Spot, analyze, and remediate threats
with one solution.
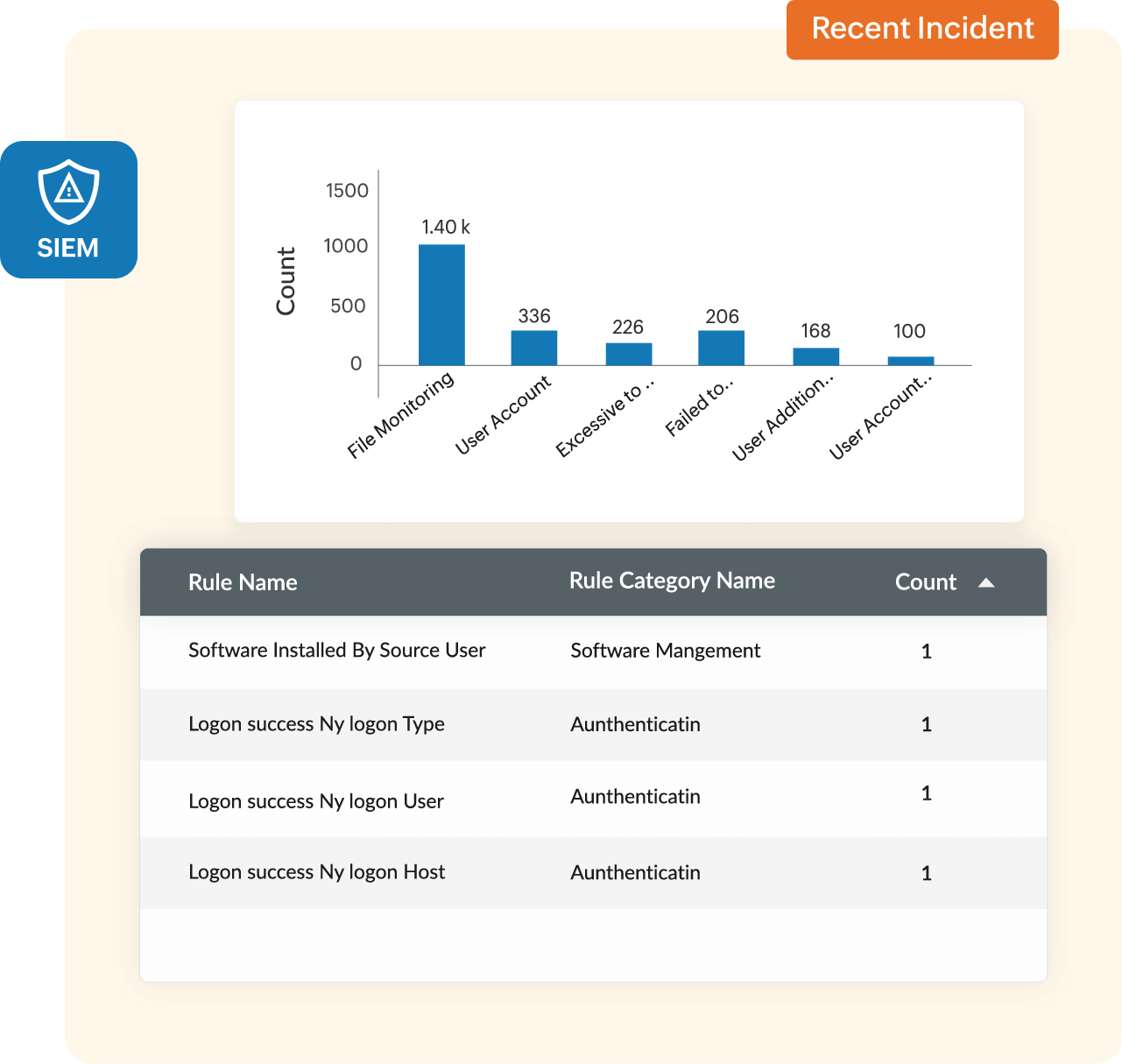
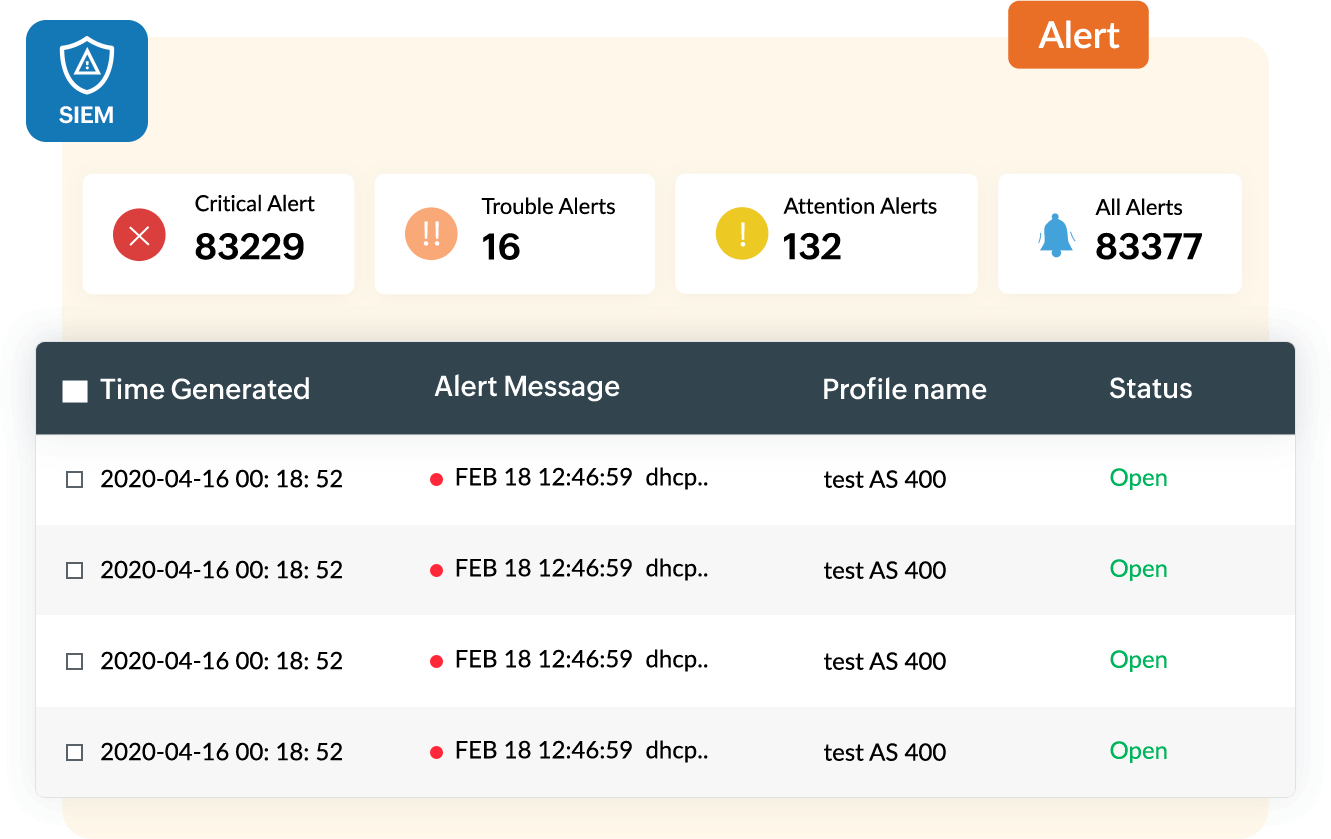
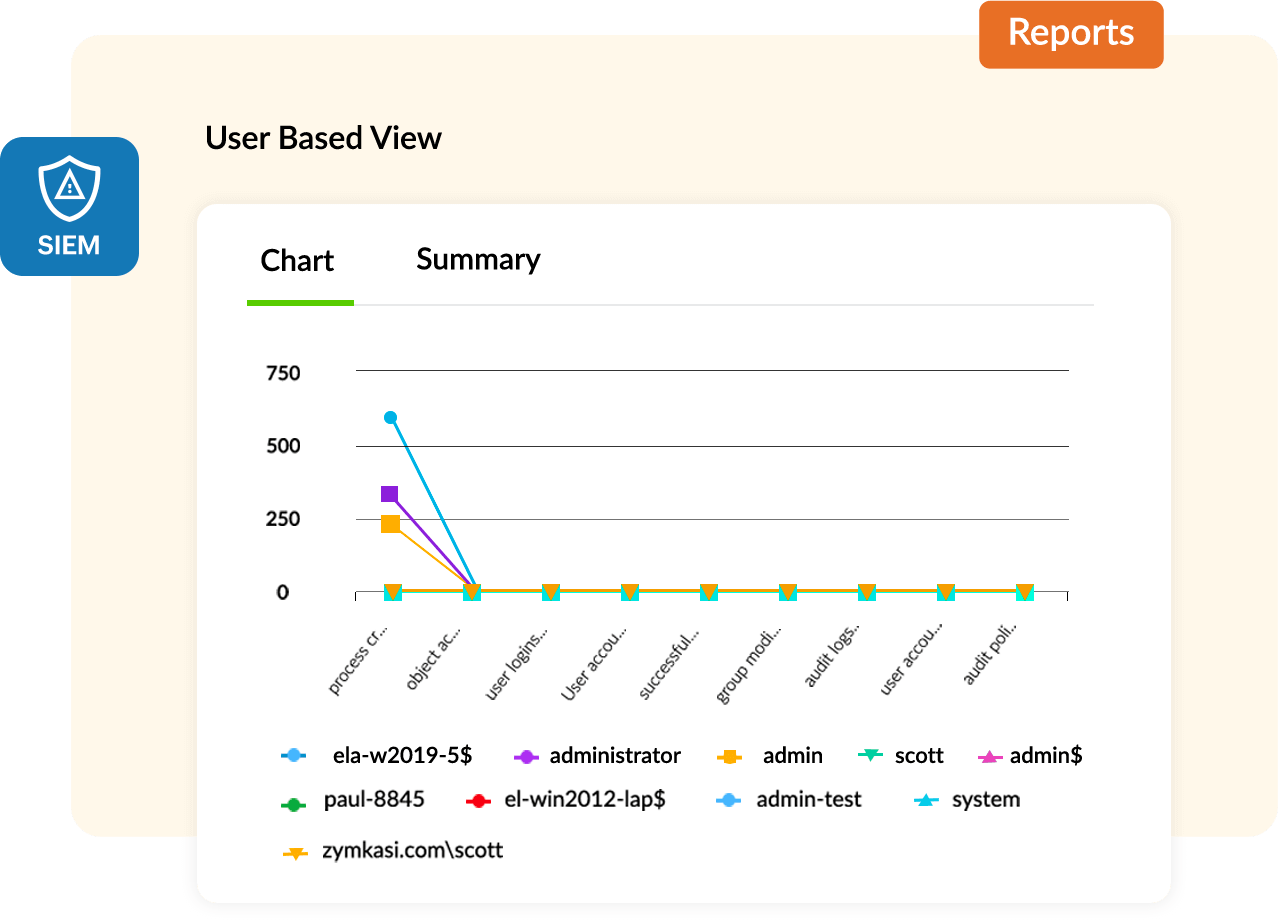
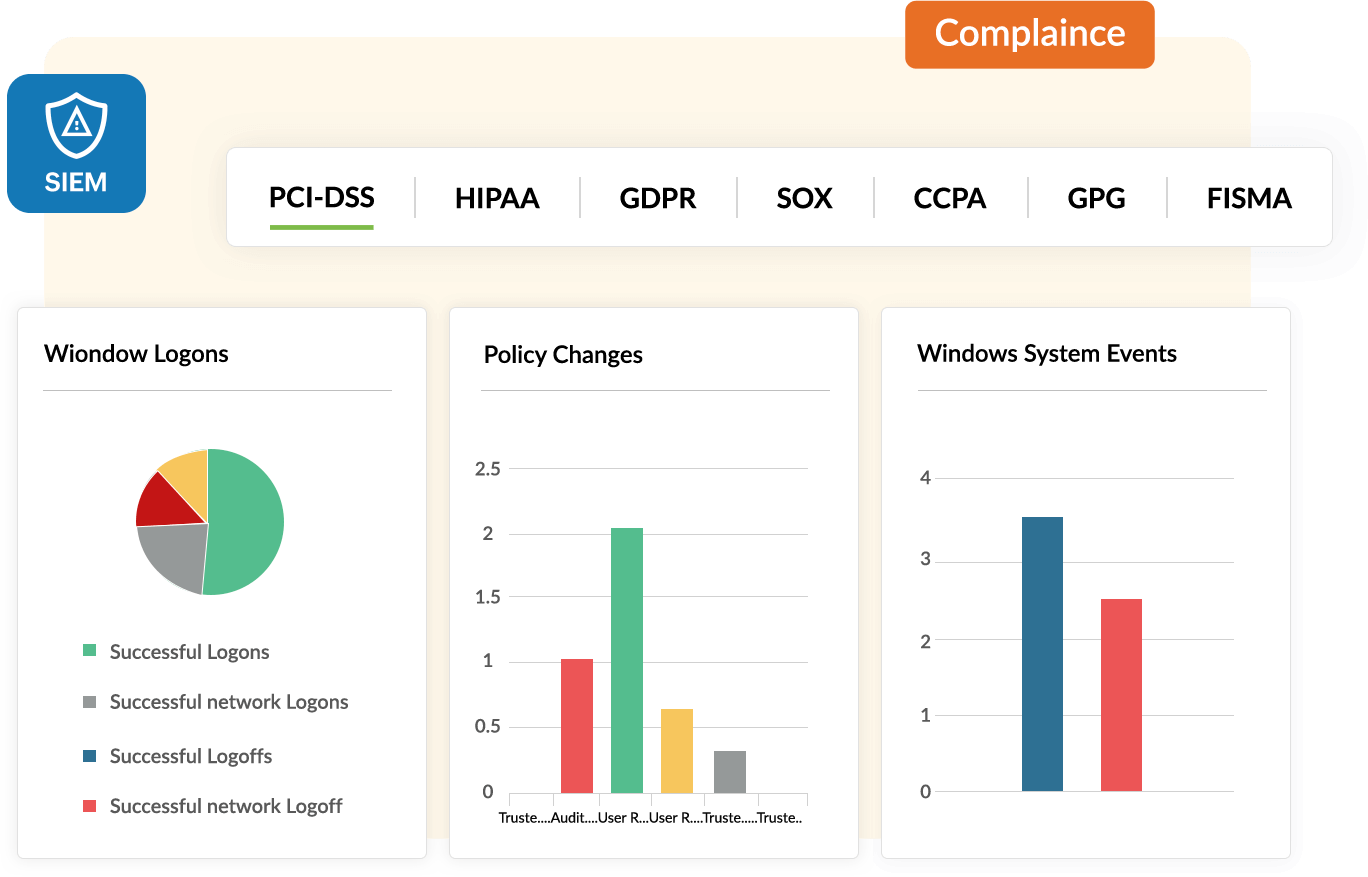
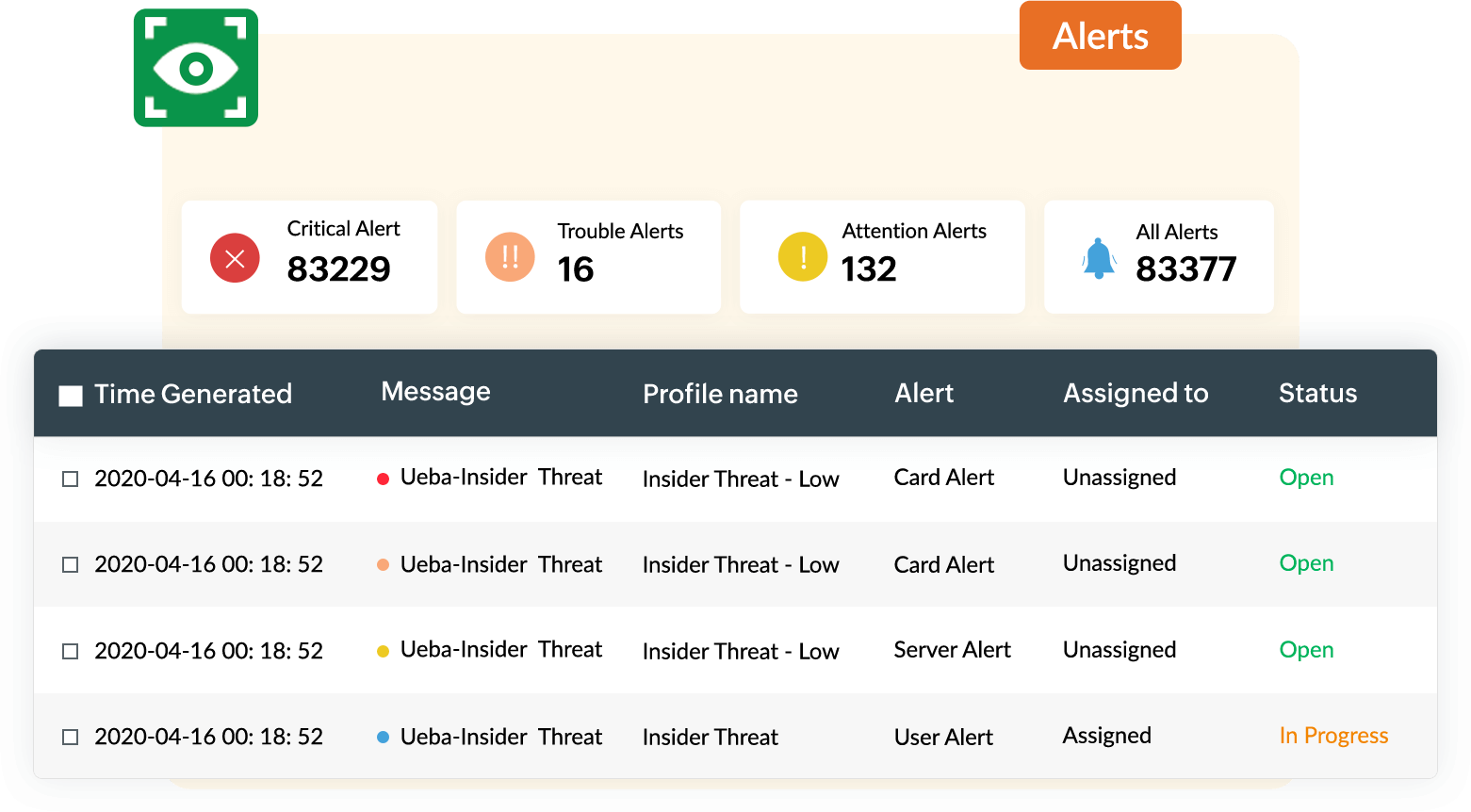
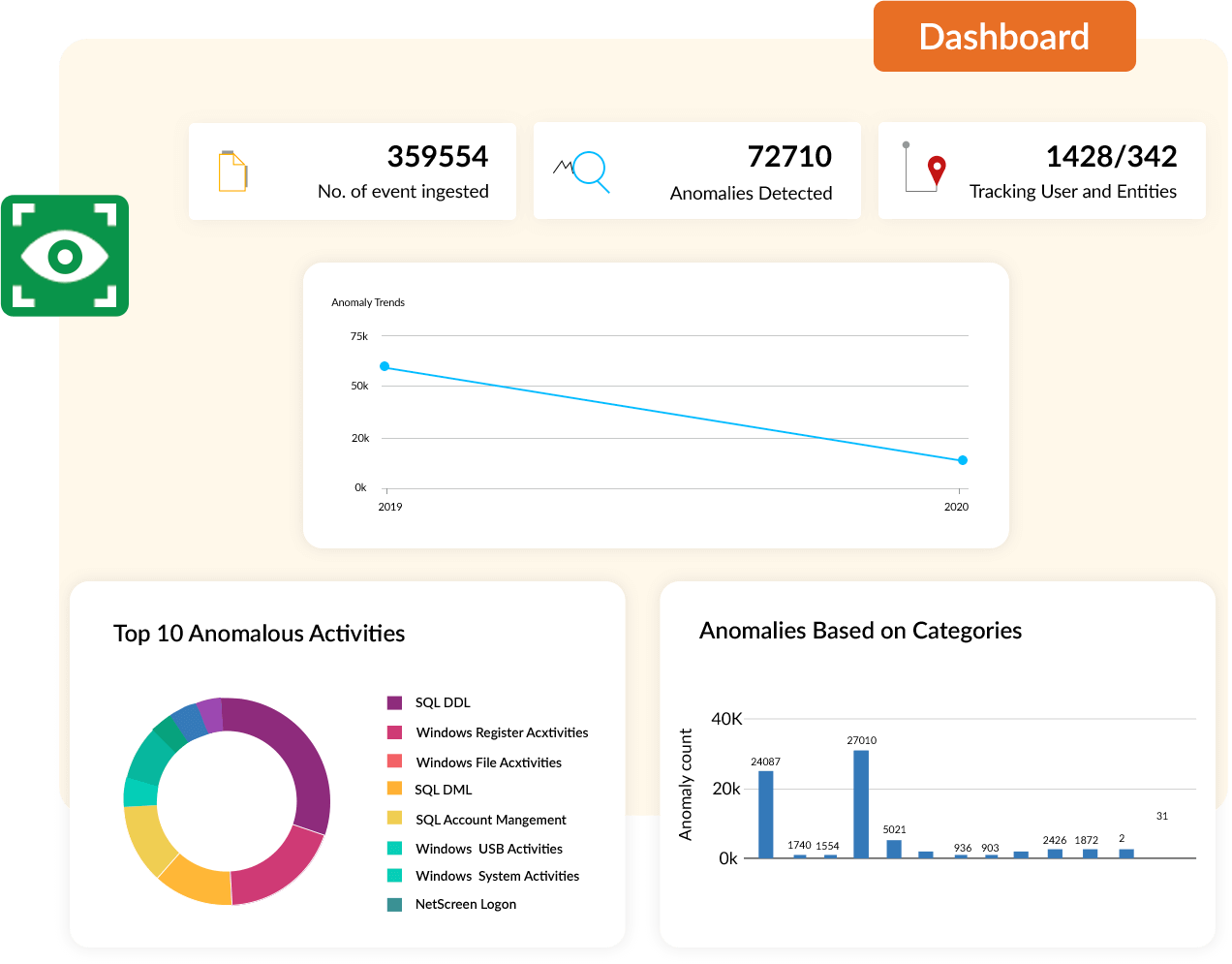
An enterprise's security operations center (SOC), which houses IT security professionals who monitor the enterprise's security posture, are responsible for tackling cyberattacks and simultaneously addressing regulatory compliance requirements. This is not a simple task, and is enough to keep the security team busy 24x7. If your team depends on a basic log management tool to collect, store, and search through logs, your organization is going to fall behind on security and may succumb to an attack.
Attackers are becoming more dangerous and regulatory mandates are continuously evolving, and basic tools just can't keep up. It's time to deploy a more sophisticated solution: security information and event management (SIEM). SIEM solutions have become an integral part of the network and data security ecosystem, and are critical in tackling advanced and targeted cyberattacks.