

Over 180,000 organizations across 190 countries trust
ManageEngine to manage
their IT.


Log360 is the best SIEM solution for your SOC
Mitigate security threats effectively by automating your incident response and creating incident workflows that sync with alerts. Speed up threat mitigation by integrating the process with ITIL solutions to ensure accountability for incident resolution.
Monitor all security events compiled from your Windows and Linux/Unix machines; IIS and Apache web servers; SQL and Oracle databases; and perimeter security devices such as routers, switches, firewalls, intrusion detection systems, and intrusion prevention systems in real time through interactive dashboards, out-of-the-box reports, and graphs.
Uncover security threats accurately with Log360's various techniques such as event log correlation, threat feed analysis to identify malicious IPs and URLs, and machine learning combined with user behavior analysis to identify insider threats.
Monitor and analyze your log data for security breaches, and meet regulatory compliance requirements with compliance reports for PCI DSS, FISMA, GLBA, SOX, HIPAA, ISO 27001, and more.
Find malicious actors and potential hidden attacks that have slipped through your initial security defenses by leveraging insights into attackers’ tactics, techniques, and procedures (TTP) and advanced threat analytics.
A risk score is calculated for each user and entity in the organization after comparing their actions to their baseline of regular activities. The risk score can range from anywhere between 0 to 100, indicating no risk to maximum risk, respectively. The risk score is dependent on factors such as the allotted weight of the action, the extent of the deviation from the baseline, the frequency of deviation, and the time elapsed since the deviation.
In addition to an overall risk score, each user and entity will also have an associated risk score for insider threats, account compromise, and data exfiltration. If the IT administrator feels an entity or user's risk score is too high, they can investigate it further and quickly stop any potential catastrophes.
Here are some activities that might increase the risk score of users and entities, indicating possible insider threats, account compromise, and data exfiltration.
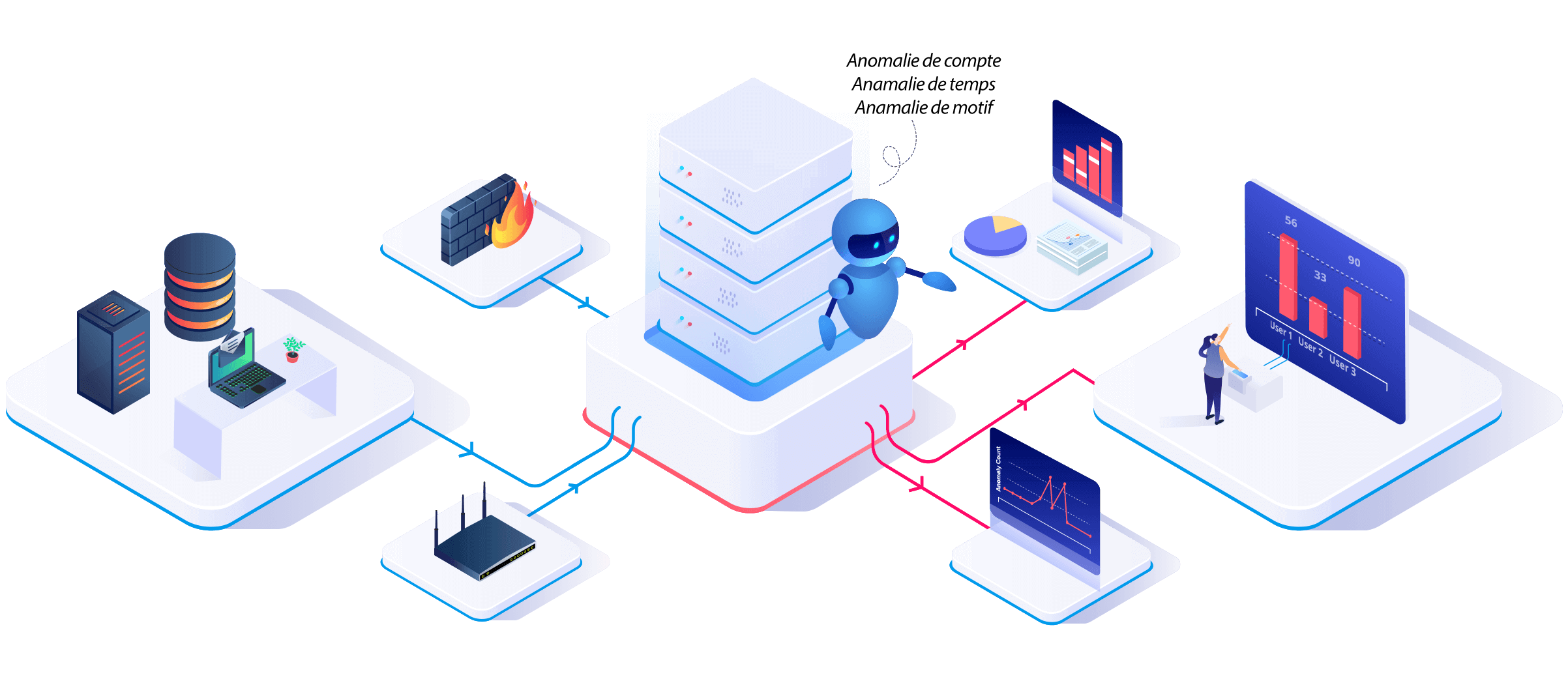
Log360 UEBA analyzes logs from different sources including firewalls, routers, workstations, databases, and file servers. Any deviation from normal behavior is classified as a time, count, or pattern anomaly.
CISCONet ScreenSophosPalo AltoWatch GuardWindows
CiscoHewlett Pakard
Windows 10Windows 8.1 Windows 8 Windows 7 Windows Vista Windows XP Prof. X64 ed. Windows XP
Window Server 2019 Window Server 2016 Window Server 2012 Window Server 2012 R2 Window Server 2008 Window Server 2008 R2 Window Server 2003 Window Server 2003 R2
OracleSQL ServerMy SQL
Windows Servers
Access to reports such as:
Logon reports File activities reports Logon failure reports Firewall changes reports Configuration changes reports
All the data used to generate the reports can be viewed in graphical form.
UEBA maintains a risk score for each and every user and entity profile. Whenever an activity log for a user/entity differs from its baseline, the risk score of that particular profile increases. An increased risk score of a profile helps the IT admin to look into the matter immediately to prevent any security breach.
Graphically represents the variations in the number of anomalies for a given time period.
2022. Zoho Corporation Pvt. Ltd. All Rights Reserved.