Thank You!
You can click and start reading the chapters from below. We've also sent the
link to
your inbox for future reference.
Grab your free e-book
included!Explore Now
Read Online
- 01Introduction
- 02Basic Windows auditing
- 03Advanced Windows Auditing
- 04Sysmon logging for Windows Security
- 05Registry auditing for Windows security
- 06Windows auditing mindmap included
- 07About Us
Why you need to log and audit Windows events
In 2019, it was reported that the Windows operating system was used on 72.1 percent of the servers worldwide. Most organizations today are predominantly Windows shop.
Windows auditing and log monitoring becomes inevitable when you want to ensure and maintain the cybersecurity posture of your network. However, this is often easier said than done.
In this vital resource, we'll elaborate on what you need to know about Windows auditing, including from login to what information you need to obtain from the logs, and how you can correlate the log details with other activities on your network to gain a holistic view of your security posture.
The basic Windows auditing policy specifies a set of security-related activities for evaluating critical events. In Windows, by default, the logging and auditing of events are disabled, but this auditing policy allows you to enable logging of certain events to gain visibility into the most common security activities happening in your network.
The following events are covered under the nine basic security auditing policies:
- 1. Account logon events
- 2. Account management
- 3. Directory services
- 4. Logon events
- 5. Object access
- 6. Policy changes
- 7. Privilege use
- 8. Process tracking
- 9. System events
From the different events suggested, you can enable auditing for specific events depending on the security needs of your organization. We’ve curated some of the basic events and mapped them with the use case it can resolve.
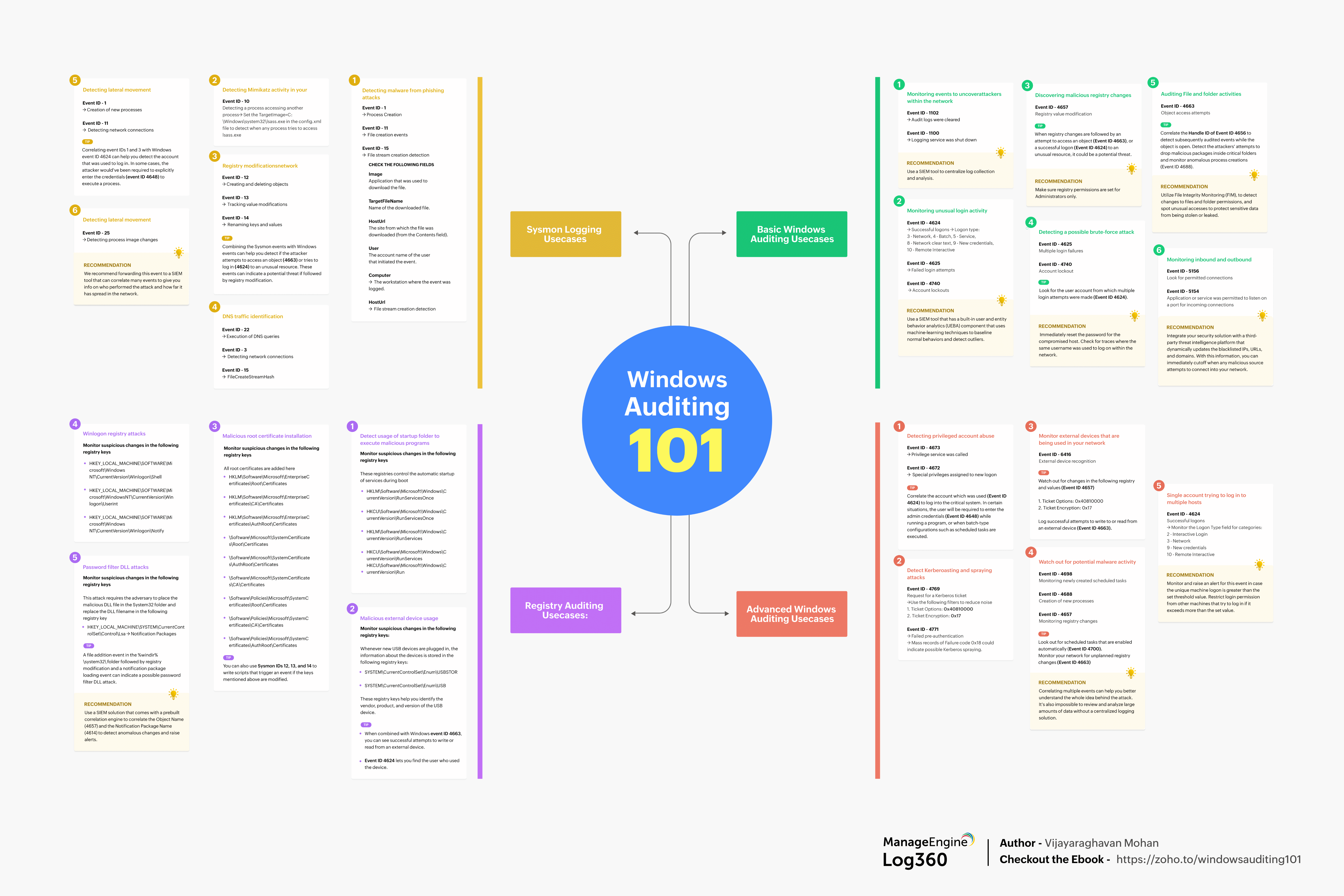
1. Events to look to uncover attackers within network
Intruders and impostors want to stay inside the network unnoticed. They try to cover up traces of their malicious operations and lateral movements. However, if you monitor closely, you can differentiate the trace deletions from legit actions. We recommend you enable auditing for these events and inspect them regularly to uncover threat actors in your network:
i. Audit log clearance
Platforms where this event can be logged and audited:
- Windows 2008 R2 and 7
- Windows 2012 R2 and 8.1
- Windows 2016 and 10
- Windows Server 2019
Look for the user account from which the logs were cleared. Gathering and investigating all the activities done by that user account will add more contextual data to evaluate the audit log clearance and help you determine if it's a legitimate activity or not.
ii. Shutting down the logging service
Platforms where this event can be logged and audited:
- Windows 2008 R2 and 7
- Windows 2012 R2 and 8.1
- Windows 2016 and 10
- Windows Server 2019
Unless this is a planned event for maintenance, it can indicate a possible cyberattack.
Tip: To gain clear and better visibility, look for the account which performed this operation (Event ID 4624) and from which machine the service was shut down. This gives you additional information that will help you differentiate the legitimate operation from the suspicious ones.
Our recommendation:
Use a security information and event management (SIEM) solution to collect, archive, and encrypt logs periodically. Centralized log collection also makes it easier to correlate and analyze the events happening in your network. Effective Windows log management also helps in resolving operational issues and troubleshoot critical failures.
2. Monitoring unusual login activity
Monitoring login activities can provide information on the anomalous activities happening within the network. For instance, User A logging in after work hours and trying to access protected information is subject to investigation. Multiple logins from the same account, a large number of login failures, and account lockouts are all common examples of unusual account activities. To monitor the login activities, enable auditing for these events:
i. Successful logons
Platforms where this event can be logged and audited:
- Windows 2008 R2 and 7
- Windows 2012 R2 and 8.1
- Windows 2016 and 10
- Windows Server 2019
The mode of logging in can give you clues to check the legitimacy of the attempt.
Monitor the Logon Type field for categories 3, 4, 5, 8, 9, and 10.
- 3 - Network: The user has logged in to the computer from somewhere else within the network.
- 4 - Batch: A process might be configured to execute on behalf of the user.
- 5 - Service: A service can be used to perform the login process.
- 8 - Network Clear Text: Transferring passwords in clear text format is dangerous as it could be sniffed to reveal. Avoid this logon type by protecting your network connection using encryption protocols like SSL/TLS or using VPN.
- 9 - New credentials: The user could have used different credentials to access any sensitive areas or execute admin-level commands (Runas) on the computer.
- 10 - Remote Interactive: Indicates that the logon was through Terminal Services or Remote Desktop. Could be a sign of lateral movement.
ii. Failing to log in
Platforms where this event can be logged and audited:
- Windows 2008 R2 and 7
- Windows 2012 R2 and 8.1
- Windows 2016 and 10
- Windows Server 2019
This event id is generated after every failed attempt regardless of the logon type. So you can easily check the type of logon used to access the system or resources. A massive spike in failure events within a short span may indicate a possible brute-force attack.
iii. Account lockouts
Platforms where this event can be logged and audited:
- Windows 2008 R2 and 7
- Windows 2012 R2 and 8.1
- Windows 2016 and 10
- Windows Server 2019
This happens when the user or attackers uses too many wrong passwords. Such events should always be followed up to check if it was legitimate.
Our recommendation:
Use a security tool to analyze the logon trends and user behaviors.Setup alerts to capture unusual logins including logins outside business hours, unusual volume of login failures and more. Most often, enterprises use a rule-based threat detection technique to spot malicious activities. However, the accuracy of differentiating a legitimate event from a suspicious one is relatively less in a rule-based or signature-based threat detection technique.
We recommend using a SIEM that has a built-in machine-learning based behavioral analytics component. User and entity behavior analytics (UEBA) modules use machine-learning techniques to baseline normal behaviors and then detect outliers. Often, they are also associated with risk management systems to validate the impact of a threat and reduce false positives to a greater extent.
For example, when Mark from the marketing department tries to access financial data, which he has never accessed, a high-risk score alert will be triggered, indicating a possible malicious action. By combining UEBA with automated incident response capabilities, you can take corrective actions such as restricting access to the user, or locking out the system.
3. Discover malicious registry changes
Attackers may try to modify the registry values to launch a malicious application or service during system startup. They can sometimes replace a whole registry or a particular key value in it to achieve this. One such example is the password filter DLL attack, where the hacker injects a malicious DLL file in the HKEY_LOCAL_MACHINE\ SYSTEM\ CurrentControlSet\ Control\ Lsa -> Notification Packages registry.
Monitoring registry changes lets you:
- 1. Capture unauthorized users or applications that change registry values.
- 2. Closely track privileged users registry activities to uncover privilege abuse and prevent malicious actions.
- 3. Ensure spot malware activity or suspicious changes to key registry values.
Here's a critical registry change event that you need to enable and monitor:
i. Registry value modification
Platforms where this event can be logged and audited:
- Windows 2008 R2 and 7
- Windows 2012 R2 and 8.1Windows 2016 and 10
- Windows 2016 and 10
- Windows Server 2019
Enable registry auditing and alerting on systems containing high-value data, domain controllers, and servers. Take regular backups of the registries in case anything goes wrong.
Tip: When registry changes are followed by an attempt to access an object (Event ID 4663), or a successful logon (Event ID 4624) to an unusual resource, it could be a potential threat. Use your security solution to correlate registry changes with critical follow-up actions to spot threats early and stop them from causing damage.
Our recommendation:
Make sure registry permissions are set for Administrators only and monitor key registries for malicious actions.
4. Detecting a possible brute-force attack
Brute force is a technique used by adversaries trying to input hundreds and thousands of username and password combinations within a short period, hoping to get one right. There are lots of tools to automate this process. With the help of these Windows events, you can perform basic brute force attack detection.
i. Multiple login failures
Platforms where this event can be logged and audited:
- Windows 2008 R2 and 7
- Windows 2012 R2 and 8.1
- Windows 2016 and 10
- Windows Server 2019
To spot brute-force attacks, look for multiple logon failures within a short period, and at least one successful logon from the same source.
Tip: Though signature-based brute force detection is helpful, it can be misleading and provide false alarms. Advanced behavioral analytics powered by machine-learning techniques can accurately spot unusual volume of logon failures baselining with regular activity. When coupled with automatic remediation responses, it can immediately take corrective actions, such as locking the system or cutting off communication from malicious sources, thus saving time and preventing damage.
ii. Account lockout
Platforms where this event can be logged and audited:
- Windows 2008 R2 and 7
- Windows 2012 R2 and 8.1
- Windows 2016 and 10
- Windows Server 2019
This happens when the user or attackers uses too many wrong passwords.
Tip: Look for the user account from which multiple login attempts were made (Event ID 4624). This can help you find which account was compromised, the permissions that the account has, etc. Using this you can restrict access permissions to the compromised account before major damage.
Our recommendation:
Immediately reset the password for the compromised host. Check for traces where the same username was used to log on within the network.
Adjust the threshold if you have a single point of authentication.
5. Watch out for file and folder activities
When adversaries gain access to your network, they want to drop malware packages like ransomware, or exfiltrate sensitive data and sell it on the dark web. A sudden spike in access requests to certain databases may indicate a potential breach. These are some of the events that you must log and audit to spot suspicious file and folder changes:
i. Attempting to access objects
Platforms where this event can be logged and audited:
- Windows 2008 R2 and 7
- Windows 2012 R2 and 8.1
- Windows 2016 and 10
- Windows Server 2019
This event id is generated when an object is accessed. The object can be a file, kernel system, registries, or files present on a removable disk. It is recommended that you set alerts to determine if anyone tries to access any object in protected servers.
Tip: Hackers will attempt other attacks if they don't get what they want. To thwart them, correlate the Handle ID of Event ID 4656 to detect subsequently audited events while the object is open. You can also detect the attackers' attempts to drop malicious packages inside critical folders by monitoring anomalous process creations (Event ID 4688).
Our recommendation:
Utilize File Integrity Monitoring (FIM), a critical capability that can detect changes to files and folder permissions, and spot unusual accesses to protect sensitive data from being stolen or leaked.SIEM solutions come with this built-in capability. If your organization is storing or processing sensitive data at large volumes or is liable to comply with any of the regulatory mandates, such as PCI-DSS, HIPAA, GDPR, and others, we recommend you to go for the tool with embedded FIM capability to protect your network from security breaches.
6. Watch out inbound and outbound connections
Monitoring the traffic from and to the network adds contextual information to your threat hunting process. Connection details available in log data such as the source IP address and its location provide clear visibility of what's happening in your network when trying to detect security threats or attack attempts. When this information is correlated with other events, it helps you to identify the compromised systems, lateral movement of adversaries, malicious packages that are dropped into your network, and more. Therefore, it becomes essential for you to log and closely monitor the inbound and outbound connections. These are some of the events that you must log to conduct security auditing:
i. Look for permitted connections
Platforms where this event can be logged and audited:
- Windows 2008 R2 and 7
- Windows 2012 R2 and 8.1
- Windows 2016 and 10
- Windows Server 2019
This event id is generated whenever the Windows Filtering Platform allows an inbound or outbound connection. Since this is a high-volume event, we recommend auditing only if every network connection to a server or application needs to be tracked. For example, a browser connecting to the internet versus PowerShell making an outbound connection.
ii. An application or service is permitted to listen on a port for incoming connections
Platforms where this event can be logged and audited:
- Windows 2008 R2 and 7
- Windows 2012 R2 and 8.1
- Windows 2016 and 10
- Windows Server 2019
Our recommendation:
When a connection from or to a malicious source is being established, it should be immediately cut-off. To do this, you need a list of blacklisted IP addresses, URLs, and domains. Unfortunately, such threat feeds are dynamic and constantly changing.
The ideal way is to either have a built-in threat intelligence platform in a SIEM tool or to integrate your security solution with a third-party threat intelligence platform. These threat intelligence solutions have a list of all blacklisted and malicious sources that are updated dynamically. Further, they also provide you with a reputational score that helps you determine the trustworthiness of a site, geo-location of a malicious source, and more.
Windows Advanced Auditing Policy overlaps with the basic Windows auditing policies stated above. However, these are recorded and applied differently. Advanced auditing empowers administrators to be more selective in the number and types of events to audit.
For instance, if you enable success auditing for the basic Audit account logon events, success events for all account logon-related behaviors will be logged. However, with advanced auditing policy, administrators can select only the behaviors they want to monitor and exclude audit results for behaviors that are not important. Administrators can enable success events for one subcategory of account logon category, failure events for another subcategory, and choose to not audit the rest of the subcategories. Such granular control over audit policy largely reduces noise and false positives while spotting security threats.
We've mapped a few events that you need to monitor and that fall under the advanced auditing policy, with the security use case it can detect.
1. Detecting privileged account abuse
An attacker will not always end up with an account with higher levels of access. So they will try to elevate the level of access of any account they get their hands on. They also try to access privileged user accounts to take control of the entire network. Therefore, we need to monitor for unauthorized privilege access attempts.
Analyzing the following events will provide insights into privilege abuses.
i. Privileged service was called
Platforms where this event can be logged and audited:
- Windows 2008 R2 and 7
- Windows 2012 R2 and 8.1
- Windows 2016 and 10
- Windows Server 2019
This event id is generated when SeSystemtimePrivilege, SeCreateGlobalPrivilege, or SeTcbPrivilege is called. You can have a list of allowed and denied user rights or process names and trigger alerts for misuse of "Privileges" and "Process Name" fields.
Platforms where this event can be logged and audited:
- Windows 2008 R2 and 7
- Windows 2012 R2 and 8.1
- Windows 2016 and 10
- Windows Server 2019
Monitor this event with the “Subject\Security ID” or “Account Whose Credentials were Used\Security ID” that correspond to the accounts that indicate malicious actions.
Tip: Correlate the account which was used to login (Event ID 4624) to the critical system. In certain situations, the user will be required to enter the admin credentials (Event ID 4648) while running a program, or when batch-type configurations such as scheduled tasks are executed.
You should also check if the user has logged in outside the authorized hours or used an unauthorized workstation to do it (Event ID 4776).
Correlate the file and folder changes (Event ID 4663) which are immediately followed by privileged access attempts.
Our recommendation:
You can use these event ids to track pass-the-hash attacks. But it is not easy to detect lateral movement from such attacks. A SIEM solution with UEBA capabilities can correlate many events to keep a risk score of the accounts in the network. When the set threshold value is reached, alerts will be raised.
2. Detect Kerberoasting and spraying attacks
In Kerberoasting attacks, the service account credential hashes are extracted from Active Directory for offline cracking. This attack is very effective when people create poor passwords.
Every Kerberos ticket is stored with AES128-CTS-HMAC-SHA1-96 encryption (from Windows Server 2008 and Vista). Attackers request Kerberos service tickets which are then exported for decryption. Different New Technology Local Area Network Manager (NTLM) hashes are used to do this, and once the ticket is successfully opened, the correct service account password is discovered.
i. Request for a Kerberos ticket
Platforms where this event can be logged and audited:
- Windows 2008 R2 and 7
- Windows 2012 R2 and 8.1
- Windows 2016 and 10
- Windows Server 2019
Attackers may request hundreds of service tickets hoping to find the password in any one of them. So lookout for a spike in requests for service tickets.
Use the following filters to reduce noise
- 1. Ticket Options: 0x40810000
- 2. Ticket Encryption: 0x17
ii. Failed pre-authentication
Platforms where this event can be logged and audited:
- Windows 2008 R2 and 7
- Windows 2012 R2 and 8.1
- Windows 2016 and 10
- Windows Server 2019
This event is generated every time the key distribution center fails to issue a Kerberos ticket-granting ticket (TGT). Look for mass records of Failure code 0x18 which could indicate possible Kerberos spraying.
Our recommendation:
1. Strengthen passwords: Implement a strong password policy in your organization, especially for service accounts.
2. Deploy honeypots: You can set traps with honey accounts to serve as decoy targets for attackers, and trigger alerts when they are used to generate a service ticket.
3. Continuously monitor: Monitor the service accounts for anomalous activity. UEBA uses machine learning to keep track of the risk score or all the objects in your network. When the threshold is reached, alerts will be triggered instantly so that you can respond immediately.
3. Monitor external devices that is being used in your network
Sometimes rogue employees might try to steal information using external storage devices. The main purpose of USB device analysis is to identify the devices connected to your network and monitor the usage metrics—files copied to or from the device, connection time, etc.
i. External device recognition
Platforms where this event can be logged and audited:
- Windows 2016 and 10
- Windows Server 2019
This event id can be used in servers or networks where important information is stored. Set alerts for this event whenever the Subject\Security ID field is not SYSTEM.
Tip: Watch out for changes in the following registry and values (Event ID 4657):
- 1. Ticket Options: 0x40810000
- 2. Ticket Encryption: 0x17
Log successful attempts to write to or read from an external device (Event ID 4663).
Our recommendation:
Since this event is used to track anomalous usage of external devices, a SIEM tool with UEBA functionalities can be used to detect malicious behavior. This feature correlates several events to keep a risk score of the objects in the network. When the set threshold value is reached, alerts will be raised.
4. Watch out for potential malware activity
Malwares use scheduled tasks to perform malicious actions after they enter the network. They are also used to maintain a presence in the network by installing backdoors or remote access tools to enter effortlessly after every reboot.
i. Monitoring newly created scheduled tasks
Platforms where this event can be logged and audited:
- Windows 2008 R2 and 7
- Windows 2012 R2 and 8.1
- Windows 2016 and 10
- Windows Server 2019
Tip: Monitor the Task Scheduler Library root node for new tasks and raise an alert if the Task Content: XML contains <LogonType>Password<LogonType> value. This code can be used by attackers to extract the password of the account with which the scheduled task was created.
ii. Creation of new processes
Platforms where this event can be logged and audited:
- Windows 2008 R2 and 7
- Windows 2012 R2 and 8.1
- Windows 2016 and 10
- Windows Server 2019
Every malware can execute a code by creating a new process, once it's inside the network. This process will automatically launch depending on the attack type (sometimes days or months after infiltration).
By tracking this event id 4688, you can trace the instances of the malware processes, and find possible spreading to other devices in the network.
iii. Monitoring registry changes
Platforms where this event can be logged and audited:
- Windows 2008 R2 and 7
- Windows 2012 R2 and 8.1
- Windows 2016 and 10
- Windows Server 2019
This event id lets you capture unauthorized processes that change registry values and spot malware activity or suspicious changes to key registry values. Enable auditing and alerting on systems containing high-value data, domain controllers, and servers. Take regular backups of the registries in case anything goes wrong. Know more about tracking registry modifications.
- Tip: Find the user who started the process, modified the registry, or created the scheduled task (Event ID 4624).
- Look out for scheduled tasks that are enabled automatically (Event ID 4700). These tasks created by the adversaries could be configured to launch days or months after the initial creation.
- Look for registry changes (Event ID 4663).
Our recommendation:
Correlating multiple events can help you better understand the whole idea behind the attack. It's also impossible to review and analyze large amounts of data without a centralized logging solution. We recommend you use a SIEM tool that centrally collects the logs to make it easier for defenders to perform mitigation activities easily.
5. Single account trying to log in to multiple hosts
Most users log in to one or two systems during a typical day. But user accounts that try to log in from different machines may indicate compromise. Remote logins can indicate possible lateral movement.
i. Successful logons
Platforms where this event can be logged and audited:
- Windows 2008 R2 and 7
- Windows 2012 R2 and 8.1
- Windows 2016 and 10
- Windows Server 2019
Monitor the Logon Type field for categories 2,3,9, and 10.
2 - Interactive Login: Indicates a user logged into the system by using the keyboard.
3 - Network: The user has logged in to the computer from somewhere else within the network.
9 - New credentials: The user could have used different credentials to access any sensitive areas or execute admin-level commands (Runas) on the computer.
10 - Remote Interactive: Indicates that the logon was through Terminal Services or Remote Desktop.
Our recommendation:
Monitor and raise an alert for this event in case the unique machine logon is greater than the set threshold value. Restrict login permission from other machines that try to log in if it exceeds more than the set value.
Sysmon (System Monitor) is a Windows system service and device driver that comes as a part of Windows Security utlities and logs events to Windows event logs. Sysmon logs provide information on process creation, network connection, and changes to file creation time.
Some Sysmon log information and regular Windows event information overlap. However, Sysmon logs possess below additional information that differentiates it in security auditing.
Sysmon logs:
- 1. Provide information on both current and parent processes.
- 2. Record the hash of process image files using SHA1, MD5, SHA256, or IMPHASH.
- 3. Include information on the process GUID, which acts as a unique parameter allowing correlation of Windows events that reuses the process IDs.
- 4. Include the session GUID, which acts as a unique parameter for session monitoring and correlating different events occurring on the same logon session.
- 5. Provide details on the loading of drivers or DLLs.
- 6. Help detect changes in file creation times to understand when a file was actually created.
As you can see, Sysmon logs provide critical details that help you to hunt down security threats effectively and proactively.
Below, we'll look at what kind of threats can be detected or prevented by monitoring specific Sysmon events.
Tip: Sysmon logs can be found in the Sysmon folder: Applications and Services Logs > Microsoft > Windows > Sysmon.
Sysmon doesn't have built-in analytics capabilities. All it does is generate logs for specific events. You need a security information and event management (SIEM) solution or at the minimum a Windows event collection and analysis tool to get actionable insights from Sysmon logs.
1. Detecting malware from phishing attacks
Phishing is one of the most commonly used techniques to break into a corporate network. Phishing scams are often used to drop malicious programs in the network that can cause data breaches or launch ransomware attacks.
Attackers may send bulk emails to employees to trick them into initiating malicious processes. Once the process or task is created, the attacker can compromise accounts, exfiltrate data, or laterally move within the network to exploit other systems. Sysmon analysis helps spot and contain malware at the earliest stages.
Process Creation - Event ID 1
Just like Windows event ID 4688, Sysmon event ID 1 tracks all the newly created processes along with when they are terminated. But this Sysmon event gives you more information on the parent process ID, location of the parent process, and more. This helps with tracking the process hierarchy, which comes in handy during forensic investigations.
Attackers send malicious files or links in the emails that can download payload data onto your systems when executed. This payload can then be used to:
- 1. Find credentials.
- 2. Download additional malware.
- 3. Encrypt files in the network.
File creation events - Event ID 11
The most critical resources needed for a system to function properly are stored in the C drive. Attackers can drop malware in this drive, so that it gets loaded along with the boot files during startup.
This event detects file creation in places inside the C drive, like temporary, and download folders where malware can be configured to create files when needed.
File stream creation detection - Event ID 15
Each downloaded file from the web is tagged with a Zone.identifier tag by the browser. This tag contains information on the zone from which the file originated and the URL from which it was downloaded.
The Zone ID values indicate different sources, such as:
- 0 - Local computer
- 1 - Local intranet
- 2 - Trusted sites
- 3 - Internet
- 4 - Restricted sites
This information can be used to trigger security responses on the downloaded files.
Event ID 15 is generated whenever a file stream is created and contains the following data:
- Image - Application that was used to download the file.
- TargetFileName - Name of the downloaded file.
- HostUrl - The site from which the file was downloaded (from the Contents field).
- User - The account name of the user that initiated the event.
- Computer - The workstation where the event was logged.
2. Detecting Mimikatz activity in your network
Tools such as Mimikatz are used by malicious actors to extort credentials from the memory. These tools can extract passwords, hashes, Kerberos tickets, and more.
When installed into your system, the tool (Mimikatz), which is started as a process, accesses credential storage areas such as lsass.exe to dump the credentials. It is difficult to detect such activities with Windows log auditing because the parent process isn't known. Therefore, Sysmon analysis provides better visibility and helps connect different events to stop the attackers at their initial stages.
Detecting a process accessing another process - Event ID 10
Set the TargetImage=C:\Windows\system32\lsass.exe in the config.xml file to detect when any process tries to access lsass.exe.
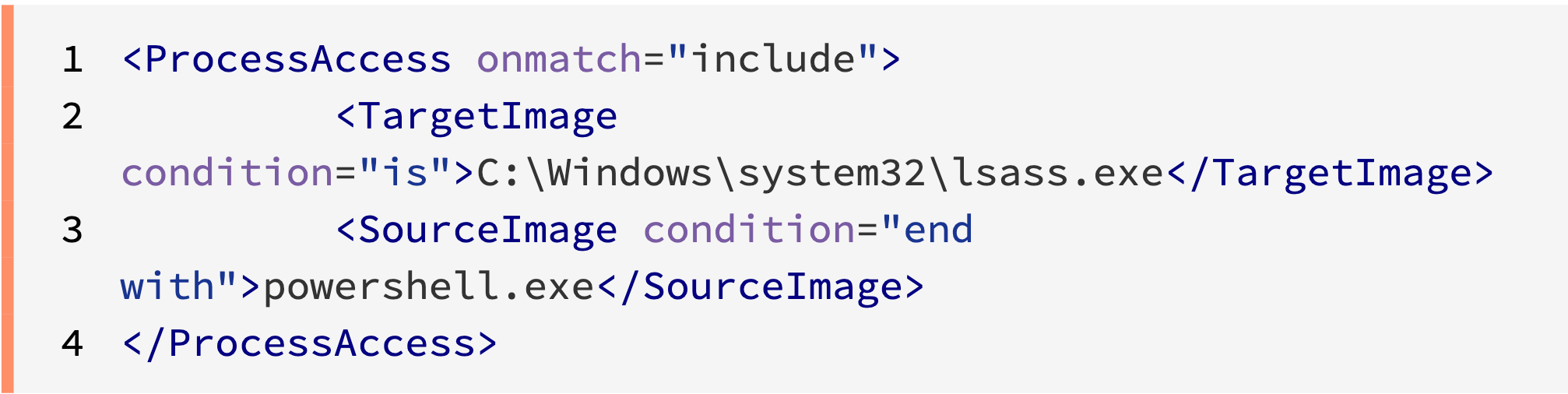
Look for Sysmon logs with the event ID 10.
3. Registry modifications
Attackers may try to modify the registries to launch a malicious application or service during system startup. They can sometimes modify a whole registry or a particular key value in it to achieve this. One such example is the password filter DLL attack, where the hacker injects a malicious DLL file in the HKEY_LOCAL_MACHINE\ SYSTEM\ CurrentControlSet\ Control\ Lsa > Notification Packages registry.
So, you need to monitor registry changes as they can help you:
- 1. Capture unauthorized processes that change registry values.
- 2. Track privileged accounts and prevent malicious actions.
- 3. Spot malware activity or suspicious changes to key registry values.
Here are some sysmon events that you need to monitor:
Creating and deleting objects - Event ID 12
This event tracks the key and value creation or deletion operations of specific registries.
Tracking value modifications - Event ID 13
This event ID tracks registry value changes made by attackers.
Renaming keys and values - Event ID 14
This event tells you when the registry keys and values are renamed along with the new name given to it.
Tip: Combining the Sysmon events with Windows events can help you detect if the attacker attempts to access an object (4663) or tries to log in (4624) to an unusual resource. These events can indicate a potential threat if followed by registry modification.
4. DNS traffic identification
Attackers may use the application layer protocols to avoid detection by blending in with regular traffic. Using these protocols they can send commands to the Command and Control servers to drop payloads or exfiltrate data. One of the places you need to monitor for anomalous behavior is DNS traffic.
Execution of DNS queries - Event ID 22
This event ID is generated whenever a process executes a DNS query. You can use this event ID to check the process origin and the final query executed by the process. This event ID is supported only on Windows 8.1 and later.
Detecting network connections - Event ID 3
This event ID is generated whenever there is a TCP/UDP connection on the machine. You can use both Event ID 22 and 3 to check for DNS queries.
This event ID gives you information on the image being used, port name, and destination address. For example, if you see a process accessing a server using an SSH port, it could be malicious.
Tip: For more context, correlate event IDs 22 and 3 with the following event.
FileCreateStreamHash - Event ID: 15
This event can be correlated with event ID 22 to see the name of the file they downloaded and the source URL. The hash provided from this event ID can be used to check if the same operation was done on any other system in the network.
5. Detecting lateral movement
Detecting lateral movements in your network can be a challenging task. When attackers gain admin privileges, it becomes especially difficult to differentiate malicious actions from legitimate ones. With a SIEM solution capable of Sysmon monitoring, you can quickly detect attempts to move laterally.
Creation of new processes - Event ID 1
Once the attacker gains access to a host, they can spread malware to other devices by using trusted Windows tools like PsExec. They might also change the name of the executable to evade detection. For example, they can rename their executed process to PsExec.exe, which will remain undetected if you had set alerts for the original process name.
Event ID 1 retains the original metadata (OriginalFileName) of the executable to give you the opportunity to get alerts upon attempts to evade detection by renaming processes.
Detecting network connections - Event ID 3
Attackers may try to connect to critical servers once they get access to a system in the network. A standard user trying to connect to a server to which they don't have access is a suspicious event. This event ID tracks all the TCP/UDP connections on the machine. Using the source and destination hostnames and IP addresses, you can find out which system was compromised.
Tip: Correlating the above mentioned events with Windows event ID 4624 can help you detect the account that was used to log in. In some cases, the attacker would've been required to explicitly enter the credentials (event ID 4648) to execute a process.
You can also implement a SIEM tool with UEBA capabilities to detect lateral movement. UEBA tracks the activity of each user object in your environment to assign risk scores. Alerts will be raised when the set risk score is reached.
6. Detecting process tampering
Attackers have been using techniques like process hollowing and herpaderping to execute malicious code masked under legitimate processes.
Process Hollowing - A technique that deallocates legitimate code in a trusted Windows process and then replaces it with a malicious code when needed. This malicious code will now run under a legitimate Windows process.
Process Herpaderping - This is a technique where the contents of the process are modified after the image is mapped. This makes the process appear harmless to the user while a malicious process runs in the memory. For example, Mimikatz can be executed under chrome.exe, making it appear to the OS that a trusted process is running with a valid Google signature.
Detecting process image changes - Event ID 25
Process hallowing has been around for years. But herpaderping is a relatively new and powerful approach used to remain undetected if auditing is not enabled.
This event detects the process hiding techniques explained above. The Image field in this event ID gives you info on the process that was tampered with.
We recommend forwarding this event to a SIEM tool that can correlate many events to give you info on who performed the attack and how far it has spread in the network.
Tuning Sysmon config.xml
Since Sysmon auditing is noisier than Windows auditing, it's a best practice to decide on the files and folders you want to include and exclude from monitoring, and keep the file length to a minimum. This reduces management issues and helps you collect only the things you really need. This event filtering is done using the config.xml file.
Example
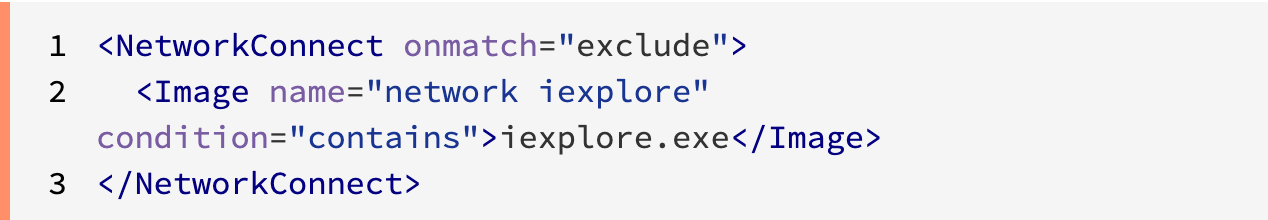
When an intruder gains access to this configuration file, they can easily find out the places you are monitoring and exploit someplace you're not. So, you should monitor these registry keys and files for suspicious changes:
- Computer\ HKEY_LOCAL_MACHINE\ SYSTEM\ CurrentControlSet\ Services\ Sysmon64 (service responsible for monitoring).
- Computer\ HKEY_LOCAL_MACHINE\ SYSTEM\ CurrentControlSet\ Services\ SysmonDrv (communicates the state of the events generated).
- The config.xml filename and its location.
Tip: Don't forget to change the default name of the config.xml file and move it from the default location (C:\Windows).
Sysmon does not register events when key values in the registries mentioned above are changed. To report such changes, Windows Security event ID 4657 must be used.
The registry in Windows is like the CPU in a computer: You know why it's there and what it does. But if something goes wrong, you don't attempt to fix it unless you're sure how to do it.
A registry is an internal database that consists of the settings necessary for Windows applications to function properly. Adversaries can use the registry to maintain a presence in your network, and one of the simplest ways they do that is by adding malicious applications to your startup folder. They might also try to modify the values in the registry to execute malicious packages dropped off in the system.
By auditing the registry, you can help prevent the persistence of malware in your system.
Monitoring the registry lets you:
- 1. Capture unauthorized users or applications that change registry values.
- 2. Closely track privileged users' registry activities to uncover privilege abuse and prevent malicious actions.
- 3. Spot malware activity or suspicious changes to key registry values.
Let's look at some use cases that show how to detect modifications to registry keys or their values, and our recommendations for mitigation.
1. Using the startup folder to execute malicious programs
When adversaries gain initial access, the first thing they want to do is drop malware packages in your system. These malware packages are usually dropped in the startup folder of the system (C:\Users\[User Name]\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup) so the package reloads every time the user logs in.
How to detect it:
The following registry keys control the automatic startup of services during boot:
- HKLM\Software\Microsoft\Windows\CurrentVersion\RunServicesOnce
- HKCU\Software\Microsoft\Windows\CurrentVersion\RunServicesOnce
- HKLM\Software\Microsoft\Windows\CurrentVersion\RunServices
- HKCU\Software\Microsoft\Windows\CurrentVersion\RunServices
- HKCU\Software\Microsoft\Windows\CurrentVersion\Run
Our recommendation:
Registry changes can also happen under normal circumstances. So, monitor them for suspicious changes that don't correlate with any updates, network-wide changes in policies, application installs, and other known network activities.
2. Malicious external device usage
Rogue employees may try to steal information using external storage devices. USB device analysis helps to identify the devices connected to your network and monitor usage metrics like files copied to or from the device and connection time.
How to detect it:
Whenever new USB devices are plugged in, the information about the devices is stored in the following registry keys:
- SYSTEM\CurrentControlSet\Enum\USBSTOR
- SYSTEM\CurrentControlSet\Enum\USB
These registry keys help you identify the vendor, product, and version of the USB device.
When combined with Windows event ID 4663, you can see successful attempts to write or read from an external device. Event ID 4624 lets you find the user who used the device.
Our recommendation:
We recommend using a SIEM tool with UEBA capabilities to detect malicious behavior in your network. You can correlate multiple events to keep a risk score for each object. When the set threshold value is reached, alerts will be triggered.
3. Malicious root certificate installation
Root certificates are public key certificates that are commonly used by browsers to establish a secure TLS/SSL communication with a website. Usually when a user tries to connect to a website that doesn't support a trustable certificate, a warning is displayed.
Malicious actors can install a custom root certificate on a compromised system to persist in the network. Since the system or application trusts all the certificates presented in the root's chain of trust, adversaries can easily connect to a command and control (C2C) server without triggering a security warning.
How to detect it:
All root certificates are added in the following registry keys:
- HKLM\Software\Microsoft\EnterpriseCertificates\Root\Certificates
- HKLM\Software\Microsoft\EnterpriseCertificates\CA\Certificates
- HKLM\Software\Microsoft\EnterpriseCertificates\AuthRoot\Certificates
They're also in registry keys containing the following:
- \Software\Microsoft\SystemCertificates\Root\Certificates
- \Software\Microsoft\SystemCertificates\AuthRoot\Certificates
- \Software\Microsoft\SystemCertificates\CA\Certificates
- \Software\Policies\Microsoft\SystemCertificates\Root\Certificates
- \Software\Policies\Microsoft\SystemCertificates\CA\Certificates
- \Software\Policies\Microsoft\SystemCertificates\AuthRoot\Certificates
Tip: You can also use Sysmon IDs 12, 13, and 14 to write scripts that trigger an event if the keys mentioned above are modified.
4. Winlogon registry attacks
Winlogon is a critical component of Window systems that's responsible for handling the secure attention sequence (Ctrl+Alt+Del), which ensures you're logging on to a secure desktop and no other software can monitor your keyboard activity while typing in your password. This component is also responsible for loading your user profile during logon, shutting down your system, locking your screen due to inactivity, controlling the actions that happen when a user logs on, and more.
Adversaries can use certain features of Winlogon to execute malicious code into your system to establish persistence, so it's crucial to monitor the registry keys that define which processes start during a Windows logon.
How to detect it:
Monitor suspicious changes in the following registry keys:
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Shell
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Userinit
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Notify
Attackers will drop malicious executables in the System32 folder and modify any of the registry keys mentioned above to include and run the payload during Windows logon.
5. Password filter DLL attacks
Every time a user raises a password change request, the local security authority calls the password filters to validate them against a predefined policy to prevent the use of weak passwords.
Adversaries can install a malicious password filter DLL file into the domain controller to capture clear text passwords and pass them on to their C2C server.
How to detect it:
This attack requires the adversary to place the malicious DLL file in the System32 folder and replace the DLL filename in the following registry key:
So, monitor this registry key for suspicious modifications.
Tip: A file addition event in the %windir%\system32\ folder followed by registry modification and a notification package loading event can indicate a possible password filter DLL attack.
Our recommendation:
We recommend using a SIEM solution that comes with a prebuilt correlation engine to correlate the Object Name (4657) and the Notification Package Name (4614) to detect anomalous changes and raise alerts.
About the Author
Vijay is a cybersecurity enthusiast at ManageEngine, a division of Zoho. He is passionate about exploring the latest developments in the field. With a focus on connected devices, operational technology, and enterprise security he is dedicated to staying at the forefront of knowledge in this rapidly evolving space. Believing that cybersecurity will soon become a lifestyle choice for all, he aims to educate and inform through his writing. When not researching, you can find him dancing, embarking on adventure trips, or writing newsletters.
About Log360
ManageEngine Log360, a comprehensive SIEM solution, helps enterprises to thwart attacks, monitor security events, and comply with regulatory mandates.
The solution bundles a log management component for better visibility into network activity, and incident management module that helps quickly detect, analyze, prioritize, and resolve security incidents. Log360 features an innovative ML-driven user and entity behavior analytics add-on that baselines normal user behaviors and detects anomalous user activities, as well as a threat intelligence platform that brings in dynamic threat feeds for security monitoring.
Log360 helps ensure organizations combat and proactively mitigate internal and external security attacks with effective log management and in-depth AD auditing.
Download Request for a personalized demo