Installing PAM360 Application
To install PAM360, follow the installation procedure that best suits your operating system and environment. Ensure that all prerequisites are met before beginning the installation. For detailed information on each component and its capabilities, refer to the basic requirements document. This guide provides step-by-step instructions for installing PAM360 on various operating systems. You can navigate to specific sections using the links provided below or scroll down for more information.
Each section offers a comprehensive step tailored to different operating systems, ensuring a smooth and efficient installation process for PAM360.
- Installing PAM360 on Windows
- Installing PAM360 on Windows Core Server
- Installing PAM360 on Linux
- Silent Installation
- Transferring a PAM360 Installation
1. Installing PAM360 on Windows
- To begin the installation, double click the downloaded ManageEngine_PAM360.exe.
- The InstallShield wizard for PAM360 appears on the screen. Click Next to continue the installation.
- The Software License Agreement appears. Read the Agreement carefully. Click Yes to agree and proceed with the installation. Click Back to go back to the previous wizard. Click No to exit the setup. You can also Print the License Agreement for future reference.
- Choose the folder to install PAM360 on your system. You can either go with the default location, C:\Program Files\Manage Engine\PAM360 or click Browse to install PAM360 in a different location. Click Next to proceed with the installation. Click Back to go back to the previous wizard.
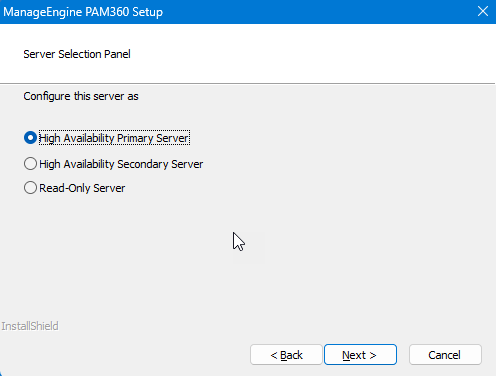
- The Server Selection Panel appears. Here, select the option relevant to the server you are setting up, e.g., Read-Only Server.
- High Availability Primary Server - The primary server will be your predominant server, which controls and manages PAM360's operations and services. It will always be fully functional, with all the features and functions provided by the PAM360 intact.
- High Availability Secondary Server - Select this option if you wish to install PAM360 in another instance - a secondary server. The secondary server will offer Read/Write access to users (except password reset) whenever the primary server is down and until it is brought back to service. The changes made in the database in the intervening period will be automatically synchronized with the primary server upon connection restoration.
- Read-Only Server - Select this option to configure PAM360 in multiple instances in your system environment. The Read-Only servers acts like mirror servers and synchronizes all the actions carried out by the primary server. In case of a primary server failure, any Read-Only server can be configured as the primary server.
- The Registration for Technical Support dialog box appears. Fill in the necessary details, such as Name, E-mail Id, Phone, Company Name, and Country. Click Next to proceed with the installation. Click Skip if you do not want to register. Click Back to go back to the previous wizard.
- Now, the Begin Installation wizard appears that will require you to review your settings and begin the installation. Click Back to make any changes or click Next to proceed with the installation.
- After the installation process, a wizard appears, indicating the completion of installation process. Choose to do any of the following by selecting the corresponding checkboxes:
- Select the Yes, I want to view readme file check box, to view the readme file.
- Select the Start PAM360 Service check box, to start the PAM360 service.
- Untick the boxes if you do not want to view the readme file or start the PAM360 service.
- Click Finish to complete with the installation process.
2. Installing PAM360 on Windows Core Server
- Execute the command powershell to open Microsoft Powershell.
- Execute the following command to download the PAM360 application build:For example:start-bitstransfer -source https://www.manageengine.com/privileged-access-management/6167/ManageEngine_PAM360_64bit.exe -destination C:\Users\Administrator
start-bitstransfer -source <full URL of the executable> -destination <full path to which you would like the executable to be downloaded>
- Execute the following command to download the silent installation file:For example:start-bitstransfer -source https://www.manageengine.com/privileged-access-management/help/WindowsPrimaryNonMSP.zip -destination C:\Users\Administrator
start-bitstransfer -source <full URL of the executable> -destination <full path to which you would like the executable to be downloaded>
- Execute the following command to extract the silent installation file:For example:Expand-Archive -LiteralPath C:\Users\Administrator\WindowsPrimaryNonMSP.zip -DestinationPathC:\Users\Administrator\WindowsPrimaryNonMSP
Expand-Archive -LiteralPath <full path of the executable file> -DestinationPath<full path to which you would like the file to be extracted>
- Execute the following commands to install the Nano Text editor:
Set-ExecutionPolicy Bypass -Scope Process -Force; iex ((New-Object System.Net.WebClient).DownloadString('https://chocolatey.org/install.ps1'))choco install nano
- Execute the following command to edit the extracted file, WindowsPrimaryNonMSP.iss:
nano WindowsPrimaryNonMSP.iss
- Now, edit the Name, MailId (mandatory), Phone, Company, Country (mandatory), and Save the file.
- Next, execute the following command:
ManageEngine_PAM360_64bit.exe -a -s -f1"C:\Windows\WindowsPrimaryNonMSP.iss" -f2"C:\Windows\WindowsPrimaryNonMSP.log"
Upon executing the above commands, the PAM360 application will be installed successfully, and the service will start automatically.
3. Installing PAM360 on Linux
Caution
The PAM360 application needs to be installed on the Linux server with a non-root Linux account.
- Download the file ManageEngine_PAM360.bin for Linux.
- Execute the command: chmod a+x <file-name> to assign the executable permission.
- Execute the command: ./<file_name>
- Execute the command: ./<file_name> -i console, if you are installing on a headless server.
- The InstallAnywhere wizard for PAM360 appears on the screen with an introduction. Click Next to continue the installation.
- The PAM360 License Agreement appears. Read the Agreement carefully and click I accept the terms of the License Agreement to proceed with the installation. Click Previous to go back to the previous wizard. Click Cancel to exit the setup anywhere between the installation.
- Choose the folder to install PAM360 on your system. You can either go with the default location, or click Choose to install PAM360 in a different location. You can also click Restore Default Folder to change from the given different location to the default location. Click Next to proceed with the installation. Click Previous to go back to the previous wizard.
- The Server Selection Panel appears. Here, select the option relevant to the server you are setting up, e.g., Read-Only Server.
- High Availability Primary Server - The primary server will be your predominant server, which controls and manages PAM360's operations and services. It will always be fully functional, with all the features and functions provided by the PAM360 intact.
- High Availability Secondary Server - Select this option if you wish to install PAM360 in another instance - a secondary server. The secondary server will offer Read/Write access to users (except password reset) whenever the primary server is down and until it is brought back to service. The changes made in the database in the intervening period will be automatically synchronized with the primary server upon connection restoration.
- Read-Only Server - Select this option to configure PAM360 in multiple instances in your system environment. The Read-Only servers acts like mirror servers and synchronizes all the actions carried out by the primary server. In case of a primary server failure, any Read-Only server can be configured as the primary server.
- Now, the Pre-Installation Summary wizard appears that will require you to review your settings and begin the installation. Click Previous to make any changes or click Install to proceed with the installation
- Now, the InstallAnywhere wizard begins with the PAM360 installation process.
- Now, a wizard appears, indicating the completion of installation process. Click Done to complete the installation.
- Upon installation, log in as a root user and perform the following steps. This is to install the PAM360 as a startup service.
- Open the console and navigate to the <PAM360-Installation-Directory>/bin folder.
- Execute the command sh pam360.sh install (In Ubuntu, execute as bash pam360.sh install).
3.1 Limitations of Installing PAM360 on Linux without Root Access
When deploying PAM360 on a Linux system without root access, distinct limitations should be considered:
- Agent Requirement - Installing an agent on Windows systems is necessary for managing passwords and conducting tasks such as remote password resets.
- AD Authentication - Linux installations do not support logging into PAM360 using Active Directory (AD) credentials.
- Resource Discovery - Standard discovery methods cannot be utilized to identify Windows resources and Remote Apps.
These constraints necessitate alternative configurations or additional considerations when implementing PAM360 in environments where root access to Linux systems is restricted.
4. Silent Installation
For information about silent installation of PAM360, click here.
5. Transferring PAM360 Installation
If you need to move your PAM360 installation to a different machine or to a different location on the same machine, follow these steps:
- Backup and Precaution: Do not remove the existing installation until the new one is confirmed to be working properly. This ensures you have a backup and can recover from any issues or data corruption during the transfer process.
- Backup Current Database: Take a backup (PostgreSQL | MS SQL) of the current PAM360 database.
- Install on New Machine: Install PAM360 on the new machine.
- Restore Backup Data: Restore (PostgreSQL | MS SQL) the backup data to the new installation.
By following these steps, you can ensure a smooth and secure transition to your PAM360 installation.