PAM360 APIs and Workflow
PAM360 simplifies secure password management for applications and scripts within your infrastructure by eliminating the need to hard-code passwords. Instead, applications can securely query PAM360 to retrieve passwords dynamically. This approach supports best practices like regular password rotation without the hassle of manual updates across multiple configurations or scripts.
1. PAM360 APIs Prerequsites
Before configuring and using PAM360 APIs, ensure the following prerequisites are met:
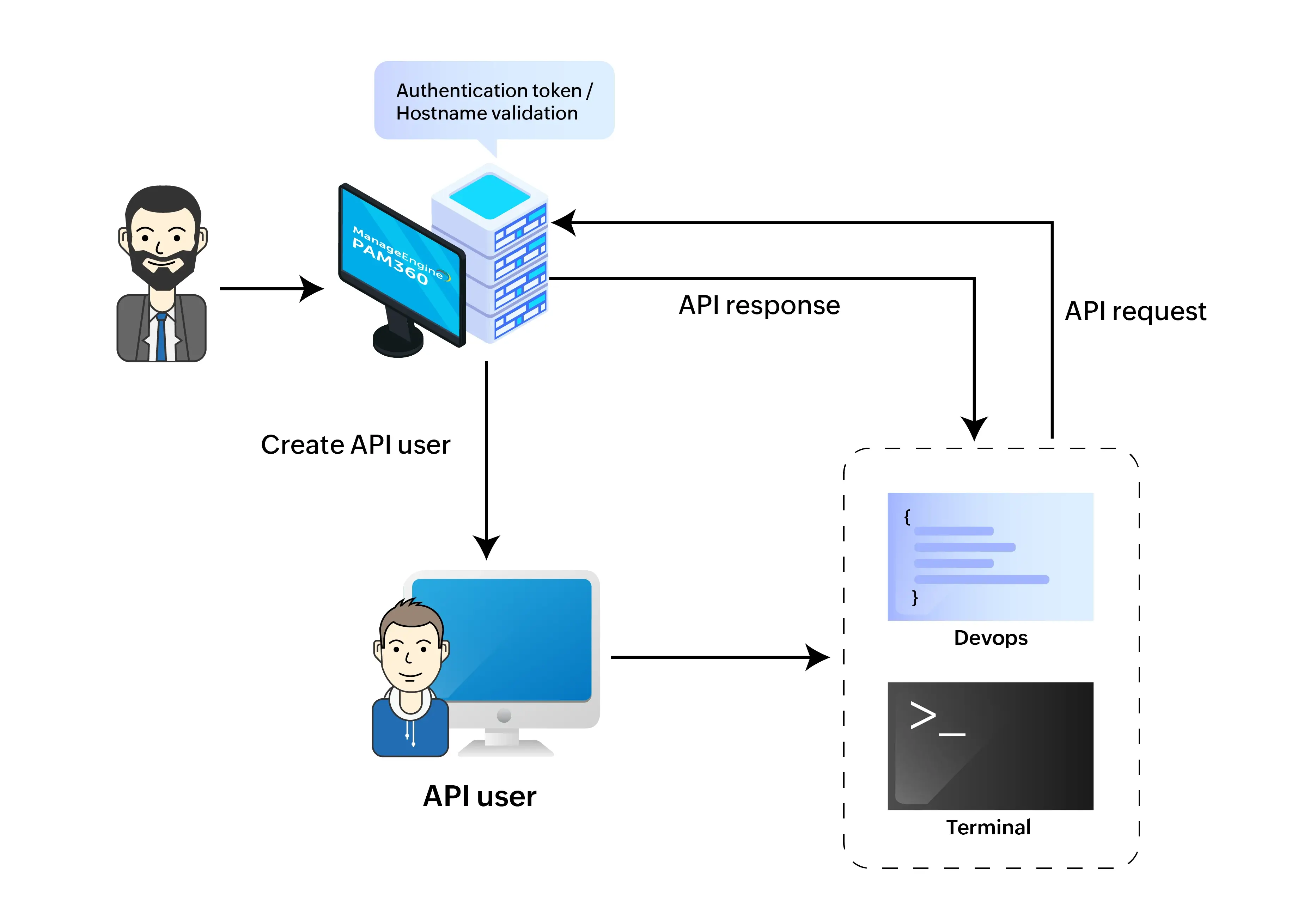
- Create dedicated user accounts within PAM360 specifically for API usage. Each user account should be associated with a unique endpoint (e.g., user@hostname).
- API users can leverage either the SSH CLI or RESTful APIs for integration. For SSH CLI access, authentication relies on PKI (Public Key Infrastructure).
- Users need to provide an OpenSSH format public key that corresponds to their private key.
- PAM360 includes a built-in SSH server that can be configured to operate on specified ports, enhancing security and control.
- Once API users and SSH servers are configured, PAM360 is ready to support API interactions seamlessly.
- Administrators manage access permissions for API users similarly to other users, ensuring that API users can only access passwords authorized for their use through the API.
2. Supported API Types in PAM360
PAM360 supports two types of APIs:
- Command Line Interface (CLI): Enables script-based interactions via Secure Shell (SSH), utilizing PKI authentication for secure access to PAM360.
- RESTful API: Offers a flexible and standardized approach for integrating with PAM360, suitable for diverse application and automation needs.
By implementing these APIs, organizations can enhance security and operational efficiency, empowering applications to retrieve passwords securely and dynamically from PAM360 as needed.
Top