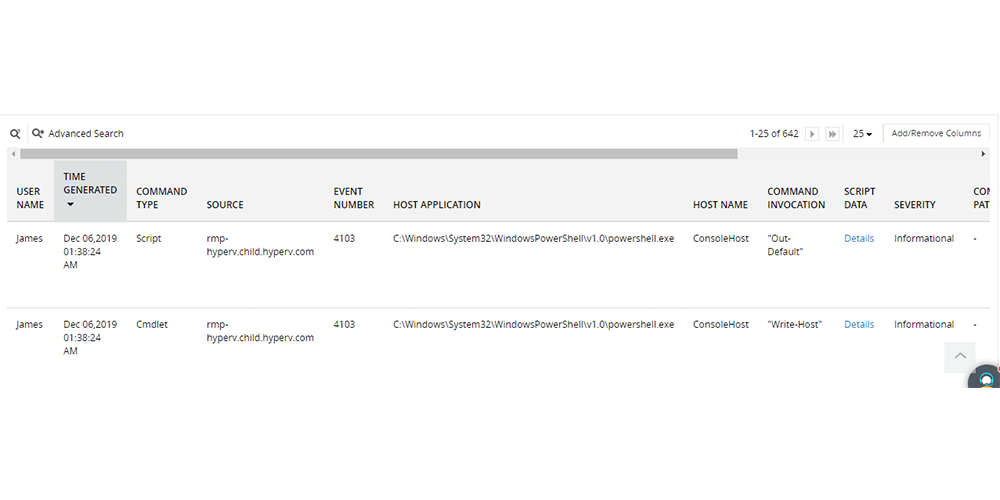
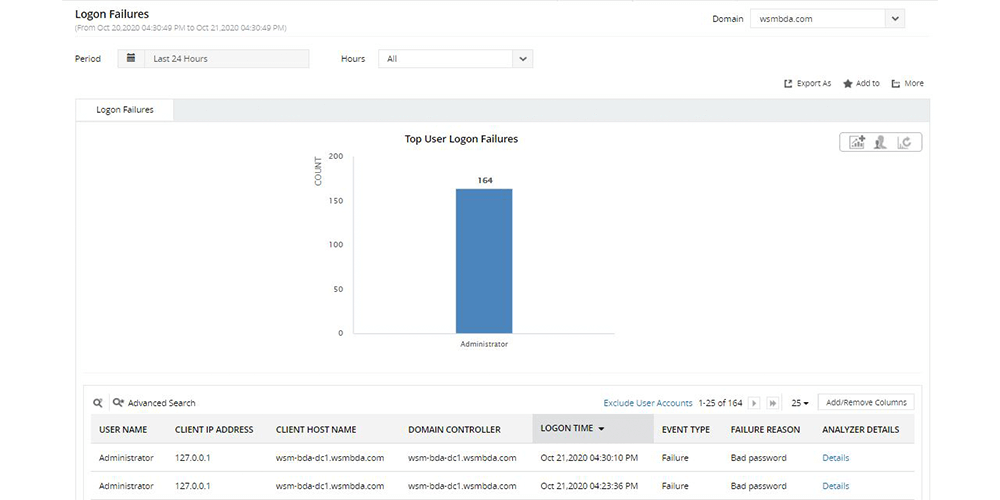
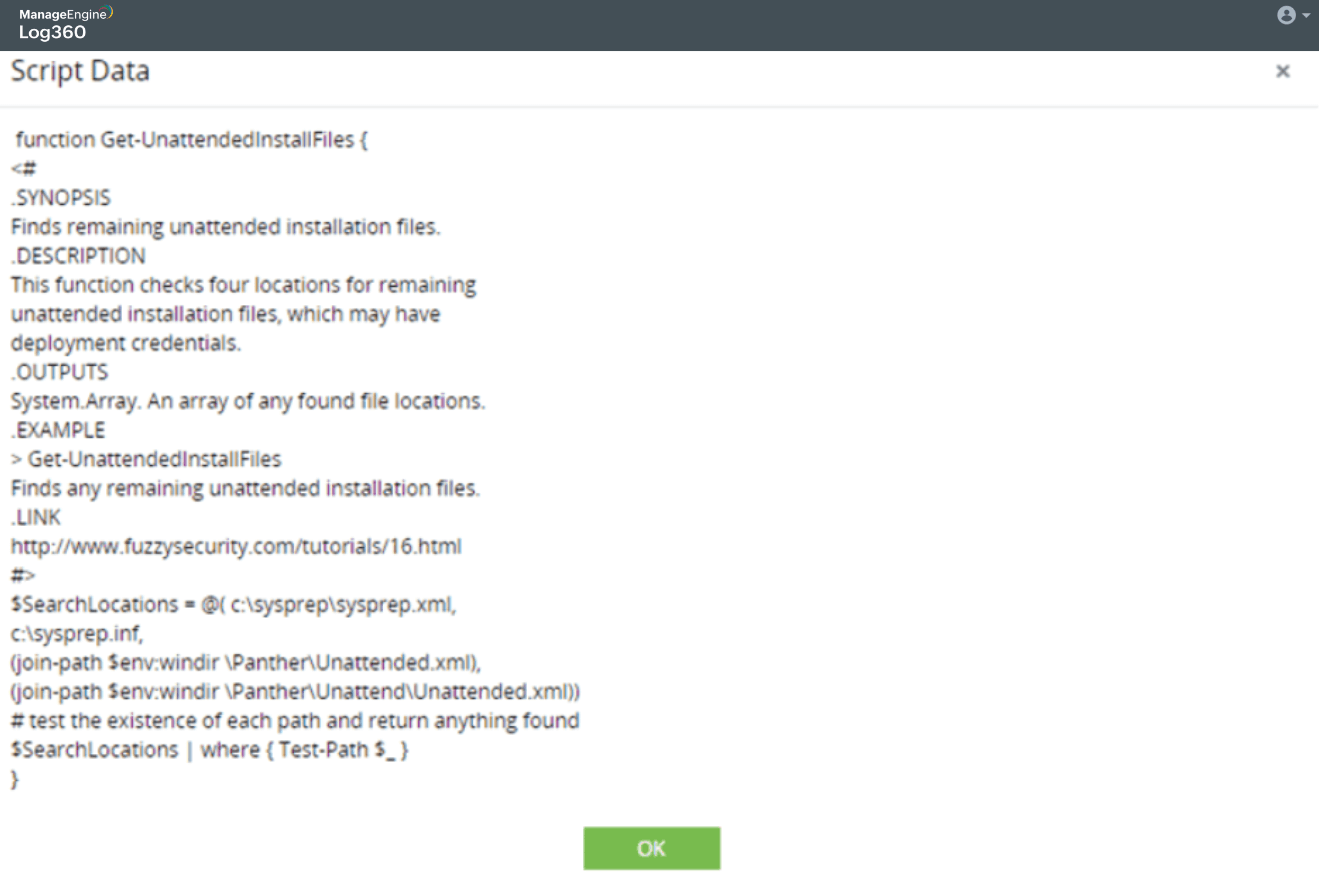
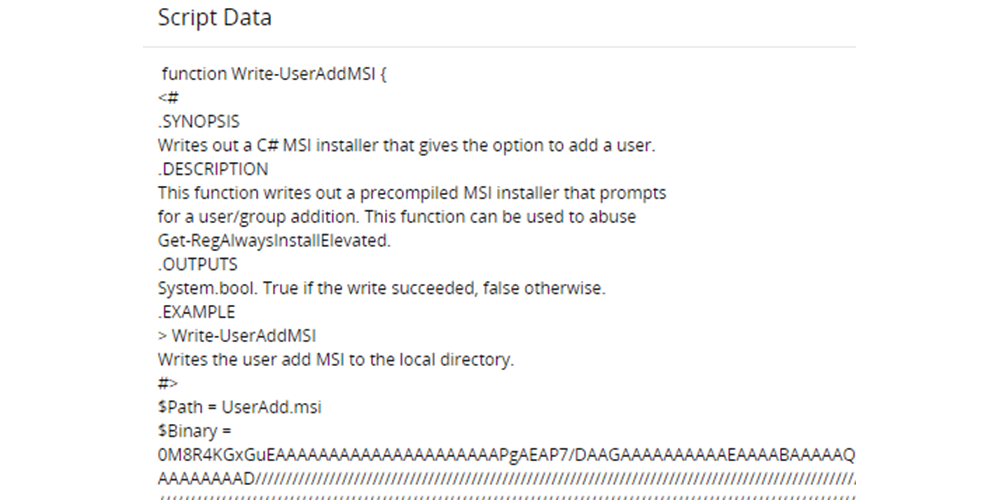
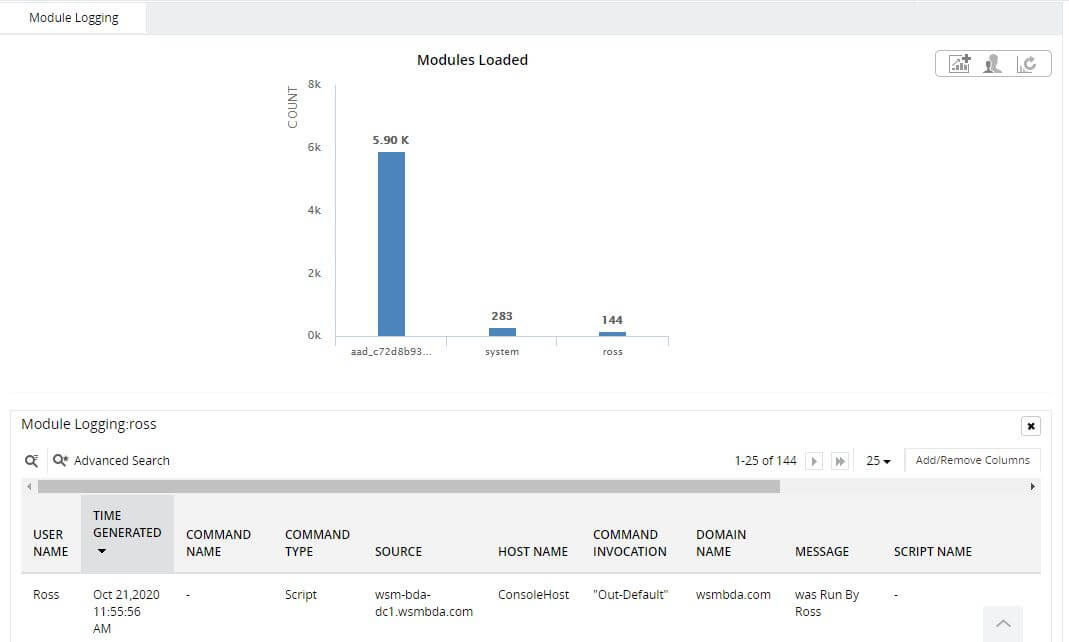
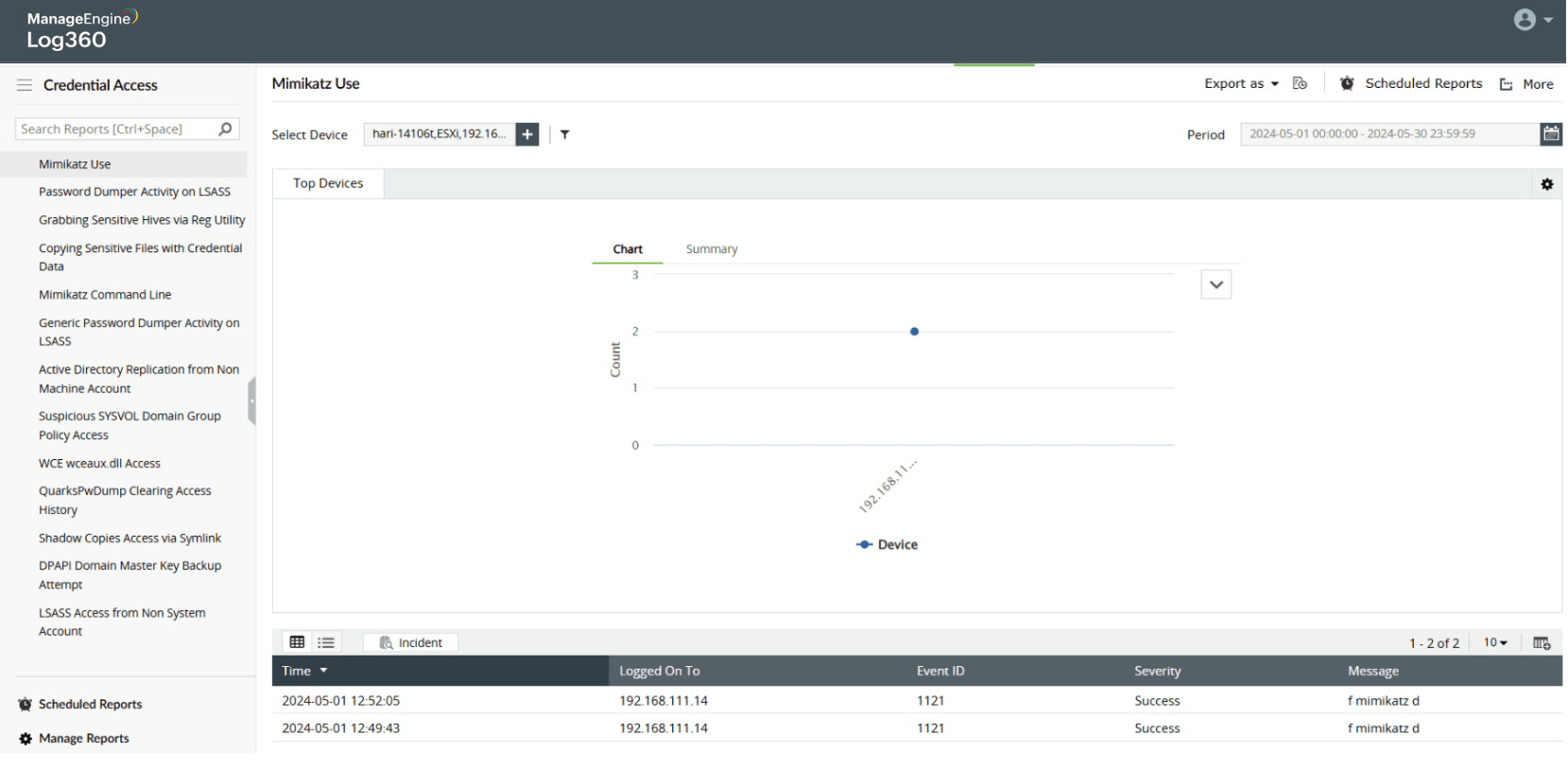
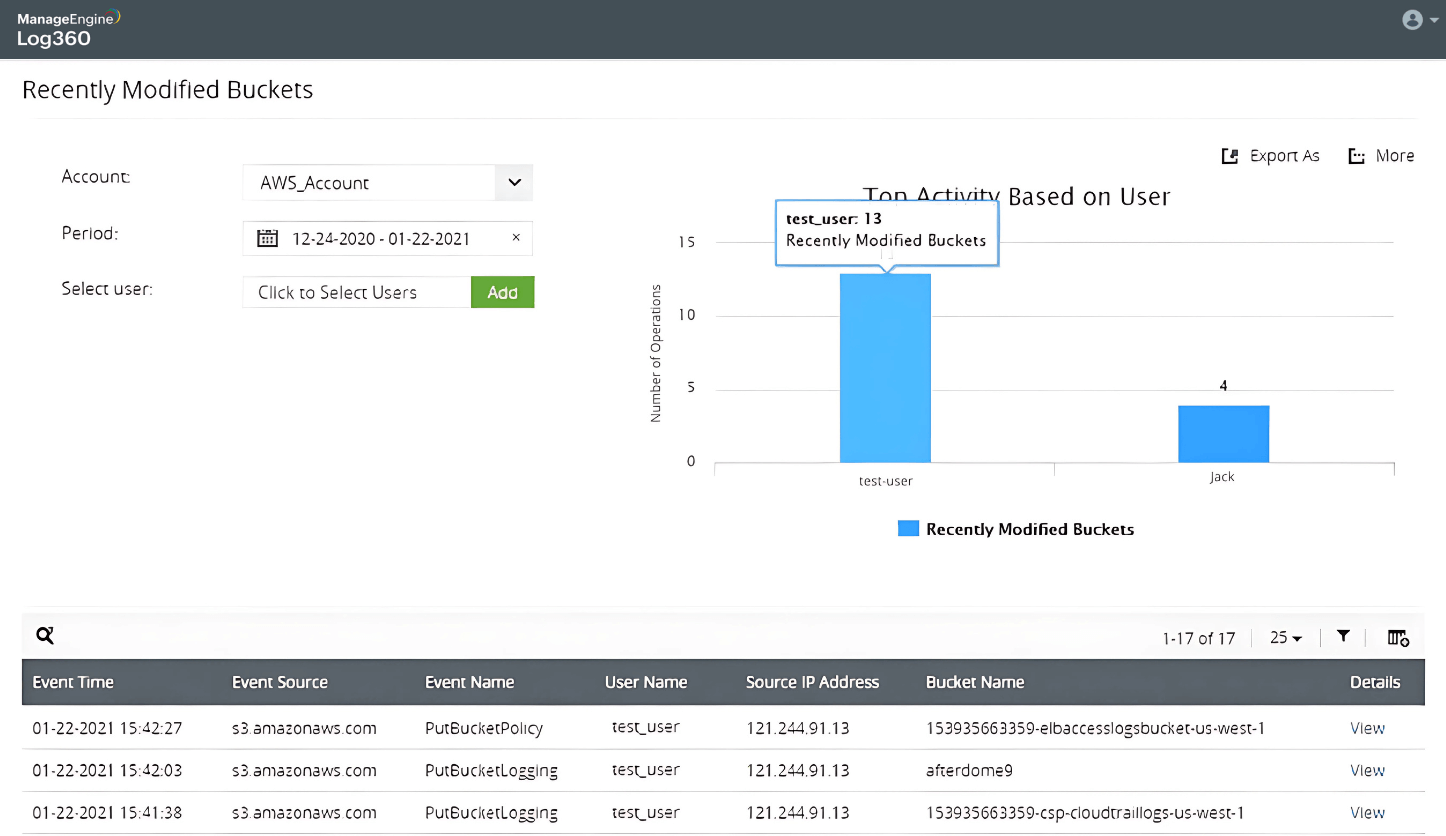
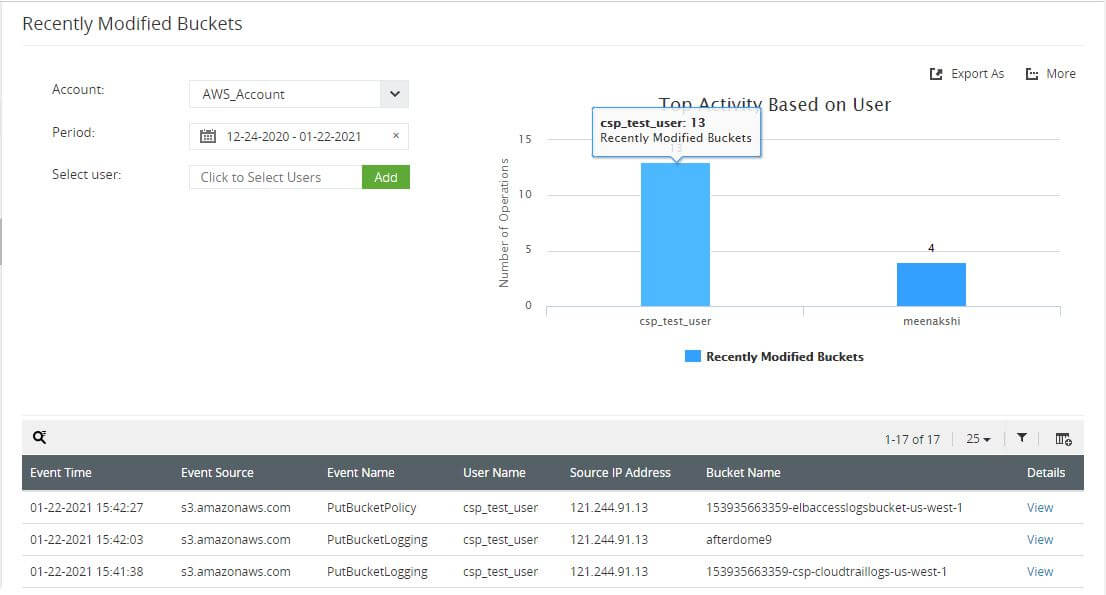
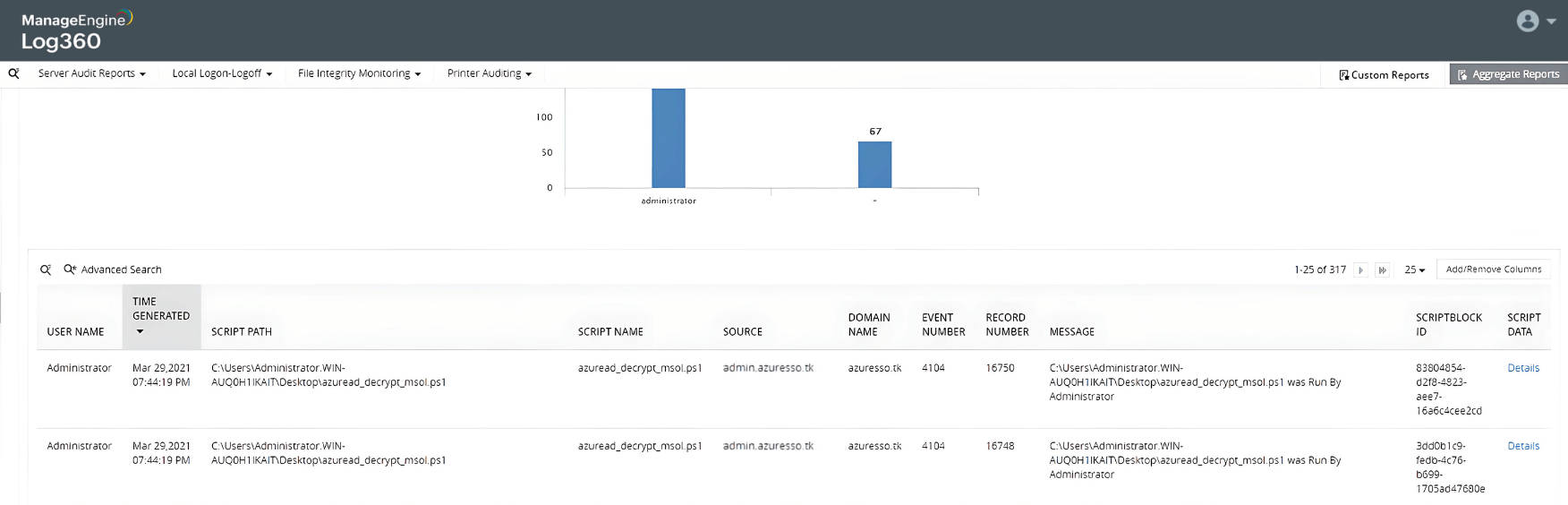
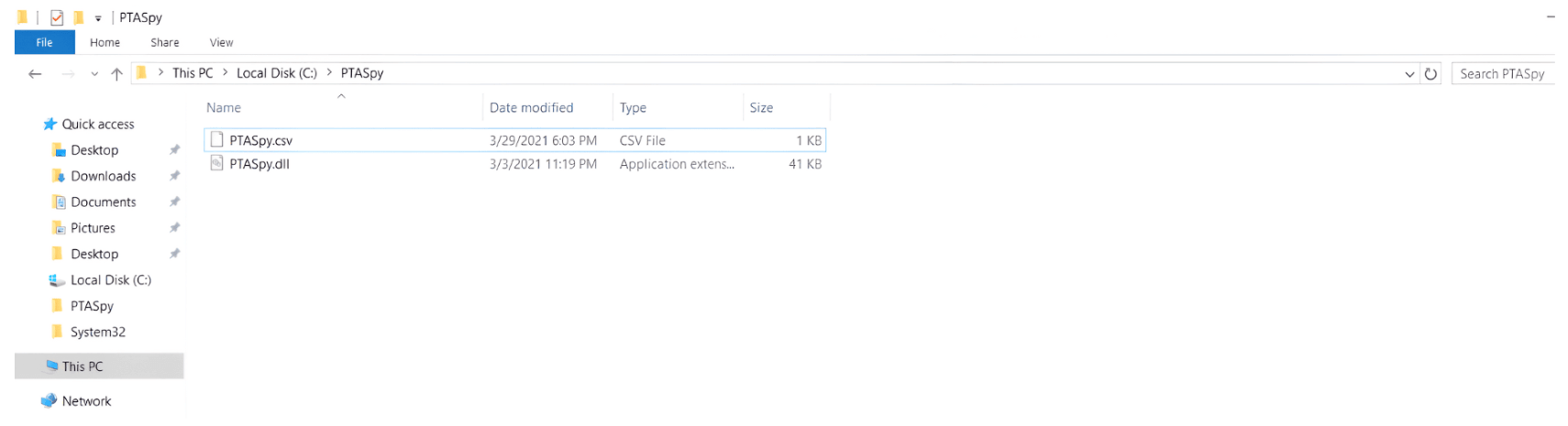
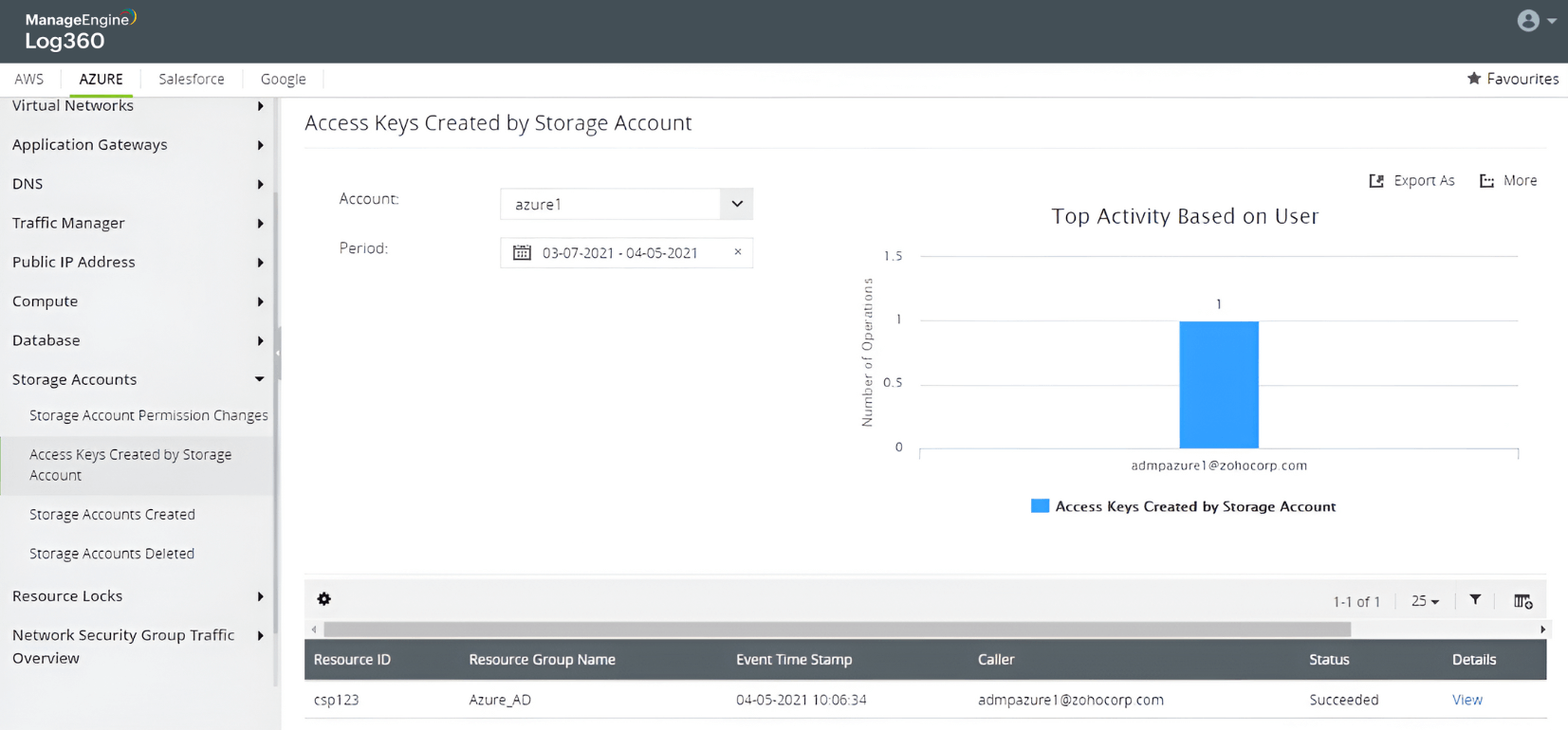
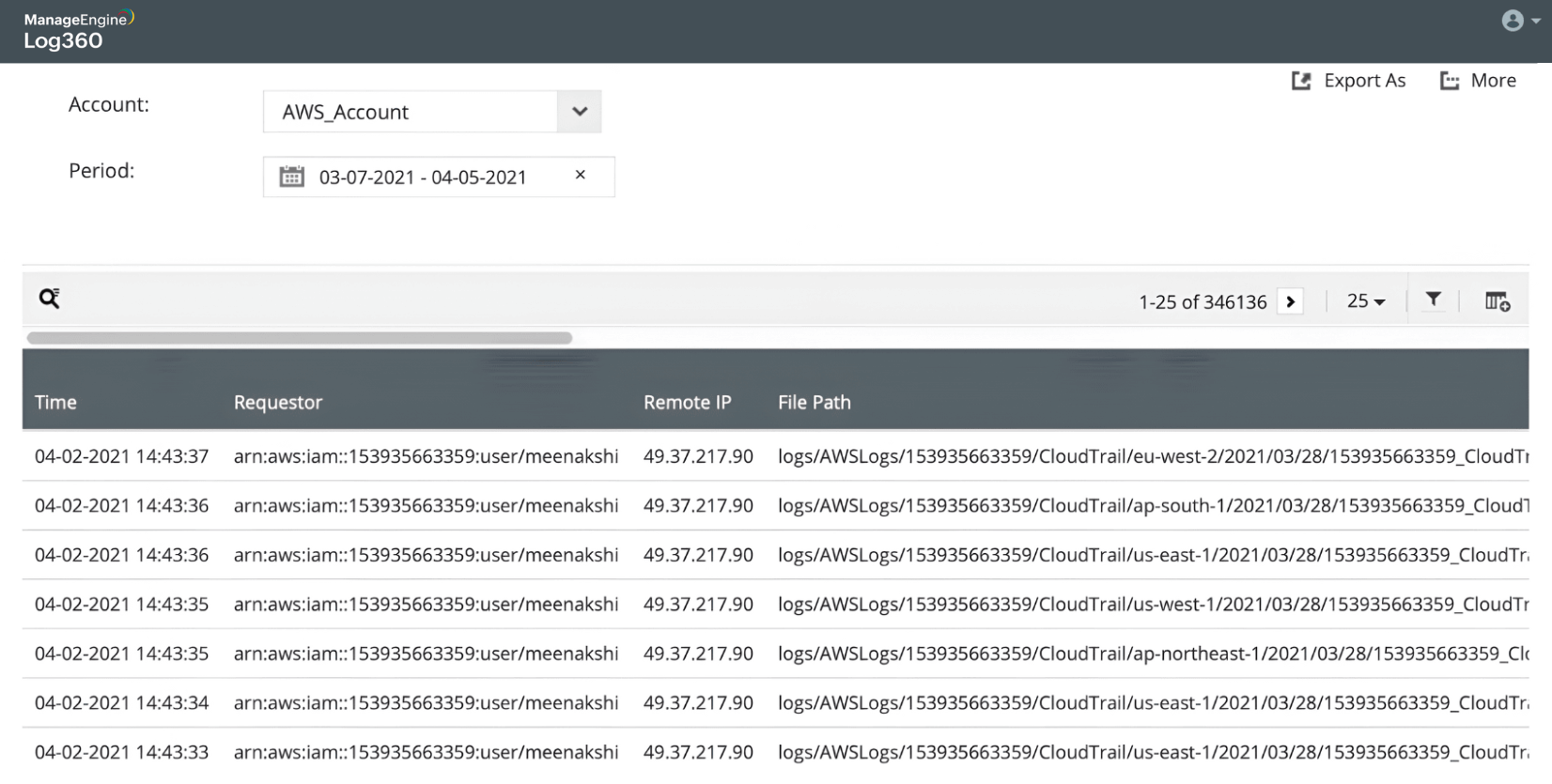
-
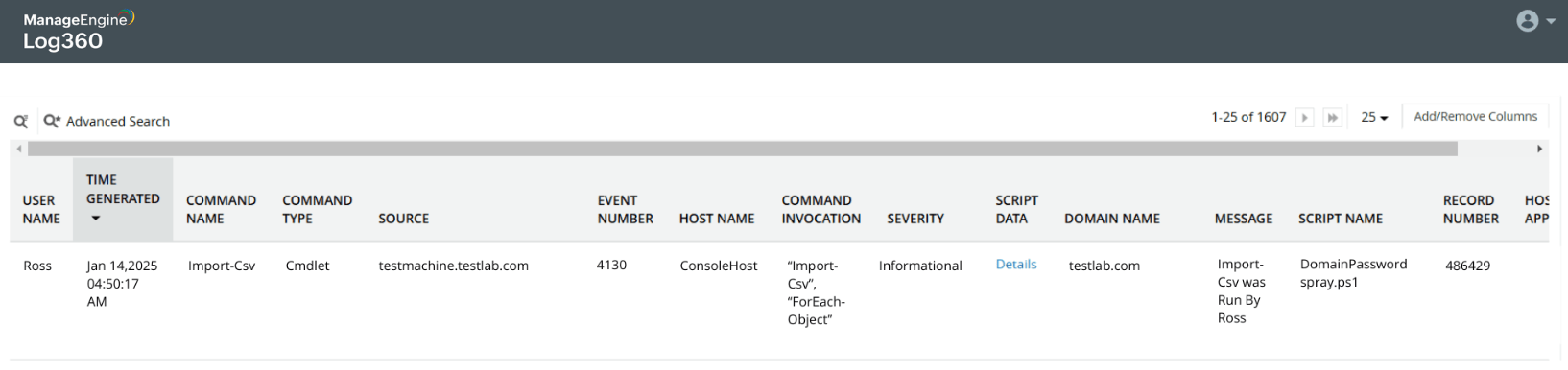
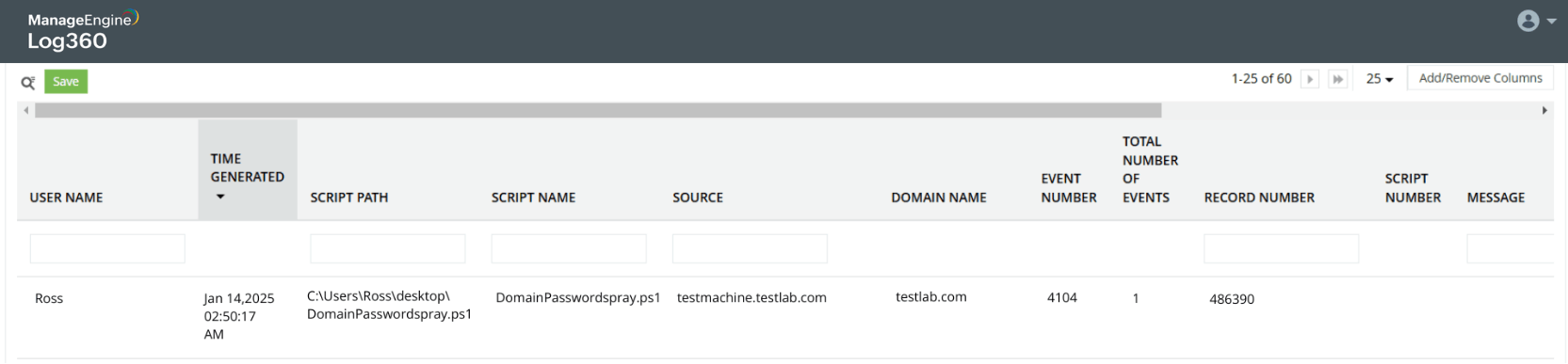
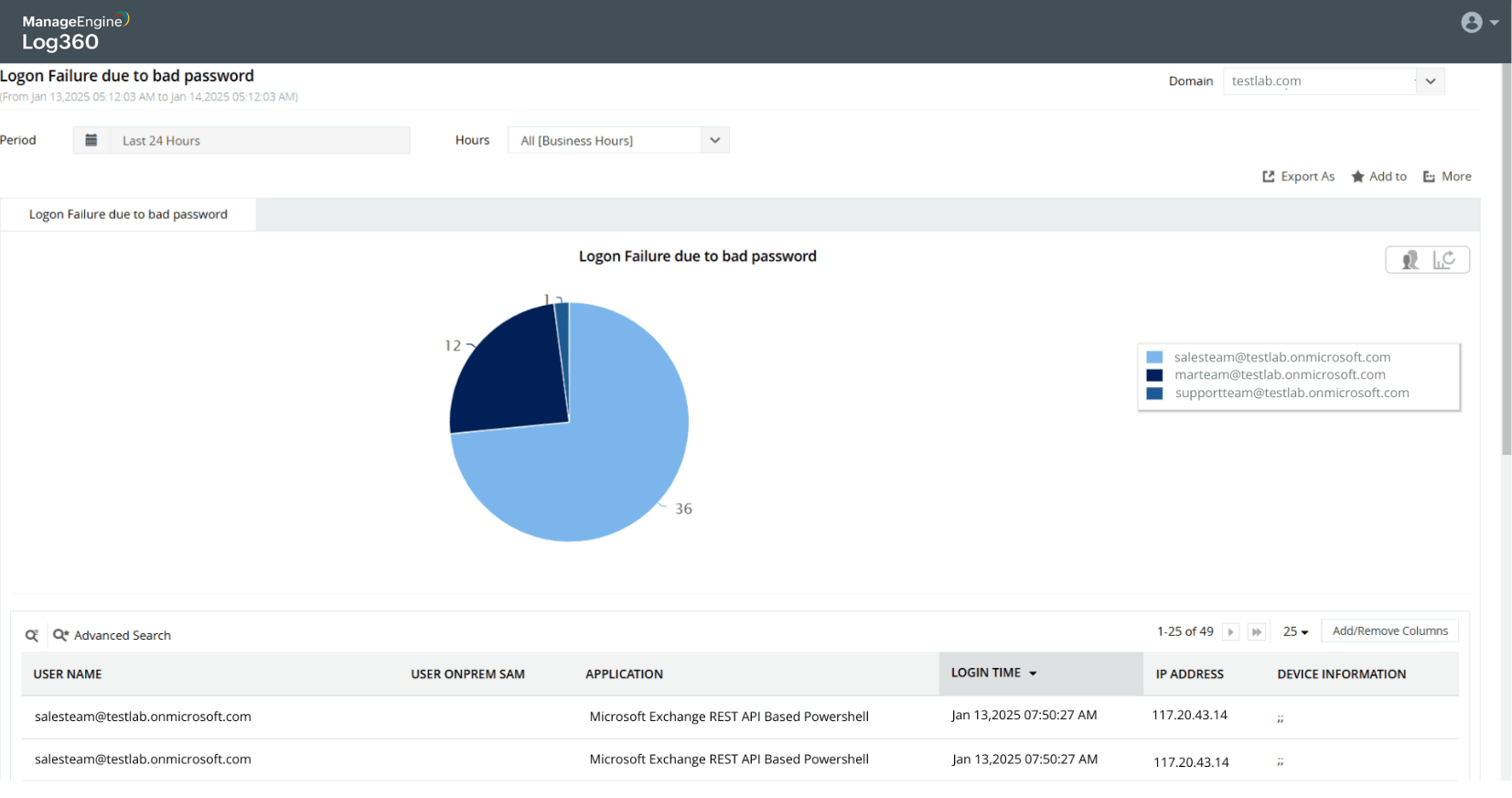
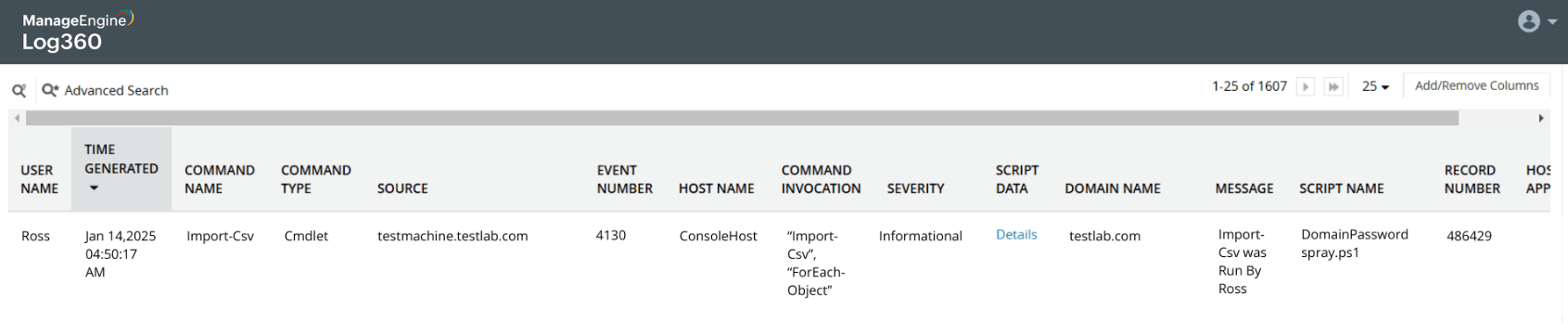
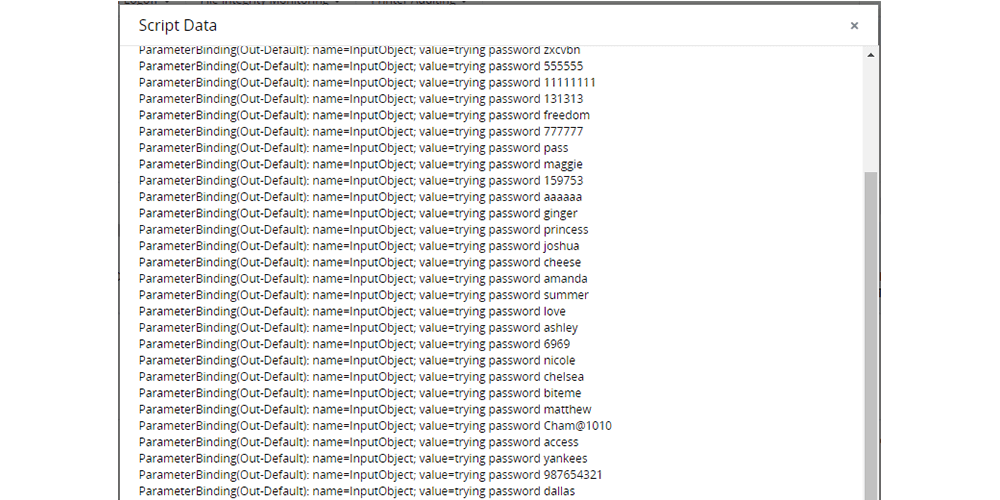
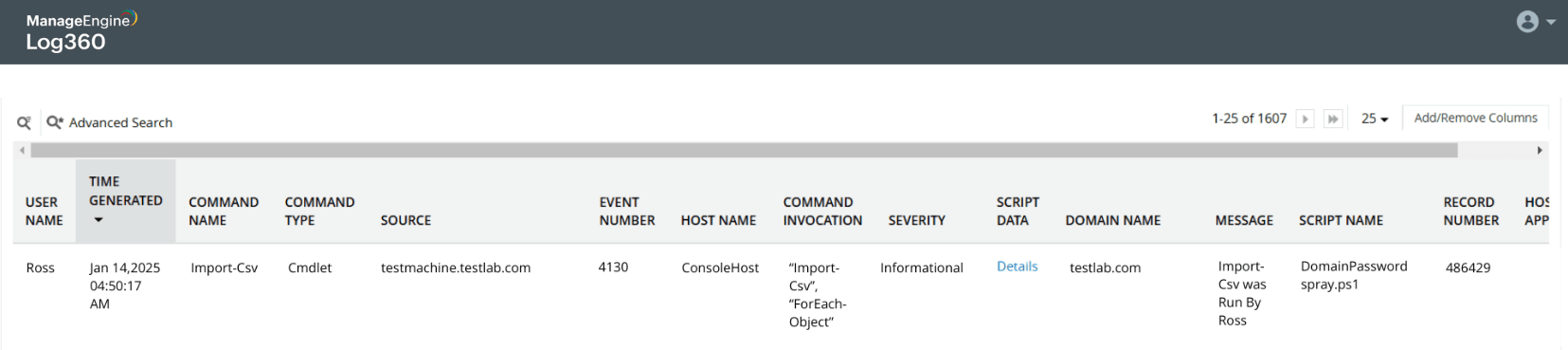
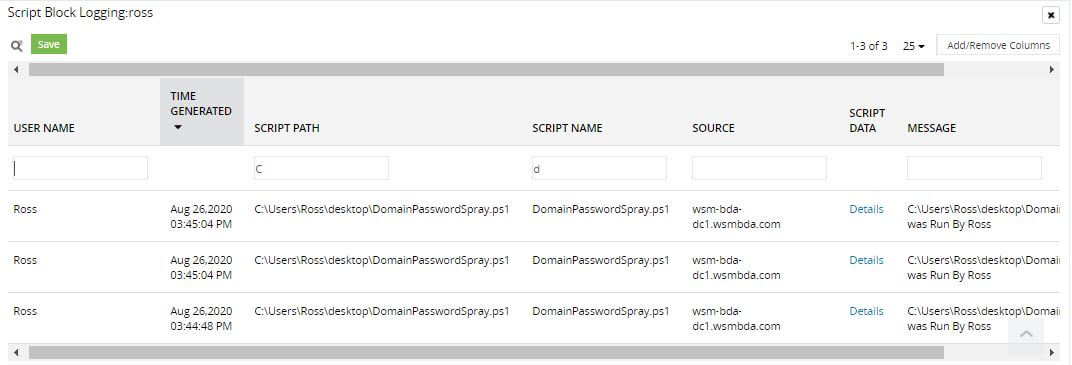
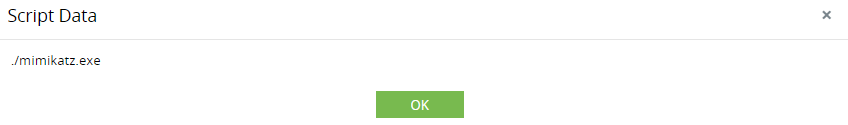
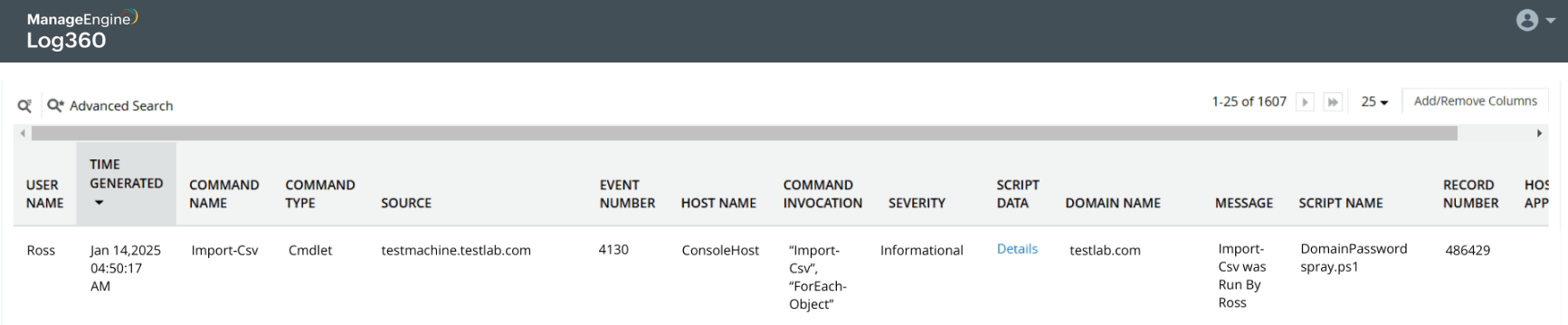
Password spray attack on Active Directory users
Learn more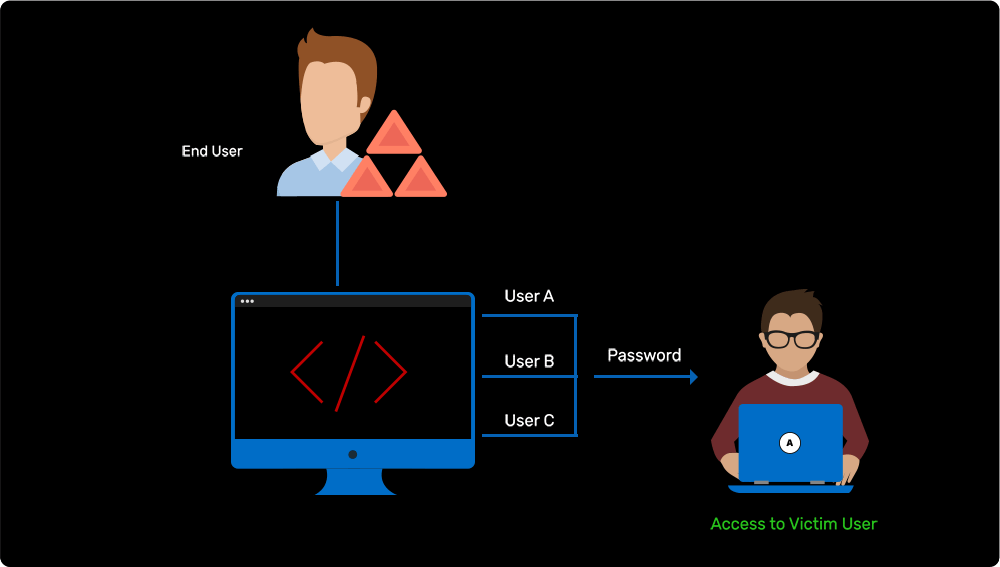
-
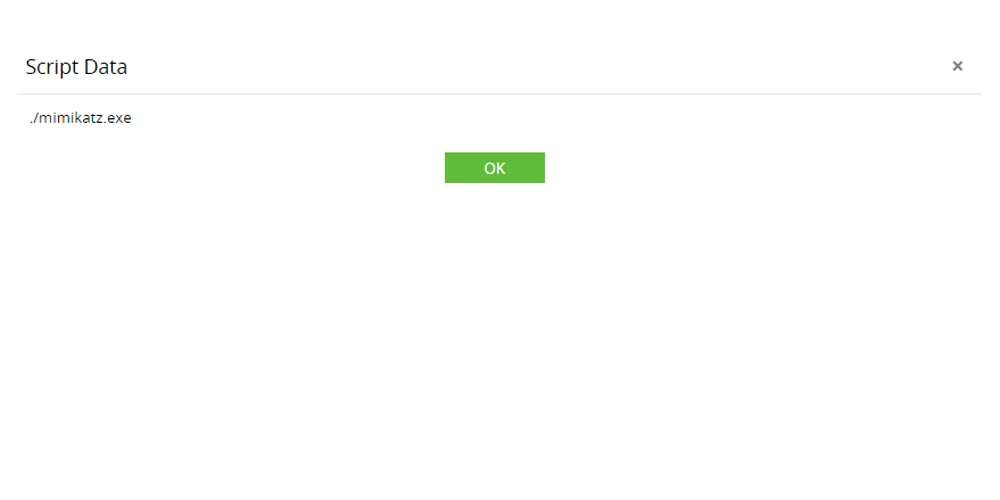
Passing the password hash of admin to gain instant privilege
Learn more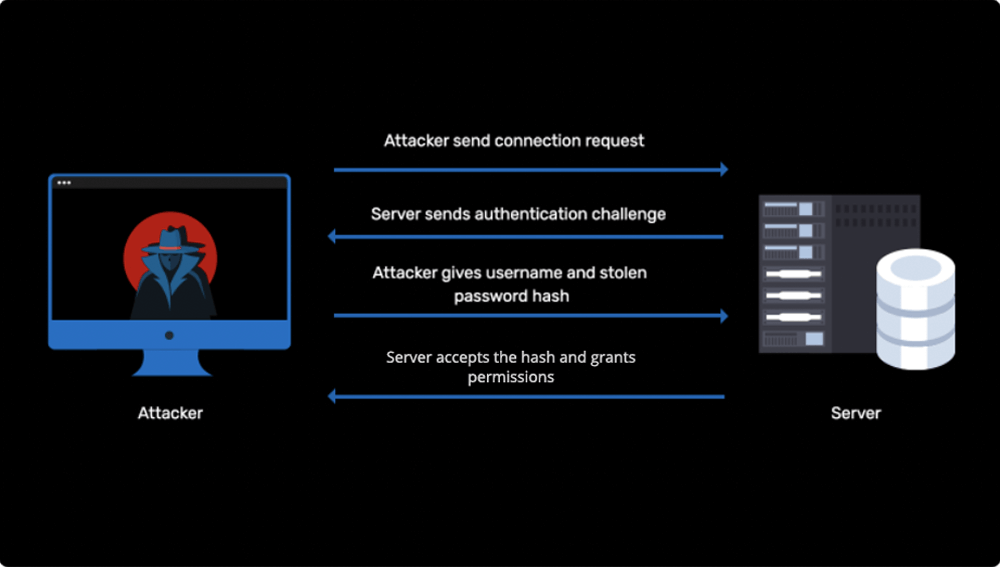
-
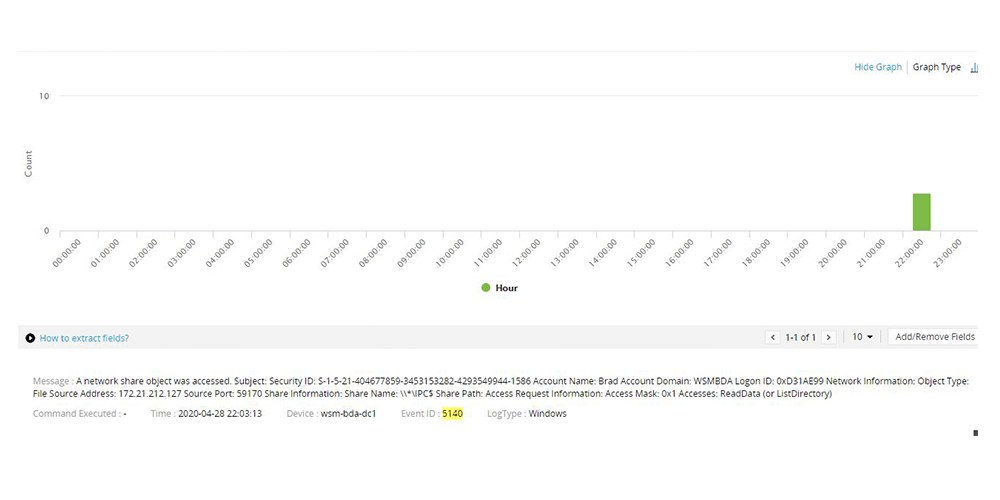
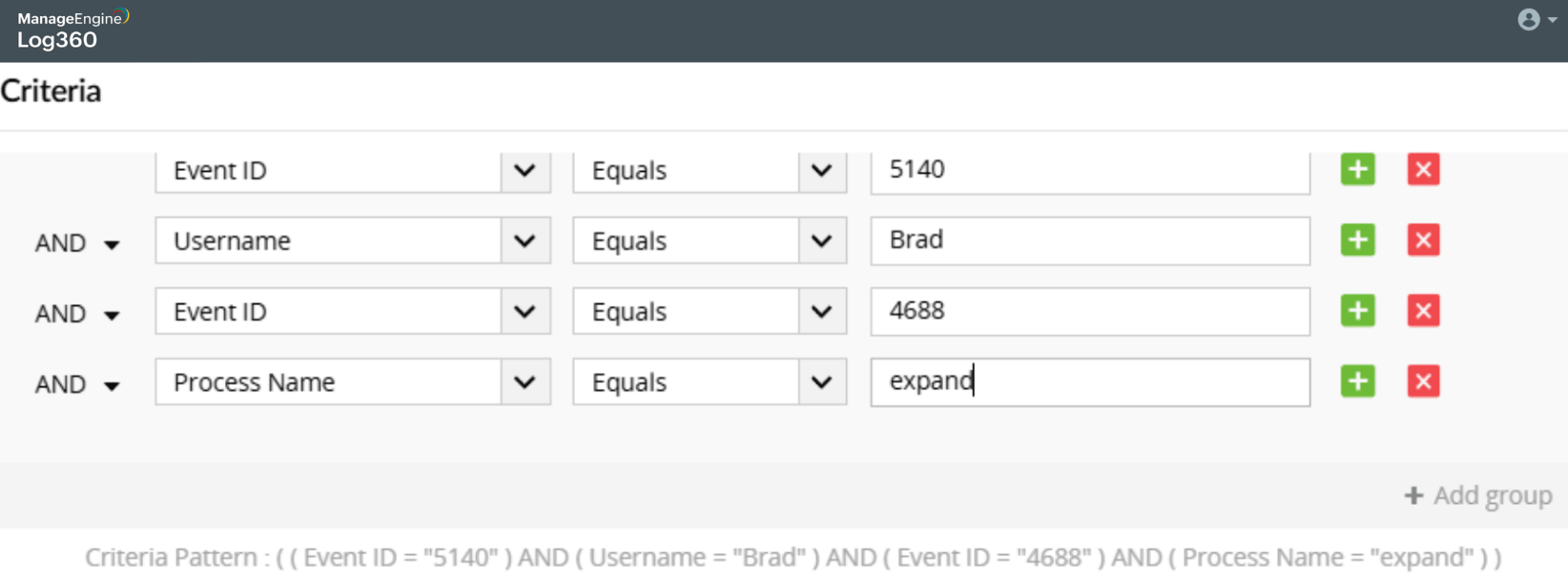
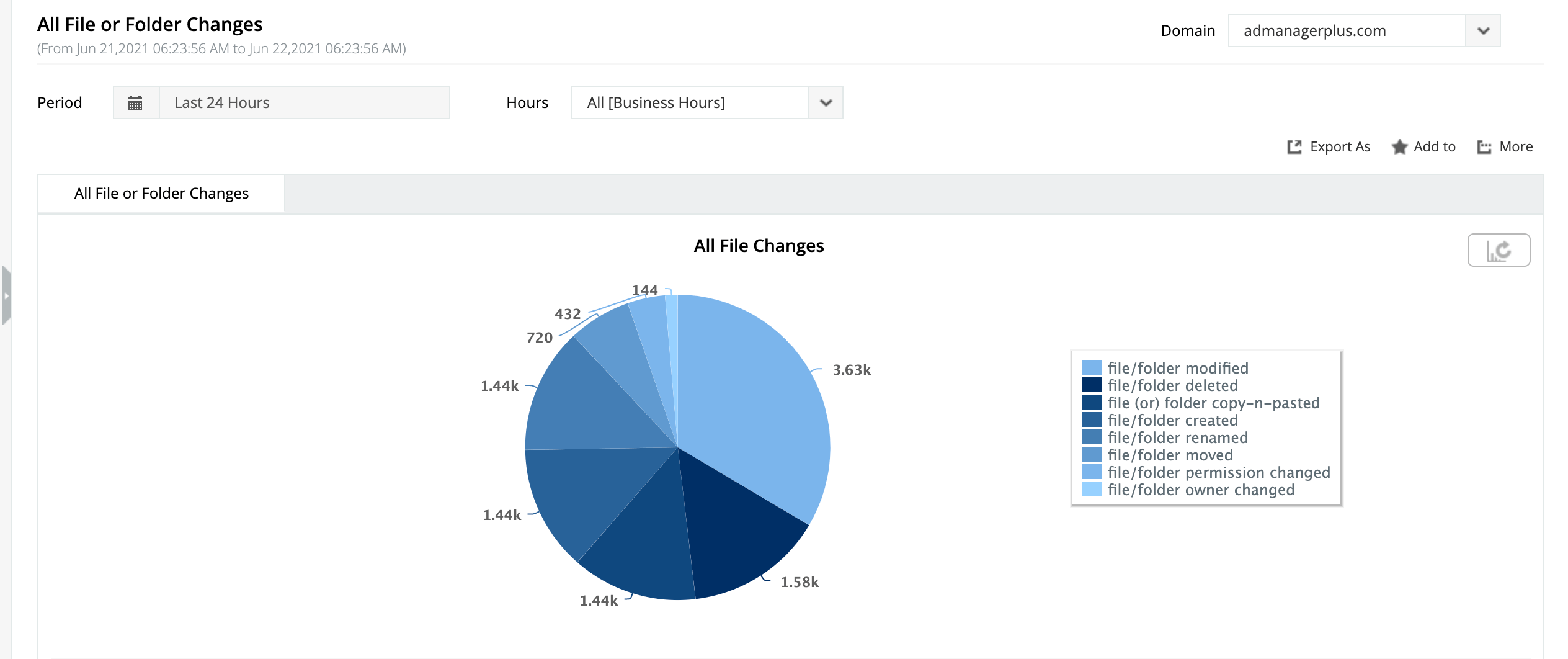
Secretly copying files from a remote location
Learn more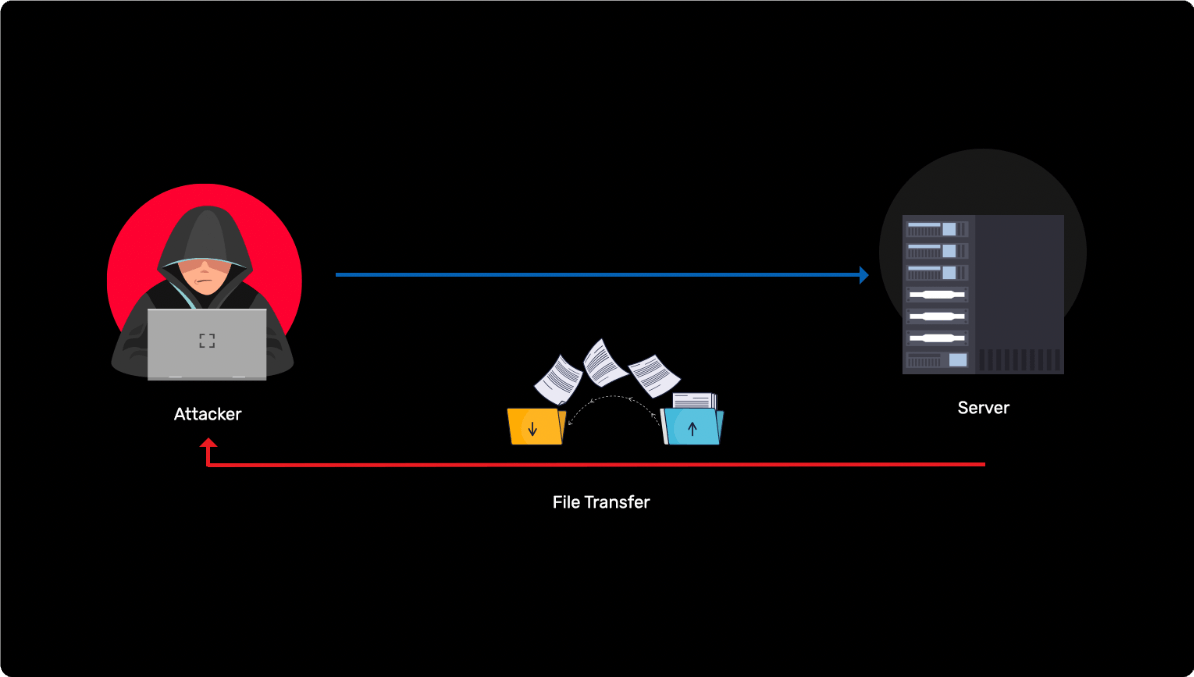
-
Detecting attacks in Linux environments
Learn more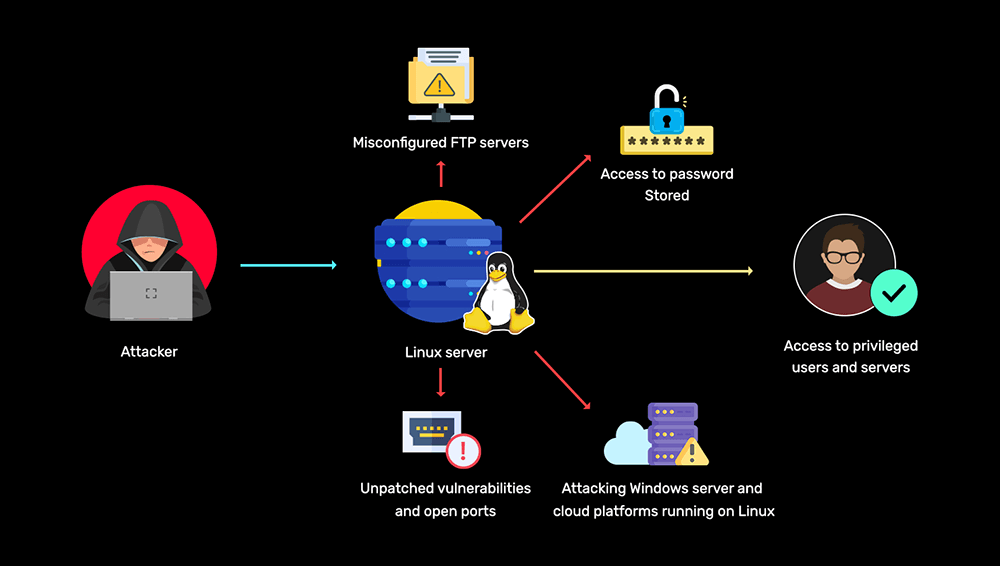
-
Detecting attacks in Windows environments
Learn more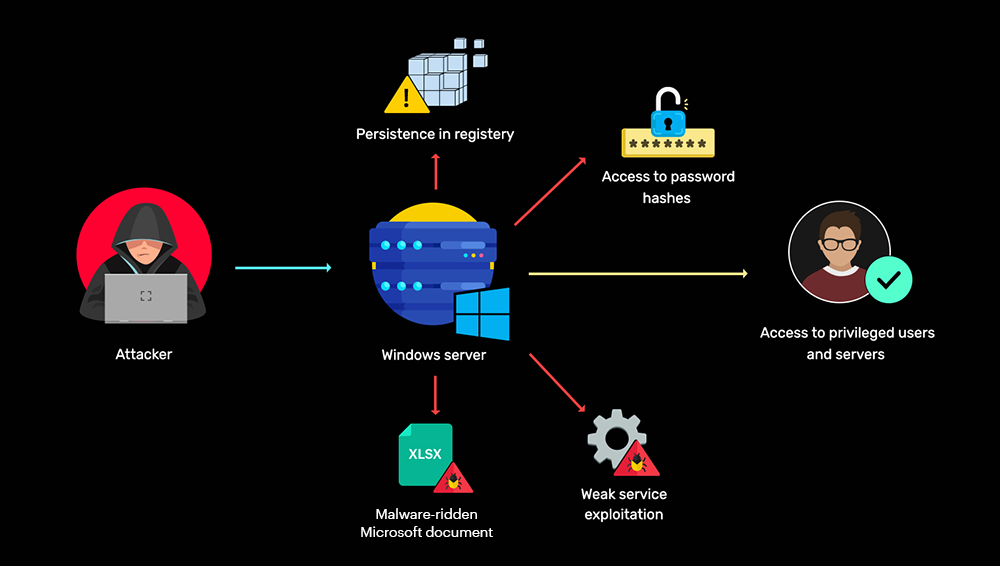
-
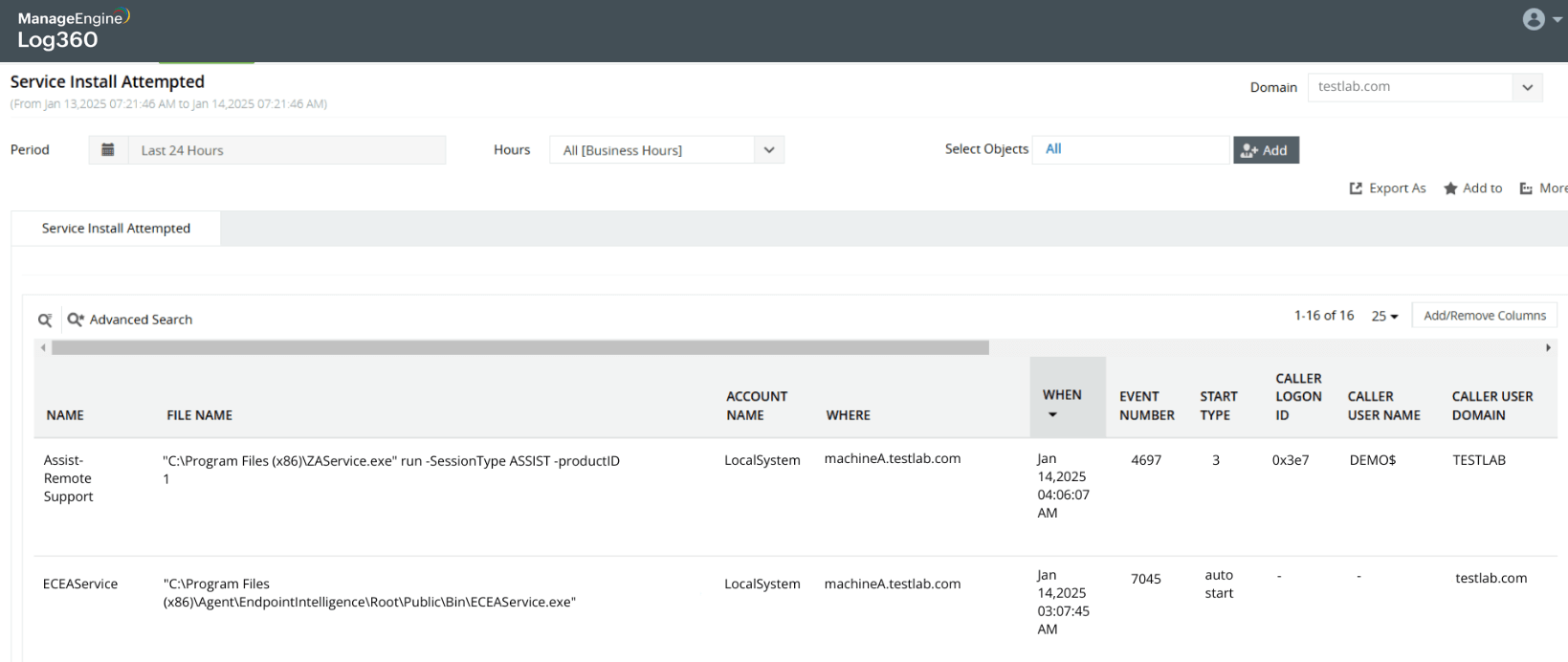
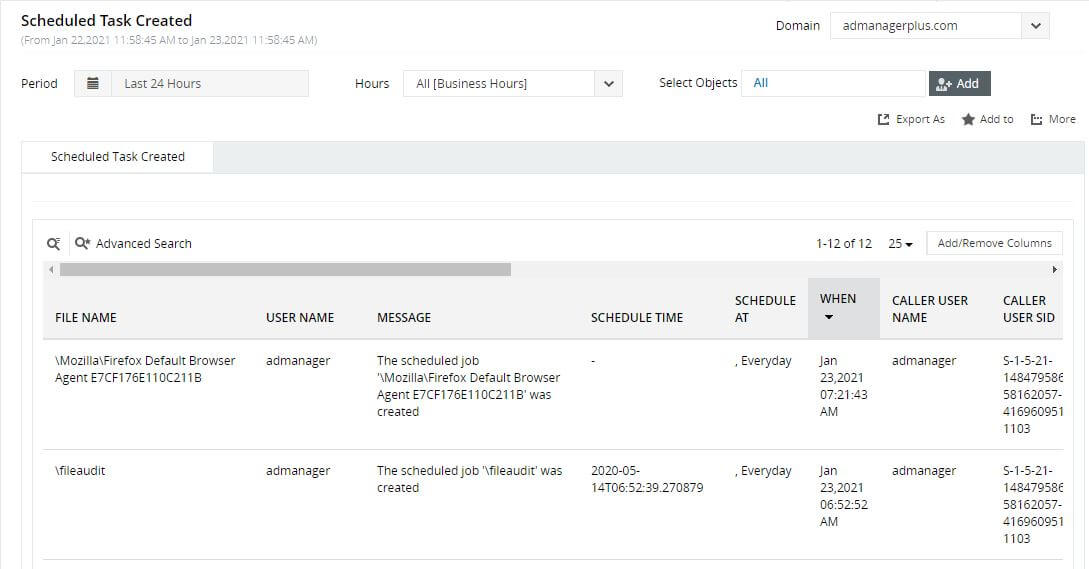
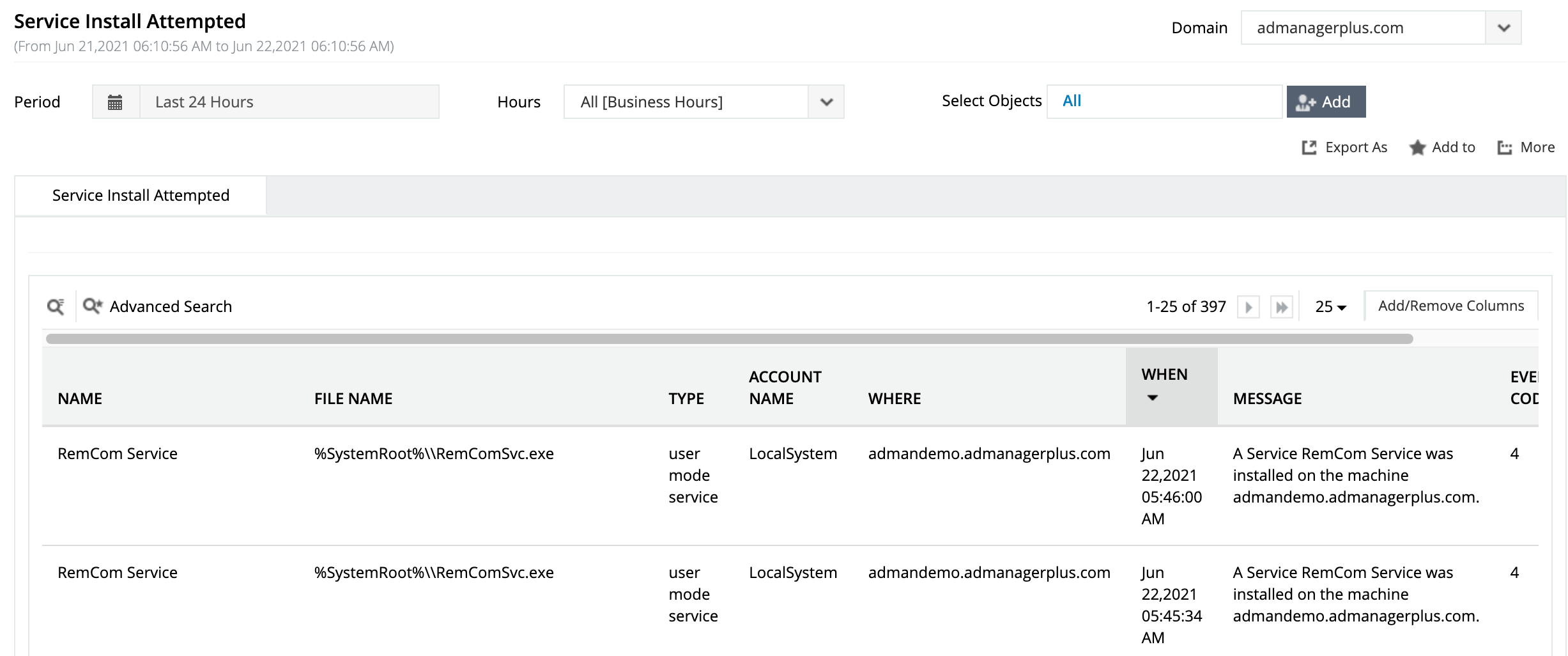
Installing a malicious backdoor service
Learn more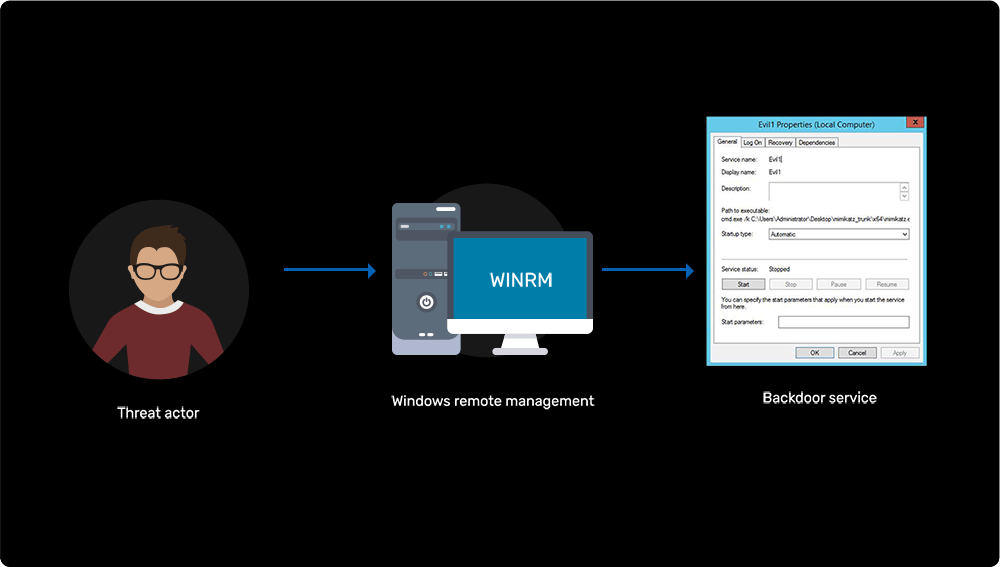
-
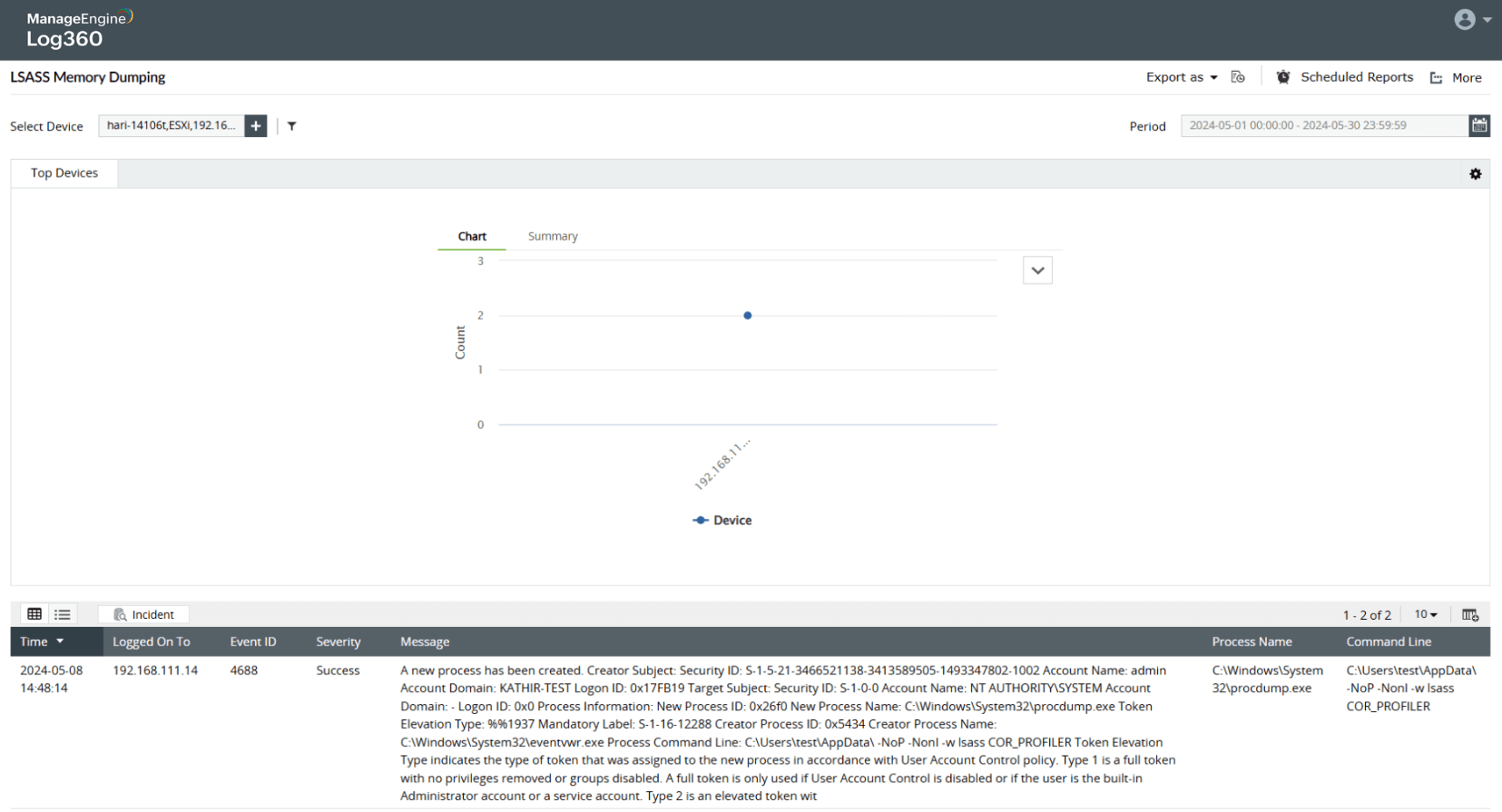
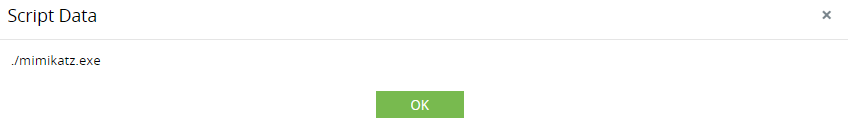
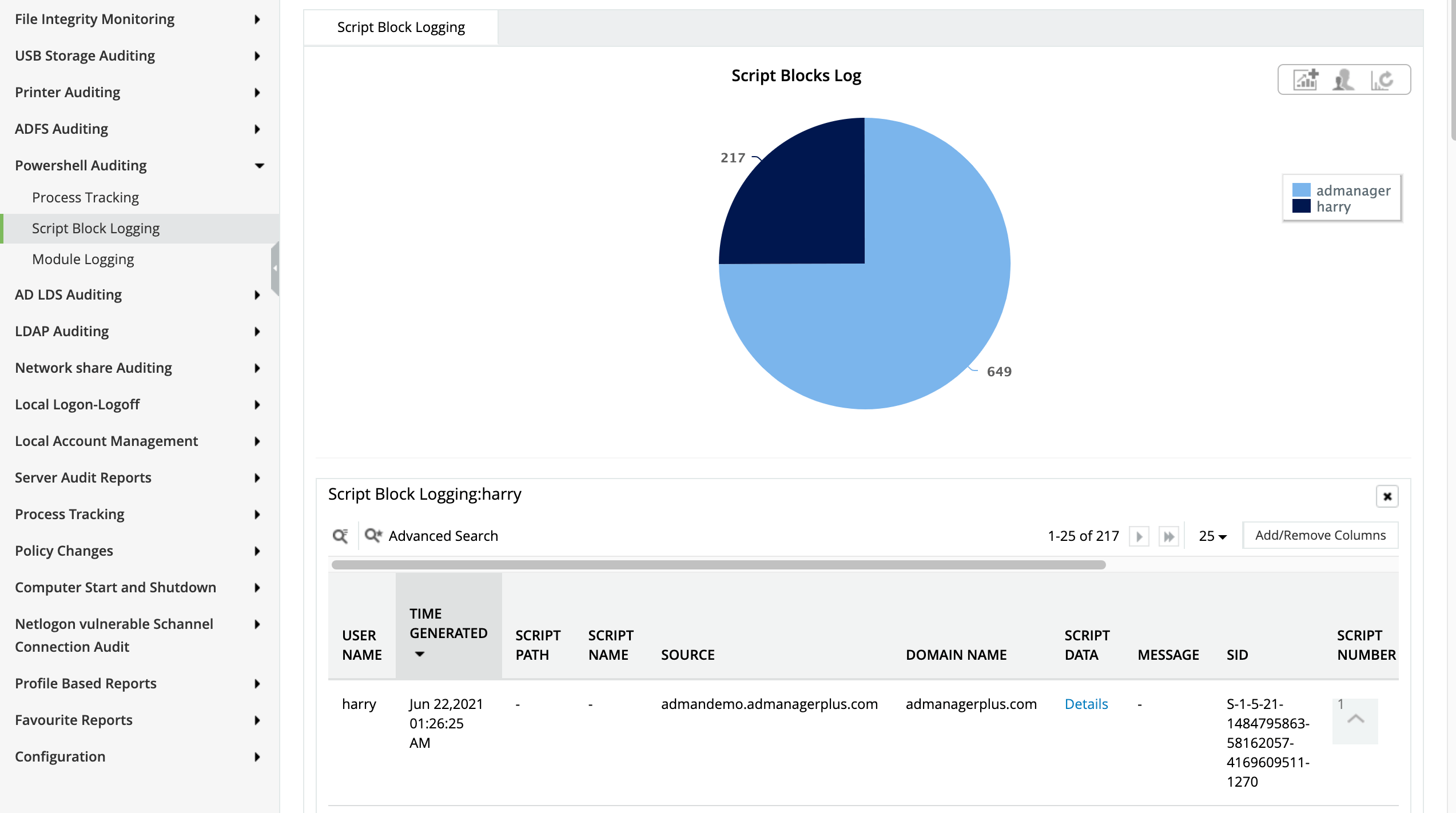
Dumping credentials from local memory of servers (LSA)
Learn more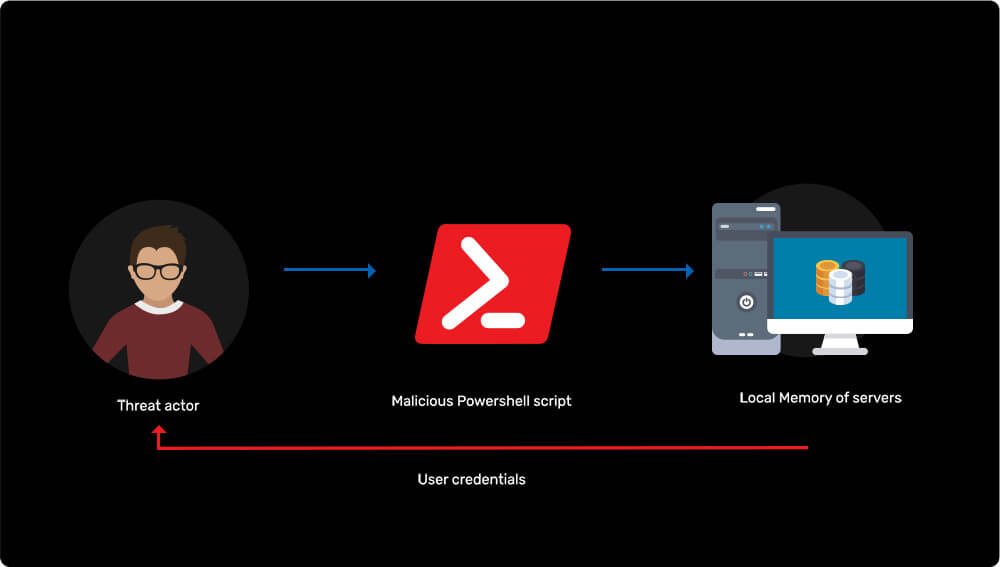
-
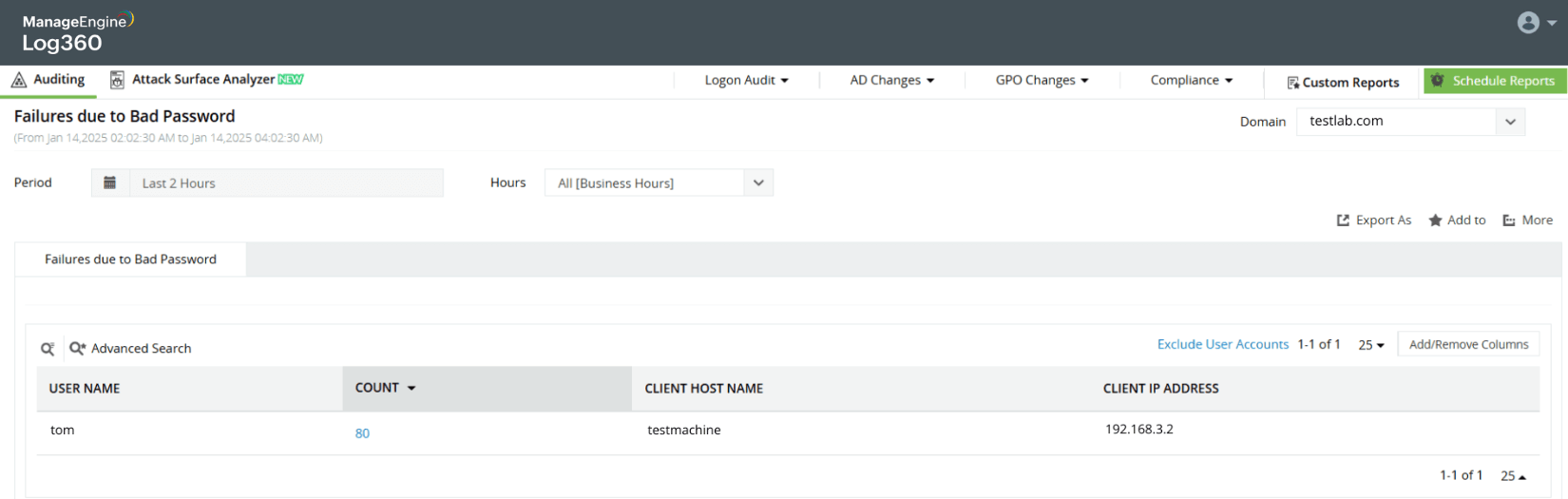
Brute forcing Active Directory administrator's password
Learn more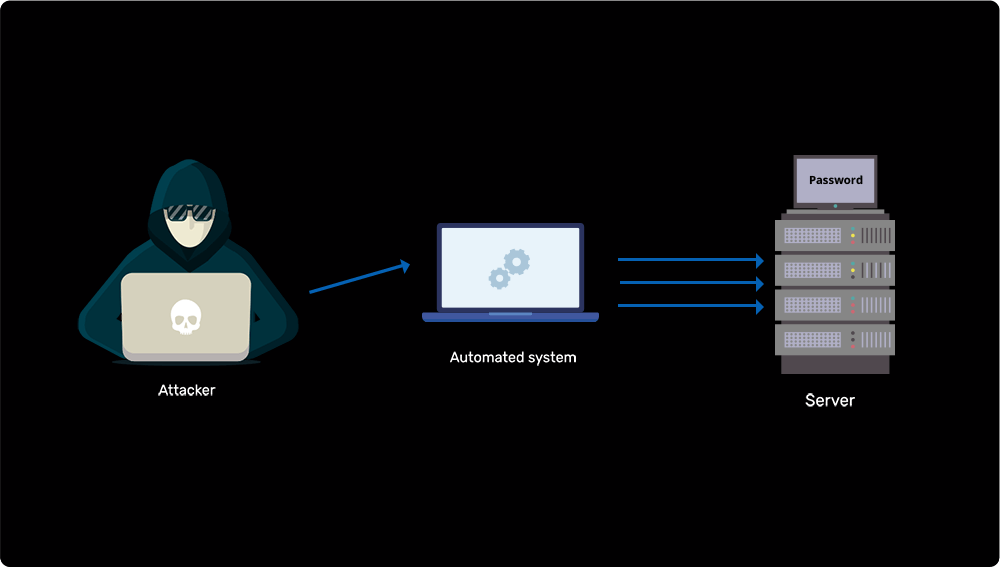
-
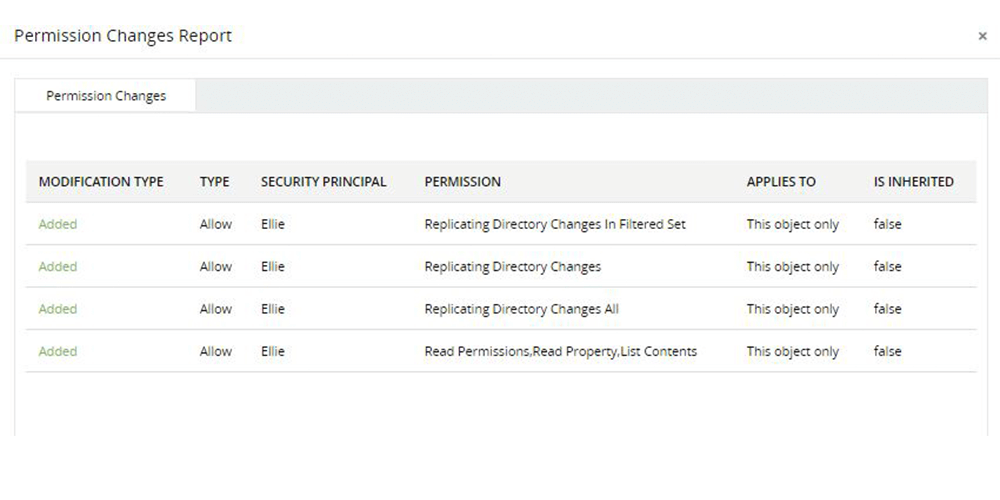
Backdooring users into privileged groups in Active Directory
Learn more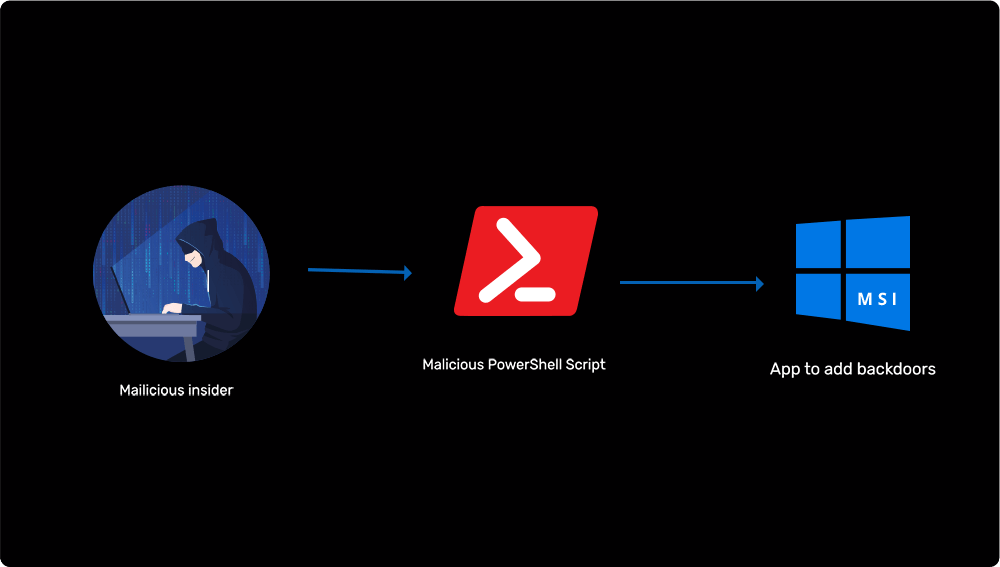
-
Compromising an exchange server and extracting sensitive emails
Learn more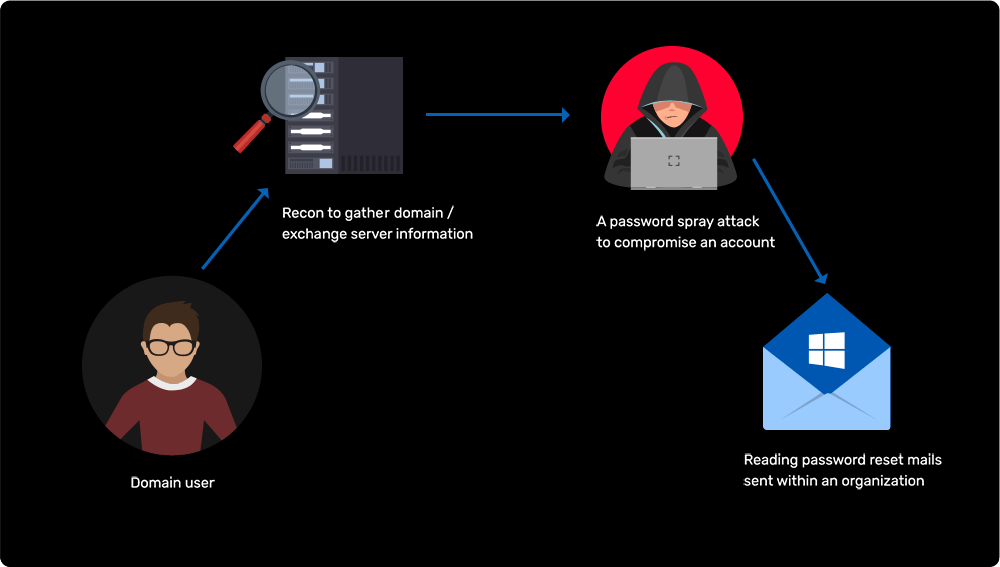
-
Simulating domain controller behavior to get Active Directory user passwords
Learn more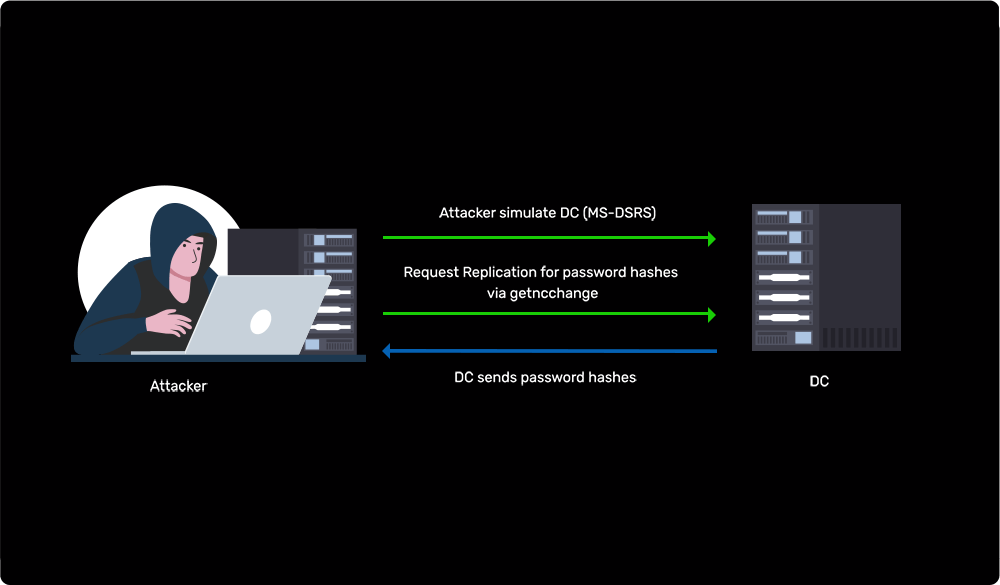
-
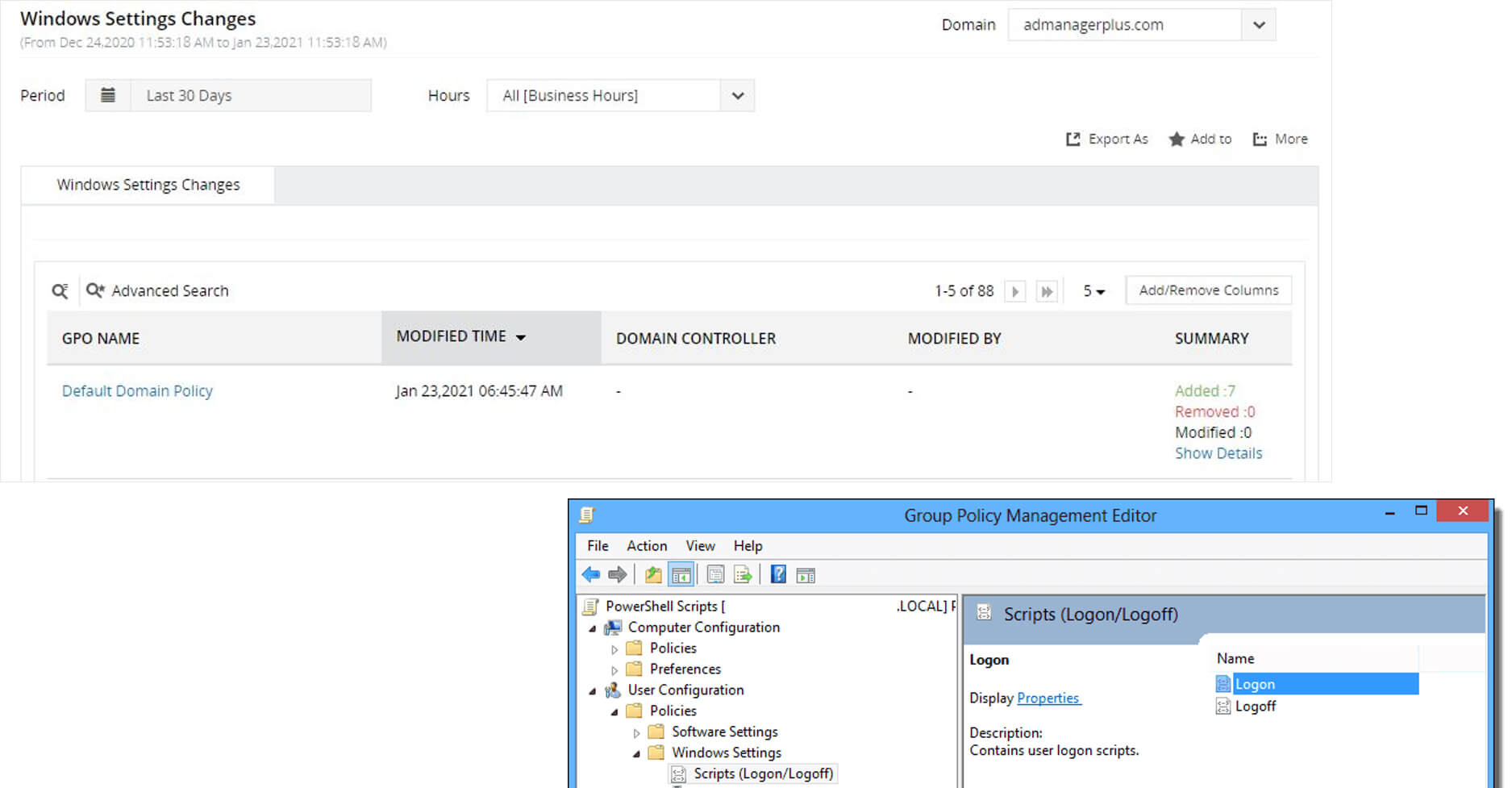
Registering a rogue domain controller to inject backdoor changes into Active Directory
Learn more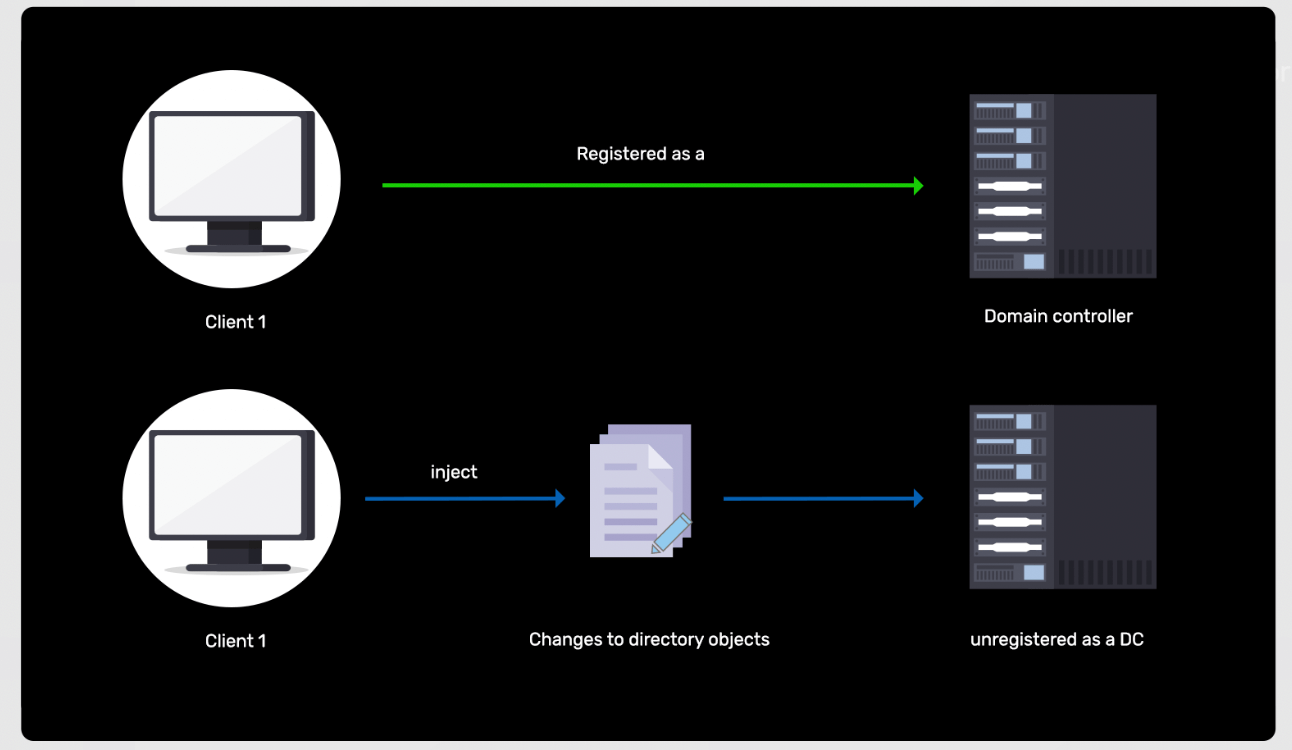
-
Bypass Windows Logons attack
Learn more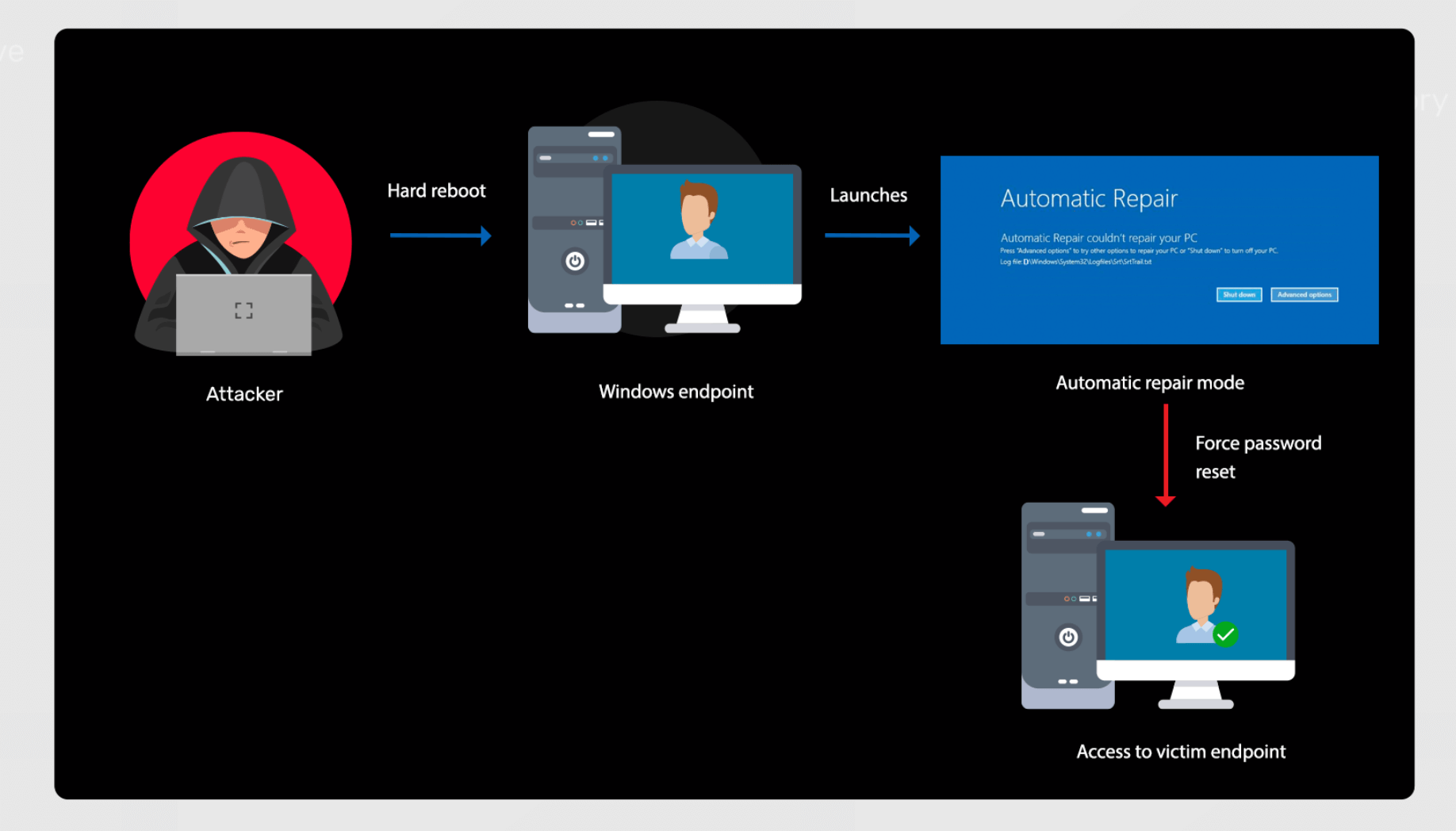
-
Malicious Microsoft Office macro creation
Learn more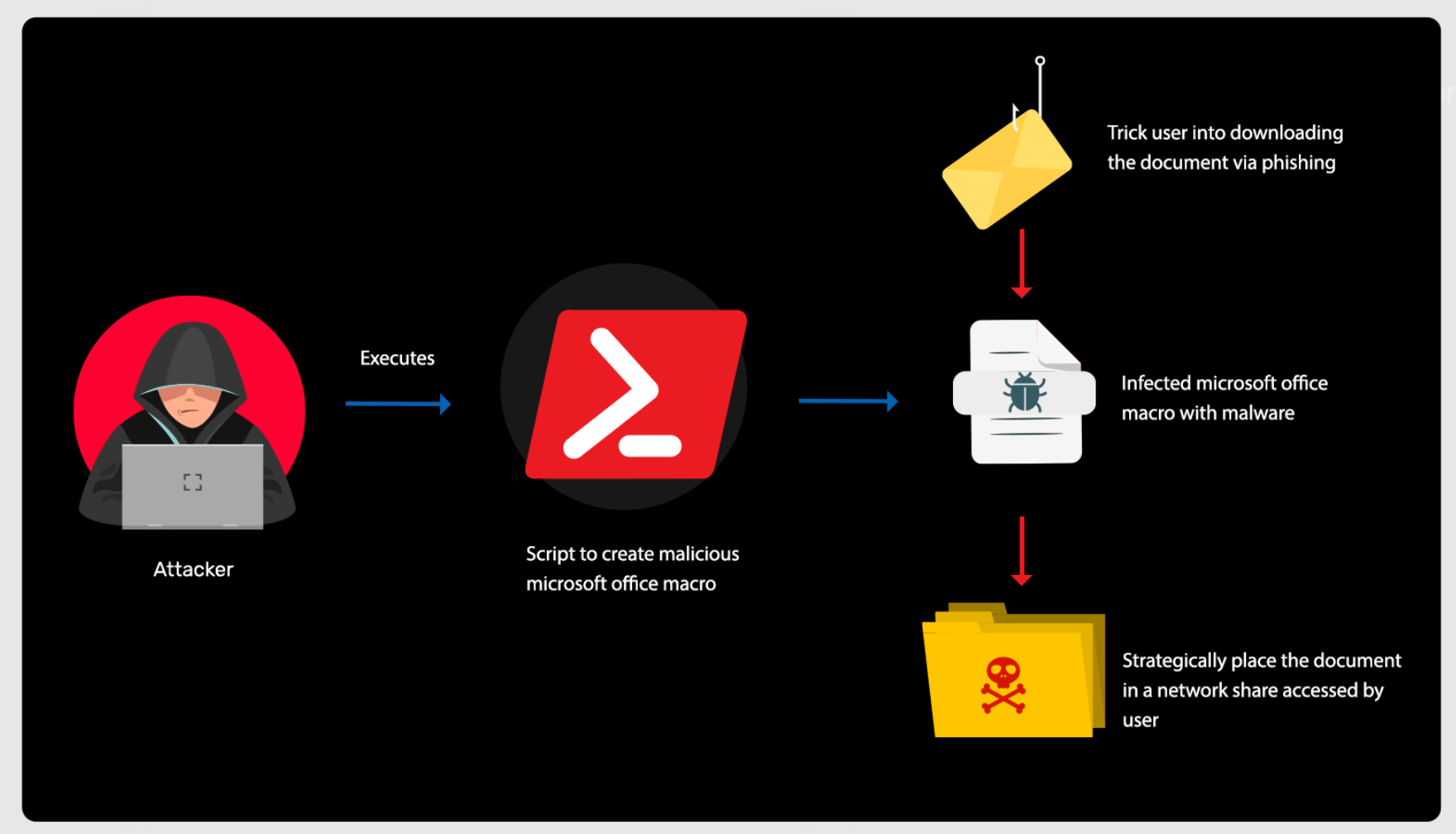
-
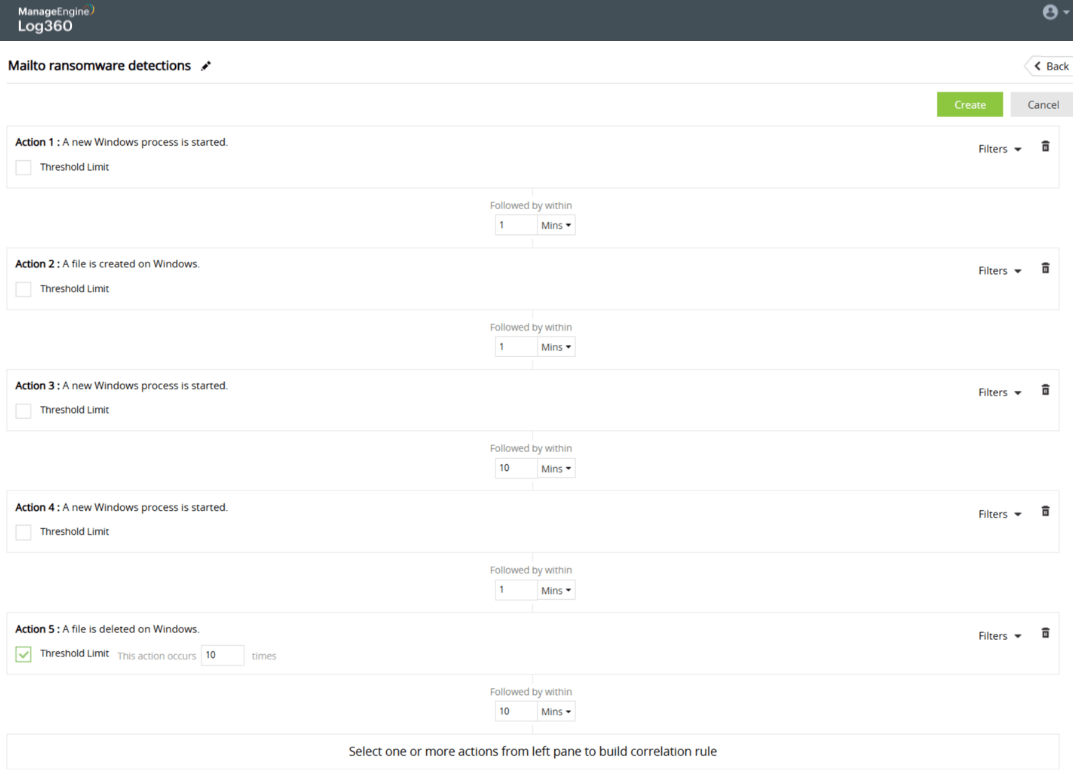
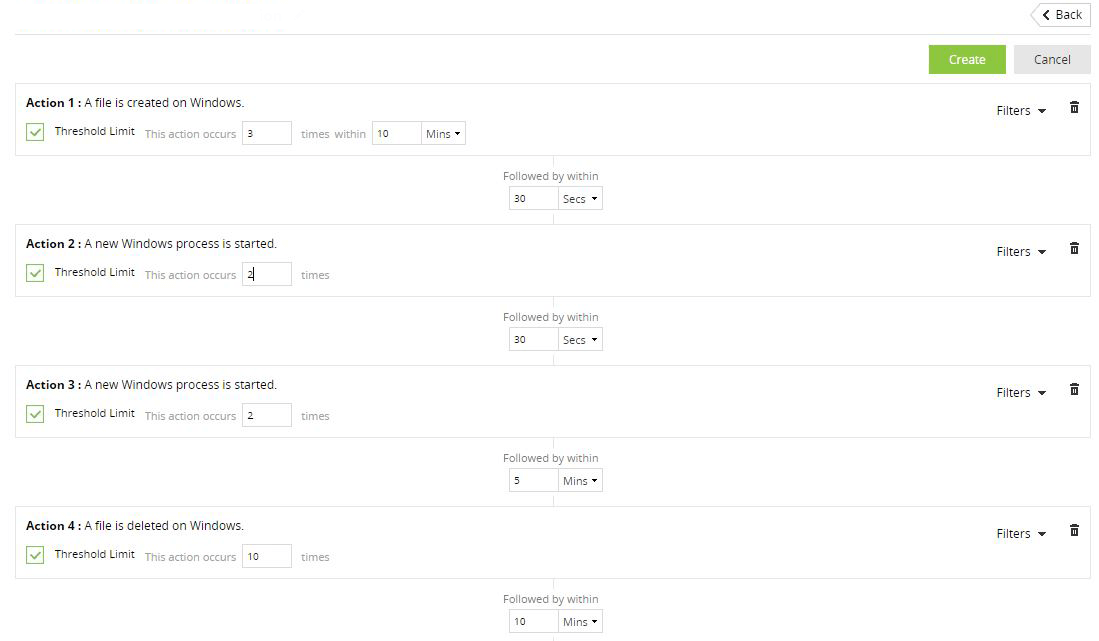
Ransomware attacks on organizations
Learn more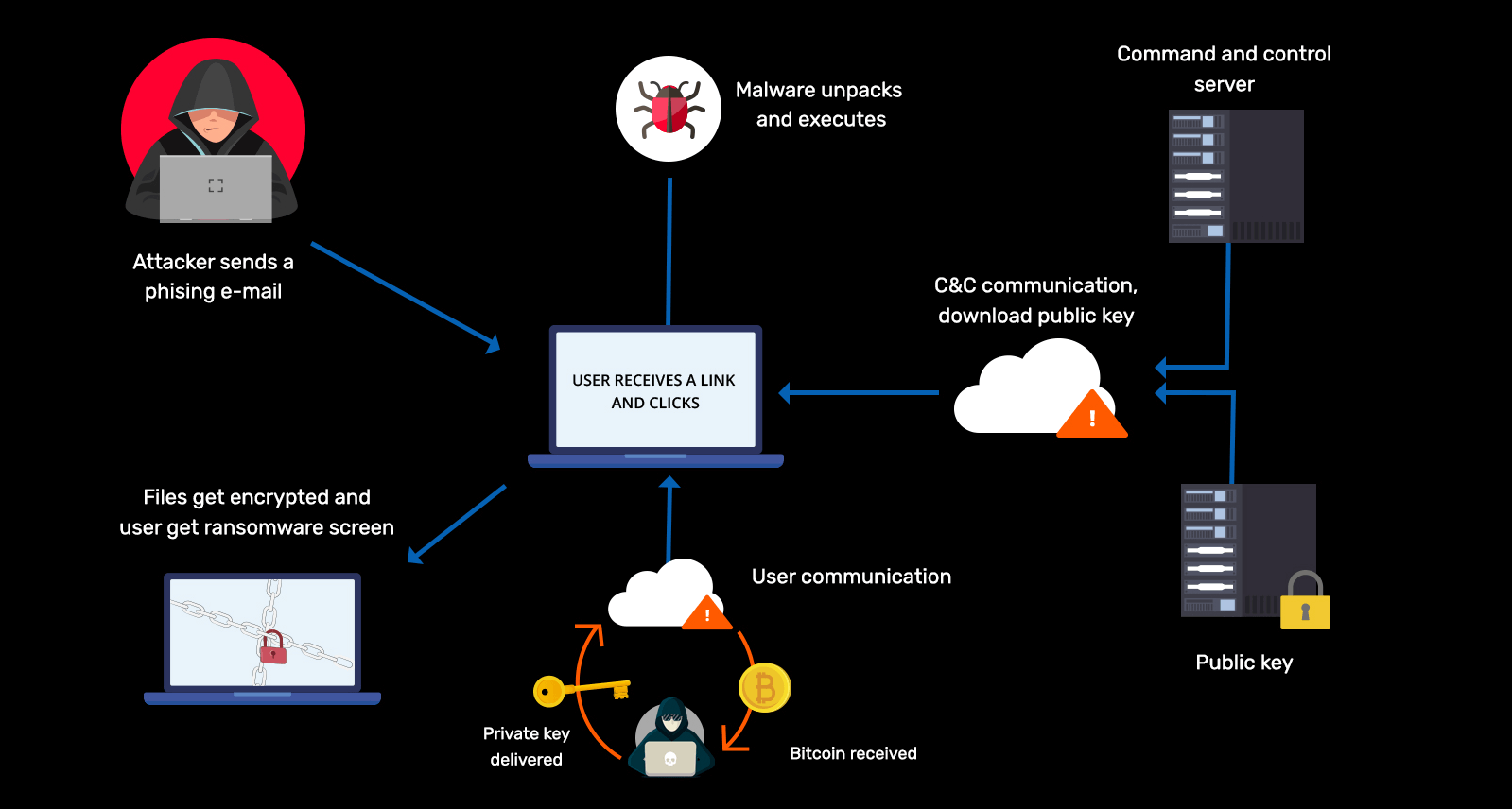
-
Hybrid AD reconnaissance
Learn more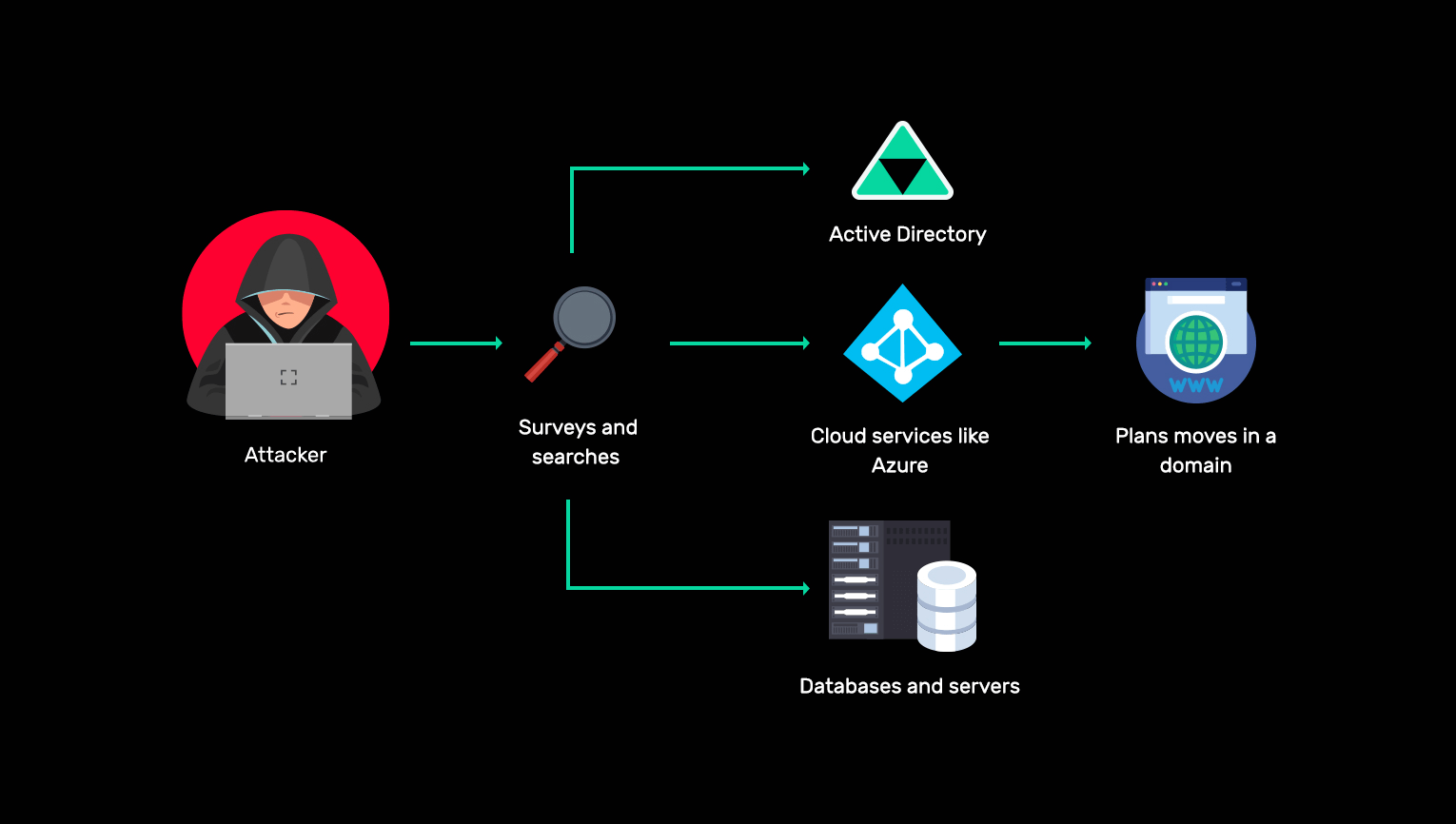
-
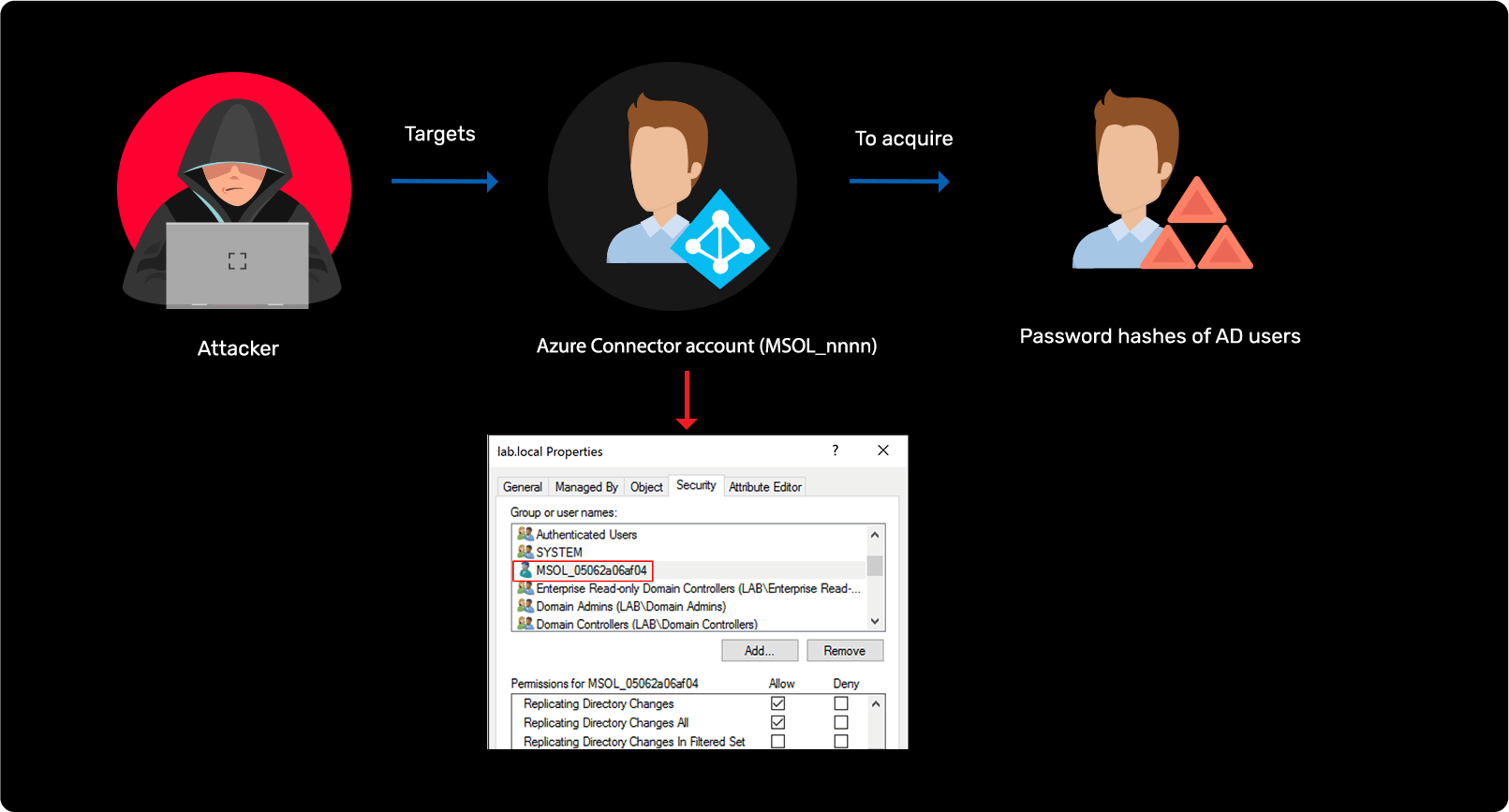
AD to Azure AD attack
Learn more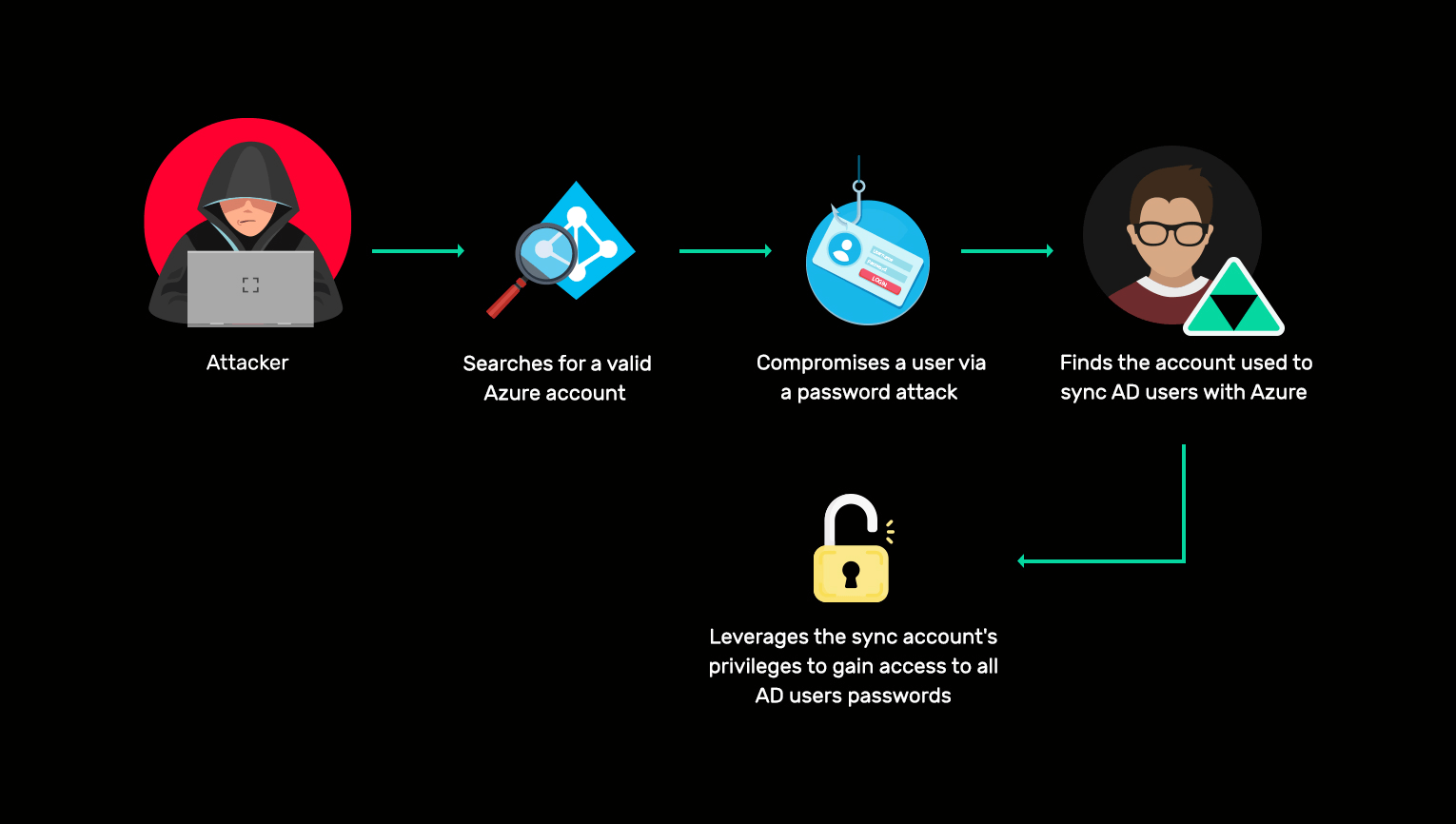
-
Credential dumping attack
Learn more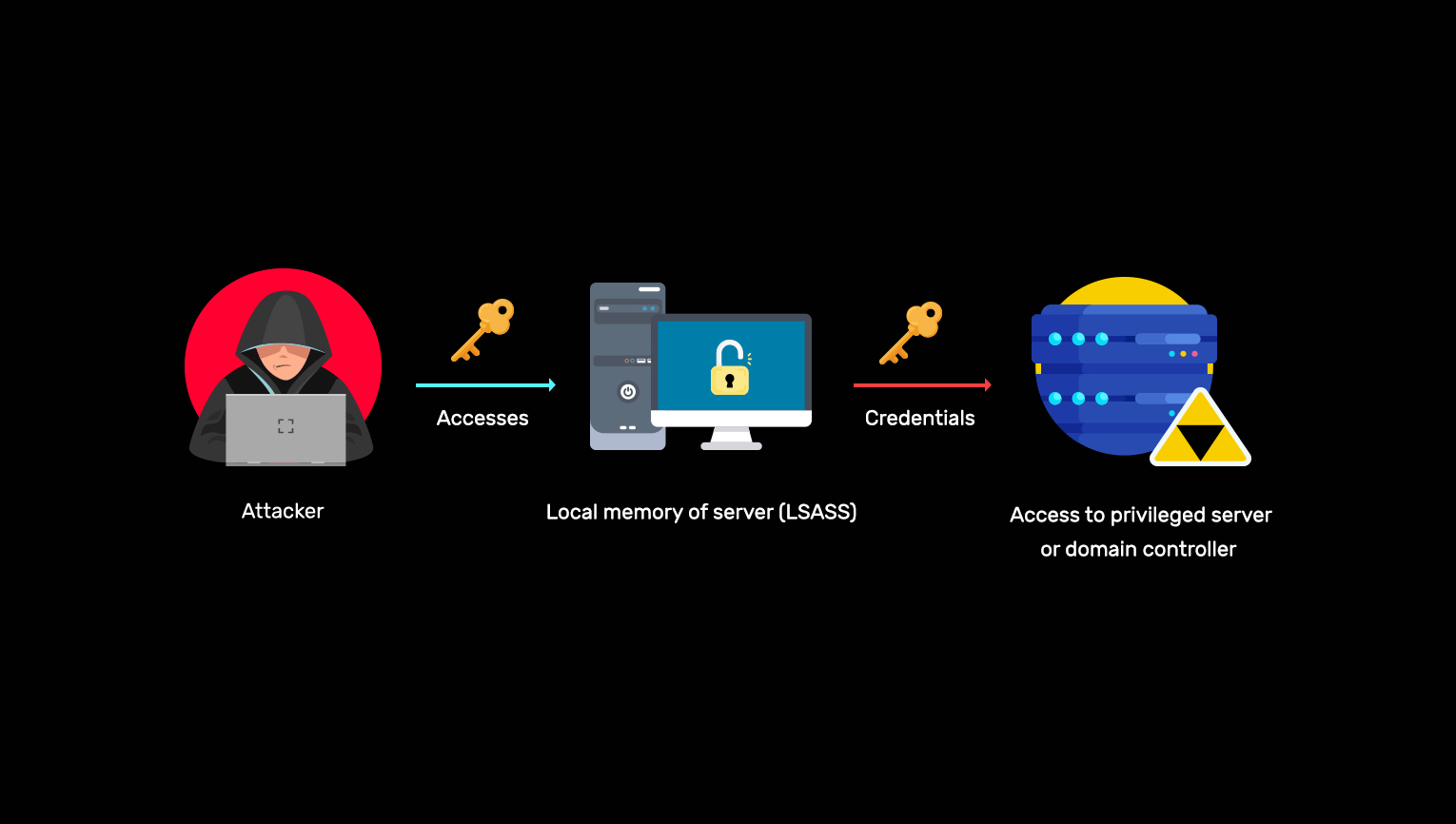
-
Kerberroasting attack
Learn more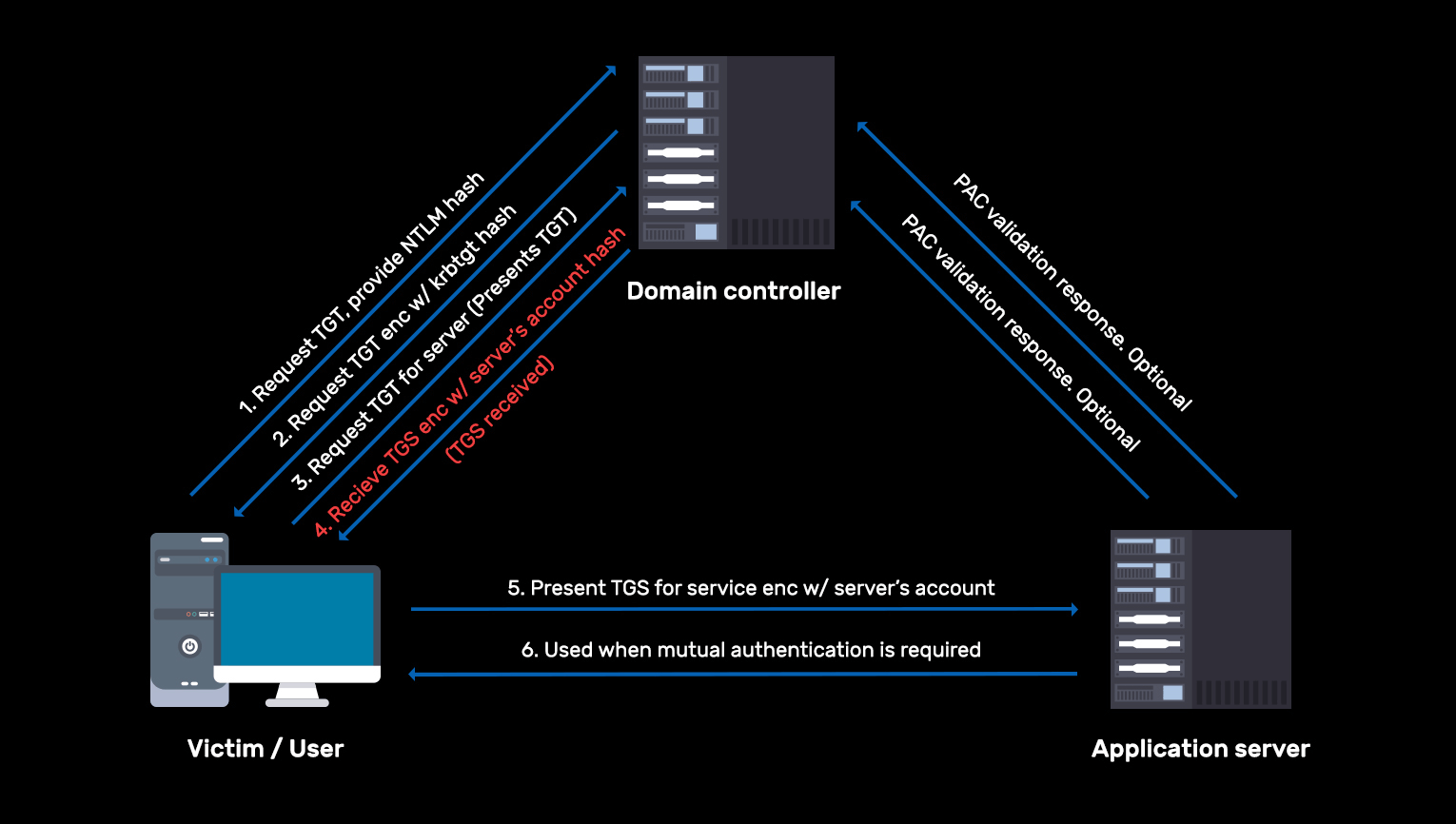
-
AWS ransomware attack
Learn more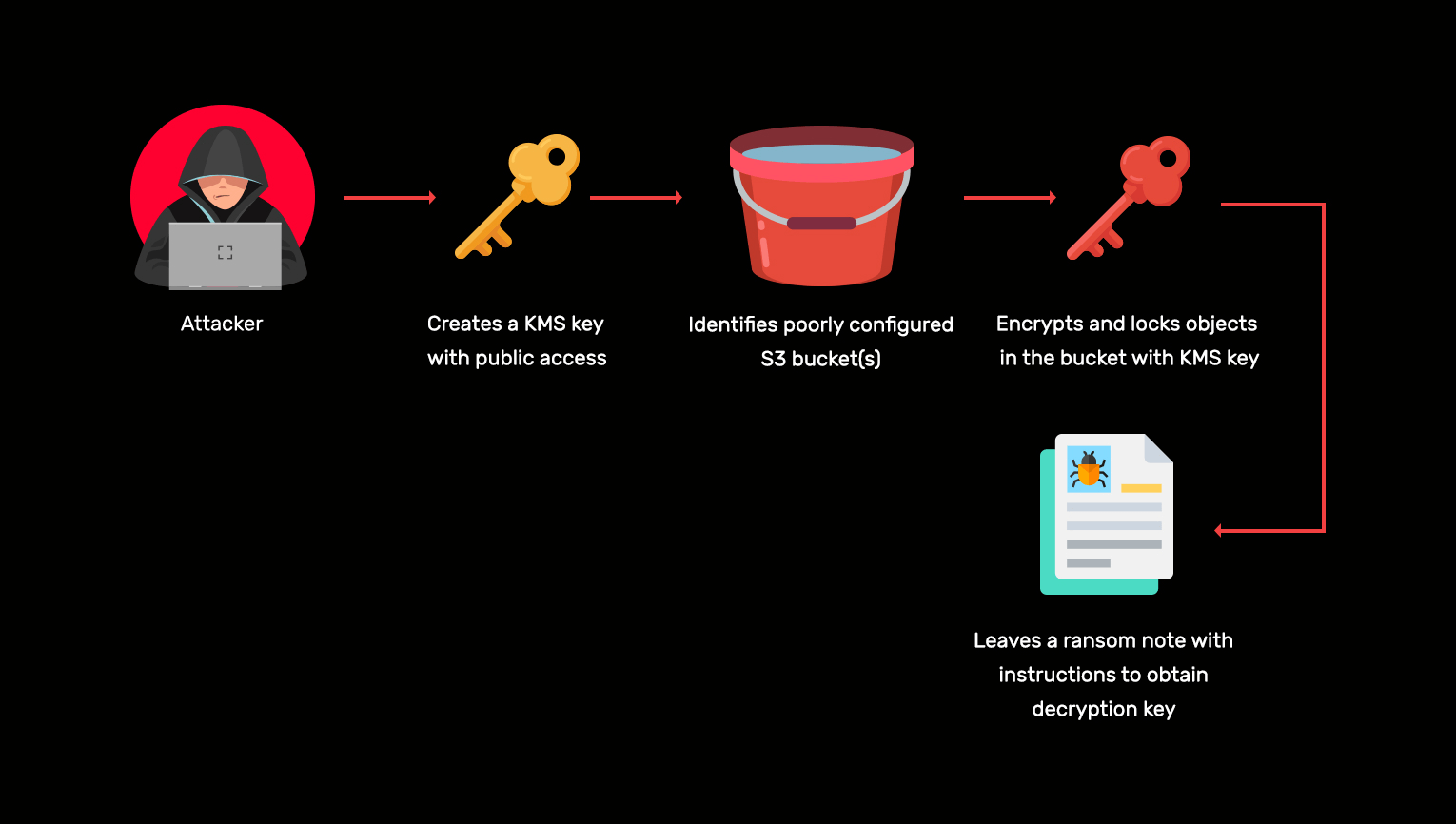
-
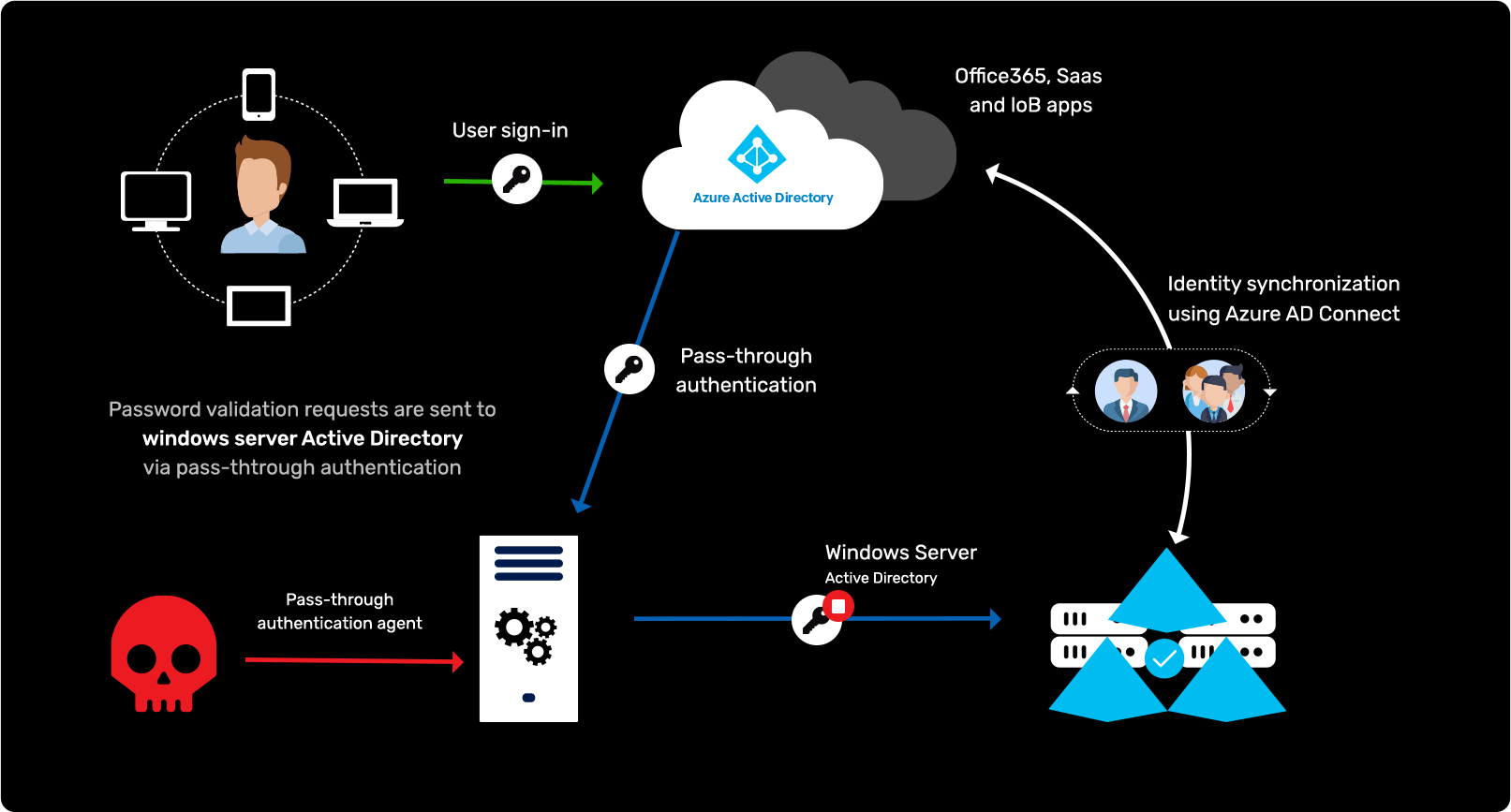
Attacking authentication in AD and Azure environments
Learn more
-
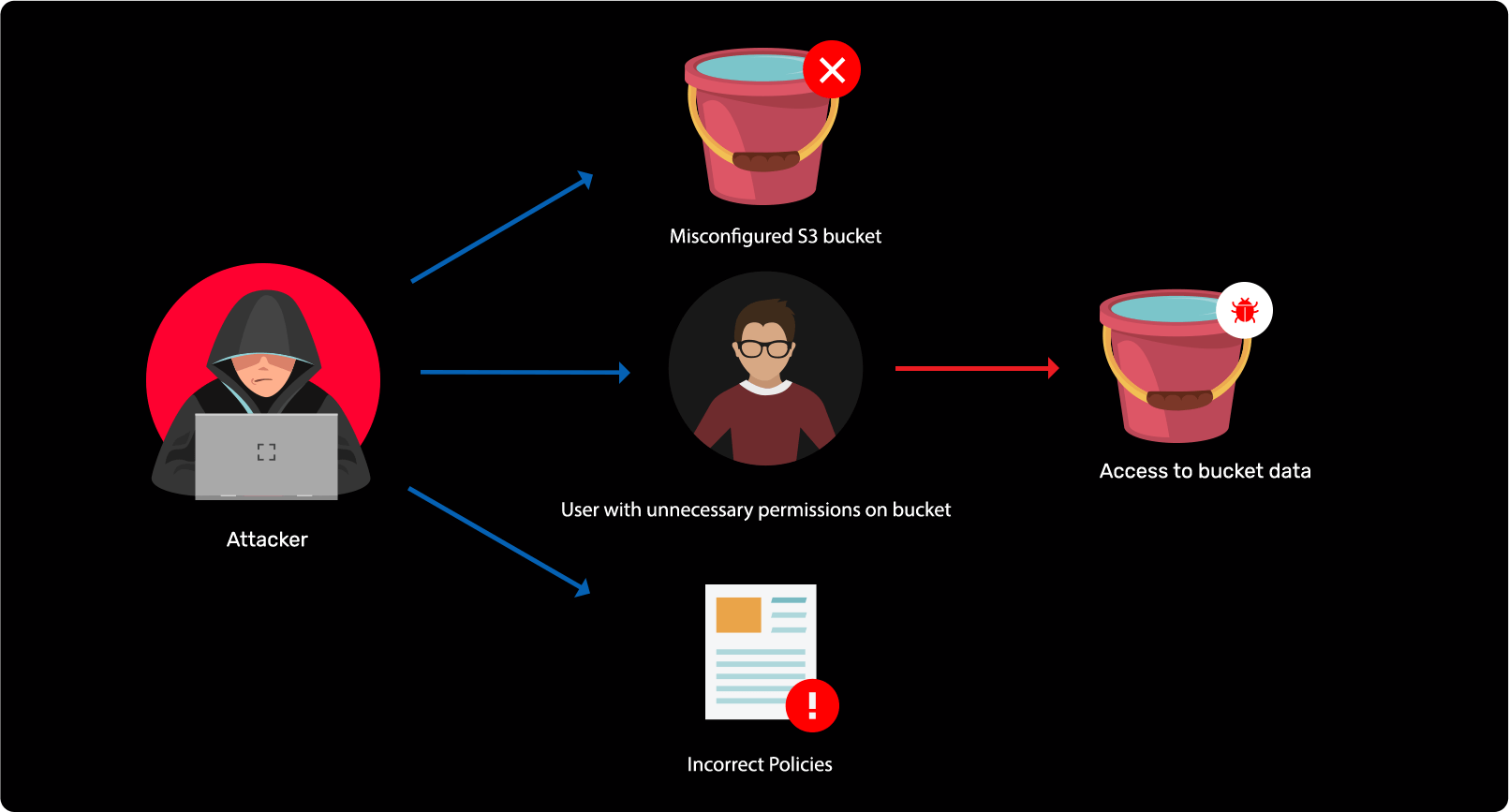
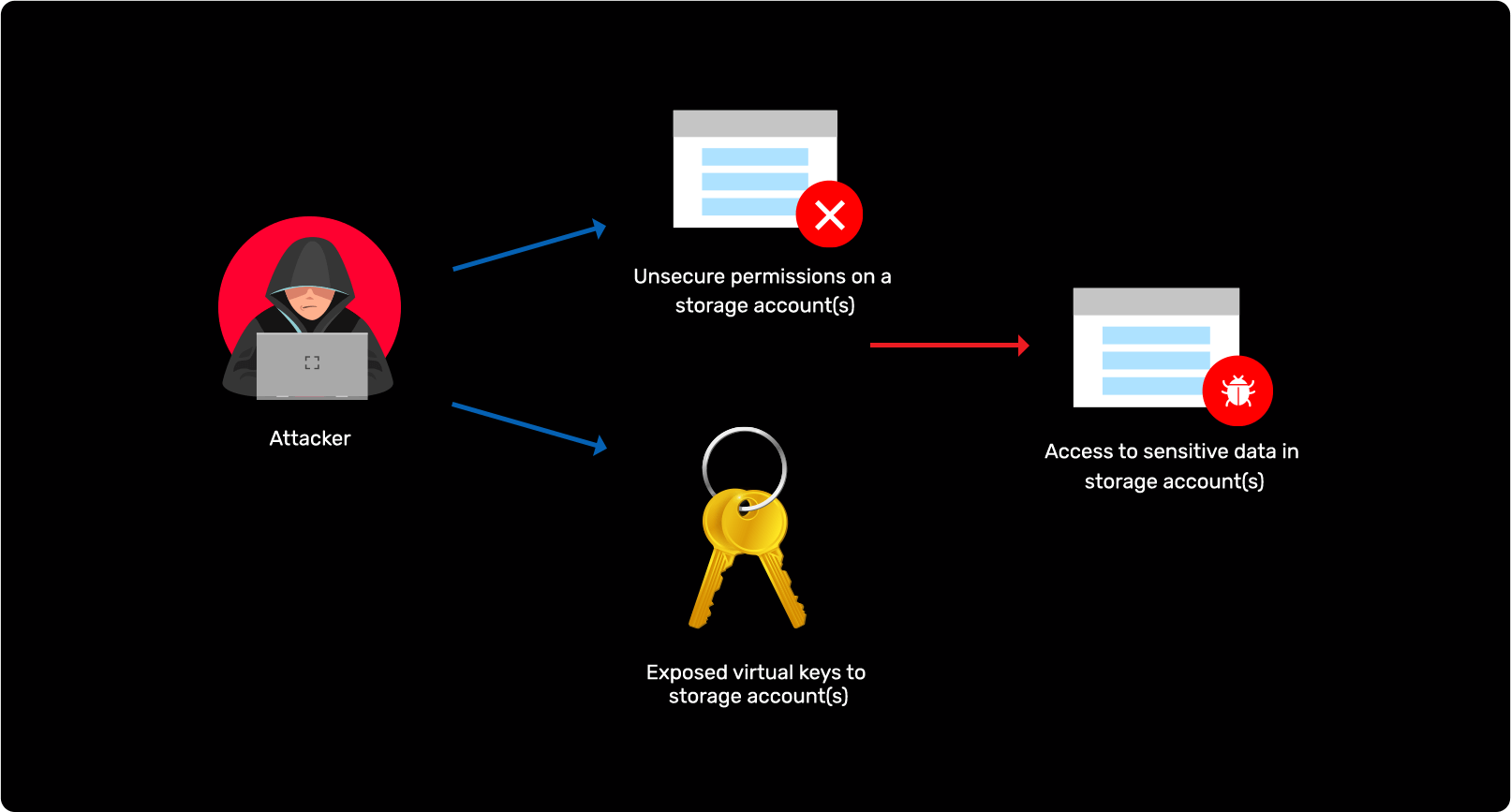
Storage attack in Azure and AWS
Learn more