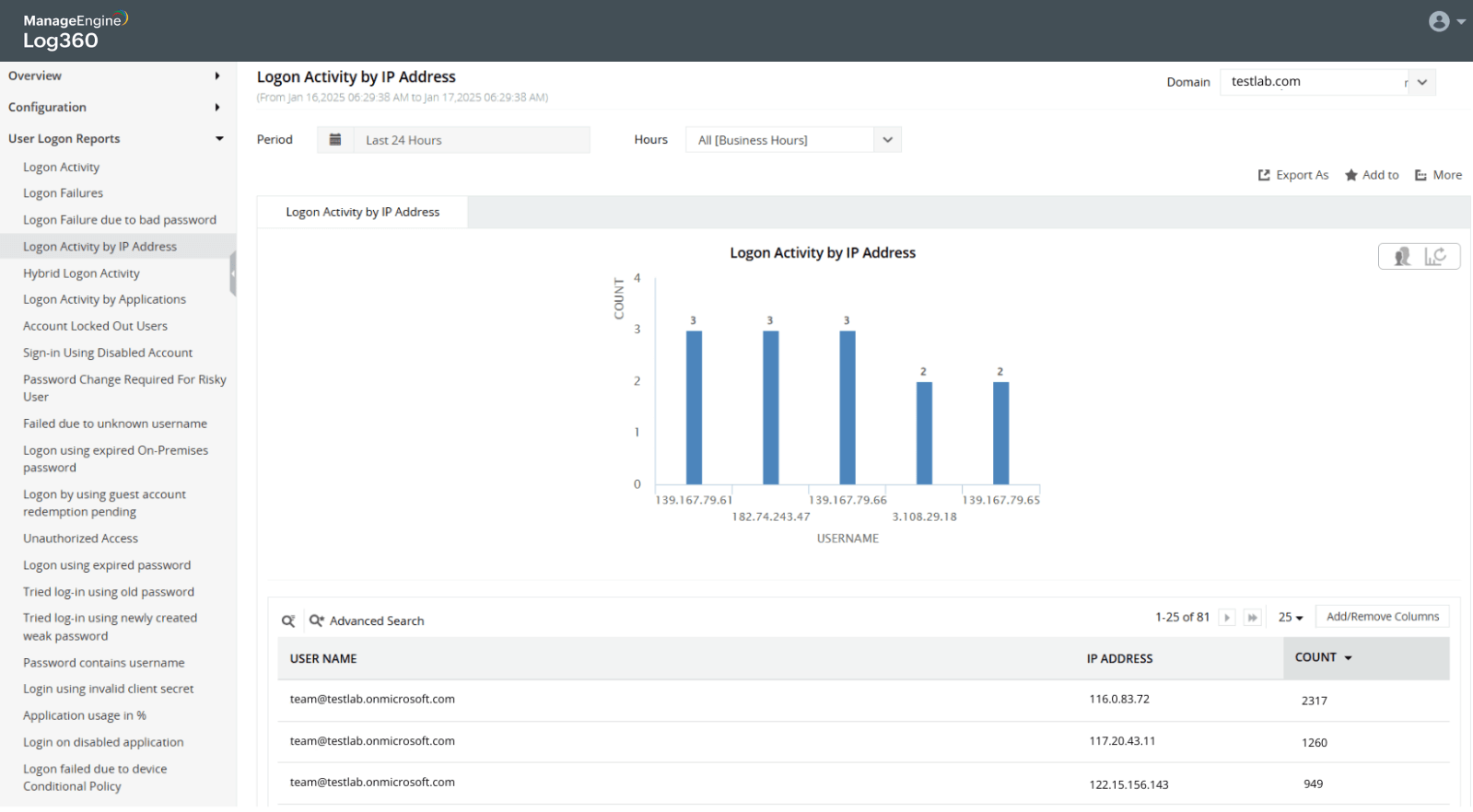
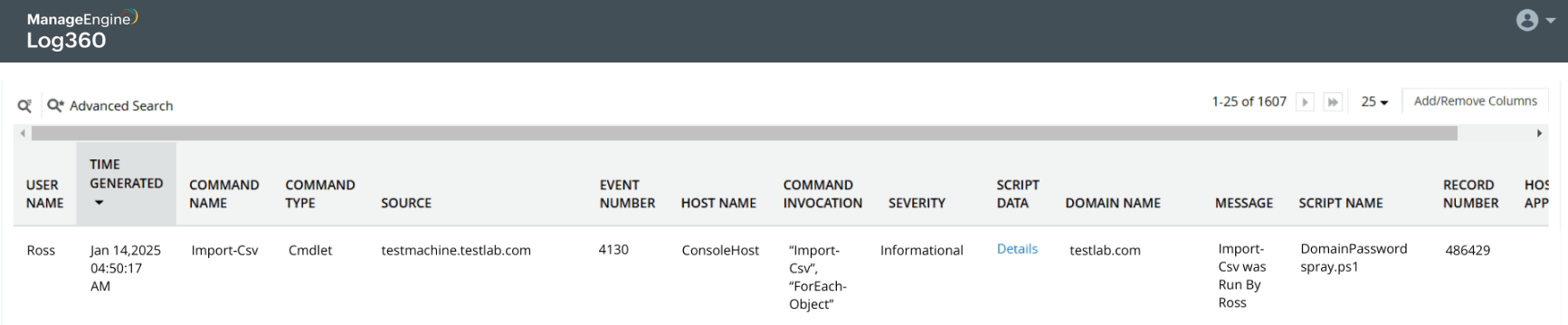
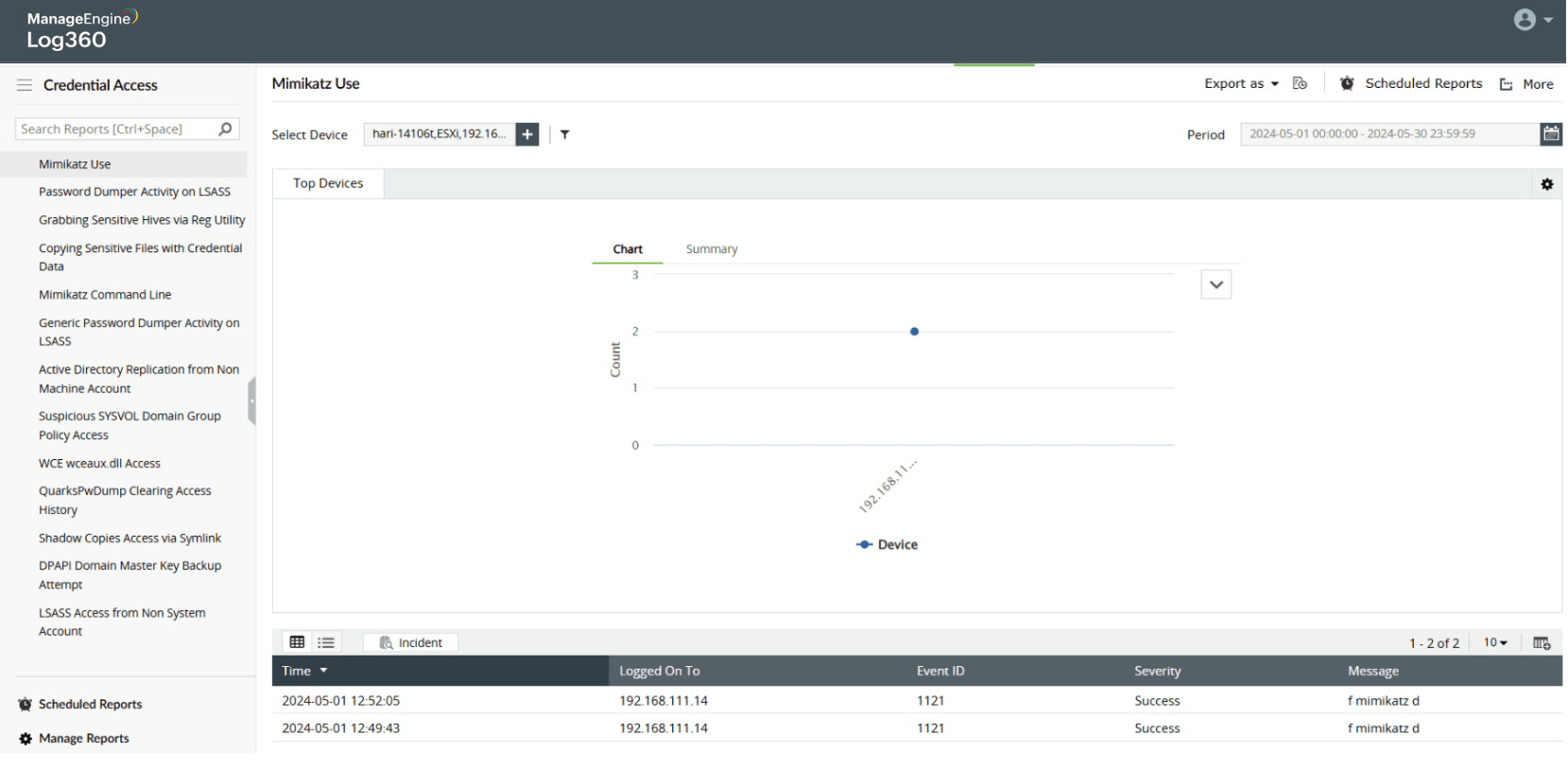
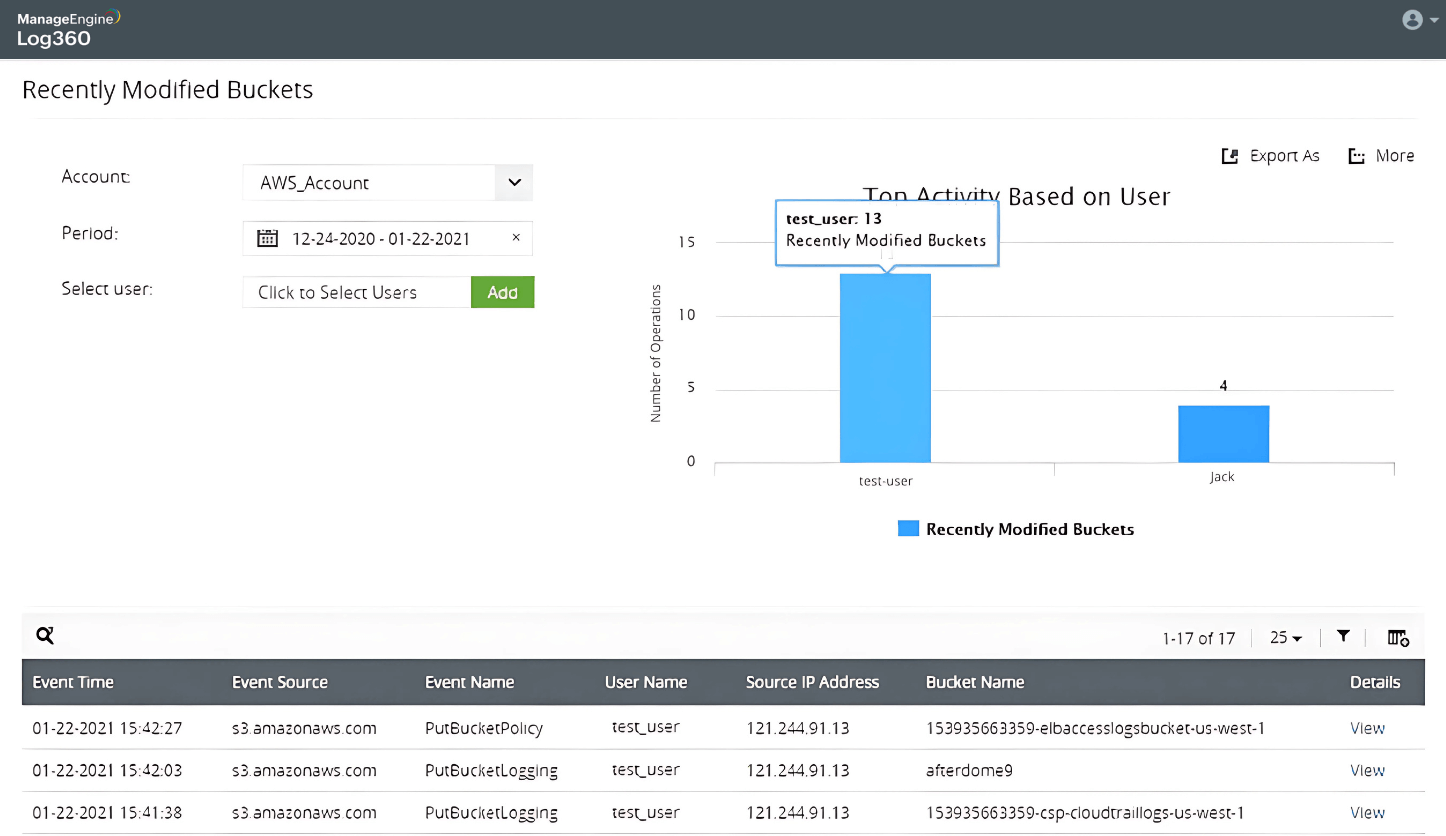
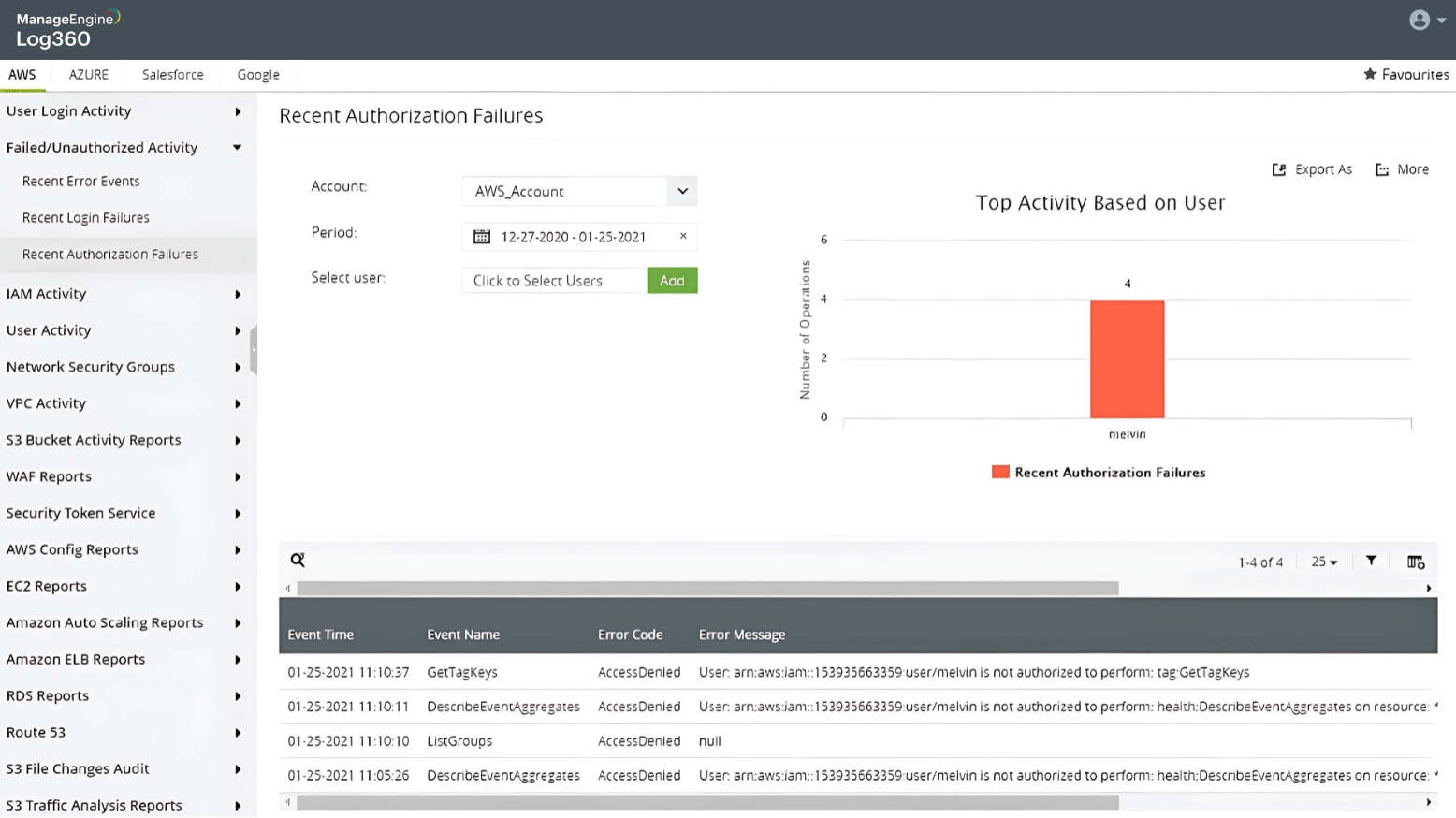
Password spray attack on Active Directory users

Password spray attack on Active Directory users
Password spray attack on Active Directory users
Explore real-world stories where Red sets the trap and Blue turns the tables.
Zoho Corporation Pvt. Ltd. All rights reserved