- What does "machine" stand for in machine identity management?
- What is a machine identity?
- How does machine-to-machine authentication happen?
- Importance of machine identity management
- Best practices associated with machine identity management
- How can organizations establish a machine identity management framework across their IT network?
What does "machine" stand for in machine identity management?
The word "machine" generally makes you think about hardware such as laptops, servers, printers, mobile phones, and IOT devices. However, in the context of machine identity management, any non-human node in a network that sends or receives data is known as a machine.
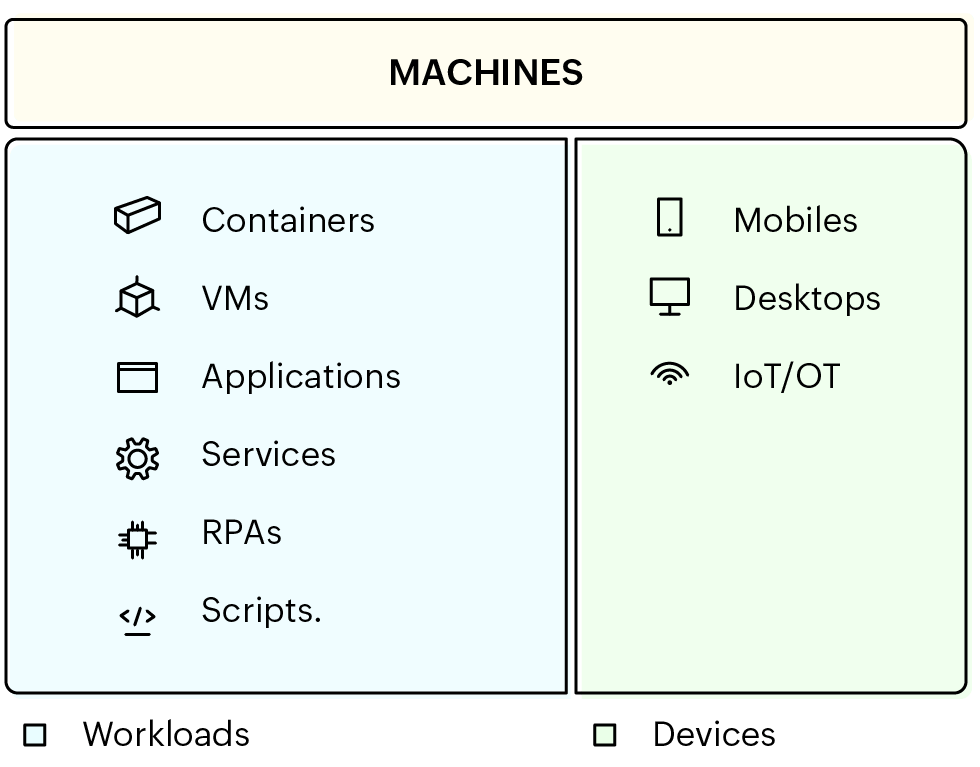
An IT network typically has two types of machines: workloads and devices.
Obvious hardware, such as computers, printers, routers, servers, and switches, fall under devices, but the term "machine" in machine identity management includes workloads, such as containers, VMs, applications, services, RPAs, and scripts.
Machines, including hardware devices and workloads, when part of a network, are expected to verify their identity to communicate with other machines in the network securely.
What is a machine identity?
In any conventional network, there are two types of users: humans and machines. Human users include customers, employees, vendors, consultants, and other temporary or permanent human users.
Similar to how human users authenticate themselves using passwords, auth-tokens, and OTPs, machines also use identities to authenticate themselves while communicating with another machine or human in the network. These privileged identities are known as machine identities.
Like passwords, these machine identities should also be secured, regulated, and managed to uphold confidentiality between machine to machine communications throughout the network. Before we dive into the significance of machine identity management, let's see what a machine identity looks like.
Examples of machine identities
- 01
Certificates
This is an SSL/TLS certificate issued to www.zoho.com.
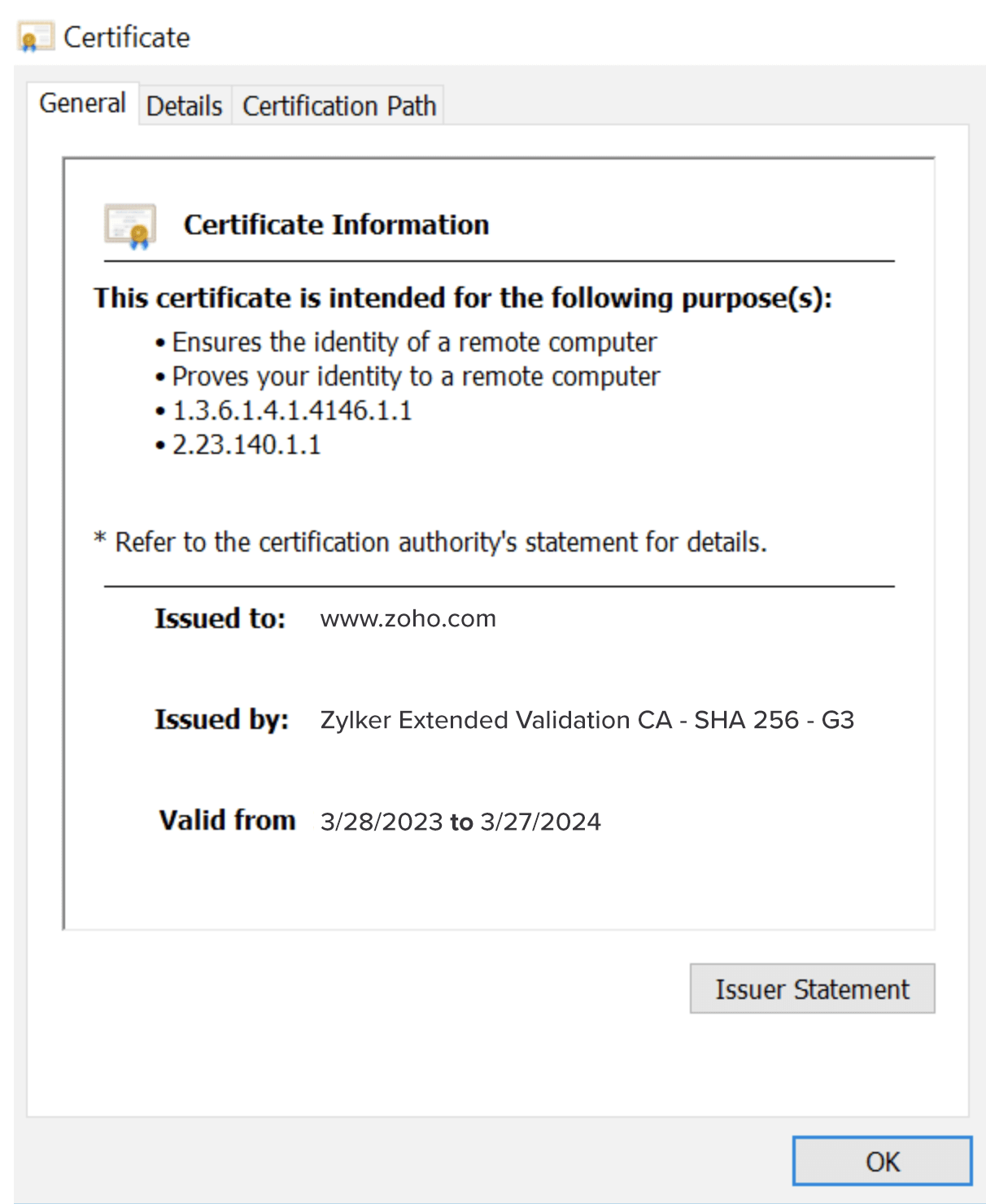
An SSL certificate typically has the details of the issuer, validity, and the purpose of the certificate. Predominantly machine identities are certificates, or cryptographic keys, generated to authenticate machine-to-machine identity and access management.
- 02
Keys
There are different types of keys used in an enterprise IT network to validate connections between different types of machines. One common example is a bluetooth pairing key that you authenticate when establishing a bluetooth connection. Similarly, SSH keys are also used to encrypt and authenticate communication between different devices.
How does machine-to-machine authentication happen?
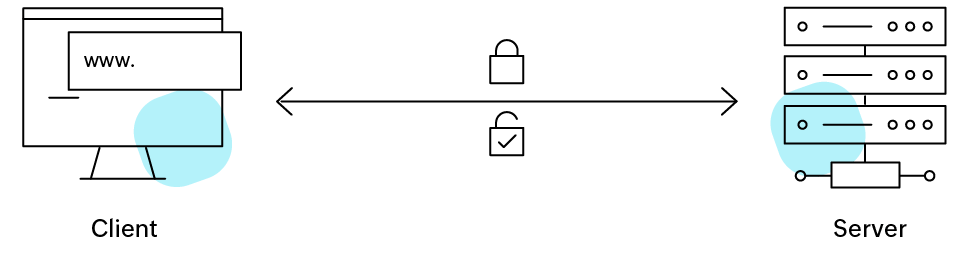
When a machine in a network, such as a client, attempts to establish a connection with another machine, the client will request to verify the machine identity of the device or workload it is attempting to connect to.
The process through which one machine, be it a device or a workload, validates another's identity is called machine-to-machine authentication.
Enforcing strict policies while configuring machine-to-machine authentication is highly recommended while practicing machine identity management.
Importance of machine identity management
Practicing machine identity management strategies helps organizations drastically reduce network vulnerabilities and mitigate threat response measures in case of exploits.
- 01
Website downtime
All web domains are certified by a certificate authority. Such TLS/SSL certificates are also considered machine identities in the context of MIM. If such certificates are compromised or are expired, it will lead to unprecedented downtime affecting critical business functions throughout the enterprise.
- 02
Pipeline failure
Any CI/CD pipeline or container platform holds secrets. Such secrets are regularly used by bot routines while accessing remote machines in a network. A common mispractice involves embedding these secrets in text files or scripts. Such secrets are also considered machine identities in the context of MIM.
These secrets are constantly used throughout a workflow pipeline. If secrets become vulnerable to exploits, or if they are even inadvertently exposed, it often causes cascading failures throughout the pipeline, and can result in multiple levels of automation failures.
To avoid critical business failures, organizations need to make sure that the machine identities used for authentication of enterprise IT networks are regulated through machine identity management strategies.
Best practices associated with machine identity management
- Maintain a complete record of all functional machines in the network and their identities, while also regularly updating said list with latest information regarding such machine identities.
- Discover these machine identities and store them in a centrally located vault, that is accessible only by administrative users.
- Regularly renew machine identities based on the criticality of the business function each machine performs and associate credential policies accordingly.
- Set alerts based on the time of expiry for each machine identity, and set up schedules to initiate renewal procedures.
- Monitor all activity performed by these machines, including their interaction between human and non-human users, be it remote sessions, file transfers, secret rotation, or any other privileged behavior.
- Share machine identities with all third-party vendors and collaborators following the principle of least privilege, and ensure such machine identities are revoked after the designated project or task is completed.
- Ensure zero standing privileges while sharing and revoking access to all critical machine identities.
How can organizations establish a machine identity management framework across their IT network?
Adopting a machine identity management routine provides several technical advantages for an IT admin against privilege abuse. Machine identity management helps you govern critical machine identities through several technical strategies associated with securing certificates, keys, secrets, and other machine identities.
- 01
Certificate and key lifecycle management
Certificate and key lifecycle management (CLM) is a machine identity management strategy that helps enterprises discover, secure, renew, deploy, and audit certificates in an IT network throughout their lifecycle.
By deploying CLM strategies in your MIM framework, you can efficiently manage the lifecycle of all SSL/TLS certificates and keys in your enterprise IT network. Most importantly, you can set up schedules to renew certificates and keys based on predefined policies and configurations.
- 02
Secrets management
Secrets management refers to the MIM strategy that mandates secure storage, management, and restricted access to business-critical identities, collectively known as secrets.
All secrets used in container platforms or CI/CD pipelines can be discovered and vaulted. Such secrets can also regularly be rotated based on custom predefined policies and reset schedules thus easing an otherwise bothersome process of cloud secrets management.
Furthermore, machine identity management strategies incorporated into your IT network using privileged access management can address voids such as identity and access governance, access control, and compliance audits.