Conditional Exchange Access
Conditional Exchange Access (CEA) or Exchange Conditional Access policy allows you to monitor the devices accessing your Exchange server, permitting access only to authorized devices. This is ideal for a BYOD environment as it ensures that corporate data is accessed only from an MDM authorized device. It makes MDM the single point of control for monitoring devices, as any access restriction set up using this feature overrides the access specifications provided in the Exchange server. Mobile Device Manager Plus also supports Exchange Server 2019.
Points to be Noted
- Conditional Exchange Access is supported only for Exchange Server and Exchange Online. CEA for Office 365 can be configured only for Windows devices.
- CEA policy grants access only to email clients configured using the Exchange ActiveSync profile in MDM. Refer the table below for the list of email clients supported with CEA. The email clients marked with a cross and corporate accounts configured manually by the user on managed devices will be blocked.
- CEA is supported only on MDM on-premises.
- After applying the Conditional Exchange Access policy if the unmanaged devices are re-appearing every time you delete them from the console, change the password for these devices or change the Default Access Level to Block.
- CEA is not supported for Outlook app and the app will be blocked from accessing Exchange once CEA is applied. Learn why?
| Platform | Native e-mail app | Gmail app | Outlook/third-party app | ||||||
|---|---|---|---|---|---|---|---|---|---|
| iOS |  |
 |
 |
||||||
| Windows |  |
 |
 |
||||||
|
 |
 |
 |
||||||
 |
 |
 |
|||||||
 |
 |
 |
|||||||
In case the account to be used for setting up Conditional Exchange Access has multi-factor authentication enabled, you need to provide an app-specific password instead of your usual password when initiating Exchange server sync with MDM. You can learn more about app-specific passcodes here.
This feature is available in Professional, Free, and Trial editions of MDM.
Pre-requisites for configuring Conditional Exchange Access
Ensure the following pre-requisites are met before configuring Conditional Exchange Access.
- Powershell 5.1 is installed on the machine where the MDM server is running. You can download this from here.
- Basic authentication needs to be enabled for CEA to function.
- Configure Exchange on managed devices by associating Exchange ActiveSync policy (iOS/iPadOS, Android and Windows) before associating a Conditional Exchange Access policy to the device.
Exchange on-premises
Additionally, ensure the following pre-requisites are met before configuring Conditional Exchange Access on Exchange on-premises
- If you are using Exchange Server 2010, enable Basic Authentication to configure Conditional Exchange Access as explained here .
Enable 'Basic Authentication' in the machine running Exchange server
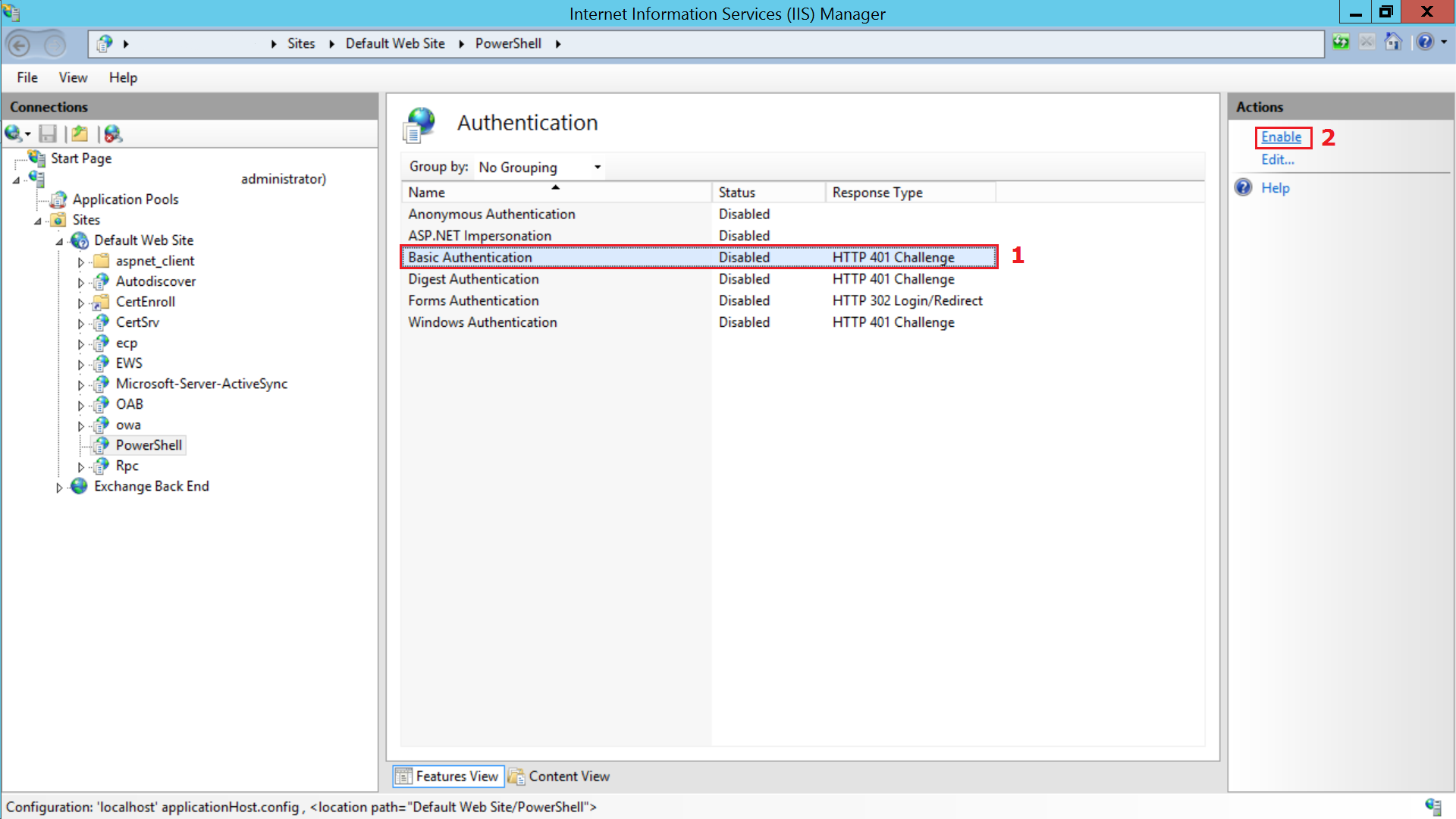
Open IIS Manager, select Sites from the left pane. Then select Default Website > PowerShelland select Authentication.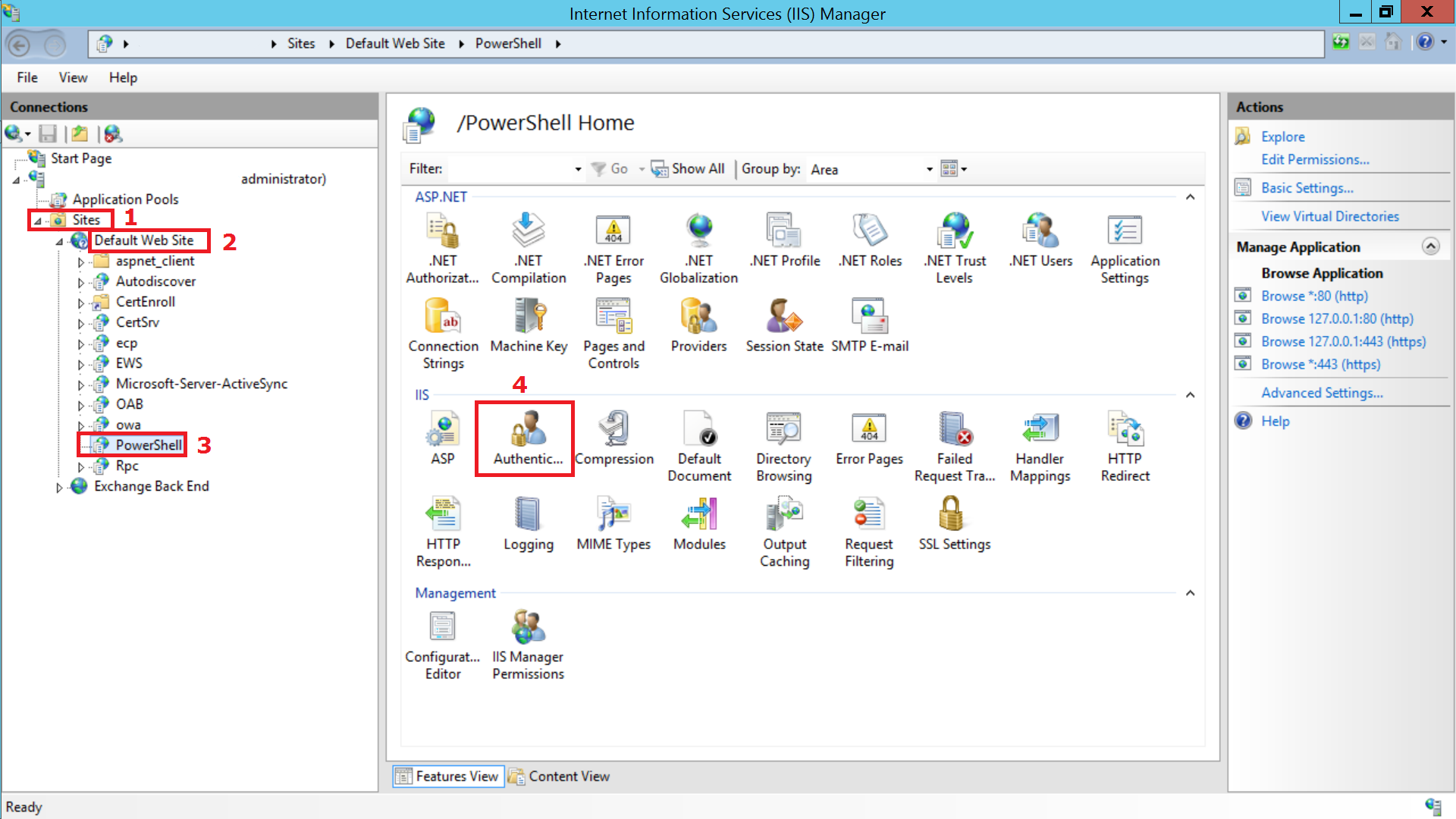
Enable Basic Authentication option by selecting Enable from the Actions menu in the right pane and click Apply.
Exchange Online
For enabling Conditional Exchange Access on Exchange Online, Microsoft has recommended organizations to upgrade to the latest Exchange Online Powershell V2 module (EXO V2 module). This contains a new list of commandlets that simplify bulk import of data from Exchange Online.
- According to the information given by Microsoft,
- For the access state to change, the device must contact Exchange Online and attempt to fetch mails.
- In Exchange Online, it may take upto 24 hours for the access state to change.
Follow any of the steps given below to upgrade to EXO V2 module:
- You can also download the script, copy and paste it on Powershell, and press Enter twice to execute.
OR
- Follow the steps given below:
- Download the zip file available here and extract the Powershell script.
- Open Powershell with Administrator privileges and navigate to the extracted path to execute the script on the device running the MDM server.
- If you encounter an error specifying that executing scripts is disabled on the machine, you can enable it by executing the command Set-ExecutionPolicy Unrestricted
NOTE: In case, you've already configured Exchange Access for Exchange Online and are facing issues in syncing with Exchange Online, we recommend you to update to EXO V2 module to resolve these issues and re-configure CEA.
Configuring Conditional Exchange Access
We have made your job simpler!
Learn how to set up Conditional Exchange Access in under 3 minutes through this demo video.
-
You can configure Conditional Exchange Access on the MDM server, by navigating to Device Mgmt -> Conditional Exchange Access.
-
Provide your Exchange admin credentials or an Exchange account that can execute this list of commandlets, to allow MDM to fetch the details of users and devices accessing Exchange. This includes both the enrolled and unenrolled devices. After providing the credentials, MDM syncs with the Exchange server daily to obtain details of new devices accessing Exchange server. Syncing can also be performed manually.
Recommended Default Access level is Quarantine.
Configuring Access policy
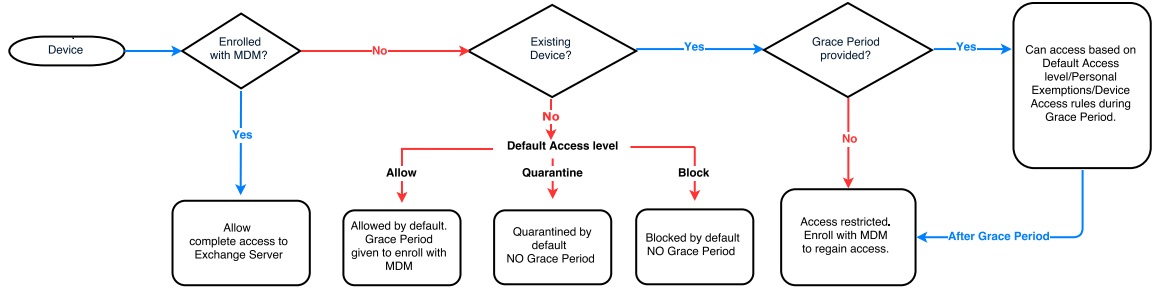
The following flowchart describes the general workflow after a Conditional Exchange Access policy is applied:
NOTE:
-
Using the Exchange Access policy you can define the users you want to monitor. If you want to monitor all the users who are accessing your Exchange, select All users for the Apply policy on option. Else, if you want to selectively monitor and manage users choose Specific users.
-
You can also choose to exclude monitoring specific users. Assuming you want to exclude only the top level employees in your organization, you can click on Exclude specific users and add them there.
- You can also set a Grace Period during which MDM doesn't restrict the users from accessing Exchange. The user must enroll the device within the Grace period else the access is revoked upon completion of the Grace period.
- The users to whom the Grace Period Mails must be sent, must be selected in the Conditional Exchange Access Policy and must have devices which are in "Allowed" state but not enrolled in MDM.
- When the Conditional Exchange Access daily sync scheduler runs at 4am the Grace Period mails are sent.
You can also choose to notify the users when their access to the corporate Exchange account is revoked using the Exchange email. To customize the content in the Exchange mail, go to https://Exchange Server FQDN/ecp (for example https://mdm-exchange/ecp). Click on Edit and you'll be redirected to Exchange ActiveSync Access Settings. Add the Self Enrollment URL to the content which is to be sent to users from Exchange server.
Once, the restriction is applied, the devices cannot send or receive mails. However, mails in the users' mailbox before the restriction is applied are accessible.
How Conditional Exchange Access policy works?
Conditional Exchange Access works based on how you have defined the policy. The MDM Exchange Conditional Access policy can be defined to monitor:
- All Users
- Specific Users
Restricting all users can be ideally used to ensure that users can access the organization's data only using authorized devices. If you want to get a better understanding of the working of the policy, you can test the policy by applying it only on specific users, and then applying it to all the users in your organization.
The policy can be defined to restrict access to Exchange server:
- Immediately (No Grace Period)
- After a specific duration or Grace Period
If the policy is defined to restrict access immediately, all devices are denied access irrespective of Personal Exemptions/Device Access rules specified in the Exchange server. Users need to enroll with MDM to regain access to Exchange server.
If the policy is defined with a Grace Period, devices are given a period of time to enroll. After the Grace Period, only devices enrolled with MDM can access Exchange.
The following table shows the Grace Period and Access type for all devices based on the Default Access level.
| Default Access level | Existing Devices | New Devices | ||
|---|---|---|---|---|
| Grace Period given | Access to mailbox during Grace Period |
Grace Period given | Access to mailbox during Grace Period |
|
| Allow | As specified in the policy | Full Access | As specified in the policy | Full Access |
| Block | As specified in the policy | Full Access | No Grace Period | Blocked by default |
| Quarantine | As specified in the policy | Full Access | No Grace Period | Quarantined by default |
In case the configured Conditional Exchange Access policy doesn't allow access to Exchange despite the devices being enrolled, click on Enrollment tab on the MDM web console and select the column chooser present on the right. Now select the parameter EAS Identifier and add it to the view. Then verify if the EAS identifier of the enrolled device (not granted access to Exchange) is the same in Enrollment view and Conditional Exchange Access view. If they do not match, then it implies Exchange was not configured on the device using MDM, which is one of the pre-requisites for Conditional Exchange Access.
NOTE: Devices allowed access to Exchange server using Personal Exemptions and/or Device Access rules have full access to Exchange server during Grace Period, even when not enrolled with MDM. Devices denied access to Exchange server using Personal Exemptions and/or Device Access rules gain full access to Exchange server when they enroll with MDM. After Grace Period, only devices enrolled with MDM can access Exchange server.
Removing/Modifying the policy
If you modify or remove the policy with the rollback option enabled, the blocked devices of the unselected users are granted access to Exchange. Otherwise, the access state of these devices remain restricted and you have to manually make changes to the access state of these devices. You can still get details of new devices accessing Exchange server but cannot restrict the users who are not monitored by the policy.
When the Exchange server details are removed, all the changes implemented using the policy are not reverted automatically. You can neither get details of new devices accessing Exchange server nor restrict them.
List of Commandlets used by MDM
These are the commandlets required by MDM for Conditional Exchange Access.
To initiate a Powershell Session with Exchange ActiveSync host from the MDM server:
- New-PSSession
- Import-PSSession
READ-only commandlets which MDM uses to fetch data (mailbox-mobileDevice information) from Exchange ActiveSync host.
- Get-ExchangeServer
- Get-ActiveSyncOrganizationSettings
- Get-Recipient
- Get-MobileDeviceStatistics
- Set-ADServerSettings This is to get mailboxes-mobile device data from the entire forest of your AD/Exchange Organization setup.
WRITE-only commandlets
- Set-CASMailbox
This is used only when the policy is applied, after configuring Conditional Exchange Access.
- Remove-MobileDevice
This is used only when manually initiated by administrator from MDM.

