Configuring Enterprise Ticketing Systems in PAM360
PAM360 provides administrators with the flexibility to integrate a variety of enterprise ticketing systems, enabling streamlined validation of service requests for privileged access. By integrating these ticketing systems, PAM360 extends access control workflow capabilities by granting approvals to password access requests upon automatic validation of corresponding service requests in the ticketing system. This ensures compliance with organizational security standards, minimizes unauthorized access risks, and simplifies audit trails for privileged account activities.
With PAM360, you can configure both on-premises and cloud-based ticketing solutions to align with your IT service management (ITSM) processes. Whether your organization uses ServiceDesk Plus, ServiceNow, Jira Service Desk, or BMC Remedyforce, PAM360 allows seamless integration with these platforms, offering robust support for incident and service request management.
In this document, you will learn how to configure and integrate the following ticketing systems with PAM360:
- Integrating ME ServiceDesk Plus
- Integrating ME ServiceDesk Plus Cloud
- Integrating ME ServiceDesk Plus MSP
- Integrating ServiceNow
- Integrating Jira Service Desk
- Integrating BMC Remedyforce
- Ticketing System Validation Enforcement and Exceptions
Additional Detail
For custom or other ticketing system integration with PAM360, refer to this help document.
1. Integrating ME ServiceDesk Plus
PAM360 facilitates integration with ManageEngine ServiceDesk Plus by validating change request in addition to the ticket ID entered by the user in the ticketing system. And validation occurs only when the change ID provided is approved in Manage Engine Service Desk Plus.
To integrate ManageEngine ServiceDesk Plus with PAM360 as a ticketing system, perform the below steps.
- Log in to ManageEngine ServiceDesk Plus.
- Click API Key Generation under Username at the top-right corner of the page.
- Copy the generated key and log in to the PAM360 web interface.
- Navigate to Admin >> Integrations >> Ticketing System.
- On the page that appears, click the Enable button in the ManageEngine ServiceDesk Plus tile.
- In the pop-up window that appears, enter the copied key in the Technician Key field.
- In the Ticketing System URL field, enter the URL of the ServiceDesk Plus server (for example, https://dnsname:port).
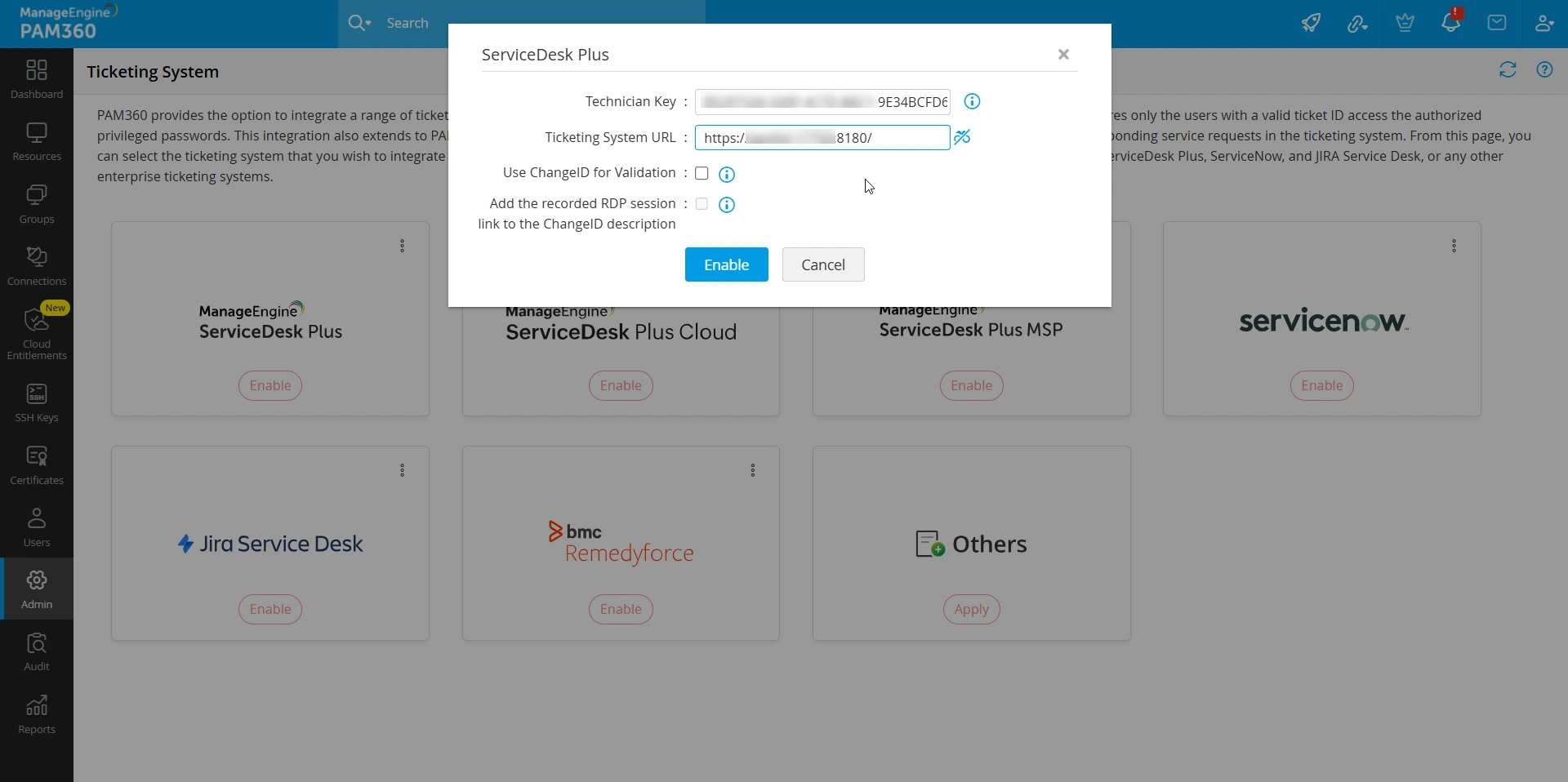
- Tick the Use ChangeID for Validation checkbox to make users provide valid Change IDs for the validation of password access requests and other similar operations. If the checkbox is disabled, users have to submit valid Request IDs for the validation.
- Next, tick the Add the recorded RDP session link to the ChangeID description checkbox if you want to add the link of recorded RDP session to the ChangeID description.
- Click the Enable button to complete configuring the ticketing system integration. Then, click the Refresh icon at the top-right corner of the page to make the changes appear.
Now, the ManageEngine ServiceDesk Plus ticketing system has been integrated successfully.
2. Integrating ME ServiceDesk Plus Cloud
PAM360 integrates with ManageEngine ServiceDesk Plus Cloud to automatically validate access request with a valid ticket ID to grant privileged access. The ServiceDesk Plus Cloud ticketing system integration involves three stages:
- Generating Client ID and Client Secret
- Configuring ServiceDesk Plus Cloud Ticketing System
- Authorizing ServiceDesk Plus Cloud Integration
2.1 Generating Client ID and Client Secret
- Go to the Zoho Developer Console.
- Select the Client Type as Server-based Application.
- Enter the following details:
- Client Name: The name of your application you want to register with ManageEngine ServiceDesk Plus Cloud (PAM360 is advisable).
- Home page URL: Mention the PAM360 access URL. For example: https://<hostname>:port/ (or) https://<domain_name>.com
- Authorized Redirect URIs: <Home_page_URL>/sdpodAuth/saveSDPODRefreshAndAccessTokens
- Click Create to generate the following credentials:
- Client ID: The consumer key generated from the connected application.
- Client Secret: The consumer secret generated from the connected application.
With the Client ID and Client Secret copied from the developer console, go to the PAM360 web interface and perform the ServiceDesk Plus Cloud ticketing system configuration.
2.2 Configuring ServiceDesk Plus Cloud Ticketing System
- Navigate to Admin >> Integrations >> Ticketing System.
- Click Enable under ManageEngine ServiceDesk Plus Cloud.

- Now, enter the Client ID and Client Secret that you have copied earlier.
- Mention the Ticketing System URL and the Redirect URL.
Caution
- If there are multiple portals available in the ServiceDesk Plus Cloud, enter the Ticketing System URL with the relevant portal name. For example, https://sdpondemand.manageengine.com/app/<itdesk>
- Mention the Home page URL from the previous step as the Redirect URL.
- Click Enable to complete the configuration and enable the ServiceDesk Plus Cloud ticketing system.
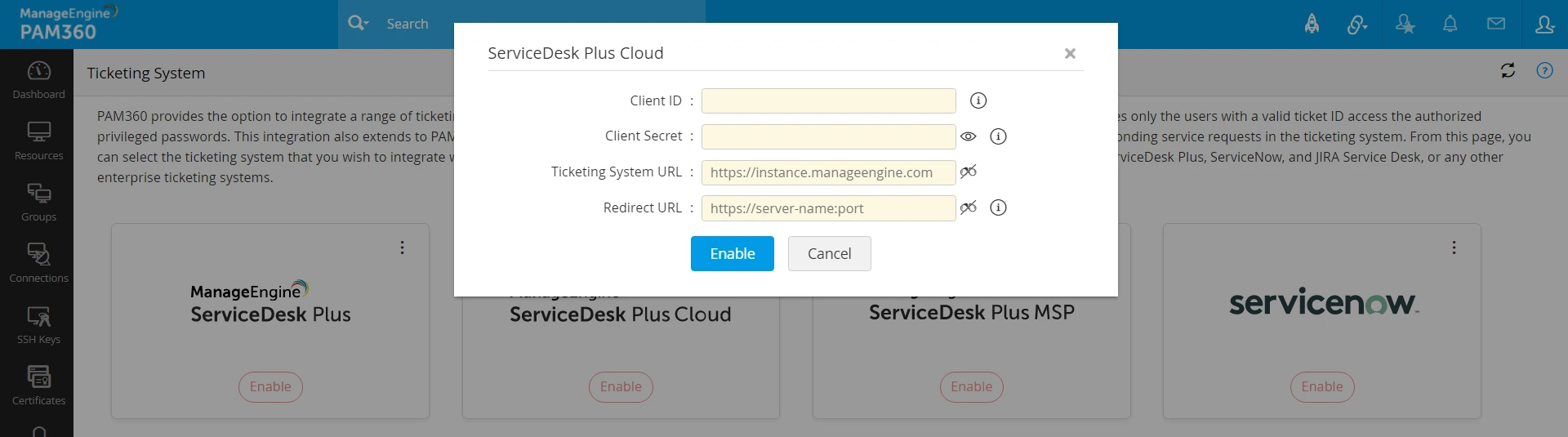
The ServiceDesk Plus Cloud configuration has been saved successfully.
2.3 Authorizing ServiceDesk Plus Cloud Integration
- On the Ticketing System page, click the Refresh icon at the top-right corner for the changes to appear.
- Then, click the red icon at the top-left corner of the ManageEngine ServiceDesk Plus Cloud tile. This will authorize the integration.
- In the UI that appears, Accept the consent form to access the data.
Caution
Remember, only users with a technician role in the Ticketing System should Accept the above request to view and validate the tickets.
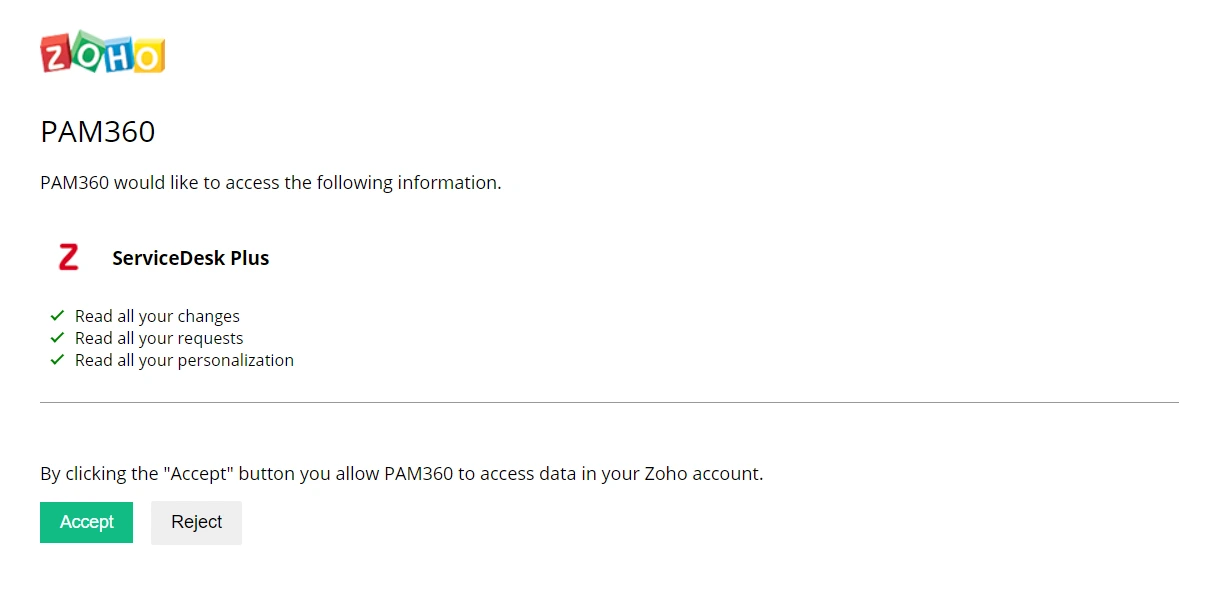
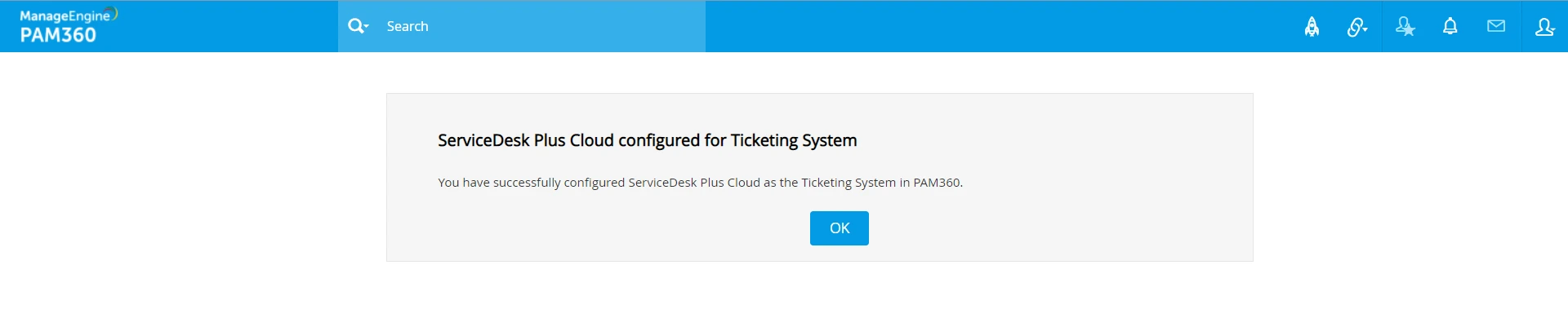
- Now, ServiceDesk Plus Cloud has been configured successfully as ticketing system in PAM360. Click OK to exit the GUI and click the Refresh icon at the top-right corner of the Ticketing System page in PAM360 again for the changes to appear.
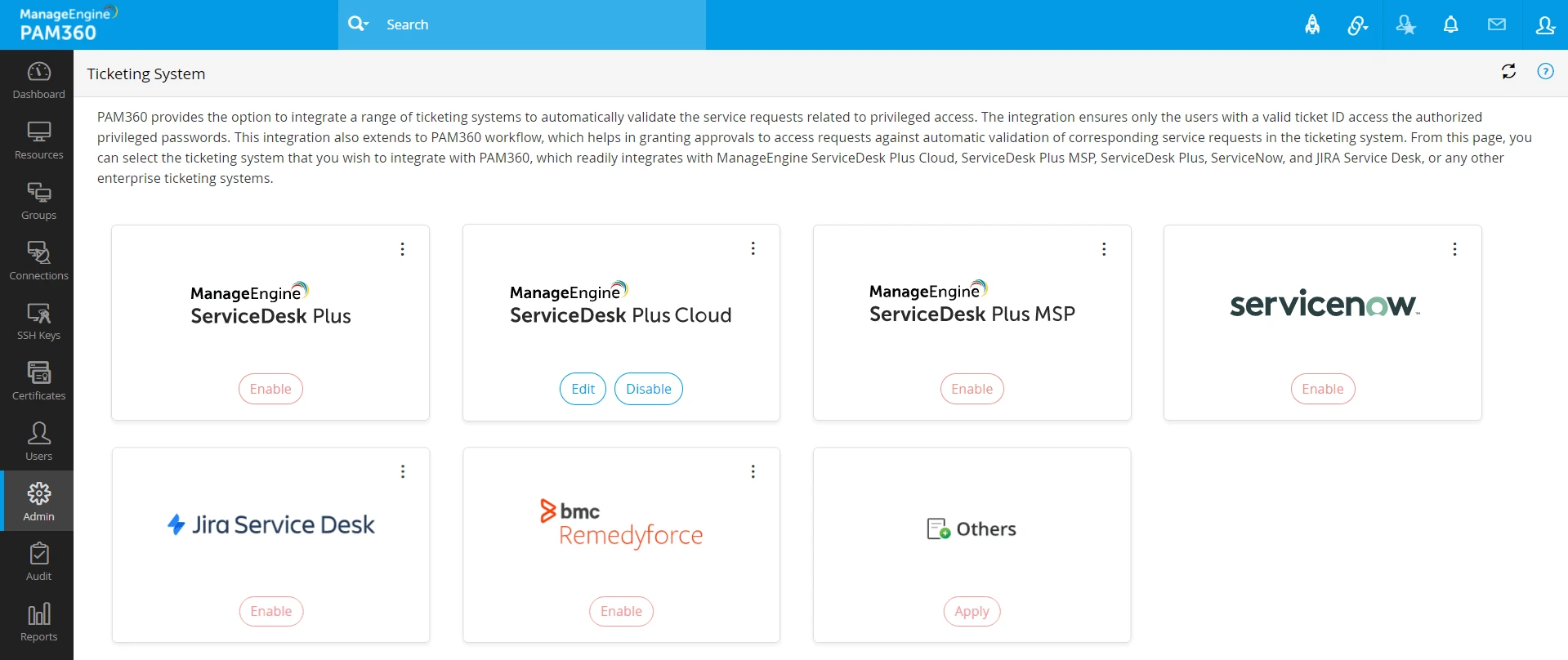
3. Integrating ME ServiceDesk Plus MSP
PAM360 supports integration with ManageEngine ServiceDesk MSP to automatically validate access request to privilege access only with a valid ticket ID. This can be done by generating a Technician key and entering the valid ticket ID in the ticketing system. To perform the integration, follow the below steps:
- Log in to ManageEngine ServiceDesk Plus MSP.
- Click API Key Generation under Username at the top-right corner of the page.
- Copy the generated key and log in to the PAM360 web interface.
- Navigate to Admin >> Integrations >> Ticketing System.
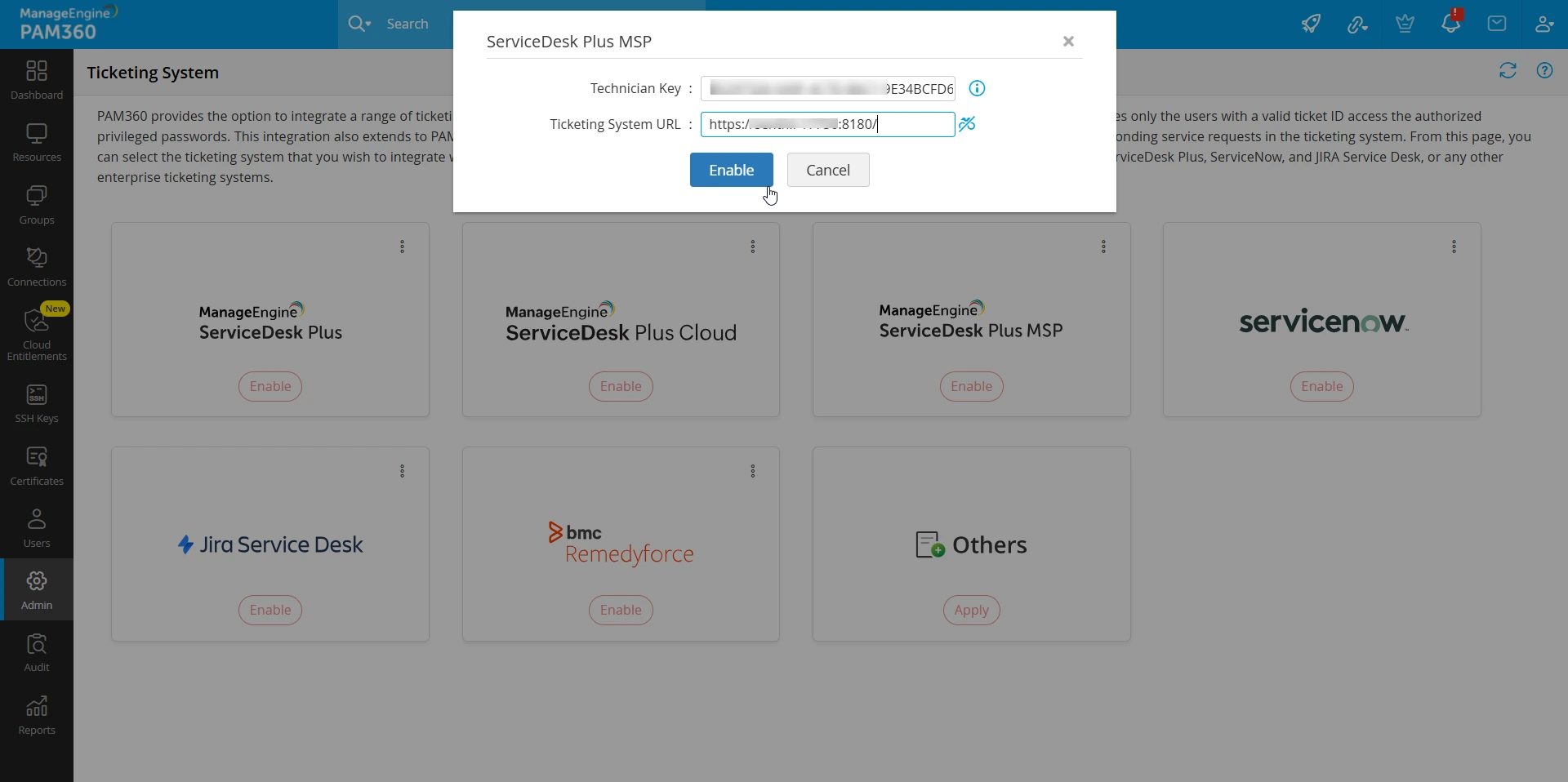
- Click the Enable button for ServiceDesk Plus MSP.
- In the pop-up that appears, enter the key that you have copied in the Technician Key field.
- In the Ticketing System URL field, enter the URL of the ServiceDesk Plus MSP server (for example, https://dnsname:port).
Now, the ManageEngine ServiceDesk Plus MSP ticketing system has been integrated successfully.
4. Integrating ServiceNow
By integrating ServiceNow with PAM360, organizations can automate the validation of service requests for privileged access, ensuring that access is granted only in response to approved and verified tickets. This integration helps enforce security policies, improve accountability, and streamline IT workflows by bridging the gap between privileged access management and ITSM.
The integration supports automated ticket validation, making it easier for administrators to align with organizational compliance standards and reduce manual effort. With this setup, every request for privileged access is linked to a corresponding ServiceNow ticket, ensuring a secure and efficient approval process.
Caution
Ensure that you have the ServiceNow login credentials ready before integrating it with PAM360.
To configure ServiceNow ticketing system in PAM360, perform the below steps:
- Log in to the PAM360 web interface and navigate to Admin >> Integrations >> Ticketing System.
- On the page that appears, click the Enable button on the ServiceNow tile.
- In the pop-up that opens, click on Generate beside the AUTH Token field.
- In the pop-up that appears, enter the ServiceNow login credentials (username and password).
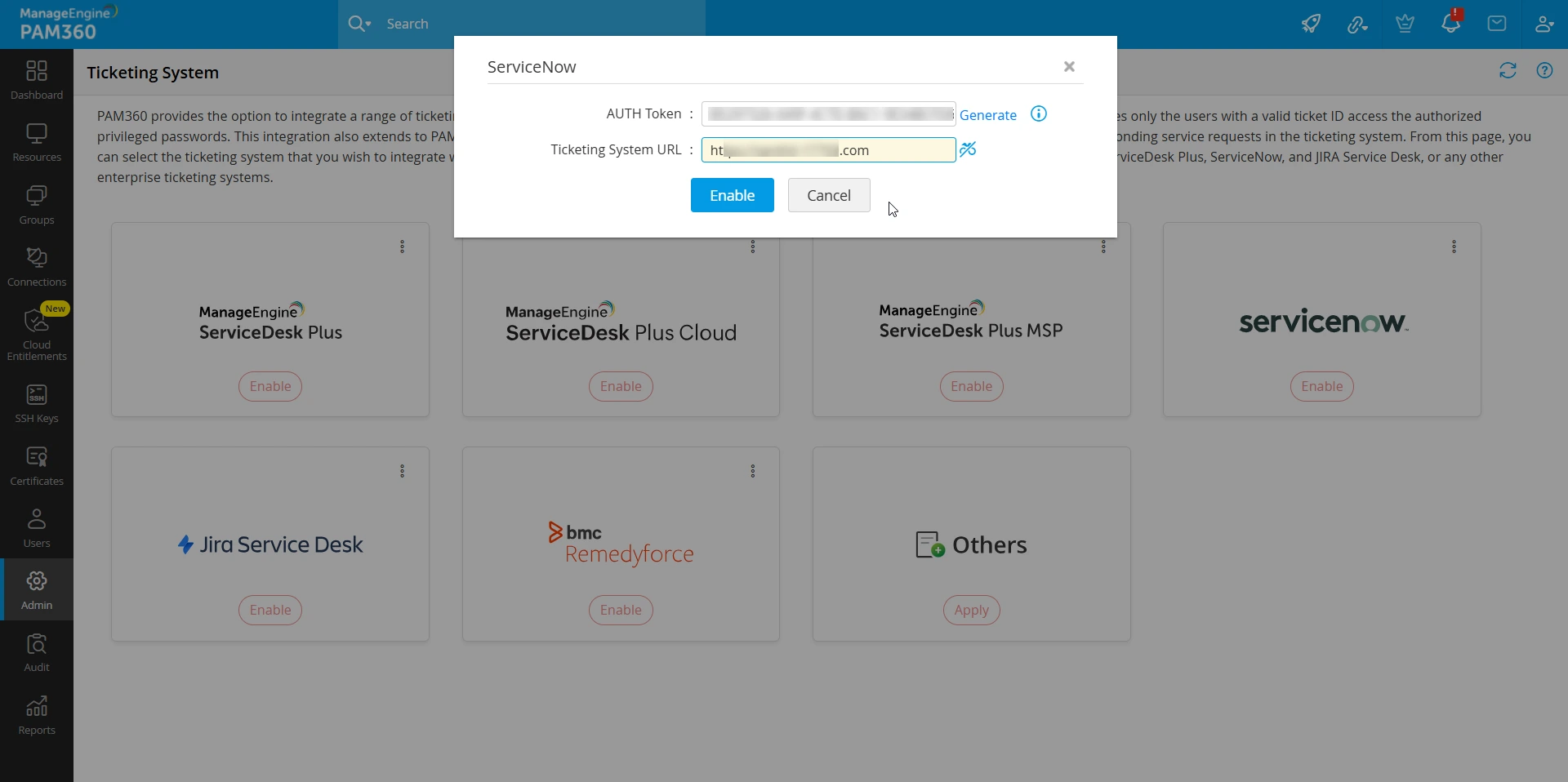
- Once the AuthToken is generated, enter the ServiceNow server URL (for example, https://instance.servicenow.com)in the Ticketing System URL field.
- Click the Enable button to complete configuring the ticketing system.
Now, click the Refresh icon at the top-right corner of the page to make the changes appear. You have successfully integrated ServiceNow ticketing system with PAM360.
Using the ServiceNow ticket IDs, privileged actions such as password access requests, retrieval, and rotation are performed by the user. The following are some ServiceNow ticket ID formats:
- ServiceNow Incident - INC(7 digit number) eg) INC0010007
- ServiceNow Change - CHG(7 digit number) eg) CHG0000003
- ServiceNow Change Task - CTASK(7 digit number) eg) CTASK0000009
- ServiceNow Request - REQ(7 digit number) eg) REQ0010004
- ServiceNow Request Item - RITM(7 digit number) eg) RITM0010007
- ServiceNow Problem - PRB(7 digit number) eg) PRB0000007
- ServiceNow Project - PRJ(7 digit number) eg) PRJ0000009
- ServiceNow Project Task - PRJTASK(7 digit number) eg) PRJTASK0010001
- ServiceNow Task - TASK(7 digit number) eg) TASK0010001
5. Integrating Jira Service Desk
PAM360 now seamlessly integrates with Jira Service Desk, enabling organizations to automate the validation of service requests related to privileged access. This integration ensures that access to critical resources is granted only in response to authorized and approved Jira Service Desk tickets. PAM360 facilitates secure authentication and authorization through OAuth 2.0, ensuring that only verified service requests trigger privileged access. With this integration, administrators can streamline access control processes by leveraging Jira Service Desk's robust ticketing capabilities.
The Jira Service Desk ticketing system integration involves three stages:
- Generating Client ID and Client Secret
- Configuring Jira Service Desk Ticketing System
- Authorizing Jira Service Desk Cloud Integration
5.1 Generating Client ID and Client Secret
- Go to Atlassian Developer Console and log in with your email account.
- Click the Create drop-down and select the OAuth 2.0 integration from the drop-down list.
- Provide the application Name (recommended name, 'PAM360') in the field that appears, and agree to the Atlassian's developer terms by selecting the checkbox. Click Create.
- In the UI that appears, click Permissions from the left pane and perform the below steps:
- Click Add and then Configure against the Jira API.
- On the page that appears, click Edit Scope under Jira Service Management API.
- Select View Jira Service Management Request Data and click Save.
- Select Authorization from the left pane and click Add.
- In the UI that appears, specify the Callback URL in the format - https://<hostname>:<port>/jiraAuth/saveJiraAccessToken and click Save changes.
- Click Settings from the left pane and note down the Client ID and Client Secret.
With the Client ID and Client Secret copied from the developer console, go to the PAM360 web interface and perform the Jira Service Desk ticketing system configuration.
5.2 Configuring Jira Service Desk Ticketing System
- Log in to the PAM360 web interface and navigate to Admin >> Integrations >> Ticketing System.
- On the Ticketing System page, click the Enable button on the Jira Service Desk tile.
- In the pop-up window that appears,
- Enter the Client ID and Client Secret (that you have noted down previously) in the required fields.
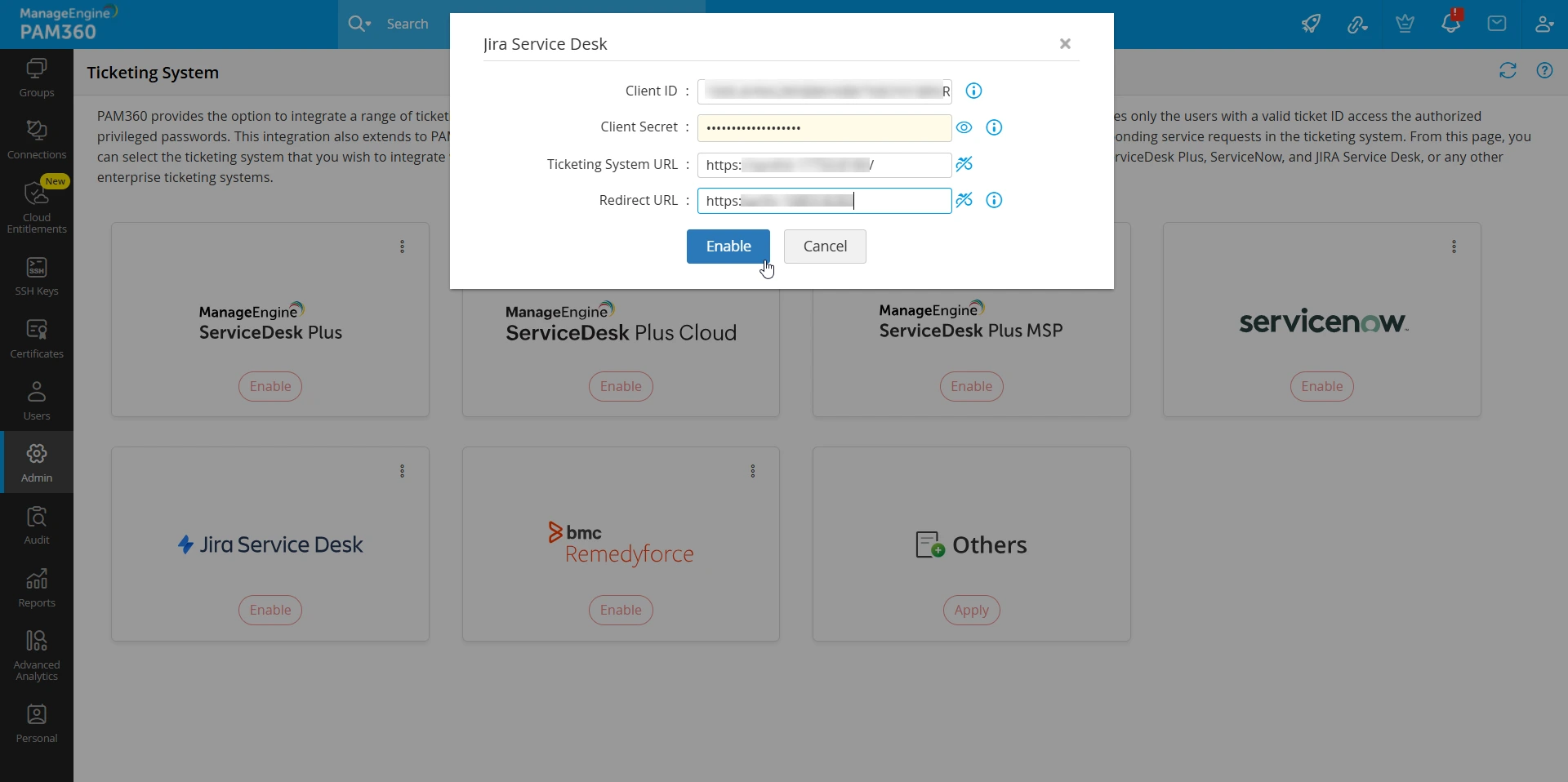
- Next, enter the ticketing system URL (for example, https://instance.atlassian.net) in the Ticketing System URL field.
- Specify the redirect URL (for example, https://<dnsname>:<port> or https://<instance>.<server>.com) in the Redirect URL field to return the data after authorization.
- Click the Enable button to complete the configuration and enable the Jira Service Desk ticketing system.
- Enter the Client ID and Client Secret (that you have noted down previously) in the required fields.
The ServiceDesk Plus Cloud configuration has been saved successfully.
5.3 Authorizing Jira Service Desk Integration
- On the Ticketing System page, click the Refresh icon at the top-right corner for the changes to appear.
- Then, click the red icon at the top-left corner of the Jira Service Desk tile. This will authorize the integration.
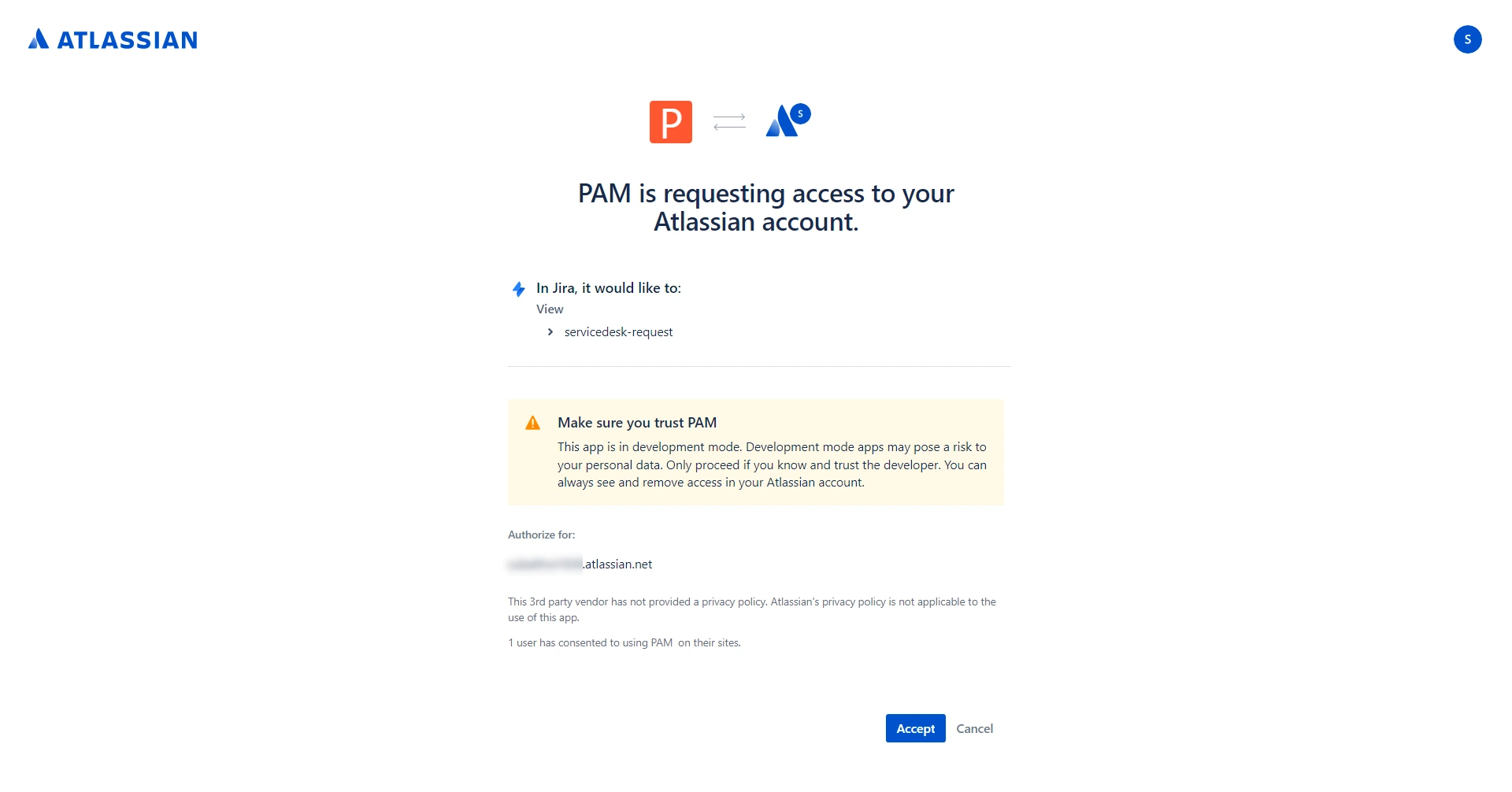
- In the UI that appears, Accept the consent form to allow PAM360 to access the data.
You will now be redirected to the PAM360 UI with a success message. Jira Service Desk has been configured successfully as a ticketing system in PAM360.
6. Integrating BMC Remedyforce
BMC Helix Remedyforce is a complete IT service management tool that includes Incident/Problem Management, Client Management, Service Management, Reports/Analysis, etc., that can be tailored to meet the requirements of enterprises. PAM360 now integrates with BMC Helix Remedyforce to provide automatic validation of service requests pertaining to privileged access. Users will have to submit valid ticket ID's to administrators to gain access to privileged passwords. Through automatic validation of the relevant service requests in the ticketing system, the integration assists in approving access requests.
To configure BMC Helix Remedyforce as ticketing system in PAM360, perform the below steps:
- Navigate to Admin >> Integrations >> Ticketing System.
- Click the Enable button in the BMC Remedyforce tile.
- In the pop-up that appears,
- Enter the Salesforce account credentials in the Username and Password fields.
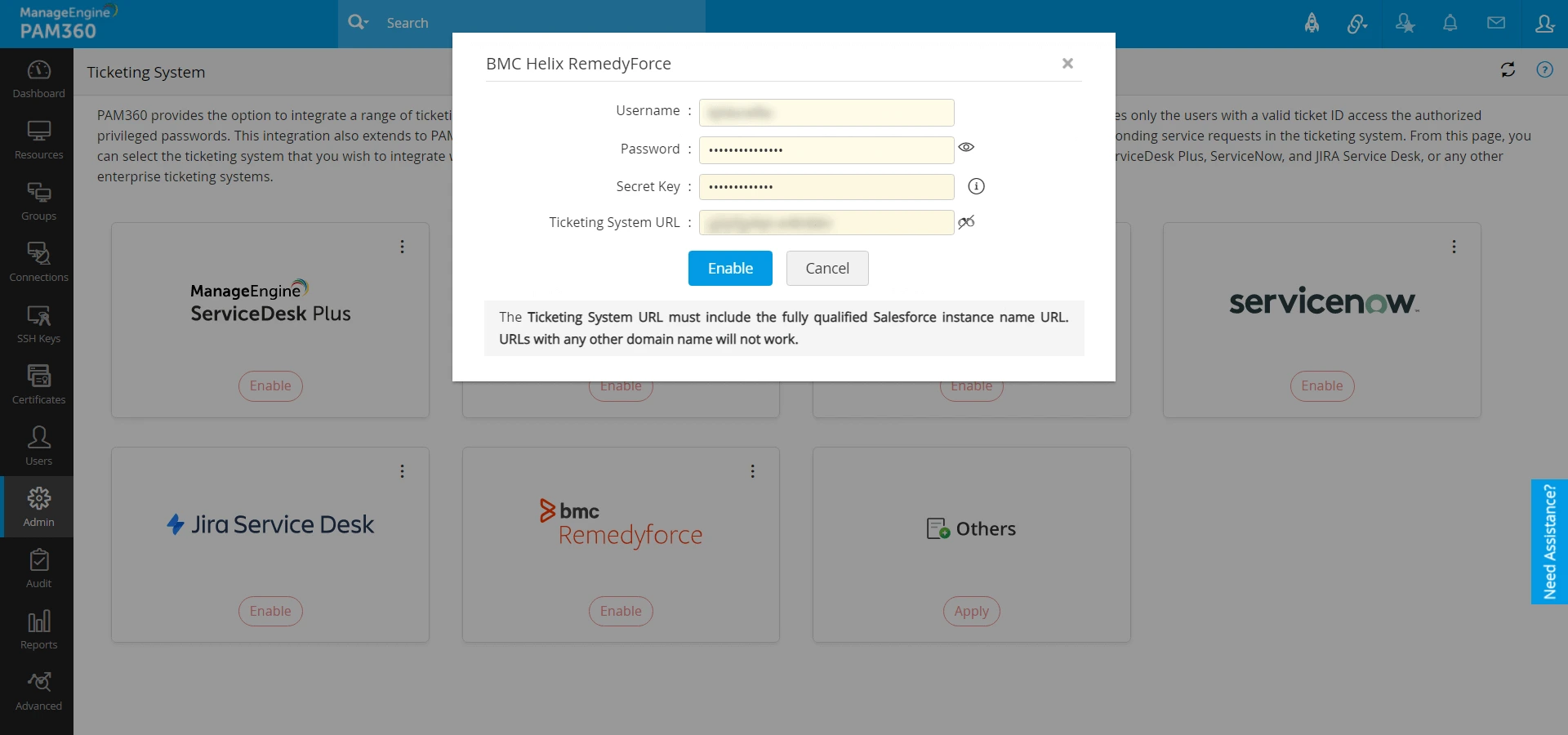
- Specify the security token in the Secret Key field. To know more about the Security Token, click here.
- Mention the Salesforce Instance Name URL in the Ticketing System URL field.
- Click the Enable button to complete the configuration.
Caution
The Ticketing System URL should include the fully qualified Salesforce instance name URL. Also, note that URLs with any other domain name will not work.
- Enter the Salesforce account credentials in the Username and Password fields.
You have now successfully enabled BMX Helix Remedyforce as a ticketing system in PAM360.
7. Ticketing System Validation Enforcement and Exceptions
Once the ticketing system integration is configured, it is enforced globally, requiring users to provide valid ticket IDs to access passwords. By default, super administrators are exempt from this requirement. In addition to global enforcement, ticket ID validation can also be applied selectively at different levels, such as specific resource groups or user groups. Furthermore, users can be required to provide ticket IDs as part of the access control workflow, allowing automated access after successful ticket validation.
The following sections outline the options available for managing ticketing validation enforcement:
- Selective Enforcement for Resource Groups: Enable or disable ticketing enforcement for specific resource groups.
- General Settings for Ticketing Validation: Configure ticketing validation rules globally for user-specific operations.
- User Group-Specific Ticketing Settings: Define ticketing validation rules for individual user groups.
- Ticket ID Validation for Auto Approval Workflow: Enable ticket ID validation for resources configured with auto-approved access control.
7.1 Selective Enforcement for Resource Groups
You can enable or disable ticketing enforcement for specific resource groups:
- Navigate to the Groups tab and select the desired resource groups.
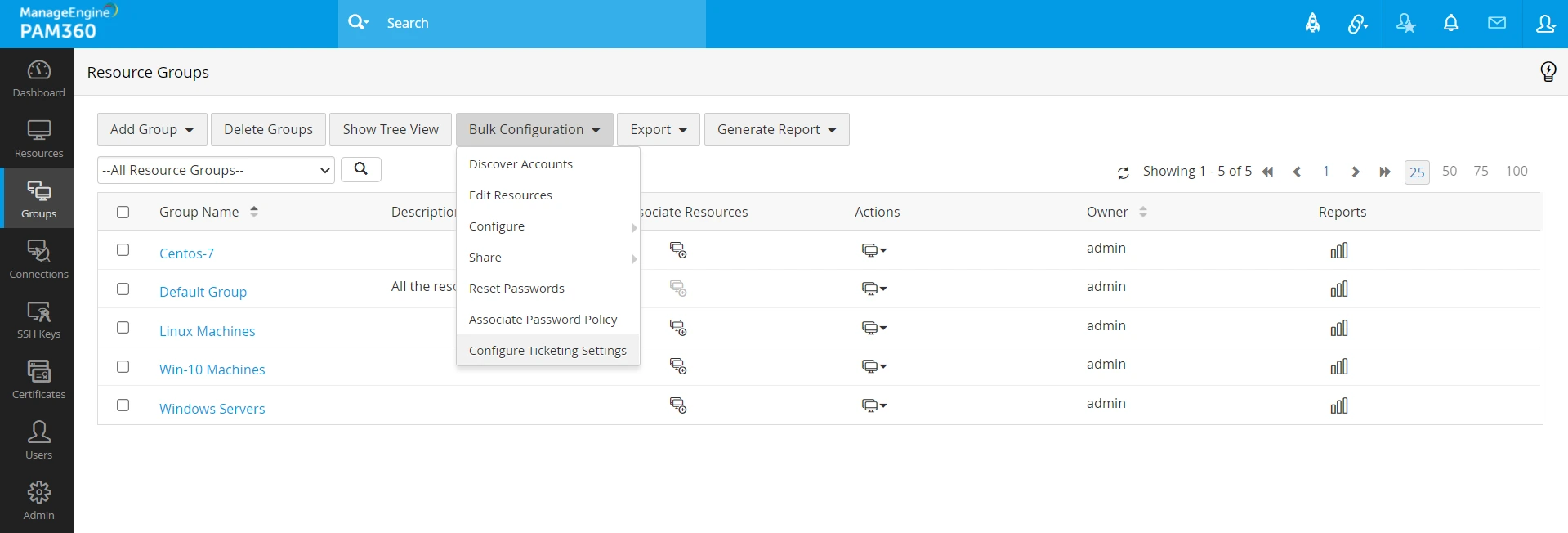
- Click the Bulk Configuration button at the top pane, select Configure Ticketing Settings, and enable or disable the ticketing system for the resource group accordingly.
7.2 General Settings for Ticketing System Validation
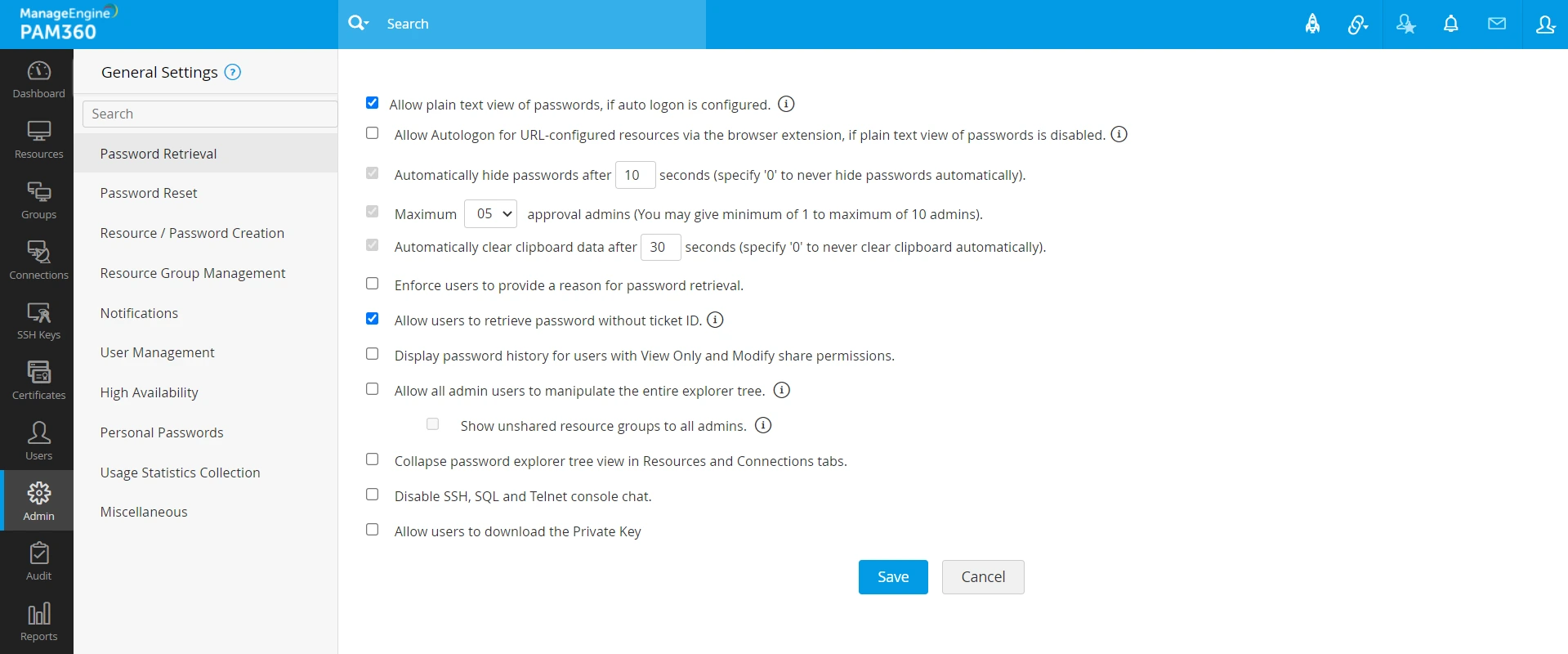
From the General Settings, you can selectively allow or restrict ticket validation requirements for user-specific operations:
- Allow users to retrieve passwords without a ticket ID (under the Password Retrieval section).
- Allow users to reset passwords without a ticket ID (under the Password Reset section).
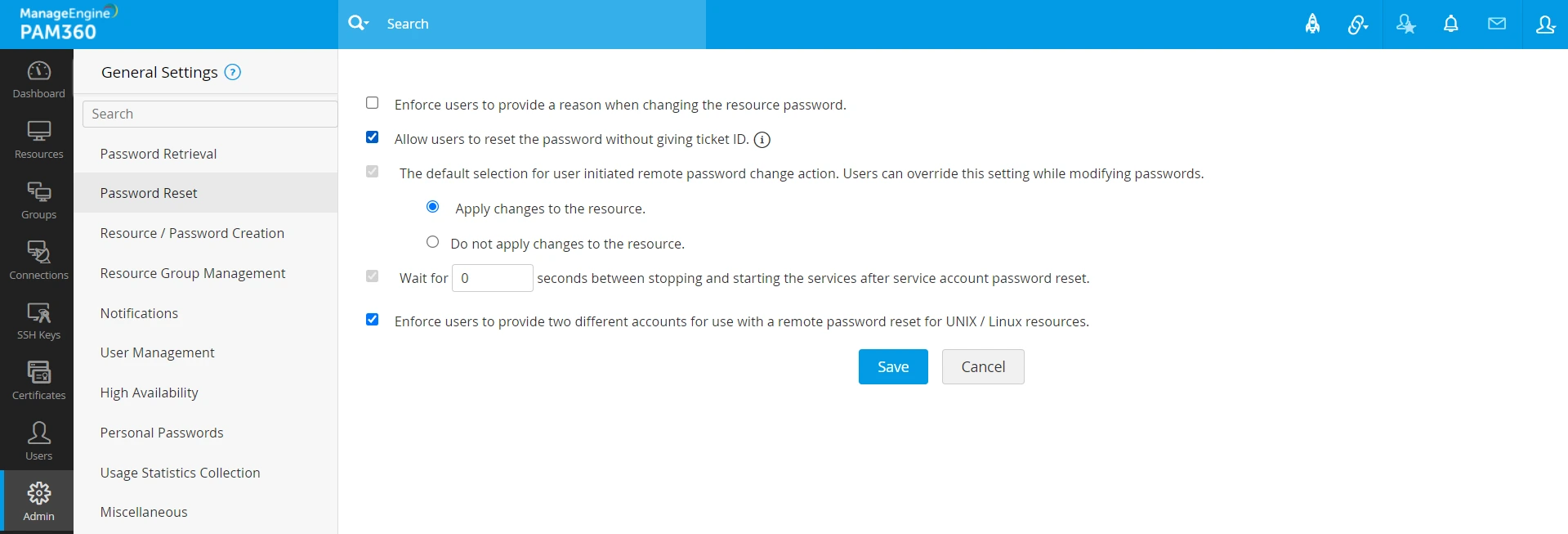
7.3 User Group-Specific Ticketing Settings
To configure ticketing validation rules for specific user groups, navigate to the User Groups tab and define ticketing settings as per your requirements for each user group.
By offering flexible configuration options, PAM360 enables precise control over ticketing validation enforcement across users, groups, and resource groups.
7.4 Ticket ID Validation for Auto Approval Workflow
To enable the ticket ID validation for auto approval of password access requests for a resource/account, perform the below steps:
- Navigate to the Resources tab. Click the Resource Actions icon beside the resource and select Configure >> Access Control >> Auto Approval.
- If you want to configure the ticket ID validation for an account, switch to the Passwords tab and click Account Actions beside the account. Select Configure Access Control >> Auto Approval.
- In the Auto Approval tab, tick the Approve access requests automatically for requests raised checkbox.
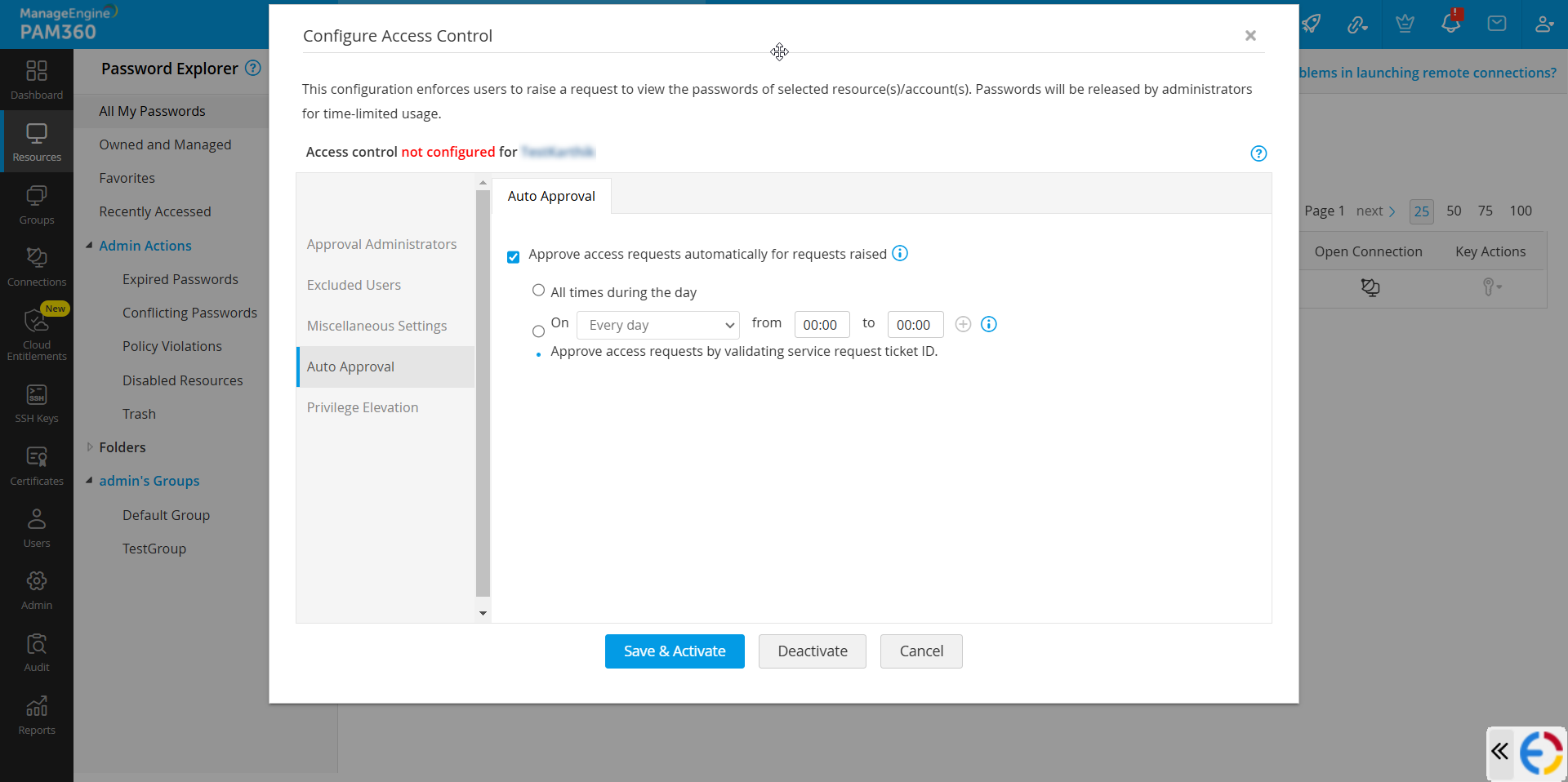
- Now, select the Approve access requests by validating service request ticket ID option and click Save & Activate.
For detailed instructions on how access control works for ticket ID validation on service requests, click here.