What is an insider threat?
An insider threat is any malicious or unintended security threat to an organization's data or information systems posed by an individual in the organization or operating inside the organization. A malicious insider is arguably more dangerous than an external hacker. There are three main reasons for this.
First, all of a company's sensitive data is within an arm's reach for an insider. Even if malicious insiders don't have privileged access to data, they may know what information to target, the location where it's stored, and how to obtain it.
Second, most companies trust their employees; so the malicious insider can easily slip under the radar. It might take a long time for the company to discover it was an insider that initiated the breach, because that's often the last person a company would suspect.
Third, malicious insiders have more opportunities to cover their tracks and hide their crime. Compared to an outsider, it's relatively easy for an insider to delete audit logs in Active Directory (AD); likewise, an insider doesn't need to breach any perimeter defenses to access the network.
How to prevent insider threats
To prevent insider threats:
- Implement AD hygiene by putting a Zero Trust and least privilege policy in place.
- Perform risk assessments at regular intervals to identify vulnerabilities.
- Monitor the behavior of all users and systems in real time, and look for indicators of insider threats.
- Look for anomalies in time, count, and patterns in the behavior of users and entities.
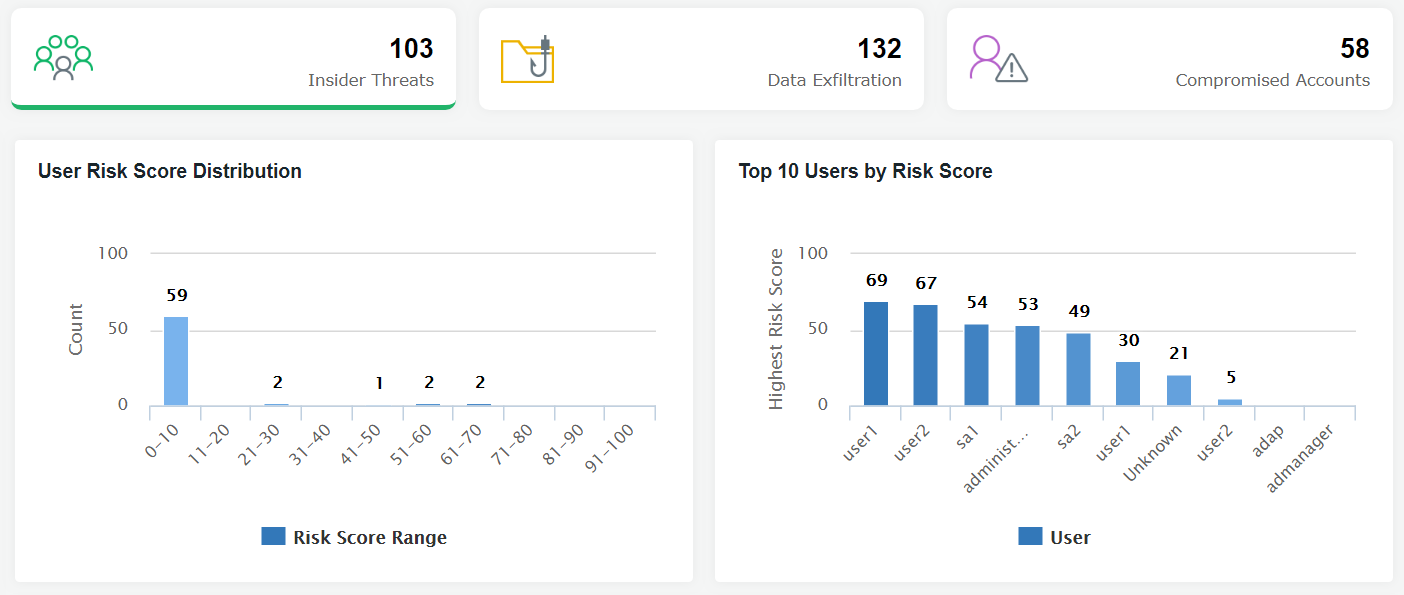
- Implement a system of risk scoring to detect the telltale signs of an insider attack.
- Put users with high risk scores for an insider threat in a watch list and monitor them closely.
- Develop a formal insider threat management program for your organization.