PAM360 Application Gateway Deployment Scenarios
In organizations with distributed IT infrastructures, managing privileged resources across different network environments can be challenging. Certain resources may reside in separate locations, isolated networks, or secure environments like DMZs, making direct access from the PAM360 server either difficult or restricted due to security policies. Additionally, organizations operating in multi-location setups require a flexible solution to ensure seamless privileged access management.
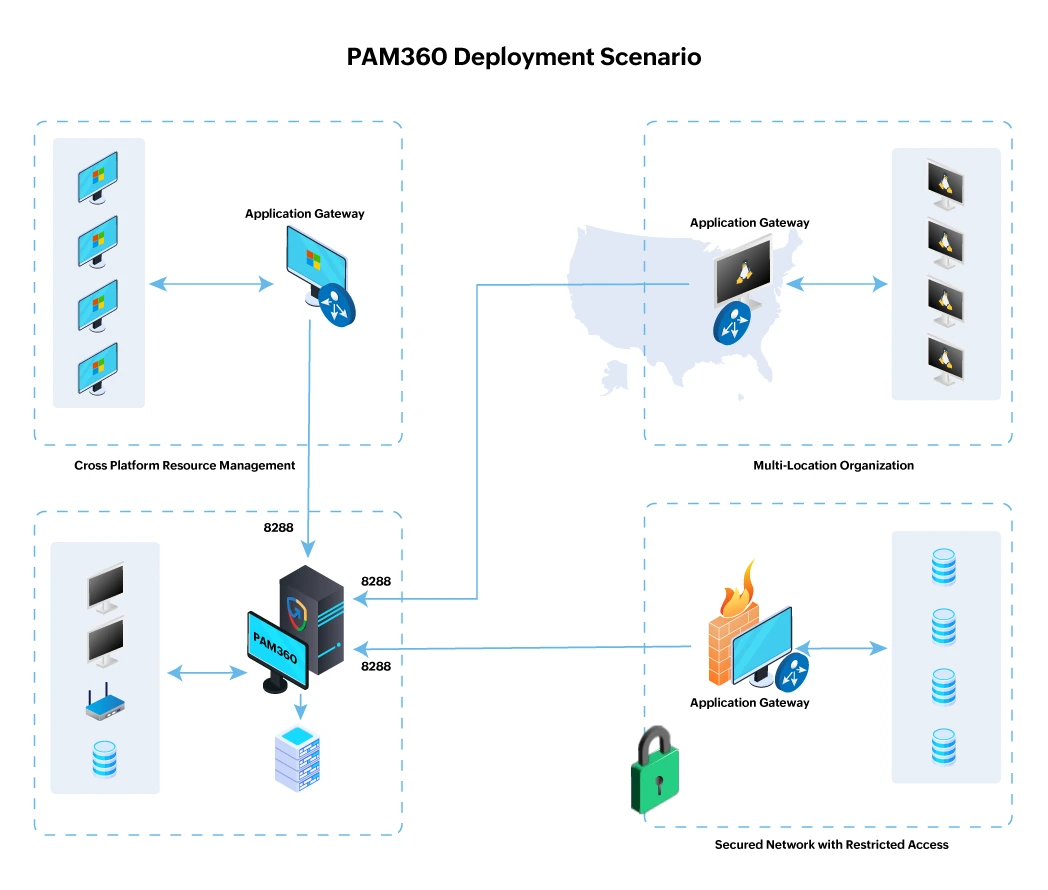
The Application Gateway in PAM360 addresses these challenges by acting as an intermediary, securely bridging the connection between the PAM360 server and remote resources. By strategically deploying the Application Gateway, organizations can extend resource and password management capabilities to manage privileged access across diverse network architectures. Let's explore the different scenarios where deploying an Application Gateway can be beneficial.
- Multi-location Organizations: Businesses with offices spread across multiple locations can use the Application Gateways to centralize privileged access management across different network environments from a single location.
- Secure Networks with Restricted Access: In environments with secure subnets or DMZs, where organizations prefer not to expose their resources directly, the Application Gateway acts as a secure communication bridge for managing privileged resources.
- Cross-platform Resource Management: When the PAM360 web server is hosted on a Linux machine but the target systems to be managed are Windows-based, an Application Gateway can be deployed on a Windows machine that has network access to all other Windows devices. This setup enables seamless management of Windows resources from a Linux-hosted PAM360 server, bridging the gap between different operating systems and ensuring effective cross-platform resource handling.
- Managed Service Providers (MSPs): MSPs managing multiple client organizations can use Application Gateways to maintain secure and efficient access to their clients' privileged resources across different environments.
- Isolated Networks: To manage resources located within an isolated network managed by a service gateway without agents. The Application Gateway can be deployed on the service gateway machine to securely access and manage these privileged resources.
- Load Disribution: Organizations with high volumes of privileged resources and related operations can deploy multiple Application Gateways to distribute the workload efficiently. This setup ensures optimal performance and minimizes latency by balancing resource discovery and password management operations across multiple Gateways.
1. Multi-location Organizations
Let us understand how Application Gateways can be helpful with a scenario. Consider ABC Corporation, a global enterprise with offices in four geographically distributed locations: Location A in Asia, Location B in Europe, Location C in Australia, and Location D in North America. The PAM360 server is hosted at Location A, the central hub for all privileged resource management operations. Due to strict network segmentation policies and security considerations, Locations B, C, and D are not directly connected. However, each of these locations maintains secure connectivity with Location A.
ABC Corporation wishes to manage privileged resources at Locations B, C, and D using the centrally hosted PAM360 server at Location A. Although there is no direct connectivity between locations B, C, and D, deploying an Application Gateway in each of these locations helps bridge the gap and manage the privileged resources at these locations via the PAM360 server deployed at Location A. These gateways establish secure, encrypted communication channels between the PAM360 server at Location A and the Application Gateway deployed machine in each location, without directly exposing the individual resources at each location to the PAM360 server.
With this setup, administrators at Location A can centrally discover and manage privileged resources, verify credentials, and perform password resets across all remote locations without compromising security or operational efficiency. The Application Gateway ensures that secure resource management is possible even in a highly segmented, multi-location network architecture.
2. Secure Networks with Restricted Access
In environments with secure subnets or demilitarized zones (DMZs), organizations enforce strict network segmentation to protect critical resources from unauthorized access and potential security threats. These network zones often house sensitive systems, databases, and application servers that should not be directly exposed to external networks, including the PAM360 server. While this enhances security, it also creates operational challenges in managing privileged access to these resources.
Without a direct connection between the PAM360 server and the privileged resources in the secure subnet or DMZ, administrators may face difficulties performing essential operations such as discovering privileged resources and associated accounts and managing passwords. This lack of connectivity can lead to inefficiencies, requiring manual intervention or workarounds that could compromise security policies.
By deploying an Application Gateway within the secure subnet or DMZ, organizations can establish a secure communication bridge between PAM360 and the isolated resources. The Application Gateway facilitates privileged access management while ensuring that sensitive credentials and resource databases remain protected within their restricted environments. This setup allows administrators to discover, manage, and rotate credentials securely without exposing critical infrastructure to external threats, ensuring compliance with organizational security policies.
3. Cross-platform Resource Management
PAM360 is commonly deployed on Linux machines in environments that primarily consist of Linux resources. In mixed infrastructure setups, managing Windows resources from a Linux-based PAM360 server may present compatibility challenges. An Application Gateway can be deployed on a Windows machine within the network to manage the Windows resources seamlessly. This approach ensures enterprises operating in heterogeneous IT infrastructures can maintain a centralized and efficient privileged access management strategy while overcoming platform-specific limitations.
4. Managed Service Providers (MSPs)
MSP Organizations often oversee IT infrastructure and security for multiple client organizations, each operating in distinct network environments with varying security policies and access restrictions. Traditionally, MSPs relied on PAM360 agents to manage privileged resources across these client environments, which could lead to complex deployments and increased administrative overhead. To streamline this process, MSPs can now deploy the Application Gateways on a single machine within each client’s network and manage the respective resources via the deployed Application Gateway. These Application Gateways act as secure communication bridges, allowing the MSP’s PAM360 instance to connect with and manage the privileged resources within the client’s infrastructure seamlessly. This approach reduces administrative overhead, empowering MSPs to scale their privileged access management services more efficiently.
5. Isolated Networks
In some organizations, certain business units or projects may operate within isolated networks segmented from the rest of the corporate infrastructure for enhanced security or compliance reasons. These networks may not have direct access to the PAM360 server and often lack support for agent-based communication due to policy restrictions or network architecture limitations. These networks are commonly managed through service gateways that regulate traffic and enforce access policies. In such setups, discovering privileged resources and managing them may pose a considerable challenge without compromising the isolation.
PAM360 addresses this challenge by allowing organizations to deploy an Application Gateway server directly on the service gateway machine or any machine with network-level access to the isolated resources. Once deployed, the Application Gateway server establishes an outbound, secure, and encrypted communication channel with the PAM360 server, ensuring that no inbound connection is required, thus maintaining the integrity of the network’s isolation.
6. Load Distribution
Consider XYZ Technologies, a mid-sized enterprise with operations spanning across two key locations: Location X in Asia and Location Y in North America. The PAM360 server is hosted at Location X, serving as the central hub for managing all privileged resources and the associated accounts. The location X hosts around 11000 privileged resources and the location Y hosts around 17,000 privileged resources, a total of 26000 resources. These resources include user devices, workstations, servers, databases, and network devices distributed across various departments and functions. To efficiently manage this workload, the administrators at XYZ Technologies deploy two Application Gateways at Location X and three at Location Y to evenly distribute the workload. By deploying the Application Gateways and associating the resources strategically to manage groups of resources, either based on resource types or balanced according to operational load in the respective location, XYZ Technologies ensures optimal performance and minimizes latency by balancing resource and password management operations across multiple Application Gateways.