- Related Products
- AD360
- Log360
- ADManager Plus
- ADSelfService Plus
- EventLog Analyzer
- Exchange Reporter Plus

 Click here to expand
Click here to expand
Object level auditing must be configured to ensure that events are logged whenever any Active Directory object related activity occurs.
Click on View and ensure that Advanced Features is enabled. This will display the advanced security settings for selected objects in Active Directory Users and Computers.
Note: Use Clear all to remove all permissions and properties before selecting the appropriate permissions.
| Auditing Entry number | Auditing Entry for | Access | Apply onto | |
|---|---|---|---|---|
| Windows Server 2003 | Windows Server 2008 and above | |||
| 1&2 | OU |
|
This object and all child objects | This object and all descendant objects |
|
Organizational Unit objects | Descendant Organizational Unit objects | ||
| 3&4 | GPO |
|
This object and all child objects | This object and all descendant objects |
|
groupPolicyContainer objects | Descendant groupPolicyContainer objects | ||
| 5&6 | User |
|
This object and all child objects | This object and all descendant objects |
|
User objects | Descendant User objects | ||
| 7&8 | Group |
|
This object and all child objects | This object and all descendant objects |
|
Group objects | Descendant Group objects | ||
| 9& 10 | Computer |
|
This object and all child objects | This object and all descendant objects |
|
Computer objects | Descendant Computer objects | ||
| 11&12 | Contact |
|
This object and all child objects | This object and all descendant objects |
|
Contact objects | Descendant Contact objects | ||
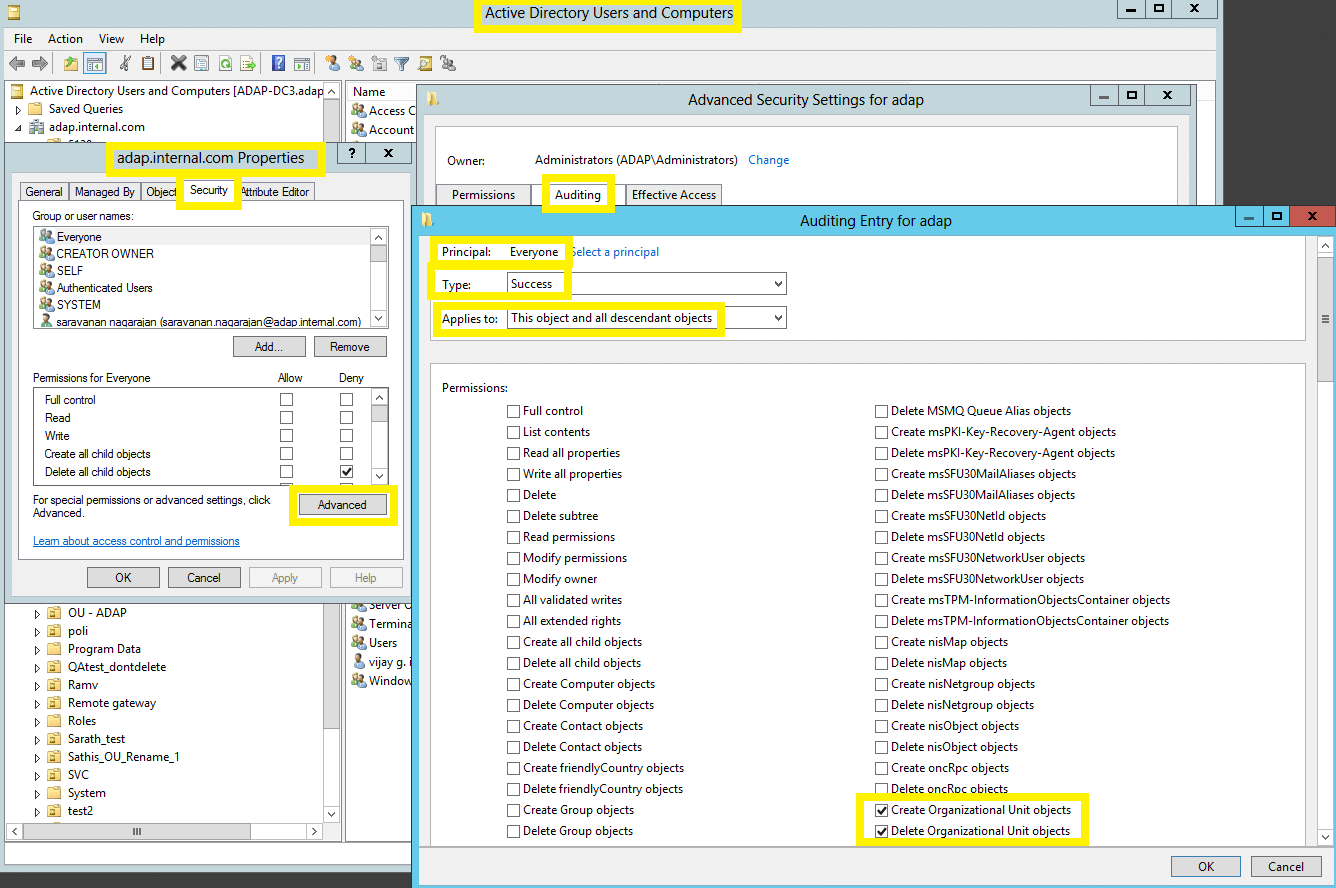
Image displaying: Auditing Entry number 1.
Note: All 12 Auditing Entries must be enabled.
Note: Use Clear all to remove all permissions and properties before selecting the appropriate permissions.
| Auditing Entry | Access | Apply onto | |
|---|---|---|---|
| Windows Server 2003 | Windows Server 2008 and above | ||
| Container |
|
Container objects | Descendant Container objects |
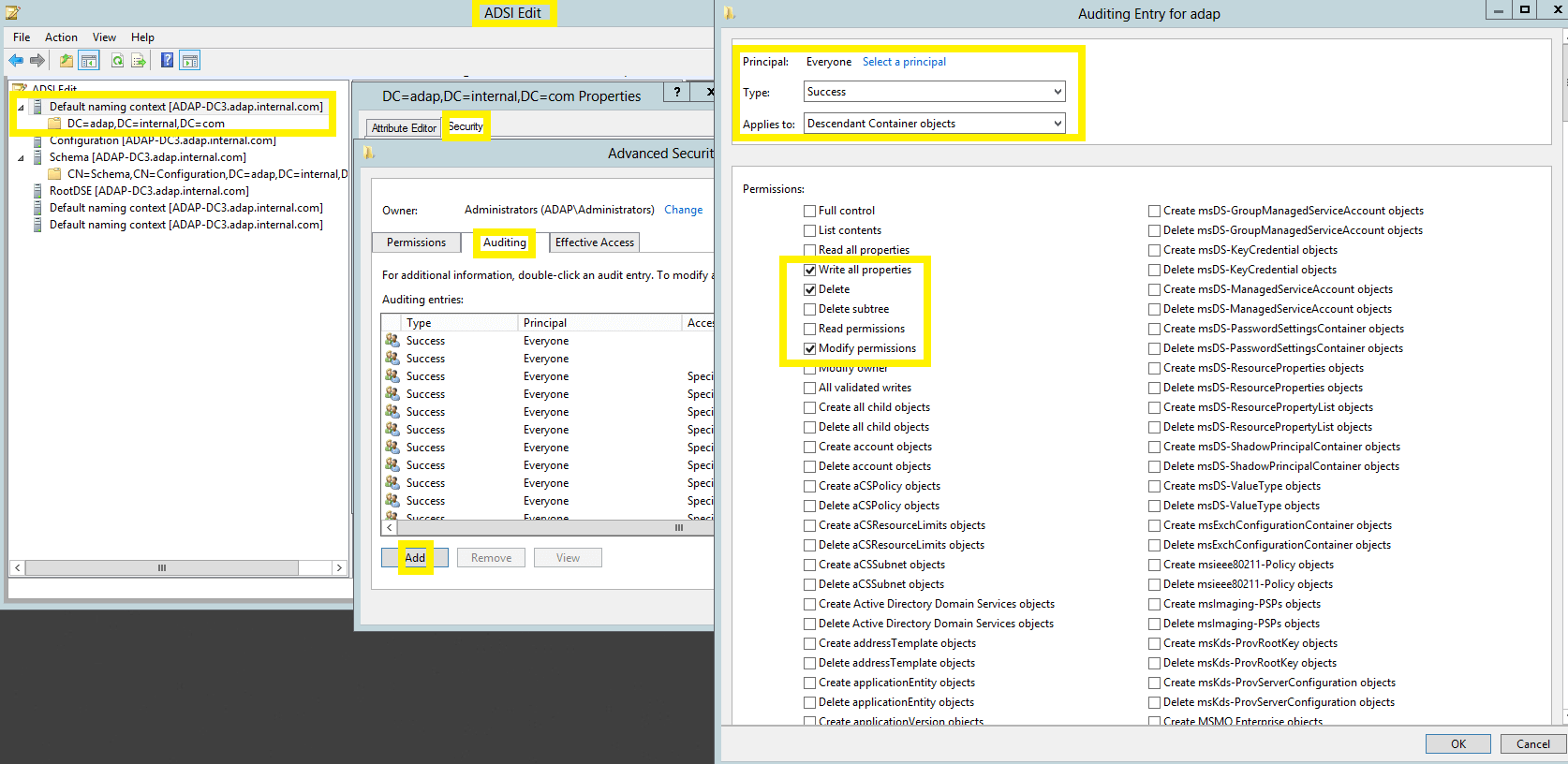
Note: Use Clear all to remove all permissions and properties before selecting the appropriate permissions.
| Auditing Entry number | Auditing Entry for | Access | Apply onto | |
|---|---|---|---|---|
| Windows Server 2003 | Windows Server 2008 and above | |||
| 1&2 | Password Settings Container |
|
Not Applicable | This object and all descendant objects |
|
Not Applicable | Descendant msDS-PasswordSettings objects | ||
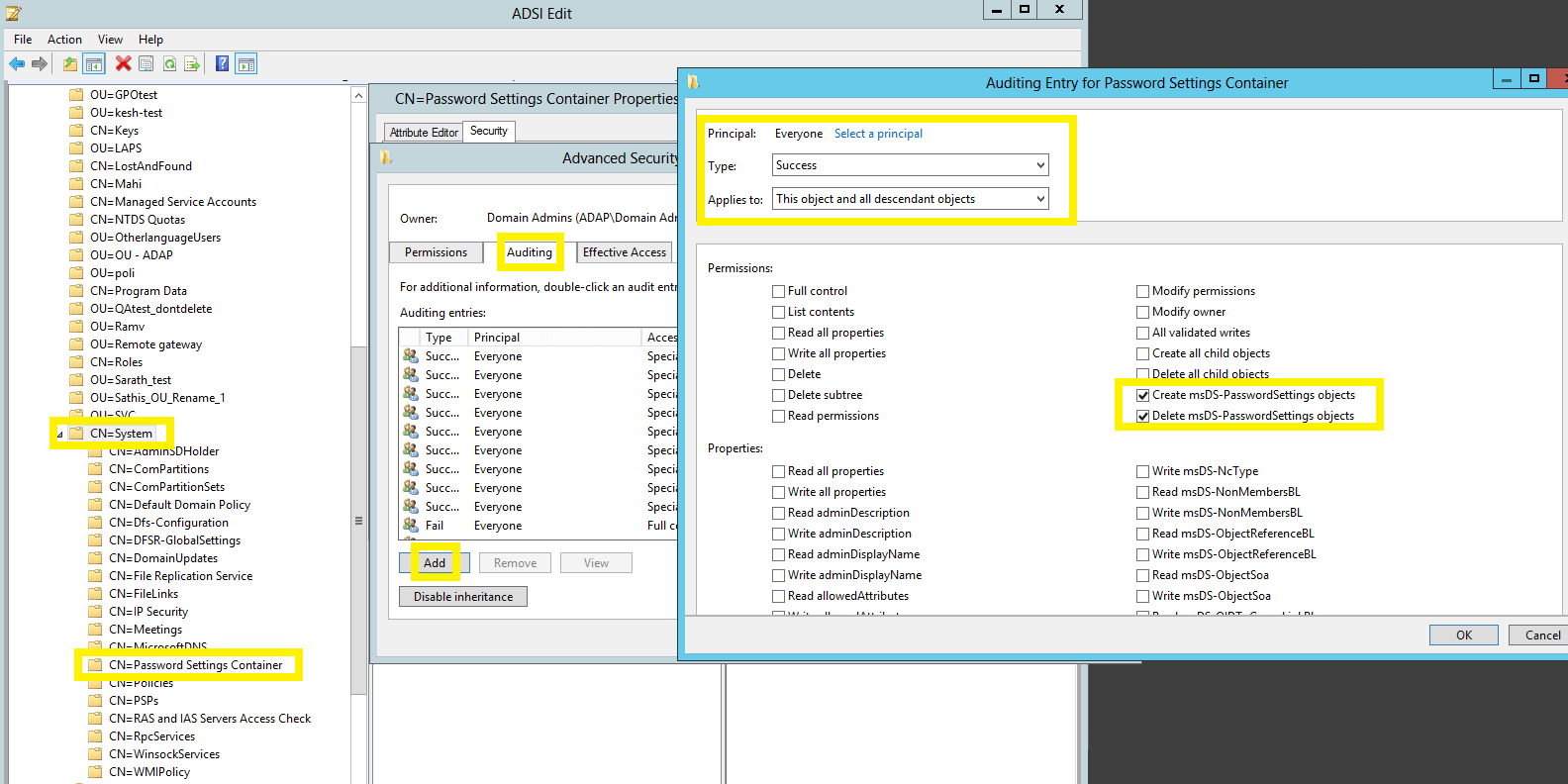
Image showing: Auditing Entry number 1.
Note: Both Auditing Entries must be enabled.
Note: Use Clear all to remove all permissions and properties before selecting the appropriate permissions.
| Auditing Entry for | Access | Apply onto | |
|---|---|---|---|
| Windows Server 2003 | Windows Server 2008 and above | ||
| Configuration |
|
This object and all child objects | This object and all |
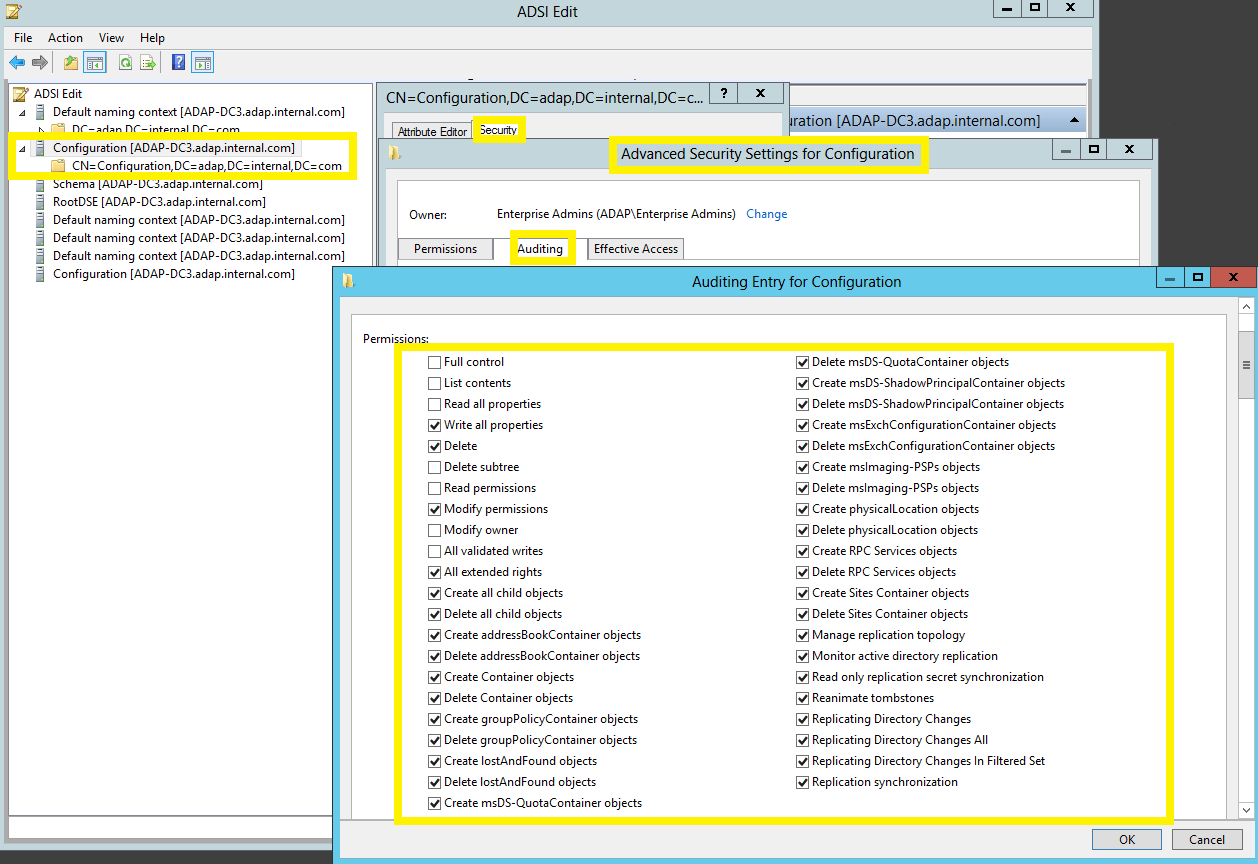
Note: Use Clear all to remove all permissions and properties before selecting the appropriate permissions.
| Auditing Entry for | Access | Apply onto | |
|---|---|---|---|
| Windows Server 2003 | Windows Server 2008 and above | ||
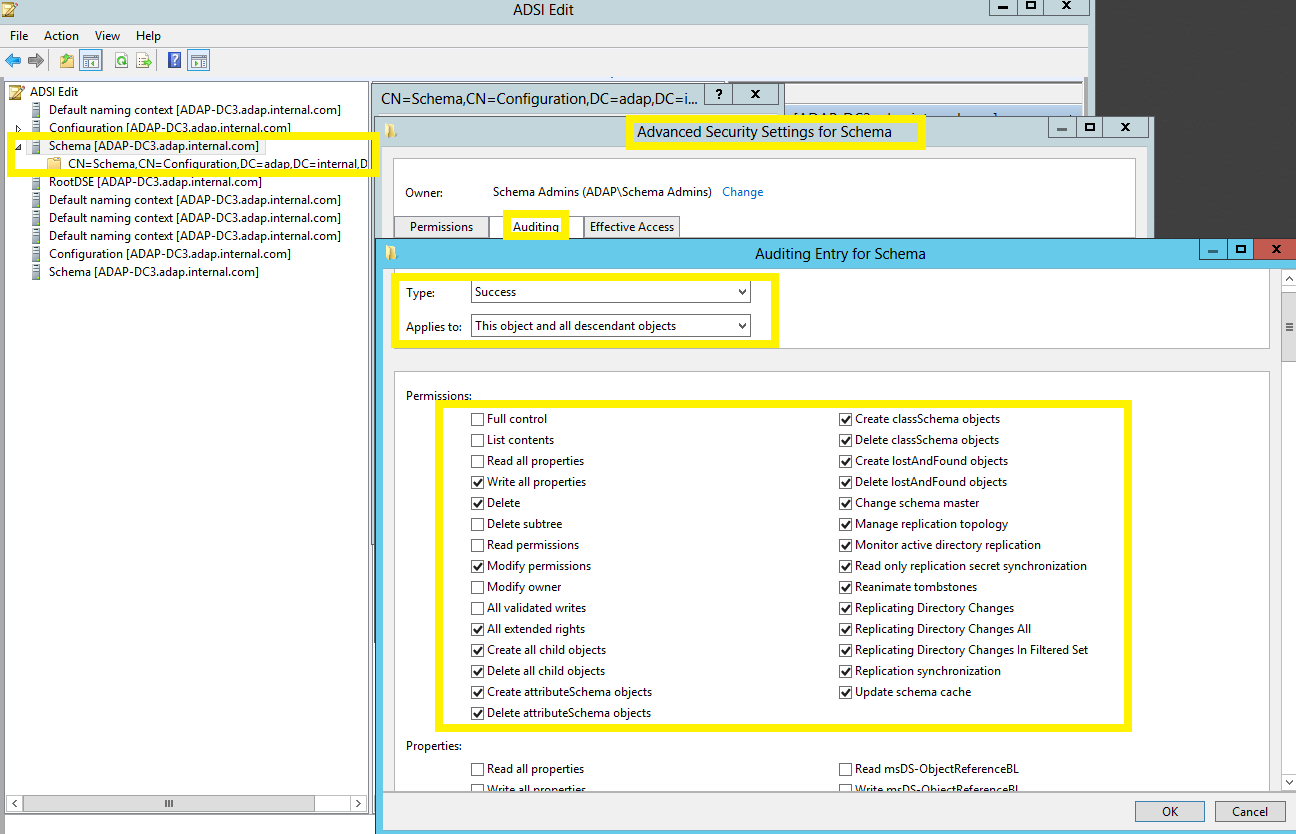
| Schema |
|
This object and all child objects | This object and all descendant objects |
Note: Use Clear all to remove all permissions and properties before selecting the appropriate permissions.
| Auditing Entry number | Auditing Entries for | Access | Apply onto | |
|---|---|---|---|---|
| Windows Server 2003 | Windows Server 2008 and above | |||
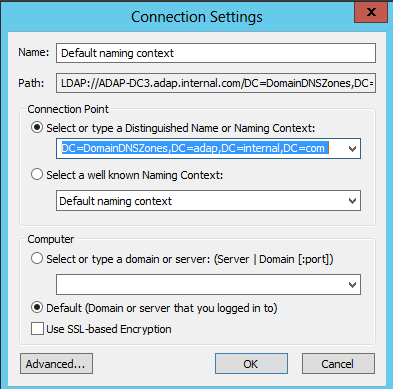
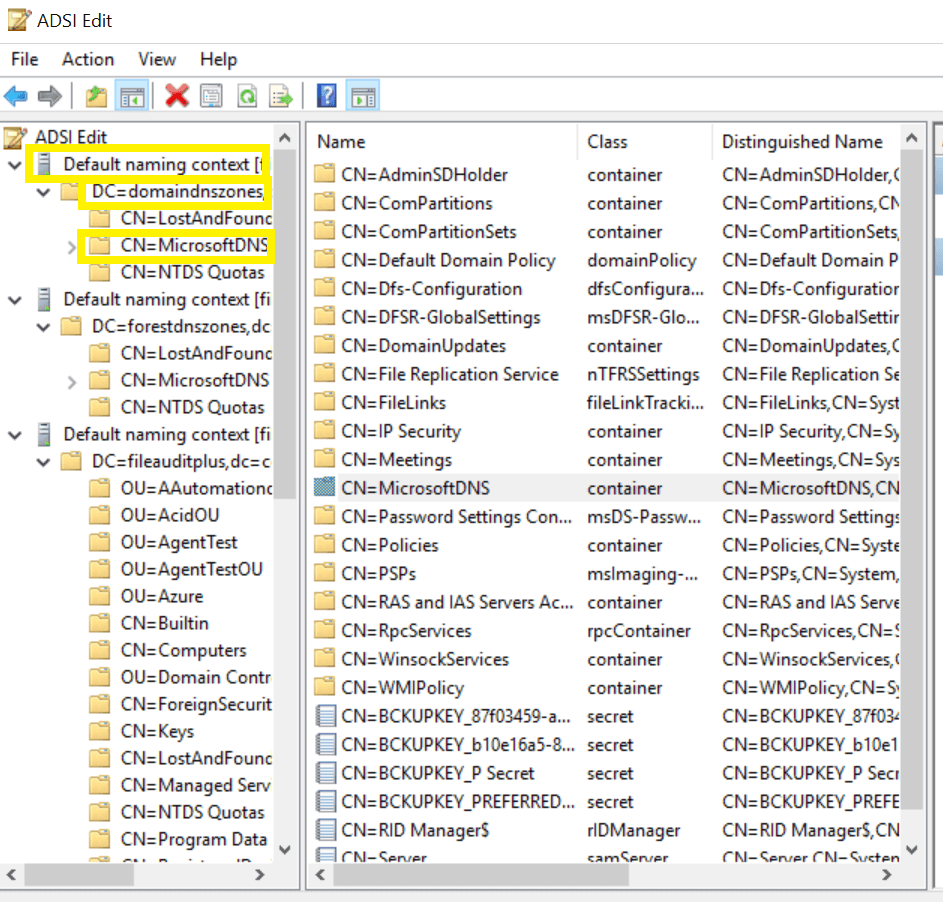
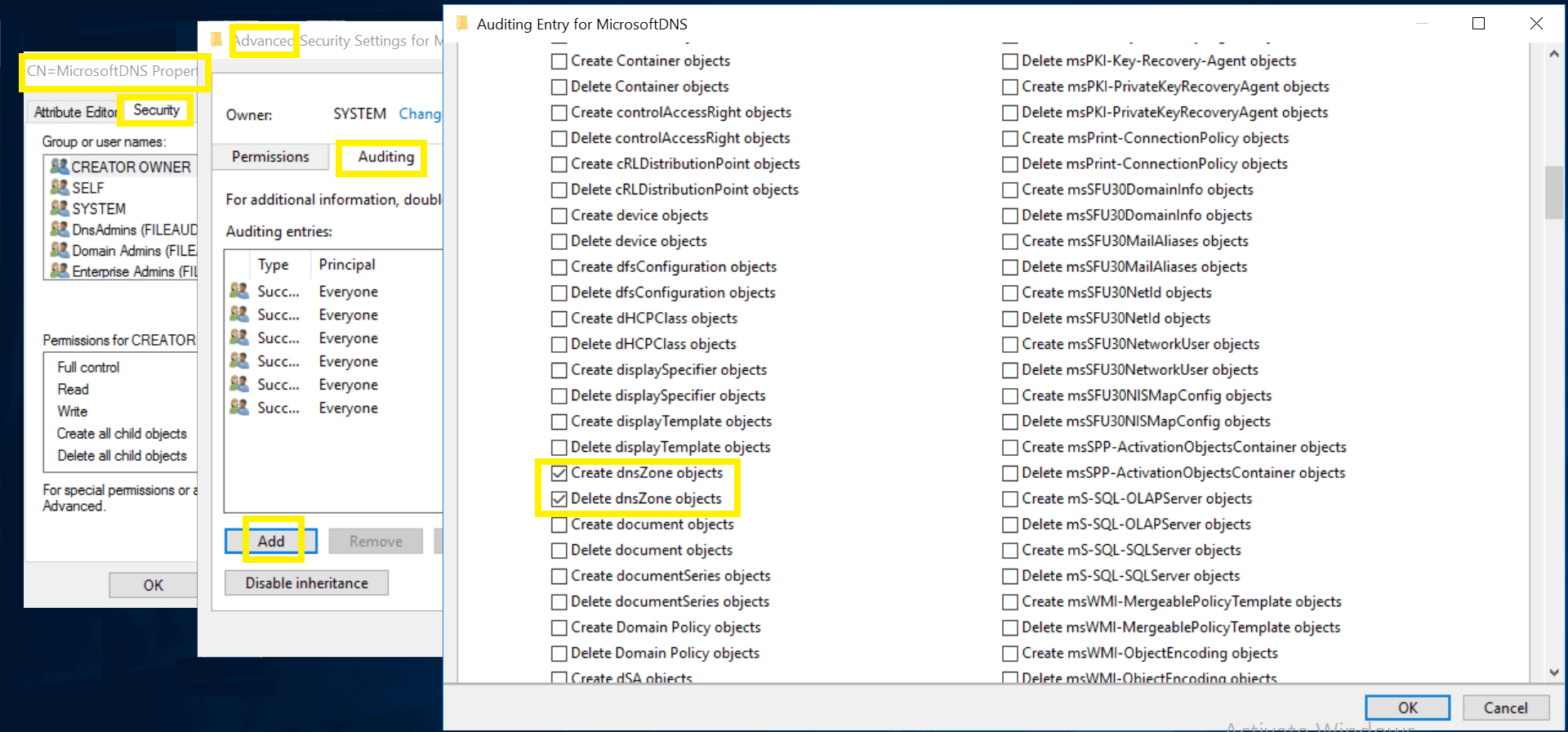
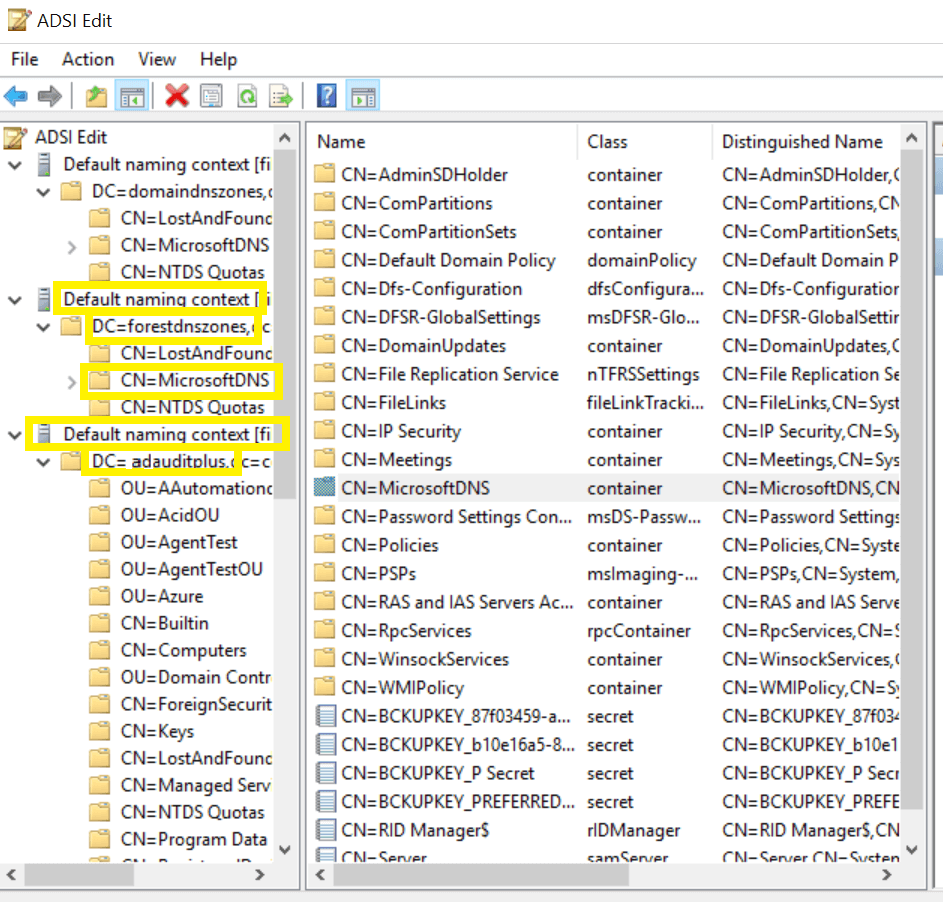
| 1&2 | DNS Zones |
|
This object and all child objects | This object and all descendant objects |
|
DNS Zone objects | Descendant DNS Zone objects | ||
| 3&4 | DNS Nodes |
|
This object and all child objects | Descendant DNS Zone objects |
|
DNS Node objects | Descendant DNS Node objects | ||
Note:Repeat steps iii. and iv. for the remaining 2 default naming contexts.
Copyright © 2020, ZOHO Corp. All Rights Reserved.